Day 16. Network Troubleshooting and Tools
CompTIA A+ 220-901 Exam Topics
![]() Objective 2.9: Given a scenario, use appropriate networking tools.
Objective 2.9: Given a scenario, use appropriate networking tools.
![]() Objective 4.4: Given a scenario, troubleshoot wired and wireless networks with appropriate tools.
Objective 4.4: Given a scenario, troubleshoot wired and wireless networks with appropriate tools.
Key Topics
Today we will be looking at tools used to troubleshoot both wired and wireless networks. We will be looking at what to do for little or no connectivity, slow transfer speeds, wireless networks that cannot be found, as well as many other typical networking problems. We will also be looking at both hardware and software tools that can be used to diagnose and troubleshoot the causes, as well as the solutions to these types of problems.
Common Network Symptoms
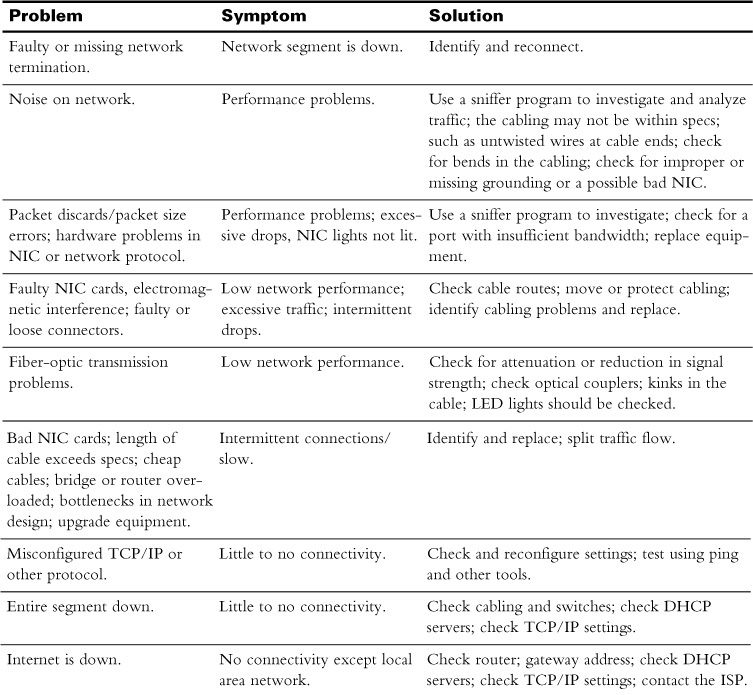
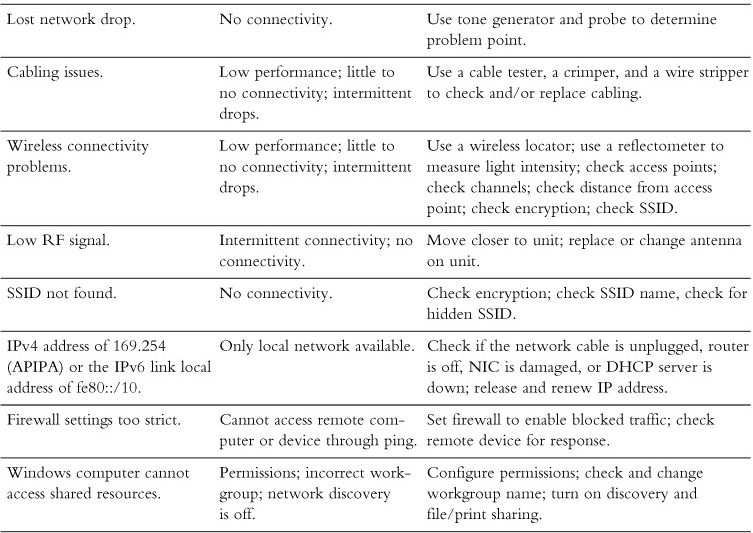
Networking problems come in many forms, which can make troubleshooting difficult. The causes can be just as varied as the solutions. Table 16-1 is not all-inclusive, but it does cover many of the most typical networking issues, their symptoms, and possible solutions.
