CHAPTER 10. Routers
SOME OF THE MAIN TOPICS IN THIS CHAPTER ARE
The Difference Between Routable Protocols and Routing Protocols 150
When Do You Need to Use a Router? 151
Router Ports and Connections 157
Routers are perhaps one of the most misunderstood devices found in a network. After you create a LAN using simple devices such as switches—which require little or no configuration—managing a router can be very intimidating. Some of the reasons for this include
![]() Most people do not understand the difference between a connectivity device, such as a switch, and a router. This is compounded by the popularity of devices that include both router and switch functionality in one box. After all, they both can be used to connect computers to a LAN, right?
Most people do not understand the difference between a connectivity device, such as a switch, and a router. This is compounded by the popularity of devices that include both router and switch functionality in one box. After all, they both can be used to connect computers to a LAN, right?
![]() Unless you use sophisticated network console management software, the management and configuration interface for most routers often seems cryptic.
Unless you use sophisticated network console management software, the management and configuration interface for most routers often seems cryptic.
![]() Like computers, routers have an “operating system” that controls how they function. There is no universal operating system that can be learned for use with routers from different vendors.
Like computers, routers have an “operating system” that controls how they function. There is no universal operating system that can be learned for use with routers from different vendors.
![]() Routers come in all sizes and shapes. You can find a small, inexpensive router to connect a small office LAN to a broadband connection (such as DSL or a cable modem). Still larger standalone and rack-mounted units can be used for Enterprise networks. At the high end of this market are powerful machines used as Internet core routers.
Routers come in all sizes and shapes. You can find a small, inexpensive router to connect a small office LAN to a broadband connection (such as DSL or a cable modem). Still larger standalone and rack-mounted units can be used for Enterprise networks. At the high end of this market are powerful machines used as Internet core routers.
In this chapter you will learn about the functions performed by routers—from those at the low end of the scale to the top of the line. In addition, this chapter introduces some of the topics that enable routers to be used as a firewall.
![]() Firewalls are discussed in more detail in Chapter 45, “Firewalls.”
Firewalls are discussed in more detail in Chapter 45, “Firewalls.”
What Routers Do
Bridges and repeaters can be used to add to the number of computers and extend the distance covered by an older Ethernet or Token-Ring LAN. Bridges, intelligent hubs, and most switches operate at level 2 in the OSI network model, making decisions by analyzing the hardwired MAC addresses of the installed network card for each system on the LAN. Remember that the hardware addressing scheme produces a flat address space. If you want to create a switch that communicates easily with all the computers hooked up to the Internet, it would need to store millions upon millions of these unorganized addresses in memory—an impossible task indeed.
Note
Although it is convenient to think of switches, routers, and hubs as separate devices, in reality you often find network devices that perform multiple functions. For example, although routers generally are used to connect different LAN segments or networks, you also will find routers that contain built-in switches, as well as support for bridging and other tasks. In this chapter, the focus is on routing. Don’t be surprised if the equipment you purchase offers other capabilities.
Also, keep in mind that older Ethernet bridges, hubs, and repeaters are now considered to be legacy equipment.
Routers operate one step farther up the OSI model at the third layer, the Network layer. The Network layer offers a logical address space, which makes it easier to organize networks and route traffic between networks. This overcomes the flat address space provided by lower-level devices that use Media Access Control (MAC) addresses. Each router contains two or more network interfaces. One or more of these interfaces can be used to connect the router to a wide area network, whereas other interfaces can be used to connect to local network segments. Routers receive input from one network interface, and then make routing decisions based on which interface can best get the packet to its eventual destination. The port on which the packet is retransmitted can lead to another router or another LAN segment directly connected to the router.
![]() Switches are covered in Chapter 8, “Network Switches,” and in Chapter 9, “Virtual LANs.”
Switches are covered in Chapter 8, “Network Switches,” and in Chapter 9, “Virtual LANs.”
![]() If you’re interested, the OSI network reference model is covered in Appendix A, “Overview of the OSI Seven-Layer Networking Reference Model.”
If you’re interested, the OSI network reference model is covered in Appendix A, “Overview of the OSI Seven-Layer Networking Reference Model.”
Hierarchical Network Organization
The important difference between MAC addresses and logical network addresses (such as TCP/IP and IPX/SPX) is that the logical network addresses allow for the organization of a collection of networks into a hierarchy. This logical distribution of network addresses can be modeled after the logical organization of your business, as in a collection of departmental LANs based on an organizational chart. Or it can represent a geographical model of a business, with individual LANs located in branch offices. Or, as is usually the case, it can be a combination of both of these.
