Confidentiality
</objective> <objective>Integrity
</objective> <objective>Availability
</objective> <objective>Intruder Prevention System
</objective> <objective>Adaptive Security Appliance
</objective> <objective>Anomaly Guard
</objective> <objective>Cisco Secure Agent
</objective> <objective>Network Admission Control
</objective> <objective>Monitoring, Analysis, and Response System
</objective> </feature><feature><title>Concepts and Techniques You’ll Need to Master:</title> <objective>Importance of security policies
</objective> <objective>Basic mitigation steps
</objective> </feature>To say that security is important is to state the obvious. With Cisco routers and switches forming the backbone to today’s network infrastructures, it becomes especially important to keep security in mind. Should your backbone be breached, the entire network could be crippled, sensitive information could be eavesdropped on, and data could be corrupted or altered in a way that could have drastic effects on your operations. For this reason, Cisco expects you to have a general understanding of network security, which includes
Describing the increase in security threats and the need for a security policy
Explaining general methods to mitigate threats
Describing the functions of common security appliances/applications
Describing the recommended practices of securing network devices
The goal of security is to keep that which is vulnerable from being exploited. Servers, network devices, operating systems, and applications can all contain vulnerabilities that you may be responsible for protecting against attacks. These vulnerabilities exist because of coding errors and configuration problems. Today’s networks are becoming increasingly complex and more difficult to manage. As networks become more complex, the number of vulnerabilities in a network increases.
A second reason for the rise of threats is the constant challenge of software developers balancing features and ease of use and at the same time providing a secure product. People want software and hardware that contains many features and is easy for them to operate; introducing security into their software often limits the amount of features that can be offered and introduces more configuration steps.
No matter what software or hardware you decide to use in your environment, securing your network is a never-ending task that involves addressing three key goals:
Confidentiality
Integrity
Availability
Table 9.1 describes each of these goals and the general ways to mitigate threats against them.
Table 9.1. Security Goals
Goal | Description | Examples | Mitigation Steps |
|---|---|---|---|
Confidentiality | Keeping your data private from eavesdropping | Packet capturing and replaying | Use encryption to hide the contents of the data in transit |
Integrity | Keeping your data from being altered | Man-in-the-middle (MiTM) attacks | Use hashing to take a fingerprint of your data so you can verify it has not changed from its original form |
Availability | Keeping your data, hosts, and services available for their intended purposes | Denial of service (DoS) attacks | Use rate limiting to stop an excessive flow of traffic and install the latest patches |
Exam Alert
Be sure to memorize Table 9.1 for the exam. You should be familiar with the terms confidentiality, integrity, and availability, examples of each, and the mitigation steps.
At this point it might appear that all the security problems and solutions are technology related. In reality, this could not be further from the truth. At the end of the day, the problem of security is not with technology, but with the existence and enforcement of security policies. Wherever security measures are lacking, the security policy is either lacking or is not enforced. For example, if you do not have a policy stating that only management-approved software may be installed on a user’s computer, a user may install software that contains malicious code that could have drastic effects on your network. Your security policy should include a high-level overview as to your organization’s stance on security.
A security policy is good at detailing an organization’s overall position on security, but it does not define the specific processes for how threats should be handled. You should have a plan before an attack occurs for how you will mitigate any infrastructure threats.
Attacks against your Cisco infrastructure can fall into one of three categories:
The first type of attack is a reconnaissance attack. Before a malicious hacker attempts to gain access into your network, he or she will begin with trying to discover as much information as possible about your network. The information may include such things as IP addresses, types of devices, and software revisions. Attacks may take the form of packet-capturing software, ping sweeps, and Internet information queries, to name a few.
Packet-capturing software allows a hacker to sit back and capture all packets of data or voice as they traverse the network. The attacker can use information in these packets to learn about the type of traffic on the network. For example, if a hacker captures a number of packets that include web traffic to a particular type of web server, the hacker can use that information to look for attacks against that version of web server.