Cabling Tools
The following tools shown in Figure 16-1 and described in the following list are meant for troubleshooting cabling. The only one not used for cabling that we will be covering is the Wi-Fi analyzer.
![]() Crimper—A crimping tool is a device that joins two pieces of metal by pressing them together. The most commonly used crimping tool is used with networking and telephone cables. Most crimpers come with the ability to crimp either an RJ-45 Ethernet connector or an RJ-11 telephone connector on both ends of the cable.
Crimper—A crimping tool is a device that joins two pieces of metal by pressing them together. The most commonly used crimping tool is used with networking and telephone cables. Most crimpers come with the ability to crimp either an RJ-45 Ethernet connector or an RJ-11 telephone connector on both ends of the cable.
![]() Cable stripper—One of the most important aspects of making a cable is to strip the plastic sheathing off the end of the wire without putting a nick in the jacket covering the copper center, thus creating a short in the cable. Strippers are used to safely remove the sheathing without creating nicks. They can be used for coaxial, fiber-optic, and unshielded twisted pair.
Cable stripper—One of the most important aspects of making a cable is to strip the plastic sheathing off the end of the wire without putting a nick in the jacket covering the copper center, thus creating a short in the cable. Strippers are used to safely remove the sheathing without creating nicks. They can be used for coaxial, fiber-optic, and unshielded twisted pair.
![]() Toner probe—Sometimes called a fox and hound, a tone generator is a two-part tool designed to connect to a cable at one end that generates a tone. The other end is a probe you can run along cabling racks or punchdown blocks until the tone is heard. This indicates the other end of the cable. This tool is used when technicians are unable to determine where a wire or cable terminates.
Toner probe—Sometimes called a fox and hound, a tone generator is a two-part tool designed to connect to a cable at one end that generates a tone. The other end is a probe you can run along cabling racks or punchdown blocks until the tone is heard. This indicates the other end of the cable. This tool is used when technicians are unable to determine where a wire or cable terminates.
![]() Cable tester—A cable tester is an electronic device used to verify the connections in a cable. It is also known as a continuity tester or cable certifier. It works by plugging an RJ-45 end into a port and then running a test on each wire to determine whether they are working properly and wired correctly.
Cable tester—A cable tester is an electronic device used to verify the connections in a cable. It is also known as a continuity tester or cable certifier. It works by plugging an RJ-45 end into a port and then running a test on each wire to determine whether they are working properly and wired correctly.
![]() Punchdown tool—A punchdown tool (also known as a punch down tool) is a small tool used by telecommunication and network technicians to terminate wire into connectors on a punchdown block. After adjusting wires to match a wiring scheme like T568A or B, the punchdown tool is used to force the wires into the slots. It is designed so that the blunt side of the blade pushes the wire into a slot and simultaneously the sharp side of the blade cuts excess wire off.
Punchdown tool—A punchdown tool (also known as a punch down tool) is a small tool used by telecommunication and network technicians to terminate wire into connectors on a punchdown block. After adjusting wires to match a wiring scheme like T568A or B, the punchdown tool is used to force the wires into the slots. It is designed so that the blunt side of the blade pushes the wire into a slot and simultaneously the sharp side of the blade cuts excess wire off.
![]() Multimeter—A testing device that can take measurements of the integrity of circuits and the quality of electricity in computer components. It primarily measures voltages, amps, and resistance (ohms). A small digital display will show measurement readouts. Multimeters are used to diagnose circuits, discover electronic designs, and even test batteries.
Multimeter—A testing device that can take measurements of the integrity of circuits and the quality of electricity in computer components. It primarily measures voltages, amps, and resistance (ohms). A small digital display will show measurement readouts. Multimeters are used to diagnose circuits, discover electronic designs, and even test batteries.
![]() Loopback plug—A loopback plug simulates a short crossover network connection. It can help determine whether the network interface card is working properly by redirecting output back into the interface. This makes the network card believe that it is transmitting and receiving data.