The router is the device that can connect all these different LAN segments so that larger networks can be created that go beyond the limits imposed by LAN topology standards, such as Ethernet and Token-Ring. The Internet is the prime example of a large collection of separate networks, all managed in a decentralized manner, but organized in a logical hierarchical address space. Routers connect these many thousands of networks and make decisions on how best to deliver network information from one client to another on a different network, all based on constantly changing, constantly updating routing information. They do this by storing information about how to deliver packets to different networks on the Internet.
A routing table keeps track of these routes, which can include multiple routing hops on the way to the eventual destination. A router does not always know the entire route that a packet will take to get to its destination. If the destination is on another LAN segment attached to the router, the router might not know the immediate network destination. If this is the case, the router uses a catch-all “default gateway” to send the packet to. On the Internet, a packet usually passes through many routers to reach its destination. In this case, a router simply keeps in its routing table the “next hop” that the packet needs to be sent to in order to reach its destination. Each router on the way to the destination knows the next hop in the path, or uses its default gateway entry in the routing table.
Routers are not limited to using the TCP/IP protocols, though perhaps most of the routers in the world today—on the Internet—are used for IP routing. Most corporate and business-class routers can be configured to route many other protocols, such as IPX/SPX and AppleTalk, in addition to TCP/IP, and do it all at once. However, SOHO routers, such as those used to connect a network to a cable or DSL modem, use only the TCP/IP protocol.
Note
Although most of us tend to think of routers as just another kind of network device, computers—from PCs all the way up to mainframes—also can perform routing functions. All that is needed is for the computer to be equipped with more than one network adapter, connections to more than one network, and routing functionality in the protocol stack. For example, you can set up Windows 2000/2003 or Unix/Linux systems to perform routing for your network.
Both Unix and Linux systems can be outfitted with multiple network adapters and configured to route network traffic. Many network administrators use Linux systems as part of a firewall. A lot of existing software, both free and commercial, can be used on these systems for this purpose.
Providing Security
When you think about how a router functions—it examines the header information of the network protocol portion of a packet so that it can make routing decisions—it also should become obvious that it is at the router that you can create a “chokepoint” for your network. That is, you can use router configuration rules to allow or deny network traffic based on information found in the network packet header. For example, when using a router as a first-defense mechanism in a firewall, you can enable or disable communication over specific TCP or UDP ports, to deny access to network traffic for selected applications. For example, this is how you could prevent someone from using Telnet to log in to a computer on your network—by blocking Telnet communications (port 23) at the router. You can also block certain network addresses from passing data through a router into your network (and vice versa). This is a very powerful capability used as part of a firewall.
A firewall, though, is usually composed of more than just a simple router, and includes things such as stateful-inspection techniques and application proxies. However, routers were the first devices used to create a “firewall” when it became obvious that the ever-expanding Internet no longer was the safe, academic environment it once was.
![]() You can learn more about routers and how they function in a firewall environment in Chapter 45, “Firewalls.” Chapter 24, “Overview of the TCP/IP Protocol Suite,” covers TCP and UDP ports.
You can learn more about routers and how they function in a firewall environment in Chapter 45, “Firewalls.” Chapter 24, “Overview of the TCP/IP Protocol Suite,” covers TCP and UDP ports.
Routers also provide logging facilities. You can use this data when trying to determine whether your network has been infiltrated. Although most serious hackers today are more sophisticated and would spoof IP addresses in a packet, newcomers who simply download the many free hacker utilities off the Internet can be found easily by checking log files on a router. To provide extra safety, some routers allow you to send log file information to the syslog daemon on the Unix/Linux host so that if the router itself is compromised, the log file data will still be available.
The Difference Between Routable Protocols and Routing Protocols
So far we’ve discussed routers and what they do, but we have not discussed the protocols involved. There are basic kinds of protocols that you need to understand when it comes to routers: routable protocols and routing protocols. For a protocol to be routable, it must make some provision for identifying a network as well as the host that’s on a network. If a router had to keep track of every host on the Internet, it would be impossible to build a machine large enough to store all the routing table information. Instead, routable protocols specify network addresses as well as addresses of computers on those networks. Thus, routers only need to store a much smaller routing table that tells them where to forward packets based on the network address. After the packet reaches its destination network, it is delivered to the intended host using the host portion of the address field. TCP/IP (discussed in Chapter 24), for example, sets aside a portion of the IP address to use as a network ID. Other routable protocols include NetWare’s IPX/SPX, DECnet, and AppleTalk. Each of these protocols can be used to create diverse network segments that can be tied together using a router. Many routers also support multiprotocol stacks and can route more than just TCP/IP. Examples of nonroutable protocols include Digital’s (now HP) Local Area Transport (LAT) and NetBIOS (although NetBIOS over TCP/IP, or NBT, can overcome this limitation).
A routing protocol, on the other hand, is a protocol that routers use to communicate routing information among themselves. These protocols involve exchanging information about new routes, or old routes that no longer work, as well as metrics that describe the route (that is, the speed and hop count of the route). Routes are the path that a packet takes on its journey to its final network destination. At the local network, the host portion of the protocol address will be used to determine which computer on the local network the packet is destined for.
