Day 22. Ports and Protocols
CompTIA A+ 220-901 Exam Topics
![]() Objective 2.4: Explain common TCP and UDP ports, protocols, and their purpose.
Objective 2.4: Explain common TCP and UDP ports, protocols, and their purpose.
Key Topics
Today we will cover common TCP and UDP ports used for connecting a source to a destination. We will be looking at only a few of the most commonly used ports and protocols. We also will examine networking protocols and their purpose. Finally, we will compare TCP and UDP.
Common Ports
A port number is a logical address used by applications or processes that are network based. They are associated with TCP/IP network connections. A total of 65,535 ports are in use today. They are assigned by the Internet Assigned Numbers Authority (IANA) and are used by applications to determine the type of traffic being sent. The application then uses the port to listen for connections sending that specific application’s traffic.
The following are the most commonly used ports and the ones most likely to be seen on the CompTIA exams.
Ports 20/21—FTP
File Transfer Protocol (FTP) is used to transfer files between two devices over a network. Authentication is made up of both username and passwords sent in clear text. TCP port 20 is used to send, and TCP port 21 is used to receive.
Port 22—SSH
Secure Shell (SSH) is a Unix-based TCP protocol port used to securely access a remote server. It is a secure replacement for older protocols such as Telnet, rlogin, rsh, and rcp. Commands are encrypted, and authentication occurs using a digital certificate.
Port 23—TELNET
Telnet is a TCP port text-based terminal emulation program used to connect to a remote computer. Telnet is short for telecommunication network. Historically, it was used to maintain, update, and configure routers, firewalls, and other remote Internet devices. Telnet client programs use an IP address to connect to the Telnet services running on the remotely located machine. It is not a secure protocol and this port should be blocked.
Port 25—SMTP
Simple Mail Transfer Protocol (SMTP) port 25 is a TCP port used for the transmission of e-mail reliably and efficiently. Most e-mail programs use SMTP for sending e-mail over the Internet, although it can be used for receiving as well. The receiving end is limited and cannot queue messages, so SMTP usually is utilized along with Post Office Protocol 3 (POP3) and Internet Message Access Protocol (IMAP) for message retrievals.
Port 53—DNS
Domain Name System (DNS) port 53 uses both TCP and UDP to resolve UNC hostnames into IP addresses that are used to locate websites. It is a hierarchical distributed naming system for computers to use when connected to the Internet.
Port 67/68—DHCP
Dynamic Host Configuration Protocol (DHCP) uses UDP on ports 67 and 68 for transport. It is a client/server protocol that automatically assigns an IP address and subnet mask, as well as DNS and gateway addressing information to clients requesting them. Addresses obtained using DHCP are called dynamic as opposed to a manually configured computer, which is called static. It previously was known as the bootstrap protocol.
Port 80—HTTP
Hypertext Transfer Protocol (HTTP) port 80 uses TCP to transmit. It is a stateless, application-level protocol used by the World Wide Web. It is stateless because each command is executed without knowing any command sent before it. It defines how messages are formatted and transmitted, as well as error codes.
Two of the most common HTTP error codes are 404 - File Not Found and 502 - Service Temporarily Overloaded, which indicates that the server is busy or there is too much traffic. A 503 error - Service Unavailable Connection Refused by Host is another error that can be seen when access requires permission or a password is incorrect.
Port 110—POP3
POP3 uses TCP port 110 to download e-mail from a server and then delete it. This means the e-mail is no longer available from the server, although some systems are designed to keep a copy for a period of time.
The following characteristics are common:
![]() Only one computer can be used to retrieve e-mail.
Only one computer can be used to retrieve e-mail.
![]() E-mails are stored on the local computer.
E-mails are stored on the local computer.
Port 143—IMAP
IMAP uses TCP port 143 to store e-mails on a remote server. It is usually a better option than POP3 because e-mails can be accessed from multiple devices and locations. The latest version is 4.
![]() Any computer can be used to view e-mail.
