Throughput is a measure of how much transport successfully passes through a single point in the network during a given time period. It is often thought about as the speed of data transmission, although this is a flawed idea. A good parallel to this is looking at a motorway. A car might be able to travel at 70 mph (110 km/h) but can only carry five people. A bus that travels at 50 mph (80 km/h) but carries 50 passengers results in higher throughput than the car, despite traveling at a lower speed. In addition to this, some of the vehicles are actually lost and effectively create congestion without getting to where they want to go.
Measuring network utilization (how much traffic is on the network and being delivered successfully per unit time) is a useful metric, but it is limited; network utilization does not show what is consuming the bandwidth, or why packets might be failing. Effectively, network utilization is the equivalent of a picture of slow-moving traffic. The observer cannot tell whether this has been caused by a traffic accident ahead, because everyone is on their way to work, or simply that the speed limit on that road has been reduced.
Gaining more insight into the situation requires more data. NetFlow can be used to gain further insight as it separates outflows by port (allowing protocol to be inferred). NetFlow allows us to know that the bulk of the people on the road at that time are destined for work, which gives us a better understanding of the traffic. NetFlows may, for example, show big changes in the destination country (by IP address) as the company's staff communicate with Asian, European, and American markets at different times of the day. If the company doesn't have multinational dealings, flows to a variety of countries may be more of an anomaly.
Capturing full packets allows the SOC to analyze the full contents of the traffic. However, this has considerable drawbacks; the storage required for full packet captures, and then the processing to analyze the data and create alerts is much more resource intensive than using NetFlow.
The following screenshot shows a side-by-side comparison of the same set of traffic data (collected over only 41 seconds). The NetFlow presents a summary, which, although it is still a lot of data, is much smaller than the 693 full packets captured in Wireshark; full packet capture collects more data but at the expense of processing and analysis time:
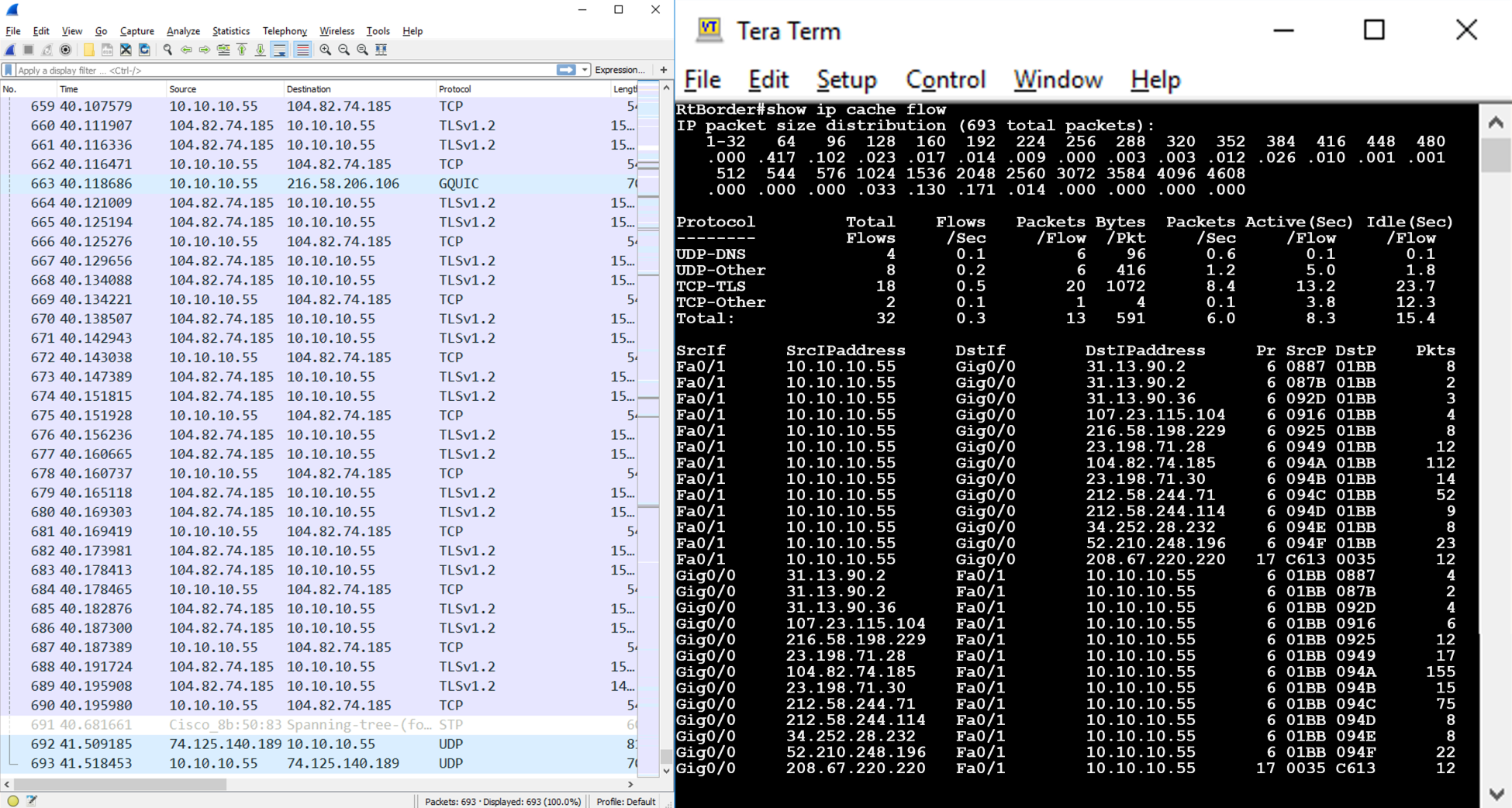
Hybrid systems do exist, with Cisco's Stealthwatch technology collecting and analyzing NetFlow data, before transitioning to full packet capture if an anomaly or alert is triggered.
