Malware is often considered to be the infected file or files. However, it is often the case that the executable file leaves remnants of itself (which are still dangerous). One method that malware can use to hide is to launch processes rather than run as its own application.
Processes run in the background, and are often named cryptically; Nvidia GeForce Experience driver (nvxdsync) is not as obvious as it could be! This allows malware to hide away. Even if the user knows that malware has started a rogue process, it may be tricky to differentiate between malware and legitimate processes.
An example of this is csrss.exe, which is an essential subsystem (client/server runtime subsystem) in Win32 (mostly XP and 32-bit Windows 7). The W32/Spybot.worm.gen malware often appears as the similarly named scrss.exe; worse still, the W32/Nimda.gen@MM malware can appear as csrss.exe in the process list. The only method of differentiation is that the legitimate csrss.exe process is run from the C:WindowsSystem32 folder.
To further hide malware actions, a more recent innovation has been to run malware as a Windows service. The service is run at system startup. Windows can directly launch applications as services in which case the file launching the service will be listed in the HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServices<servicename>
registry entry under the ImagePath value. Services can also package themselves as dynamic-link libraries (.dll files rather than .exe), which cannot operate on their own. A process called svchost.exe can be used to host these services, and these will appear in the task manager as the svchost.exe process and not the actual application name.
Svchost is an important process with many legitimate uses. It is, therefore, important to investigate the underlying .dll, which is listed at HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServices<servicename> Parameters under the ServiceDll value. Each of these variations is shown in the following composite screenshot:
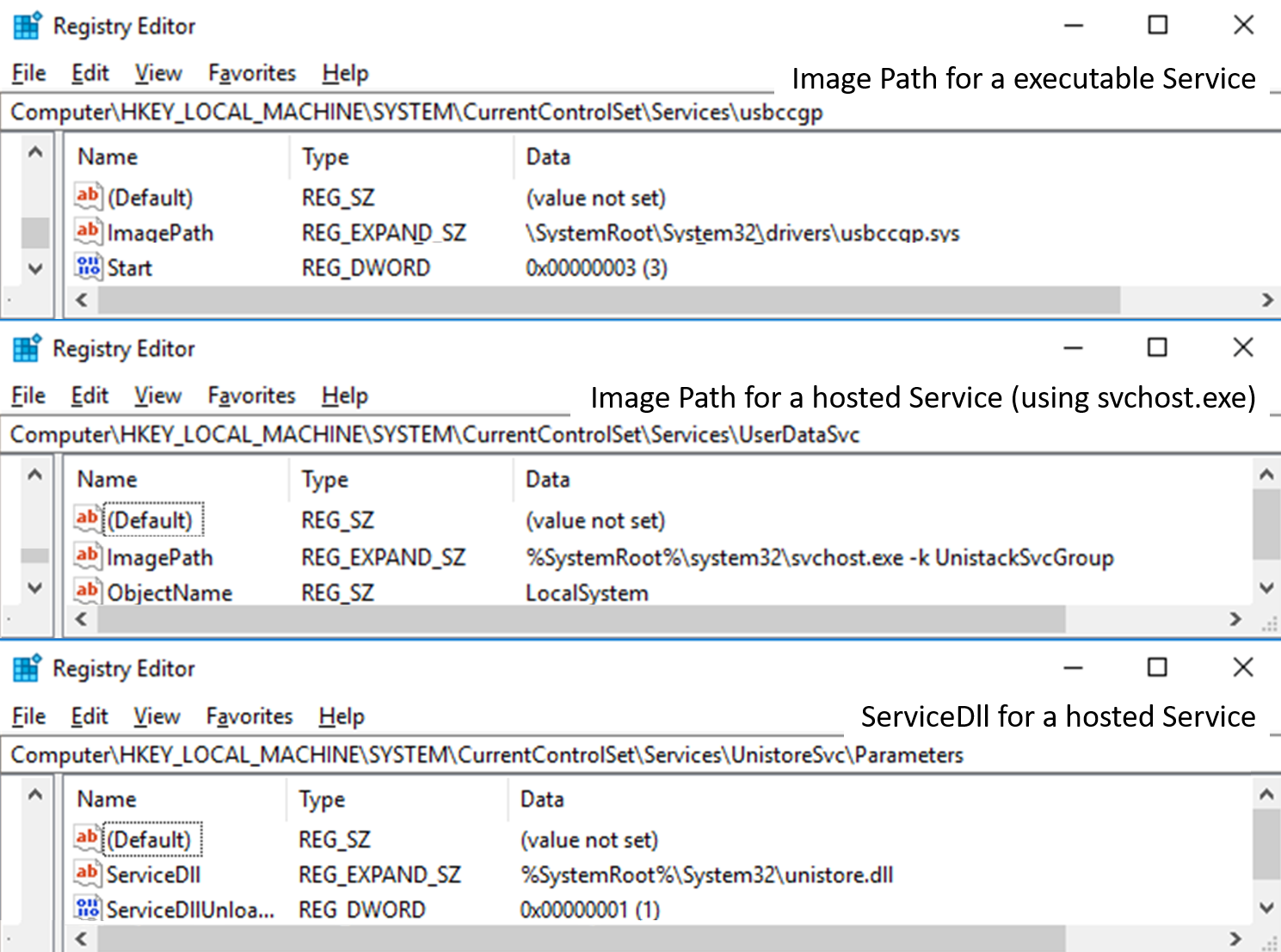
The ControlSet is the complete configuration used to launch services and other features in Windows. There are always at least two types of ControlSets—one or more numbered ControlSets (for example, ControlSet001) and CurrentControlSet, which is effectively the current running configuration on the machine. CurrentControlSet is conceptually not stored after a system shutdown. It is a mirror of the loaded numbered ControlSet, which might be the Default, Failed, or LastKnownGood ControlSet. The relevant number identifiers are in the registry under HKEY_LOCAL_MACHINESYSTEMSelect as individual values as shown in the following screenshot:
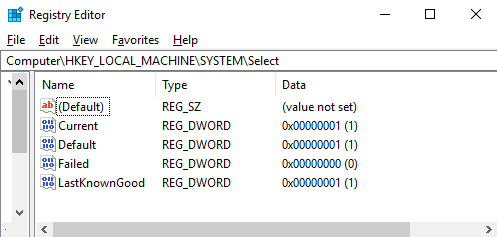
In the sampled system, there is only one numbered ControlSet (ControlSet001); there have been no failed launches on the machine so far, so the value is 0x00000000.
