This chapter covers the following topics:
Implementing, Configuring, Verifying, and Troubleshooting VLANs, and the Benefits of VLANs in a Multilayer Switched Network
Understanding and Configuring Private VLANs
Implementing, Configuring, Verifying, and Troubleshooting VLAN Trunks in a Multilayer Switched Network
Configuring, Verifying, and Troubleshooting the VLAN Trunking Protocol
Previous chapters have discussed the network architectures that are associated with Cisco multilayer switched networks and the basic configuration of multilayer switches. This and subsequent chapters discuss the features of multilayer switches in detail, along with each feature’s implementation and benefits to the multilayer switched network.
VLANs, trunking, and the VLAN Trunking Protocol (VTP) are significant features of multilayer switched networks, and implementation of these features in multilayer switched networks improves overall network performance, scalability, security, and availability. Cisco Systems, Inc. provides VLAN-capable solutions across its entire suite of internetworking switches and mid-range to high-end routers. VLANs not only solve many of the immediate problems associated with administrative changes, but they also provide for improved scalability, interoperability, and increased dedicated throughput.
A VLAN trunk is a physical point-to-point link that is primarily used to carry frames for multiple VLANs. VLAN trunks are common in any multilayer switched network; therefore, network architects need to understand VLANs to be able to implement and troubleshoot them appropriately.
Furthermore, Cisco switches use VTP to distribute and synchronize information about VLANs that are configured throughout a switched network. VTP reduces the manual configuration that is needed on each switch in the network. In a large switched network, VTP allows enterprises to manage the VLAN implementation consistently.
This chapter discusses VLANs, trunking, VTP, and their inherent advantages within a Cisco multilayer switched network. In brief, this chapter covers the following topics:
In terms of preparing for the CCNP BCMSN switching exam, focus on all the sections in this chapter except the section on VTP version 3. VTP version 3 is a new feature that is not widely deployed or covered on the CCNP BCMSN switching exam.
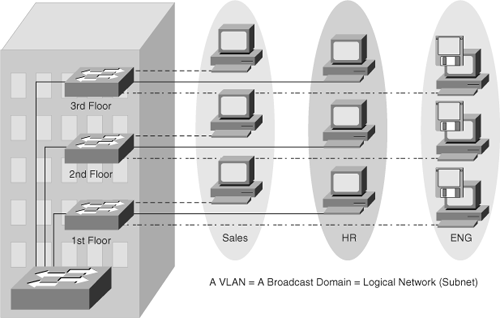
A VLAN is a logical group of end devices with a common set of requirements independent of their physical location, as shown in Figure 4-1, where Sales, HR, and Engineering are three different VLANs spread on all three floors. End devices include end-user workstations, servers, routers, and the like.
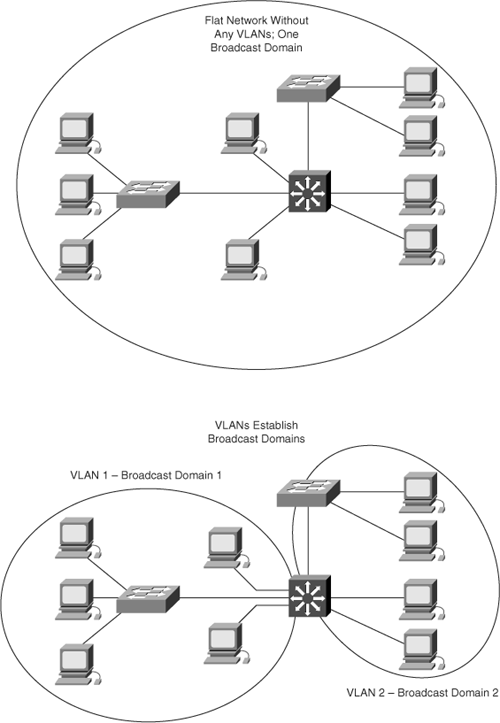
Larger, flat networks generally consist of many end devices where broadcasts and unknown unicast packets are flooded on all ports in the network, as shown in the top portion of Figure 4-2. One advantage of using VLANs is the ability to segment the Layer 2 broadcast domain. All devices in a VLAN are members of the same broadcast domain. If an end device transmits a Layer 2 broadcast, all other members of the VLAN receive the broadcast. Switches filter the broadcast from all the ports or devices that are not part of the same VLAN, as shown in the bottom portion of Figure 4-2.
Although switches do not propagate Layer 2 broadcasts between VLANs, VLANs are slightly different from a physical subnet. A physical subnet consists of devices on a physical cable segment. A logical subnet consists of devices that communicate with each other regardless of their physical location. As a result, VLANs are a type of logical subnet where interconnectivity of end devices is not directly limited by physical location. Instead, switch configurations limit interconnectivity of VLANs. Furthermore, VLANs may exist anywhere in the switch network. Because a VLAN is a single broadcast domain, a VLAN generally belongs to one IP subnet. To communicate between VLANs, packets need to pass through a router or Layer 3 device.
End-to-end VLANs are VLANs that span throughout the entire network. Local VLANs are VLANs that are local to a specific domain, such as Building Access submodule switches and their respective Building Distribution submodule. An end-to-end VLAN may span several wiring closets or even several buildings. End-to-end VLANs are usually associated with a workgroup, such as a department or project team. For redundancy, end-to-end VLANs need the Spanning Tree Protocol (STP), which is discussed in subsequent chapters. As a result of large spanning-tree topologies and simplified network management and troubleshooting with the use of local VLANs compared to end-to-end VLANs, designs using local VLANS, illustrated in Chapters 1 and 2, are becoming more popular.
Because VLANs are an important aspect of any multilayer switched network, all Cisco Catalyst switches support VLANs. A Catalyst switch implements VLANs by virtually limiting data forwarding to ports within the same VLAN. For example, when a broadcast frame arrives on a switch port, the switch retransmits the frame only to ports that belong to the same VLAN. The implication is that using VLANs on Catalyst switches improves scalability by limiting the transmission of unicast, multicast, and broadcast traffic.
Generally, a port carries traffic only for the single VLAN. For a VLAN to span across multiple switches, Catalyst switches use trunks. A trunk carries traffic for multiple VLANs by using Inter-Switch Link (ISL) encapsulation or IEEE 802.1Q. This chapter discusses trunking in more detail in the “VLAN Trunking” section.
This section continues the discussion of VLAN by explaining the following topics related to the implementation and configuration of VLANs:
Implementing VLANs in multilayer switched networks
Mapping VLANS to a hierarchical network
Static and dynamic VLANs
VLAN ranges
Configuring VLANs
Verifying the VLAN configurations
Troubleshooting VLANs
VLANs are helpful in improving the scalability of multilayer switched networks. The following subsections discuss the benefits and implementation of VLANs in multilayer switched networks.
Implementation of VLANs in multilayer switched networks provides scalability, improved performance, and higher availability. The following list details several benefits inherent to VLANs in multilayer switched networks:
Efficient bandwidth utilization—. VLANs solve the scalability problems found in large, flat networks by dividing the network into smaller broadcast domains or subnets. Furthermore, end devices require the use of routers to route packets across VLANs.
Security—. VLANs provide a basic level of security by allowing segregation of frames that contain sensitive or critical information from unauthorized users on separate VLANs. In addition, VLAN boundaries are marked by a Layer 3 interface where additional security measures, such as access lists, are applicable. In addition, several Catalyst switches support VLAN access lists for Layer 2 application.
Load balancing multiple paths—. Combined with routing, VLANs intelligently determine the best path to a destination and offer the ability to load-balance when multiple paths to a destination exist.
Isolation of failure domains—. One of the most important reasons to implement VLANs is to reduce the impact of network problems. In a flat network, a faulty device, a Layer 2 loop, or a broadcast-intensive application may potentially affect the entire network to the point of a total failure. One of the most effective measures against such network failures is to properly segment the network into VLANs with the use of a router. Using a router with VLANs effectively prevents these types of issues from being propagated from a VLAN to other segments or VLANs while maintaining the ability to route traffic between VLANs.
An end-to-end VLAN spans the entire switched network, while a local VLAN is limited to a single switch or group of Building Access submodule and Building Distribution submodule switches.
A network that is deploying end-to-end VLANs has the following characteristics:
End devices such as workstations are grouped into VLANs regardless of physical location.
When the users and their workstations move around the campus, their VLAN membership typically remains the same.
Each VLAN has a common set of security and resource requirements for all members across the campus.
As enterprises move to centralize their network resources, end-to-end VLANs are becoming more difficult to maintain. As a result, enterprise networks are now creating “local” VLAN boundaries around physical boundaries, such as Building Access submodules, rather than around commonality boundaries, such as organizations or departments. In addition, enterprise networks deploy applications that access many resources outside the local VLAN. These types of applications include storage applications, stock tickers, databases, and intranet web services. Although this design of creating local VLANs results in user traffic crossing a Layer 3 router or multilayer switch to reach network resources, this design still allows the network to provide for a deterministic, secure, and consistent method of transporting data, voice, and video. Nevertheless, the use of local VLANs for user end devices maintains the performance and efficiency advantages of VLANs, including collision and broadcast domain segmentation.
Local VLANs, typically used in the Building Access submodule, are also easier to manage and conceptualize than VLANs spanning different areas of the network. A typical VLAN organization configures the minimum number of VLANs on a single access switch within a wiring closet, rather than having VLANs from multiple departments configured on the same switch. Figure 4-3 shows that every Building Access submodule switch belongs to two VLANs, one for voice and one for data, which terminate at the Building Distribution submodule switches.
The goal of local VLANs is not to extend the VLANs beyond the Building Distribution submodule, as shown in Figure 4-3. Using the local VLAN structure to provide access into the network and to provide Layer 3 connectivity allows users to move from one VLAN to another without involving network administrators when using features such as DHCP. In addition, local VLANs provide users with the same level of performance regardless of their location, because Layer 3 devices also switch and route at wire rate due to hardware-switching.
Troubleshooting local VLANs that are contained within a single area is much easier than troubleshooting a VLAN and modules that span an entire functional area in the end-to-end design. In addition, because STP is configured for redundancy, the switch limits the STP to only the Building Access and Building Distribution submodules.
Static VLANs constitute switch ports that are manually assigned to a particular VLAN, as shown in Figure 4-4. Dynamic VLANs, on the other hand, are VLANs that are assigned based on a source Media Access Control (MAC) address that has been entered into a VLAN Management Policy Server (VMPS).
Static VLAN configurations on switches require a VLAN-management application or the use of the command line to assign a specific switch port to a particular VLAN. Although static VLANs require manual entry changes, they are secure, easy to configure, and straightforward to monitor. This type of VLAN assignment method works well in networks where adds, moves, and changes are rare. As shown in Figure 4-4, with the manual configuration of ports with the proper VLAN, if a person who belongs in the Engineering VLAN on Floor 2 tries to connect to the port configured for the Marketing VLAN, that person will not be able to communicate with the members of the Engineering VLAN (as indicated by the “X”) until the Engineering VLAN uses Layer 3 routing.
Dynamic VLAN configuration is accomplished by using the VMPS. With dynamic VLANs, the switch assigns a VLAN to a host based on information in the MAC address-to-VLAN mapping on the VMPS. When a host moves from a port on one switch in the network to a port on another switch in the network, the switch assigns the new port to the proper VLAN for that host dynamically. The VMPS contains a database that maps the MAC addresses to VLAN assignments. When VMPS is enabled, the switch downloads a MAC address-to-VLAN mapping database from a Trivial File Transfer Protocol (TFTP) server and begins to service client requests. When a frame arrives on a dynamic port at the Catalyst access switch, the Catalyst switch queries the VMPS for the VLAN assignment based on the MAC address of the arriving frame. A dynamic port belongs to only one VLAN at a time. Multiple hosts may be active on a dynamic port only if they all belong to the same VLAN.
