This chapter covers the following topics:
Comparing Cisco CatOS and Cisco IOS
Handling Initial Configuration of Management Parameters for Cisco Catalyst Switches
Managing Catalyst Switch Configurations
Handling Cisco IOS File System and Software Images for Catalyst Switches
Upgrading Software Versions on Catalyst Switches
Implementing Basic Troubleshooting Practices
Cisco Systems, Inc. ships most Catalyst switches today with Cisco IOS (Native Mode) Software. The only exceptions are by order request for the Catalyst 6500 with a Multilayer Switch Feature Card (MSFC) module with Cisco CatOS. All Catalyst 6500 families of switches with an MSFC, MSFC2, or MSFC3 are capable of running Cisco CatOS or Cisco IOS software. In terms of product life cycle, the only Catalyst switch that currently supports new features and hardware support in Cisco CatOS is the Catalyst 6500 family of switches. CatOS 8.x, at the time of publication, is deemed the last version of CatOS with maintenance releases for bug fixes lasting the next few years. New features will no longer be added to Cisco CatOS.
When building Cisco multilayer switched networks, it is important to understand the features that are available and the initial configuration of each operating system (OS). Foremost, before configuring any Catalyst switch for operation in a multilayer switched network, you need to understand the basic OS command-line interface (CLI) to upgrade to specific software versions for network consistency, hardware support, code updates, and new features. In addition, you must understand how to configure basic system parameters, such as IP addresses, and other basic management functions, such as DNS and system logging (syslog), and prevent unauthorized access to the switch and multilayer switched network. To prepare you for initial installations of Catalyst switches, this chapter discusses the following CLI configuration topics:
Switch name
Management IP configuration
Telnet and SSH
DNS
System logging
SNMP
In addition, this chapter covers the following specific topics to aid in the initial setup of Catalyst switches:
This chapter concludes with a summary and a lab exercise. In terms of CCNP BCMSN exam preparation, focus on all sections except the section on SNMP. The SNMP section is outside the scope of the CCNP BCMSN exam, yet is important to both Enterprise Campus and Data Center deployments.
In addition, concentrate on Cisco IOS because the BCMSN exam focuses on Cisco IOS instead of Cisco CatOS.
Cisco CatOS is the traditional Layer 2 operating system for Cisco Catalyst switches. Configuring Catalyst 6500 for Layer 3 features with Cisco CatOS requires a separate Layer 3 or router module running Cisco IOS software version. The term hybrid mode refers to the use of Cisco CatOS for configuring Layer 2 features and Cisco IOS for Layer 3 interfaces on the same platform.
Cisco IOS Software is capable of configuring both Layer 2 and Layer 3 features. Cisco IOS runs on any Cisco router or switch that can have interfaces that act as router ports (Layer 3) or as switched ports (Layer 2). Furthermore, Cisco IOS supports Layer 2–only switches such as the Catalyst 2950. Ports act as router or switch ports depending on the software configuration and hardware support of the respective interface. Cisco IOS running on Catalyst switches is also referred to as integrated IOS because Cisco IOS integrates the functions of multiple layers. Cisco IOS ships on all Catalyst families of switches, including the Catalyst 2940, 2950, 2970, 3550, 3560, 3750, 4500, and 6500 families. An alternative name for Cisco IOS running on the Cisco Catalyst 6500 family of switches is Native IOS. Likewise, another term for running Cisco IOS on any Catalyst switch is Cisco IOS Native Mode. This book uses the term Cisco IOS to describe Cisco IOS running on a Catalyst switch. Furthermore, Cisco IOS also supports Layer 2–only switches.
With the 6500 family of switches, support exists for either a hybrid-mode (running CatOS on the Supervisor Engine and Cisco IOS on the MSFC) or Cisco IOS when an MSFC module is present on the Supervisor Engine. When running Cisco CatOS on a Catalyst 6500 Supervisor Engine with an MSFC module, the MSFC itself runs a separate Cisco IOS image. The terms commonly used to describe a Catalyst 6500 running CatOS on the Supervisor Engine for Layer 2 functionality and Cisco IOS on the MSFC are hybrid mode and Hybrid OS. All other models of Catalyst switches support either Cisco CatOS or Cisco IOS but not specifically the hybrid-mode software. Currently, Cisco still supports the Cisco CatOS operating system on the Catalyst 4500 and 6500 families of switches. Table 3-1 illustrates which Catalyst switches run Cisco CatOS, Hybrid OS, and Native IOS. This book uses hybrid mode to represent a Catalyst 6500 running CatOS on the Supervisor Engine and Cisco IOS on the MSFC.
Table 3-1. Cisco CatOS, Hybrid OS, and Cisco IOS Platform Matrix
Platform | Cisco OS |
|---|---|
Catalyst 6500 with MSFC or MSFC2 | Either hybrid-mode (Hybrid OS) or Cisco IOS |
Catalyst 6500 without an MSFC or MSFC2 | Cisco CatOS |
Catalyst 6500 with Supervisor Engine 720, PFC3, and MSFC3 | Either hybrid-mode (Hybrid OS) or Cisco IOS |
Catalyst 6500 with Supervisor Engine 32 | Either hybrid-mode (Hybrid OS) or Cisco IOS |
Catalyst 4000 or 4500 with Supervisor Engine II+, III, IV, or V; Catalyst 4948 | Cisco IOS |
Catalyst 4912G | Cisco CatOS (Layer 2–only platform) |
Catalyst 4000 or 4500 with Supervisor Engine I or II | Cisco CatOS (Layer 2–only platform) |
Catalyst 3550, 3560, or 3750 | Cisco IOS |
Catalyst 3500XL | Cisco IOS (Layer 2–only platform) |
Catalyst 2940, 2950, 2955, 2960, or 2970 | Cisco IOS (Layer 2–only platform) |
Catalyst 2948G, 2980G, or 2948-GE-TX | Cisco CatOS (Layer 2–only platform) |
2948G-L3 or 4908G-L3 | Cisco IOS |
Cisco Catalyst Express Switches | Cisco IOS |
Feature parity does exist between hybrid-mode Cisco CatOS and Cisco IOS, although some differences exist between platform uses of Cisco IOS. The ultimate goal of Cisco IOS is complete feature and configuration parity with Cisco CatOS.
Note
This text focuses primarily on Cisco IOS. Most examples include Cisco CatOS for completeness and for those individuals using Cisco CatOS switches to prepare for the BCMSN switching exam. The BCMSN switching exam does not currently include coverage of Cisco CatOS commands.
Not surprisingly, differences do exist between the two types of operating systems. Table 3-2 illustrates the main system differences between Cisco CatOS and Cisco IOS.
Table 3-2. Cisco CatOS and Cisco IOS System Differences
Feature | Cisco CatOS | Cisco IOS |
|---|---|---|
Configuration file | Two configuration files: one for the Supervisor Engine, or Network Management Processor (NMP), and one for the MSFC. | One configuration file. Use standard Cisco IOS commands such as copy to save the configuration. |
Software image | Two images: one for the Supervisor Engine and one for the MSFC in the case of the Catalyst 6500. | One software image. An MSFC boot image is also required to allow the MSFC to load properly. |
Default port mode | Every port is a Layer 2 switched port. | Every port is a Layer 3 interface (routed port) on the Cisco 6500 family of switches. |
Default port status | Every port is enabled. | Every port is in the shutdown state for the Catalyst 6500 family of switches. Some switches allow for an option to configure all interfaces up or down during the automated setup program. |
Configuration commands format | The command keyword set precedes each configuration command. | Cisco IOS command structure with global and interface-level commands. |
Configuration mode | No configuration mode (set, clear, and show commands). | The command configure terminal activates the VLAN configuration mode. |
Removing/changing the configuration | Via use of clear, set, or enable/disable commands. | Same as Cisco IOS command structure; keyword no negates a command. |
Before you deploy Cisco Catalyst switches, you must configure them to ease administration and troubleshooting. The basic configuration-management parameters are as follows:
System name
Management IP configuration
Clock and Network Time Protocol (NTP) settings
Telnet and Secure Shell (SSH)
DNS
System logging
Simple Network Management Protocol (SNMP)
These configuration parameters are necessary for proper management and to simplify troubleshooting during initial installation. Your enterprise network may deploy other configuration parameters such as RMON. The preceding list of basic configuration-management parameters are those necessary to establish a switch in the network for in-band management and troubleshooting during initial installation.
Configuration of a meaningful system name is essential in managing Catalyst switches effectively. The default names of Switch, Router, and Console on multiple switches are not easily distinguishable from the CLI when multiple Telnet, SSH, or console sessions are open to multiple switches. Configuring meaningful and unique switch system names throughout the enterprise network is extremely useful, particularly system names that allude to location. For example, a system name of Sw4thFlRm2 abbreviates “Switch 4th Floor Room 2.” Meaningful system names provide for quick examination of the precise switch currently being accessed. To configure the Catalyst switch system name on Cisco IOS–based switches, use the following command:
hostname name-string
name-string refers to the switch name. To configure the Catalyst switch system name on Cisco CatOS–based switches, use the following command:
set system name name-string
Examples 3-1 and 3-2 illustrate a user configuring the Catalyst switch system name on a Cisco IOS–based and Cisco CatOS–based switch, respectively.