Routing protocols exchange information between routers so that routers gradually build up a view of the networks that can be reached. This information is dynamic because systems and routers can always experience downtime. When this happens, routers exchange information and, if a new route exists that can still reach the destination, the router may change its routing entries. When multiple routes to a destination exist, depending on the protocol, certain metrics (such as the number of hops between the source and destination) are used to determine what route a packet should take.
Note
Many kinds of routing protocols are in use today, each of which has its merits and shortcomings. Some are used for small internetworks, whereas others function on the Internet core routers. The most popular of these routing protocols are discussed in further detail in Chapter 33, “Routing Protocols.”
When Do You Need to Use a Router?
Not every network needs a router. If you operate a small-office LAN, a simple switch-based LAN can provide all the file and print sharing your business needs within the LAN. However, if you have remote locations, or if you connect to the Internet (and who doesn’t) then you need a router because of the security features it can provide.
One such feature is called Network Address Translation (NAT). NAT allows you to use one or more IP addresses that are valid on the Internet, while using a reserved address space for the computers on the LAN. Although this might not seem important at first glance, keep in mind that it helps prevent computers outside your LAN from learning the addresses of computers inside your LAN. NAT is not the only technology used in a firewall, but it is a good start. For a small office, home office (SOHO) network, a router that performs NAT is a necessity when using a cable modem or DSL to connect to the Internet. As an added bonus, most SOHO routers that perform NAT also act as a DHCP server, preventing the requirement to configure another system on your network to run the DHCP service. Other features that NAT provides include expanding the address space so that you do not have to pay for additional IP addresses that are valid for use on the Internet. The reserved address space used inside the network is all yours to use.
There are several other situations in which a router might be needed:
![]() The size of your local LAN has grown rapidly and you are having problems with network congestion. You can divide your network into multiple subnets and connect them using a router. With this method, traffic local to a subnet doesn’t have to pass through the router and use up bandwidth on other subnets.
The size of your local LAN has grown rapidly and you are having problems with network congestion. You can divide your network into multiple subnets and connect them using a router. With this method, traffic local to a subnet doesn’t have to pass through the router and use up bandwidth on other subnets.
![]() The size of your local LAN has grown rapidly and you would like to delegate authority for groups of users to individual departments, each on its own separate network segment.
The size of your local LAN has grown rapidly and you would like to delegate authority for groups of users to individual departments, each on its own separate network segment.
![]() You want to connect to branch offices or other wide area networks, such as the Internet.
You want to connect to branch offices or other wide area networks, such as the Internet.
![]() You want to be able to filter the network traffic that passes between one LAN and the next, or between your network and the Internet. This use of a router generally is found as part of a firewall solution.
You want to be able to filter the network traffic that passes between one LAN and the next, or between your network and the Internet. This use of a router generally is found as part of a firewall solution.
![]() For more information about NAT, as well as detailed information on using packet filtering techniques with a router as part of a firewall, see Chapter 45.
For more information about NAT, as well as detailed information on using packet filtering techniques with a router as part of a firewall, see Chapter 45.
Growing LAN Sizes
As a business in today’s market grows, so do the computing requirements. A company starting out with only a few computers, or even a few hundred, can easily get by using a LAN constructed with switches. However, there comes a point when you reach the limits of either the traffic capacity of your LAN or the topological restrictions imposed by the type of LAN you create. When this happens, you can segment the network, using a router, thus preventing congestion or topology problems.
The IP address space provides a hierarchical addressing structure. Basically, there are different classes of IP addresses; for each type a certain number of bits are set aside to record a network address, and the remaining bits are used to specify the host on that network. By using the hierarchical nature of IP addressing, you can configure your IP subnets using routers, in a manner that reflects your business organization.
![]() For more information about the different address classes and other techniques, such as Classless Interdomain Routing (CIDR), see Chapter 24.
For more information about the different address classes and other techniques, such as Classless Interdomain Routing (CIDR), see Chapter 24.
Using TCP/IP, each local network generally makes up both a physical and a logical subnet. The physical subnet consists of all the devices attached to the same broadcast domain, which includes all devices attached to the same hub and all hubs connected to that hub, if you are still using this older technology. Unless you’ve configured Virtual LANs (VLANs), the same goes for most switches, although the broadcast domain concept is limited when using a switch. For all nodes that exist on a particular physical subnet, it is a good idea to assign IP addresses that fall into the same network address or subnetwork address. Again, Chapter 24 explains how the network portion and subnet portion of the IP address work. The thing to remember here is that each separate physical subnet generally uses a separate IP network or subnetwork ID to identify all computers on that LAN segment. A separate host ID is used for each computer on each subnet.
