CHAPTER 45. Firewalls
SOME OF THE MAIN TOPICS IN THIS CHAPTER ARE
Intrusion Detection (Stateful Inspection) 877
Inexpensive Firewalls for SOHO Environments 889
How Do You Know That the Firewall Is Secure? 891
You must be on the Internet if you want your business to remain competitive during the next decade. Yet the Internet remains an insecure territory, much like those in the old Wild West days. To help keep your network protected from people who would try to cause you problems, it is unthinkable for a business in today’s market to make a connection to the Internet without using a firewall. The term firewall is casually tossed around by news reporters and in magazine articles, and it might be difficult for you to understand exactly what a firewall is and what it does. That’s because a good firewall is not a single entity, but instead a set of components, each of which has a specific purpose. In this chapter, you’ll look at some basic firewall technologies and the problems they help prevent. With this knowledge, you’ll be in a better position to make decisions about how best to protect your network.
What Is a Firewall?
A firewall is a set of components that stands between your network and the Internet and acts as a gatekeeper, allowing in trusted friends and keeping out known or suspected enemies. A firewall can be a single device, such as a router, computer, or dedicated hardware appliance, which has software capable of making the decisions needed to monitor the flow of data to and from the corporate network and the outside world. A firewall also can be composed of more than one router, computer, or network appliance, each performing a specific function. For small offices/home offices (SOHO)—especially those using a broadband, always-on connection—a simple firewall appliance that you can purchase at the local computer store might be all you need. Just about every device that is called a broadband router/switch supports such basic functions as Network Address Translation (NAT), which is covered in this chapter. These inexpensive router/switches do provide some measure of security, but they do not prevent attacks that originate from emails or other locally executed viruses or exploits, especially prevalent in the Windows environment. If you are a home user with a broadband connection, you should install some kind of network appliance between your cable or DSL modem and your computer. Even so, the best protection for SOHO networks is to disconnect your network from your broadband connection when you are not using it. The next best option is to use a firewall program that prevents unauthorized outbound traffic. Additionally, as with every computer connected to the Internet, you should be using an antivirus software package on a regular basis, and using the service offered by the manufacturer to keep the virus database up-to-date.
Note
Although this chapter is targeted toward business entities that have valuable data to protect, the information here also can be useful to home users. If you have a broadband connection—be it DSL (digital subscriber line) or a cable modem—for your home computer, you might find yourself either the victim of an attack or an unwitting accomplice to an attack on another larger network. Most of the denial-of-service attacks that have been aimed at popular websites involve a multitiered attack method known as a distributed denial-of-service attack. This type of attack involves breaking into computers of home users and planting the attack program code that will be used later to attack the actual target site. Because many home users are not security conscious, they might have such a program on their computers and never know it. Yet, after infiltrating hundreds, if not thousands, of innocent home computers and installing the attack program, the attacker simply needs to send a command out to these systems to begin an attack on a third party.
Several kinds of firewall technologies are used, and they generally can be classified into the following categories:
![]() Packet filters
Packet filters
![]() Stateful inspection
Stateful inspection
![]() Proxy servers
Proxy servers
![]() Hybrids
Hybrids
Although many vendors offer firewall products (implemented in both hardware and software products), the technology used is so diverse that it’s difficult to make direct comparisons between products. The best you can do is carefully review each product and ask a lot of questions before deciding whether it will offer the protection you need for your network. Also remember that even though new security holes are always popping up for firewall products, networks, and computer operating systems (OSs), many times a security breach occurs simply because a particular router or computer is not properly configured from a security standpoint. This chapter covers the basic concepts used for firewall technology. However, as this field continues to adapt and grow, you should be careful when choosing a solution for your network. Evaluate products from many vendors before making a purchase.
Tip
As suggested in Chapter 43, “Auditing and Other Monitoring Measures,” in a large network you need to dedicate staff members to exclusively handle firewall duties. A firewall in a SOHO environment is not the same as a firewall in an enterprise network. In larger networks where there are many connections to the Internet, a dedicated staff is required to monitor, update, and fix problems as they occur. In this environment you cannot simply set up a hardware or software firewall and expect that your LAN or network is now secured from the outside world. Just as firewall technology continues to adapt to new conditions, so do hackers and others who may cause harm to your network.
Packet Filters
A packet filter provides the most basic functions of a firewall and can be implemented with a simple router. Indeed, packet-filtering routers were the first type of firewall created to help keep a network safe from intruders. A packet filter examines every network packet that passes through it, and either forwards or drops the packet, according to a set of rules established by the firewall administrator. Just about every router being manufactured today allows you to restrict traffic flowing inward or outward based on the contents of the TCP/IP packet header information.
A packet filter can be configured to block traffic by creating filters for the following:
![]() IP addresses—This includes both source and destination addresses. You can specify individual addresses or ranges of addresses.
IP addresses—This includes both source and destination addresses. You can specify individual addresses or ranges of addresses.
![]() Protocols—Typical protocols include UDP (User Datagram Protocol) and the TCP (Transmission Control Protocol).
Protocols—Typical protocols include UDP (User Datagram Protocol) and the TCP (Transmission Control Protocol).
![]() Port numbers—Port numbers are used to identify connections between applications, such as FTP or Telnet. You usually can specify a range of port numbers, or use filters that allow you to say “greater than” or “less than” a port number.
Port numbers—Port numbers are used to identify connections between applications, such as FTP or Telnet. You usually can specify a range of port numbers, or use filters that allow you to say “greater than” or “less than” a port number.
![]() Direction—Filtering can be done based on whether the network packet is coming into your network from the Internet or being sent out by a user on your network to the Internet.
Direction—Filtering can be done based on whether the network packet is coming into your network from the Internet or being sent out by a user on your network to the Internet.
Note
As indicated, firewalls stand between your network and the Internet. However, in a large corporate network, firewalls are also typically deployed between different networks that exist within the same company. For example, you might place a firewall between the network used by the payroll department and the network that handles manufacturing computers for your company. Think of a firewall as a locked door, which can be used to keep out those who do not belong. Although usernames and passwords provide a general sort of security within your network, it’s probably a good idea to isolate network segments that contain sensitive information from the rest of your network. Usernames and passwords are easily compromised. A properly configured firewall is not.
Filtering on IP Addresses
Chapter 24, “Overview of the TCP/IP Protocol Suite,” discusses the information found in the Internet Protocol (IP) packet header. To briefly review, the IP protocol is used by other higher-level protocols (such as TCP and UDP) to provide a connectionless best-effort data-delivery service. To do so, the IP datagram encapsulates the TCP or other protocol segment by adding source and destination addresses, port numbers, and other header information before sending the datagram farther down the protocol stack, where it is eventually transmitted on the wire bit-by-bit by the physical components of the network.