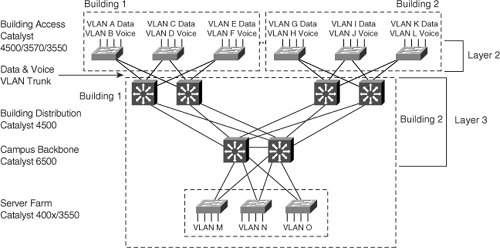
The management IP address allows for administrative access to the switch using Telnet, SSH, and HTTP. For Layer 2 switches and for Layer 3 switches acting solely as Layer 2 switches, use a single IP address for administrative access. This IP address occupies a specific VLAN. For example, Figure 3-1 illustrates a medium-sized network in which each access layer switch consists of two VLANs: one for voice and one for data. The switch management IP address resides in the data VLAN in this example. If VLAN A represents VLAN 101, then you should configure an interface VLAN 101 on your access layer switch with an IP address in VLAN 101.
Use the following command to configure an IP address on a Cisco IOS–based switch:
ip address ip-address subnet-mask
Example 3-3 illustrates configuration of an IP address on a VLAN interface on a Cisco IOS–based switch.
Because Layer 2 switches do not perform routing functions, Layer 2 switches require a default gateway IP address to reach subnets beyond the local subnet. Use the following command to configure an IP default gateway on a Cisco IOS–based switch:
ip default-gateway ip-address
Example 3-4 illustrates the configuration of an IP default gateway on a Cisco IOS–based switch.
Cisco CatOS–based switches are Layer 2 switches. As a result, these switches use a specialized interface for management, known as the sc0 interface. The sc0 configuration parameters include IP address, subnet mask, and VLAN. Use the following command to configure the sc0 management interface on Layer 2–only Cisco CatOS–based switches:
set interface sc0 [vlan] [ip_address [netmask [broadcast]]]
Then use the following command to configure the default gateway for a Cisco CatOS–based switch:
set ip route default gateway [primary]
To view the current sc0 interface configuration, use the following command:
show interfaceExample 3-5 illustrates the configuration of an IP address on the sc0 interface and default gateway configuration on a Cisco CatOS–based switch in VLAN 5. Note that the broadcast address is automatically configured unless otherwise specified.
Example 3-5. Configuring an IP Address, Subnet Mask, VLAN Assignment, and Default Gateway on a Cisco CatOS–Based Switch
Console (enable) set interface sc0 5 10.1.101.11 255.255.255.0 Interface sc0 vlan set, IP address and netmask set. Console (enable) set ip route default 10.1.101.1 Route added. Console (enable) show interface sl0: flags=51<UP,POINTOPOINT,RUNNING> slip 0.0.0.0 dest 0.0.0.0 sc0: flags=63<UP,BROADCAST,RUNNING> vlan 5 inet 10.1.101.1 netmask 255.255.255.0 broadcast 10.1.101.255
The Building Distribution and Campus Backbone submodule switches in Figure 3-1 are Layer 3 switches; these switches are composed of multiple IP subnets on either VLANs or Layer 3 interfaces. Consequently, these switches have multiple IP addresses, which may act as a management IP address. As long as the management IP address is reachable from any network for in-band access, any IP address configured on the Layer 3 switches suffices as a management IP address. However, it is nonetheless recommended to separate out a specific subnet for management purposes. In addition, these switches do not require default gateways because they are performing routing functions and using routing protocols. Later chapters of this book discuss Layer 3 routing configuration in more detail.
Clock settings to accurately display the time and date are essential in monitoring and troubleshooting Catalyst switches. Knowing exactly when events occur is crucial to maintaining control and stability of an enterprise network because system logging functionality uses timestamps. Furthermore, NTP is useful for synchronizing the system clocks for all network devices in the enterprise. Events for which time stamping is crucial include SNMP traps, SNMP inform messages, and system logging messages such as link state change, system reload, and so on. Use the following commands on Cisco IOS–based switches to configure the time and date along with the time zone; the clock set commands have two alternative formats:
clock set hh:mm:ss day month year clock set hh:mm:ss month day year clock timezone zone hours-offset [minutes-offset]
The clock set command is an executable command; the clock timezone command is a global configuration command. For the clock timezone configuration command, zone represents the time zone in abbreviations such as EST and PST, and hours-offset indicates the number of hours the current time zone is offset from UTC.
For Cisco CatOS–based switches, use the following commands to accomplish the same time and date configuration tasks:
set time [day_of_week] [mm/dd/yy] [hh:mm:ss] set timezone [zone_name] [hours [minutes]]
Examples 3-6 and 3-7 illustrate configuration of the time, date, and time zone on Cisco IOS–based switches and Cisco CatOS–based switches, respectively.
Daylight savings time adjustments are configurable to automatically update the system clock if your location observes yearly time adjustments. Use the following commands to configure recurring or one-time time adjustments, respectively, on a per-time basis for Cisco IOS–based switches:
clock summer-time zone recurring [week day month hh:mm week day month hh:mm [offset]] clock summer-time zone date date month year hh:mm date month year hh:mm [offset] clock summer-time zone date month date year hh:mm month date year hh:mm [offset]
Use the following commands to configure recurring or one-time clock adjustments, respectively, for Cisco CatOS–based switches:
set summertime {enable | disable} [zone] set summertime recurring [{week} {day} {month} {hh:mm} {week | day | month | hh:mm} [offset]] set summertime date {month} {date} {year} {hh:mm} {month | date | year | hh:mm} [offset]
Examples 3-8 and 3-9 illustrate the configuration of the standard United States recurring daylight savings time on Cisco IOS–based switches and Cisco CatOS–based switches, respectively.
Example 3-9. Configuring Recurring Time Adjustments on Cisco CatOS–Based Switches
Switch> (enable) set summertime recurring second Sunday March 2:00 first Sunday november 2:00 1f Summertime is enabled and set to '' Start : Sun Mar 11 2007, 02:00:00 End : Sun Nov 4 2007, 02:00:00 Offset: 1 hour Recurring: yes, starting at 02:00am of second Sunday of March and ending on 02:00 am of first Sunday of November.
The United States summertime parameters are the default and do not appear in the configuration. However, between 2007 and 2009, there is a shift to extend the period of daylight saving time in the United States as part of the Energy Policy Act of 2005. After 2009, a study will be presented to Congress to determine whether the extended period for daylight saving time is valuable and should continue.
Moreover, NTP is useful in synchronizing all the system clocks in the enterprise. Time synchronization is helpful in troubleshooting and network monitoring. To configure a Cisco IOS–based switch to synchronize its clock to an NTP server, use the following command:
ntp server ip-address
For information about the switch itself acting as an NTP server and additional NTP configuration options such as authentication keys and preferences, consult the configuration guide for the respective Catalyst switch.
To configure a Cisco CatOS–based switch to synchronize its clock to an NTP server, use the following command:
set ntp server ip_address
Examples 3-10 and 3-11 illustrate the configuration of NTP server associations on Cisco IOS–based switches and Cisco CatOS–based switches, respectively.
Both Cisco IOS–based and Cisco CatOS–based switches support administrative access via Telnet and SSH. Catalyst switches running Cisco IOS require a virtual terminal password configuration for command-line access, and both Cisco IOS and CatOS require an enable password for configuration access. Telnet passes passwords in clear-text. As a result, SSH, which does not transmit passwords in clear-text, is the preferable in-band connection method for CLI access to Catalyst switches. SSH requires the configuration of usernames and passwords and may optionally use RADIUS and TACACS+ methods of centralized security access. Cisco Secure supports both the TACACS+ and Radius Server features.
To configure a Cisco IOS–based switch’s virtual terminal password and an enable password, use the following virtual terminal interface and global configuration commands, respectively:
password password enable password [level level] {password | [encryption-type] encrypted-password}
For this command, encryption-type specifies the Cisco-proprietary algorithm used to encrypt the password. Currently, the only encryption type available is 7. If you specify encryption-type, the next argument you supply must be an encrypted password (a password already encrypted by a Cisco router). For simplicity, do not use the encryption-type option; simply enter a nonencrypted password in the command line when configuring the enable password.
To configure a Cisco CatOS–based switch’s virtual terminal password and an enable password, use the following commands to generate prompt scripts for changing passwords:
set password set enablepass
Examples 3-12 and 3-13 illustrate the configuration of Catalyst Cisco IOS–based switches and Cisco CatOS–based switches for enabling passwords and virtual terminal passwords, respectively.
Note
The line vty command in Example 3-12 specifies virtual terminal lines 0 through 15 inclusively, the default number of virtual terminal lines for remote access.
In Example 3-13, if this is the first time you are configuring a password in Cisco CatOS, press Enter to enter a null password for the old password.
Example 3-13. Configuring the Enable Password and Virtual Terminal Password on a Cisco CatOS–Based Switch
Console> (enable) set enablepass Enter old password: Enter new password: cisco Retype new password: cisco Password Changed Console> (enable) set password Enter old password: Enter new password: cisco Retype new password: cisco Password Changed
As mentioned previously, SSH does not transmit passwords in clear-text and is the preferable method of in-band access. The SSH feature is available only on recent versions of Cisco IOS for the Catalyst switches. Table 3-3 lists the Cisco IOS versions for which the SSH feature is available.
To enable SSH on a Cisco IOS–based switch, use the following command to generate the necessary keys for SSH:
crypto key generate rsaOther types of keys besides RSA are available in different versions of Cisco IOS. In addition to the crypto key generate command, enabling SSH requires the global configuration of aaa new-model. This command enables the use of local usernames and passwords for authentication, DNS name configuration, and virtual terminal configuration for inbound SSH sessions. Chapter 14 discusses additional security configurations and explains the aaa new-model command in more detail.
Example 3-14 illustrates the enabling of SSH as the only method of in-band access on a Cisco IOS–based switch.
