Chapter 1 WLAN Security Overview
IN THIS CHAPTER, YOU WILL LEARN ABOUT THE FOLLOWING:
The future of 802.11 security
The 802.11-2012 standard defines wireless local area network (WLAN) technology, including all Layer 2 security mechanisms. To better understand WLAN security, you need to have a general appreciation of computer security and the components that are used to provide computer security. Security should never be taken lightly for wired or wireless networks. Since the early days of Wi-Fi communications, there has been a concern about the ability to transmit data securely over a wireless medium and properly protect wired network resources. This concern is as valid now as it was in 1997 when 802.11 was introduced. The difference between then and now is that the technologies and standards for Wi-Fi communications are much more secure and easier to implement. In addition to the standards providing better WLAN security, the people who are installing and managing these networks are much more knowledgeable about the design and implementation of secure wireless networks.
In 2004, the 802.11i amendment was ratified by the IEEE, defining stronger encryption and better authentication methods. The 802.11i amendment, which is now part of the 802.11-2012 standard, fully defines a robust security network (RSN), which is discussed later in this chapter. If proper encryption and authentication solutions are deployed, a wireless network can be as secure as, if not more secure than, the wired segments of a network.
Before you learn about the various wireless security methods, techniques, and tools, it is important to learn some of the basic terms and concepts of encryption and computer security. WLAN security is based on many of the same concepts and principles as hard-wired systems, with the main difference being the natural reduced security of the unbounded medium (RF waves) that is used in wireless communications. Because data is transmitted freely and openly in the air, proper protection is needed to ensure data privacy. Thus strong encryption is needed.
The function of most wireless networks is to provide a portal into some other network infrastructure, such as an 802.3 Ethernet backbone. The wireless portal must be protected, and therefore an authentication solution is needed to ensure that only authorized users can pass through the portal via a wireless access point. After users have been authorized to pass through the wireless portal, virtual local area networks (VLANs) and identity-based mechanisms are needed to restrict access, additionally, to network resources. 802.11 wireless networks can be further protected with continuous monitoring by networking accounting and a wireless intrusion detection system. All of these security components should also be cemented with policy enforcement.
In this chapter we will explore the basic terminology of WLAN security. We will discuss the organizations that create the standards, certifications, and recommendations that help guide and direct wireless security. In addition, you will learn about these wireless security standards and certifications.
Standards Organizations
Each of the standards organizations discussed in this chapter helps guide a different aspect of security that is used in wireless networking.
The International Organization for Standardization (ISO) created the Open Systems Interconnection (OSI) model, which is an architectural model for data communications.
The Institute of Electrical and Electronics Engineers (IEEE) creates standards for compatibility and coexistence between networking equipment, not just wireless networking equipment. However, in this book we are concerned primarily with its role in wireless networking and more specifically wireless security.
The Internet Engineering Task Force (IETF) is responsible for creating Internet standards. Many of these standards are integrated into the wireless networking and security protocols and standards.
The Wi-Fi Alliance performs certification testing to make sure wireless networking equipment conforms to interoperable WLAN communication guidelines, which are similar to the IEEE 802.11-2012 standard.
You will look at each of these organizations in the following sections.
International Organization for Standardization (ISO)
The International Organization for Standardization, or ISO, is a global, nongovernmental organization that identifies business, government, and society needs and develops standards in partnership with the sectors that will put them to use. The ISO is responsible for the creation of the Open Systems Interconnection (OSI) model, which has been a standard reference for data communications between computers since the late 1970s.
The OSI model is the cornerstone of data communications. Becoming familiar with it is one of the most important and fundamental tasks a person in the networking industry can undertake.
The layers of the OSI model are as follows:
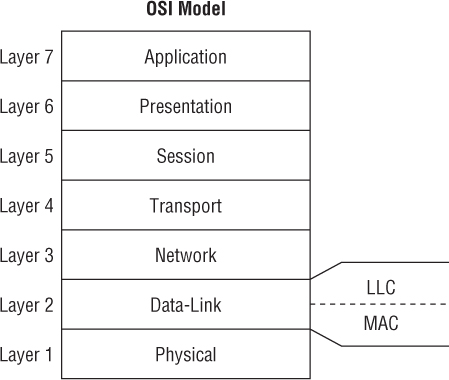
The IEEE 802.11-2012 standard defines communication mechanisms only at the Physical layer and the MAC sublayer of the Data-Link layer of the OSI model. By design, the 802.11 standard does not address the upper layers of the OSI model, although there are interactions between the 802.11 MAC layer and the upper layers for parameters such as quality of service (QoS).
TIP
You should have a working knowledge of the OSI model for both this book and the CWSP exam. Make sure you understand the seven layers of the OSI model and how communication takes place at the different layers. If you are not comfortable with the concepts of the OSI model, spend some time reviewing it on the Internet or from a good networking fundamentals book prior to taking the CWSP exam. More information about the ISO can be found at www.iso.org.
Institute of Electrical and Electronics Engineers (IEEE)
The Institute of Electrical and Electronics Engineers, commonly known as the IEEE, is a global professional society with more than 400,000 members. The IEEE’s mission is to “foster technological innovation and excellence for the benefit of humanity.” To networking professionals, that means creating the standards that we use to communicate.
The IEEE is probably best known for its LAN standards, the IEEE 802 project. IEEE projects are subdivided into working groups to develop standards that address specific problems or needs. For instance, the IEEE 802.3 working group was responsible for the creation of a standard for Ethernet, and the IEEE 802.11 working group was responsible for creating the WLAN standard. The numbers are assigned as the groups are formed, so the 11 assigned to the wireless group indicates that it was the 11th working group formed under the IEEE 802 project. IEEE 802.11, more commonly referred to as Wi-Fi, is a standard technology for providing local area network (LAN) communications using radio frequencies (RF). The IEEE designates the 802.11-2012 standard as the most current guideline to provide operational parameters for WLANs.
