Chapter 13 Wireless LAN Security Auditing
IN THIS CHAPTER, YOU WILL LEARN ABOUT THE FOLLOWING:
✓ WLAN security auditing tools
The diligent practice of WLAN security auditing is just as important to a healthy network as good planning and performance tuning but is often overlooked due to budgetary and time constraints. When building an 802.11 WLAN, you focus a lot of attention on the users, the intended use of the network, the devices used, channels, application support, security measures, signal strength, and bandwidth utilization. Although often overlooked in the past, proper planning and deployment of 802.11 WLAN security infrastructure should be considered mandatory. Over time, the network utilization and coverage can change, along with the number of WLAN devices and the applications being used. In addition, the equipment deployed as well as the industry standards and government regulations that apply to the use of wireless communications may evolve.
These changes may directly affect the security posture of the WLAN. The users of a WLAN will often complain if the network becomes “slow” or “unavailable” but will not complain about security holes because they know neither of their existence nor how to look for them. Users only care about their ability to access resources and do their jobs. Security holes, such as weak keys, unencrypted traffic, wired leakage, or rogue devices, do not concern the average user as long as their work is not impeded. Improperly configured security settings may reduce the usability of the network or allow attackers access to private information. While end users serve as a network performance monitor of sorts, there is no such built-in user monitoring for WLAN security mechanisms. Security is sometimes considered a luxury or an undesired expense until there is a breach that costs an organization a lot of time or money. Furthermore, if a WLAN security breach becomes public news, the organization faces embarrassment, potential loss of stock values, and potential legal liabilities.
In this chapter, you will learn about recommended WLAN audit procedures as well as the hardware and software tools needed to carry out a successful audit with the goal of creating a more secure wireless network.
WLAN Security Audit
Security does not make a computer network function, nor does it create a profit for an organization. However, without correctly implemented security, profitability and confidential information are in grave danger. WLAN security audits must be conducted on a regular basis to ensure compliance and aid in the early detection of vulnerabilities. Audits should also be conducted after any change is made to the WLAN infrastructure in order to ensure that the WLAN is not vulnerable to attacks due to the changes that were made. Regularly scheduled internal audits are a recommended practice and should be included as part of the organization’s security policy. Larger organizations should also consider hiring a third party for an outside WLAN security audit. When a different set of eyes examines a WLAN during an audit, potential vulnerabilities missed by the internal auditor are often exposed. A security audit should also be used to verify that the WLAN is still meeting security requirements that are often set by industry standards, government regulations, and organizational policies.
NOTE
In most countries, there are mandated regulations on how to protect and secure data communications within all government agencies. Legislation also often exists for protecting information and communications in certain industries. Various industry standards and U.S. government regulations will be discussed in greater detail in Chapter 15, “Wireless Security Policies.”
A series of evaluation procedures will normally comprise a typical WLAN security audit. These auditing best practices include the following:
Layer 1 audit
Layer 2 audit
Penetration testing
Wired infrastructure audit
Social engineering audit
WIPS audit
The physical security and inventory of the deployed WLAN devices should also be audited and documented. If you do not have physical security for the devices, what real security do you have? Wired infrastructure devices are usually locked in server rooms. However, WLAN devices, such as access points and antennas, are often exposed to the naked eye. Physical inspection of devices and cabling is part of a complete WLAN audit. Improperly secured APs are susceptible to theft or manipulation. It is not uncommon for expensive WLAN devices to have been replaced with low-cost clones purchased from Internet auction sites. Some APs have a console or serial port. An attacker may access the exposed ports of an unsecured AP to extract information about WLAN configuration settings or to make changes to the WLAN configuration.
A good audit also includes proper documentation as well as the final recommendations to make the WLAN more secure. Security auditing is a method of threat assessment with the eventual goal of risk mitigation. Any security threats and risks that are found will be presented to the WLAN network owner together with an assessment of their impact and often with a proposal for mitigation. Recommended technical and nontechnical solutions will be part of a final proposal.
OSI Layer 1 Audit
WLAN site surveys have changed dramatically over the years. When most individuals are asked to define a wireless site survey, the usual response is that a site survey is for determining RF coverage and capacity planning. Although that definition is absolutely correct, the site survey encompasses so much more, including looking for potential sources of RF interference. Before conducting the coverage analysis site survey, a spectrum analysis site survey should be considered mandatory for locating sources of potential interference.
Unfortunately, many site surveys completely ignore spectrum analysis because of the high cost generally associated with purchasing the necessary spectrum analyzer hardware. Spectrum analyzers are frequency domain measurement devices that can measure the amplitude and frequency space of electromagnetic signals. Spectrum analyzer hardware can cost upward of $40,000 (U.S. dollars), thereby making them cost-prohibitive for many smaller and medium-sized businesses. The good news is that several companies have solutions, both hardware and software based, that are designed specifically for 802.11 site survey spectrum analysis and are drastically less expensive. Figure 13.1 depicts an example of an affordable spectrum analyzer that can be used to monitor the 2.4 GHz and 5 GHz bands. Wi-Spy DBx is a custom USB spectrum analyzer from MetaGeek (www.metageek.com). The USB spectrum analyzer can be run from a laptop together with analysis software called Chanalyzer.
FIGURE 13.1 Wi-Spy DBx 2.4 GHz and 5 GHz spectrum analyzer
So what does the spectrum analysis during a site survey have to do with a Layer 1 security audit? Effectively the methods and tools used during both procedures are exactly the same. Spectrum analysis during a site survey is usually done for performance reasons, whereas spectrum analysis during a security audit is done to identify potential devices that will cause a Layer 1 denial of service (DoS). The original site survey is executed prior to deployment and installation of the WLAN infrastructure. The spectrum analysis portion of the survey is performed only one time, and it can be for both performance and security evaluation. Layer 1 security audits are enacted on a regularly scheduled basis after the WLAN infrastructure is already operational.
The main purpose of spectrum analysis during a WLAN site survey is to locate the potential sources of interference that may negatively impact the performance of the WLAN. As you learned in Chapter 12, “Wireless Security Risks,” most RF interference is unintentional. Unintentional interference will result in data corruption and Layer 2 retransmissions that negatively affect WLAN performance.