However, VMPS requires its own management overhead. Unless adds, moves, and changes create a significant management overhead, do not use VMPS to maintain end-station MAC addresses and custom filtering tables. Nonetheless, enterprises rarely deploy VMPS and opt for IEEE 802.1X as a security access feature instead. Chapter 14, “Securing Your Multilayer Switched Network to Minimize Service Loss and Data Theft,” discusses 802.1X in more detail.
The Catalyst 4000, 5000, and 6500 families of switches running Cisco CatOS support VMPS functionality. In addition, an external server may act as a VMPS. Note, however, that several switches, such as the Cisco Catalyst 2900XL, Catalyst 2950/3550/3560, and Cisco Catalyst 4000 and 4500 families of switches running Cisco IOS, do not support the VMPS functionality, but they do support VMPS client functionality.
This chapter discusses static VLANs in more detail but does not discuss dynamic VLANs any further. To learn more about dynamic VLANs, consult the document “Configuring Dynamic Port VLAN Membership with VMPS” on Cisco.com:
Cisco Catalyst switches support up to 4096 VLANs depending on platform and software version. Table 4-1 illustrates the VLAN division for Cisco Catalyst switches.
Table 4-1. VLAN Ranges
VLAN Ranges | Range | Usage | Propagated via VTP |
|---|---|---|---|
0, 4095 | Reserved | For system use only. You cannot see or use these VLANs. | |
1 | Normal | Cisco default. You can use this VLAN, but you cannot delete it. | Yes |
2–1001 | Normal | For Ethernet VLANs. You can create, use, and delete these VLANs. | Yes |
1002–1005 | Normal | Cisco defaults for FDDI and Token Ring. You cannot delete VLANs 1002–1005. | Yes |
1006–1024 | Reserved | For system use only. You cannot see or use these VLANS. | |
1025–4094 | Extended | For Ethernet VLANs only. | Not supported in VTP versions 1 and 2. The switch must be in VTP transparent mode to configure extended-range VLANS. Only supported in version 3. |
All Cisco Catalyst switches support VLANs. That said, each Cisco Catalyst switch supports a different number of VLANs, with high-end Cisco Catalyst switches supporting as many as 4096 VLANs. Table 4-2 notes the maximum number of VLANs supported by each model of Catalyst switch.
Note
The Catalyst 2950 and 2955 support as many as 64 VLANs with the Standard Software image, and up to 250 VLANs with the Enhanced Software image. Cisco Catalyst switches do not support VLANs 1002 through 1005; these are reserved for Token Ring and FDDI VLANs. Furthermore, the Catalyst 4500 and 6500 families of switches do not support VLANs 1006 through 1024. In addition, several families of switches support more VLANs than the number of Spanning Tree instances. For example, the Cisco Catalyst 2970 supports 1005 VLANs but only 128 Spanning Tree instances. For information on the number of supported Spanning Tree instances, refer to Cisco Product Technical Documentation.
As mentioned in previous chapters, Catalyst switches use either Cisco CatOS or Cisco IOS. This section covers the configuration of VLANs with respect to both Cisco CatOS and Cisco IOS, with emphasis on Cisco IOS.
In Cisco IOS, two methods exist to create VLANs:
Global configuration mode—. A relatively new method to configure VLANs, this mode adds support for configuring extended VLANs not configurable by the VLAN database configuration mode.
VLAN database configuration mode—. Another method to configure VLANs, this mode supports only the configuration of VLANs in normal VLAN range (from 1 to 1005).
To create a new VLAN in global configuration mode, follow these steps:
Example 4-1 shows how to configure a VLAN in global configuration mode.
To configure VLANs in the VLAN database configuration mode, you use the vlan database privileged EXEC command.
Note
The VLAN database command mode is different from other modes because it is session oriented. When you add, delete, or modify VLAN parameters, the switch does not apply the changes until you exit the session by entering the apply or exit command. Use the abort command to not apply the changes made to the VTP database.
To create a new VLAN in VLAN database configuration mode, follow these steps:
Enter VLAN database configuration mode.
Switch#vlan databaseCreate a new VLAN with a particular ID number.
Switch(vlan)#vlan vlan-id
Name the VLAN.
Switch(vlan)#vlan vlan-id name vlan-name
Exit VLAN database configuration mode.
Switch(vlan)#exit
Example 4-2 shows an example of creating a VLAN via the VLAN database configuration mode.
Note
Cisco recommends using global configuration mode to define VLANs. Future Cisco IOS releases for Catalyst switches may not support VLAN database configuration mode because it has been deemed an obsolete method of configuring VLANs.
To delete a VLAN in global configuration mode, follow these steps:
Enter global configuration mode.
Switch#configure terminalDelete the VLAN by referencing its ID number.
Switch(config)#no vlan vlan-id
Exit global configuration mode.
Switch(config)#end
Note
After a VLAN is deleted, the access ports that belong to that VLAN move into the inactive state until the ports are moved to another VLAN. As a security measure, ports in the inactive state do not forward traffic.
Example 4-3 shows deletion of a VLAN in global configuration mode.
To delete an existing VLAN in VLAN database configuration mode, follow these steps:
To assign a switch port to a previously created VLAN, follow these steps:
From global configuration mode, enter the configuration mode for the particular port you want to add to the VLAN.
Switch(config)#interface {FastEthernet | GigabitEthernet} slot/port
Specify the port as an access port.
Switch(config-if)#switchport mode access Switch(config-if)#switchport host
Note
The switchport host command effectively configures a port for a host device such as a workstation or server. This feature is a macro for enabling Spanning Tree PortFast and disabling EtherChanneling on a per-port basis. These features are discussed in Chapters 5–7.
Remove or place the port in a particular VLAN.
Switch(config-if)#[no] switchport access vlan vlan-id
Example 4-4 illustrates configuration of an interface as an access port in VLAN 200.
Example 4-4. Assigning an Access Port to a VLAN
Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#interface FastEthernet 5/6 Switch(config-if)#description PC A Switch(config-if)#switchport Switch(config-if)#switchport host Switch(config-if)#switchport mode access Switch(config-if)#switchport access vlan 200 Switch(configif)#no shutdown Switch(config-if)#end
To configure a VLAN in Cisco CatOS, use the following command:
set vlan vlan-id [vlan-name]
vlan-id represents the VLAN number. The vlan-name is an optional description for the VLAN.
Note
In Cisco CatOS, Cisco Catalyst switches require the configuration of a VTP name or a change of the VTP mode to transparent before new VLANs can be created. This chapter discusses VTP in the “VLAN Trunking Protocol” section.
Example 4-5 shows creation of a VLAN in Cisco CatOS.
To assign ports to a VLAN in Cisco CatOS, use the following command:
set vlan vlan-id [mod/port]
Example 4-6 shows assigning of ports to a VLAN in Cisco CatOS.
To delete VLANs in Cisco CatOS, use the clear vlan command, as shown in Example 4-7.
Example 4-7. Deleting VLANs in Cisco CatOS
Console> (enable) clear vlan 3 This command will deactivate all ports on vlan(s) 3 All ports on normal range vlan(s) 3 will be deactivated in the entire management domain. Do you want to continue(y/n) [n]?y VTP advertisements transmitting temporarily stopped, and will resume after the command finishes. Vlan 3 deleted
To verify the VLAN configuration of a Catalyst switch, use show commands. The show vlan command from privileged EXEC mode displays information about a particular VLAN. Table 4-3 documents the fields that are displayed by the show vlan command.
Table 4-3. show vlan Field Descriptions
Field | Description |
|---|---|
VLAN | VLAN number |
Name | Name, if configured, of the VLAN |
Status | Status of the VLAN (active or suspended) |
Ports | Ports that belong to the VLAN |
Type | Media type of the VLAN |
SAID | Security association ID value for the VLAN |
MTU | Maximum transmission unit size for the VLAN |
Parent | Parent VLAN, if one exists |
RingNo | Ring number for the VLAN, if applicable |
BrdgNo | Bridge number for the VLAN, if applicable |
Stp | Spanning Tree Protocol type used on the VLAN |
BrdgMode | Bridging mode for this VLAN |
Trans1 | Translation bridge 1 |
Trans2 | Translation bridge 2 |
AREHops | Maximum number of hops for All-Routes Explorer frames |
STEHops | Maximum number of hops for Spanning Tree Explorer frames |
Example 4-8 displays information about a VLAN identified by number in Cisco IOS.
Example 4-8. Displaying Information About a VLAN by Number in Cisco IOS
Switch#show id vlan 3
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
3 VLAN0003 active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
3 enet 100003 1500 - - - - - 0 0
------- --------- ----------------- -------------------------------------------Example 4-9 displays information about a VLAN identified by name in Cisco IOS.
Example 4-9. Displaying Information About a VLAN by Name in Cisco IOS
Switch#show vlan name VLAN0003
VLAN Name Status Ports
---- -------------------------------- --------- ---------------------
3 VLAN0003 active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- ------ ------
3 enet 100003 1500 - - - - 0 0To display the current configuration of a particular interface, use the show running-config interface interface_type slot/port command. To display detailed information about a specific switch port, use the show interfaces command. The command show interface interface_type slot/port with the switchport keyword displays not only a switch port’s characteristics but also private VLAN and trunking information. The show-mac address-table interface interface_type slot/port command displays the MAC address table information for the specified interface in specific VLANs.
Example 4-10 displays the configuration of a particular interface.
Example 4-11 displays detailed switch port information as the port VLAN and operation modes.
Example 4-11. Displaying Detailed Switch Port Information
BXB-6500-10:8A#show interfaces FastEthernet 4/1 switchport
Name: Fa4/1
Switchport: Enabled
Administrative Mode: static access
Operational Mode: static access
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 2 (VLAN0002)
Trunking Native Mode VLAN: 1 (default)
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Voice VLAN: none (Inactive)
Appliance trust: noneExample 4-12 displays the MAC address table information for a specific interface in VLAN 1.
Example 4-12. Displaying MAC Address Table Information
Switch#show mac-address-table interface GigabitEthernet 0/1 vlan 1
Mac Address Table
------------------------------------------
Vlan Mac Address Type Ports
---- ----------- ---- -----
1 0008.2199.2bc1 DYNAMIC Gi0/1
Total Mac Addresses for this criterion: 1When troubleshooting problems related to VLANs, always review the following items:
Physical connections
Switch configuration
VLAN configuration
Figure 4-5 shows, at a high level, VLAN problems that may occur on a switch.
The following sections cover several common VLAN issues and the action plan to troubleshoot these issues.
To troubleshoot slow-throughput issues within the same VLAN, perform the following steps:
A point-to-point switch link consists of two ports where the problem may exist on either side of a link. Make sure the speed and duplex settings are consistent on both link partners.
Using show commands, check to see what types of errors exist on the suspected interfaces. Combinations of frame check sequence (FCS) errors, alignment errors, and runts generally point to a duplex mismatch; auto-negotiation is the usual culprit, but it could also be a mismatched manual setting.
Determine which Layer 2 path the packet is taking if there are redundant paths using spanning tree. For additional information on troubleshooting Spanning Tree Protocol (STP), consult Chapter 5, “Understanding and Configuring the 802.1D, 802.1s, and 802.1w Spanning Tree Protocols,” and Chapter 6, “Adding Resiliency to Spanning Tree Using Advanced Features and Troubleshooting STP Issues.”
If you see from the output of the show interface command that the number of collisions is increasing rapidly, the problem may be an oversubscribed half-duplex link, faulty hardware, a bad cable, or a duplex mismatch.