VLANs allow you to configure the subnet that a port belongs to on a port-by-port basis. This is covered in the preceding chapter, “Virtual LANs.”
In this situation, each computer on each segment is a peer to all other computers on the same segment. Communications take place on the local segments at the Ethernet frame level using hardware (MAC) addresses. In Figure 10.1, for example, workstation A and workstation B can send data frames back and forth, and the traffic they generate between them never passes through the router. The local hardware addresses are resolved using ARP (see Chapter 24 for more about ARP), and both nodes can talk directly to each other using Ethernet frames.
Figure 10.1. Routers are used to link different network segments to create a larger internetwork.
If workstation A needs to exchange data with workstation D or E, network traffic travels between the different subnets through routers 1 and 2. To carry the concept a step further, workstation A would have to send a data packet through three routers to exchange data with workstations G through L. As you can see, a router works much like a bridge in that it segregates traffic and passes it on to other segments only when the destination address of the packet isn’t on the local segment. However, bridges work at layer 2 of the OSI model and use hardware MAC addresses. Routers switch traffic based on layer 3 addresses, such as IP.
A router is needed only when a packet needs to travel to a different logical IP subnet or network. Routers come in all sizes and combinations. Some have serial-line ports, Ethernet ports, twisted pair, and fiber-optic ports. If you have reached the limit on your LAN and don’t want to add more workstations, consider installing a new LAN segment and connecting both your old and new LANs using a router.
Tip
Besides making it easy to organize your network layout by matching IP network and subnet addresses to your business organizational chart, you also can organize your Domain Name System (DNS) names to reflect the business organization. Remember that the host and domain names you assign to a particular network device or computer can, but do not have to, relate directly to the underlying IP address. Instead, these are assigned by the network administrator (or by using DHCP with certain scopes of addresses reserved for selected subnets). Thus, it is possible to use both IP addressing and DNS names to add some organization to the madness that typically makes up a large network. For more about using DNS and how fully qualified domain names are translated to IP and other network addresses, see Chapter 29, “Network Name Resolution.”
Using this method, each subnet has its own unique subnet portion of the IP address space. The router is like all other devices on a traditional Ethernet network—it can see all traffic on the segments attached to it. In modern networks in which switches are used, each computer is configured to use a router (the default gateway) when it needs to send a packet to a network that is not on the same subnet. The router, however, has connections to more than one network segment and can transfer packets of information from one segment to another, based on their network address.
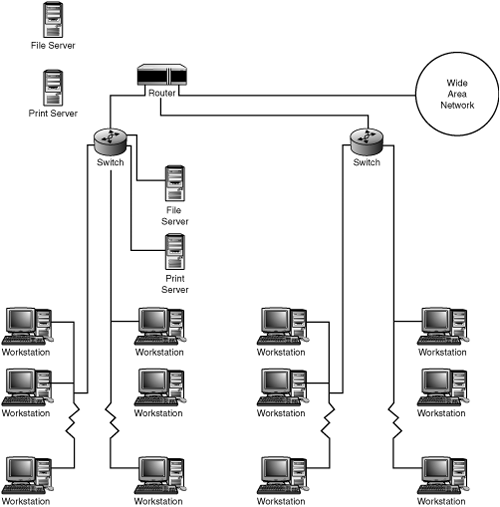
Figure 10.1 showed only a simplistic view of how routers can connect different network segments. In practice, you’ll most likely have switches or hubs separating your client computers and servers from the hub. Figure 10.2 shows this view. The router is used to connect several LAN segments, each of which may have a switch (with attached workstations) or a powerful server. Additionally, a WAN port on the router is used to connect to the wide area network, such as the Internet.
Figure 10.2. In a typical large network, switches or hubs separate individual workstations from the wide-area router connection.
As mentioned before, when you configure a client computer to use TCP/IP, you generally specify a default gateway (or this value can be supplied by DHCP when the client boots). The default gateway is the address of the router that attaches the local subnet to the larger network structure. Thus, when a client computer wants to send a packet, or series of packets, to a computer that is on a different logical IP subnet, it sends the packets instead to the default gateway—the router. The client computer can tell from its own address what subnet it is connected to. The client software knows to direct a packet to the default gateway when the network or subnet address of the packet differs from the sender’s own network address.
A router makes decisions on where next to send the packet based on routing tables. Routing tables can be configured manually (static routing) by the network administrator, or they can be configured dynamically using various routing protocols. Simple routing protocols are useful for small internetworks, and complicated routing protocols are used by Internet core and border routers. However, the principle of routing is basically the same for all these protocols. Routers make decisions based on the Network Access layer of the OSI model using logical IP addresses. Your local area network uses the ARP protocol to determine the actual hardware address (a flat address space) for communications within the local LAN segment.