The main purpose of spectrum analysis during a security audit is to identify any devices that can cause a DoS at Layer 1. Any continuous transmitter will cause a DoS. RF jamming devices can be used by an attacker to cause an intentional Layer 1 DoS attack. Denial of service at Layer 1 usually occurs as an unintentional result of transmissions from non-802.11 devices. Video cameras, baby monitors, cordless phones, and microwave ovens are all potential sources of unintentional interference. Unintentional interference may cause a continuous DoS; however, the disruption of service is often sporadic. This disruption of service will upset the performance of Wi-Fi networks used for data applications but can completely disrupt VoWiFi communications within a WLAN. The majority of unintentional interfering devices transmit in the 2.4 GHz ISM frequency band. The 5 GHz UNII bands are less susceptible to unintentional interference.
The 2.4 to 2.4835 GHz ISM band is an extremely crowded frequency space. The following are potential sources of unintentional interference in the 2.4 GHz ISM band:
Microwave ovens
2.4 GHz cordless phones: both direct sequence spread spectrum (DSSS) and frequency hopping spread spectrum (FHSS) phones
Halogen gas lights
2.4 GHz video cameras
Elevator motors
Cauterizing devices
Plasma cutters
Bluetooth radios
2-way radios
During an audit, any source of interference must be identified, documented, and classified as either an intentional or unintentional source of interference that may cause a DoS. As you learned in Chapter 12, 802.11 radios use a clear channel assessment (CCA) to determine if the RF medium is busy or clear. Any “continuous” RF transmission that is constantly heard during the clear channel evaluation will cause 802.11 transmissions to cease completely until the signal is no longer present. Interfering devices may prevent an 802.11 radio from transmitting, thereby causing a DoS. There are multiple types of RF interference:
Narrow-band Interference A narrow-band RF signal occupies a smaller and finite frequency space and will not cause a DoS for an entire band such as the 2.4 GHz ISM band. A narrow-band signal is usually very high amplitude and will absolutely disrupt communications in the frequency space in which it is being transmitted. Narrow-band signals can disrupt one or several 802.11 channels. Narrow-band RF interference can also result in corrupted frames and Layer 2 retransmissions. The only way to eliminate narrow-band interference is to locate the source of the interfering device with a spectrum analyzer. Figure 13.2 shows a spectrum analyzer capture of a narrow-band signal close to channel 11 in the 2.4 GHz ISM band.
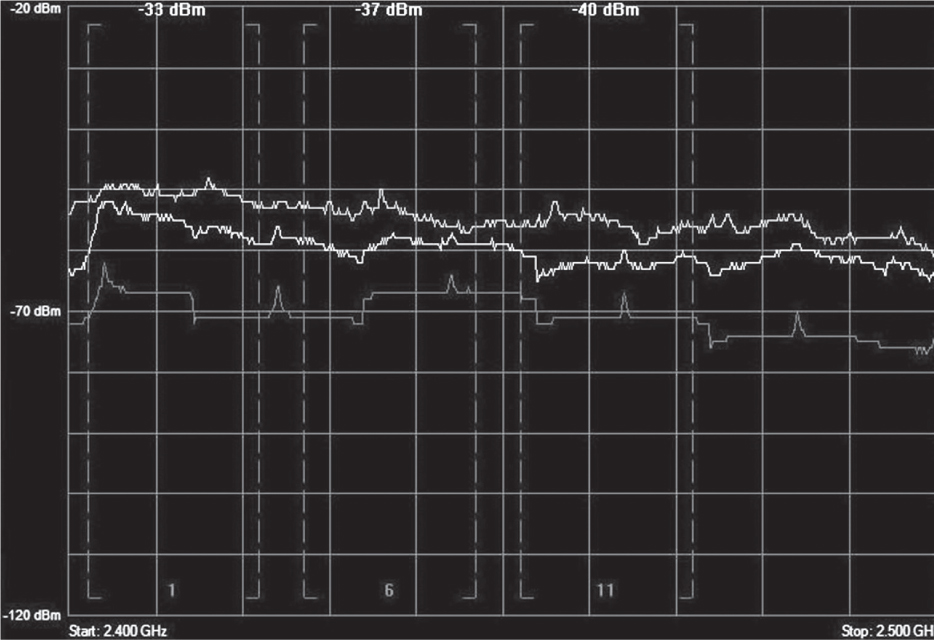
Wide-band Interference A source of interference is typically considered wide band if the transmitting signal has the capability to disrupt the communications of an entire frequency band. Wide-band jammers exist that can create a complete DoS for the 2.4 GHz ISM band. The only way to eliminate wide-band interference is to locate the source of the interfering device with a spectrum analyzer and remove the interfering device. Figure 13.3 shows a spectrum analyzer capture of a wide-band signal in the 2.4 GHz ISM band with average amplitude of –60 dBm.