Loopback plug—A loopback plug simulates a short crossover network connection. It can help determine whether the network interface card is working properly by redirecting output back into the interface. This makes the network card believe that it is transmitting and receiving data.
![]() Wi-Fi analyzer—(Not shown in graphic.) This is a mobile tool for auditing and troubleshooting wireless networks. It can be used to scan nearby wireless networks to see which channel is being used in order to avoid interference with other devices. It also can help improve performance by finding a less crowded channel. Some analyzers offer channel ratings, signal strength over a period of time, or a list of all access points in the area.
Wi-Fi analyzer—(Not shown in graphic.) This is a mobile tool for auditing and troubleshooting wireless networks. It can be used to scan nearby wireless networks to see which channel is being used in order to avoid interference with other devices. It also can help improve performance by finding a less crowded channel. Some analyzers offer channel ratings, signal strength over a period of time, or a list of all access points in the area.
![]() Activity 16-1: Match the Networking Tool to Its Picture
Activity 16-1: Match the Networking Tool to Its Picture
Refer to the Digital Study Guide to complete this activity.
Command-line Tools
Microsoft’s command prompt is its command-line interface (CLI). It is a text-based environment where you can issue commands that affect the file system or the OS. To open it in Windows 8, right-click the Start button and select command prompt. In Windows 7 or Vista, navigate to Start > All Programs > Accessories > command prompt. In all versions of Windows, you can perform a search for the word “command” or “cmd” or search for words and phrases that are associated with it. If possible, you should run the command prompt as an administrator for access to elevated commands by right-clicking the program and selecting Run as Administrator.
Notice that Figure 16-2 shows the command prompt being run at an elevated administrator level at the top.
By going to the command line (otherwise known as the command prompt), technicians can access many tools without worrying about the GUI interfering. Some tools are available only at the command-line level.
Ping
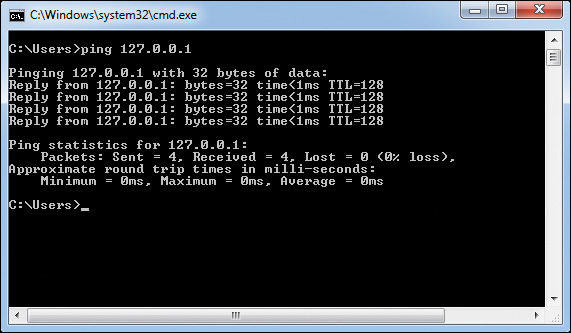
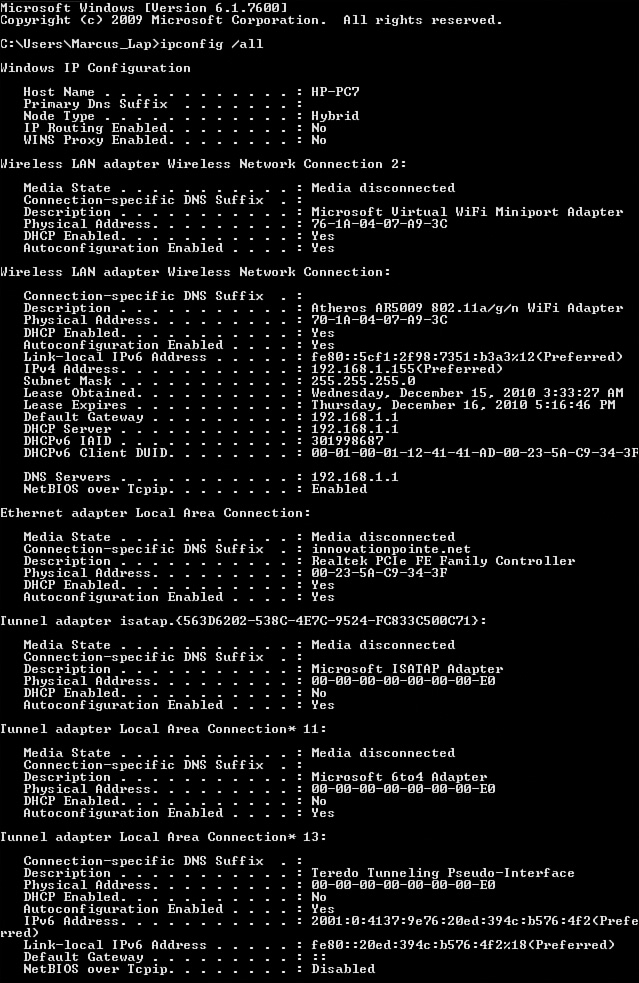
Ping sends out an Internet Control Message Protocol (ICMP) request to determine whether other devices can receive and respond to a request. Ping can be used to determine a break in a route to a remote location. When troubleshooting with ping, start by pinging the local loopback address: 127.0.0.1 for IPv4, and ::1 for IPv6. This will show if the IP stack is working correctly, as shown in Figure 16-3.