Example 3-14. Configuring a Switch for SSH for Exclusive In-Band Access on a Cisco IOS–Based Switch
Switch(config)#ip domain-name cisco.com Switch(config)#aaa new-model Switch(config)#username cisco password cisco Switch(config)#crypto key generate rsa modulus 2048 The name for the keys will be: Switch.cisco.com % The key modulus size is 2048 bits Generating RSA keys ... [OK] 00:02:36: %SSH-5-ENABLED: SSH 1.5 has been enabled Switch(config)#line vty 0 15 Switch(config-line)#transport input ssh
For additional configuration parameters and examples of configuring SSH on Cisco IOS routers and switches, refer to the following technical document on Cisco.com:
“Configuring Secure Shell on Routers and Switches Running Cisco IOS”
In regard to Cisco CatOS software, Table 3-4 illustrates the software support of the SSH feature on Cisco CatOS–based Catalyst switches.
Example 3-15 illustrates the enabling of SSH as the only method of in-band access on a Cisco CatOS–based switch. Enabling an IP permit list without entries prevents access via the configured protocol.
Example 3-15. Configuring a Catalyst Switch for Exclusive In-Band Access via SSH on a Cisco CatOS–Based Switch
Switch (enable) set crypto key rsa 2048 Generating RSA keys............... [OK] Switch (enable) set ip permit enable telnet TELNET permit list enabled. WARNING!! IP permit list has no entries.
Although SSH is fairly secure, there are several inherent vulnerabilities that exist as a result of the protocol itself. Aside from protocol vulnerabilities, implementation and hardware or software defects on specific Cisco products might yield additional vulnerabilities. Keeping up-to-date on Cisco field notices, product vulnerabilities, and software versions minimizes security issues with SSH. The following list describes possible vulnerabilities with SSH, most of which have been addressed in the latest software versions of Cisco IOS and other vendor SSH server and client software:
Buffer overflows or DoS attacks, for example, continuous unauthorized login attempts.
Transmitting invalid fields. Incorrect packet lengths or invalid string lengths in the IP, TCP, or data fields of the packet to the router or switch can yield unexpected behavior such as a software crash or unauthorized access (DoS attack).
Transmitting invalid padding and padding length of IP frame. This can yield unexpected behavior such as a software crash or unauthorized access (DoS attack).
Attempting to transmit anomalous algorithms to network device.
Software or hardware defect that can yield anomalous behavior.
Weak usernames and passwords that are easily broken. Such passwords include the user’s default username and simple passwords such as the user’s birthday without the use of special characters.
Key analysis by intercepting large number of frames.
Configuring DNS on Catalyst switches is useful for resolving domain names to IP addresses for management and troubleshooting purposes. To configure Cisco IOS–based switches for DNS, use the following commands:
ip name-server address [address2...address6] ip domain-name domain ip domain-lookup
The ip name-server address command configures up to eight domain servers to query for DNS resolution. The ip domain-name domain command specifies the domain on which the switch resides, and the ip domain-lookup command enables DNS resolution.
To configure Cisco CatOS–based switches for DNS, use the following commands:
set ip dns server ip-addr [primary] set ip dns domain name set ip dns {enable | disable}
The set ip dns server ip-addr command adds DNS servers to configured lists of servers. The Catalyst switch queries the primary DNS server before moving to other DNS servers in the list if there is no response to the DNS query. The set ip dns enable command enables the switch to perform DNS queries.
Examples 3-16 and 3-17 illustrate configuring Catalyst Cisco IOS–based switches and Cisco CatOS–based switches for DNS functionality, respectively.
Example 3-17. Configuring DNS Lookup on a Cisco CatOS–Based Switch
Console> (enable) set ip dns server 10.4.1.209 10.4.1.209 added to DNS server table as primary server. Console> (enable) set ip dns server 10.4.1.210 10.4.1.210 added to DNS server table as backup server. Console> (enable) set ip dns domain cisco.com Default DNS domain name set to cisco.com Console> (enable) set ip dns enable DNS is enabled
System logging is another useful tool to manage Catalyst switches. By default, Catalyst switches log critical information to a local buffer that is configurable in size. In addition, Catalyst switches support various logging levels, from emergency-level settings to debugging-level settings of various features and components, such as the Cisco Discovery Protocol (CDP) and the IEEE 802.1D Spanning Tree Protocol (STP). Generally, it is advisable to log all messages up to the critical status to a syslog server. Using a syslog server centralizes monitoring of multiple Catalyst switches in the enterprise.
For more information about syslog levels, facilities, and components, refer to the technical documentation for the respective Catalyst switch on Cisco.com. Recommended practice is to configure all Catalyst switches to log to syslog servers as part of their initial configuration.
To configure a Cisco IOS–based switch for system logging to a syslog server, use the following command:
logging ip-address
To configure a Cisco CatOS–based switch for system logging to a syslog server, use the following commands:
set logging server ipaddress set logging server {enable | disable}
Examples 3-18 and 3-19 illustrate the configuration of Catalyst Cisco IOS–based switches and Cisco CatOS–based switches for DNS functionality, respectively.
For information about different logging levels of Catalyst features and system capabilities, consult Cisco.com.
Simple Network Management Protocol (SNMP) is a powerful and standards-based protocol by which to manage network devices. Example use of SNMP includes the following:
Configuration and configuration file management
Interface link up and down tracking
Feature monitoring, such as HSRP tracking
Interface statistics and performance measuring
In small networks, SNMP is mostly useful for monitoring; however, in large enterprise networks, SNMP is useful for configurations as well. Due to the large size of enterprise networks, centralized management and configuration is essential to successful deployments of multilayer switched networks.
All Cisco Catalyst switches support SNMP. A complete discussion of SNMP is outside the scope of the BCMSN; nevertheless, it is important to review the basic configuration needed to allow remote management of Cisco Catalyst switches through SNMP. Applications such as CiscoWorks, HP OpenView, and What’s Up use SNMP to manage, track, monitor, and gather performance data from Cisco network devices.
There are three main versions of SNMP:
Version 1 (RFC 1157)
Version 2c (RFC 1901, 1905, 1906)
Version 3 (RFCs 2273-2275)
Most enterprise networks currently use version 2c with a defined upgrade path to version 3. Version 3 is the only version that supports a high level of security using encryption. Table 3-5 shows the security levels available with SNMP.
Table 3-5. SNMP Security Models and Levels
Model | SNMP Level | Authentication | Encryption | Description |
|---|---|---|---|---|
v1 | noAuthNoPriv | Community String | No | Uses a plaintext community string for authentication. |
v2c | noAuthNoPriv | Community String | No | Uses a plaintext community string for authentication. |
v3 | noAuthNoPriv | Username | No | Uses a username match for authentication. |
v3 | authNoPriv | MD5 or SHA | No | Provides authentication based on the HMAC-MD5 or HMAC-SHA algorithms. |
v3 | authPriv | MD5 or SHA | DES | Provides authentication based on the HMAC-MD5 or HMAC-SHA algorithms. Provides DES 56-bit encryption in addition to authentication based on the CBC-DES (DES-56) standard. |
Recommended practice is to use SNMPv3 with secure authentication and command encryption; however, most enterprise networks have built their management applications around SNMPv2, and it might be some time before enterprise networks fully migrate to SNMPv3. Nevertheless, avoid using the read-only and read-write community strings as public and private, because those strings tend to be the standard default in enterprise networks. In review, SNMPv3 provides enhanced network security through the following features:
Data can be collected securely from SNMP devices without fear of the data being tampered with or corrupted (message integrity).
Encrypting confidential information. For example, SNMP set command packets that change a router’s configuration can be encrypted to prevent the packet contents from being exposed on the network in plaintext.
User authentication is optionally based on encryption algorithms (verifies valid source).
For more information on configuring SNMP with Cisco IOS on Catalyst switches, search the Cisco.com website for SNMP.
To configure Cisco IOS with an SNMPv2 community string, use the following command:
snmp-server community string [view view-name] [ro | rw] [number]
In this command, ro represents read-only and rw represents read-write. string represents the community string. Most network devices are configured with strings public and private for the ro and rw community strings. In terms of security, recommended practice is that these strings be something other than the common public and private strings. Nevertheless, with SNMPv2, these strings are transmitted in clear-text. number represents an optional ACL for restricting access.
Example 3-20 illustrates configuring a Catalyst switch with a public and private community string.
To specify an identification name (ID) for either the local or remote SNMP engine on the router, use the following command in global configuration mode:
snmp-server engineID [local engineid-string] | [remote ip-address udp-port port- number engineid-string]
To configure the recipient of an SNMP trap operation, use the following command in global configuration mode:
snmp-server host host [traps | informs][version {1 | 2c | 3 [auth | noauth | priv]} ] community-string [udp-port port] [notification-type]
Example 3-21 illustrates configuring the SNMP server engine ID and trap destination.
To configure a new SNMP group or a table that maps SNMP users to SNMP views, use the following command in global configuration mode:
snmp-server group [groupname {v1 | v2c | v3 [auth | noauth | priv]}][read readview] [write writeview] [notify notifyview] [access access-list]
To configure a new user to an SNMP group, use the following command in global configuration mode:
snmp-server user username [groupname remote ip-address [udp-port port] {v1 | v2c | v3 [encrypted] [auth {md5 | sha} auth-password [priv des56 priv password]] [access access-list]
Note that the options for the snmp-server user command allow for encrypted username and passwords. In addition, the preceding commands require additional configurations and usually occupy AAA configurations. Refer to the SNMP configuration documentation at Cisco.com for more details. As previously noted, SNMP is outside the scope of the current BCMSN switching examination.