When a client computer sends a packet to the default gateway router, it uses the source address in the frame header for the address of the router, even though that is not the eventual destination of the frame. The router is just the next hop for the frame. When the router notices a frame on a port that is addressed to it, it unpacks the frame to expose the IP header portion. Using the IP address, the router then decides on the next hop for the packet and reconstructs a frame to transmit the packet to the next hop. This might be another router or a host on another segment attached to the router. As you can see, routers actually change the packet (or frame) as it travels through an internetwork. For example, the Ethernet frame destination address is changed to indicate the next hop for the frame. Inside the IP header, the router changes the TTL (Time to Live) value. When this value reaches zero, the packet has traveled the maximum hops allowed and a router discards it. Because a router must change fields in the IP header, as well as the Ethernet frame header information, it also must recalculate any error-checking fields for these headers.
At each hop, a router also can be configured with a set of rules that filters out the packet. This capability provides for some security for your network, because you can prevent certain IP addresses or services from passing between your network and the Internet.
One very important concept to grasp is that routers only get a packet delivered to the router port that connects to the network that contains the destination of the packet. After the router determines that the packet should be output through a certain port, the MAC addresses of the networked computers and other devices come into play. That is, the IP address gets the data to the destination network. After the data has arrived, it is the MAC address that is used for the final leg of the journey.
On the local subnet the router sends out an ARP frame that contains the IP address of the packet. When a computer recognizes its IP address, it sends a frame back to the router telling the router what its MAC address is. From then on, the router can use the computer’s MAC address to send additional packets. Routers keep a cache in memory of MAC addresses for a short period so that a continuous stream of data can be delivered after the router knows the MAC address of a computer on the local network.
Delegating Responsibility for Local Area Networks
Because routers can be used to separate one group of users from another, it makes delegation of administration at the local level much easier. Responsibility implies security. Routers can be programmed using a technique called Access Control Lists (ACLs), which are nothing more than rules that specify the following:
![]() What direction packets can travel—inbound to the LAN or outbound to another LAN
What direction packets can travel—inbound to the LAN or outbound to another LAN
![]() Which IP addresses, both network and host addresses, can pass through the router (normally addresses can also be specified as wildcards)
Which IP addresses, both network and host addresses, can pass through the router (normally addresses can also be specified as wildcards)
![]() Which TCP or UDP ports can be allowed to pass through the router
Which TCP or UDP ports can be allowed to pass through the router
This packet filtering capability lets a local administrator, who understands the router control, restrict access to the local LAN. For security reasons, this can be very important. Most people think of a firewall as a device that sits at the edge of a network and makes the connection to the Internet. That is only one use of a firewall.
A second use is to isolate departments within a particular network. For example, it’s probably a good idea to isolate the accounting department from other sections of your company. You don’t want employees probing around trying to break into your payroll records! With a router, you can configure rules that allow only selected users on other LANs (such as the one that services the executive suite) to pass through your router, while keeping others out.
By using controls within your network as well as at the edge, you also can help prevent the spread of any attack or infiltration that does occur.
Another important feature that many routers provide is logging. You usually can log both successes and failures to keep track of how your network is being used. If you find a particular workstation trying to Telnet or FTP to a prohibited LAN, you can use this evidence to discipline the employee. Many routers allow you to designate another system as the location for logging files. Typically, this is done using the Unix syslog daemon. This type of feature improves on security. If the router itself is compromised, you will have a record of the events leading up to it. If you regularly review your log files, you can take preventive measures if you suspect that suspicious activity is occurring.
Connecting Branch Offices
Many companies have offices in multiple locations. In the early days of computing, when 300 baud modems were the norm, sending data between two sites usually consisted of dial-up access. Today, you can lease lines between central headquarters and multiple branch offices. Additionally, other long-haul services, such as those provided by Frame Relay and Asynchronous Transfer Mode (ATM), can be used to enable you to connect securely to remote branch offices.
![]() For more information about using Frame Relay or ATM, as well as other high-speed network connections, see Chapter 15, “Dedicated Connections.”
For more information about using Frame Relay or ATM, as well as other high-speed network connections, see Chapter 15, “Dedicated Connections.”
Routers come in all sizes and offer various features. You can use a router to connect branch offices easily. All you need to do is to provide a separate network ID—or more likely subnet ID—for each location and choose an appropriately sized router for each location. Some routers even allow you to use a dial-up line for a remote connection that is used only infrequently. This situation is ideal when all you need to do is poll remote computers after-hours to get sales totals and other information of that sort. Still other routers, usually at the low end of the line, allow you to connect to a cable modem or a digital subscriber line (DSL) modem and share that single IP address connection with several other computers. This kind of router/switch combination is ideal for a home office or a branch office that has only a few computers that need to be networked.