FIGURE 13.2 Narrow-band RF interference
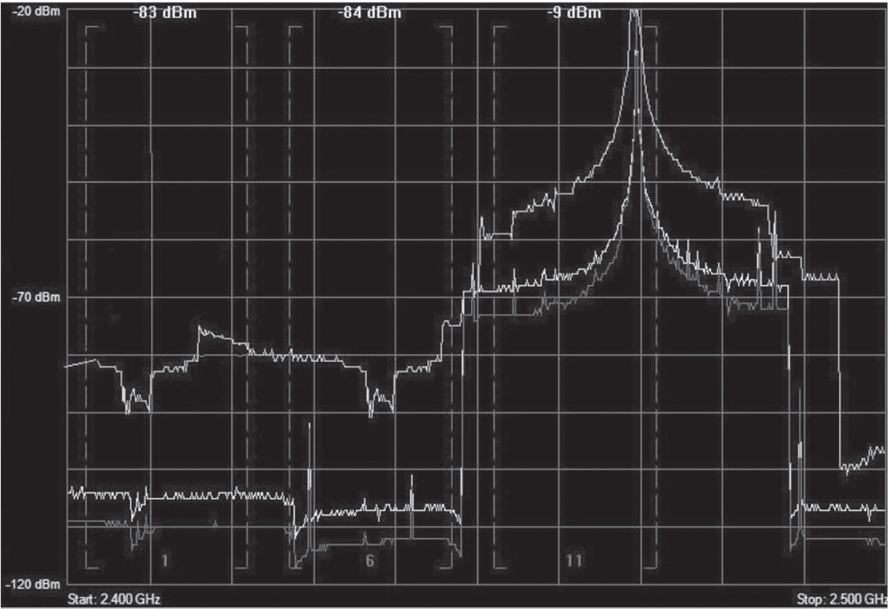
FIGURE 13.3 Wide-band RF interference
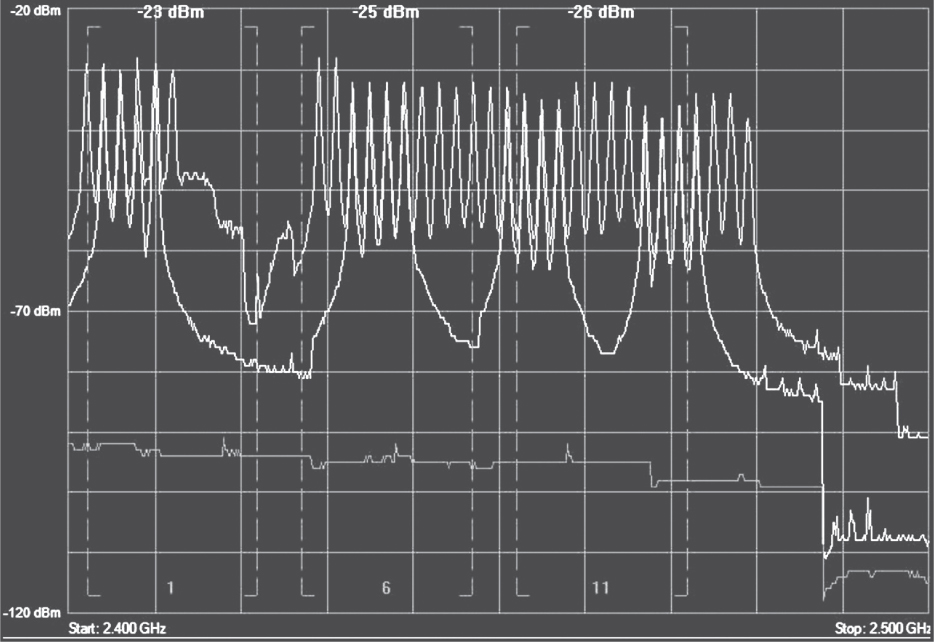
All-Band Interference The term all-band interference is typically associated with frequency hopping spread spectrum (FHSS) communications that usually disrupt the 802.11 communications at 2.4 GHz. FHSS constantly hops across an entire band, intermittingly transmitting on very small subcarriers of frequency space. A legacy 802.11 FHSS radio, for example, transmits on hops that are 1 MHz wide. 802.11b radios transmit in a stationary 22 MHz of frequency space and 802.11g/n radios transmit on fixed channels of 20 MHz of spectrum. While hopping and dwelling, an FHSS device will transmit in sections of the frequency space occupied by an 802.11b/g/n channel. Although an FHSS device will not typically cause a DoS, the frame transmissions from the 802.11b/g/n radios can be corrupted from the all-band transmissions of the FHSS interfering radio.
Bluetooth (BT) is a short-distance RF technology defined by the 802.15 standard. Bluetooth uses FHSS and hops across the 2.4 GHz ISM band at 1,600 hops per second. Older Bluetooth devices were known to cause severe all-band interference. Newer Bluetooth devices use adaptive mechanisms to avoid interfering with 802.11 WLANs. Bluetooth adaptive frequency hopping is most effective at avoiding interference, with a single AP transmitting on one 2.4 GHz channel. If multiple 2.4 GHz APs are transmitting on channels 1, 6, and 11 in the same physical area, it is impossible for the Bluetooth transmitters to avoid interfering with the WLAN. Digital Enhanced Cordless Telecommunications (DECT) cordless telephones also use frequency hopping transmissions. Some DECT phones transmit in the 2.4 GHz band. A now-defunct WLAN technology known as HomeRF also used FHSS; therefore, HomeRF devices can potentially cause all-band interference.
The existence of a high number of frequency-hopping transmitters in a finite space will result in some 802.11 data corruption and Layer 2 retransmissions. All-band interference may not cause a continuous DoS; however, the disruption of service due to Layer 2 retransmissions can be significant from a performance perspective. The only way to eliminate all-band interference is to locate the source of the interfering device with a spectrum analyzer and remove the interfering device. Figure 13.4 shows a spectrum analyzer capture of a frequency hopping transmission in the 2.4 GHz ISM band.
NOTE
A Layer 1 security audit is normally accomplished using some sort of handheld spectrum analyzer or laptop spectrum analyzer. Some WLAN vendors offer 24/7 spectrum monitoring capabilities with a distributed spectrum analysis system (DSAS). A more detailed discussion of DSAS can be found in Chapter 14, “Wireless Security Monitoring.”
FIGURE 13.4 All-band RF interference
OSI Layer 2 Audit
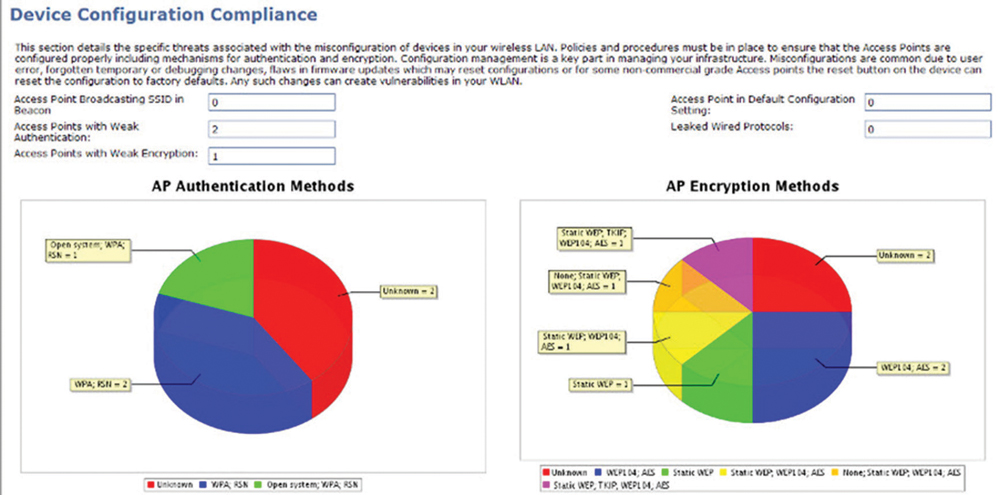
The gathering and analysis of OSI Layer 2 information is a vital part of the wireless LAN security audit process and can reveal a great deal of information about both the WLAN functionality and the security posture of the network being examined. One of the main purposes of a Layer 2 audit is initially to detect any rogue devices or unauthorized 802.11 devices. Identifying rogue devices during an initial security audit is critical, especially if a distributed WIPS monitoring solution has not been deployed. A proper Layer 2 WLAN security audit will also be used initially to identify all authorized 802.11 WLAN devices, including access points and authorized clients. As shown in Figure 13.5, a Layer 2 audit can also be used to validate WLAN security compliance. In other words, if the mandated security required the use of Protected Extensible Authentication Protocol (PEAP) authentication and CCMP/AES encryption, all authorized devices can be evaluated to verify the proper security configuration. Any authorized devices that have not been properly configured will be flagged.