Routers can be configured easily to examine the contents of the IP header and drop packets that don’t match a set of rules that the network or firewall administrator configures on the router. Perhaps the most obvious example is to filter out packets arriving from the Internet that have a source address that falls within the same network address range used on the internal network. Because such a packet, if it were indeed valid, would have to originate inside the network, it shouldn’t be coming in from the outside! It is easy to forge IP packets so that the source address, as well as other header information, can be set to anything a hacker desires. A lot of programs are freely available on the Internet to do this.
When a packet with a source address is sent into your network, it’s more likely that the destination server or workstation in your network will accept it as a valid packet, thinking it’s coming from a user on the local network, and the packet will be processed as usual. Using this method, it’s easy to get packets into your network and actually have them delivered, when they should not be.
This is only one example of a good reason to filter packets based on the IP addressing information in the packet header. Because addresses can be forged, and because it’s not practical to list all the millions of addresses that are allocated to computers on the Internet and pick and choose, you need to be cautious when using this kind of specific filtering. For example, suppose your network becomes the subject of a denial-of-service attack. You can use a network analyzer to discover the source addresses of the packets, and quickly insert a rule in the router (or firewall product) database that drops all packets that come from the network from which those packets are coming.
![]() Network analyzers are discussed in Chapter 49, “Network Testing and Analysis Tools.”
Network analyzers are discussed in Chapter 49, “Network Testing and Analysis Tools.”
Filtering Based on Protocols
In the IP packet, a field is used to indicate the type of protocol the packet is carrying data for. For example, if the IP packet is carrying TCP data, the protocol field in the IP header is 6. If it’s carrying an ICMP (Internet Control Message Protocol) message, the protocol number is 1. The capability to filter out certain protocols is useful because many of the protocols in use on the Internet were created many years ago when security was not as much of an issue as it is in today’s commercial Internet.
Take ICMP, for example. The Ping utility makes use of ICMP packets to determine whether another host is reachable. An ICMP ECHO REQUEST packet is sent to the address of the host computer in question. If it receives the packet, the destination computer sends back an ICMP ECHO REPLY packet. Sounds simple and safe, doesn’t it? Well, it is simple, but not necessarily safe. Inside your network, Ping can be a useful tool for quickly determining that somewhere along the network path something is wrong and a computer is not reachable, whether the destination you are pinging is inside your network or on the Internet.
However, just as you wouldn’t give out your credit-card number to a stranger, it’s not a good idea to give out any information about your network, especially the addresses of the computers on the network, to an outsider. And, that’s exactly what the ping command can do. It’s easy to write a program that sits back and cycles through a range of IP addresses, sending out ICMP ECHO REQUEST packets and looking to see what replies come back. This saves a malicious hacker time because he now knows that an IP address is in use and can proceed to further try to intrude and compromise the system. Because automated tools are available for continuing the hacker’s probe, it’s imperative that you keep your network address information secret.
If you’ve ever received those boring telemarketing calls during the early evening hours, you can understand how this works. The telemarketers just cycle through phone numbers until they get someone to pick up the phone and answer. Allowing ICMP ECHO REPLY packets to respond to requests from outside your network is the equivalent of picking up the phone. Although you can hang up on a telemarketing call, after a hacker has your network address, she can always try back later when you’re not around and use a wide variety of tools to probe your system to determine what is needed to get inside.
For this reason, it’s usually a good idea to block incoming ICMP ECHO REQUEST packets. You probably don’t want to block outgoing packets of the same sort, because they serve a useful purpose. You can allow users inside your network to Ping other servers on the Internet. For example, suppose you want to place an order with a business that has a website, yet it doesn’t pop up in your browser when you try to get to its home page. You can use Ping to determine whether the business’s computer is on the Net and functioning, and then from there start your troubleshooting efforts to find out why you can’t bring up the business’s Web page. If you Ping the site and get no response, you can be sure that either it’s down or somewhere along the network path a router or another device is not letting traffic get through.
The same goes for you if you offer a service on the Internet. However, in such a case, you should make sure that your Web servers are highly secured and located on a network segment that can limit the damage should these servers be compromised. This network segment is called a demilitarized zone (DMZ), and you’ll learn more about that later in this chapter.
Another utility that uses ICMP is Tracert. This command probes the network path and returns a list of all the routers and other intermediary devices it passes through to get to a destination address. Again, this is a useful tool when used properly, but you should block this sort of packet at your firewall. Do you want outsiders to know the addresses of routers and other devices on your network? After an outsider has the address and knows that a computer is online using that address, it’s easy to use one of the many hacker tools available on the Internet to begin breaking into the computer.
![]() You can learn more about using the Tracert and Ping commands in Chapter 27, “Troubleshooting Tools for TCP/IP Networks.”
You can learn more about using the Tracert and Ping commands in Chapter 27, “Troubleshooting Tools for TCP/IP Networks.”
Filtering Based on Port Numbers
The TCP and UDP protocols use port numbers in their header information to identify applications. Although filtering based on IP addresses blocks all network traffic from a particular source, you can use filtering rules that block only specific ports. Thus, you might allow customers to interact with Web servers inside your network using the ports set aside for WWW activity—port 80, for typical WWW traffic—but block other ports, such as port 23 that is used for Telnet functions.
As another example, you might want to allow some users to use Telnet (port 23) or FTP (ports 20 and 21) to connect to servers outside the corporate network while denying this capability to others. You can do this by setting up rules in the packet filter and specifying both a host source address and a port number. Ports are a two-way path. You can block incoming connections, outgoing connections, or both for each port.
Packet filtering is an integral component of most every firewall and has several advantages:
![]() Usually inexpensive—If you use a router to connect to external sources, you already have the hardware—you just need to configure it.
Usually inexpensive—If you use a router to connect to external sources, you already have the hardware—you just need to configure it.
![]() Fast—It does only minimal processing on the header information and does not make decisions based on multiple packets.
Fast—It does only minimal processing on the header information and does not make decisions based on multiple packets.
![]() Flexible—It is easy, although some would say cumbersome, to configure as many address inclusions or exclusions as you like.
Flexible—It is easy, although some would say cumbersome, to configure as many address inclusions or exclusions as you like.
However, there are also several disadvantages to using a packet filter firewall:
![]() Packet filters perform no authentication—A packet is a packet no matter “who” the sender is. The address is the only thing that counts. This is important because IP addresses, ports, and any other part of the packet can be forged using simple tools available on the Internet.
Packet filters perform no authentication—A packet is a packet no matter “who” the sender is. The address is the only thing that counts. This is important because IP addresses, ports, and any other part of the packet can be forged using simple tools available on the Internet.