Using a Router to Protect Your Network—NAT and Packet Filtering
Chapter 45 demonstrates how routers fit into a well-designed firewall solution. However, this topic is important enough to deserve a brief mention here. When the Internet was first being commercialized, there were lots of IP addresses to go around. It was easy back then to get an ISP to assign you a group of IP addresses that were valid on the Internet. As the Internet has expanded year by year at a phenomenal rate, the IP address space has begun to run out.
Most routers provide a function called Network Address Translation (NAT). Briefly, NAT allows your network to use one, or a few, valid IP addresses on the Internet connection side of the router, and a private address space on your local network side of the router. When communications take place between a client on your network and a server on the Internet, the traffic passes through the router, which uses its own valid IP address to make contact with the outside server. Responses received from the server are repackaged and returned to the original client. Besides using IP address substitution, another version of NAT employs a technique of manipulating port addresses to keep track of multiple connections.
NAT helps keep your network secure because it helps prevent anyone outside your network from finding out any addressing information about servers or workstations inside your network. One of the most important security goals you can accomplish in network security is preventing outsiders from gaining any knowledge about your network, be it network addresses, hardware platforms, or operating systems and applications. The capability for a router to also block certain ports, as well as addresses, makes your local network even more secure. For example, although you might want to allow your users to browse the Web and possibly establish an FTP session with a remote server to download a new driver or software update, you might not want the reverse to be possible. By appropriately configuring your gateway router, you can pretty much block all but the most persistent hacker from getting into your network.
Router Ports and Connections
In a central headquarters, where network segments converge, a larger router with a greater capacity to handle large volumes of network traffic is used. A typical router found in many corporate environments, for example, is the Cisco 2505 series. This router comes in several models—to accommodate different network interfaces—and can provide for both Ethernet and Token-Ring support. The Cisco 2505 appears in Figure 10.3, from the rear, so that you can see the physical connections.
Figure 10.3. A router usually contains multiple interface connections to join different network segments.
In this figure, you can see that the 2505 model provides for eight UTP Ethernet connections on the left side that can be used to connect either individual computers or switches (using crossover cables that swap the transmit and receive wires).
Tip
When configuring a router, you need to supply information about each port, or network interface, that is used. Typically, each port is named to indicate its use. For example, the Cisco IOS (Internetworking Operating System) software uses E0 to represent the first Ethernet port, E1 for the second, and so on. Serial ports are denoted using an “S” (S0, S1, and so on).
Other local area network interfaces you will find on other models in this series of routers include Token-Ring connectors (usually a DB-9 connector) and Attachment Unit Interface (AUI, usually a DB-15 connector) used to connect an Ethernet transceiver to the router.
Near the middle of Figure 10.3 are two 60-pin serial connections (DB-60 connectors) that can be used to connect to wide area networks. These connections usually are made to either a modem or a CSU/DSU that interfaces with the high-speed link. Like LAN ports, different models allow for other kinds of WAN connections. For example, the 2500 series includes support for Basic Rate ISDN to connect your office to a WAN.
In Figure 10.4, you can see a close-up of the serial ports, along with two RJ-45 ports.
Figure 10.4. Serial connections allow you to connect a router to wide area connections while the console port allows you to configure and manage the router.
Next to the WAN serial connections are two RJ-45 ports labeled CONSOLE and AUX. The console port is used to connect a terminal to the router for configuration and management purposes. The terminal you use can be either a dumb terminal (such as a VT-series terminal) or a terminal emulation program running on a PC. Either way, you’ll probably also have to obtain an adapter to convert the RJ-45 connector to the type of serial port used on your terminal or PC serial port. Standard serial port converters might or might not be included with the router, so be sure to check the accessories list.
The AUX port can be used to connect a modem to the router. This can be handy for dial-on-demand routing, for infrequent connections to remote sites that don’t need a full-time dedicated connection.
Caution
Although you can connect a modem to the console port, this is not always a good idea. Some routers, such as the Cisco 2500 series we’re discussing here, don’t support RS232 modem controls. This means that when a user using this port logs out, the modem connection is not automatically dropped. If another call comes in shortly afterward, it’s possible to access the router without knowing the administrative password, because the session is still in effect.
If you want to use a modem to control the router, make sure the router supports RS232 modem controls.
The Cisco 2505 router is designed to handle a variety of connections and network types. However, if your network is strictly TCP/IP and uses UTP Ethernet cable, you won’t need the DB-60, AUI, or other types of connections supported by the 2505. Other types of Cisco routers use RJ-45 ports or USB ports to connect to newer types of networks.