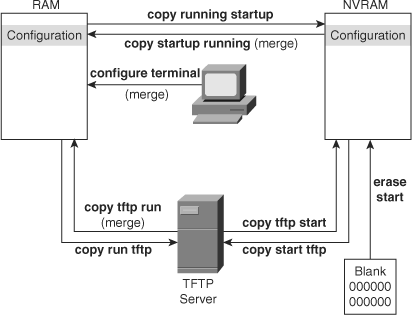
Cisco IOS software and Cisco CatOS software use the copy command to move configurations from one component or device to another, such as RAM, NVRAM, or a TFTP server. In addition to using AutoInstall, the setup utility, or the CLI to load or create a configuration, the copy command allows configurations to exist on servers elsewhere in the network.
The syntax of the copy command requires that the first argument indicate the source (from where the configuration is to be copied), followed by the destination (to where the configuration is to be copied), such as the copy tftp flash command when moving files on the Cisco IOS File System (IFS). For example, the copy running-config tftp command copies the running configuration in RAM to a TFTP server. The command prompts the user for the source filename, destination filename, and TFTP server address.
Furthermore, the copy command can copy the running configuration to NVRAM for nonvolatile storage. Startup-config is the term in Cisco IOS to refer to the configuration in NVRAM, and running-config represents the configuration currently running in RAM. To save a running-config to the startup-config, use the copy running-config startup-config command. This command performs the same operation as the write memory command. Similarly, using the command copy startup-config running-config copies the startup-config to the running-config. Analogous commands exist for copying files between a TFTP server and either NVRAM or RAM as indicated in the “Upgrading Software Versions on Catalyst Switches” section later in this chapter. The erase startup-config and write erase commands delete the saved startup-config in NVRAM. These commands are useful when resetting switches back to factory default.
Cisco CatOS–based switches immediately write configuration changes to NVRAM. There is no concept of running and startup configuration on Cisco CatOS–based switches.
Figure 3-2 illustrates the use of TFTP and Cisco IOS commands to move and store Cisco IOS configuration files in RAM and NVRAM. Example 3-22 illustrates a user saving a switch configuration to NVRAM followed by saving the configuration to a TFTP server on a Cisco IOS–based Catalyst switch.
Example 3-22. Managing Configuration Files on Catalyst Switches
Switch#copy running-config startup-config Destination filename [startup-config]? Building configuration... [OK] Switch#copy startup-config tftp Address or name of remote host []? 10.18.118.100 Destination filename [Switch-confg]? !! 3007 bytes copied in 1.028 secs (2925 bytes/sec)
All currently shipping Catalyst switches, both with Cisco CatOS and Cisco IOS, use the Cisco IFS. The Cisco IFS uses physical, local flash file systems containing memory space to store OS images and configuration files. This memory space size is generally between 16 MB and 2 GB, depending on platform. The flash file system acts similarly to a UNIX file system where files may be added, deleted, renamed, and so on, depending on platform. All Cisco Catalyst switches include an internal Flash file system (referred to as bootflash memory), while several Cisco Catalyst switches include a PCMCIA or Flash Disk slot or slots for adding memory space.
In addition to the physical Flash file systems, the IFS supports using network file systems such as TFTP, remote copy protocol (rcp), and FTP. Furthermore, the IFS supports other endpoints for reading or writing data, including NVRAM, DRAM, ROM, and so on. Example 3-23 displays a user formatting a PCMCIA Flash card, copying an image to it, verifying the image on the Flash card, and then deleting the image.
Example 3-23. Formatting and Copying Images on the IFS in Cisco CatOS
Console> (enable) format slot0: All sectors will be erased, proceed (y/n) [n]? y Enter volume id (up to 31 characters): Formatting sector 1 Format device slot0 completed Console> (enable) dir slot0: No files on device 24772608 bytes available (0 bytes used) Console> (enable) dir bootflash: -#- -length- -----date/time------ name 1 6238120 Nov 26 2002 14:10:11 cat6000-sup2k8.7-4-3.bin 25743320 bytes available (6238248 bytes used) Console> (enable) copy bootflash:cat6000-sup2k8.7-4-3.bin slot0: 24772480 bytes available on device slot0, proceed (y/n) [n]? y CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC ! Output omitted for brevity File has been copied successfully. Console> (enable) dir slot0:: -#- -length- -----date/time------ name 1 6238120 Nov 26 2002 14:10:11 cat6000-sup2k8.7-4-3.bin 25743320 bytes available (6238248 bytes used) Console> (enable) delete slot0:cat6000-sup2k8.7-4-3.bin
Cisco CatOS and Cisco IOS use network file systems to copy OS images and configurations to local file systems. Table 3-6 illustrates the file systems and their associated prefixes for use on Cisco CatOS–based and Cisco IOS–based (Native Mode) Catalyst switches.
Table 3-6. The IFS Prefix Descriptions
Prefix | Description |
|---|---|
bootflash: | Bootflash memory. |
disk0: | ATA Flash disk occupying the first (or only) PCMCIA or SanDisk slot. |
disk1: | ATA Flash disk occupying the second (or only) PCMCIA or SanDisk slot. |
flash: | Flash memory. This prefix is available on all platforms. For platforms that do not have a device named flash:, the prefix flash: is aliased to bootflash: or slot0:. Therefore, you can use the prefix flash: to refer to the main Flash memory storage area on all platforms. |
flh: | Flash load helper log files. |
ftp: | FTP network server. |
nvram: | NVRAM. |
rcp: | Rcp network server. |
scp: | Secure copy protocol server. |
sftp: | Secure FTP server. |
slot0: | First PCMCIA Flash memory card. |
slot1: | Second PCMCIA Flash memory card. |
system: | Contains the system memory, including the running configuration. |
tftp: | TFTP network server. |
Note
As a standard practice, always use secure copy methods such as SFTP and SCP for copying images, because passwords and data that is passed through the network are encrypted.
To determine the size, available space, and contents of the Cisco IFS, use the following command in both Cisco CatOS and Cisco IOS:
show flashExample 3-24 illustrates a user displaying information about the IFS on a Catalyst 2950 and 4500 running Cisco IOS and a Catalyst 6500 running Cisco CatOS, respectively. Note that the Catalyst 4500 does not support the show flash command on the current software version.
Example 3-24. Displaying Information About the IFS on Cisco CatOS and Cisco IOS Switches
! Catalyst 2950 Switch: Switch#show flash Directory of flash:/ 2 -rwx 2664051 Mar 01 1993 00:03:38 c2950-i6q4l2-mz.121-11.EA1.bin 3 -rwx 616 Mar 06 1993 01:45:22 vlan.dat 4 -rwx 2774747 Mar 03 1993 18:35:17 c2950-i6q4l2-mz.121-12c.EA1.bin 22 -rwx 316 Mar 03 1993 20:11:35 env_vars 7 drwx 896 Mar 03 1993 18:36:23 html 19 -rwx 110 Mar 03 1993 18:37:12 info 20 -rwx 110 Mar 03 1993 18:37:12 info.ver 7741440 bytes total (571392 bytes free) ___________________________________________________________________________________ ! Catalyst 4500 Switch running Cisco IOS Switch#show bootflash: -#- ED ----type---- --crc--- -seek-- nlen -length- -----date/time------ name 1 .. config 76481B10 12B1018 15 56610 Jan 31 2000 22:08:56 Backup 2 .. image 40A9D879 2E07B90 28 8150708 Aug 18 2000 15:39:37 cat4000-is- mz.121-12c.EW.bin 13599856 bytes available (47741840 bytes used) ___________________________________________________________________________________ ! Catalyst 6500 Switch running Cisco CatOS: Console> (enable) show flash -#- ED --type-- --crc--- -seek-- nlen -length- -----date/time------ name 1 .. ffffffff f61a1629 673028 24 6238120 Nov 26 2002 14:10:11 cat6000-sup2k8.7- 4-3.bin 25743320 bytes available (6238248 bytes used)
The name of the Cisco IOS or Cisco CatOS image indicates the appropriate platform and version. For the Cisco IOS images, the filename contains multiple parts specifying platform, software release number, features, and type. For example, the filename c2950-i6q412-mz.121-11.EA1.bin contains this information:
c2950—. Identifies the platform on which the image runs.
i6q412—. Identifies the special capabilities of the image file. A letter or series of letters identifies the features supported in that image. In the case of the 2950, two software versions exist: a standard version and an enhanced version with additional features.
mz—. Specifies where the image runs and whether the file is compressed. In this example, mz indicates that the image runs from RAM and is zip-compressed.
12.1(11)EA1—. Indicates the version number.
.bin—. Indicates the file extension. (In this example, .bin indicates that this is a binary executable file.)
The Cisco IOS software naming conventions, field meanings, image content, and other details are subject to change. For the most updated list of Cisco IOS software naming conventions, consult the following document on Cisco.com:
“White Paper: Cisco IOS(R) Reference Guide”
Cisco IOS (hybrid mode) and Cisco CatOS use unique naming conventions to specify software versions. Because of the different models of Supervisor Engines available, unique naming conventions are necessary to ensure that a switch is using the correct image.
In the case of Cisco CatOS, software images for the Catalyst 6500 use the prefixes in Table 3-7 to indicate the applicable Supervisor Engine.
Table 3-7. Cisco CatOS Image Name to Supervisor Engine Mapping
Image Demarcation | Example | Supervisor Engine |
|---|---|---|
cat6000-sup.<features>.<version>.bin | cat6000-supcv.6-4-4.bin | Supervisor Engine I |
cat6000-sup2.<features>.<version>.bin | cat6000-sup2k8.7-6-1.bin | Supervisor Engine II |
cat6000-sup720.<features>.<version>.bin | cat6000-sup720cvk8.8-1-2.bin | Supervisor 720 |
The cv prefix indicates CiscoView ADP flash image bundling, and the k8 prefix indicates basic encryption support, whereas k9 indicates SSH server support. The corresponding Cisco IOS image running on the MSFC for Catalyst 6500 Supervisors uses an image file with a c6msfc prefix.