When one device cannot communicate with another device within a VLAN, troubleshoot the problem by doing the following:
Private VLANs (pVLAN) are VLANs that provide isolation between ports within the same VLAN. Cisco introduced pVLANs to provide security, to reduce the number of IP subnets, and to reduce the VLANs’ utilization by isolating traffic between network devices residing in the same VLAN.
Service providers use pVLANs to deploy hosting services and network access where all devices reside in the same subnet but only communicate to a default gateway, backup servers, or another network. Service providers use pVLANs not only as a security feature but also as a method to minimize the use of IP address subnets.
In multilayer switching environments, enterprises generally use pVLANs to prevent network devices that are attached to interfaces or groups of interfaces from communicating between each other, but to allow communication to a default gateway such as a VLAN interface or router or to a particular group of devices. Although the network devices reside in different pVLANs, they use the same IP subnet. In this manner, network devices on the same VLAN can communicate only with the default gateway to reach networks beyond the default gateway or only to a particular group of devices if necessary.
Each pVLAN consists of two supporting VLANs:
A primary VLAN—. The Primary pVLAN is the high-level VLAN of the pVLAN. A primary VLAN can be composed of many secondary VLANs with the secondary VLANs belonging to the same subnet of the primary VLAN.
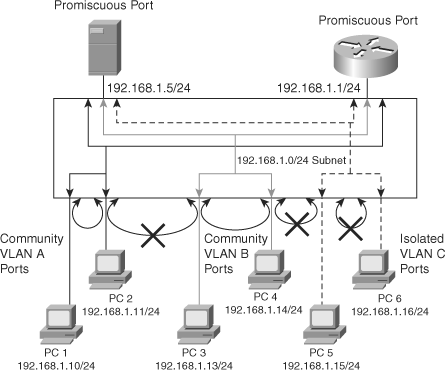
A secondary VLAN—. Every secondary VLAN is a child to a primary VLAN and is mapped to one primary VLAN. End devices are attached to secondary pVLANs. pVLANs define the use of promiscuous ports. All the devices in the pVLAN can communicate with the promiscuous ports. A promiscuous port is only part of one primary VLAN, but each promiscuous port can map to more than one secondary VLAN. Promiscuous ports are generally router ports, backup servers, or VLAN interfaces, as shown in Figure 4-6.
The following are the two types of secondary VLANs:
Community VLANs—. Ports that belong to the community VLAN are able to communicate with the other ports in the same community and promiscuous ports of the pVLAN. In Figure 4-6, PC 1 and PC 2, which belong to community VLAN A, can communicate with each other but (as indicated by the “X”) not with PC 3 and PC 4, which belong to community VLAN B.
Isolated VLANs—. Ports that belong to an isolated VLAN can only communicate with promiscuous ports. Isolated ports cannot communicate with other ports in the same isolated VLAN, as reflected in Figure 4-6, where PC 5 and PC 6, although in the same isolated VLAN, cannot communicate with each other but can communicate with the promiscuous ports. Each pVLAN has only one isolated VLAN.
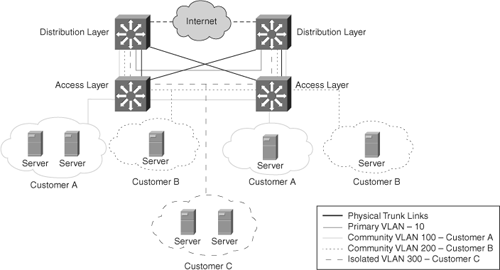
Figure 4-7 illustrates an example of implementing pVLANs in a service-provider environment. Here, a service provider has three customers under one primary VLAN. Customer A belongs to community VLAN 100, Customer B belongs to community VLAN 200, and Customer C belongs to isolated VLAN 300. Despite belonging to the same subnet, Customer A’s, Customer B’s, and Customer C’s network devices cannot communicate with one another. All devices that reside in Customer A’s community VLANs can communicate with one another even though the devices are spread across multiple switches. In addition, all devices that reside in Customer B’s community VLANs can communicate with one another. However, devices in Customer C’s isolated VLAN cannot communicate with one another.
pVLANs can span multiple switches that support the pVLANs’ trunking feature.
The Cisco Catalyst 6500 and 4500 families of switches support all the features of the pVLANs mentioned earlier in this chapter, except that a Cisco 4500 running IOS does not support community VLANs at this time. The low-end Catalyst switches, such as the Catalyst 2950, and the Catalyst 3550/3560 family of switches support only the isolated port feature of pVLANs. These switches refer to isolated ports as pVLAN edge (protected ports). The protected port is a feature that has only local significance to the switch, and there is no isolation between two protected ports located on different switches. A protected port cannot forward traffic (unicast, multicast, or broadcast) to any other port that is also a protected port in the same switch, hence providing isolation.
Note
There are some restrictions and limitations with the configuration of pVLANs. A few limitations and restrictions are as follows:
pVLAN configuration requires VTP to be in transparent mode for VTP version 1 and 2.
You cannot configure Layer 3 VLAN interfaces for secondary VLANs.
Private VLANs are not supported on EtherChannels or span destination ports.
To view the complete list of restrictions and limitations, consult the following documents on the Cisco.com website.
For the Catalyst 4000 family of switches (Configuration Guide):
For the Catalyst 6500 family of switches:
http://www.cisco.com/univercd/cc/td/doc/product/lan/cat6000/122sx/swcg/pvlans.htm
To configure pVLANs in Cisco IOS, perform the following steps:
Enter VLAN global configuration mode to configure the pVLANs.
Switch(config)# vlan pVLAN-id
Configure the VLANs as a type of pVLAN.
Switch(config-vlan)# private-vlan {community | isolated | primary}
Exit the configuration mode.
Switch(config-vlan)# exitEnter the VLAN global configuration mode to configure primary VLAN.
Switch(config)# vlan primary-vlan-id
If it is a primary VLAN, make sure to associate the Layer 2 secondary VLAN to the primary VLAN.
Switch(config-vlan)#private-vlan association {secondary-vlan-list | add secondary-vlan-list | remove secondary-vlan-list}
Select the interface configuration mode for the primary VLAN.
Switch(config)#interface vlan primary-vlan-id
Map secondary VLANs to the Layer 3 VLAN interface of a primary VLAN to allow Layer 3 switching of pVLAN ingress traffic.
Switch(config-if)#private-vlan mapping {secondary-vlan-list | add secondary-vlan-list | remove secondary-vlan-list}
Select the LAN port interface to configure as the pVLAN host or promiscuous port.
Switch(config)#interface type slot/port
Configure the LAN port for Layer 2 operation if the default behavior is Layer 3 operation.
Switch(config-if)#switchportConfigure the Layer 2 port as a pVLAN port either as host or promiscuous port.
Switch(config-if)#switchport mode private-vlan {host | promiscuous}
For access pVLAN ports, associate the community or isolated pVLAN to the pVLAN.
Switch(config-if)#switchport private-vlan host-association primary- vlan-id secondary-vlan-id
For promiscuous ports, configure the interface by mapping the port to the pVLAN.
Switch(config-if)#switchport private-vlan mapping primary-vlan-id {secondary-vlan-list | add secondary-vlan-list | remove secondary-vlan-list}
Exit the interface configuration mode.
Switch(config)#end
Example 4-13 represents the configuration of one community VLAN 200 and one isolated VLAN 300 with a primary VLAN 100. Port 5/1 binds with community VLAN 200, and port 5/2 binds with isolated VLAN 300. The VLAN 100 interface permits routing of secondary VLAN ingress traffic from VLANs 200 and 300.
Example 4-13. Sample Configuration of pVLANs in Cisco IOS
Switch# configure terminal Switch(config)# vlan 100 Switch(config-vlan)# private-vlan primary Switch(config)# vlan 200 Switch(config-vlan)# private-vlan community Switch(config)# vlan 300 Switch(config-vlan)# private-vlan isolated Switch(config)# vlan 100 Switch(config-vlan)# private-vlan association 200,300 Switch(config-vlan)# exit Switch(config)#interface vlan 100 Switch(config-if)#private-vlan mapping add 200,300 Switch(config-if)#exit Switch(config)# interface FastEthernet 5/1 Switch(config-if)# switchport mode private-vlan host Switch(config-if)# switchport private-vlan host-association 100 200 Switch(config)# interface FastEthernet 5/2 Switch(config-if)# switchport mode private-vlan host Switch(config-if)# switchport private-vlan host-association 100 300 Switch(config-if)# end
Example 4-14 illustrates the commands used to verify the configuration of pVLANs in Cisco IOS.
Example 4-14. Verifying pVLAN Configuration in Cisco IOS
Switch# show vlan private-vlan Primary Secondary Type Interfaces ------- --------- ----------------- ------------------------------------------ 100 200 community 100 300 isolated Switch# show interfaces FastEthernet 5/2 switchport Name: Fa5/2 Switchport: Enabled Administrative Mode: private-vlan host Operational Mode: down Administrative Trunking Encapsulation: negotiate Negotiation of Trunking: On Access Mode VLAN: 1 (default) Trunking Native Mode VLAN: 1 (default) Administrative private-vlan host-association: 100 (VLAN0200) 300 (VLAN0300) Administrative private-vlan mapping: none Operational private-vlan: none Trunking VLANs Enabled: ALL Pruning VLANs Enabled: 2-1001 Capture Mode Disabled
To configure pVLANs on the Catalyst 6000 and 4000 families of switches that are running Cisco CatOS, perform the following steps:
Create a primary VLAN.
set vlan vlan-id pvlan-type primary
Create secondary VLANs.
set vlan vlan-id pvlan-type {isolated | community}
Map the primary VLAN to the secondary VLANs.
set pvlan primary-vlan-id {isolated-vlan-id | community-vlan-id}
Bind ports to the primary and secondary pVLANs.
set pvlan primary-vlan-id {isolated-vlan-id | community-vlan-id} mod/ports
Specify which ports will act as promiscuous ports.
set pvlan mapping primary-vlan-id {isolated-vlan-id | community-vlan-id} mod/ports
Verify the pVLAN configuration.
show pvlan [vlan-id] show pvlan mapping
Example 4-15 represents the configuration of one community VLAN 200 and an isolated VLAN 300 associated with the primary VLAN 100. Port 5/1 binds to the community VLAN, port 5/2 binds to the isolated VLAN 300, and port 15/1 is the promiscuous port, which is a Catalyst 6500 Multilayer Switch Feature Card (MSFC) acting as a default gateway. As a result, devices that are connected on ports 5/1 and 5/2 cannot communicate with one another, but they are able to communicate with the promiscuous port, which is the MSFC port. Using the VLAN 100 interface on the MSFC, these ports can communicate with the rest of the network.
Example 4-15. Sample Configuration of pVLANs
Console> (enable) set vlan 100 pvlan-type primary Vlan 100 configuration successful Console> (enable) set vlan 300 pvlan-type isolated Vlan 300 configuration successful Console> (enable) set vlan 200 pvlan-type community Vlan 200 configuration successful Console> (enable) set pvlan 100 200 5/1 Successfully set the following ports to Private Vlan 100,200: 5/1 Console> (enable) set pvlan 100 300 5/2 Successfully set the following ports to Private Vlan 100,300:5/2 Console> (enable) set pvlan mapping 100,200 15/1 Successfully set mapping between 100 and 200 on 15/1 Console> (enable) set pvlan mapping 100 300 15/1 Successfully set mapping between 100 and 300 on 15/1
Example 4-16 illustrates several commands for verifying the configuration of pVLANs in Cisco CatOS.