As the need arises to revise existing standards created by the working groups, task groups are formed. These task groups are assigned a sequential single letter (multiple letters are assigned if all single letters have been used) that is added to the end of the standard number (for example, 802.11g, 802.11i, and 802.3at). Some letters are not assigned. For example, o and l are not assigned to prevent confusion with the numbers 0 and 1. Other letters may not be assigned to task groups to prevent confusion with other standards. For example, 802.11x has not been assigned because it can be easily confused with the 802.1X standard and because 802.11x has become a common casual reference to the 802.11 family of standards.
NOTE
More information about the IEEE can be found at www.ieee.org.
It is important to remember that the IEEE standards, like many other standards, are written documents describing how technical processes and equipment should function. Unfortunately, this often allows for different interpretations when the standard is being implemented, so it is common for early products to be incompatible between vendors, as was the case with early 802.11 products.
NOTE
The CWSP exam is based on the most recently published version of the standard, 802.11-2012. The 802.11-2012 standard can be downloaded from http://standards.ieee.org/getieee802/802.11.html.
Internet Engineering Task Force (IETF)
The Internet Engineering Task Force, commonly known as the IETF, is an international community of people in the networking industry whose goal is to make the Internet work better. The mission of the IETF, as defined by the organization in a document known as RFC 3935, is “to produce high quality, relevant technical and engineering documents that influence the way people design, use, and manage the Internet in such a way as to make the Internet work better. These documents include protocol standards, best current practices, and informational documents of various kinds.” The IETF has no membership fees, and anyone may register for and attend an IETF meeting.
The IETF is one of five main groups that are part of the Internet Society (ISOC). The ISOC groups include the following:
Internet Engineering Task Force (IETF)
Internet Architecture Board (IAB)
Internet Corporation for Assigned Names and Numbers (ICANN)
Internet Engineering Steering Group (IESG)
Internet Research Task Force (IRTF)
The IETF is broken into eight subject matter areas: Applications, General, Internet, Operations and Management, Real-Time Applications and Infrastructure, Routing, Security, and Transport. Figure 1.1 shows the hierarchy of the ISOC and a breakdown of the IETF subject matter areas.
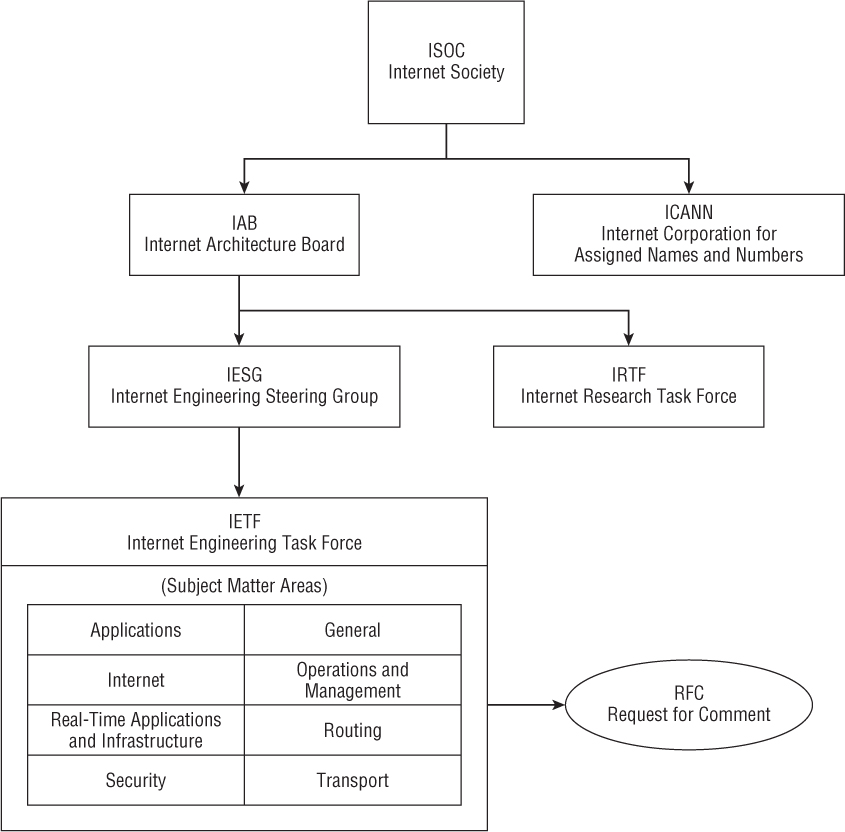
The IESG provides technical management of the activities of the IETF and the Internet standards process. The IETF is made up of a large number of groups, each addressing specific topics. An IETF working group (WG) is created by the IESG and is given a specific charter or topic to address. There is no formal voting process for the working groups. Decisions in working groups are made by rough consensus, or basically a general sense of agreement among the working groups.
The results of a working group are usually the creation of a document known as a Request for Comment (RFC). Contrary to its name, an RFC is not actually a request for comment, but a statement or definition. Most RFCs describe network protocols, services, or policies and may evolve into an Internet standard. RFCs are numbered sequentially, and once a number is assigned it is never reused. RFCs may be updated or supplemented by higher numbered RFCs. As an example, Mobile IPv4 is described in RFC 3344 and updated in RFC 4721. In 2012, RFC 5944 made RFC 3344 obsolete. At the top of the RFC document, it states whether it is updated by another RFC and also if it makes any other RFCs obsolete.
Not all RFCs are standards. Each RFC is given a status, relative to its relationship with the Internet standardization process: Informational, Experimental, Standards Track, or Historic. If it is a Standards Track RFC, it could be a Proposed Standard, Draft Standard, or Internet Standard. When an RFC becomes a standard, it still keeps its RFC number, but it is also given an “STD xxxx” label. The relationship between the STD numbers and the RFC numbers is not one to one. STD numbers identify protocols whereas RFC numbers identify documents.