![]() Most system administrators don’t take advantage of a router’s auditing features—You will most likely not even know that attempts were made to break in to the network; if the router does provide some kind of statistical information, you won’t be able to determine where the attack came from. If you turn on logging for every packet that comes through your router, you’ll experience a tremendous slowdown in network response time through the router. Selectively logging events is a better option, but then again you might miss important events. Small SOHO routers do not provide logging, so keep that in mind if you use one.
Most system administrators don’t take advantage of a router’s auditing features—You will most likely not even know that attempts were made to break in to the network; if the router does provide some kind of statistical information, you won’t be able to determine where the attack came from. If you turn on logging for every packet that comes through your router, you’ll experience a tremendous slowdown in network response time through the router. Selectively logging events is a better option, but then again you might miss important events. Small SOHO routers do not provide logging, so keep that in mind if you use one.
![]() Packet filters operate at the network level—They are not very effective at stopping sophisticated attacks that are directed at higher-level protocols, such as TCP.
Packet filters operate at the network level—They are not very effective at stopping sophisticated attacks that are directed at higher-level protocols, such as TCP.
![]() Internal network information is not kept from outside prying eyes—Using ordinary utilities, such as Tracert and Ping, mischievous persons can gain knowledge about your network unless you specifically block the protocol used by these utilities (ICMP).
Internal network information is not kept from outside prying eyes—Using ordinary utilities, such as Tracert and Ping, mischievous persons can gain knowledge about your network unless you specifically block the protocol used by these utilities (ICMP).
Note
Although a typical packet filter is fast, more advanced devices offer additional service that can be compute-intensive. Extensive logging is one example. The capability to detect a large number of bad packets coming into the network in a short time can also be useful. Using this technique, packet filters can block access to subsequent packets. This can be useful in a denial-of-service attack.
If you had the choice, which of the following would you choose:
![]() Allow everything, but deny specific addresses.
Allow everything, but deny specific addresses.
![]() Deny everything, but allow selected known good addresses.
Deny everything, but allow selected known good addresses.
If it’s not obvious that the second choice is the best, you need to stop and think about this again.
A good approach for configuring the rules to use on a packet filter is to first deny all traffic. Then, selectively enable only those addresses or services that are essential to your business. If you try to do this in reverse—allowing all traffic and then denying specific items—there’s no way you can create a set of rules that covers all possible sources of mischief. You might leave out something that didn’t seem important at the time you did the configuration, or a new twist on an old technology might creep up and surprise you later.
Intrusion Detection (Stateful Inspection)
A stateful inspection device operates in a manner similar to a packet-filtering firewall in that it also examines the source and destination addresses of every packet that passes its way. However, a packet filter is never aware of the context of any communication. Each packet that passes through it is treated on an individual basis. A firewall that employs stateful inspection techniques attempts to keep track of requests and responses to be sure they match.
This type of firewall maintains tables of information about current connections so that it can determine whether incoming packets are unsolicited or whether they are in response to a request that was made by a user on the internal network. Another name sometimes used for this type of firewall is dynamic packet filter.
When a connection terminates, the firewall removes the reference from its internal table so that an external source cannot use it to gain entry again.
Many proprietary stateful inspection firewall products are on the market today. Study the documentation of this type of product before you make a purchase so that you can fully understand how it operates.
Filtering Based on Applications
Filtering based on applications enables you to specify which programs are permitted to access the Internet, rather than specifying which TCP or UDP ports are permitted to access the Internet. This type of filtering is a form of stateful packet inspection (SPI) that is designed to make configuration relatively simple for the end user.
The updated version of Windows Firewall introduced in Windows XP Service Pack 2 as well as most third-party firewall programs use application filtering. Note that most firewalls, including Windows Firewall, can also perform port-based filtering when necessary.
Application-based firewalls enable the user to specify a list of applications (sometimes known as trusted applications) which can be used for network and Internet access. Applications not on the trusted list trigger a warning when an attempt is made to access them from the network or Internet (depending on the firewall’s configuration).
Windows Firewall Versus Third-Party Firewall Programs
Although both the Windows XP Service Pack 2 Firewall (Windows Firewall) and third-party firewalls are application-based, there are significant differences in how they operate.
The Windows Firewall is enabled by default when Windows XP Service Pack 2 is installed. It is controlled through the Windows Firewall icon in Control Panel, or through the Advanced tab of the network connection properties sheet in Network Connections.
Windows Firewall includes a default list of programs it permits to accept incoming connections. You can add programs to the list or specify particular TCP or UDP ports as desired for programs in which application-based filtering does not work properly.
It is commonly believed that any application that is not on the list and attempts to listen for inbound traffic will trigger an alert dialog. This is not correct. Some programs include Windows Firewall API function calls which will automatically create exceptions to the firewall when the program is run, but the program will not be listed on the Exceptions list. However, when the Windows Firewall detects a connection by a program that does not use Windows Firewall APIs and has not been manually granted access, it displays an alert dialog asking you if you want to:
![]() Keep blocking—Click this option to continue to block the program from Internet access and adds the program to the exceptions list in a Disabled state
Keep blocking—Click this option to continue to block the program from Internet access and adds the program to the exceptions list in a Disabled state
![]() Unblock—Click this option to permit the program to access the Internet and adds the program to the exceptions list in an Enabled state
Unblock—Click this option to permit the program to access the Internet and adds the program to the exceptions list in an Enabled state
![]() Ask me later—Blocks program this time, but the next time the program runs, Windows Firewall will again ask whether to block or unblock the program
Ask me later—Blocks program this time, but the next time the program runs, Windows Firewall will again ask whether to block or unblock the program
It’s important to realize that Windows Firewall is designed to stop unauthorized programs from listening for incoming traffic. It does not block outgoing traffic. Consequently, Windows Firewall cannot stop worms, spyware, and Trojans that send data out to remote computers.
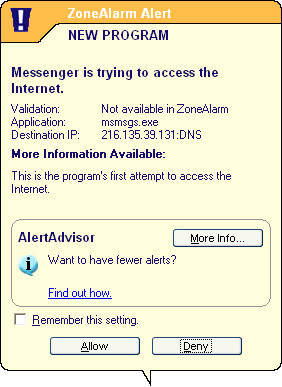
By contrast, many third-party firewalls are usually configured to block both inbound and outbound connections. Firewalls with inbound and outbound filtering usually display a dialog when a program attempts to make an outbound connection and asks the user if the program should be granted access (see Figure 45.1).
Figure 45.1. The ZoneAlarm firewall program displays an alert when a program attempts to access the Internet.
Outbound access can be granted on a one-time or continuous basis. If you select the option to permit access one time only, the firewall program will ask you for permission the next time the program attempts outbound access. Select an option such as “Remember this setting” (refer to Figure 45.1) to permit the program to have Internet access from now on.