Next, ping another host on the local network to determine whether the local area network is up and running. If not, this could be an indication that a switch or another networking device is the problem. If those pings work properly, next, select the gateway address to determine whether it can be reached. If a message returns stating Request Timed Out or Destination host Unreachable, the connection is down.
Look for latency problems as well as connection problems when running ping by noting the approximate roundtrip times in milliseconds. Latency is the time it takes for sent packets to be received by the remote computer. Local networks should have latencies around 1 millisecond (ms).
These options for ping are important to know:
![]() Ping -t—This will ping the host until the command is manually stopped by pressing Ctrl+C or by closing the command prompt. It’s known as a continuous ping.
Ping -t—This will ping the host until the command is manually stopped by pressing Ctrl+C or by closing the command prompt. It’s known as a continuous ping.
![]() Ping -n—This pings a host a specific number of times. Its syntax is ping -n 20 192.168.0.1.
Ping -n—This pings a host a specific number of times. Its syntax is ping -n 20 192.168.0.1.
![]() Ping -a—Resolves an IP address to a hostname.
Ping -a—Resolves an IP address to a hostname.
![]() Ping -4—This forces the use of IPv4 instead of IPv6. This might be necessary on a host that runs both IPv4 and IPv6 when you want to send an IPv4 echo request to a remote host using IPv4.
Ping -4—This forces the use of IPv4 instead of IPv6. This might be necessary on a host that runs both IPv4 and IPv6 when you want to send an IPv4 echo request to a remote host using IPv4.
![]() Ping -6—This forces the use of IPv6 instead of IPv4. This might be necessary on a host that runs both. It is also used to send an IPv6 echo request to a remote host using IPv6.
Ping -6—This forces the use of IPv6 instead of IPv4. This might be necessary on a host that runs both. It is also used to send an IPv6 echo request to a remote host using IPv6.
For additional information on the ping, or any other command-line tool, you can key in the command-line tool at the prompt followed by the question mark option—for example, ping /?.
ipconfig
Ipconfig is a utility that shows TCP/IP configuration information for Microsoft Windows machines. It will display the current TCP/IP configuration values for both the IPv4 and IPv6 addresses. It also displays the subnet mask and default gateway. Using the ipconfig /all command switch provides more information, including DHCP, DNS addresses, and MAC addresses for each network card installed on the machine. Use the ipconfig command to determine whether the IP configuration is correct.
If there is missing information or incorrect information, using ipconfig /all will display it. Look for missing network adapters or a Media state disconnected statement. To check for incorrect gateway addresses, see whether the IPv4 network portion of the IP address matches the default gateway address. If you see a Class C address, expect to see a Class C subnet mask. This is true of any subnet mask unless classless routing is involved.
For DNS, a single or multiple DNS server addresses should be displayed. If the address is blank, there is a problem. The IP address for DNS does not necessarily have to match the IP address used for the machine. An incorrect or missing DHCP address will show an Automatic Private IP Addressing (APIPA) address starting with 169.254 for the main IPv4 address. Expect the DHCP address to match the network portion of the IPv4 address used on the machine. Figure 16-4 provides a screenshot of the information provided when using the ipconfig /all command with everything working as expected.