FIGURE 13.5 Device configuration compliance
The payload of a wireless frame, meaning the Layer 3 and higher information, should normally be hidden due to encryption. The payload may be encrypted but the header and trailer information is always readable without any special decoding required. The header and trailer information must be in cleartext for the exchanges to work properly. Any 802.11 frame exchange can be captured and can reveal Layer 2 information about the devices directly involved in a frame exchange. A Layer 2 audit is necessary to ensure that no pertinent information is being exposed and that it is properly protected.
The following is a list (in no special order) of some of the more important things auditors should strive to find, identify, and classify at Layer 2 during audits:
MAC addresses
SSID
BSSID
Device types being used
Authentication methods
Encryption methods
Traffic types
Neighboring devices
Channels in use
Default configurations
Active Layer 2 attacks
Weak keys in use
Ad hoc clients
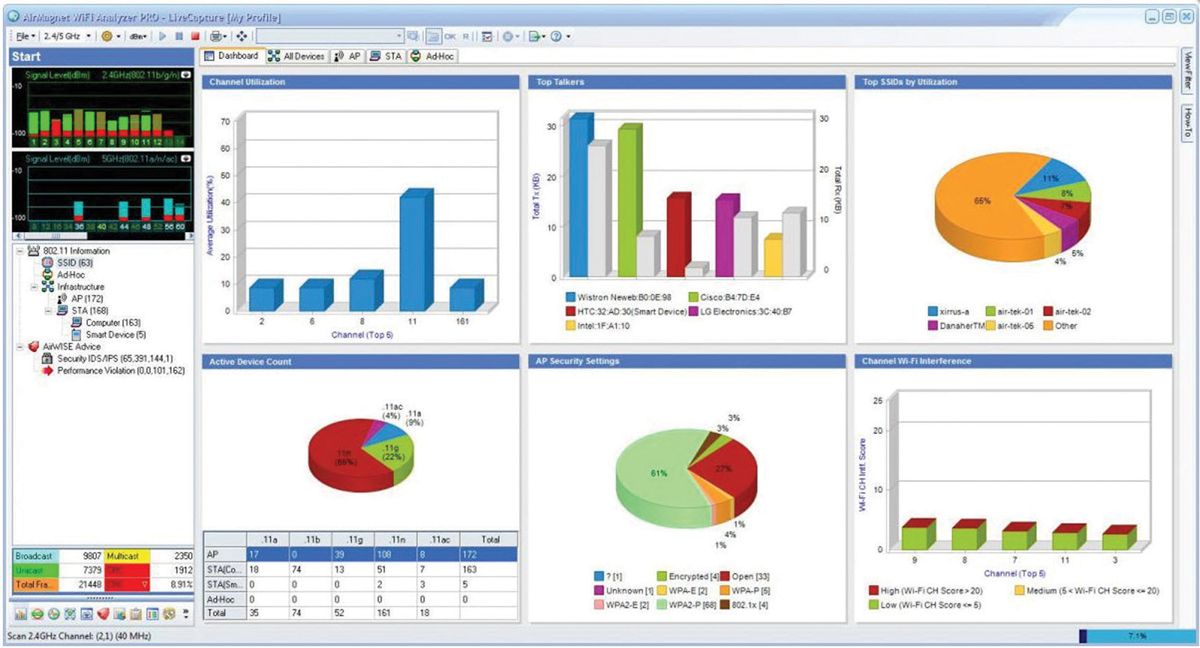
As you can see in Figure 13.6, a simple WLAN protocol analyzer installed on a laptop is usually sufficient to perform a Layer 2 audit. WLAN protocol analyzers are typically used for Layer 2 troubleshooting and WLAN performance analysis. However, as Figure 13.6 shows, some software WLAN protocol analyzers provide a greater emphasis on security auditing and can be used effectively as a mobile wireless intrusion detection system (WIDS) solution. An example of such a professional tool, seen in Figure 13.6, is Fluke Networks’ AirMagnet WiFi Analyzer PRO.
FIGURE 13.6 Layer 2 protocol analyzer
Penetration Testing
You have already learned that WLAN auditing is a process used to ensure that 802.11 communications and devices are secured and functioning as required by organizational policies, industry standards, and/or governmental regulations. Wireless LAN auditing may also include wireless penetration testing if desired as part of the scope of work agreement between the organization and the auditor. A WLAN penetration test is used to evaluate the security of the WLAN by simulating an attack from a malicious intruder. Many of the tools used during WLAN penetration testing are the same tools that hackers may use for malicious purposes. WLAN penetration testing tools are used to find security vulnerabilities due to hardware/software flaws, improper system configuration, and known technical weaknesses.
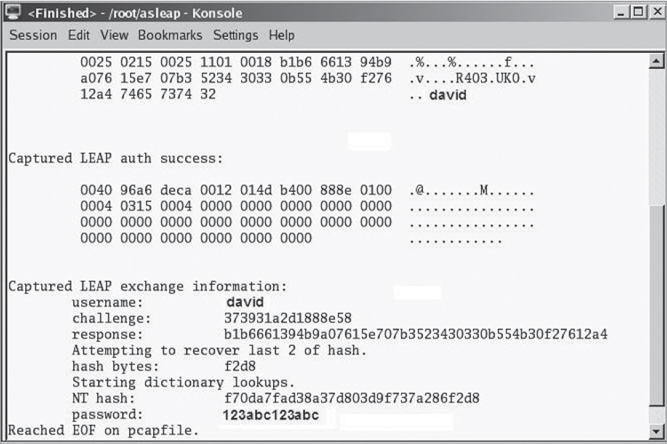
A good example of a penetration test is using known authentication cracking software tools to demonstrate the weakness of the chosen passwords or passphrases. Weaker authentication methods are often deployed due to cost concerns. A good penetration test would be an attempt to circumvent weaker authentication methods such as Lightweight Extensible Authentication Protocol (LEAP) or WPA/WPA-2-Personal. You learned in earlier chapters that LEAP is susceptible to an offline dictionary attack. As shown in Figure 13.7, a software auditing tool called Asleap can be used with a hashed rainbow table of adequate size to reveal the hashed LEAP password in a matter of seconds.