Any computer can be used to view e-mail.
![]() E-mails are stored on the server.
E-mails are stored on the server.
![]() Server space can be limited by the provider.
Server space can be limited by the provider.
Port 443—HTTPS
Hypertext Transfer Protocol Secure (HTTPS) uses TCP port 443 to provide a Secure Sockets Layer (SSL) Certificate to encrypt the transfer of data on a webpage. HTTPS is actually a combination of the SSL protocol and Transport Layer Security (TLS) protocol. Websites using HTTPS will show https:// as a part of the URL instead of http://.
Port 3389—RDP
Remote Desktop Protocol (RDP) port 3389 uses TCP to view and control another computer running Windows on a network. It is a Microsoft protocol that provides encryption, print redirection, remote control, network load balancing, and access to the clipboard. The remote computer must be turned on and must have a network connection, and the Remote Desktop application must be running.
Ports 137–139—NetBIOS/NetBT
Ports 137–139 use TCP for communications. They are client server NetBIOS protocols that provide methods for network file and print sharing. They can run over multiple protocols including TCP/IP, NetBIOS, and NetBEUI.
Ports 137–139 were used by Microsoft to enable the transport of NetBEUI over TCP/IP networks. The combination is known as NetBT—though, technically, ports 137–139 were known as NBT over IP. They are not secure and can give out information such as server name, domain, workgroup name, and account information.
Port 445—SMB/CIFS
SMB stands for server message blocks and is also known as Samba. Port 445 was created for Windows 2000 to provide a direct path to TCP/IP without the need for the NetBIOS layer. The SMB protocol goes directly to this TCP port. If it is not available, the traffic can revert to Ports 137–139, which are not secure. Port 445 is also a protocol that is not considered as secure.
Port 548—AFP
Apple Filing Protocol (AFP) port 548 is a proprietary file services protocol, offering file sharing services for the Mac OS X. Apple migrated from AFP to SMB2 in OS X 10.9. It uses both UDP and TCP.
Port 427—SLP
The service location protocol (SLP) is a service discovery protocol used to find services in networks. It also is used to announce services on a local network. It has three different roles for devices, user agents (UAs) that search for services, service agents (SAs) that announce services, and directory agents (DAs) that cache services information. It is a packet-oriented protocol using both UDP and TCP.
![]() Activity 22-1: Match the Port Number to Its Purpose
Activity 22-1: Match the Port Number to Its Purpose
Refer to the Digital Study Guide to complete this activity.
Common Protocols
Protocols are a set of agreed-upon rules that are followed in order to provide communication between devices. These rules cover communication timing, packet sizes, length of transmission periods, and other specifications that allow multiple technologies to coexist and provide networking communication for a specific purpose and environment.
DHCP
DHCP is used to automatically assign TCP/IP addressing information to computers that request it. It sends not only the IP address, but also the subnet mask, the gateway address, and any DNS information it has. An address range is set on a server running the DHCP service and then handed out to clients as needed. The server can set the duration of the IP address kept by the client from a few hours to an unlimited time period.
The client goes through a six-stage process with the server as follows:
![]() Initializing
Initializing
![]() Selecting
Selecting
![]() Requesting
Requesting
![]() Binding
Binding
![]() Renewing
Renewing
![]() Rebinding
Rebinding
The process is started by the client sending out a DHCPDISCOVER message on UDP port 67 using broadcasting. Note that if the server is on a different subnet, a router must be configured to use DHCP-relay to forward the request.
The server responds to the DHCPDISCOVER request with a DHCPOFFER message that contains IP configuration for the client. The offer is sent on Port 68 using the client’s MAC address.
When the client receives the offer, it sends a DHCPREQUEST informing the server it has accepted the offer.
The DHCP server then sends a DHCPACK message acknowledging that it has accepted the DHCPREQUEST. The message contains all the configuration information requested. The client then binds the IP configuration and is now able to communicate on the network.
Renewing and rebinding are used if the server request is not answered or if the request is declined. In this case, a new DHCPREQUEST is initiated.