Unauthorized inbound connections are usually blocked automatically. Depending upon the firewall program, an alert dialog might be displayed. You can configure the firewall to permit or continue to block inbound connections. The ability to monitor and block both inbound and outbound access is very useful at stopping Trojans, spyware, and other threats that connect to a remote server as part of their operation. This is one of the biggest advantages of third-party firewall programs over Windows Firewall.
Both Windows Firewall and third-party firewalls can be configured to permit different levels of access. For example, Windows Firewall’s Change Scope option (located on the Edit tab) permits you to unblock a particular program for any computer (including Internet access), all computers on the current subnet, or a custom list of specified IP address ranges.
Proxy Servers
Proxy servers, also known as application gateways, provide protection for your network at the Application layer. Although packet filters make decisions based on the header information in a packet, they do not understand the application protocols, such as FTP or HTTP. Thus, it’s easy for a hacker to exploit known problems with application protocols, and problems can ensue if the packet filter allows the packet to enter the network.
A proxy server can perform this function by managing connections to and from the outside world. A proxy server acts as a “man in the middle” by accepting requests for an application for your users and making that request for them. A proxy server never allows a packet to pass through the firewall; instead, a proxy server follows these steps:
1. Receives an outgoing request from one of your users. It creates a new packet and substitutes the proxy server’s own address as the source address, replacing the user’s actual source address.
2. The proxy server sends this new packet out onto the Internet on behalf of the user.
3. When a response is received from the Internet server, the proxy server examines the packet to determine whether the data contained in the packet is appropriate for the particular application. If so, it creates a new packet, inserts the data, and places the Internet server’s address in the source address field. The packet then is sent back to the original user.
4. The user receives the packet and assumes that it’s actually communicating directly with the Internet server—after all, it has the correct addressing information in the header.
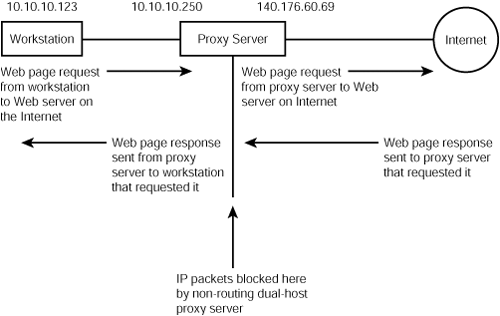
Figure 45.2 shows an example of how a typical proxy server functions.
Figure 45.2. A proxy server communicates with the computer inside your network and the Internetserver, but it does not allow network traffic to pass directly through the firewall.
Proxy servers also can be used to provide authentication, logging, content filtering, and other security measures. There are two kinds of proxy servers: classical proxy servers and transparent proxy servers.
A classical proxy server can be used with any application. The user needs to take a few extra steps to use the proxy server because the application itself was not written to understand the proxy process. A classical proxy server works in the following manner:
1. A client executes a command, such as the Telnet command, to connect to the proxy server.
2. The proxy server receives this request and sends a packet back to the user prompting for authentication information, such as a username and password.
3. The user interacts with this man-in-the-middle by entering the required information.
4. If the proxy server has been configured to allow this user to make use of the service, it prompts the user to enter the target system for the service. For example, after being authenticated by the proxy server, a user could enter [email protected]. In this example, username is the username that will be used to authenticate the user on the Internet server, and internetserver.com is the name of the Internet server to which the user wants to make a connection.
5. The proxy server proceeds to create a packet containing the Telnet request, and sends it out onto the Internet. The Internet server sends back a packet requesting a password (if required) for the service.
6. The proxy server prompts the user to enter the password and passes it back to the Internet server. If the authentication succeeds, the proxy server begins operating as described earlier, by intercepting packets to and from the Internet server, substituting its own address for the user’s address when sending packets to the Internet server, and substituting the Internet server’s address for packets returned to the client.
After the initial authentication and connection to the service, each side of the communication process thinks it’s actually talking to the other. However, because the user must initially authenticate himself to the proxy server, this type of proxy might be undesirable in some environments because some users find these extra steps a burden.
Note
A popular proxy server product called the TIS Internet Firewall Toolkit (FWTK) can be downloaded from the Internet. This kit contains proxy applications for most of the usual Internet services, such as Telnet, email, and FTP, and allows you to create your own specific proxy server applications. You can read more about this package and download it free from www.fwtk.org.
A transparent proxy server works a little differently. In this case, the application is modified so that it understands that a proxy server is being used. For this to work, you must tell the application the address of the proxy server for each service you want to use. For example, to configure proxy server information in Internet Explorer, you would take these steps:
1. Select Start, Programs, Internet Explorer (or Start, Internet Explorer if this appears in the top portion of the Start menu).
2. Select Tools, Internet Options. When the Internet Options properties page appears, click the Connections tab.
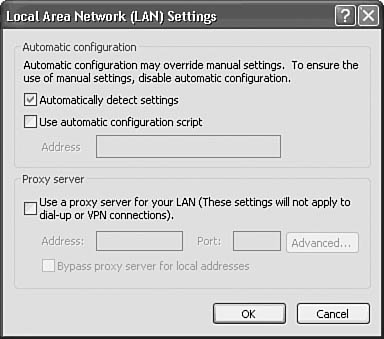
3. At the bottom of the page, click the LAN Settings button to open the Local Area Network (LAN) Settings dialog box (see Figure 45.3).
Figure 45.3. The Local Area Network (LAN) Settings dialog box allows you to select automatic configuration of a proxy server or enter the information yourself.
4. In Figure 45.3, the Automatically Detect Settings check box has been selected. If your network is configured to distribute this information automatically, all you need to do is select this check box and click the OK button. Internet Explorer queries the network to determine the proxy server settings and sets them up for you automatically. The Use Automatic Configuration Script check box can be used in a similar manner, but you’ll have to get the address for the server that contains the file from your network administrator.
5. To manually configure a proxy server, select the Use a Proxy Server check box, and enter the address or hostname of the proxy server and the port that will be used (typically port 8080). This sets up Internet Explorer to use the same proxy server for all the network services you use.
6. If you want to configure each service separately, click the Advanced button shown in Figure 45.3, and the Proxy Settings dialog box appears (see Figure 45.4).
Figure 45.4. Use the Proxy Settings dialog box when you need to use more than one proxy server for different network services.
7. In Figure 45.4, you can see that Internet Explorer allows you to enter a different proxy server and port for several common network applications. You can use the Exceptions pane to enter hostnames or addresses that should not go through the proxy server. For example, hosts that reside inside your network can be contacted directly, and you don’t need to use a proxy server to reach them. If you use this feature, you can enter more than one name or address, separating each entry by a semicolon, and you can use the asterisk (*) character as a wildcard. When finished, click OK.