In the case of Cisco IOS, software images for the Catalyst 6500 use the prefixes in Table 3-8 to indicate the applicable Supervisor Engine.
Table 3-8. Cisco IOS Image Name to Supervisor Engine Mapping
Image Demarcation | Example | Supervisor Engine |
|---|---|---|
c6sup.<version>.bin | cat6000-sup.6-1-1.bin | Supervisor Engine I with MSFC |
c6sup11.<version> | c6sup11-js-mz.121-19.E | Supervisor Engine I with MSFC (replaces c6sup for clarity) |
c6sup12.<version> | c6sup12-jsv-mz.121-19.E | Supervisor Engine I with MSFC2 |
c6sup22.<version> | c6sup22-jo3sv-mz.121-19.E | Supervisor Engine II with MSFC2 |
s72033.<version>.bin | s72033-psv-mz.122-14.SX.bin | Supervisor Engine 720 with PFC3 and MSFC3 |
In summary, the following Cisco IOS prefixes indicate the use of the following hardware:
c6sup (original name for Integrated Cisco IOS image)—. For use with the Supervisor Engine I with an MSFC1
c6sup11—. For use with the Supervisor Engine I with an MSFC1
c6sup12—. For use with the Supervisor Engine I with an MSFC2
c6sup22—. For use with the Supervisor Engine II with an MSFC2
s72033—. For use with the Supervisor Engine 720 with an MSFC3 and PFC3
Upgrading software images on current-generation Catalyst switches is a straightforward process of loading a new image on the IFS and configuring the switch to load the new image on the next reload. When deleting the existing flash image, take extreme care not to reload the switch while copying a new image. If the switch loads without a proper image, a recovery mechanism such as Xmodem is required to load a bootable image.
The most common method of copying an image to a Catalyst switch is via TFTP using the following copy command for both Cisco IOS–based and Cisco CatOS–based Catalyst switches:
copy tftp flashThe copy tftp flash command asks the user for additional information when executed. This additional information includes the source filename, destination filename, and TFTP server IP address. After you confirm these entries, the procedure may prompt you to erase the Flash. Erasing Flash memory makes room for the new image. You should perform this task if there is not sufficient Flash memory for more than one Cisco IOS image. Generally, all current Cisco Catalyst switches contain enough memory in Flash for at least two software images.
Alternatively, you can back up the Catalyst switches’ images and configuration to a TFTP server. To copy existing images in Flash to a TFTP server, use the following command:
copy flash tftpIn summary, the following steps are necessary to load a new image on a Catalyst switch:
Copy the appropriate software image file to the appropriate TFTP directory on the workstation or server.
Log in to the switch through the console port or via a Telnet or SSH session.
Download the software image from the TFTP server using the copy tftp flash command. When prompted, enter the IP address or host name of the TFTP server and the name of the file to download. On those platforms that support the Flash file system, a prompt appears for the Flash device to which to copy the file and the destination filename.
The switch downloads the image file from the TFTP server to the respective file system after you finish entering the necessary prompts for the copy tftp flash command.
After the image completes the download process, modify the BOOT environment variable on the switch using the boot system flash device:filename command for Cisco IOS–based switches or the set boot system flash device:filename prepend command for Cisco CatOS–based switches. The purpose of modifying the BOOT environment is to ensure that the switch boots the correct image on the next reload.
For Cisco IOS–based switches, save the configuration using the copy running-config startup-config command to retain the boot variable configuration changes.
Reset the switch using the reload command on a Cisco IOS–based switch or the reset system command for Cisco CatOS–based switches. Any open Telnet or SSH sessions disconnect during switch reload.
When the switch reboots, enter the show version command to verify the version of software running on the switch.
Note
When you are using Telnet or SSH to access the switch during an upgrade procedure, the current Telnet or SSH session disconnects when power-cycling the switch to run the new software.
TFTP is not a secure protocol method to transfer images. Moreover, most TFTP server software does not support files larger than 16 MB or 24 MB, which are found with Cisco IOS 12.2 and 12.3 images for Catalyst switches. As a result, you should not attempt to copy images using TFTP over congested or low-speed interfaces. Opt for protocols such as SFTP, available on newer versions of Cisco CatOS and Cisco IOS, for more resilient file copies.
Example 3-25 illustrates a user backing up the existing Cisco IOS image to a TFTP server and copying a new image to the switch. In this example, the user configures the switch to load the correct software image by manipulating the boot parameters using the boot system command. The switch used in this example is a Catalyst 3550 switch running Cisco IOS software.
Example 3-25. User Upgrading Cisco IOS Image
Switch#copy flash tftp Source filename [/c3550-i5q3l2-mz.121-12c.EA1/c3550-i5q3l2-mz.121-12c.EA1]? c3550- i5q3l2-mz.121-12c.EA1.bin Address or name of remote host []? 10.1.118.100 Destination filename [c3550-i5q3l2-mz.121-12c.EA1.bin]? c3550-i5q3l2-mz.121- 12c.EA1.bin !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! ! Output omitted for brevity !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! 3823261 bytes copied in 11.640 secs (328459 bytes/sec) Switch#copy tftp flash Address or name of remote host [10.1.118.100]? 10.1.118.100 Source filename [c3550-i5q3l2-mz.121-13.EA1a.bin]? c3550-i5q3l2-mz.121-13.EA1a.bin Destination filename [c3550-i5q3l2-mz.121-13.EA1a.bin]? c3550-i5q3l2-mz.121- 13.EA1a.bin Accessing tftp://10.1.118.100/c3550-i5q3l2-mz.121-13.EA1a.bin... Loading c3550-i5q3l2-mz.121-13.EA1a.bin from 10.1.118.100 (via FastEthernet0/1): !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! ! Output omitted for brevity !!!!!!!!!!!!!!!!!!!!!!!! [OK - 3993235 bytes] 3993235 bytes copied in 94.716 secs (42160 bytes/sec) Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#boot system flash:c3550-i5q3l2-mz.121-13.EA1a.bin Switch(config)#end Switch#copy run start Destination filename [startup-config]? Building configuration... [OK] Switch#reload Proceed with reload? [confirm] 00:32:35: %SYS-5-RELOAD: Reload requestedBase ethernet MAC Address: 00:0b:5f:cf:6f:80 Xmodem file system is available. The password-recovery mechanism is enabled. Initializing Flash... flashfs[0]: 34 files, 5 directories flashfs[0]: 0 orphaned files, 0 orphaned directories flashfs[0]: Total bytes: 15998976 flashfs[0]: Bytes used: 11586048 flashfs[0]: Bytes available: 4412928 flashfs[0]: flashfs fsck took 18 seconds. ...done Initializing Flash. Boot Sector Filesystem (bs:) installed, fsid: 3 Loading "flash:c3550-i5q3l2-mz.121-13.EA1a.bin"... ############################################################################################## ############################################################################################## ############################################################################################## ############################################################################################## ####################################################### ####### File "flash:c3550-i5q3l2-mz.121-13.EA1a.bin" uncompressed and installed, entry point: 0x3000 executing... (text deleted) 00:00:36: %SYS-5-RESTART: System restarted -- Cisco Internetwork Operating System Software IOS (tm) C3550 Software (C3550-I5Q3L2-M), Version 12.1(13)EA1a, RELEASE SOFTWARE (fc1) Copyright (c) 1986-2003 by cisco Systems, Inc. Compiled Tue 25-Mar-03 23:42 by yenanh
Note
The Catalyst 3550 includes an archive and install software feature to ease installation of the software image and web interface files. See the software release notes for more details.
Note
The exclamation point (!) or pound sign (#) indicates the successful transfer of a UDP segment of the complete software image file.
For Cisco CatOS–based switches, follow the same procedure as upgrading Cisco IOS–based switches, except use the set boot system flash device:filename prepend command to manipulate the system image to boot.
Other modes of copying images to Flash exist, such as FTP, SFTP, and Xmodem. In general, only use the serial protocols such as Xmodem for disaster-recovery processes, such as when all the images have been accidentally removed from Flash. Example 3-26 illustrates the available transport methods on a Catalyst 3550 switch running Cisco IOS 12.1.13.EA1.
Example 3-26. Available Image Transport Methods
Switch#copy ?
/erase Erase destination file system.
bs: Copy from bs: file system
flash: Copy from flash: file system
ftp: Copy from ftp: file system
null: Copy from null: file system
nvram: Copy from nvram: file system
rcp: Copy from rcp: file system
running-config Copy from current system configuration
startup-config Copy from startup configuration
system: Copy from system: file system
tftp: Copy from tftp: file system
vb: Copy from vb: file system
xmodem: Copy from xmodem: file system
ymodem: Copy from ymodem: file system
zflash: Copy from zflash: file systemMost current Catalyst switches use the Cisco IOS operating system instead of the traditional Cisco CatOS Software. For the Catalyst 6500 family of switches with an MSFC that runs either Cisco Native IOS or Cisco CatOS, the option exists to convert switches currently running Cisco CatOS to Cisco IOS. The exact commands that are used to convert from Cisco CatOS to Cisco IOS depend on the Multilayer Feature Switch Card (MFSC) model and configuration specifics that are used on the switch. Check the reference documentation for the hardware in question for specific instructions on configuration migrations.
The following steps illustrate, at a high-level overview, the steps necessary to convert Cisco CatOS to Cisco IOS:
Back up the configuration files by using the copy command.
Obtain the appropriate Cisco IOS software image.
