Internet Security Association and Key Management Protocol (ISAKMP)
</objective> <objective>Internet Key Exchange (IKE)
</objective> <objective>Authentication Header (AH)
</objective> <objective>Encapsulating Security Payload (ESP)
</objective> <objective>Virtual Private Networks (VPN)
</objective> </feature><feature><title>Concepts and Techniques You’ll Need to Master:</title> <objective>Components of IPSec VPNs
</objective> <objective>Use of SSL VPNs
</objective> </feature>In Chapter 7, “Introduction to Wide-Area Networks,” you learned about the fundamentals of Wide-Area Networks (WAN). Specifically, you learned about WAN encapsulations such as PPP, HDLC, and Frame Relay. These encapsulations add information to a frame to help the frame get from one end of a WAN to another.
This chapter advances your studies of WANs to include virtual private networking (VPN).
Although Frame Relay and leased lines are the ideal WAN solutions for most organizations, you can opt for an IPSec or Secure Socket Layer (SSL) virtual private network (VPN). Several reasons why you might want to use a secure VPN follow:
Cost savings—. Packet-switched and dedicated leased lines might be too expensive for your organization. With IPSec and SSL VPNs, you can use your existing connection to the Internet for your WAN.
Backup—. If your organization requires high availability, IPSec and SSL VPNs can be used as a backup connection should your primary connection go down.
Security—. If you want an additional layer of security in your organization, you might want to use IPSec or SSL VPNs.
Telecommuters—. For mobile and home users, IPSec and SSL VPNs are the only practical and secure solutions to connect into your organization’s network.
IPSec VPNs use a suite of IP security protocols to provide a means of securing TCP/IP communication. SSL VPNs use secure HTTP but work only with HTTP traffic. Of course, if that’s all you knew about the two types, the exam would be too easy, and we wouldn’t want that, so let’s take a look at these topics more in depth.
Exam Alert
You do not need to know how to configure IPSec or SSL VPNs for the CCENT or CCNA exam, but you do need to be familiar with how they work—including the reasons why you would use a VPN and its major components.
IPSec provides the following security benefits:
Authentication of every IP packet
Verification of the data integrity for each packet
Confidentiality of your packet payload
Antireplay protection to verify that each packet is unique
To accomplish these benefits, IPSec uses several components, including security protocols, key management exchanges, and security algorithms, as described in Table 15.1.
Table 15.1. IPSec Components
IPSec Component | Description | Examples |
|---|---|---|
Security Protocols | Methods that use security algorithms to secure communications | Authentication Header (AH) Encapsulating Security Payload (ESP) |
Key Management | Responsible for exchanging secret keys that are used in the algorithms to secure IPSec VPNs | Internet Security Association and Key Management Protocol (ISAKMP) Internet Key Exchange (IKE) Secure Key Exchange Mechanism (SKEME) Oakley |
Security Algorithms | The mathematical algorithms used to secure communications | Data Encryption Standard (DES) Triple DES (3DES) Advanced Encryption Standard (AES) Message Digest 5 (MD5) Secure Hashing Algorithm (SHA-1) |
The security protocols include encapsulating security payload (ESP) and authentication header (AH). Both define the headers (and, in the case of ESP, the trailers) involved when securing your communications. ESP provides confidentiality, integrity, origin authentication, and antireplay (for more on these terms, see Chapter 9, “Basic Network Security”). AH does not provide confidentiality but does provide integrity, origin authentication, and optional partial sequence integrity for antireplay.
Note
ESP uses IP protocol 50 and AH uses IP protocol 51. Make sure you have these protocols allowed through your firewall. Remember, these are IP protocols and not port numbers.
The headers and trailers used with ESP and AH depend on whether you use your VPN in tunnel mode or transport mode. If you want to create a VPN between two networks, use tunnel mode. Tunnel mode is usually configured between a VPN appliance such as a router with VPN capabilities, Adaptive Security Appliance (ASA), or VPN Concentrator. If you want to protect two hosts, such as the communication between two servers on a network, use transport mode.