Standard Proxy Applications
Most off-the-shelf firewall products come with proxy applications for commonly used network applications, such as these:
![]() Telnet
Telnet
![]() FTP
FTP
![]() X Windows
X Windows
![]() HTTP
HTTP
![]() HTTPS
HTTPS
![]() Mail (POP and SMTP)
Mail (POP and SMTP)
![]() Socks
Socks
![]() News (NNTP)
News (NNTP)
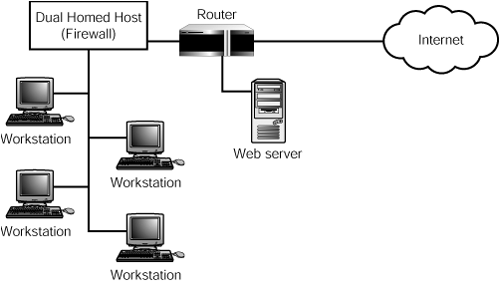
Because proxy servers operate at the application level, they are sometimes referred to as application gateways. You can set up the gateway using several different topologies. An example of an application gateway is a dual-homed host that runs the proxy software. In this setup, a computer has two network cards, each attached to a different network. Proxy software runs on the host and mediates between the two, deciding what traffic it will allow to flow between the two networks. You can set up a Unix or Windows NT/2000/2003 Server computer to perform this kind of function. In Figure 45.5, you see a small network that uses a router to connect to the Internet.
Figure 45.5. A dual-homed host is used to connect the local network to the Internet.
However, the network is not directly connected to the router. Instead, a computer has been designated for this purpose. The dual-homed host has two network cards—one talks to the router and the other participates in the local network. The router can be configured to perform filtering functions while the dual-homed host can supply the proxy functions for any services you want to allow between your network and the Internet. When this host is configured with maximum security measures to provide a defense from external sources, it is sometimes referred to as a bastion host or a screened host architecture.
As an added advantage, another computer is used to host the company’s Web pages so that Internet users can access them without penetrating the interior company network.
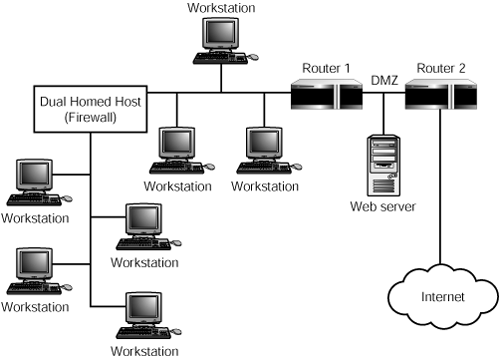
You can carry this concept further by using multiple routers to connect to the Internet. Figure 45.6 shows a setup similar to the one just described, but there are two routers between the innermost network clients and the Internet.
Figure 45.6. Use multiple firewalls to segment users into restrictive and less restrictive networks.
The dual-homed host connects the most secure clients to the first router. Between the dual-homed host and the first router are other computers that do not need the same level of restrictions imposed by the proxy server. Again, the Web server sits on the network at a point closest to the Internet, and thus is subject to fewer restrictions than the other computers on this network. The Web server that sits between Router 1 and Router 2 should be treated very cautiously when it comes to security because it’s the least-protected computer on the network. As stated earlier in the chapter, the space between these two routers is referred to as the demilitarized zone, or DMZ. Another method of creating a DMZ is to use a router with multiple interfaces and select one interface to use for a network segment that will be the DMZ (see Figure 45.7).
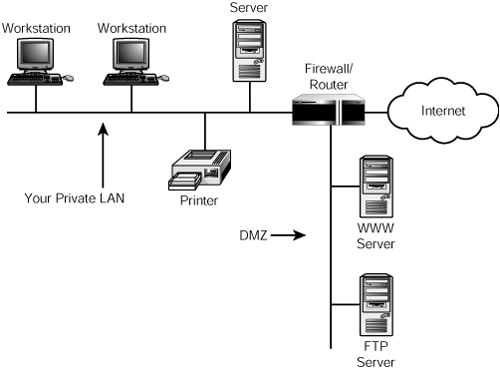
Figure 45.7. A simple DMZ can be created by using a separate LAN segment connected to the router.
In this example, the firewall/router has three adapters: one for the DMZ, one for your private LAN, and one to connect to the Internet. Traffic from the Internet destined to your FTP or WWW servers is never passed by the firewall to the private LAN segment, but only to those servers residing in the DMZ. Thus, if one of your Web servers is compromised, the computers on your LAN are still safe.
Creating a DMZ with a SOHO or Small-Business Router
On a SOHO or small business network that uses a router with Network Address Translation (NAT), a DMZ can also be created by specifying the private IP address of a particular computer or device that needs unrestricted access from the Internet in the router’s DMZ configuration dialog. This dialog is usually located in the router’s advanced configuration section.
A DMZ configuration is sometimes used as an alternative to configuring lists of allowable TDP and UDP ports and applications for use by a firewall device, a firewall program, or the port forwarding feature built into most routers. It permits unrestricted access to and from the IP address specified in the DMZ.
However, while setting up the DMZ for a particular computer is easy, it is not recommended unless it is not possible for particular programs or tasks to be performed in any other way. The reason is that the computer or device in the DMZ has absolutely no protection against remote attacks. By placing the computer or device in the DMZ, address translation and port filtering are no longer present.
Caution
If you decide that you must use the DMZ feature to permit a particular application or task to operate, make sure you specify the correct IP address for the computer. Use the ipconfig command or the list of DHCP clients in the router’s DHCP configuration to determine this information. If your network uses DHCP addressing and many computers or other devices connect and disconnect from the network, consider assigning the computer that will be placed in the DMZ a static IP address. Otherwise, it’s possible that at some point the wrong computer or device will wind up in the DMZ.
To protect sensitive data on the computer in the DMZ, don’t use shared folders on that computer. Store data on another computer.
Contact the vendor of the application, device, or service that will not work unless the computer using it is in the DMZ for a list of allowable TDP or UDP ports that can be configured to permit traffic or for an update to the application or device drivers that will permit the computer to no longer use the DMZ and still function as desired.
Impersonating the End User: Network Address Translation (NAT)
One of the main driving forces behind a new Internet protocol (IPv6) was the assumption that the 32-bit address used by IPv4 was not large enough to keep up with the quickly growing Internet. It was assumed that eventually the entire address space would be used up. Of course, other features of IPv6, such as the security enhancements, also are making it seem as though the Internet eventually will migrate to the newer protocol. However, when you think about how a proxy server works to use its own address instead of the address of the internal network client, it seems that the address space limitation imposed by the 32-bit address is not such a big issue anymore.