Example 4-16. Verifying pVLAN Configuration in Cisco CatOS
Console> (enable) show pvlan Primary Secondary Secondary-Type Ports ------- --------- -------------- ------------ 100 300 isolated 5/2 100 200 community 5/1 Console> (enable) show pvlan mapping Port Primary Secondary ----- -------- ---------- 15/1 100 200,300
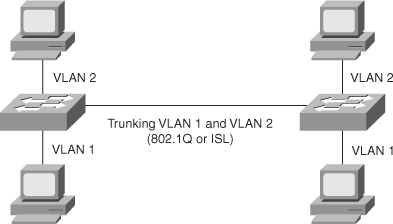
Trunks carry the traffic for multiple VLANs across a single physical link. Trunking is used to extend Layer 2 operations across an entire network, such as end-to-end VLANs, as shown in Figure 4-8. The host in VLAN 2 can communicate with the host in VLAN 2 in the other switch over the single trunk link the same as a host in VLAN 1 can communicate with a host in another switch in VLAN 1.
ISL and IEEE 802.1Q are two protocol-independent methods that Cisco Catalyst switches use to mark frames with a respective VLAN for transmission across the trunk interface. ISL is an encapsulation method for trunking, whereas 802.1Q trunking uses a tagging method. The 802.1Q frames place an additional 4-byte tag into the original packet. Catalyst switches add the tag before transmission on trunk lines and, as a result, compute a new FCS for each egress frame. At the receiving end, the link partners’ trunking interface removes the tag and forwards the packet to the correct destination in the respective VLAN. ISL is a Cisco proprietary protocol, but Cisco licensed its use to many NIC vendors, including Intel and Compaq, for interoperability. Nevertheless, 802.1Q is the standard-based IEEE protocol that is commonly found in network devices regardless of manufacturer. The current generation of low-end Catalyst switches no longer supports ISL. As a result, when deploying multilayer switched networks, opt for trunking using 802.1Q instead of ISL.
The following sections discuss trunking implementation, configuration, and troubleshooting in a multilayer switched network in more detail, including coverage of the following topics:
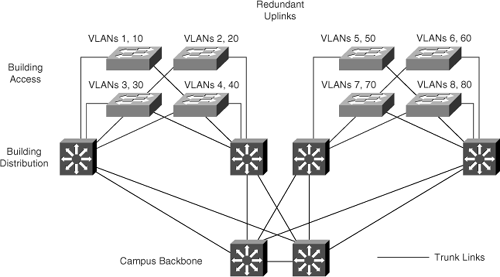
Trunking is an important part of the multilayer switched network. The Campus Infrastructure module is hierarchical. The Building Distribution block is introduced to terminate local VLANs from many Building Access submodule switches using trunk links. Typically, several end-user nodes connect to single Building Access submodule switches with a selected number of access VLANs that provide basic connectivity to network resources, as shown in Figure 4-9.
Cisco design guides recommend using redundant links for each Building Access submodule switch. Redundant links from the Building Distribution submodule switches to the Campus Backbone switches are recommended to provide multihomed redundancy.
This subsection covers the following two trunking protocols in more detail:
Inter-Switch Link (ISL)—. A Cisco proprietary trunking encapsulation
IEEE 802.1Q—. An industry-standard trunking method
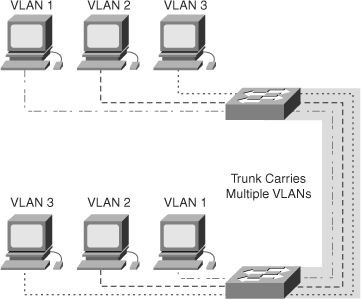
As mentioned in a previous section, ISL is a Cisco proprietary protocol for interconnecting Layer 2–capable devices that carry VLAN traffic, as illustrated in Figure 4-10. The dotted and shaded lines between the switches in Figure 4-10 show the trunk carrying traffic for three VLANs. Every PC belongs to a separate VLAN and can communicate with the other PCs connected to the remote switch in the same VLAN over the trunk link. Besides specific models of Cisco Catalyst switches, high-end routers and network appliances support ISL. This chapter highlights trunking on Catalyst switches exclusively. For configuration information regarding trunking on Cisco IOS routers or other network devices, refer to the Cisco Systems, Inc. technical documentation.
A non-ISL device that receives ISL-encapsulated Ethernet frames may consider those frames to be transmission errors if the size of the header plus the data frame exceeds the MTU size. Furthermore, devices that do not support ISL simply drop ISL frames on ingress because they cannot decode the ISL encapsulation. Figure 4-11 illustrates the ISL frame; note that the header encapsulation is 26 bytes plus an additional 4 bytes for a header cyclic redundancy check (CRC).
When you are examining the frame formats for Layer 2 frames, notice that the ISL Layer 2 header is placed before the other Layer 2 field information in the frame.
The ISL frame contains two FCS fields. The original transmitting device generates one FCS field, and the ISL trunk port generates the other FCS field. ISL encapsulates the frame without modifying its contents.
The ISL Ethernet frame header contains additional fields; consult Cisco.com for more details on these fields.
All Catalyst switches support 802.1Q tagging for multiplexing traffic from multiple VLANs onto a single physical link, as shown in Figure 4-12.
IEEE 802.1Q trunk links employ the tagging mechanism to carry frames for multiple VLANs, in which each frame is tagged to identify the VLAN to which the frame belongs. The IEEE 802.1Q/802.1p standard provides inherent architectural advantages over ISL:
802.1Q has smaller frame overhead than ISL. As a result, 802.1Q is more efficient than ISL, especially in the case of small frames. 802.1Q overhead is 4 bytes, whereas ISL is 30 bytes.
802.1Q is a widely supported industry-standard protocol.
802.1Q has the support for 802.1p fields for QoS.
Figure 4-13 describes the 802.1Q frame.
The 802.1Q Ethernet frame header contains the following fields:
Dest—. Destination MAC address (6 bytes)
Src—. Source MAC address (6 bytes)
Tag—. Inserted 802.1Q tag (4 bytes, detailed here)
EtherType(TPID)—. Set to 0x8100 to specify that the 802.1Q tag follows.
CFI—. Canonical Format Indicator is always set to 0 for Ethernet switches and to 1 for Token Ring-type networks.
PRI—. 3-bit 802.1p priority field.
VLAN ID—. 12-bit VLAN field. Of the 4096 possible VLAN IDs, the maximum number of possible VLAN configurations is 4094. A VLAN ID of 0 is used to indicate priority frames, and value 4095 (FFF) is reserved. CFI, PRI, and VLAN ID are represented as Tag Control information (TCI) fields.
Len/Etype—. 2-byte field specifying length (802.3) or type (Ethernet II).
Data—. Data itself.
FCS—. Frame check sequence (4 bytes).
IEEE 802.1Q uses an internal tagging mechanism that modifies the original frame (as shown by the “X” over FCS in the original frame in Figure 4-13), recalculates the CRC value for the entire frame with the tag, inserts the new CRC value in a new FCS. ISL, in comparison, wraps the original frame and adds a second FCS that is built only on the header information but does not modify the original frame FCS.
IEEE 802.1p redefined the three most significant bits in the 802.1Q tag to allow for prioritization of the Layer 2 frame.
The 802.1Q tagged frame supports Layer 2 compatibility on any Layer 2 device. Layer 2 devices, except those with 802.1Q trunk ports, do not have the capability to discern the EtherType field or the tag. If a non-802.1Q-enabled device or an access port receives a frame, the device ignores the tagged portion of the frame and switches the packet at Layer 2 as if it were a standard Ethernet frame. This allows for the placement of Layer 2 intermediate devices, such as other switches or bridges, on the 802.1Q trunk link.
Baby giants are frames that are larger than the standard MTU of 1500 bytes but less than 2000 bytes. Because ISL and 802.1Q tagged frames increase the MTU beyond 1500 bytes, switches consider both frames as baby giants. ISL-encapsulated packets over Ethernet have an MTU of 1548 bytes, whereas 802.1Q has an MTU of 1522 bytes.
802.1Q trunks define a native VLAN for frames that are not tagged by default. Switches transmit any Layer 2 frames from a native VLAN on the trunk port untagged, as shown in Figure 4-14. The receiving switch forwards all untagged packets to its native VLAN. The native VLAN is the default VLAN configuration of the port. When the port is not trunking, the access VLAN configuration defines the native VLAN. In the case of Cisco switches, the default VLAN is VLAN 1 and is configurable.
It is important that the 802.1Q trunk port between two devices has the same native VLAN configuration on both sides of the link. Misconfiguration of the native VLAN for 802.1Q trunk ports on the same trunk link might cause Layer 2 loops or black holes. With 802.1Q trunks, frames for the native VLAN are untagged, and if there is a native VLAN misconfiguration on peer switches, the untagged frames are received on the wrong VLAN on the peer switch. Furthermore, CDP issues a “VLAN mismatch” error message to any active consoles where native VLANs do not match. Note that there are some specific cases where CDP is either turned off or cannot be transmitted through an intermediate Layer 2 device in the same manner that 802.1Q frames are transmitted.
With an 802.1Q native VLAN, a switch forwards any Layer 2 frame that is received on a trunk port, whether tagged or not, to an intended VLAN. Compared to 802.1Q, ISL drops any unencapsulated frames that are received on a trunk port, and all frames that are transmitted from a trunk port are encapsulated, including the native VLAN.
Each physical port on the switch has a parameter called Port VLAN ID (PVID). Switches assign every 802.1Q port a PVID value based on its native VLAN ID. (The default is VLAN 1.) All switches assign all untagged frames to the VLAN that is specified in the PVID parameter. When a port receives a tagged frame, the tag is respected. If the frame is untagged, it is forwarded to the VLAN that is contained in the PVID. This allows the coexistence on the same Ethernet segment of VLAN-aware bridges or stations and VLAN-unaware bridges or stations.
All recent Cisco Catalyst switches, except for the Catalyst 2900XL and 3500XL, use a Cisco proprietary point-to-point protocol called Dynamic Trunking Protocol (DTP) on trunk ports to negotiate the trunking state. DTP negotiates the operational mode of directly connected switch ports to a trunk port and selects an appropriate trunking protocol. Negotiating trunking is a recommended practice in multilayer switched networks because it avoids network issues resulting from trunking misconfigurations.
ISL supports VLAN numbers in the range of 1 to 1005, whereas 802.1Q VLAN numbers are in the range of 1 to 4094. The default behavior of VLAN trunks is to permit all normal- and extended-range VLANs across the link if it is an 802.1Q interface and to permit normal VLANs in the case of an ISL interface. However, switches support configurations to restrict a single VLAN, range of VLANs, or group of VLANs across a trunk interface. Best practice is to limit the trunk to only the intended VLANs to reduce the possibility of loops and to improve bandwidth utilization by restricting unwanted VLAN data traffic from the link. Unnecessary VLANs can be limited by VTP pruning or manual removal of the VLANs from the trunk interfaces. This chapter discusses pruning later in the “VTP Pruning” section.
Cisco switches require VLAN mapping for the following reasons when traversing networks using both 802.1Q and ISL:
In a network environment with devices that are connected to Cisco switches through 802.1Q trunks, 802.1Q VLANs in the range of 1 to 1000 are automatically mapped to the corresponding ISL VLAN; however, 802.1Q VLAN numbers greater than 1000 must be mapped to an ISL VLAN to be recognized and forwarded by Cisco network devices.
In a network with non-Cisco devices that use reserved VLANs, VLANs must be mapped to nonreserved VLANs to work in Cisco networks.
The following restrictions apply when mapping 802.1Q VLANs to ISL VLANs:
Limited to eight 802.1Q-to-ISL VLAN mappings on a switch.
Limited to mapping 802.1Q VLANs to Ethernet-type ISL VLANs.
It is important not to enter the native VLAN of any 802.1Q trunk in the mapping table to avoid overlapping numbers.
Mapping an 802.1Q VLAN to an ISL VLAN blocks the traffic on the 802.1Q VLAN corresponding to the mapped ISL VLAN. For example, mapping 802.1Q VLAN 2000 to ISL VLAN 200 blocks the traffic on 802.1Q VLAN 200.