Many of the protocol standards, best current practices, and informational documents produced by the IETF affect WLAN security. In Chapter 4, “802.1X/EAP Authentication,” you will learn about the many varieties of the Extensible Authentication Protocol (EAP) that are defined by the IETF RFC 3748.
NOTE
More information about the IETF can be found at www.ietf.org.
Wi-Fi Alliance
The Wi-Fi Alliance is a global, nonprofit industry association of about 600 member companies devoted to promoting the growth of WLANs. One of the primary tasks of the Wi-Fi Alliance is to market the Wi-Fi brand and raise consumer awareness of new 802.11 technologies as they become available. Because of the Wi-Fi Alliance’s overwhelming marketing success, the majority of the worldwide Wi-Fi users are likely to recognize the Wi-Fi logo seen in Figure 1.2.
FIGURE 1.2 Wi-Fi Alliance logo

The Wi-Fi Alliance’s main task is to ensure the interoperability of WLAN products by providing certification testing. During the early days of the 802.11 standard, the Wi-Fi Alliance further defined some of the ambiguous standards requirements and provided a set of guidelines to ensure compatibility between different vendors. This is still done to help simplify the complexity of the standards and to ensure compatibility. As seen in Figure 1.3, products that pass the Wi-Fi certification process receive a Wi-Fi Interoperability Certificate that provides detailed information about the individual product’s Wi-Fi certifications.
FIGURE 1.3 Wi-Fi Interoperability Certificate
The Wi-Fi Alliance, originally named the Wireless Ethernet Compatibility Alliance (WECA), was founded in August 1999. The name was changed to the Wi-Fi Alliance in October 2002.
The Wi-Fi Alliance has certified more than 25,000 Wi-Fi products for interoperability since testing began in April 2000. Multiple Wi-Fi CERTIFIED programs exist that cover basic connectivity, security, quality of service (QoS), and more. Testing of vendor Wi-Fi products is performed in independent authorized test laboratories worldwide. A listing of these testing laboratories can be found on the Wi-Fi Alliance’s website. The guidelines for interoperability for each Wi-Fi CERTIFIED program are usually based on key components and functions that are defined in the IEEE 802.11-2012 standard and various 802.11 amendments. In fact, many of the same engineers who belong to 802.11 task groups are also contributing members of the Wi-Fi Alliance. However, it is important to understand that the IEEE and the Wi-Fi Alliance are two separate organizations. The IEEE 802.11 task group defines the WLAN standards, and the Wi-Fi Alliance defines interoperability certification programs. The Wi-Fi CERTIFIED programs include the following:
Core Technology & Security The core technology and security program certifies 802.11a, b, g, n, and/or ac interoperability to ensure that the essential wireless data transmission works as expected. Each device is tested according to its capabilities. Table 1.1 lists the five different core Wi-Fi transmission technologies along with the frequencies and maximum data rate that each is capable of.
TABLE 1.1 Five generations of Wi-Fi
Wi-Fi technology |
Frequency band |
Maximum data rate |
802.11a |
5 GHz |
54 Mbps |
802.11b |
2.4 GHz |
11 Mbps |
802.11g |
2.4 GHz |
54 Mbps |
802.11n |
2.4 GHz, 5 GHz, 2.4 or 5 GHz (selectable), or 2.4 and 5 GHz (concurrent) |
450 Mbps |
802.11ac |
5 GHz |
1.3 Gbps |
Each certified product is required to support one frequency band as a minimum, but it can support both. The CWSP exam will not use the terms 802.11 a/b/g/n/ac; however, the a/b/g/n/ac terminology is commonplace within the industry because of the Wi-Fi Alliance certifications.
NOTE
Although 802.11n specifies data rates of up to 600 Mbps and 802.11ac specifies data rates of up to 6.93 Gbps, as of this writing, equipment to support these maximum data rates had not been developed yet. Therefore, the Wi-Fi certification tests do not test up to the maximum 802.11n or 802.11ac specified data rates.
In addition to having the required transmission capabilities, each device must support robust security network (RSN) capabilities, security mechanisms that were originally defined in the IEEE 802.11i amendment. Devices must support Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access 2 (WPA2) security mechanisms for personal (WPA2-Personal) or enterprise (WPA2-Enterprise) environments. Additionally, enterprise devices must support Extensible Authentication Protocol (EAP), which is used to validate the identity of the wireless device or user. In 2012, support for Protected Management Frames extended WPA2 protection to unicast and multicast management action frames.
Wi-Fi Multimedia Wi-Fi Multimedia (WMM) is based on the QoS mechanisms that were originally defined in the IEEE 802.11e amendment. WMM enables Wi-Fi networks to prioritize traffic generated by different applications. In a network where WMM is supported by both the access point and the client device, traffic generated by time-sensitive applications such as voice or video can be prioritized for transmission on the half-duplex RF medium. WMM certification is mandatory for all core certified devices that support 802.11n. WMM certification is optional for core certified devices that support 802.11 a, b, or g.
WMM Power Save WMM Power Save (WMM-PS) helps conserve battery power for devices using Wi-Fi radios by managing the time the client device spends in sleep mode. Conserving battery life is critical for handheld devices such as barcode scanners and voice over Wi-Fi (VoWiFi) phones. To take advantage of power-saving capabilities, both the device and the access point must support WMM Power Save.
Wi-Fi Protected Setup Wi-Fi Protected Setup defines simplified and automatic WPA and WPA2 security configurations for home and small-business users. Users can easily configure a network with security protection by using a personal identification number (PIN) or a button located on the access point and the client device. This technology is defined in the Wi-Fi Simple Configuration Technical Specification.