Configuring Routers
Most routers are similar to computers in that they run an “operating system.” You can think of the router as a small computer that has only one basic function: Sort out where incoming packets need to go. To preserve your investment, most manufacturers store the router’s operating system in nonvolatile memory that can be reprogrammed when updates or fixes are released. When the router is first powered up, it runs a small bootstrap program that is used to locate and load the operating system. Most routers also allow you to load the router OS using a trivial FTP (tftp) server. This type of FTP server doesn’t require a password and shouldn’t be used in an insecure environment. However, within a LAN, using a tftp server to download router OS data can make it easier to keep track of different versions of the OS and the routers that are configured to use them.
Cisco’s OS for its main router line is called IOS, and it has been updated many, many times over the years and adapted to the newest equipment. Cisco’s website can tell you which versions are available for the different routers it manufactures. If you deal heavily in Cisco equipment, a good website for you to bookmark is the Cisco documentation website. Although Cisco routers do ship with a CD that contains most of this documentation, you’ll find up-to-date copies at these websites:
www.cisco.com/en/US/support/index.html
www.cisco.com/univercd/home/home.htm
Configuring a router usually begins after you take it out of the box and plug in everything. For each interface (that is, network connection), you need to configure the appropriate information. For example, for a 10BASE-T or Fast Ethernet port connecting to a LAN that uses TCP/IP, you must specify an IP address and subnet mask for the port.
There are also tasks you need to perform to configure the routing protocols that the router uses. The information you need for this depends, of course, on the routing protocols you plan to use.
Other configuration issues you need to address include access and security. If the router is being used as part of a firewall, or if there is a need within your network, you might have to set up access control lists to permit or deny network traffic from passing through any of the network interfaces.
One important thing to keep in mind is that the router’s OS and the configuration information you enter are separate entities. Both the OS and the configuration file can be stored in nonvolatile memory (NVRAM), and both usually can be downloaded from a tftp server. However, the configuration file that is created when you initially set up a router should be saved in more than one place for backup purposes. Indeed, keeping a printed copy of the information contained in the configuration file can be a helpful troubleshooting tool.
Router Chassis Types
Cisco manufactures a wide range of router products that spans the small home office to Internet core routers. After you get beyond a small basic router that would be useful in a small home office, routers tend to become more configurable—from a hardware perspective. That is, they are modular, and different models can be adapted to different environments by installing interface cards to match your needs. Additionally, all but the smallest routers come in rack-mounted versions so that you don’t have to dedicate a large amount of valuable office space to them. No matter what size your LAN or network is, it’s a bet that Cisco has a router solution for you.
At the high end of the market are routers capable of serving as Internet core routers. These are the high-bandwidth routers that your local ISP or other large-scale provider uses to connect to the Internet backbone. Such routers allow for line cards that allow them to connect to high-speed fiber-optic links, as well as cards that allow for connections to more typical 100BASE-T networks.
In addition to Cisco, other router vendors also offer a full range of products. At the high end of the market, however, the competition isn’t so great. One vendor, Juniper Networks, markets only high-end routers. This company makes routers that are intended for very large networks and network backbone uses. For example, Juniper’s M10i routers can route and forward network packets at 12.8Gbps (gigabits per second!) in full-duplex mode. Juniper’s routers can be configured with various physical interface cards (PICs), each of which contains different network interfaces, ranging from simple 10BASE-T Ethernet connections up to OC-192c/STM-64 optical fiber link connections. The high-end M320 router (shown in Figure 10.5) is intended to serve as either an Internet core router or a very flexible, configurable high-end router for a large network backbone.
Figure 10.5. The Juniper M320 is a high-end Internet backbone router. Photo courtesy of Juniper Networks.
In Figure 10.6, you can see one of the PIC modules you can use with M-series routers. This figure shows a simple Gigabit Ethernet module.
Figure 10.6. This PIC module enables M-series routers to connect to a Gigabit Ethernet link. Photo courtesy of Juniper Networks.
By carefully choosing the modules you add to a high-end router, it is possible to aggregate smaller links, such as those provided by ISDN or T-carrier lines, into high-speed connections to the Internet. The fact that you can always change out modules to accommodate a changing network infrastructure helps justify the cost of these high-end routers.
Juniper, Cisco, and other manufacturers produce various types of highly configurable high-end routers. However, most users of this book will be dealing with low-end to medium-sized networks, and will find that they don’t have to spend a lot of time configuring or managing a router if you set it up correctly in the first place. If you work with an ISP and use a high-end router, plan to spend a lot of time with the manuals.
For small offices, a multitude of vendors make router/switch combinations that can be used to connect using dial-up or broadband (cable/DSL) to the Internet and other remote networks.
![]() Cable modems are discussed in Chapter 17, “Using a Cable Modem,” and DSL devices are covered in Chapter 16, “Digital Subscriber Lines (DSL) Technology.”
Cable modems are discussed in Chapter 17, “Using a Cable Modem,” and DSL devices are covered in Chapter 16, “Digital Subscriber Lines (DSL) Technology.”