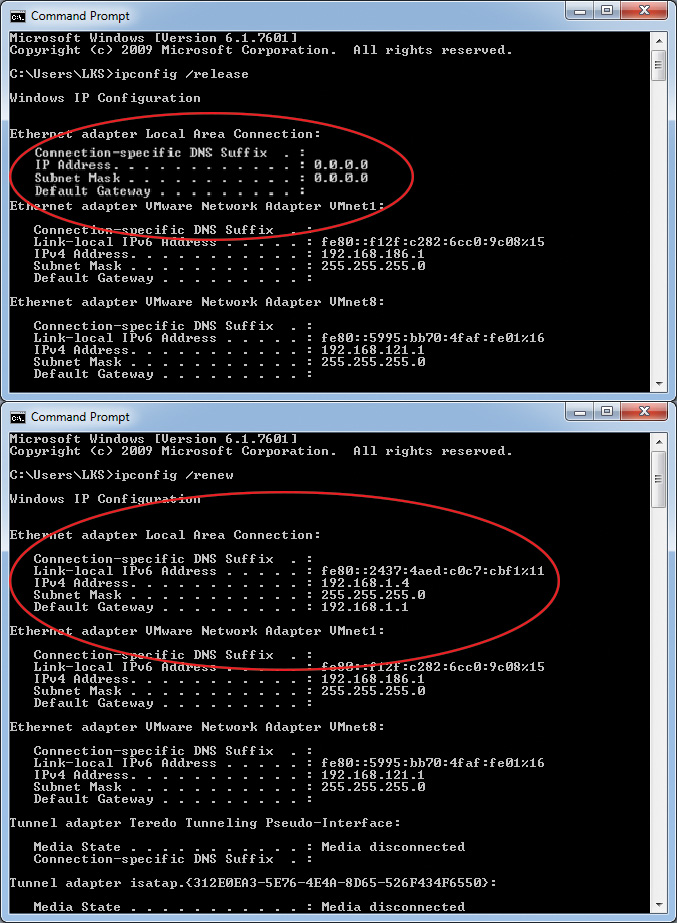
You also can use ipconfig with options to release and renew a DHCP IP address configuration. By running ipconfig /release, the computer gives up its current address configuration from the DHCP server. By running ipconfig /renew, the computer requests a new address configuration from the DHCP server. Another option, ipconfig /flushdns, can be used to erase DNS cached information. For more information about ipconfig, use the ipconfig /? command.
Figure 16-5 shows the results of running the ipconfig /release and ipconfig /renew commands.
ifconfig
ifconfig works the same as the ipconfig command. It is used on Linux and OS X operating systems. It, uses the same options and provides the same results.
tracert/traceroute
The tracert command is used for tracing the route between two points on a network. It actually pings each router along the way to provide a list of the path the packet is taking. tracert gives the path the packet should be taking when everything is working correctly. It can then be used with the ping command to locate a downed connection.
Here is an example of some tracert results:
Tracing route to 54.36.193.56] over a maximum of
30 hops:
1 <1 ms <1 ms <1 ms 10.100.140.254
2 <1 ms <1 ms <1 ms 172.21.240.250
3 <1 ms <3 ms <1 ms 134.187.253.128
4 1 ms 1 ms 1 ms toldb-r8-ge-4-0-1s644.core.oar.net [197.18.158.248]
Note: These additional lines were not shown in the above example:
5 * * * Request timed out.
6 Trace complete.
Lines 1–4 show the ping responses measured in milliseconds. Lines 1–4 also represent a hop, or the next device in the communication path through a network. Note that at the end of the first four lines is the name of the router or its IP address. Row 5 shows what happens when the tracert command does not complete successfully, and row 6 shows what happens when it does complete successfully.