Boot to ROMMON by setting the configuration register and rebooting. (ROMMON is a ROM-based program used by Catalyst switches for power-up and recovery from fatal exception errors. In addition, switches enter the ROMMON mode if there is no valid configuration file, if the NVRAM contents are corrupted, or by specific settings of the configuration-register.)
Compare the current running configurations to the backup copy of the configuration from Step 1.
Change the boot variables so that the switch will boot Cisco IOS the next time it restarts.
Reload the original configuration from the backup copy from Step 1.
Make any necessary manual configuration changes.
For specific instructions about how to convert the Catalyst 6500 family of switches from Cisco CatOS to Cisco IOS, refer to the following locations on the Cisco Technical Assistance Center (TAC) website. (These locations require you to be a registered Cisco.com user.)
In addition, Cisco.com provides useful tools to aid in converting from Cisco CatOS to Cisco IOS software and configurations on a Catalyst 6500 switch for registered Cisco.com users. Refer to the following documents, respectively, for information about the tools:
Basic troubleshooting of Catalyst switches involves the use of show and debug commands. The show commands provide state information, and the debug commands provide real-time information about specific events. The use of show commands is always a first step in troubleshooting anomalies. In addition to show and debug commands, logging information with time stamps is useful in monitoring and debugging Catalyst switches. This section discusses these topics in the order listed in the following outline:
show and debug commands
Configurations and commands useful when troubleshooting
The impact of debug commands and recommended use
Cisco IOS show and debug commands are important tools for troubleshooting network anomalies, connectivity problems, performance issues, and other anomalous behavior. The show commands provide a static collection of information about the status of a network device, neighboring switches and routers, and network performance. Use show commands when gathering facts for isolating problems in an enterprise network, including problems with interfaces, nodes, media, servers, clients, or applications. An example of using show commands for troubleshooting is using the show interface command to gather error statistics such as the number of Layer 2 cyclic redundancy check (CRC) frames received from a directly attached device.
The debug commands provide a flow of information about the traffic being seen (or not seen) on an interface, error messages generated by nodes on the network, protocol-specific diagnostic packets, and other useful state troubleshooting data. Use debug commands when you need to see process operations on the router or network to determine whether events or packets are working properly. One such example is debugging Cisco Express Forwarding (CEF) switching to verify behavior of packet flows.
Use debug commands only to isolate problems, not to monitor network or switch operation. Generally, it is advisable to use debug commands only under the supervisor of a TAC engineer because debugs may result in high CPU overhead. The following list summarizes important notes about the use of debug commands:
Be aware that the debug commands may generate too much data that is of little use for a specific problem. You need to have knowledge of the protocol(s) being debugged to properly interpret the debug outputs.
debug commands may generate high CPU overhead that may disrupt network device operation; therefore, only use debug commands when you are looking for specific types of traffic or solutions to problems and have narrowed problems to a likely subset of causes.
When using the debug troubleshooting tools, be aware that output formats vary with each protocol. Some protocols generate a single line of output per packet, whereas others generate multiple lines of output per packet.
Some debug commands generate large amounts of output; others generate only occasional output. Some generate lines of text, and others generate information in field format.
debug commands can obtain information about network traffic and router or switch status. Use these commands with great care.
Time stamping of debug and log messages is essential to proper debugging. Knowing time frames and exact instances when events occur is critical to troubleshooting performance issues. To configure Cisco IOS–based switches to time stamp debug and log messages, use the following Cisco IOS global configuration commands:
service timestamps debug {datetime | uptime} [{msec} {localtime} {show-timezone}] service timestamps log {datetime | uptime} [{msec} {localtime} {show-timezone}]
Other parameters exist for configuring debug and logging time stamps; the commands listed with the msec and localtime options add millisecond time stamps using the switch’s current time to all messages. These parameters are found to be the most useful when troubleshooting from the CLI. For Cisco CatOS–based switches, use the following command to enable and disable logging:
set logging timestamp [enable | disable]
On Cisco CatOS–based switches, time-stamp logging is a default configuration.
Noting CPU load before enabling debugging is necessary to prevent high CPU conditions. To determine the current CPU load before enabling debug commands, use the following Cisco IOS command:
show processesThis command reveals the current processes that are running and the total CPU utilization. It is not advisable to enable debugging when the CPU utilization is over 70 percent; doing so may further increase CPU utilization and cause anomalous behavior on the switch. Recall that current Catalyst switches use hardware switching for packet forwarding, and CPU utilization is not a direct correlation of packet performance.
Two other useful commands when enabling and disabling debugs are the no debug all and undebug all commands. These commands are useful for immediately disabling all debugs to prevent further CPU utilization.
Generally, if an abnormal situation results in the use of debugs, temporarily trading off switching and CPU efficiency for the opportunity to rapidly diagnose and correct the problem may be ideal. To effectively use debugging tools, determine the following information:
The impact that the troubleshooting tool has on router or switch performance
The most selective and focused use of the diagnostic tool
How to minimize the impact of your troubleshooting on other processes that are competing for resources on the network device
How to stop the troubleshooting tool when you are finished diagnosing so that the router or switch can resume its most efficient switching
Using debugs to troubleshoot a lab network that lacks end-user application traffic is different from troubleshooting in a production network. Without proper precautions, the impact of broadly focused debug commands could worsen the issue. With the proper, selective, and temporary use of these tools, though, debugs can obtain potentially useful information without needing a protocol analyzer or other third-party tool.
Some considerations for using debug commands are as follows:
You are highly advised to use debug commands only during periods of lower network traffic and fewer users. Debugging during these periods reduces the effect these commands have on other users on the system.
Gather the information from the debug commands in a timely manner and immediately disable the debug command (and any other related configuration settings, if any) to enable the router or switch to resume its normal behavior. Then, using the information collected during the debug window, continue problem solving and create a better-targeted action plan for additional debug commands if necessary.
All debug commands are entered in privileged EXEC mode, and most debug commands do not require parameters. Nevertheless, debug parameters are useful in isolating debug information to a specific interface or feature.
Note
Do not use the debug all command, because this debug can cause a system crash due to the overwhelming number of processes being debugged.
To list and see a brief description of all the debugging command options, enter the debug ? command in privileged EXEC mode.
By default, the network server sends the output from debug commands and system error messages to the console. Monitoring debugging output by using a virtual terminal connection is the preferable debugging method to the console port. However, in certain situations, virtual terminal access may be affected by the issue you are trying to debug. To redirect debugging output, use the logging command options within configuration mode. Possible destinations include the console, virtual terminals, internal buffer, and UNIX hosts running a syslog server. The syslog format is compatible with 4.3 Berkeley Standard Distribution (BSD) UNIX and its derivatives. Note that by default, virtual terminal sessions do not display debug or logging output; enter the terminal monitor EXEC command to enable display of logging and debug output to the current virtual terminal session.
For additional information about troubleshooting using protocol analyzers and other debugging and baselining tips, see Chapter 17, “Performance and Connectivity Troubleshooting Tools for Multilayer Switches.”
This section discusses several basic and common initial configuration issues that arise when configuring a Catalyst switch for the first time. Specifically, the section covers the following issues:
What to do when you are unable to connect to a Cisco Catalyst switch via the console port
What to do when you are unable to establish IP connectivity to or from the switch using Telnet or SSH
If you are unable to connect to the switch via the console port, perform the following troubleshooting steps. The order of the steps is not significant:
Verify that you are using the correct type of cable: straight-through or rollover. (Refer to the hardware documentation for your switch Supervisor Engine to find out which cable to use.) Furthermore, several models of Catalyst switches have a front panel selectable toggle switch for selecting either console connectivity via straight-through or rollover cable. Select the opposite setting, and determine whether console connectivity is working.
Make sure the terminal configuration matches the switch console port configuration. The Cisco default console port settings are 9600 baud, 8 data bits, no parity, 1 stop bit for any current Catalyst switch.
Make sure the cable pinouts for the terminal serial port are correct for your Catalyst Supervisor Engine or fixed-port density Catalyst switch. (Refer to the hardware documentation for your switch Supervisor Engine.)
Attempt to make console connectivity via more than one workstation or terminal server to rule out the possibility that the workstation or terminal server is contributing to the console connectivity problem.
Check and verify whether the Catalyst switch is receiving sufficient power and airflow.
Locate the front panel status LINK LEDs and note any light illumination. Check the product documentation for an explanation of these indicators because they may indicate a hardware fault or other state that is preventing console access.
Occasionally, the console speed of a Cisco router, switch, or other network device might be set to 38400 bps for troubleshooting purposes. If all other attempts to connect to the console port have failed, attempt to establish a connection through the console port with a serial speed of 38400 bps.
If you are unable to establish connectivity to or from a switch using Telnet or SSH, perform the following troubleshooting steps. The order of these steps is significant:
Make sure the LINK LED for the port connecting the switch to the network and the port connecting the respective workstation is green. In addition, verify that all switch ports connecting switches and workstations from the CLI are in the UP state using the show interface command with Cisco IOS and show port with Cisco CatOS.
Check the cabling and ensure that the port connecting the switch to the network is properly cabled. Switch-to-switch connections typically use crossover cables.
For SC-type or ST-type fiber connections, make sure the transmit (Tx) connectors on each link attach to the receive (Rx) connectors on the other end of the link.
Using the show interface command, make sure the respective management interface (sc0, VLAN, or interface) states are in the UP state and properly configured.
Make sure the IP address, subnet mask, and VLAN membership of the switch interface (sc0, me1, VLAN interface, or Layer 3 interface) are correct using the show interface command.
Verify the default gateway configuration or IP routing configuration by using the show ip route command.
Make sure the host configuration for the IP address, subnet mask, default gateway, speed, and duplex setting used by remote access software (Telnet, SSH or Java) to the switch is correct.