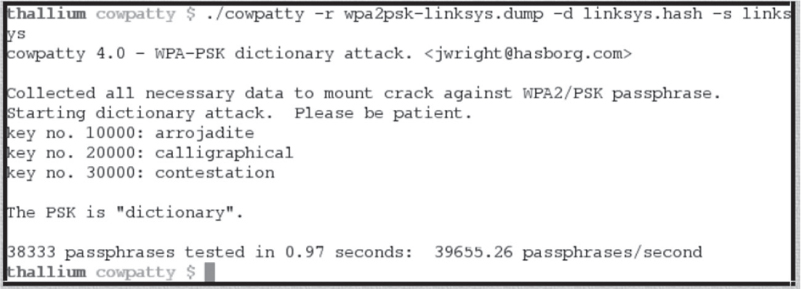
You also have already learned that WPA/WPA2-Personal, using preshared keys, is a weak authentication method that is vulnerable to an offline brute-force dictionary attack. There is no difference between cracking WPA or WPA2 preshared keys. The authentication methodology used in both formats is basically the same, so the technique used to obtain the passphrase is the same. As Figure 13.8 shows, a software auditing tool called coWPAtty can be used to derive weak passphrases.
NOTE
The Asleap and coWPAtty authentication cracking auditor tools were created by wireless security expert Joshua Wright. The tools can be downloaded from Joshua’s website at www.willhackforsushi.com.
A great tool for auditing that you may have used in the past is BackTrack Linux. This older penetration testing tool has been replaced by a greatly improved successor, Kali Linux. As shown in Figure 13.9, Kali Linux is an open source project maintained and funded by Offensive Security, a provider of information security training and penetration testing services. Kali Linux comes preinstalled with over 600 penetration-testing programs. Kali Linux is a Debian-based distribution with a collection of security and forensics tools. These tools include Nmap (a port scanner), Wireshark (a packet analyzer), John the Ripper (a password cracker), Aircrack-ng (a software suite for WLAN penetration testing), and web application security scanners Burp Suite and OWASP Zed Attack Proxy (ZAP). Kali Linux can run natively when installed on a computer’s hard disk, or you can boot it from a live CD or live USB, or run it from within a virtual machine.
NOTE
This Study Guide is not a book on how to use the numerous WLAN penetration utilities that are available. A great instructional book that we recommend is Kali Linux: Wireless Penetration Testing Beginner’s Guide, by Vivek Ramachandran and Cameron Buchanan (Packt Publishing, 2015).
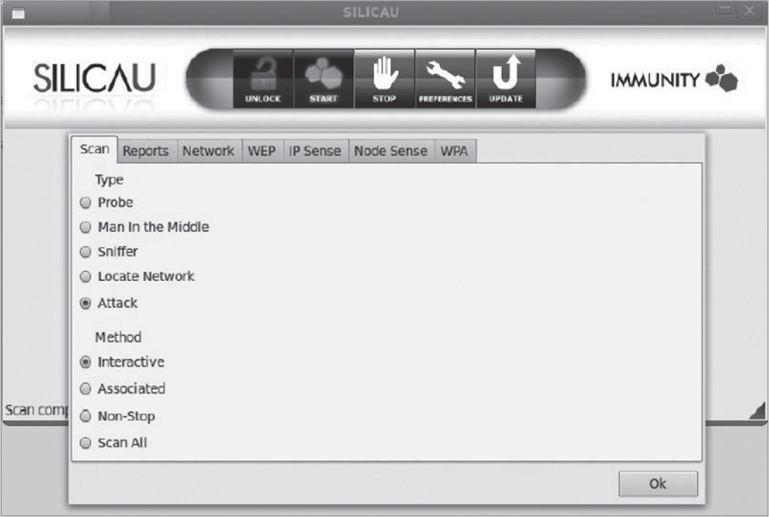
WLAN penetration testing tools are freely available on the Internet; however, there is often a learning curve as to how to properly use a wide variety of software programs. Several commercial vendors offer automated WLAN assessment solutions such as Immunity’s SILICA solution, shown in Figure 13.10.
FIGURE 13.10 Immunity SILICA WLAN security assessment software
Another WLAN auditing tool that has become popular is Wi-Fi Pineapple from Hak5. WiFi Pineapple consists of custom, purpose-built hardware and software, enabling its users to quickly and easily deploy advanced attacks using an intuitive web interface. As shown in Figure 13.11, WiFi Pineapple features dual unlocked high-gain radios and SMA (SubMiniature version A) connectors to allow the user to install professional antennas. One appealing feature if you are conducting audits with little time to do so is the tool’s auto-attack mode. It allows you to have customized boot-time payloads without the need to log in. All you need to do is set the switches to your attack mode of choice and power on.
FIGURE 13.11 WiFi Pineapple Mark V

Wired Infrastructure Audit
The normal purpose of a WLAN is to act as a wireless portal to network resources that reside on the wired network infrastructure. As you have already learned, penetration testing can be used to see if strong authentication solutions are deployed properly to protect the portal. Once authorized to access network resources, WLAN users can be further restricted as to what resources may be accessed and where they can go. Role-based access control (RBAC) security can be used to restrict certain groups of users to certain network resources. RBAC is usually accomplished with firewall policies and access control lists. Penetration testing of the firewall used to restrict WLAN user access to certain network resources should be a mandatory procedure during the security audit. All WLAN infrastructure interfaces should also be audited. Wireless infrastructure hardware, such as autonomous access points and WLAN controllers, can be managed by administrators via a web interface, a command-line interface, a serial port, a console connection, and/or Simple Network Management Protocol (SNMP). It is imperative that these interfaces be protected. Interfaces that are not used should be disabled. Strong passwords should be used, and encrypted login capabilities such as Hypertext Transfer Protocol Secure (HTTPS) and Secure Shell (SSH) should be utilized if available.
