Up-to-date security software can identify known malware, but not all threats have defined signatures; threat actors amend their tactics constantly, new malware is developed, and new domains and IP addresses are registered and used.
It is important for cybersecurity operators to understand that security software cannot 100% definitively classify activity into the binary malware/non-malware groups. This fact that sometimes software classifies activity incorrectly means that there are four different categories.
The four different categories are often thought about in terms of a table dividing the actual threat against the software classification. The following diagram shows a different interpretation of this setup:
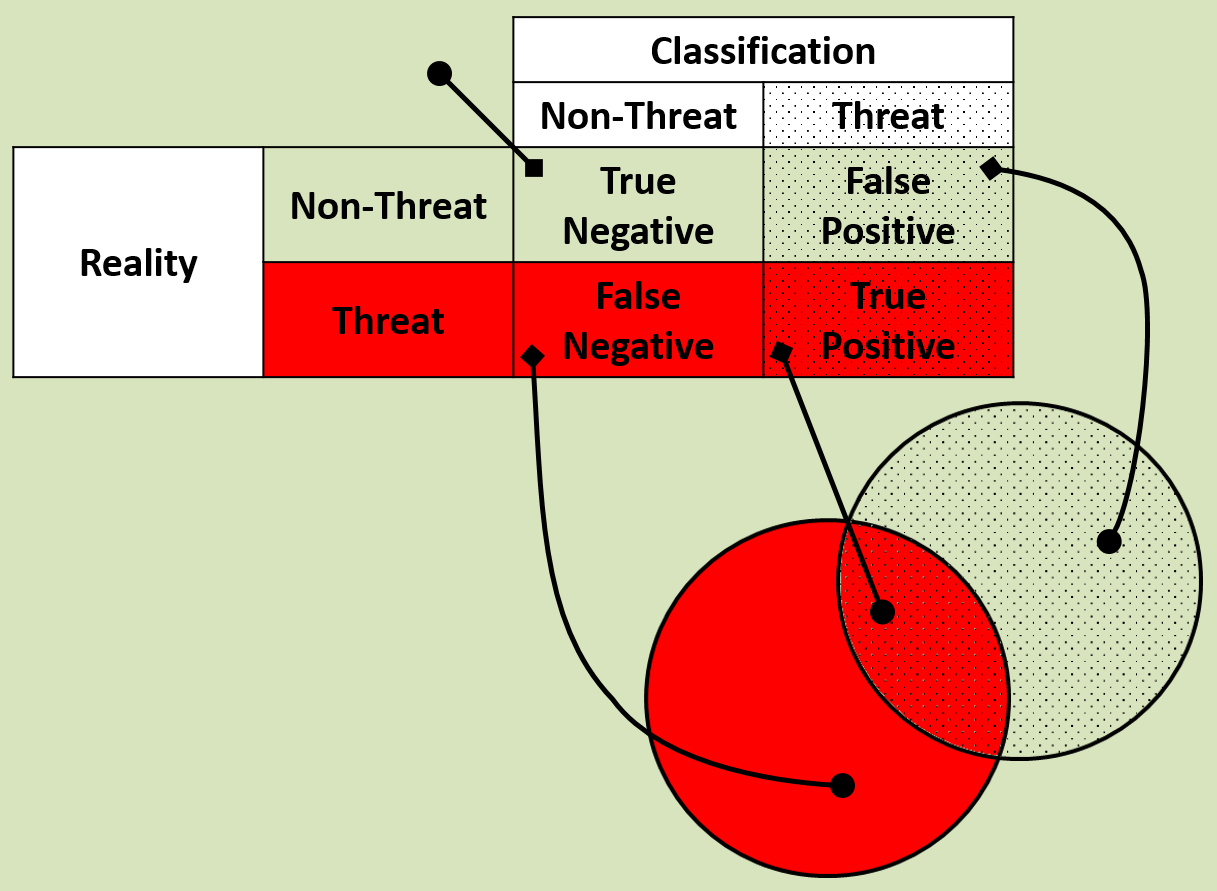
In an ideal world, the hatched circle (classified threat) should overlap totally with the red section (actual threats). It is also worth noting that the vast majority of traffic is legitimate, so it is important for a balance to be made between protecting and restricting users.