If the host is in the same subnet as the switch interface, verify that the switch interface to which the host connects resides in the same VLAN. Use the show interface and show configuration commands to verify the VLAN settings.
If the host resides in a different subnet than the management IP address, make sure the default gateway on the switch resides in the same subnet as the default gateway router. Use the show ip route command to verify the default gateway settings.
Using the show interface command on Cisco IOS–based switches and the show port command on Cisco CatOS–based switches, make sure the speed and duplex settings on the host and the appropriate switch ports are correct.
Using the show mac address dynamic command on Cisco IOS–based switches and the show cam dynamic command on Cisco CatOS–based switches, make sure the switch is learning the MAC address of the host.
Attempt to establish IP connectivity on the same IP subnet in which the management IP address of the switch resides.
Move the switch and the host to different switch interfaces and retry connecting to the switch over IP.
The following bullets review important BCMSN certification exam preparation points of this chapter. The bullets only briefly highlight the main points of this chapter related to the BCMSN exam and should be used only as supplemental study material. Consult the text of this chapter for additional information regarding these topics:
Always use SSH instead of Telnet for remote access to Cisco devices because of the security risks involved with Telnet transmitting passwords in clear-text and other security issues.
Although more secure than Telnet because of encryption, SSH still has vulnerabilities.
Layer 2–only switches require a default-gateway configuration to reach non-local IP subnets.
Always configure the following features for management and troubleshooting purposes on Cisco routers: privileged passwords, remote access passwords, IP management, timestamps, syslog, NTP, and SNMP.
To copy a file to a Catalyst switch’s bootflash, use the copy tftp bootflash: command.
To copy a file to a Catalyst switch PCMCIA Flash card, use the copy tftp slot0: command.
To copy a file to a Catalyst switch ATA disk (PCMCIA or SanDisk), use the copy tftp disk0: command.
When troubleshooting, use show commands to get state information and debug commands to gather real-time information.
Currently, all shipping Catalyst switches run exclusively Cisco IOS, with the exception of the Catalyst 6500 family of switches. The Catalyst 6500 family of switches still has the option of running either Cisco IOS or Cisco CatOS.
Before loading Cisco IOS onto a Catalyst switch, always check for required features, versions, bug fixes, and memory requirements.
Table 3-9 lists important commands to review for the BCMSN certification exam.
Table 3-9. Commands to Review
Command | Description |
|---|---|
configure terminal | Enters the global configuration mode |
copy running-config bootflash: | Copies the running-configuraton to bootflash |
copy running-config startup-config | Copies the running-configuration to the startup-configuration (i.e., saves the configuration to NVRAM) |
copy running-config tftp: | Copies the running-configuration to a TFTP server |
copy tftp bootflash: | Initiates a macro to copy a software image from a TFTP server to bootflash |
copy tftp disk0: | Initiates a macro to copy a software image from a TFTP server to an ATA disk in disk0 |
copy tftp slot0: | Initiates a macro to copy a software image from a TFTP server to the PCMCIA card in slot0 |
delete flash-device:filename | Deletes an image on the device |
format flash-device:filename | Formats a device for use on the current system; all data on device is deleted during format |
(config-if)#ip address ipaddr subnet-mask | Configures the IP address and subnet mask of an interface |
(config)#ip default-gateway ip-address | Configures a Layer 2-only switch or a Layer 3 switch with IP routing disabled for a default gateway |
no debug all | Immediately disables all enabled debugs |
show arp | Displays the ARP table contents |
show hardware | Displays hardware information (similar to the show version command) |
show interface | Displays all interfaces with statistics |
show ip interface brief | Displays, in brief output, all interfaces on the system with an IP address and state |
show ip route | Displays the IP routing table |
show running-config | Displays the running-configuration |
show version | Displays the software version, uptime and so on. |
squeeze flash-device:filename | Removes deleted files on the device and recovers file system space |
(config)#[no] shutdown | Administratively shuts down an interface |
(config)#[no] switchport | Configures an interface as a Layer 2 interface |
terminal monitor | Configures the virtual terminal to monitor system messages |
All Cisco Catalyst families of switches are moving to supporting only Cisco IOS for new platforms and new feature support. The only Catalyst switch still using Cisco CatOS for new features and products is the Catalyst 6500 family of switches. As a result, consider upgrading and planning for Cisco IOS–based Catalyst switches as appropriate.
The initial configuration of a Catalyst switch involves basic management and IP configuration parameters that ease administration and troubleshooting. These management and IP configuration parameters include clock settings, NTP, DNS, and SSH configurations.
When performing basic troubleshooting, use show commands to gather state information and debug commands to gather real-time information. Note that the debug commands may affect the performance of the router, so you need special consideration when enabling these debug commands on production networks.
Complete this configuration exercise to familiarize yourself with the initial configuration of a Cisco IOS–based Catalyst switch discussed in the chapter.
The resources and equipment required to complete this exercise are as follows:
A Cisco IOS–based Catalyst switch such as a Catalyst 2950, 3550, 3560, 3750, 4500, or 6500
A terminal server or workstation connected directly to the console port of the Catalyst switch
Ethernet connection for IP connectivity
Available IP address for assignment to the management IP address of the switch
IP addresses of DNS and syslog servers
Network connectivity via another switch or router
TFTP server
Workstation capable of Telnet and SSH
The purpose of this exercise is to demonstrate the initial configuration of a Cisco IOS–based Catalyst switch acting as a Layer 2 switch. At the end of this exercise, you will be able to execute the following initial configurations on Cisco IOS–based Catalyst switches:
Connect to Catalyst switch via the console port
Configure the switch for management access via IP
Configure IP services such as DNS, Telnet, and SSH
Upgrade the Cisco IOS to a different software version
The exercise exposes topics (such as VLANs) that are found in later chapters; however, the main purpose of this exercise is to demonstrate initial switch configuration.
Figure 3-3 shows the network layout for this lab exercise.
In this lab exercise, you will use the commands listed in Table 3-10. These commands are in alphabetical order so that you can easily locate the information you need. Refer to this table if you need configuration command assistance during the lab exercise. The table includes only the specific parameters used in the example and not all the available options for the command.
Table 3-10. Command List for Lab Exercise
Command | Description |
|---|---|
archive download-sw /overwrite source-url | Automates software upgrade procedure on Catalyst 2950 and 3550 family of switches |
boot system filesystem:filename | Configures the system boot image |
clock set hh:mm:ss month day year | Configures the clock date and time |
clock summer-time zone recurring [week day month hh:mm week day month hh:mm [offset]] | Configures recurring time adjustments, such as daylight saving time |
clock timezone zone hours-offset | Configures the time zone in offset from UTC |
configure terminal | Enters the configuration mode |
copy running-config startup-config | Copies the running configuration to NVRAM |
copy tftp flash | Executes a procedure to copy a file from a TFTP server to the IFS |
dir flash: | Displays the contents of the IFS |
enable | Enters the privilege mode |
end | Configuration EXEC command to end the configuration mode |
exit | Ends the current configuration mode leaf |
hostname hostname | Configures switch with a descriptive name |
interface FastEthernet | GigabitEthernet interface | Enters an interface configuration mode |
interface vlan vlan-id | Enters the VLAN configuration interface mode |
ip address ip-addr subnet-mask | Configures an IP address and subnet mask |
ip default-gateway ip-addr | Configures a default gateway for switches that do not perform Layer 3 routing |
ip domain-lookup | Enables domain name lookup via DNS |
ip domain-name domain-name | Configures the Internet domain suffix for the switch name |
ip name-server ip-addr | Configures the domain name servers (DNS) |
logging ip-addr | Configures the system that is logging the server destination IP address |
ntp server ip-addr | Configures the NTP server IP address |
no shutdown | Configures an interface in the Administrative UP state |
ping ip-addr | Sends ICMP echoes to a specific destination |
reload | Soft reboots the switch |
show clock | Displays the current time and date |
show ntp associations | Displays the NTP associations |
show version | Displays the running software version, and so on. |
switchport access vlan vlan-id | Configures an interface for a specific VLAN ID |
transport input | Configures the virtual terminal for allowable protocols |
vlan vlan-id | Adds or removes a VLAN ID in the VLAN database |
write erase | Erases the startup-config |
Connect the Catalyst switch to a terminal server or directly to a workstation’s serial port for out-of-band connectivity.
Verify the serial port configuration for out-of-band access.
Using the terminal server or PC from Step 1, verify connectivity to the console port of the switch. If this is an initial install of a Catalyst switch, the prompt will indicate Switch> or a prompt asking to enter initial configuration dialog.
IOS (tm) C3550 Software (C3550-I5K2L2Q3-M), Version 12.1(13)EA1a, RELEASE SOFTWARE (fc1) Copyright (c) 1986-2003 by cisco Systems, Inc. Compiled Tue 25-Mar-03 23:56 by yenanh 00:00:42: %LINK-3-UPDOWN: Interface FastEthernet0/1, changed state to up 00:00:43: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/1, changed state to up 00:01:14: %LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan1, changed state to up Would you like to enter the initial configuration dialog? [yes/no]: n Press RETURN to get started! Switch>Note
If previous configuration parameters exist on the Catalyst switch, issue the erase start command to restore the configuration back to the default. Next, after issuing the write erase command, issue the reload command and answer no to the prompt for saving the configuration to reload the switch with the default configuration.
Some versions of Cisco IOS software store VLAN information in a vlan.dat file in bootflash. Simply delete this file to delete the VLAN configuration.
Configure the system switch name using the global configuration command hostname hostname.
Switch>enable Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#hostname Fl1Rm226 Fl1Rm226(config)#
Using an available IP address, configure the switch with an IP address in the appropriate VLAN.