Social Engineering Audit
The weakest link in security for any type of computer network is usually the network end users. In Chapter 12, you learned how social engineering is the act of manipulating people into divulging confidential information for the purpose of obtaining information used to access a computer network. Therefore, social engineering techniques are often used by the security auditor to circumvent the WLAN and gain access to network resources. Social engineering performed by an auditor is a form of penetration testing and is usually the most successful method. An auditor will most likely find lapses in security due to improper employee training or employee policy enforcement. Although penetration testing using software tools is often successful, the auditor will probably have more luck with social engineering techniques used for penetration testing purposes.
WIPS Audit
If a company has been hired to perform a WLAN security audit, chances are that the customer is not using a distributed wireless intrusion detection system (WIDS) or distributed wireless intrusion prevention system (WIPS). Many of the WIDS/WIPS vendors will often perform an initial WLAN security audit for free. The WIPS/WIPS vendor will show the customer potential security holes, make recommendations, and then offer to sell the customer a distributed WIDS/WIPS solution that is capable of full-time WLAN security monitoring.
If a distributed WIDS/WIPS monitoring solution has already been deployed, the monitoring solution should also be audited. Hacker attacks, such as DoS, MAC spoofing, rogue devices, and so on, should be simulated to see if the proper WIDS/WIPS alarms are triggered for each attack. For example, a third-party access point can be connected to a wired port to test the rogue detection capabilities of a distributed WIPS monitoring solution. Another example is when Layer 2 DoS attacks are simulated to verify detection by the WIPS server and sensors. If certain alarms are not triggered, alarm thresholds may need to be adjusted on the WIDS/WIPS server.
NOTE
WIDS and WIPS monitoring solutions will be discussed in greater detail in Chapter 14.
Documenting the Audit
The job is not finished until the paperwork is done. This is a common quotation but true nonetheless. Documenting the audit is of great importance to both the auditor and the customer. The auditor needs to be able to produce evidence of his or her findings to the customer and make recommendations for improving security and WLAN health based on these findings. The customer will need documentation to prove compliance with regulations. Documentation can also be used by the customer to have their own IT staff implement the security changes recommended by the auditor.
Documentation of an audit can be presented in several formats. An all-written presentation in PDF format is often used; some auditors use Microsoft PowerPoint slide shows. The actual deliverable can vary based on the statement of work (SOW) agreement and customer’s requirements. The customer may also provide some documentation such as a network topology map and corporate policy documents prior to the audit. Here is some of the documentation required for the audit:
Statement of Work This document outlines the audit requirements, deliverables, and timeline that the auditor will execute for a customer. Pricing and detailed terms and conditions are specified in the SOW.
Liability Waiver It is very important that any auditor obtain signed permission in the form of a liability waiver or hold harmless agreement to perform the security audit. An audit should never take place without authorized permission.
Network Topology Map Understanding the layout of the customer’s wired network infrastructure and WLAN infrastructure will speed up the audit process and allow for better planning of penetration testing. A computer network topology map will provide necessary information, such as the location of the wiring closets, access points, WLAN controllers, and firewalls.
Mutual Nondisclosure Agreement Some organizations may not wish to reveal their network topology for security reasons. It may be necessary to obtain security clearance and/or sign nondisclosure agreements to gain access to these documents.
Corporate Security Policy Obtaining a copy of the customer’s written security policy document will be valuable for determining risk assessments. Very often the corporate security policy will be nonexistent or outdated.
Audits and or penetration tests should not go beyond the written corporate policy or the SOW agreement. Documentation in IT can be thought of as a type of unicorn, something you have heard about but never see. This does not mean it should not be requested prior to beginning the audit. Often an auditor is called upon to assist the customer in creating documentation such as policy documents.
By finding out what is visible in WLAN communications, the auditor is able to document the information being made available to attackers and to begin to secure the transmissions. If there is a written wireless security policy, auditors are able to determine if WLAN communications are being conducted within the policy guidelines by comparing the information contained in captured traffic with the written policy.
Unfortunately, the existence of a written security policy that governs wireless communications is a rare thing. Most organizations rely on a generic security statement that focuses on inappropriate Internet and phone usage rather than on WLAN security. In the absence of written WLAN usage policy, auditors can compare captured traffic with industry compliance policies or governmental regulations such as PCI or SOX. If there is no organizational awareness of WLAN security, the comparison of current traffic and industry or governmental standards is a very useful tool in helping networks become and remain secure.
Audit Recommendations
The main purpose of the WLAN security audit is to expose potential security holes so that proper solutions and procedures can be implemented. After the audit is completed, recommendations will be made based on the audit findings on how to protect the WLAN and the network infrastructure more securely. Recommendations could include the following:
Stronger Dynamic Encryption If no encryption or weak encryption such as WEP is being used, the recommendations will be to upgrade to an available dynamic encryption method such as CCMP/AES.
Stringent Authentication Penetration testing may reveal weak authentication such as LEAP or WPA/WPA2-Personal. Upgrading to an 802.1X/EAP authentication solution using tunneled authentication will almost always be recommended.
Role-Based Access Control (RBAC) Recommendations can be made on how to segment groups of users and devices to certain network resources using firewall policies, access control lists, and VLANs.
Monitoring Recommendations will be made about the types of distributed WIDS/WIPS monitoring solutions that may be needed.
Corporate Policy An extra addendum to the security recommendations might be corporate WLAN policy recommendations. The auditor might assist the customer in drafting a wireless network security policy if they do not already have one.
Training One of the most overlooked areas of WLAN security is proper training. It is highly recommended that security training sessions be scheduled with the customer’s network administration personnel. Additionally, condensed training WLAN security sessions should be scheduled with all end users.
Physical Security The installation of enclosure units to protect against theft and unauthorized physical access to access points may be a recommendation. Enclosure units are also often used for aesthetic purposes.
WLAN Security Auditing Tools
To conduct a successful WLAN security audit, you must use tools designed for that purpose. Although attackers may use some of the same tools to exploit poorly secured networks, WLAN security auditors use them to expose areas of the WLAN that are in need of increased protection or reconfiguration. The audit is performed in order to prevent attackers from gaining access to network resources and to assist the organization in reaching the required security levels demanded by industry and policy compliance. Auditors have an advantage over attackers in that they are typically allowed physical access to the premises that they are auditing. This access is much like the access granted during a WLAN site survey, and it may require an escort or special identification to traverse the area. A degree of overlap exists between a good WLAN site survey kit and a good WLAN auditing kit.