Wi-Fi Direct Wi-Fi Direct enables Wi-Fi devices to connect directly without the use of an access point, making it easier to print, share, sync, and display. Wi-Fi Direct is ideal for mobile phones, cameras, printers, PCs, and gaming devices needing to establish a one-to-one connection, or even for connecting a small group of devices. Wi-Fi Direct is simple to configure (in some cases as easy as pressing a button), provides the same performance and range as other Wi-Fi CERTIFIED devices, and is secured using WPA2 security. This technology is defined in the Wi-Fi Peer-to-Peer Services Technical Specification.
Converged Wireless Group-RF Profile Converged Wireless Group-RF Profile (CWG-RF) was developed jointly by the Wi-Fi Alliance and the Cellular Telecommunications and Internet Association (CTIA), now known as The Wireless Association. CWG-RF defines performance metrics for Wi-Fi and cellular radios in a converged handset to help ensure that both technologies perform well in the presence of the other. All CTIA-certified handsets now include this certification.
Voice Personal Voice Personal offers enhanced support for voice applications in residential and small-business Wi-Fi networks. These networks include one access point, mixed voice and data traffic from multiple devices (such as phones, PCs, printers, and other consumer electronic devices), and support for up to four concurrent phone calls. Both the access point and the client device must be certified to achieve performance matching the certification metrics.
Voice Enterprise Voice Enterprise offers enhanced support for voice applications in enterprise Wi-Fi networks. Enterprise-grade voice equipment must provide consistently good voice quality under all network load conditions and coexist with data traffic. Both access point and client devices must support prioritization using WMM, with voice traffic being placed in the highest-priority queue (Access Category Voice, AC_VO). Voice Enterprise equipment must also support seamless roaming between access points (APs), WPA2-Enterprise security, optimization of power through the WMM-Power Save mechanism, and traffic management through WMM-Admission Control.
Tunneled Direct Link Setup Tunneled Direct Link Setup (TDLS) enables devices to establish secure links directly with other devices after they have joined a traditional Wi-Fi network. This will allow consumer devices such as TVs, gaming devices, smartphones, cameras, and printers to communicate quickly, easily, and securely between each other.
Passpoint Passpoint is designed to revolutionize the end-user experience when connecting to Wi-Fi hotspots. This is done by allowing security identity module (SIM) and non-SIM mobiles devices to automatically identify a Wi-Fi network and connect to it, automatically authenticating the user to the network using Extensible Authentication Protocol (EAP), and providing secure transmission using WPA2-Enterprise encryption. Passpoint is also known as Hotspot 2.0. Passpoint has also been specified by the Wireless Broadband Alliance and the GSMA Terminal Steering Group.
WMM-Admission Control WMM-Admission Control allows Wi-Fi networks to manage network traffic based on channel conditions, network traffic load, and type of traffic (voice, video, best effort data, or background data). The access point allows only the traffic that it can support to connect to the network, based on the available network resources. This allows users to confidently know that, when the connection is established, the resources will be there to maintain it.
IBSS with Wi-Fi Protected Setup IBSS with Wi-Fi Protected Setup provides easy configuration and strong security for ad hoc (peer-to-peer) Wi-Fi networks. This is designed for mobile products and devices that have a limited user interface, such as smartphones, cameras, and media players. Features include easy push button or PIN setup, task-oriented short-term connections, and dynamic networks that can be established anywhere.
Miracast Miracast seamlessly integrates the display of streaming video content between devices. Wireless links are used to replace wired connections. Devices are designed to identify and connect with each other, manage their connections, and optimize the transmission of video content. It provides wired levels of capabilities but the portability of Wi-Fi. Miracast provides 802.11n performance, ad hoc connections via Wi-Fi Direct, and WPA2 security. This technology is defined in the Wi-Fi Display Technical Specification.
Wi-Fi Aware Wi-Fi Aware provides a real-time and energy-efficient discovery mechanism for Wi-Fi devices to discover other devices and services within its proximity. It is designed as an enabling technology for personalized social, local, and mobile applications and services, and is optimized to work well even in crowded environments.
As 802.11 technologies evolve, new Wi-Fi CERTIFIED programs will be detailed by the Wi-Fi Alliance.
802.11 Networking Basics
In addition to understanding the OSI model and basic networking concepts, you must broaden your understanding of many other networking technologies in order to design, deploy, and administer an 802.11 wireless network properly. For instance, when administering an Ethernet network, you typically need a comprehension of TCP/IP, bridging, switching, and routing. The skills to manage an Ethernet network will also aid you as a WLAN administrator, because most 802.11 wireless networks act as “portals” into wired networks. The IEEE defines the 802.11 communications at the Physical layer and the MAC sublayer of the Data-Link layer.
To understand the 802.11 technology completely, you need to have a clear concept of how wireless technology works at the Physical layer of the OSI model, and at the heart of the Physical layer is radio frequency (RF) communications. A clear concept of how wireless works at the second layer of the OSI model is also needed. The 802.11 Data-Link layer is divided into two sublayers. The upper portion is the IEEE 802.2 Logical Link Control (LLC) sublayer, which is identical for all 802-based networks, although not used by all of them. The bottom portion of the Data-Link layer is the Media Access Control (MAC) sublayer, which is identical for all 802.11-based networks. The 802.11-2012 standard defines operations at the MAC sublayer.
NOTE
Because the main focus of this study guide is WLAN security, it is beyond the scope of this book to discuss general 802.11 networking topics in great detail. For a broad overview of 802.11 technology, we suggest CWNA: Certified Wireless Network Administrator Official Study Guide: (Exam CWNA-106), by David D. Coleman and David A. Westcott (Sybex, 2014).
If you have ever taken a networking class or read a book about network design, you have probably heard the terms core, distribution, and access when referring to networking architecture. Proper network design is imperative no matter what type of network topology is used. The core of the network is the high-speed backbone or the superhighway of the network. The goal of the core is to carry large amounts of information between key data centers or distribution areas, just as superhighways connect cities and metropolitan areas.