Fl1Rm226(config)#vlan 1 Fl1Rm226(config-vlan)#exit Fl1Rm226(config)#interface vlan 1 Fl1Rm226(config-if)#ip address 10.1.118.103 255.255.255.0 Fl1Rm226(config-if)#no shutdown Fl1Rm226(config-if)#exit Fl1Rm226(config)#interface FastEthernet0/1 Fl1Rm226(config-if)#switchport access vlan 1 Fl1Rm226(config-if)#no shutdown Fl1Rm226(config-if)#exit
Configure the switch for the appropriate default gateway for the configured IP subnet.
Fl1Rm226(config)#ip default-gateway 10.1.118.1 Fl1Rm226(config)#exit
Verify IP connectivity using the ping command.
Fl1Rm226#ping 10.1.118.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.118.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms Fl1Rm226#ping 10.1.116.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to ping 10.1.116.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/4 ms
Configure the switch for DNS lookup.
Fl1Rm226(config)#ip name-server 10.1.1.200 10.1.1.201 Fl1Rm226(config)#ip domain-lookup Fl1Rm226(config)#exit
Verify DNS operation using the ping command.
Fl1Rm226#ping www.cisco.com Translating "www.cisco.com"...domain server (10.1.1.200) [OK] Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.1.1.200, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 60/60/64 ms
Configure the enable password and virtual terminal password.
Fl1Rm226#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Fl1Rm226(config)#enable password cisco Fl1Rm226(config)#line vty 0 4 Fl1Rm226(config-line)#password cisco Fl1Rm226(config-line)#exit
Configure local usernames and passwords for SSH sessions.
Fl1Rm226(config)#username cisco password cisco
Enable AAA authentication for SSH connectivity.
Fl1Rm226(config)#aaa new-modelConfigure the switch for SSH.
Fl1Rm226(config)#ip domain-name cisco.com Fl1Rm226(config)#crypto key generate rsa The name for the keys will be: Fl1Rm226.cisco.com Choose the size of the key modulus in the range of 360 to 2048 for your General Purpose Keys. Choosing a key modulus greater than 512 may take a few minutes. How many bits in the modulus [512]: 2048 Generating RSA keys ... [OK] 00:56:19: %SSH-5-ENABLED: SSH 1.5 has been enabled
Configure the switch for in-band connectivity via SSH only.
Fl1Rm226(config)#line vty 0 15 Fl1Rm226(config-line)#transport input ssh Fl1Rm226(config-line)#exit Fl1Rm226(config)#exit
Verify that the switch is only accessible via SSH for in-band connectivity.
SUN_Workstation:43> ssh -l cisco 10.1.118.103 [email protected]'s password: cisco Fl1Rm226>exit Connection to 172.18.118.103 closed. SUN_Workstation:44> telnet 10.1.118.103 Trying 10.1.118.103... telnet: Unable to connect to remote host: Connection refused
Set the clock correctly, and configure NTP on the switch to update its time to an NTP server.
Fl1Rm226#clock set 11:22:00 november 6 2003 Fl1Rm226#show clock 11:22:02.051 UTC Fri Jun 6 2003 Fl1Rm226#configure terminal Fl1Rm226(config)#clock timezone EST -5 Fl1Rm226(config)#clock summer-time EST recurring Fl1Rm226(config)#ntp server 10.1.1.202 Fl1Rm226(config)#exit Fl1Rm226#show ntp associations address ref clock st when poll reach delay offset disp *~10.1.1.202 .GPS. 1 253 256 377 5.4 0.09 0.1 * master (synced), # master (unsynced), + selected, - candidate, ~ configured
Configure the switch to log all default messages to a syslog server.
Fl1Rm226(config)#logging 10.1.1.199
Download the latest software version for the switch from Cisco.com.
Following the upgrade instructions for the specific Catalyst switch used for this exercise, upgrade the switch to the latest software version.
Method 1:
Fl1Rm226#copy tftp flash Address or name of remote host []? 10.1.1.21 Source filename []? c3550-i5k2l2q3-mz.121-13.EA1a.bin Destination filename [c3550-i5k2l2q3-mz.121-13.EA1a.bin]? Accessing tftp://10.1.1.21/c3550-i5k2l2q3-mz.121-13.EA1a.bin... Loading c3550-i5k2l2q3-mz.121-13.EA1a.bin from 10.1.1.21 (via Vlan118): !! (text deleted) !!!!!!!!!!!!!!!!!!!!!!!!!! [OK - 4578754 bytes] 4578754 bytes copied in 116.884 secs (39173 bytes/sec) Switch#dir flash: Directory of flash:/ 3 -rwx 1955 Mar 05 1993 23:00:14 config.text 4 -rwx 5 Mar 05 1993 23:00:14 private-config.text 6 -rwx 856 Mar 03 1993 16:23:01 vlan.dat 23 -rwx 0 Mar 04 1993 00:26:17 env_vars 7 -rwx 346 Mar 04 1993 00:26:17 system_env_vars Fl1Rm226#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Fl1Rm226(config)#boot system flash:c3550-i5k2l2q3-mz.121-13.EA1a.bin Fl1Rm226(config)#no boot system flash:c3550-i5q3l2-mz.121-12c.EA1.bin Fl1Rm226(config)#end Fl1Rm226#copy running-config startup-config Fl1Rm226#show boot BOOT path-list: flash:c3550-i5k2l2q3-mz.121-13.EA1a.bin Config file: flash:/config.text Private Config file: flash:/private-config.text Enable Break: no Manual Boot: no HELPER path-list: NVRAM/Config file buffer size: 393216 Fl1Rm226#reload Proceed with reload? [confirm] 01:27:11: %SYS-5-RELOAD: Reload requested (text deleted) 00:00:37: %SYS-5-RESTART: System restarted -- Cisco Internetwork Operating System Software IOS (tm) C3550 Software (C3550-I5K2L2Q3-M), Version 12.1(13)EA1a, RELEASE SOFTWARE (fc1) Copyright (c) 1986-2003 by cisco Systems, Inc. Compiled Tue 25-Mar-03 23:56 by yenanh Fl1Rm226>en Password: cisco Fl1Rm226#show version Cisco Internetwork Operating System Software IOS (tm) C3550 Software (C3550-I5K2L2Q3-M), Version 12.1(13)EA1a, RELEASE SOFTW ARE (fc1) Copyright (c) 1986-2003 by cisco Systems, Inc. Compiled Tue 25-Mar-03 23:56 by yenanh Image text-base: 0x00003000, data-base: 0x008BA914 ROM: Bootstrap program is C3550 boot loader Fl1Rm226 uptime is 4 minutes System returned to ROM by power-on System restarted at 12:42:04 EST Sat Jun 21 2003 System image file is "flash:c3550-i5k2l2q3-mz.121-13.EA1a.bin" (text deleted)
Method 2:
Fl1Rm226#archive download-sw/overwrite tftp://198.30.20.19/c3550- i5q3l2- tar.121-13.EA1.tar (text deleted) Loading c3550-i5k2l2q3-tar.121-13.EA1a.tar from 172.18.118.184 (via Vlan118): ! (text deleted) !!!!!!!!!!!!!!!!!!!!!!! extracting info (261 bytes)! [OK - 6597120 bytes] Image info: Version Suffix: i5k2l2q3-121-13.EA1a Image Name: c3550-i5k2l2q3-mz.121-13.EA1a.bin Version Directory: c3550-i5k2l2q3-mz.121-13.EA1a Ios Image Size: 4580864 Total Image Size: 6596096 Image Feature: LAYER_3 | MIN_DRAM_MEG=64 Image Family: C3550 Extracting files... Loading c3550-i5k2l2q3-tar.121-13.EA1a.tar from 172.18.118.184 (via Vlan118): ! c3550-i5k2l2q3-mz.121-13.EA1a/ (directory) c3550-i5k2l2q3-mz.121-13.EA1a/html/ (directory) extracting c3550-i5k2l2q3-mz.121-13.EA1a/html/homepage.htm (3992 bytes)! (text deleted) extracting c3550-i5k2l2q3-mz.121-13.EA1a/info (261 bytes) extracting info (261 bytes)! extracting info.ver (261 bytes) [OK - 6597120 bytes] New software image installed in flash:c3550-i5k2l2q3-mz.121-13.EA1a Configuring system to use new image...done. Fl1Rm226#reload Proceed with reload? [confirm] 01:27:11: %SYS-5-RELOAD: Reload requested (text deleted) 00:00:37: %SYS-5-RESTART: System restarted -- Cisco Internetwork Operating System Software IOS (tm) C3550 Software (C3550-I5K2L2Q3-M), Version 12.1(13)EA1a, RELEASE SOFTWARE (fc1) Copyright (c) 1986-2003 by cisco Systems, Inc. Compiled Tue 25-Mar-03 23:56 by yenanh Fl1Rm226>en Password: cisco Fl1Rm226#show version Cisco Internetwork Operating System Software IOS (tm) C3550 Software (C3550-I5K2L2Q3-M), Version 12.1(13)EA1a, RELEASE SOFTW ARE (fc1) Copyright (c) 1986-2003 by cisco Systems, Inc. Compiled Tue 25-Mar-03 23:56 by yenanh Image text-base: 0x00003000, data-base: 0x008BA914 ROM: Bootstrap program is C3550 boot loader Fl1Rm226 uptime is 4 minutes System returned to ROM by power-on System restarted at 12:42:04 EST Sat Jun 21 2003 System image file is "flash:c3550-i5k2l2q3-mz.121-13.EA1a.bin" (text deleted)
For multiple-choice questions, there might be more than one correct answer.