Day 21. SOHO Router Installation
CompTIA A+ 220-901 Exam Topics
![]() Objective 2.5: Compare and contrast various Wi-Fi networking standards and encryption types.
Objective 2.5: Compare and contrast various Wi-Fi networking standards and encryption types.
![]() Objective 2.6: Given a scenario, install and configure SOHO wireless/wired router and apply appropriate settings.
Objective 2.6: Given a scenario, install and configure SOHO wireless/wired router and apply appropriate settings.
Key Topics
In this day, we will compare the different Wi-Fi standards and the encryption types used to secure wireless communications. We also will discuss how to install a small office/home office (SOHO) router. Finally, we will explore the SOHO router configuration pages and make the necessary changes to ensure that the router will provide the required services to the network.
Wireless Standards
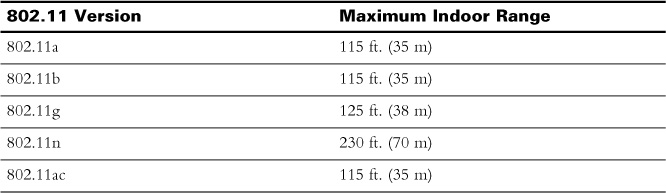
Wireless communications are more popular than ever. Mobile devices, laptops, and even desktops can connect to networks wirelessly. Many wireless standards (IEEE 802.11) exist that define the radio frequencies used and the maximum transmission data rate that can be achieved. Refer to Table 28-7 in Day 28 for details about the various Wi-Fi standards. Table 21-1 shows the distance limitations of each of the 802.11 standards.
SOHO Router Configuration
When setting up a Wi-Fi router for the first time, it is easiest to connect it directly to a desktop or laptop computer for initial configuration. To accomplish this, set the computer’s IP address manually to an address on the same network as the Wi-Fi router. This is often either the 192.168.1.0 or 192.168.0.0 network. Check the documentation of the router to determine the default network.
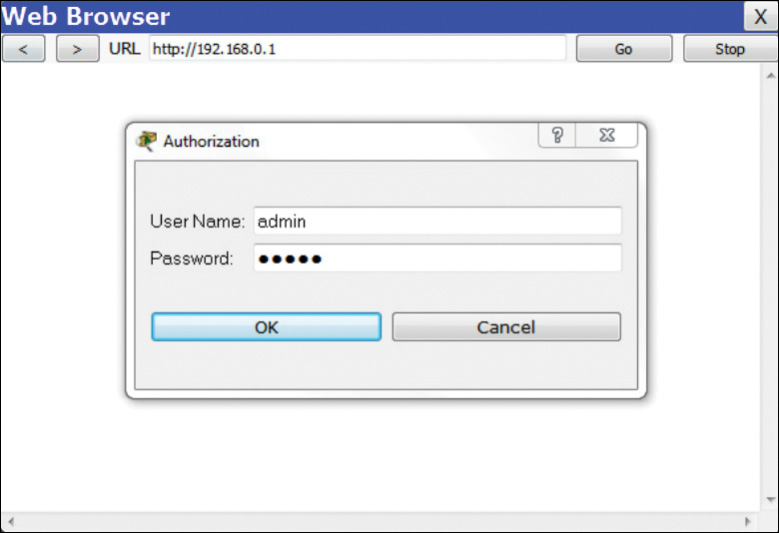
After setting the IP address, a web browser is commonly used to connect to the built-in web server on the Wi-Fi router. Point the browser to the IP address of the router, and log in using the default username and password provided by the router manufacturer, as shown in Figure 21-1.
At this point, decide whether DHCP will be used by the router to automatically assign IP addresses to clients. If manual addressing will be used, turn off DHCP in the router configuration.
Like a PC or laptop, a Wi-Fi router has firmware that controls the hardware and stores the software to configure the router. Make sure the router is using a firmware version that has the desired configuration settings and features. Upgrade the firmware only if necessary.