The traceroute command is used for Linux and Apple computers. It performs the same operation as the tracert command and uses the same syntax.
netstat
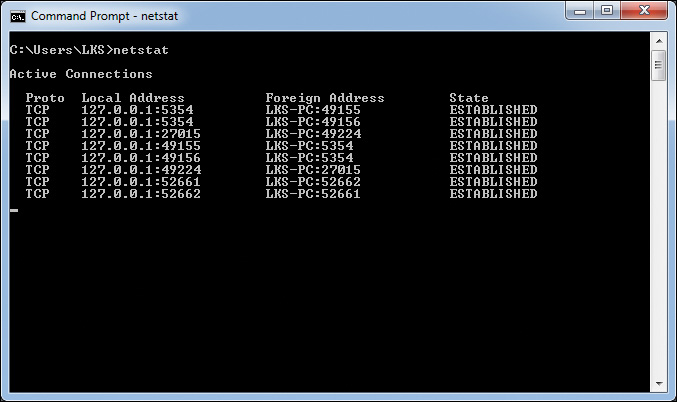
netstat displays connection status of the following protocols: TCP, IP, ICMP, and UDP. It also shows the IP routing table, IPv4 statistics, and both incoming and outgoing sessions to which a local machine is listening. Without parameters, netstat displays active TCP connections to remote computers. See Figure 16-6 for an example of the netstat command.
netstat can be used to print network connections, routing tables, and the interfaces. It also has options that can be used for finding problems in the network and determining the amount of traffic on a network.
netstat has the following helpful options, shown in Table 16-2, that can be used to troubleshoot.
netstat provides the protocol, local address, remote (foreign) address, and connection state. It also provides the port information. The most common connection states are
![]() CLOSED—The server has received a signal from the client and the connection is closed.
CLOSED—The server has received a signal from the client and the connection is closed.
![]() ESTABLISHED—The session is established and open.
ESTABLISHED—The session is established and open.
![]() LISTENING—The server is ready to accept a connection.
LISTENING—The server is ready to accept a connection.
![]() TIME_WAIT—Indicates that the client recognizes the connection as still active but not being used.
TIME_WAIT—Indicates that the client recognizes the connection as still active but not being used.
Nbtstat
Nbtstat is a diagnostic tool for helping to troubleshoot NetBIOS name resolution problems when traveling over TCP/IP. It can display statistics and current TCP/IP connections as well as a table with the NetBIOS names for the devices on a Windows network.
The -a and-A options are the most frequently used. The -a option is used when you know the machine name and want the IP address. The -A option is used when you know the IP address and want to know the machine name. The following are examples of both:
Nbtstat -a HH104-35
Nbtstat -A 192.168.115.201
NET
The NET command can be used to manage almost any networking services, including managing the network file system, users, printing, and much more. Options for the NET command can act as commands in and of themselves. Typically, the NET command is used to start or stop services. A good example of this is the following:
net stop spooler
This command would stop the printing spooler from running.
The exam covers the net use command, which is used to display or create mapped network drives. To view a network drive, use net use. To create a mapped drive, the command syntax would be similar to the following:
net use x: \computernamesharename
where x represents the drive letter to be mapped, computername represents the remote host, and sharename is the share created on the remote host. For additional information, type net /? at the prompt. For more information on the net use command, type net use /?.
Netdom
This is a tool built in to Windows Server designed to manage Active Directory domains from a command line. To access it, Active Directory Domain Services or the tools supporting it must be installed. It is used to join computers to a domain, manage remote accounts, establish trust relationships between multiple domains, and perform other Active Directory management tasks.
nslookup
The nslookup command is a utility used to query DNS servers to discover either an IP address or a hostname. It is a tool used to find out information about a domain server including the type of services it provides and information about various hosts and domains it is aware of, or to print a list of them.
For example, to find out what the IP address is for Microsoft.com, you would run the command nslookup Microsoft.com. It will display the IP address. If you need the name of the domain and all you have is the IP address, nslookup can be used in the same manner. For example, the command nslookup 134.170.185.46 will display the domain name grp.microsoft.com.
![]() Activity 16-2: Select the Correct Tool to Solve Networking Problems
Activity 16-2: Select the Correct Tool to Solve Networking Problems
Refer to the Digital Study Guide to complete this activity.

![]() Check Your Understanding
Check Your Understanding
Refer to the Digital Study Guide to take a quiz covering the content of this day.