The micro segmentation solution contains various components that must be integrated to make them work well together. These components range from networking devices and infrastructure services, to storage area network devices and applications. Each of these components has a large number of potentially valid configurations, but only a few of these configurations result in an integrated, functional system that meets the specified business and technical requirements of a solution.
The key components in the conceptual design are described in the following sections:
- Internal project networks: These networks represent the main project's workloads; these workloads can be virtual cloud-based, or legacy physical and virtual-based. The customer’s network security model allows systems of any type to reside in alternative networks classified in multiple zones: Intranet (ISZ), and Secured (Newyork). Standard rules of this network security model allow for VMs in Newyork zones to communicate among them, but only if members of the same project, and for VMs in the ISZ zone, communicate among different projects. NSX DFW will grant that this rule be enforced.
- External non-trusted networks: These networks are external to the customer managed network zones. Connectivity to and from external networks is through standard firewalls. The networks falling in this category include the internet and other networks used to interconnect the cloud to third-party provided services.
- Internal non-projects networks: This category is currently represented by a single management network that is accessed by a dedicated network interface, and it is mainly used and targeted at the backup process.
- Perimeter firewalls: This category includes the physical firewalls, which exist at the perimeter of the data centers. Traffic internal to projects, whatever the network zone they are into, won't be enforced by perimeter firewalls. Only traffic with external, non-trusted network-based services will.
The micro segmentation logical view is as follows:
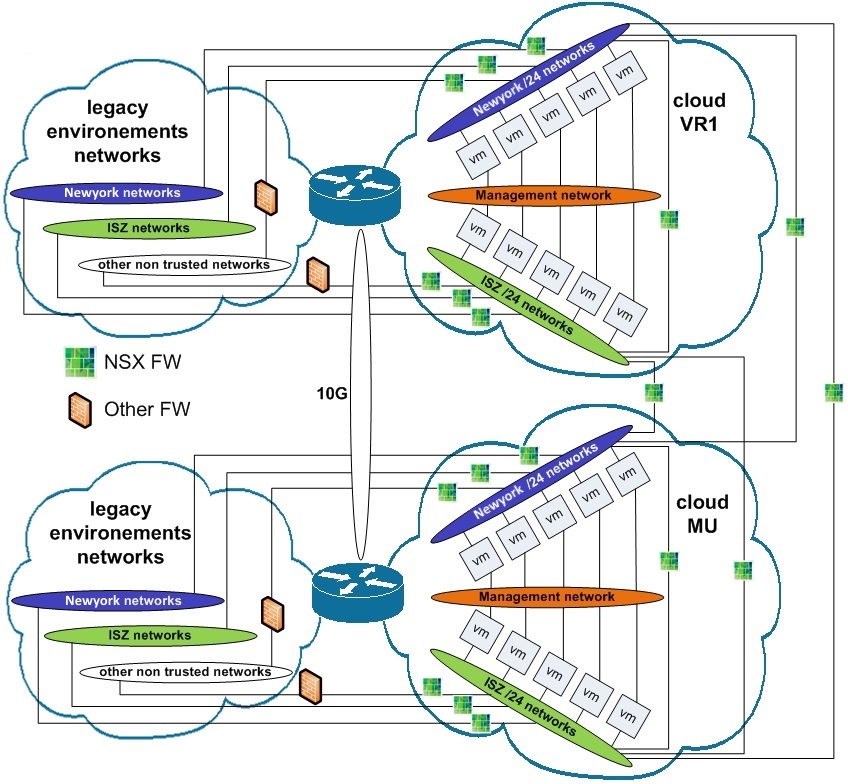
vSphere infrastructure in each site hosts 2 vCenter servers: one instance dedicated to the cloud management plane components, and one vCenter for the workload resources, with dedicated clusters for production, Q&A, and test environments.
The three types of clusters are as follows:
- Payload cluster(s): Which will host all of the VMs provisioned for customers
- Edge cluster: Which will host all edge service gateways and NSX Controller appliances
- Management cluster: Which has all management VMs, such as the NSX Manager instances, the vCenter Server, and any other management VMs that are needed