VLAN mappings are local to each switch. Configure the same VLAN mappings on all appropriate switches in the network.
Another feature of 802.1Q is its capability to support tunneling features, such as 802.1Q-in-Q tunneling, which allows service providers to transport VLANs within VLANs, preserving individual customer’s VLAN assignments without requiring them to be unique. Layer 2 protocol tunneling is a scaleable method for tunneling protocol data units (PDUs) through the service provider network, as shown in Figure 4-15. Chapter 16, “Designing, Building, and Connecting Cisco Multilayer Switched Networks Using Metro Solutions,” discusses 802.1Q-in-Q tunneling in more detail.
Table 4-4 describes the different trunking modes supported by Cisco switches.
Table 4-4. Trunking Modes
Mode in Cisco CatOS | Mode in Cisco IOS | Function |
|---|---|---|
Off | Access | Puts the interface into permanent nontrunking mode and negotiates to convert the link into a nontrunk link. The interface becomes a nontrunk interface even if the neighboring interface does not agree to the change. |
On | Trunk | Puts the interface into permanent trunking mode and negotiates to convert the link into a trunk link. The interface becomes a trunk interface even if the neighboring interface does not agree to the change. |
Nonegotiate | Nonegotiate | Puts the interface into permanent trunking mode but prevents the interface from generating DTP frames. You must configure the neighboring interface manually as a trunk interface to establish a trunk link. Use this mode when connecting to a device that does not support DTP. |
Desirable | Dynamic desirable | Makes the interface actively attempt to convert the link to a trunk link. The interface becomes a trunk interface if the neighboring interface is set to trunk, desirable, or auto mode. This is the default mode for all Ethernet interfaces in Cisco IOS. |
Auto | Dynamic auto | Makes the interface willing to convert the link to a trunk link. The interface becomes a trunk interface if the neighboring interface is set to trunk or desirable mode. This is the default mode in Cisco CatOS. |
Table 4-5 lists the Ethernet trunking modes that Cisco switches support.
Table 4-6 lists which Catalyst switches support ISL and 802.1Q.
Note
The Cisco Catalyst 4000 and 4500 switches run Cisco IOS or Cisco CatOS depending on the Supervisor Engine model. The Supervisor Engine I and II only support 802.1Q. Furthermore, specific oversubscribed line modules for the Catalyst 4000 and 4500 do not support ISL encapsulation on a per-port basis. Refer to the product documentation on Cisco.com for more details.
To configure a switch port as an ISL trunking port in Cisco IOS, use the following commands:
Enter the interface configuration mode.
Switch(config)#interface {FastEthernet | GigabitEthernet} slot/port
Select the encapsulation type.
Switch(config-if)#switchport trunk encapsulation {isl | dot1q | negotiate}
Configure the interface as a Layer 2 trunk.
Switch(config-if)#switchport mode {dynamic {auto | desirable} | trunk}
Specify the native VLAN.
Switch(config-if)#switchport trunk native vlan vlan-id
Configure the allowable VLANs for this trunk.
Switch(config-if)#switchport trunk allowed vlan {add | except | all | remove} vlan-id[,vlan-id[,vlan-id[,...]]]
Note
With Cisco IOS Software Release 12.1(13)E and later, VLAN IDs may be in the range of 1 to 4094, except in the case of reserved VLANs. With Cisco IOS Release 12.1(11b)E or later, it is possible to remove VLAN 1 from a trunk port. Even after removing VLAN 1 from a trunk, the trunk interface continues to send and receive management traffic. For example, CDP, VTP, Port Aggregation Protocol (PAgP), and DTP all use VLAN 1, regardless of the existence of VLAN 1 on the port.
Example 4-17 shows configuration of a port for ISL trunking in Cisco IOS.
Example 4-17. Configuring a Port for ISL Trunking in Cisco IOS
Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#interface FastEthernet 5/8 Switch(config)#switchport Switch(config-if)#switchport trunk encapsulation isl Switch(config-if)#switchport mode trunk Switch(config-if)#end
Example 4-18 shows configuration of interface Fast Ethernet 5/8 for 802.1Q trunking in the desirable mode and allowing only VLANs 1 through 100 on the trunk.
Example 4-18. Configuring a Port for 802.1Q Trunking in Cisco IOS
Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#interface FastEthernet 5/8 Switch(config-if)#switchport trunk encapsulation dot1q Switch(config-if)#switchport mode dynamic desirable Switch(config-if)#switchport trunk allowed vlan 1-100 Switch(config-if)#no shutdown Switch(config-if)#end
To configure ISL trunks in Cisco CatOS, use the following commands in the privileged EXEC mode:
The following command configures the trunking mode and method.
set trunk mod/port [on | desirable | auto | nonegotiate] [isl | dot1q]
(Optional.) If not specified, all VLANs are allowed on the trunk. To specifically add VLANs on the trunk, use this command:
set trunk mod/port vlan-id1[,vlan-id[,vlan-id[,...]]]
(Optional.) To remove VLANs from the trunk, use the following command:
clear trunk mod/port vlan IDs
clear also removes VLANs from the trunk. Another option to remove unnecessary VLANs is to use pruning with VTP, which this chapter discusses later in the “VTP Pruning” section.
(Optional.) The following command tags all the VLANs including the native VLAN in 802.1Q. This is a global command.
set dot1q-all-tagged enable [all]
(Optional.) To tag native VLANs only on specific ports, do the following:
set port dot1q-all-tagged mod/port enable | disable
Example 4-19 shows configuration of ISL trunking on Cisco CatOS to disallow VLANs 10 to 20 from the trunk.
Example 4-20 shows configuration of 802.1Q trunking in Cisco CatOS.
To verify the trunk configuration in Cisco IOS, use the commands in Table 4-7.
Table 4-7. Cisco IOS Commands to Verify Trunk Configuration
Command | Notes |
|---|---|
show running-config interface type slot/port | Displays the running configuration of the interface |
show interfaces [type slot/port] switchport | Displays the switch port configuration of the interface |
show interfaces [type slot/port] trunk | Displays the trunk configuration of the interface |
Example 4-21 displays port configuration for trunking.
Example 4-22 displays switchport information about interface FastEthernet 5/8, which is operating as an 802.1Q trunk.
Example 4-22. Displaying Switchport Information for Trunking
Switch#show interfaces FastEthernet 5/8 switchport
Name: Fa5/8
Switchport: Enabled
Administrative Mode: dynamic desirable
Operational Mode: trunk
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: Enabled
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001Example 4-23 displays trunk information for a particular port.
Example 4-23. Displaying Trunk Information for a Particular Port
Switch#show interfaces FastEthernet 5/8 trunk
Port Mode Encapsulation Status Native vlan
Fa5/8 desirable n-802.1q trunking 1
Port Vlans allowed on trunk
Fa5/8 1-1005
Port Vlans allowed and active in management domain
Fa5/8 1-6,10,20,50,100,152,200,300,303-305,349-351,400,500,521,524,570,801-8
02,850,917,999,1002-1005
Port Vlans in spanning tree forwarding state and not pruned
Fa5/8 1-6,10,20,50,100,152,200,300,303-305,349-351,400,500,521,524,570,801-8
02,850,917,999,1002-1005To verify the trunking configuration in Cisco CatOS, use the following command:
show trunk [mod/port]
Example 4-24 shows verification of the trunking configuration in Cisco CatOS in which port 3/1 is an ISL trunk and allows only VLANs 1, 5, and 10 through 20.
Example 4-24. Verifying Trunking Configuration in Cisco CatOS
Console> (enable) show trunk 3/1
Port Mode Encapsulation Status Native vlan
-------- ----------- ------------- ------------ -----------
3/1 desirable n-isl trunking 1
Port Vlans allowed on trunk
-------- ---------------------------------------------------------------------
3/1 1,5,10-20
Port Vlans allowed and active in management domain
-------- ---------------------------------------------------------------------
3/1 1,5,10-20
Port Vlans in spanning tree forwarding state and not pruned
-------- ---------------------------------------------------------------------
3/1 1,5,10-20To troubleshoot a problem with a trunk port, verify that the following configurations are correct:
Interface modes
Native VLAN
Encapsulation types
A common problem with VLANs is where a device cannot establish a connection across a trunk link. Suggested solutions to the problem are as follows:
Ensure that the Layer 2 interface mode configured on both ends of the link is valid. The trunk mode should be trunk or desirable for at least one side of the trunk. Use the show interface interface trunk command in Cisco IOS to verify the configuration.
Ensure that the trunk encapsulation type configured on both ends of the link is valid and compatible.
On IEEE 802.1Q trunks, make sure that the native VLAN is the same on both ends of the trunk.
VTP is a protocol that is used to distribute and synchronize information about VLANs that are configured throughout a switched network. VTP minimizes misconfigurations and configuration inconsistencies that may result in various problems, such as duplicate VLAN names, incorrect VLAN-type specifications, and security violations. Switches transmit VTP messages only on 802.1Q or ISL trunks.
VTP is a Layer 2 messaging protocol that maintains VLAN configuration consistency by managing the additions, deletions, and name changes of VLANs within a VTP domain.
A VTP domain is one switch or several interconnected switches that share the same VTP environment. Catalyst switches support only a single VTP domain per switch.
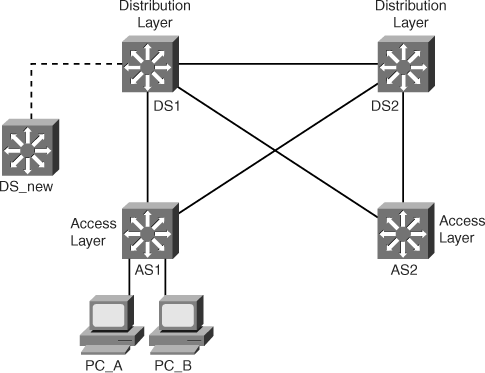
By default, a Catalyst switch is in the “no-management-domain” state until it receives an advertisement for a VTP domain over a trunk link or until a VTP configuration is applied, as shown in Figure 4-16.
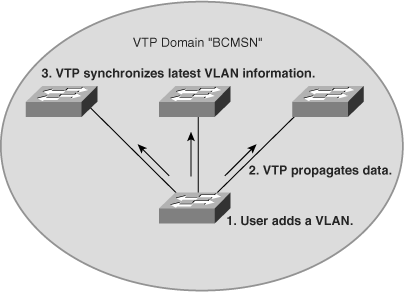
Configurations made to a single VTP server propagate across trunk links to all connected switches in the network in the following manner:
An administrator adds a new VLAN definition.
VTP propagates the VLAN information to all switches in the VTP domain.
Each switch synchronizes its configuration to incorporate the new VLAN data.
VTP operates in one of the following modes: server mode, client mode, transparent mode, or off mode. Off mode currently is supported only in Cisco CatOS. The default VTP mode is server mode, but Catalyst switches do not propagate VTP information out trunk interfaces until a management domain name is specified or learned.
Table 4-8 describes the features of the VTP client, server, transparent, and off modes.
Table 4-8. VTP Modes of Operation
Features | |
|---|---|
Client | Cannot create, change, or delete VLANs on command-line interface (CLI). Forwards advertisements to other switches. Synchronizes VLAN configuration with latest information received from other switches in the management domain. Does not save VLAN configuration in nonvolatile RAM (NVRAM). |
Server | Creates, modifies, and deletes VLANs. Sends and forwards advertisements to other switches. Synchronizes VLAN configuration with latest information received from other switches in the management domain. Saves VLAN configuration in NVRAM. |
Transparent | Creates, deletes, and modifies VLANs only on the local switch. Forwards VTP advertisements received from other switches in the same management domain. Does not synchronize its VLAN configuration with information received from other switches in the management domain. Saves VLAN configuration in NVRAM. |
Off | Similar to transparent mode except this version drops advertisements on trunk interface. |
Note
In VTP version 3, there is a concept of a primary server and a secondary server. This chapter discusses VTP version 3 later in the “VTP Version 3” section.