The core layer does not route traffic or manipulate packets but rather performs high-speed switching. Redundant solutions are usually designed at the core layer to ensure fast and reliable delivery of packets. The distribution layer of the network routes or directs traffic toward the smaller clusters of nodes or neighborhoods of the network.
The distribution layer routes traffic between virtual LANs (VLANs) and subnets. The distribution layer is akin to the state and county roads that provide medium travel speeds and distribute the traffic within a city or metropolitan area.
The access layer of the network is responsible for a delivery of the traffic directly to the end user or end node. The access layer mimics the local roads and neighborhood streets that are used to reach your final address; thus the speed of delivery in this layer is slower than at the core and distribution layers. (Remember that speed is a relative concept.) The access layer ensures the final delivery of packets to the end user.
Because of traffic load and throughput demands, speed and throughput capabilities increase as data moves from the access layer to the core layer. Additional speed and throughput tend to also mean higher cost.
Just as it would not be practical to build a superhighway so that traffic could travel between your neighborhood and the local school, it would not be practical or efficient to build a two-lane road as the main thoroughfare to connect two large cities such as New York and Boston. These same principles apply to network design. Each of the network layers—core, distribution, and access—are designed to provide a specific function and capability to the network. It is important to understand how wireless networking fits into this network design model.
Wireless networking can be implemented as either point-to-point or point-to-multipoint solutions. Most wireless networks are used to provide network access to the individual client stations and are designed as point-to-multipoint networks. This type of implementation is designed and installed on the access layer, providing connectivity to the end user. 802.11 wireless networking is most often implemented at the access layer. In Chapter 8, “WLAN Security Infrastructure,” you will learn about the evolution of WLAN architecture from the early days of autonomous APs to the many hybrid architectures that exist today. Security design and deployment considerations are unique between autonomous, centralized, and distributed WLAN architecture. Various components of these architectures exist between the core/distribution and access layers.
Wireless bridge links are generally used to provide connectivity between buildings in the same way that county or state roads provide distribution of traffic between neighborhoods. The purpose of wireless bridging is to connect two separate, wired networks wirelessly. Routing data traffic between networks is usually associated with the distribution layer. Wireless bridge links cannot typically meet the speed or distance requirements of the core layer, but they can be very effective at the distribution layer. An 802.11 bridge link is an example of wireless technology being implemented at the distribution layer.
Throughout this study guide, you will learn how to provide proper 802.11 wireless security integration at the access, distribution, and core layers of network design.
802.11 Security Basics
When you are securing a wireless 802.11 network, five major components are typically required:
Data privacy
Authentication, authorization, and accounting (AAA)
Segmentation
Monitoring
Policy
Because data is transmitted freely and openly in the air, proper protection is needed to ensure data privacy, so strong encryption is needed. The function of most wireless networks is to provide a portal into some other network infrastructure, such as an 802.3 Ethernet backbone. The wireless portal must be protected, and therefore an authentication solution is needed to ensure that only authorized users can pass through the portal via a wireless AP. After users have been authorized to pass through the wireless portal, VLANs and identity-based mechanisms are needed to further restrict access to network resources. Interim accounting along with RADIUS change of authorization (CoA) can be used to monitor the user’s connection and authorization, and dynamically change the user’s access to network resources. 802.11 wireless networks can be further protected with continuous monitoring by a wireless intrusion detection system. All of these security components should also be cemented with policy enforcement. If properly implemented, these five components of 802.11 security discussed throughout this book will lay a solid foundation for protecting your WLAN.
Data Privacy
The history of secure communications is as old as the history of communications itself. Sharing ideas and thoughts with specific people but not others is a natural human desire. The task of sharing a thought is easy when the person you want to share it with is nearby. A quiet, private conversation is often all that is needed to do this. Sharing an idea in a secure way starts to become a problem when you need to send your message over a longer distance. Whether you have to yell the message to the other person from a distance, send it to the other person via a courier, or write it down on a piece of paper and send it, all of these methods run a risk of being intercepted. Because of these types of risks, methods of encrypting or encoding messages were created. The goal of encrypting a message, even if it is overheard or intercepted, is for it to be legible only to the person who created the message and the person for whom the message is intended—or at least, that is the intent.
802.11 wireless networks operate in license-free frequency bands, and all data transmissions travel in the open air. Protecting data privacy in a wired network is much easier because physical access to the wired medium is more restricted. However, physical access to wireless transmissions is available to anyone in listening range. Therefore, using cipher encryption technologies to obscure information is mandatory to provide proper data privacy in wireless networks. A cipher is an algorithm used to perform encryption.
Along with the desire by some to keep things a secret, there is often an equal desire by others to reveal these secrets. The techniques needed to encrypt and decrypt information form the science known as cryptology. As you would expect, the science of cryptology uses specific words and phrases, many of which you will learn about in this section.
The term cryptology is derived from the Greek language and translates to mean “hidden word.” The goal of cryptology is to take a piece of information, often referred to as plaintext, and, using a process or algorithm, also referred to as a key or cipher, transform the plaintext into encrypted text, also known as ciphertext. The process of encrypting plaintext is shown in Figure 1.4. This ciphertext could then only be decrypted, converted back into plaintext, by someone who knows the key or cipher. The process of decrypting the ciphertext is shown in Figure 1.5.
FIGURE 1.4 The encryption process
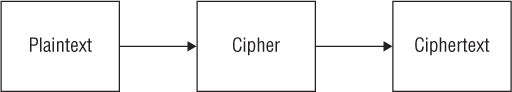
FIGURE 1.5 The decryption process

TIP
When a plaintext message is encrypted, the encrypted message is referred to as ciphertext. A detailed discussion about encryption methods used for WLAN security can be found in Chapter 3, “Encryption Ciphers and Methods.”