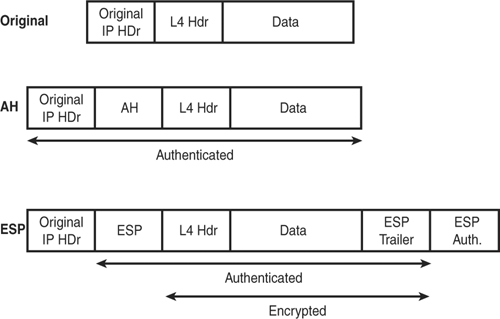
Figure 15.1 shows how your IP packet has new headers and trailers when using AH and ESP in transport mode. AH adds a header between the original IP header and the Layer 4 (TCP or UDP) header. AH uses a mathematical process called hashing that is used for authentication. The process is similar to how police use fingerprints. A fingerprint is a small representation of who you are that can be used to verify your identity. In the same way, AH takes a fingerprint of your entire packet that is verified on the receiving side. The same mathematical process is run on both sides, and if the result is the same on both the sending and receiving sides, the message is considered authenticated.
In comparison, ESP adds a new ESP header and ESP trailer that encrypt your packet. Notice that the original IP header is not changed with transport mode. The ESP authentication trailer is added to the end, which works the same way as the AH header by authenticating the packet.
Figure 15.2 shows how your IP packet has new headers and trailers when using AH and ESP in tunnel mode. Recall that tunnel mode is used when protecting communication between two gateways. The big difference between transport mode and tunnel mode from a technical standpoint is that with tunnel mode the IP packet is encapsulated into another packet by adding a new IP header that is removed on arrival at the VPN gateway endpoint. This is a lot like transporting your car on a ferry boat. The original payload in your car does not change, but now you have a new means of transport. When you get to the destination, your car will get off the ferry boat and you resume driving. In the same way, when your packet gets to the far end destination, it strips off the new tunnel header and resumes communication as the original IP packet.
The headers used with ESP and AH rely on mathematical algorithms to secure your communication. If every implementation used the same variables in its formula, you would get the same mathematical result every time you sent the same data packet. This obviously would not be secure, so to ensure uniqueness with your IPSec implementation, a secret key can be used that acts as a unique variable during the mathematical process so that the results are different with each implementation of IPSec. This key is called a shared key because both VPN endpoints use the same key. Keeping this key secret is important, just as it is to keep the key to your house protected. It doesn’t matter how many locks you have on your house, if people have access to your key, they can get into your home.
IPSec uses the Internet Key Exchange (IKE) to periodically exchange your secret keys. IKE uses UDP 500, so make sure you have that port unfiltered on your external firewalls to allow IKE to communicate. IKE encompasses three components:
The details of how each of these works is outside the scope of the exam. Do know, however, that Diffie-Helman (DH) is the algorithm used within IKE to generate and exchange secret keys. The DH algorithm uses its own set of keys to secure the exchange of keys used for secure IPSec communication. Think of it as storing a key within a locked box. You need to unlock the box with a different key to get to the key inside the box.
Unlike IPSec shared keys, Diffie-Helman uses public key cryptography where each VPN tunnel endpoint has its own public and private key. You do not need to be familiar with the inner workings of public key cryptography for the CCNA exam; that is covered in the professional certification tracks such as Cisco Certified Network Professional (CCNP) and Cisco Certified Security Professional (CCSP).
The last components of IPSec VPNs are the security algorithms used. You need to be aware of two types of security algorithms:
Encryption algorithms—. Provide confidentiality of your data. Encryption algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES).
Message integrity algorithms—. Provide you with authentication and integrity. Message integrity algorithms include Message Digest 5 (MD5) and Secure Hashing Algorithm (SHA-1).
These security algorithms do have a trade-off in that although they secure your communication, they also require processing power, and their encryption overhead can reduce the amount of actual throughput you get on your network. Still, the cost-savings, security, and flexibility you get with IPSec VPNs are attractive to many network managers.
All the components of IPSec can make VPNs complicated. A simpler alternative is to use Secure Socket Layer (SSL) VPNs. SSL is used frequently to secure Hypertext Transfer Protocol (HTTP) traffic, such as when you access a secure e-commerce site. Many organizations use HTTP for internal intranets and for thin client communication. With the Cisco Web VPN solution, users can authenticate first to a Cisco Adaptive Security Appliance (ASA) via a secure web interface before being allowed access to web applications. These are easy for end users and administrators but have the disadvantage of working only with webbased applications.