Using Routers over Wide Area Networks (WANs)
You can create a wide area network (WAN) by purchasing your own set of leased lines—an expensive proposition for many smaller companies—or you can connect your network to the Internet and take your chances there. Using a good router that provides for packet filtering and Virtual Private Networks (VPNs), you can effectively tunnel your network traffic through the Internet in encrypted form. Connecting each branch office, you might find that using DSL technologies is much cheaper than using a more expensive ISDN dial-up or T1 dedicated line. Instead, because you’ll have a larger amount of traffic bound to and from the company’s headquarters, you can install a large pipe at that point and use cheaper methods out in the field, spending the money for a large data pipe only where it is needed: at the central headquarters.
If you choose to connect a business network to the Internet, you must be familiar with firewall technology. This means you must be familiar with the specific model of router used in your organization. Cisco is perhaps the most widely known brand of routers, but for small offices there exist many viable and inexpensive choices. Besides packet filtering and NAT that are generally supported by most routers, you also should investigate using proxy servers to further isolate your network from the rest of the world.
![]() Proxy servers are covered in more detail in Chapter 45.
Proxy servers are covered in more detail in Chapter 45.
Routers and the Internet
It should be obvious that without routers it would be almost impossible to consider the connection of millions of computers such as has been accomplished with the proliferation of the Internet. In the first place, the topological restrictions placed on Ethernet, Token-Ring, and other transport protocols would limit the size to which the network could grow. Second, if routing were not done using a logical addressing scheme, any device that connects a network to another network would have to keep a table in memory that consists of all nodes on all networks to which it is connected! Although computing power has been increasing at extremely fast rates in the past few years, it’s doubtful that anyone could devise a machine that could keep track of all the computers in the world and efficiently route a large number of packets to their correct destinations. The routing table would be so large that it would take forever to route packets.
Instead, all a router must do is know the address of a network, or the address of another router that knows how to deliver packets to the destination network. If you use the tracert command in Windows (or traceroute in Unix and Linux) to trace the route a packet takes to a particular website, you’ll most likely see that it goes through many routers before it reaches its destination. For example:
G:>tracert www.bd-studios.com
Tracing route to www.bd-studios.com [207.213.224.83]
over a maximum of 30 hops:
1 140 ms 150 ms 150 ms envlnjewsap01.bellatlantic.net
![]() [192.168.125.173]
[192.168.125.173]
2 * 140 ms * 192.168.125.158
3 140 ms 150 ms 151 ms 206.125.199.71
4 140 ms 150 ms 150 ms 205.171.37.13
5 140 ms 151 ms 150 ms jfk-core-01.inet.qwest.net [205.171.30.85]
6 150 ms * 150 ms wdc-core-02.inet.qwest.net [205.171.5.235]
7 150 ms 160 ms 160 ms wdc-core-03.inet.qwest.net [205.171.24.6]
8 180 ms 180 ms 180 ms hou-core-01.inet.qwest.net [205.171.5.187]
9 180 ms 190 ms 191 ms dal-core-02.inet.qwest.net [205.171.5.172]
10 180 ms 191 ms 190 ms dal-brdr-02.inet.qwest.net [205.171.25.50]
11 180 ms 190 ms 190 ms 39.ATM1-0.BR1.DFW9.ALTER.NET [137.39.23.217]
12 180 ms 191 ms 190 ms 140.at-6-0-0.XR1.DFW9.ALTER.NET [152.63.98.126]
13 181 ms * 180 ms 185.at-1-0-0.TR1.DFW9.ALTER.NET [152.63.98.26]
14 220 ms 231 ms 230 ms 128.at-5-1-0.TR1.LAX9.ALTER.NET [152.63.3.162]
15 221 ms 230 ms 220 ms 297.ATM7-0.XR1.LAX4.ALTER.NET [152.63.112.181]
16 220 ms 230 ms 231 ms 193.ATM6-0.GW4.LAX4.ALTER.NET [152.63.113.89]
17 * 220 ms 230 ms savvis-lax2.customer.alter.net![]() [157.130.236.150]
[157.130.236.150]
18 390 ms 381 ms * affinity-2.uslsan.savvis.net [209.144.96.86]
19 431 ms 460 ms 501 ms web33.ahnet.net [207.213.224.83]
Trace complete.
Clearly, connecting to another computer on the Internet isn’t always such a simple thing! High-speed lines and fast, efficient core routers can make it seem (if you are using a fast, digital connection) as if all the servers you access are just around the corner from you. Instead, they could be on the opposite side of the world. Another interesting thing to note about routers is that packets that are part of the same original communication can take different routes to get to the eventual destination. Routing tables change constantly, and what might be a good route at one moment might not be the next. For this reason, higher-level protocols, such as TCP, take care of the mechanics involved in determining whether packets are received and reassembled into the correct order.