Switches flood VTP advertisements throughout the management domain over trunk interfaces. The switch sends the messages every 5 minutes or whenever there is a change in VLAN configurations. Cisco switches transmit VTP advertisements over the management VLAN (VLAN 1 by default) using a Layer 2 multicast frame.
A device that receives VTP advertisements checks various parameters before incorporating the received VLAN information. First, the management domain name and password in the advertisement must match those configured in the local switch. Next, if the configuration revision number indicates that the message was created after the configuration currently in use, the switch incorporates the advertised VLAN information if the switch is a VTP server or client.
One of the most critical components of VTP is the configuration revision number. Each time a VTP server modifies its VLAN information, it increments the configuration revision number by 1. It then sends out a VTP advertisement with the new configuration revision number. If the configuration revision number that is being advertised is higher than the number stored on the other switches in the VTP domain, the rest of the switches in the domain overwrite their VLAN configurations with the new information being advertised, as shown in Figure 4-17.
Because a VTP-transparent switch does not participate in VTP, that switch does not advertise its VLAN configuration or synchronize its VLAN database upon receipt of a VTP advertisement. Furthermore, a switch in VTP-transparent mode always has the configuration revision number of 0.
Note
The overwrite process means that if the VTP server deletes all VLANs and advertises with a higher revision number, the client devices in the VTP domain also delete their VLANs. Use this feature with caution.
The ensuing sections discuss the following properties of VTP:
VTP pruning uses VLAN advertisements to determine when a trunk connection is flooding traffic needlessly. By default, a trunk connection carries traffic for all VLANs in the VTP management domain. Commonly, some switches in an enterprise network do not have local ports configured in each VLAN. In Figure 4-18, switches 1 and 4 support ports statically configured in the red VLAN.
VTP pruning increases available bandwidth by restricting flooded traffic to those trunk links that the traffic must use to access the appropriate network devices. Figure 4-18 shows a switched network with VTP pruning enabled. The broadcast traffic from station A is not forwarded to switches 3, 5, and 6 because traffic for the red VLAN has been pruned on the links indicated on switches 2 and 4.
Note
Regardless of whether you use VTP pruning support, Catalyst switches run an instance of STP for each VLAN. An instance of STP exists for each VLAN even if there are no ports active in the VLAN or if VTP pruning removes the VLANs from an interface. As a result, VTP pruning prevents flooded traffic from propagating to switches that do not have members in specific VLANs. However, VTP pruning does not eliminate the switches’ knowledge of pruned VLANs.
Cisco Catalyst switches support three different versions of VTP: versions 1, 2, and 3. It is important to decide which version to use because they are not interoperable. In addition, Cisco recommends running only one VTP version for network stability. This chapter emphasizes VTP versions 1 and 2 because VTP version 3 is relatively new.
VTP version 1 is supported in Cisco CatOS version 2.1 or later and in all versions of Cisco IOS. VTP version 2 is supported in Cisco CatOS version 3.1(1) or later and in all versions of Cisco IOS.
VTP version 2 supports these features that are not implemented in VTP version 1:
Token Ring support—. VTP version 2 supports Token Ring LAN switching and Token Ring VLANs.
Unrecognized Type-Length-Value (TLV) support—. A VTP version 2 server or client propagates configuration changes to its other trunks even for TLVs that it cannot parse. VTP version 2 servers and clients are still able to save unrecognized TLVs in NVRAM.
Version-independent transparent mode—. In VTP version 1, a VTP-transparent switch inspects VTP messages for the domain name and version and forwards a message only if the version and domain name match. Because only one domain is supported in the Supervisor Engine software, VTP version 2 forwards VTP messages in transparent mode—without checking the version.
Consistency checks—. VTP version 2 performs VLAN consistency checks (such as VLAN names and values) only when you enter new information through the CLI or via the Simple Network Management Protocol (SNMP). VTP version 2 does not perform checks when new information is obtained from a VTP message or when information is read from NVRAM. If the message digest algorithm 5 (MD5) on a received VTP message is correct, VTP version 2 accepts the information. Use VTP version 2 in a Token Ring environment, because VTP version 1 does not support Token Ring VLANs.
If all switches in a domain are capable of running VTP version 2, enable VTP version 2 on one switch. The VTP server propagates the version number to the other VTP version 2–capable switches in the VTP domain.
VTP version 3 is supported in Cisco CatOS software versions 8.1 and above and is not currently available for Cisco IOS. VTP version 3 differs from earlier VTP versions in that it does not directly handle VLANs. Instead, it is responsible for distributing a list of opaque databases over an administrative domain. The following items are enhancements in VTP version 3:
Support for extended VLANs (1025 to 4094)
Support for the creation and advertising of pVLANs
Improved server authentication
Enhancements to a mechanism for protection from the “wrong” database accidentally being inserted into a VTP domain
Interaction with VTP versions 1 and 2
Configurable on a per-port basis
VTP version 3 has the same features as VTP versions 1 and 2 except for the addition of the modes of primary and secondary server and the concept of database consistency.
The primary server is the sole server in the VTP domain that is used to modify VTP configuration. A VTP domain may operate without an active primary server because the secondary servers ensure persistence of the configuration over reloads. The primary server may initiate or change the VTP configuration. A VTP domain may operate without a primary server for the following reasons:
If the switch reloads
If a high-availability switchover occurs between the active and redundant Supervisor Engines
If a forceful takeover from a secondary server occurs
If a change in the VTP mode, version, or password configuration occurs
In server mode, the switch becomes a secondary server by default. The secondary server is the same as a VTP client in VTP version 2 in that a secondary VTP server cannot modify the configuration. The only exception is that the VTP server can save the VTP configuration in NVRAM. A secondary server can be changed to the primary server by using the takeover command from the switch; this switchover to the primary server is propagated to the entire domain. All other potential primary servers in the domain resign to secondary server mode to ensure that only one primary server exists in the VTP domain at any given time. This method avoids VLAN inconsistencies and provides a higher degree of stability.
A switch that is running VTP version 3 can modify reserved VLANs 1002 through 1005; however, these VLANs are set to their default in the scaled-down database for VTP version 2 peers. A switch that is running VTP version 3 does not accept a configuration from VTP version 1 or VTP version 2 neighbors. As a result, it is highly recommended that you change all the modes of the switches that are running versions 1 and 2 to VTP clients and reset their respective VTP revision versions.
VTP domains can be secured by using the VTP password feature. It is important to make sure that all the switches in the VTP domain have the same password and domain name; otherwise, a switch will not become a member of the VTP domain. Cisco switches use MD5 to encode passwords in 16-byte words. These passwords propagate inside VTP summary advertisements. In VTP, passwords are case-sensitive and can be 8 to 64 characters in length. The use of VTP authentication is a recommended practice.
When a network device is in VTP server mode, you can change the VLAN configuration on one switch and have the VLAN configuration propagate to all switches throughout the network. VLAN configuration changes include adding, removing, or changing the name of a VLAN. Default VTP configuration values depend on the switch model and software version. For example, the default values for the Catalyst 4500 and 6500 families of switches are as follows:
VTP domain name—. None
VTP mode—. Server
VTP pruning—. Disabled
VTP password—. None
VTP trap—. Disabled (SNMP traps communicating VTP status)
Cisco switches may learn or specify a VTP domain name. By default, the domain name is not set. To set a name and password for the VTP management domain, the name and password should be the same for all switches in the domain, and passwords are case-sensitive.
VTP pruning eligibility is one VLAN parameter that the VTP protocol advertises. Enabling or disabling VTP pruning with VTP versions 1 or 2 on a VTP server propagates the change throughout the management domain. However, in the case of VTP version 3, VTP pruning must be enabled manually on each switch.
To configure a VTP server in Cisco IOS in configuration mode for VTP versions 1 and 2, follow these steps from privileged EXEC mode:
Enter global configuration mode.
Switch#configure terminalConfigure the VTP mode as server.
Switch(config)#vtp serverConfigure the domain name.
Switch(config)#vtp domain domain_name
(Optional.) Enable VTP version 2.
Switch(config)#vtp version 2(Optional.) Specify a VTP password.
Switch(config)#vtp password password_string
(Optional.) Enable VTP pruning in the management domain.
Switch(config)#vtp pruningExit global configuration mode.
Switch(config)#exit
Note
Make sure the VTP password and VTP version are the same on all the switches that are part of the VTP domain.
Note
Use these same steps to configure the VTP in the database mode except the VTP version. To change the VTP version under database mode, issue the vtp v2-mode command.
Example 4-25 shows configuration of a Catalyst switch as a VTP server in Cisco IOS in global configuration mode.
To configure a VTP server in Cisco CatOS, follow these steps from the privileged EXEC mode:
Define the VTP domain name on the switch.
set vtp domain name
Define the VTP mode.
set vtp mode client | off | server | transparent
(Optional.) Specify the password for the VTP domain.
set vtp passwd passwd
(Optional.) Specify the version of VTP. The default is 1.
set vtp version 1 | 2(Optional.) Enable VTP pruning in the whole VTP domain.
set vtp pruning enable(Optional.) Disable VTP pruning on the VLANs.
clear vtp pruneeligible vlan_range(Optional.) Add VLANs to the VTP pruning list.
set vtp pruneeligible vlan_range
Example 4-26 shows configuration of a VTP domain named Lab_Network in server mode in Cisco CatOS.
Example 4-27 shows configuration of VTP pruning for a VTP domain named BCMSN in Cisco CatOS. In addition, the example illustrates the removal of VLANs 100 through 500 from the pruning list in Cisco CatOS.
Example 4-27. VTP Pruning in Cisco CatOS
Console> (enable) set vtp pruning enable Cannot modify pruning mode unless in VTP SERVER mode. Console> (enable) set vtp mode server Changing VTP mode for all features VTP domain BCMSN modified Console> (enable) set vtp pruning enable This command will enable the pruning function in the entire management domain. All devices in the management domain should be pruning-capable before enabling. Do you want to continue (y/n) [n]? y VTP domain BCMSN modified Console> (enable) clear vtp pruneeligible 100-500 Vlans 100-500 will not be pruned on this device. VTP domain BCMSN modified.
Use the show vtp status command to display information about the VTP configuration and current state in Cisco IOS. For Cisco CatOS, use the show vtp domain command to display similar information.
Example 4-28 shows how to verify the VTP configuration by using the show vtp status command. The output describes the VTP version, the number of VLANs supported locally, the VTP operating mode, the VTP domain name, and the VTP pruning mode.
Example 4-28. Displaying VTP Status
Switch#show vtp status
VTP Version : 2
Configuration Revision : 247
Maximum VLANs supported locally : 1005
Number of existing VLANs : 33
VTP Operating Mode : Server
VTP Domain Name : Lab_Network
VTP Pruning Mode : Enabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0x45 0x52 0xB6 0xFD 0x63 0xC8 0x49 0x80
Configuration last modified by 0.0.0.0 at 8-12-99 15:04:4Use the show vtp counters command to display statistics about VTP operation. Example 4-29 displays VTP statistics in Cisco IOS.
Example 4-29. Displaying VTP Statistics in Cisco IOS
Switch# show vtp counters
VTP statistics:
Summary advertisements received : 7
Subset advertisements received : 5
Request advertisements received : 0
Summary advertisements transmitted : 997
Subset advertisements transmitted : 13
Request advertisements transmitted : 3
Number of config revision errors : 0
Number of config digest errors : 0
Number of V1 summary errors : 0
VTP pruning statistics:
Trunk Join Transmitted Join Received Summary advts received from
non-pruning-capable device
---------------- ---------------- ---------------- ------------------
Fa5/8 43071 42766 5Example 4-30 shows the output of the show vtp domain command in Cisco CatOS.