When discussing cryptology, it is important to use the term cipher instead of code, as a code is simply a way of representing information in a different way. For example, the American Standard Code for Information Interchange (ASCII) represents information as letters, numbers, and other characters. Morse code uses dots and dashes to represent letters. Like a code, a cipher also represents information in a different way. However, a cipher uses a secret technique of representing the information in a different way, with this technique known only to a select few.
The science of concealing the plaintext and then revealing it is known as cryptography. In the computer and networking industries, the process of converting plaintext into ciphertext is commonly referred to as encryption, and the process of converting ciphertext back to plaintext is commonly referred to as decryption. The science of decrypting the ciphertext without knowledge of the key or cipher is known as cryptanalysis. If cryptanalysis is successful in decrypting the ciphertext, then that key or cipher is considered to be broken, cracked, or not secure.
The term steganography is also derived from the Greek language and is translated as “concealed writing.” Unlike cryptography, where the goal is to make the message unreadable to someone without access to the key or cipher, steganography strives to hide the fact that there is a message. This is often referred to as “security through obscurity” or “hiding a message in plain sight.” A classic example of using steganography to hide a message is to write a document with the first letter of each sentence or word as the hidden message (see Figure 1.6).
FIGURE 1.6 Steganography example

Steganography is often used for digital watermarking, which embeds an artist or photographer’s information in an image so that ownership can be proven in case someone tries to use the image without permission. Steganography is useful for hiding a message where one would not be expected, which is why it is not used in environments like wireless networking where data communications is the key objective.
Authentication, Authorization, Accounting (AAA)
Authentication, authorization, and accounting (AAA) is a common computer security concept that defines the protection of network resources.
Authentication is the verification of user identity and credentials. Users must identify themselves and present credentials, such as usernames and passwords or digital certificates. More secure authentication systems use multifactor authentication, which requires at least two sets of different credentials to be presented.
Authorization determines if the device or user is authorized to have access to network resources. This can include identifying whether you can have access based on the type of device you are using (laptop, tablet, or phone), time-of-day restrictions, or location. Before authorization can be determined, proper authentication must occur.
Accounting is tracking the use of network resources by users and devices. It is an important aspect of network security, used to keep a historical trail of who used what resource, when, where, and how. A record is kept of user identity, which resource was accessed, and at what time. Keeping an accounting trail is often a requirement of many industry regulations, such as the payment card industry (PCI).
Remember that the usual purpose of an 802.11 wireless network is to act as a portal into an 802.3 wired network. It is therefore necessary to protect that portal with very strong authentication methods so that only legitimate users with the proper credentials will be authorized to access network resources.
Segmentation
Although it is of the utmost importance to secure an enterprise wireless network by utilizing both strong encryption and an AAA solution, an equally important aspect of wireless security is segmentation. Segmentation is the chosen method of separating user traffic within a network. Prior to the introduction of stronger authentication and encryption techniques, wireless was viewed as an untrusted network segment. Therefore, before the ratification of the 802.11i security amendment, the entire wireless segment of a network was commonly treated as the untrusted segment and the wired 802.3 network was considered the trusted segment.
Now that better security solutions exist, properly secured WLANs are more seamlessly and securely integrated into the wired infrastructure. It is still important to separate users and devices into proper groups, much like what is done on any traditional network. Once authorized onto network resources, users and devices can be further restricted as to what resources may be accessed and where they can go. Segmentation can be achieved through a variety of means, including firewalls, routers, VPNs, VLANs, and encapsulation or tunneling techniques; such as generic routing encapsulation (GRE). The most common wireless segmentation strategy used in 802.11 enterprise WLANs is segmentation using virtual LANs (VLANs). Encapsulation is heavily used to transport data between infrastructure devices in enterprise WLAN environments. Segmentation is also intertwined with role-based access control (RBAC), which is discussed in Chapter 9, “RADIUS and LDAP.”
Monitoring
After you have designed and installed your wireless network, it is important to monitor it. In addition to monitoring it to make sure that it is performing up to your expectations and those of your users, it may be necessary to constantly monitor it for attacks and intrusions. Similar to a business placing a video camera on the outside of its building to monitor the traffic going in and out of a locked door, it is important for the wireless network administrator to monitor the wireless traffic of a secured network. To monitor potentially malicious wireless activity on your network, you should install a wireless intrusion detection system (WIDS). WLAN security monitoring can be an integrated solution or an overlay solution. Network management solutions that include WLAN security monitoring can be cloud based or run on a private data center server.
In addition to a WIDS, you could implement a wireless intrusion prevention system (WIPS). Both WIDSs and WIPSs have the ability to classify valid and invalid devices on the network. WIPSs can also mitigate attacks from rogue access points and rogue clients by performing attacks against the rogue devices, effectively disabling their ability to communicate with your network. WIPSs will be discussed in detail in Chapter 14, “Wireless Security Monitoring.”
Policy
Securing a wireless network and monitoring for threats are absolute necessities, but both are worthless unless proper security policies are in place. What good is an 802.1X/EAP solution if the end users share their passwords? Why purchase an intrusion detection system if a policy has not been established for dealing with rogue access points? WLAN security policies must be clearly defined and enforced to solidify the effectiveness of all WLAN security components.
In most countries, mandated regulations exist for protecting and securing data communications within all government agencies. In the United States, the National Institute of Standards and Technology (NIST) maintains the Federal Information Processing Standards (FIPS). Of special interest to wireless security is the FIPS 140-2 standard, which defines security requirements for cryptography modules. Additionally, other legislation and regulations exist for protecting information and communications in certain industries such as healthcare and banking. WLAN policy enforcement is needed to meet compliance mandates set forth by these regulations. Policies and compliance regulations will be discussed in greater detail in Chapter 15, “Wireless Security Policies.”
802.11 Security History
From 1997 to 2004, not much was defined in terms of security in the original IEEE 802.11 standard. Two key components of any wireless security solution are data privacy (encryption) and authentication (identity verification). For seven years, the only defined method of encryption in an 802.11 network was the use of 64-bit static encryption called Wired Equivalent Privacy (WEP).