The successful WLAN auditor requires not only a thorough knowledge of 802.11 technology but also the proper software and hardware to perform the WLAN penetration testing. The hardware and software used during an audit vary based on the type of WLAN vulnerability to be identified. For example, if an auditor is looking for the source of noise that is causing a potential denial of service, the proper tool is a spectrum analyzer. If the auditor is conducting 802.11 traffic analysis, the proper tool would be a WLAN protocol analyzer.
The tools selected must match the job at hand. Typically a well-equipped auditor will have the following hardware devices and software to assist them in their work, either as part of their own kit or provided by the facility being audited:
At least one laptop
WLAN protocol analyzer and audit software
Spectrum analyzer
WLAN penetration testing software tools
802.11 packet generator software
2.4 GHz and 5 GHz signal generator
Facility blueprints or floor plan
WLAN cards for each frequency and protocol
Omni-directional antennas
Yagi or patch antennas
Matching pigtail connectors
Global positioning sensor (GPS)
Access point
Camera and/or video recorder
Phone or walkie-talkie
Ladders and or lifts
Battery packs and power cables
Wheeled cart
This is by no means an exhaustive listing of all the tools used to conduct a WLAN audit. The type and number of tools needed to conduct a successful audit vary based on the type of WLAN being audited and the security requirements of that WLAN. For example, security audits at a Wi-Fi hot spot may only require a visual inspection of the AP and making sure the captive portal is working, whereas large-scale enterprise WLANs may require several days of capturing 802.11 frames for evaluation as well as penetration testing.
The Layer 1 and Layer 2 auditing tools mentioned earlier in this chapter should all be considered mandatory. WLAN protocol analyzers are typically used for Layer 2 auditing, and spectrum analyzers are used for Layer 1 auditing. Many freeware Linux-based and Windows-based WLAN penetration testing software tools are also widely available. Penetration testing normally should be considered a mandatory part of the audit. Some of the other tools listed are obviously required, such as laptops and WLAN cards. Others require more explanation about their use, such as APs and battery packs. For example, an auditor may require several hours of analysis before rendering a security report; thus it’s important that the laptop and other devices have adequate power the entire time they’re gathering information. External battery packs to power the devices may be needed in areas where a wall outlet cannot be found. A third-party access point may be used to test the rogue detection capabilities of a distributed WIPS monitoring solution.
Physical inspection or building access may require identification or an escort during the audit. If conducting the audit from off the premises, the use of an antenna may be required to hear the wireless transmissions from inside the building(s). As discussed in Chapter 12, a high-gain unidirectional antenna can be used to hear RF signals from a great distance. Antennas are bidirectional passive amplifiers. In the case of an outside audit, proper antenna use often gives the auditor the ability to listen from a remote location. An outside auditor can emulate an attacker who might launch an attack from a location off company grounds.
Physical inspection of devices and cabling is part of a complete WLAN audit. To inspect such devices physically, ladders or lifts may be required. Carrying all of the equipment required for an audit about may become cumbersome and result in the auditor not covering the entire area. The use of a wheeled cart can reduce the wear and tear on the auditor (as will a comfortable pair of shoes), just like in a WLAN site survey. Pen and paper along with a camera and video recorder will give the auditor the ability to take notes and document what they find as part of the deliverable presented at the end of the audit. In a large outdoor area, the auditor may find the use of a GPS is required to record the location of outdoor 802.11 devices, such as bridges and mesh access points.
A larger deployment may require a team of auditors who need to communicate with one another during the audit. Having phones and or walkie-talkies will facilitate this communication. It is easy to see how the hardware and software used as part of a WLAN security audit resembles a kit used as part of a pre- or post-deployment WLAN site survey. Unlike a site survey, the audit will monitor channels, frequencies, and areas of coverage not required by the WLAN.
Many of the tools traditionally used for penetration testing are Linux based. Today, however, many of these tools are supported on a Windows platform. Which tool is used may depend on whether users being audited are Linux, Windows, or Mac OS users. Fewer tools are available for WLAN analysis for use on Mac OS than for Linux and Windows platforms. Table 13.1 contains a list of some of the more common WLAN security-auditing tools.
TABLE 13.1 Common tools and uses
Type of use |
Possible audit/attack |
Tools |
Wireless discovery |
Eavesdropping, discovery of rogue APs, ad hoc STAs, and open or misconfigured APs |
inSSIDer, NetSurveyor, NetStumbler, Kismet, Wellenreiter, WiFiFoFum, WiFi Explorer, WiFi Hopper, WiFi Scanner, Win Sniffer, Wireshark, and commercial WLAN protocol analyzers |
Encryption/authentication |
WEP, WPA, LEAP cracking, dictionary attacks |
Asleap, Aircrack-ng, CloudCracker, coWPAtty, AirSnort, Fern WiFi Cracker, WEPCrack, and WZCook |
Masquerade |
MAC spoofing, man-in-the-middle attacks, evil twin attacks, Wi-Fi phishing attacks |
Airsnarf, Ettercap Karma, Ghost Fisher, Hotspotter, HostAP, and SMAC |
Insertion |
Multicast/broadcast injection, routing cache poisoning, man-in-the-middle attacks |
Airpwn, CDPsniffer, chopchop, IrPass, VIPPR, and WiFitap |
Denial-of-service |
Layer 1 and Layer 2 DoS |
AirJack, Void11, Bugtraq, IKECrack, FakeAP, and RF signal generators |
Linux-Based Tools
The majority of effective wireless auditing tools run on Linux platforms, many of which can be accessed from a bootable CD such as Kali Linux. In this section, we will examine some of these tools and explain their use in conducting security audits.
There are several tools from which to choose to perform the same or similar tasks. The tools you choose will vary based on personal preference and the task at hand. The basics are the same no matter which tool you select. The devices and vulnerabilities must be discovered and documented. To find these vulnerabilities, you can use tools such as Kismet, AirSnort, and Aircrack-ng.