Example 4-30. Verifying VTP Configuration in Cisco CatOS
Console> (enable) show vtp domain
Version : running VTP1 (VTP3 capable)
Domain Name : Lab_Network Password : configured (hidden)
Notifications: disabled Updater ID: 172.20.52.19
Feature Mode Revision
-------------- -------------- -----------
VLAN Off 0
Pruning : disabled
VLANs prune eligible: 2-1000Problems with VTP configuration are usually a result of improperly configured trunk links, domain names, VTP modes, or passwords.
Perform the following steps to troubleshoot VTP issues in which VTP is not updating the configuration on other switches when VLAN configuration changes occur:
Make sure the switches are connected through trunk links. VTP updates are exchanged only over trunk links. Check to make sure all switch-to-switch connections are using the same trunking protocol. In addition, verify that the operation of each link partner’s operation speed and duplex is the same by using the show interface command in Cisco IOS.
Make sure the VTP domain name, which is case-sensitive, is configured exactly the same way on the appropriate switches. Switches only exchange VTP updates between switches in the same VTP domain. Use the show vtp status command to verify these configurations.
Check whether the switch is in VTP transparent mode. Only switches in VTP server or VTP client mode update their VLAN configuration based on VTP updates from other switches. Use the show vtp status command to verify the configured VTP modes.
If you are using VTP passwords, make sure to use the same password and authentication on all switches in the VTP domain.
Make a backup copy of VLAN.dat in Cisco IOS VLAN database configuration mode or the configuration in Cisco IOS by copying the configuration to a remote device such as a TFTP server before troubleshooting.
If a particular host is not able to communicate with another host that is in the same VLAN but in a different switch, follow these steps:
Make sure that a VLAN is created in the database by using the show vlan command.
Check to determine if the hosts are members of the same VLAN by using the show interface command.
Check to determine if the VLANs are active in the VLAN database by using the show vlan membership command. If this is not the problem, check to see if the VTP name and password, if configured, are correct or check to see that the VLAN is present in the VLAN database.
Check to determine if the particular VLAN is active on the trunk interface. Even if active, if it is a dot1q trunk, check to see if the native VLAN is the same across both sides of the trunk interfaces by using the show interface trunk command.
The following bullets review important BCMSN exam preparation points of this chapter. The bullets only briefly highlight the important concepts. Table 4-9 lists and describes the functions of the important commands covered in this chapter. Consult the text of this chapter for additional information regarding these topics:
A VLAN is a logical broadcast domain that facilitates a group of end devices with common requirements, irrespective of their physical locations. A VLAN generally encompasses a single IP subnet.
In terms of configuring VLANs in Cisco IOS, make sure to define the VLAN before you assign the ports to the newly created VLAN.
Always use the global configuration mode to configure VLANs in Cisco IOS.
Recommended practice is to configure host ports to be static access ports using the switchport mode access command.
Use the switchport access vlan vlan command to configure interfaces for a specific VLAN.
Always use the switchport host command on the ports connected to a single host to disable EtherChanneling and to enable Spanning-Tree PortFast.
Because 802.1Q is an industry-standard trunking protocol that has support for extended VLANs (VLAN IDs 1025 to 4094) and uses 802.1p fields for QoS, recommended practice is to always implement 802.1Q trunking instead of ISL trunking in multilayer switched networks.
By default, the Native VLAN of an interface is 1.
The Native VLAN of a trunk port is the configured VLAN ID as if the port were not trunking in Cisco CatOS.
The Native VLAN is not tagged; therefore, the Native VLAN does not contain 802.1p fields for QoS. However, there is a configuration option in more recent Cisco IOS versions 12.1.13 or later to tag the Native VLAN on a trunk port (that is, tag all VLANs). With this option, the Native VLAN traffic is simply tagged with the associated VLAN ID, by default, VLAN 1. It is possible to remove VLAN 1 from a trunk; however, this only removes data traffic from VLAN 1. CDP, DTP, PAgP, and so on still transmit across VLAN 1.
Dynamic Trunking Protocol (DTP) is a protocol that negotiates the operational mode of directly connected switch ports to a trunk port and chooses an appropriate trunking protocol.
Always use the switchport mode trunk command to configure the trunk port in the on mode statically if the link partner (peer) does not support DTP or the desirable mode trunking configuration.
VTP is also one of the important Layer 2 messaging protocols that is used to circulate and synchronize the VLAN database throughout the network within a VTP domain.
VTP is configurable in server, client, and transparent modes within a particular domain. In server mode, the switch can add, delete, and update VLANs. In client mode, the switch cannot add or delete VLANs, but it can synchronize and forward VTP advertisements to other switches in a VTP domain. In transparent mode, the switch can add, delete, or modify VLANs only on a local switch, but it doesn’t synchronize its VLAN database. Switches can forward VTP advertisement to other switches in a VTP domain, even when operating in the VTP transparent mode.
The default VTP mode is the server mode.
Use VTP pruning to stop flooding of unnecessary traffic on trunk ports.
Configure switches in the VTP server or client mode to receive and synchronize the VLAN database using trunk links.
Always add a new switch in either VTP transparent mode in the same domain name or in server mode with a different domain name first. Later, change the switch to the correct domain or change from VTP transparent mode to VTP server or client mode after all trunk links are up to properly synchronize the VLAN database.
Private VLANs (pVLAN) are VLANs that provide Layer 2 isolation between end devices within the same VLAN. As such, private VLANs turn a single VLAN broadcast domain into multiple small broadcast domains to facilitate security and to reduce the number of IP subnets.
Private VLANs consist of a primary and one or multiple secondary VLANs. Each secondary VLAN is associated with a primary VLAN.
Isolated and community pVLANs are secondary pVLANs. Hosts that reside in isolated pVLANs can only converse with a promiscuous port (generally, a port with a connected router, whether it is logical, physical, or virtual), but they cannot communicate with hosts in the same isolated pVLAN. In community pVLANs, hosts that belong to the same community pVLAN can communicate with other ports in the same community VLAN and any promiscuous ports; however, the hosts in the community VLAN cannot communicate with hosts in the other community pVLANs or isolated pVLANs.
Table 4-9. Commands to Review
Command | Description |
|---|---|
show vlan | Displays detailed information of all the VLANs configured on the switch. |
show vlan brief | Displays brief information about the VLANs on the switch. This command describes the VLAN names, their status, and the ports assigned to the VLANs. |
show vtp status | Provides information about VTP name, mode, version, and authentication. |
show vlan vlan-id | Displays information about a particular VLAN by VLAN-ID. |
show vlan summary | Displays a summary of active, suspended, and extended VLANs. This command is only available in Cisco CatOS. |
show interfaces type slot/port switchport | Displays administrative and operational status of a switching interface, which includes VLAN information, pVLAN status, etc. type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet |
show interfaces type slot/port trunk | Displays the trunk information of an interface. |
(config-if)#description description | Configures an interface with a description. This option is useful for quickly identifying interfaces. |
(config-if)#switchport host | This command enables Spanning-Tree PortFast and turns off channeling on an interface. This command prevents timeouts on boot for host workstations and servers. |
(config)#interface type slot/port | Configures an interface. |
(config-if)#switchport mode access | Configures an interface with nontrunking single VLAN interface. |
(config-if)#switchport access vlan vlan_id | Configures an interface to a VLAN-ID. |
(config-if)#switchport mode trunk | Configures an interface for trunking unconditionally. |
(config-if)#switchport trunk encapsulation [dot1q | isl | negotiate] | Configures the trunking protocol on a trunk interface. |
(config-if)#switchport trunk allowed vlan options | Configures VLANs allowed to pass traffic on a trunk interface. |
(config-if)#switchport trunk native vlan vlan-id | Configures the native VLAN on a trunk interface. |
This chapter discussed VLANs in detail, including coverage of trunking and VTP.
In review, a VLAN is a logical grouping of switch ports that connects nodes of virtually any type, regardless of physical location. A VLAN is usually defined as end-to-end or local. An end-to-end VLAN spans the entire switched network, whereas a local VLAN is limited to the switches in the Building Access and Building Distribution submodules. VLANs usually are defined statically by manually assigning the switch ports to particular VLANs.
Furthermore, a trunk is a Layer 2 point-to-point link between networking devices that is capable of carrying the traffic of multiple VLANs. ISL and 802.1Q are the two trunking protocols to connect two switches. ISL is a Cisco proprietary protocol used for VLAN trunking. The 802.1Q protocol is an open-standard protocol also used for VLAN trunking. ISL supports VLAN numbers 1 to 1005, whereas 802.1Q supports VLAN numbers 1 to 4094.
VTP is used to distribute and synchronize information about VLANs configured throughout a switched network. VTP pruning helps to stop flooding of unnecessary traffic on trunk links. Review the study tips section for additional summarization of this chapter.
Complete this configuration exercise to familiarize yourself with the initial configuration of VLANs, VTP, and trunking on Cisco IOS–based Catalyst switches.
The only resources that are required for this exercise are access to Cisco IOS–based Catalyst switches via the console or in-band access such as SSH.
The purpose of this configuration exercise is to demonstrate the configuration of VLANs, trunking, and VTP in the multilayer switched environment. After completing this exercise, you will be able to perform the following types of configurations on Catalyst switches that are running Cisco IOS:
Create a VTP management domain
Configure trunking
Configure VLANs
Associate VLANs with ports on your switch
Add a new switch to the existing network
Verify the VTP and VLAN status
Configure PVLANs
Figure 4-19 shows the network layout for this exercise. In the multilayer switched network, the links between the Building Access submodule switch and the Building Distribution submodule switch (as well as the links between the distribution switches) are trunks, and all the switches belong to the same VTP domain. The access switches serve as VTP clients, while the distribution switches serve as VTP servers.
In this configuration exercise, you will use the commands listed in Table 4-10. The commands are in alphabetical order so that you can easily locate the information you need. Refer to this table if you need configuration-command assistance during the configuration exercise. The table includes only the specific parameters that are used in the example, not all the available options for the commands.
Table 4-10. Command List for Configuration Exercise
Command | Description |
|---|---|
configure terminal | From privileged EXEC mode, enters global configuration mode |
enable password password | Specifies a password used to authenticate a user to enter the privileged EXEC mode |
exit | Exits the current mode |
interface FastEthernet | GigabitEthernet slot/port | Enters the interface configuration mode for a Fast Ethernet or Gigabit Ethernet interface |
interface range FastEthernet | GigabitEthernet slot/starting_port - ending_port | Moves a range of interfaces into the interface configuration mode for applying the same configuration to the range of interfaces |
name vlan-name | Specifies a name for a VLAN in either the VLAN database or VLAN configuration mode |
no interface vlan vlan-id type | Disables a VLAN interface |
ping ip-address | Sends an ICMP echo to the designated IP address, using the default settings of size and response window time |
private-vlan [primary | isolated | community] | Configures the VLAN as a pVLAN type |
private-vlan association {secondary_vlan_list | add secondary_vlan_list | remove secondary_vlan_list} | Associates a secondary pVLAN to a primary pVLAN |
private-vlan mapping {secondary_vlan_list | add secondary_vlan_list | remove secondary_vlan_list} | Maps the secondary pVLAN to the Layer 3 primary VLAN interface for routing |
show interfaces [type slot/port] switchport | Displays the switchport configuration of the interface |
show interfaces [type slot/port]trunk | Displays the trunk configuration of the interface |
show vlan | Displays VLAN information |
show vlan private-vlan | Displays the pVLAN configuration |
show vtp status | Verifies the VTP configuration |
shutdown/no shutdown | Shuts down or enables an interface |
switchport access vlan vlan-id | Specifies the default VLAN, which is used if the interface stops trunking |
switchport mode access | Puts the interface into permanent nontrunking mode and negotiates to convert the link into a nontrunk link |
switchport mode private-vlan {host | promiscuous} | Configures an interface as a pVLAN host port or a promiscuous port |
switchport mode trunk | Puts the interface into permanent trunking mode and negotiates to convert the link into a trunk link |
switchport nonegotiate | Turns off DTP negotiation |
switchport private-vlan host-association primary_vlan_ID secondary_vlan_ID | Associates a Layer 2 interface with a pVLAN |
switchport trunk allowed vlan [remove] vlan-list | Configures the list of VLANs allowed on the trunk |
switchport trunk encapsulation dot1q | Specifies 802.1Q encapsulation on the trunk link |
switchport trunk encapsulation isl | Specifies ISL encapsulation on the trunk link |
telnet ip-address | Starts a terminal-emulation program that permits you to access network devices remotely over the network |
vlan database | Enters VLAN configuration mode |
vlan vlan-id | Creates a VLAN in either VLAN database or configuration mode |
vtp domain domain-name | Sets the VTP domain name in either the VLAN database or configuration mode |
vtp mode [ client | server | transparent ] | Sets the VTP mode |
Enter privileged EXEC mode using the enable command, and then enter global configuration mode using the configure terminal command.