DNS
DNS works with root servers (also known as DNS resolvers) to answer basic queries on where a specific site is located. The hostname uniquely identifies the computer. A fully qualified domain name (FQDN) is the complete name for a specific computer or host on the Internet. It includes the name of the host and the domain on which the host resides. An example is 31days.pearson.com.
Resolving a Hostname
DNS clients use resolvers to request the IP address from a hostname. The resolver creates a query and tries to match a hostname to an IP address. This process is also called a forward lookup. Servers check their cache to determine whether they have previously resolved this request. If not, they send the request up to the root server for the domain. If the resolver does not know the answer, it can check a local text file called Hosts that resides on the computer.
Resource Record Types
A DNS zone file is constructed using resource records stored in zone files. A DNS resource record describes the type of characteristics of a zone or domain:
![]() SOA—Authoritative server for zone
SOA—Authoritative server for zone
![]() NS—Address of domain’s name server
NS—Address of domain’s name server
![]() A—Hostname to an IPv4 address
A—Hostname to an IPv4 address
![]() MX—Mail exchange server for the domain
MX—Mail exchange server for the domain
![]() AAAA—Hostname to an IPv6 address
AAAA—Hostname to an IPv6 address
![]() SRV—Defines the server for specific purpose such as HTTP, FTP, and so on
SRV—Defines the server for specific purpose such as HTTP, FTP, and so on
![]() PTR—Maps the address to the hostname for reverse lookup
PTR—Maps the address to the hostname for reverse lookup
![]() CNAME—Creates an alias name for the host
CNAME—Creates an alias name for the host
Top-level Domains
DNS root servers manage the top seven common domain suffixes:
![]() Com—Commercial businesses
Com—Commercial businesses
![]() Edu—Educational organizations
Edu—Educational organizations
![]() Gov—Government organizations
Gov—Government organizations
![]() Mil—Military organizations
Mil—Military organizations
![]() Net—Networking organizations such as ISPs
Net—Networking organizations such as ISPs
![]() Org—Noncommercial organizations
Org—Noncommercial organizations
![]() Int—International organizations such as NATO
Int—International organizations such as NATO
LDAP
The Lightweight Directory Access Protocol (LDAP) is an open, vendor-neutral directory services protocol used to access and maintain distributed directories of information (such as Microsoft’s Active Directory). It commonly is used to retrieve usernames and passwords, but it has other uses as well. Some of them are: looking for encryption certificates, printer browsing, and retrieving address books and e-mail addresses. It runs above the TCP/IP stack.
SNMP
Simple Network Management Protocol (SNMP) is used for collecting, monitoring, and managing information about devices on an IP network. Most high-end networking devices come with an SNMP agent.
The SNMP agent is a program that collects information about its environment, signals an event to the manager, and retrieves information for the manager.
An SNMP manager is a separate application that usually runs on a server and is used to query agents, set up configuration, and monitor events.
Every SNMP agent maintains a small database called a Management Information Base (MIB). The MIB files contain a set of questions a manager can ask the agent. All monitoring and configuration information stored on the device is located in the MIB.
SMB
SMB is a protocol that provides file and print sharing services over a network. It also can provide file and record locking, file attributes, and file/directory/share access information. Used on older Windows machines, it was a way to enable non-Windows computers to access data located in Windows machines on the network.
A product called Samba was created for use in Unix machines to access Windows shared directories and files. Active Directory is now used to provide file system interoperability.
CIFS
Common Internet File System (CIFS) is used to share files and printing across the Internet. It is an enhanced Microsoft version of the SMB protocol introduced in Windows 2000. It can lock files to allow multiple clients access to the same file.
SSH
Secure shell is an encrypted remote access network protocol that provides both a secured and an authenticated access to a remote computer, typically through a terminal emulator program. It was designed and created to replace Telnet. SSH uses encryption methods such as ciphers like AES, Triple DES, Blowfish, and others.