Note
IPv6 wasn’t designed just to increase the available IP address space. Other features, such as authentication and encryption, among others, are also part of this protocol. IPv4 is the most widely used version of IP today, especially at the LAN level. And some applications have been created to use some of the features that are present in IPv6 on an IPv4 network. However, in a few years you can expect to see IPv6 work its way outward from the core of the Internet to your LAN. Many large corporate LANs already make use of IPv6, if only for parts of their network.
Because only addresses used by the proxy servers need to be valid and registered on the Internet, what prevents you from using any address range on the internal network? This concept, known as network address translation (NAT) is widely used today for just this purpose. The proxy server uses these addresses with valid IP addresses to conduct business for its clients.
You can use practically any address range for the workstations on the LAN. However, RFC 1597, “Address Allocation for Private Internets,” specifies a range of addresses that are set aside for private networks. When computers on the inside network need to communicate with each other, they use their actual addresses. The proxy server also has an address that falls within this range so that it can talk to both the private LAN and the Internet.
These ranges of IP addresses are exclusively set aside by the RFC for private networks, and cannot be used on the Internet. These are the address ranges:
![]() 10.0.0.0–10.255.255.255
10.0.0.0–10.255.255.255
![]() 169.254.0.1–169.254.255.254
169.254.0.1–169.254.255.254
![]() 172.16.0.0–172.31.255.255
172.16.0.0–172.31.255.255
![]() 192.168.0.0–192.168.255.255
192.168.0.0–192.168.255.255
Tip
If the preceding address ranges look familiar, you are probably connecting to the Internet via a NAT server. Many ISPs use NAT to conserve the range of valid IP addresses allocated to them. If you buy a cable/DSL router or switch, you’ll find that one of the address spaces is used to create a private network for your LAN. Additionally, the range 169.254.0.1–169.254.255.254 is used for Automatic Private IP Addressing (APIPA), which is found in Windows 98/Me/2000/XP, for example.
Most SOHO and small-office routers are designed to use the 192.168.x.x address range only, but some can also use the 172.16.x.x address range. Consider using a different address range than 192.168.x.x if your router permits. Using a different address range could make it a bit more difficult for a casual hacker to get into your network.
You can accomplish several things by using these addresses for computers inside your network:
![]() Your business needs to buy only a small address range from your ISP to use on the firewall or routers that connect your network to the Internet.
Your business needs to buy only a small address range from your ISP to use on the firewall or routers that connect your network to the Internet.
![]() You can now use a huge address space inside your network without having to apply for a large range of addresses from your ISP.
You can now use a huge address space inside your network without having to apply for a large range of addresses from your ISP.
![]() You can use NAT for address vectoring; that is, you can let the router represent your Web service on the Internet using a single address, yet load balance the incoming requests across several servers inside the network.
You can use NAT for address vectoring; that is, you can let the router represent your Web service on the Internet using a single address, yet load balance the incoming requests across several servers inside the network.
Advantages and Disadvantages of a Proxy Server
As with every type of firewall, you can say good and bad things about proxy servers. Their capability to hide the identity of workstations on your network is a definite plus. Packet filters don’t do that. Proxy servers are usually highly customizable, and most come with a graphical interface to make the management chores a little more understandable than those that use a command-line set of cryptic instructions.
One thing packet filters usually excel at when compared to proxy servers is speed. Filtering a packet is not much more complicated than any other task a router does. It already must look at the information contained in the header so that it can make routing decisions. Checking a table of addresses to determine which ones are allowed and which are not isn’t much different from checking the routing table to decide where to forward a packet.
Note
Some advanced firewalls that provide proxy functions can be configured to support authentication and time-of-day controls. If you have a secure environment in which you need to control who gains access and limit the time of access, look for these features in the documentation before you acquire a firewall.
Hybrids
No one type of firewall that has been discussed can meet the needs of every situation. As mentioned earlier in this chapter, it is often a good idea to have several levels of defense against attack from outside your network. It is easy to segment your network so that it does not appear as one entity to the Internet. You can create several subnetworks, isolate them within your network using internal firewalls, and then enclose the collection of subnetworks with firewall protection from outside intruders.
You also can use more than one firewall between your network and the outside world. In the previous dual-homed host example, this was done because the host served as a proxy firewall that was connected to a router that performed packet filtering.
Most of the quality firewall products on the market today are not distinctly packet filters, proxy servers, or stateful inspection machines. Most are hybrids that incorporate the functions of all these firewall technologies, although by different degrees depending on the implementation. As long as you understand the concepts of the functions a firewall performs, you are in a better position to make an informed choice of what will work best for your environment.
Because the firewall has become such an important component of the network, you will find many products that perform other functions related to security that are not easily classified. For example, some firewalls can be used to screen the content of email or other data that passes through the firewall. You can contract with a service provider to obtain a list of known “offensive” or otherwise undesirable sites on a periodic basis and have your firewall block access to these sites. Some firewall products come with built-in virus screening.
Look for the following things when evaluating firewall products:
![]() Security (of course)
Security (of course)
![]() Performance
Performance
![]() Support
Support
![]() Price
Price
![]() Manageability
Manageability
Caution
A firewall protects you only at the point at which your network connects to an outside network. One of the most common mistakes administrators make is assuming that the network is secure and overlooking the modems that sit on many desktops throughout the enterprise. Even if a modem is used only for dial-out purposes, you still run risks of virus infections and other security problems when users dial out to other sites and download programs or data to their workstations, which are connected to the network. Worse yet, modems used for dial-in purposes, such as remote access for users, present an easy entry point for those who would do harm. If you do allow dial-in access, be sure that users understand the implications of downloading from the Internet using the same computer. If not, viruses and other malicious programs can be downloaded from the Internet, and then transfer themselves to your LAN via the dial-up connection. Most of this can be caught using a good firewall and antivirus programs. However, it can take a few days, or longer, after a new virus is discovered before a remedy is found.
The most important aspect of the firewall is the security it affords your network. Question the vendor about the specific methods used in the product, and whether the product has been evaluated by outside sources.
If you use the Internet connection only for the exchange of moderate amounts of email and an occasional Web-browsing session, performance might not be a significant factor in your choice. However, if you expect heavy demand on the Internet connection, from within or without, check to be sure that the product you acquire can handle the load. Packet filter firewalls provide a higher degree of performance; the trade-off is that they do not protect you as well as a proxy server might if it’s configured properly. Because a proxy server is responsible for closer examination of each packet and can be configured to perform other tasks, it is inherently slower than a packet filter.