WEP encryption has long been cracked and is not considered an acceptable means of providing data privacy. The original 802.11 standard defined two methods of authentication. The default method is Open System authentication, which verifies the identity of everyone regardless. Another defined method is called Shared Key authentication, which opens up a whole new can of worms and potential security risks. Outdated 802.11 security mechanisms will be discussed in detail in Chapter 2, “Legacy 802.11 Security.”
802.11i Security Amendment and WPA Certifications
The 802.11i amendment, which was ratified and published as IEEE Std. 802.11i-2004, defined stronger encryption and better authentication methods. The 802.11i amendment defined a robust security network (RSN). The intended goal of an RSN was to hide the data flying through the air better while at the same time placing a bigger guard at the front door. The 802.11i security amendment was without a doubt one of the most important enhancements to the original 802.11 standard because of the seriousness of properly protecting a wireless network. The major security enhancements addressed in the 802.11i amendment are as follows:
Enhanced Data Privacy Confidentiality needs have been addressed in 802.11i with the use of a stronger encryption method called Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP), which uses the Advanced Encryption Standard (AES) algorithm. The encryption method is often abbreviated as CCMP/AES, AES CCMP, or often just CCMP. The 802.11i supplement also defines an optional encryption method known as Temporal Key Integrity Protocol (TKIP), which uses the ARC4 stream cipher algorithm and is basically an enhancement of WEP encryption. It should be noted that TKIP is essentially being phased out. The IEEE and Wi-Fi Alliance mandate the use of only CCMP encryption for 802.11n and 802.11ac data rates.
Enhanced Authentication 802.11i defines two methods of authentication using either an IEEE 802.1X authorization framework or preshared keys (PSKs). An 802.1X solution requires the use of an Extensible Authentication Protocol (EAP), although the 802.11i amendment does not specify what EAP method to use.
NOTE
In 2004, the 802.11i security amendment was ratified and is now part of the 802.11-2012 standard. All aspects of the 802.11i ratified security amendment can now be found in clause 11 of the 802.11-2012 standard.
The current 802.11-2012 standard defines an enterprise authentication method as well as a method of authentication for home use. The current standard requires the use of an 802.1X/EAP authentication method in the enterprise and the use of a preshared key, technically a passphrase in a small office/home office (SOHO) environment. The 802.11-2012 standard also requires the use of strong, dynamic encryption-key generation methods. CCMP/AES encryption is the default encryption method, whereas TKIP/ARC4 is an optional encryption method.
Prior to the IEEE ratification of the 802.11i amendment, the Wi-Fi Alliance introduced the Wi-Fi Protected Access (WPA) certification as a snapshot of the not-yet-released 802.11i amendment, supporting only TKIP/ARC4 dynamic encryption-key generation. 802.1X/EAP authentication was required in the enterprise, and passphrase authentication was required in a SOHO environment.
After 802.11i was ratified by the IEEE, the Wi-Fi Alliance introduced the Wi-Fi Protected Access 2 (WPA2) certification. WPA2 is a more complete implementation of the 802.11i amendment and supports both CCMP/AES and TKIP/ARC4 dynamic encryption-key generation. 802.1X/EAP authentication is required in the enterprise, and passphrase authentication is required in a SOHO environment. WPA version 1 was considered a preview of 802.11i, whereas WPA version 2 is considered more of a mirror of the 802.11i security amendment. Once again, you should understand that all aspects of the 802.11i ratified security amendment are now defined as part of the 802.11-2012 standard. Table 1.2 compares the various security standards and certifications.
TABLE 1.2 Security standards and certifications
802.11 standard |
Wi-Fi Alliance certification |
Authentication method |
Encryption method |
Cipher |
Key generation |
802.11 legacy |
No Certification |
Open System or Shared Key |
WEP |
ARC4 |
Static |
|
WPA-Personal |
WPA Passphrase (also known as WPA PSK and WPA Pre-Shared Key) |
TKIP |
ARC4 |
Dynamic |
|
WPA-Enterprise |
802.1X/EAP |
TKIP |
ARC4 |
Dynamic |
802.11-2012 |
WPA2-Personal |
WPA2 Passphrase (also known as WPA2 PSK and WPA2 Pre-Shared Key) |
CCMP (mandatory) |
AES (mandatory) |
Dynamic |
|
|
|
TKIP (optional) |
ARC4 (optional) |
Dynamic |
802.11-2012 |
WPA2-Enterprise |
802.1X/EAP |
CCMP (mandatory) |
AES (mandatory) |
Dynamic |
|
|
|
TKIP (optional) |
ARC4 (optional) |
Dynamic |
Robust Security Network (RSN)
The 802.11-2012 standard defines what is known as a robust security network (RSN) and robust security network associations (RSNAs). Two stations (STAs) must establish a procedure to authenticate and associate with each other as well as create dynamic encryption keys through a process known as the 4-Way Handshake. This association between two stations is referred to as an RSNA. In other words, any two radios must share dynamic encryption keys that are unique between those two radios. CCMP/AES encryption is the mandated encryption method, whereas TKIP/ARC4 is an optional encryption method. An RSN is a network that allows for the creation of only RSNAs. The 802.11-2012 standard does allow for the creation of pre-robust security network associations (pre-RSNAs) as well as RSNAs. In other words, legacy security measures can be supported in the same basic service set (BSS) along with RSN-security-defined mechanisms. A transition security network (TSN) supports RSN-defined security as well as legacy security such as WEP within the same BSS.
TIP
Robust network security, the 4-Way Handshake, and dynamic encryption are discussed in more detail in Chapter 5, “802.11 Layer 2 Dynamic Encryption Key Generation.”