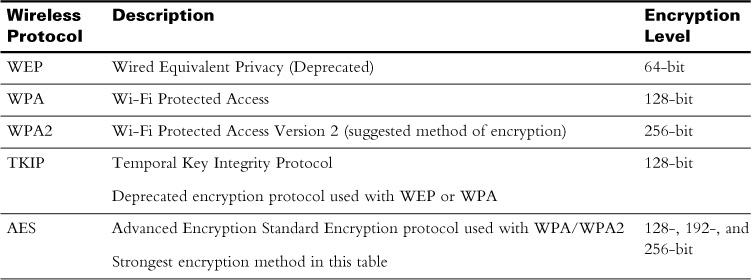
The data transmissions between devices and a wireless router are not secure. These transmissions can be intercepted unless they are encrypted. Table 21-2 shows the various wireless encryption methods, and Figure 21-2 shows a typical wireless security settings page on a wireless router.
Channels
The radios in wireless devices use a range of frequencies to communicate. When many wireless devices are in range, interference from these devices can slow down or even prevent communication. Devices such as baby monitors, cordless phones, or other Wi-Fi routers that are using the same frequency range can cause this interference.
Different frequency ranges are represented by channels. For example, channel 6 in an 802.11n network lies in the center of a 22 MHz range, with a center frequency of 2.437 GHz. The Wi-Fi router often defaults to automatically choose the best channel, but many times it can be set manually. If a specific channel is experiencing interference, try a different channel setting.
NAT
All devices on the Internet have a public (WAN) IP address so they can be uniquely identified. To address all the devices that connect to a router in the LAN, Network Address Translation (NAT) is used. NAT enables communications from multiple devices behind the router to use the same public IP address to communicate with devices on the Internet.
NAT works by remapping the IP addresses of the devices on the LAN to the public IP address of the WAN when communication crosses the router’s interface. NAT is a basic type of firewall because it prevents computers on the WAN from seeing the IP addresses of the devices on the LAN.
Port Forwarding and Port Triggering
Port forwarding is where an external network port is directed to an internal device at a specific IP address and port. This enables you to run a web server, an FTP server, or another type of service and access it from outside the network. On the Wi-Fi router, the desired port for each service, along with the IP address of the host to which the port will be forwarded, is entered.
For example, if you want to run a web server on your network, port 80 (http) would need to be forwarded to the IP address of your web server—that is, 192.168.1.100. When a web browser is pointed at your public (WAN) IP address, the router will see the request on port 80 and forward the traffic to 192.168.1.100, where the web server will respond to the request.
Sometimes, port forwarding is called destination NAT (DNAT).
Another type of configuration on a router using NAT is port triggering. Port triggering is used to forward a specific port back to the originating host when it uses a defined outgoing port. For example, a trigger port such as 2016 is the outgoing port while a destination port might be 1030. When outgoing traffic on port 2016 is seen by the router, it triggers the router to open port 1030 and send back any communications from the outbound connection to the originating device on that port. This is useful for special applications such as Internet Relay Chat (IRC), a method of chatting and sharing files between users or bit torrents, which are files shared between many users at the same time.
DMZ
Instead of using port forwarding to set up services on devices within the LAN, a demilitarized zone (DMZ) can be used. A DMZ is where devices with specific IP addresses are no longer protected by the router and all incoming ports and traffic are allowed in to the devices. It is a separate location from the LAN.
A DMZ is useful to place web, e-mail, or FTP servers into because all the untrusted Internet traffic is no longer let into the LAN. Of course, the DMZ servers are completely exposed and at risk of compromise. The DMZ should be used only when it is protected by a proxy or firewall. You can designate a server to be placed in a DMZ by entering its IP address in the DMZ settings page of the Wi-Fi router.
Basic QoS
Various types of traffic occur on networks—web browsing, e-mail, gaming, and voice and video calling, to name just a few. Some of these traffic types need to have priority over others. Quality of service (QoS) can be configured on the router to prioritize certain traffic over others. QoS ensures that these services work as best they can.
For example, web traffic would be a much lower priority than a video call. This is because the video call needs to be as close to real time as possible. If data is late or missing, it affects the quality of the call. Video or audio might drop or skip when the data does not reach the destination in time. Gaming needs priority over standard web or e-mail traffic as well, but it would not have priority over voice or video calls.
UPnP
Another feature found on Wi-Fi routers is Universal Plug and Play (UPnP). This useful feature enables computers, printers, televisions, and other network-ready devices to automatically connect with each other on the network. UPnP makes connecting devices easy for the novice user. It is primarily intended to be used on residential networks.
![]() Activity 21-1: Identify Wireless Router Terms
Activity 21-1: Identify Wireless Router Terms
Refer to the Digital Study Guide to complete this activity.
Study Resources
For today’s exam topics, refer to the following resources for more study.