Support is a critical item to consider. When purchasing an expensive firewall, many vendors include on-site assistance in configuring and setting up the firewall. Additional support, including consulting and hotline help-desk services, is important because the Internet is in a state of rapid growth, and what works today might not be sufficient tomorrow. Unless you have a highly skilled technical staff capable of making decisions about firewall techniques and implementing them, support from the vendor should be a major consideration.
Again, because a firewall is not something you simply configure and forget, the management interface is important. You should look for a product that provides easy access to configuration options so that you can review and modify them as needed. Reporting capabilities should be easy to understand so that you can review data and statistics audited by the firewall. Another important aspect of the management interface is the capability to notify you when something appears to be targeting your network with not-so-good intentions. Alarms that appear onscreen are fine, if you have a round-the-clock operations staff that will be monitoring the screen. The best products will email or page you when specific events occur that you have set a trigger for beforehand.
Finally, in many cases, remote management can be a plus, if it’s implemented correctly. Any remote management capability should include a secure authentication technique. The firewall isn’t much good if you use a clear-text password when logging in to it remotely. You should proceed under the pretense that someone is always watching what you do on the network.
Price should not be the most relevant factor in your decision. You can download some software firewall products from the Internet free. Some firewalls sell for a few hundred dollars, and some range up into the tens of thousands of dollars. The price of the firewall, however, does not indicate its safety or capabilities. In fact, some of the free firewalls you can get from the Internet are actually quite good. One of the things that the Linux platform excels at is implementing firewall technology. Its robust speed and low overhead make it a good choice for this type of chore. However, no matter what product you choose, be sure you have the skills and know-how to properly configure and operate it.
What to Expect from a Firewall
A common mistake is to assume that a firewall will do more than it can because of its name. In the building trade, a firewall that is used to protect individual units in an apartment complex or a condominium is designed according to rules laid down by the local authorities. In the networking trade, no authorities specify what a product must do to carry the “firewall” label.
In fact, several kinds of applications and devices can be classified as firewalls. Do you need a packet filter? Do you need a device that can perform stateful inspection? Before you answer these questions, first decide what you are trying to protect and what methods you are currently using.
What Do You Want to Protect?
For example, if you have highly confidential information, such as patient records or financial information about customers, you should definitely get some good legal advice on your responsibility in keeping this information from the general public. Keeping important information on a dedicated server that cannot be accessed by ordinary users on your network is the first thing to do. However, assuming that an off-the-shelf firewall application will protect you from outside penetration is being a bit simplistic.
Determine your vulnerabilities and examine your current network. Look at how sensitive data is protected now and look at the means used to access it. Then factor in how your current safeguards will enable you to keep the data secure.
Some information usually is available to everyone in the network. For example, an employee home page that contains information about processes and procedures, such as how to request a vacation or get a purchase order approved, usually will not be considered a high-priority security item. Other information, such as information you keep about your customers, not only is important to your bottom line if you want to keep the customer happy, but also might be confidential, such as a doctor’s records about patients. This kind of information should receive your utmost attention when you’re trying to decide how it can be accessed after you connect to the Internet. It might be generally available to a large number of employees, depending on your business, or it might be sequestered by OS protections so that only a single department can use this kind of data.
Of course, if you perform your payroll in-house, you are probably already aware of how sensitive this kind of information is. It must be protected from prying eyes both inside your network and outside your network.
Levels of Security
Because different kinds of information are on networks today that need various levels of security, you should carefully structure your network to handle the way information is accessed.
One connection to the Internet, through a firewall, can protect you. However, with one connection and one firewall, you must make sure that the firewall is the most restrictive you need to protect the most sensitive data that you have. One firewall to protect the entire network is one point of failure. One mistake, and the whole network is vulnerable.
Another drawback is that many users resent extremely restrictive access mechanisms and, if allowed, circumvent them.
One method is to segment the internal network and use firewalls not only to keep intruders outside the company from getting access, but also to keep out those internally who might do mischief. Also, by creating different levels of security, you can act to prevent a single security breach that causes extensive damage. This is especially important if your organization (such as a library) offers unsecured wireless access to the public and also has a closed network.
Instead of using a single network, consider creating several smaller networks and using firewall technology to connect them. For example, in-house data that never needs to be accessed from external sources can reside on one network, whereas another network can host machines that provide WWW, FTP, and other services to your external clients. The firewall that connects this network to the Internet would not have to be as restrictive as the one that joins the two networks at your site.
If you have data that is so confidential that its compromise could do severe harm, you should place it on a computer that does not have a connection to the Internet. Remember, there is no way to guarantee that a computer cannot be hacked via a network, short of pulling the plug.
Tip
Remember, firewalls can operate in both directions. Although the first thing that probably jumps into your head when you think about a firewall is that it will keep out unwanted packets, the reverse also can be true. For example, you might want to connect your network to the Internet to allow email or FTP access to and from customers and your employees. You might not want your employees to access Web pages, however, and you can block their outgoing requests to prevent this type of access.
Inexpensive Firewalls for SOHO Environments
For the small office environment it is just too expensive to hire a full-time person to manage an enterprise firewall. However, you can still protect your LAN to a large degree by using a few simple products. There are both hardware and software firewall solutions. For example, cable/DSL routers use NAT, which helps to hide addresses of computers on the LAN so that hackers on the Internet will find it difficult to obtain that information. That’s just the first step, however. For example, if your ISP gives you a static address that is valid on the Internet, the cable or DSL modem itself can be the subject of an attack, as well as the attached router. Thus, although clients inside your LAN might not be easy to get at directly, it could be very simple to reconfigure the router using the same type of software you used to set it up in the first place!
Tip
Even if you use NAT and an inexpensive firewall, don’t forget that one of the easiest ways to penetrate your LAN is to send a virus or another similar program to you as an email attachment. A good virus-checking program that is kept up-to-date with the latest virus definitions can help prevent this problem. I would recommend that you use a virus-checking program on every computer on your network, because a well-crafted virus can spread easily after it gets onto one machine on the LAN. The price you pay for a virus checker is insignificant when compared to the cost of restoring data, which itself may have been corrupted weeks or months before you discover the virus.
Hardware Solutions
Hardware firewalls are more expensive than software firewalls because the actual hardware itself costs more to produce. Software products can be replicated for a few dollars, including packaging. However, a hardware-based firewall is not beyond the reach of a SOHO environment. You just need to be sure that the firewall you purchase performs well, as described earlier in this chapter, and that the firmware can be upgraded when necessary. The latter may not be possible on an inexpensive hardware firewall, but it is a good feature to look for when making a purchase.