AFP
The Apple Filing Protocol is used to provide file services for Mac computers running OS X. It uses port 548 (and sometimes 427) for establishing communication between two systems. Mac computers can also use SMB (and other protocols) for connecting to other systems.
TCP Versus UDP
Both TCP and UDP provide port numbers to identify the type of request being sent on a packet-switched network and a checksum that verifies data arrives in good condition. They also both send short packets called datagrams. Although both are part of the TCP/IP suite, they work very differently from each other.
TCP is designed to enable two devices to establish and maintain a connection and communicate. It is connection-oriented, which means it is reliable. It can break large data packets into smaller individual packets and resend any lost packets. This causes a bit of a delay, so it is not as fast as UDP.
The following are some advantages of using TCP:
![]() Guaranteed delivery, connection-oriented
Guaranteed delivery, connection-oriented
![]() Data can be transferred in full duplex on a single connection
Data can be transferred in full duplex on a single connection
![]() Manages flow control
Manages flow control
![]() Meant to be error-free (handles retransmission)
Meant to be error-free (handles retransmission)
The following are some disadvantages of using TCP:
![]() It’s slower than UDP.
It’s slower than UDP.
![]() It’s a complex protocol to set up and maintain.
It’s a complex protocol to set up and maintain.
UDP provides minimal transport services. Because packets can be lost or out of order without affecting communications, UDP is used mainly with applications such as gaming, voice, and video. It is also a popular choice for tunneling as long as other protocols provide the encapsulation and decapsulation services.
The following are some advantages of using UDP:
![]() UDP has lower bandwidth than TCP.
UDP has lower bandwidth than TCP.
![]() It can be broadcast.
It can be broadcast.
![]() Multicast applications are built on top of UDP.
Multicast applications are built on top of UDP.
The following are some disadvantages of using UDP:
![]() Delivery can be out of order and unreliable.
Delivery can be out of order and unreliable.
![]() No protection from duplication exists.
No protection from duplication exists.
![]() No end-to-end connections.
No end-to-end connections.
![]() No congestion or flow control.
No congestion or flow control.
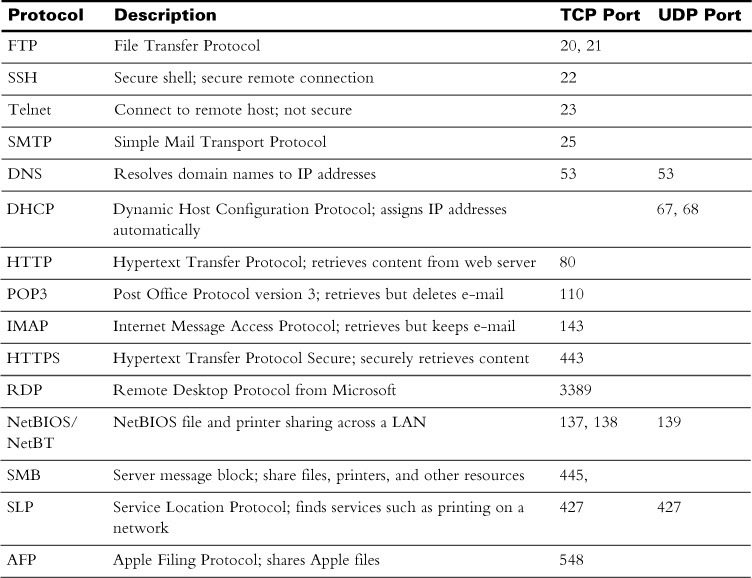
Table 22-1 shows which protocols use the TCP transport protocol and which use the UDP protocol. Note that some of them use both.
![]() Activity 22-2: Match the Protocol to Its Purpose
Activity 22-2: Match the Protocol to Its Purpose
Refer to the Digital Study Guide to complete this activity.
Study Resources
For today’s exam topics, refer to the following resources for more study.

![]() Check Your Understanding
Check Your Understanding
Refer to the Digital Study Guide to take a quiz covering the content of this day.