- (1)
The attack vector relates to the physical and logical pathway and distance from which an attack can be launched. The further away a potential attacker can be from the vulnerability, the more potential attackers there are, and the more dangerous the vulnerability is.
Attack complexity is described in question 2. - (2)
A high attack complexity describes a situation where there are many conditions beyond the attacker's control that are required to successfully exploit a vulnerability. The lower the attack complexity, the more dangerous the threat. Privileges Required refers to the level of privileges an attacker must possess before successfully exploiting the vulnerability. Obtaining these privileges is within the attacker's scope.
Attack prerequisites does not refer to a CVSS v3.0 metric.
Attack vector is described in question 1.
- (2)
Confidentiality relates to the ability to access unauthorized content. If the victim has not accepted the call, they haven't authorized the attacker to listen to the microphone content. An example of this would be similar to the FaceTime vulnerability from 2019. (Availability is described in question 6.) The victim's microphone would still be available to the victim during the attack, but the attacker is able to listen too. (Integrity is described in question 4.) The attacker is unable to change any data from the microphone, so integrity has not been compromised. (Scope is described in question 5.) The vulnerable component is the app that controls the calls. The same app controls access to the microphone, and so the scope is unchanged. - (2)
Integrity relates to the ability of an attacker to create, edit, or delete files that they are not authorized to. It is assumed that they don't have the authority to change this file under normal conditions.
(Availability is described in question 6.) This attack does not deny other (legitimate) users from accessing the file.
(Attack Vector is described in question 1.) The attack is conducted on the network. While it might seem like this should be ranked as network, it is actually Adjacent, as the attacker's computer must be on the same network as the target.
(Attack complexity is described in question 2.) There is no detail as to whether there are conditions beyond the attacker's control that must be met for the attack to be successful. - (2)
An attack against a web server that compromises web browsers that connect to it. This would be an example of a scope change. The vulnerable component is the web server, where the affected component is the web browser. A denial-of-service (DoS) attack refers to denying the availability of a resource to legitimate users.
(Editing the contents of a file on a networked computer is discussed in question 4.)
Excel has access to the user's files, and so the scope hasn't changed. A parallel to this is specifically mentioned in the CVSS v3.0 specification document, and quoted in this chapter. - (3)
CVSS:3.0/{Portion Removed}/C:N/I:N/A:H. The impact scores that are shown are in their summarized form. A threat that leaves the component offline could also be called a DoS attack, and relates to availability. There is no detail to suggest that confidentiality or integrity are affected, so these should both score none. Option 4, which has zero impact on any of confidentiality, integrity, and availability, is not a threat. - (2)
CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N. The CVSS scores that are shown are in their summarized form. The attack is conducted on a web server, so the attack vector is network. The attack complexity is low, the privileges required are none, the scope is unchanged, and the impact is the same for all four options. There isn't any detail in the description to judge these metrics in any way. The description does state that the URL must be clicked for the malicious code to execute, so the UI score must be R, required. - (4)
A compressed (archive) file:
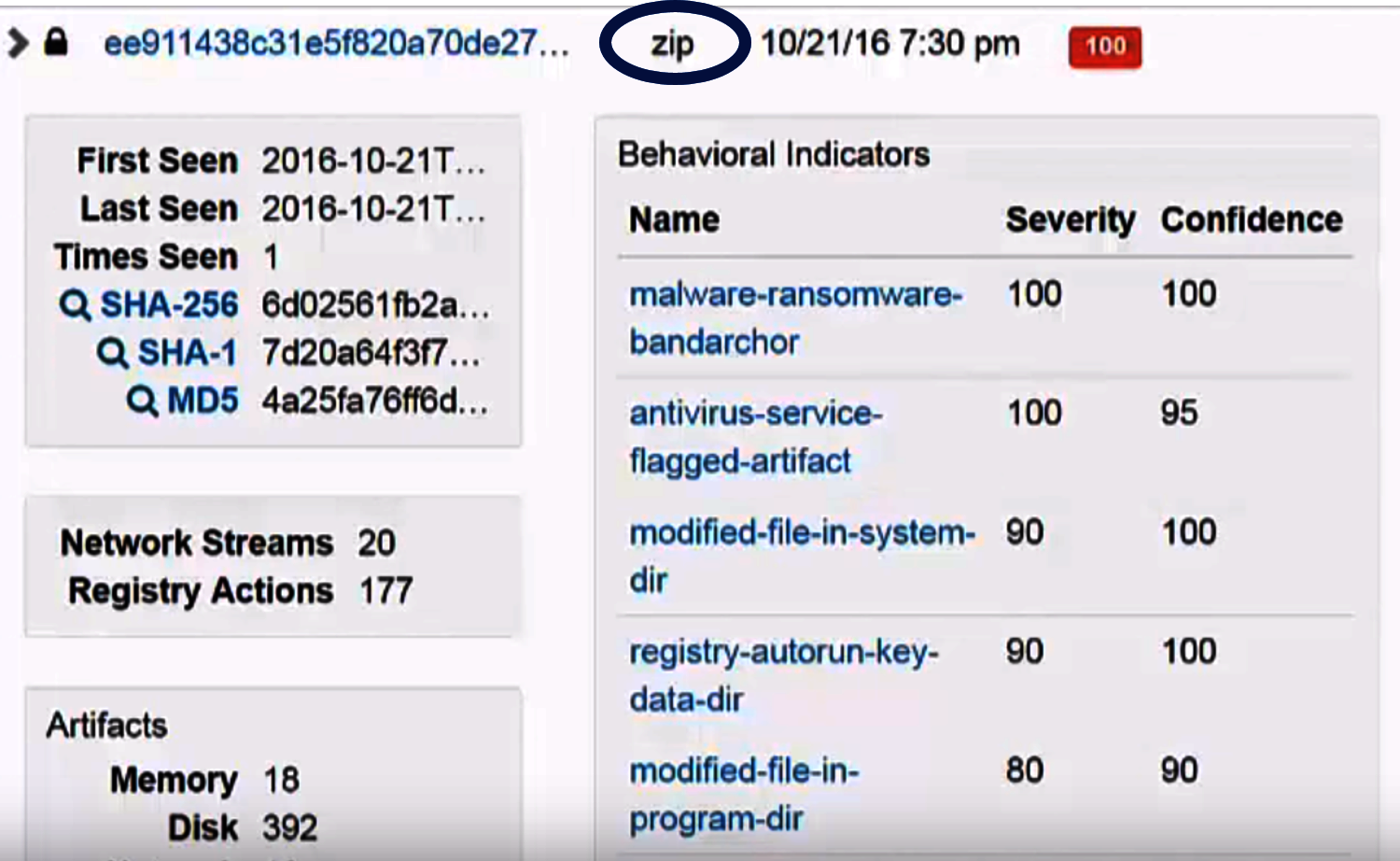
The file extension is circled. As a .zip file, it is a compressed (archive) file. An image file would be, for example, a .jpg or .png extension. Portable document files are commonly seen as .pdf, and portable executable files include .exe and .dll files.
- (1)
Immediately quarantine and block access to the file:

This file has a score of 100, which means it is definitely a known malware file. The tier-1 analyst should immediately quarantine and block access to the file. A score of 75-90 is considered dangerous, and should be referred to tier 2. A score of 56-70 is still suspicious, but needs further expertise to analyze, and should be reported to tier 3. A score of 0 would be removed from quarantine.
- (3)
Ransomware:

The report says, with a confidence level of 100%, that the item is ransomware.