Following is a list of some typical hardware-based firewalls. This is not meant to be an exhaustive list or a recommended list, but instead is presented here to give you an idea of the variety of products available:
![]() Cisco Systems—
Cisco Systems—www.cisco.com. Although Cisco is better known for its enterprise-level network hardware, it offers the SOHO 96 and small-business Cisco 831 routers. These routers feature SPI and support for IPSec VPNs (about $450). Other models incorporate cable or DSL modems.
![]() D-Link—
D-Link—www.dlink.com. This venerable manufacturer of inexpensive routers, switches, and other hardware products offers several routers with SPI firewall and VPN support that vary in price and capabilities, including DI-808HV for SOHO networks, and the DFL 200, DFL-300 and DFL-700 for small-business networks. Prices range from around $100 to $430. You can make a purchase online at D-Link’s website, or from many online web vendors.
![]() Linksys—
Linksys—www.linksys.com. This popular manufacturer of network products makes several routers with SPI and other advanced firewall features. The BEFSX41 ($100; SOHO users with VPN support); RV0041, RV016, RV042, RV082 ($170–$410; SOHO and small-office users with VPN support).
![]() Netgear—
Netgear—www.netgear.com. Its line of ProSafe VPN firewalls include SPI with prices ranging from $65 to $190.
![]() Sonicwall—
Sonicwall—www.sonicwall.com. From SOHO to enterprise networks, this manufacturer has a solution. The TZ 150 and TZ 150 Wireless (802.11b/g) for SOHO and small-business networks feature SPI packet inspection, integrated antivirus and antispyware protection, and hardware acceleration for popular encryption standards for around $400–$500. These products are sold through third-party resellers, and the website lets you choose by state so that you can find a local reseller. You can also call the sales office to find a reseller.
![]() WatchGuard SOHO and Firebox SOHO Security Appliance—
WatchGuard SOHO and Firebox SOHO Security Appliance—www.watchguard.com. This company offers firewalls that range from SOHO appliances to enterprise-scale firewall devices. The WatchGuard Firebox SOHO 6, which comes with a 10–user license, can be had for around $300. This product offers VPN functionality, stateful packet filtering, and optional Web content filtering, among other features. Antivirus software is also included. The Firebox SOHO 6 Wireless has similar features, and includes an IEEE-802.11b-compatible wireless access point (around $430–$500). To purchase either product, read the technical literature at the website and then select a reseller or an online distributor recommended by the company.
Tip
Although I don’t usually recommend where to purchase network devices or software, I will in this case. After you have read the specifications for a firewall appliance you would like to purchase, it doesn’t hurt to search the Internet to find a good price. Most of the discount sites, such as www.buy.com, will enable you to get the product at a discount off the manufacturer’s suggested retail price. Oh, watch out for those shipping charges, though! Another feature that similar websites offer is a rating for each vendor. Don’t necessarily go for the lowest price. Read about other users’ experiences before you choose a reseller. For network hardware reviews, check out www.tomsnetworking.com (the network section of Tom’s Hardware) and www.practicallynetworked.com.
Software Solutions
Many firewall solutions are based on software. One of the problems with this approach is that you must purchase a copy for each computer on the network—though this is not always the case. You can also set up one of your computers to act as a router for other computers, but this process can be complicated if you are not computer savvy. Yet a software solution that also includes an antivirus program may well be worth the cost. Windows XP also comes with a very basic packet filtering firewall, but this simple firewall does not go far in protecting your LAN. Other techniques discussed earlier in this chapter should be part of a software solution.
Some software firewalls to consider are listed here:
![]() ZoneAlarm and ZoneAlarm Pro—
ZoneAlarm and ZoneAlarm Pro—www.zonealarm.com. The basic ZoneAlarm firewall is available at no cost. ZoneAlarm Pro provides enhanced protection, can be run as a free trial, and can also be purchased as part of a security suite with antivirus and antispyware applications.
![]() Norton Internet Security 2006—
Norton Internet Security 2006—www.symantic.com. Includes firewall, intrusion detection, standard application (port) blocking, antivirus, antispam, privacy controls, and parental controls. Norton AntiVirus 2006 and Norton Personal Firewall 2006 are also available as separate products.
![]() McAfee Internet Security Suite—
McAfee Internet Security Suite—www.mcafee.com. Includes firewall, antivirus, spyware and adware detection, privacy controls, parental controls. McAfee Personal Firewall Plus and McAfee VirusScan are also available separately. McAfee Wireless Home Network Security protects wireless ethernet (Wi-Fi) networks against intrusions.
![]() Sygate Personal Firewall Pro—
Sygate Personal Firewall Pro—www.sygate.com. A good solution that offers some features that other similar products do not. Intrusion detection, VPN support, and automatic termination of known Trojan horse programs are part of this firewall, among others.
Using Both Hardware and Software Firewalls
Although the Windows Firewall built into Windows XP starting with Service Pack 2 provides stateful packet inspection, it only protects against inbound threats. Consequently, you should not count on it as the only protection between your computer and the Internet.
To provide a greater deal of security, you might want to use both a hardware and a software solution. Use the hardware firewall appliance as the front end of the network by attaching it to your broadband connection. Note that most SOHO and small office firewall appliances include multiport Ethernet switches, and some also include a Wi-Fi AP. Then use a software firewall package on computer(s) in your network.
Whichever you choose, keep in mind that no firewall can provide a complete solution to protect a network from outsiders. New viruses, Trojan horse programs, and the like are being created every day. All antivirus and firewall devices/software should have an update feature that you can use to download new software and virus definitions on a frequent basis. This type of service typically comes free for the first year, and then you can pay a small fee for following years.
How Do You Know That the Firewall Is Secure?
The problem with security is that the environment, either internal or external, is always changing. As soon as a bug in an OS or network application is found and exploited by mischievous persons, someone comes out with a fix. As soon as the fix is applied, something else crops up. When you set up a firewall to protect yourself from those who might do harm to your network, you must perform tests to be sure that it does what you think it does.
The problem with testing, however, is that you already know what you are looking for when you create and execute the test. It’s what you don’t know that can cause problems. To keep on top of things, you should continue to monitor the data collected by any auditing or logging functions the firewall provides to make sure that it is working as you expect. Look for attempts to breach the firewall and watch for unusual activity. You might find that you can stop an attack before it succeeds. Using other tools, such as Tracert, you might be able to locate the perpetrator and handle the matter using legal means.
Tip
To help determine the security of your system, visit the Gibson Research website at www.grc.com and click the Shields Up! icon. Shields Up! can perform several tests to verify system security. If your system fails any of these tests, Shields Up! provides suggestions for improving system security.
No RFCs define what a firewall must do or how it should do it. You can contact several organizations on the Internet to get information about current firewall and security software. Appendix C, “Internet Resources for Network Administrators,” contains a list of some interesting sites related to network security and firewalls that might help you decide what kind of protection you need.