Summary
This chapter explained the roles and responsibilities of four key organizations involved with wireless security and networking:
ISO
IEEE
IETF
Wi-Fi Alliance
To provide a basic understanding of the relationship between networking fundamentals and 802.11 technologies, we discussed these concepts:
OSI model
Core, distribution, and access
To provide a basic knowledge of data privacy, we introduced some of the basic components of security:
Cryptology
Cryptography
Cryptanalysis
Steganography
Plaintext
Key
Cipher
Ciphertext
Five major components that are typically required to secure an 802.11 network were also discussed:
Data privacy
Authentication, authorization, and accounting (AAA)
Segmentation
Monitoring
Policy
To provide an initial foundation, we reviewed the 802.11 security history, including:
802.11 legacy, WEP
WPA-Personal
WPA-Enterprise
802.11-2012 (RSN) - WPA2-Personal
802.11-2012 (RSN) - WPA2-Enterprise
Exam Essentials
Know the four industry organizations. Understand the roles and responsibilities of the ISO, the IEEE, the IETF, and the Wi-Fi Alliance.
Understand data privacy, AAA, segmentation, monitoring, and policy. Know the five major components typically required to secure a wireless network.
Understand cryptology, cryptography, cryptanalysis, steganography, plaintext, cipher, and ciphertext. Know the definition of each of these security terms, how they relate to each other, and the differences between them.
Know the history of 802.11 security. Know the history of wireless security and the differences between the different IEEE standards and Wi-Fi Alliance certifications.
Review Questions
1. The IEEE 802.11-2012 standard mandates this encryption for robust security network associations and the optional use of which other encryption?
A. WEP, AES
B. IPsec, AES
C. MPPE, TKIP
D. TKIP, WEP
E. CCMP, TKIP
2. What wireless security solutions are defined by Wi-Fi Protected Access? (Choose all that apply.)
A. Passphrase authentication
B. LEAP
C. TKIP/ARC4
D. Dynamic WEP
E. CCMP/AES
3. Which wireless security standards and certifications call for the use of CCMP/AES encryption? (Choose all that apply.)
A. WPA
B. 802.11-2012
C. 802.1X
D. WPA2
E. 802.11 legacy
4. A robust security network (RSN) requires the use of which security mechanisms? (Choose all that apply.)
A. 802.11x
B. WEP
C. IPsec
D. CCMP/AES
E. CKIP
F. 802.1X
5. The Wi-Fi Alliance is responsible for which of the following certification programs? (Choose all that apply.)
A. WPA2
B. WEP
C. 802.11-2012
D. WMM
E. PSK
6. Which sublayer of the OSI model’s Data-Link layer is used for communication between 802.11 radios?
A. LLC
B. WPA
C. MAC
D. FSK
7. What encryption methods are defined by the IEEE 802.11-2012 standard? (Choose all that apply.)
A. 3DES
B. WPA-2
C. SSL
D. TKIP
E. CCMP
F. WEP
8. Which organization is responsible for the creation of documents known as Requests for Comments?
A. IEEE
B. ISO
C. IETF
D. Wi-Fi Alliance
E. RFC Consortium
9. Which of the following is not a standard or amendment created by the IEEE? (Choose all that apply.)
A. 802.11X
B. 802.1x
C. 802.3af
D. 802.11N
E. 802.11g
10. TKIP can be used with which of the following? (Choose all that apply.)
A. WEP
B. WPA-Personal
C. WPA-Enterprise
D. WPA-2 Personal
E. WPA-2 Enterprise
F. 802.11-2012 (RSN)
11. Which of the following is simply a means of representing information in a different way?
A. Cryptography
B. Steganography
C. Encryption
D. Cipher
E. Code
12. What wireless security components are mandatory under WPA version 2? (Choose all that apply.)
A. 802.1X/EAP
B. PEAP
C. TKIP/ARC4
D. Dynamic WEP
E. CCMP/AES
13. An AP advertising an 802.1X/EAP employee SSID along with a guest SSID is considered to be operating what type of network device?
A. Core
B. Distribution
C. Access
D. Network layer
E. Session layer
14. The science of concealing plaintext and then revealing it is known as ___________, and the science of decrypting the ciphertext without knowledge of the key or cipher is known as ____________.
A. encryption, decryption
B. cryptanalysis, cryptology
C. cryptology, cryptanalysis
D. cryptography, cryptanalysis
E. cryptography, steganography
15. What is the chronological order in which the following security standards and certifications were defined?
1. 802.11-2012
2. 802.11i
3. WEP
4. WPA-2
5. WPA
A. 3, 5, 2, 4, 1
B. 3, 2, 5, 4, 1
C. 3, 5, 2, 1, 4
D. 1, 3, 2, 5, 4
E. 1, 3, 5, 4, 2
16. The 802.11 legacy standard defines which wireless security solution?
A. Dynamic WEP
B. 802.1X/EAP
C. 64-bit static WEP
D. Temporal Key Integrity Protocol
E. CCMP/AES
17. These qualifications for interoperability are usually based on key components and functions that are defined in the IEEE 802.11-2012 standard and various 802.11 amendments.
A. Request for Comments
B. Wi-Fi Alliance
C. Federal Information Processing Standards
D. Internet Engineering Task Force
E. Wi-Fi CERTIFIED
18. Which of the following can be used with a wireless network to segment or restrict access to parts of the network? (Choose all that apply.)
A. VLANs
B. WPA-2
C. Firewall
D. 802.11i
E. RBAC
19. 802.1X/EAP is mandatory in which of the following? (Choose all that apply.)
A. WPA SOHO
B. WPA Enterprise
C. WPA-2 SOHO
D. WPA-2 Enterprise
E. WPA2-PSK
20. Monitoring potentially malicious wireless activity on the network is handled by _____________, whereas intrusion remediation and mitigation is handled by __________________________.
A. WIDS, WIDS
B. WIPS, WIPS
C. WIDS, FIPS
D. WIPS, FIPS
E. WIDS, WIPS