Ping sweeps are when a hacker attempts to ping all possible IP addresses on a subnet. Successful responses to the ping will tell the hacker which hosts are up. The attacker can then follow that up with attempting to scan the listening ports on the hosts to discover what type of services may be running on them. After an attacker learns of the services on a system, he or she can try to exploit the vulnerabilities associated with those services.
Internet information queries are used by hackers to discover information about public hosts on the Internet. These are done using domain name system (DNS) lookups with such tools as nslookup (Windows and Linux), Dig (Linux), and Host (Linux), among others. These tools will query a regional Internet registrar (RIR) such as American Registry for Internet Numbers (ARIN) or Réseaux IP Européens (RIPE) for information about a particular public DNS domain. The registrars will respond with telling the hacker about internal technical contacts (which can be used for social engineering attacks), public host IP addresses, and email servers.
Attackers will use all these techniques to map out your infrastructure in preparation for an attack to gain access.
You can reduce the threat of reconnaissance attacks in a couple of ways. First, you should use cryptographic protocols (such as IPSec, Secure Sockets Layer [SSL], or Secure Shell [SSH]) as much as possible to protect the confidentiality of your data in transit. Second, you can protect against packet capturing by using switches instead of hubs. Because a switch with a populated and accurate MAC address table will only forward data out the respective port to reach a destination host, traffic will not be sent out other ports that might be connected to a malicious hacker. This prevents the malicious hacker from capturing traffic sent to hosts other than the hacker’s machine.
Tip: Using Switches as a Means to Protect Against Reconnaissance Attacks
Using switches is the first step, but not the only step, you should take to prevent against packet capturing. There are many methods to get around switched networks to capture traffic. Implementing switches just adds to the steps an attacker must take to capture your traffic; it does not prevent the attacker from doing it. Other countermeasures are covered in the Cisco Certified Network Professional (CCNP) and Cisco Certified Security Professional (CCSP) exams.
If a reconnaissance attack is like finding the doors and locks on a house, an access attack is like trying to break the locks and get into a house. Examples of access attacks include
Password attacks
Trust exploitation
Man-in-the-middle
Your routers and switches can—and should—be configured with passwords. If an attacker can crack the password to your router or switch, he or she can subsequently gain access to configurations and change them to either take down your network or redirect all traffic to another computer where the attacker can read, replay, alter, or destroy the data.
Trust exploitation is when an attacker elevates his or her privileges. An example would be a user on your network that has limited access but is able to exploit an application to have administrator access.
Man-in-the-middle (MiTM) attacks involve capturing data in transit and changing it or using that data to launch another attack. This is similar to the packet-capturing reconnaissance attack. For example, in Figure 9.1 a user named Chris is sending an email to Brian, and he is offering him a raise in salary. However, Tami is a malicious hacker who intercepts the email and alters it so that it reads that there is a reduction in salary. If Tami can successfully intercept the email, alter it, and forward it on to Brian while still making it appear as if it came from Chris, she will have successfully carried out a man-in-the-middle attack.
Many of the access attacks may use malicious software, called malware, to exploit a system. Examples of malware include viruses and worms. Although the terms virus and worm are often used interchangeably, there is a difference. A virus is malware that cannot spread to another computer without human assistance. In comparison, a worm does not require human assistance to spread from computer to computer.
There are almost as many countermeasures against access attacks as there are exploits. A good countermeasure that you should always employ to defend against access attacks is to keep your operating system and applications current with the latest vendor patches.
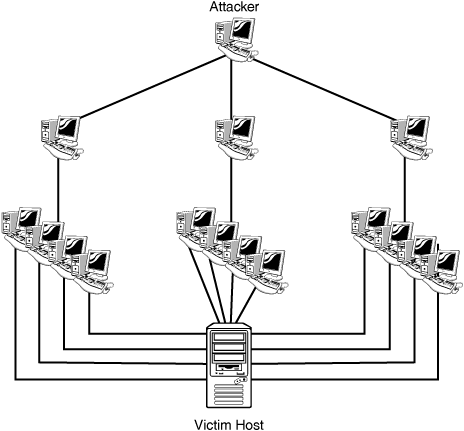
A denial of service attack is when a malicious attacker attempts to deny legitimate access to a network, system, or application. A variation of this is a distributed denial of service attack (DDoS) where an attacker will first compromise a number of zombie hosts before launching an attack on a victim host, application, or network (see Figure 9.2). In addition to increasing the severity of the attack by using multiple attacking hosts, it also makes it difficult to trace the attack back to the original attacker because there may be thousands of compromised computers used in the attack.