From global configuration mode, configure the Building Access submodule switches, AS1 and AS2:
Use the vtp domain domain-name command to configure the VTP domain name as “cisco.”
Use the vtp mode command to configure the switches as VTP clients.
Use the vtp password command to configure a VTP domain password.
Also from global configuration mode, configure the Distribution layer switches, DS1 and DS2, with the same commands, except configure them as VTP servers.
as1(config)#vtp domain cisco Changing VTP domain name from NULL to cisco as1(config)#vtp password cisco as1(config)#vtp mode client Setting device to VTP CLIENT mode.
Do the same configuration on the Building Distribution submodule switches DS1 and DS2, but configure them as server.
ds1(config)#vtp domain cisco Changing VTP domain name from NULL to cisco ds1(config)#vtp password cisco
Configure the interface on the Building Access submodule switches, AS1 and AS2, as 802.1Q trunk ports.
Note
If you need to configure the encapsulation type to dot-1Q on a switch that defaults to ISL, use the switchport trunk encapsulation dot1q command to configure the port as an 802.1Q trunk.
The Catalyst 2950XL supports 802.1Q encapsulation only, and the Catalyst 3550XL/3560 supports both ISL and 802.1Q encapsulation.
as1(config)#interface GigabitEthernet 1/1 as1(config-if)#switchport as1(config-if)#switchport trunk encapsulation dot1q as1(config-if)#switchport mode trunk
Note
Use the switchport command to configure interfaces as Layer 2 interfaces in Cisco IOS. The Catalyst 6500 family of switches running Cisco IOS defaults to Layer 3 interfaces, whereas the Catalyst 2950, 3550, 3560, and 4500 default interface operation is Layer 2. Before applying trunking to interfaces on the Catalyst 6500 or to interfaces configured as Layer 3 interfaces, use the switchport command to force the interface into Layer 2 operation.
Configure the Distribution switches DS1 and DS2 by repeating the preceding step.
ds1(config)#interface GigabitEthernet 1/1 ds1(config-if)#switchport ds1(config-if)#switchport trunk encapsulation dot1q ds1(config-if)#switchport mode trunk ds1(config-if)#end
Assign your PC port to its primary VLAN by using the switchport access vlan vlan-id command while in interface configuration mode.
as1(config)#interface FastEthernet 4/1 as1(config-if)#switchport as1(config-if)#switchport mode access as1(config-if)#switchport access vlan 10 as1(config-if)#exit
Verify that your PC has connectivity with devices in the right VLAN by issuing a ping command.
To add the new switch, DS-new, to the existing network, as shown with the dotted lines in Figure 4-19, perform the steps that follow. Make sure the interfaces connecting to existing network are shut down before physically connecting the new switch.
Change the VTP mode to transparent (or make it part of a temporary domain).
DS-new(config)#vtp mode transparent Setting device to VTP TRANSPARENT mode.Configure the DS-new switch ports connected to the other switch as trunks ports with the static on setting and force 802.1Q encapsulation. Note that if the link partner is configured for dynamic trunking, the port may have already negotiated to a trunk.
DS-new(config)#interface gigabitEthernet 1/1 DS-new(config-if)#switchport DS-new(config-if)#switchport trunk encapsulation dot1q DS-new(config-if)#switchport mode trunk DS-new(config-if)#no shutdown
Configure the VTP mode to participate as client in the VTP domain.
DS-new(config)#vtp domain cisco Changing VTP domain name from NULL to cisco DS-new(config)#vtp mode client Setting device to VTP CLIENT mode.
Use the show running-config interface mod/port commands to verify the interface config, show vtp status to verify the VTP configuration, and show vlan to verify the VLAN configuration:
as1#show running-config interface FastEthernet 4/1 Building configuration... Current configuration : 141 bytes ! interface FastEthernet4/1 no ip address no logging event link-status switchport switchport access vlan 10 switchport mode access end as1#show running-config interface GigabitEthernet 1/1 Current configuration : 154 bytes ! interface GigabitEthernet1/1 no ip address no logging event link-status switchport switchport trunk encapsulation dot1q switchport mode trunk end as1#show vtp status VTP Version : 2 Configuration Revision : 0 Maximum VLANs supported locally : 1005 Number of existing VLANs : 6 VTP Operating Mode : Client VTP Domain Name : cisco VTP Pruning Mode : Disabled VTP V2 Mode : Disabled VTP Traps Generation : Disabled MD5 digest : 0x8C 0x59 0x58 0x5C 0xF6 0x03 0x51 0x9E Configuration last modified by 0.0.0.0 at 0-0-00 00:00:00 as1# as1#show vlan VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Gi1/1 10 VLAN0010 active Fa4/1 20 VLAN0020 active 30 VLAN0030 active 1002 fddi-default act/unsup 1003 token-ring-default act/unsup 1004 fddinet-default act/unsup 1005 trnet-default act/unsup VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2 ---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------ 1 enet 100001 1500 - - - - - 0 0 10 enet 100010 1500 - - - - - 0 0 20 enet 100020 1500 - - - - - 0 0 30 enet 100030 1500 - - - - - 0 0 1002 fddi 101002 1500 - - - - - 0 0 1003 tr 101003 1500 - - - - - 0 0 1004 fdnet 101004 1500 - - - ieee - 0 0 1005 trnet 101005 1500 - - - ibm - 0 0 Remote SPAN VLANs ------------------------------------------------------------------------------ Primary Secondary Type Ports ------- --------- ----------------- ------------------------------------------
For this task, the first step is to configure the VTP mode to transparent because pVLANs are supported only in VTP transparent mode:
Configure the VTP mode to transparent to configure pVLANs.
DS1(config-vlan)#vtp mode transparentCreate a primary pVLAN 100, a community pVLAN 101, and an isolated pVLAN 102 on switches AS1 and DS1. In addition, associate the secondary pVLANs to the primary pVLAN.
DS1(config-vlan)#vlan 100 DS1(config-vlan)#private-vlan primary DS1(config-vlan)#private-vlan association 101-102 DS1(config-vlan)#vlan 101 DS1(config-vlan)#private-vlan community DS1(config-vlan)#vlan 102 DS1(config-vlan)#private-vlan isolated
Configure an interface VLAN 100 for the primary pVLAN, and map the secondary pVLAN 101.
DS1(config)#interface vlan 100 DS1(config-if)#no shutdown DS1(config-if)#private-vlan mapping 101,102
Configure the Host’s A interface as a member of pVLAN 101 and the Host’s B interface as a member of pVLAN 102 on switch DS1.
DS1(config)#interface fastEthernet 2/3 DS1(config-if)#description Host_A DS1(config-if)#switchport DS1(config-if)#switchport mode private-vlan host DS1(config-if)#switchport private-vlan host-association 100 101 DS1(config-if)#no shutdown DS1(config-if)# interface fastEthernet 2/4 DS1(config-if)#description Host_B DS1(config-if)#switchport DS1(config-if)#switchport mode private-vlan host DS1(config-if)#switchport private-vlan host-association 100 102 DS1(config-if)#no shutdown
Verify the Private VLAN configuration, and make sure Host A is not able to send an ICMP ping to Host B.
DS1#show vlan private-vlan Primary Secondary Type Ports ------- --------- --------- ------------------------------------------ 100 101 community Fa2/1, Fa2/3 100 102 isolated Fa2/2, Fa2/4
For multiple-choice questions, there might be more than one correct answer.
Questions 7 through 9 are based on the configuration in Example 4-31.
Example 4-31. Configuration Example for Questions 7 through 9
Catalyst6500-IOS#show run interface gigabitEthernet 3/9
Building configuration...
Current configuration : 137 bytes
!
interface GigabitEthernet3/9
mtu 9216
no ip address
switchport
switchport access vlan 5
switchport trunk encapsulation dot1q
endIf the interface in Example 4-31 negotiates trunking, what would be the Native VLAN?
| |
Under what condition can the interface in Example 4-31 negotiate ISL trunking?
| |
Which statements are true in regards to the configuration of the interface in Example 4-31?
|
Questions 10 through 12 are based on the configuration in Example 4-32.
Example 4-32. Configuration Example for Questions 10 Through 12
svs-san-6509-2#show interfaces gigabitEthernet 3/9 switchport
Name: Gi3/9
Switchport: Enabled
Administrative Mode: dynamic auto
Operational Mode: down
Administrative Trunking Encapsulation: dot1q
Negotiation of Trunking: On
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 2 (VLAN0002)
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Operational private-vlan: none
Trunking VLANs Enabled: ALL
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALLWhat is trunk Native VLAN based on configuration Example 4-32?
| |
Based on the configuration Example 4-32, what statement is true if the link partner (peer switch) is configured for the dynamic trunking mode?
| |
What is the interface’s access mode VLAN in configuration Example 4-32?
| |
How does implementing VLANs help improve the overall performance of the network?
| |
What are two advantages of using local VLANs over end-to-end VLANs? (Choose two.)
| |
Which prompt indicates that you are in VLAN database configuration mode of Cisco IOS?
| |
Which switch port mode unconditionally sets the switch port to Access mode regardless of any other DTP configurations?
| |
What information is contained in the FCS of an ISL-encapsulated frame?
| |
802.1Q uses an internal tagging mechanism, where a tag is inserted after the _____ field.
| |
Which command correctly configures a port with ISL encapsulation in Cisco IOS?
| |
Which command correctly sets the native VLAN to VLAN 5?
| |
If the Layer 2 interface mode on one link partner is set to dynamic auto, a trunk will be established if the link partner is configured for which two types of interface modes in Cisco IOS? (Choose two.)
| |
What is the default VTP mode for a Catalyst switch?
| |
When is a consistency check performed with VTP version 2?
| |
Which command correctly sets the VTP version to version 1 in Cisco IOS global configuration mode?
| |
Which of the following are valid VTP version 1 and 2 modes? (Check all that apply.)
| |
After you complete the VTP configuration, which command should you use to verify your configuration?
| |
What command might correct a problem with incorrect VTP passwords?
| |
What is the purpose of pruning? | |
What are the advantages of pVLANs? | |
Suppose you have two workstations, A and B. If both workstations A and B are members of the same community pVLAN, can they communicate to each other? If they are members of different community pVLANs, can they communicate? If they are members of the same isolated pVLAN, can they communicate? Can they both communicate to the same promiscuous ports? Explain all your answers. |