Protecting against DoS and DDoS attacks is similar to protecting against access attacks in that you should always keep your systems up to date with the current patches. A second step to protecting against DoS and DDoS attacks is to configure rate limiting on our Internet facing routers to prevent against traffic floods. (Rate limiting configuration is covered in the Cisco Certified Network Professional track.)
Networks must be able to absorb attacks and remain operational much like a person’s immune system functions when infected with a virus. The rate of increased security threats makes it difficult for information technology professionals to maintain control over their networks. Cisco recognizes the importance of security for your organization’s network infrastructure. Their self-defending network (SDN) initiative integrates security into your network to identify, prevent, and adapt to threats. Cisco SDN solutions include
The Cisco Intruder Prevention System (IPS) listens to all traffic on your network to detect an attack. When an attack is matched against a signature, the IPS can automatically modify firewall and access control lists on your routers to block the attacker. An IPS can be a standalone device or can be integrated into the IOS of a router and into Cisco’s Adaptive Security Appliance.
The Cisco Adaptive Security Appliance (ASA) is the replacement to the Cisco PIX firewall. It not only operates as a firewall but can also support antivirus, IPSec, network admission control, IPS, and virtual private network (VPN) technologies into a single device.
Cisco DDoS Guard protects against distributed denial of service (DDoS) attacks. A DDoS attack is a DoS attack involving many distributed systems (often thousands) that are working in sync to attack a single system or service. Cisco DDoS Guard will detect the presence of a potential DDoS attack and block malicious traffic in real-time while not affecting the flow of legitimate, mission-critical transactions.
The Anomaly Guard and Protector (also called the Cisco Anomaly Guard) works in conjunction with the DDoS Guard. The DDoS Guard matches only known DDoS signatures; it cannot detect new forms of attacks for which there is no signature. The Anomaly Guard uses behavior analysis to maintain a profile for normal traffic and detect any deviations from the normal traffic profile. It can send alerts or interact with the DDoS guard to mitigate the attack.
The Cisco Secure Agent (CSA) is software installed on endpoint systems such as desktop clients, servers, and point-of-sale (POS) systems. It defends against targeted attacks, spyware, rootkits, and day-zero attack (a threat for which no patch has been written). CSA features include a built-in IPS, malicious mobile code protection, OS patch assurance, and audit logs.
Network Admission Control (NAC), formerly called Cisco Clean Access, allows administrators to authenticate, authorize, evaluate, and remediate wired and wireless users prior to allowing the users on the network. It can quarantine and prevent noncompliant end stations from accessing the network until they achieve security policy compliance.
Finally, the security Monitoring, Analysis, and Response System (MARS) provides security monitoring for security devices and host applications. It offers event aggregation, device discovery, compliance reporting, and notifications. Using MARS can greatly assist with analysis and response of threats on your network.
Although no one can claim to secure your network entirely, Cisco has made great strides with its self-defending network solutions to give you peace of mind that your network is guarded and protected against most current and future threats.
With all the attacks occurring today, it may be tough to know where to begin protecting your network. No matter what your level of experience is with Cisco routers, there are a few basic best practices that you should use whenever setting up a new Cisco router. These include the following:
Use SSH instead of Telnet.
Configure access lists to permit only necessary traffic.
Use difficult passwords that do not use words found in a dictionary.
Use current Cisco IOS Software.
Encrypt all passwords in the configuration.
Disable services that you do not need.
After you have taken these initial steps, you can then decide what additional steps you may need to take to protect your network.