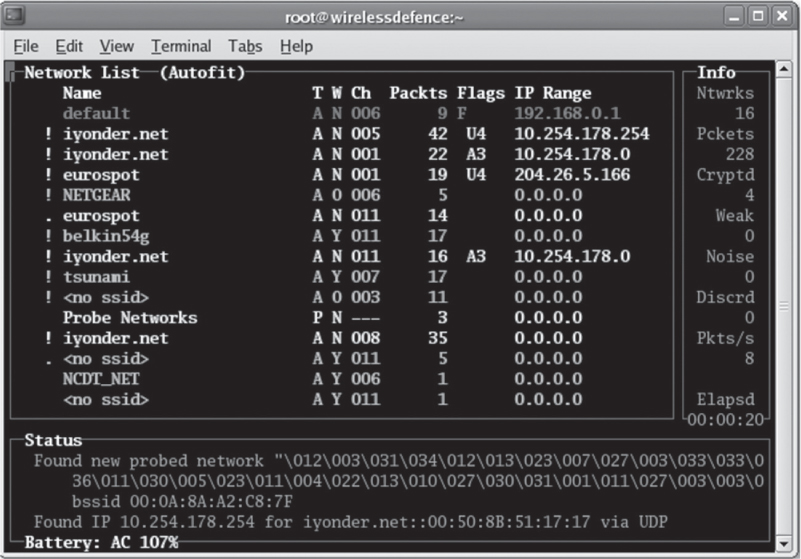
Blueprinting or enumerating network devices should be part of every audit. Looking for anything in use, not just the device traffic you would expect, will reveal rogue devices as well as incorrect configuration of authorized devices. Wardriving software tools are still used for simple WLAN discovery whereas other tools are used for packet capture. Since these tools are largely freeware and run on the Linux platform, there are lots of user groups and online tutorials and videos detailing their usage. THC-wardrive is a Linux-based wardriving tool that uses both an 802.11 radio and a GPS device to link the discovered 802.11 devices with latitude and longitude coordinates. As shown in Figure 13.12, Kismet is a Linux-based 802.11 Layer 2 wireless protocol analyzer and intrusion detection system. Kismet will work with any wireless card that supports raw monitoring (rfmon) mode, and it can sniff 802.11b, 802.11a, and 802.11g traffic.
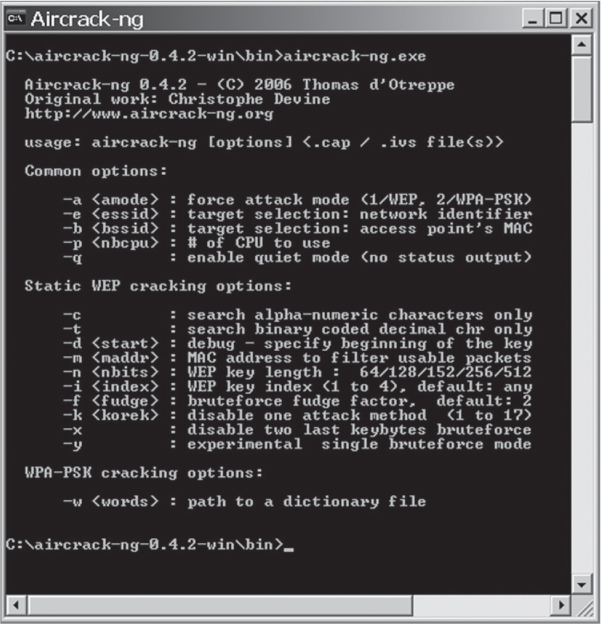
Once the target has been identified, the auditor must determine what additional information might be extracted using penetration testing. For example, if the auditor has been tasked with determining the WEP key or the WPA preshared key (PSK), they may use a tool such as AirSnort or Aircrack-ng. These tools are used to derive keys. AirSnort passively gathers packets until enough containing the Initialization Vector (IV) are captured, and then it cracks the WEP key offline. It takes roughly 300,000 to 500,000 IVs in the packet capture to crack the WEP key based on the complexity of the WEP key used. As shown in Figure 13.13, Aircrack-ng is a set of tools used together for cracking WEP and WPA-PSK. The Aircrack-ng tools include Airodump (used for packet capturing), Aireplay (used to inject traffic), Aircrack (used to crack WEP and WPA-PSK), and AirPcap (used to decode WEP and WPA-PSK captures). Aircrack-ng enables WEP and WPA-PSK traffic to be cracked in a short time frame as compared to older methods.
NOTE
More information about the Aircrack-ng auditor tools can be found at www.aircrack-ng.org.
No matter which tools are used, the auditor’s goals remain constant—find the devices, get on the network, and/or decode the data. Attackers use the same tools but for malicious reasons. Although there are many tools from which to choose, auditors and attackers alike find some tools they prefer more than others, with speed and ease of use weighing heavily in the decision. Most of the modern Linux command-line tools have been ported over to GUI-based tools that require less interaction and allow for quicker rendering of the desired information.
Summary
Diligently conducting WLAN security audits will reveal areas where improvements can be made in protecting the wireless network. The WLAN audit process involves inspection of Layer 1, Layer 2, the wired network, and the WIPS monitoring solution. The information gathered during these audits can be leveraged to make the proper recommendations for protecting both the WLAN as well as the wired network resources. Numerous tools are available to assist the auditor in their duties; some are commercial tools and others are freeware. Many of the tools used by hackers can also be used during a WLAN security audit for penetration testing. The best tool found in any auditor’s toolbox is social engineering skills.
Exam Essentials
Explain the various components of a WLAN security audit. These include a Layer 1 and 2 audit, penetration testing, wired infrastructure audit, social engineering audit, and possibly a WIPS audit.
Describe social engineering techniques. Explain why social engineering skills are usually the most successful WLAN auditing tool.
Understand the various methods of WLAN security auditing. Explain the importance of auditing both Layers 1 and 2 of the OSI model. Define aspects of penetration testing, wired infrastructure auditing, and WIPS auditing.
Explain WLAN security auditing and penetration testing tools. Discuss how Layer 1 and Layer 2 tools are used during a WLAN security audit. Describe some of the methods and tools used during WLAN penetration testing.
Review Questions
1. Which of these devices are potential sources of all-band interference? (Choose all that apply.)
A. Bluetooth
B. Microwave oven
C. 2.4 GHz DSSS cordless phone
D. 802.11 FHSS access point
E. HomeRF access point
F. 2.4 GHz DECT phone
2. Which of these WLAN auditing tools has the most success in compromising network resources when penetration testing is performed?
A. WLAN protocol analyzer
B. Asleap
C. Aircrack-ng
D. coWPAtty
E. Social engineering
F. Kismet
3. A WLAN security auditor recently walked into the ACME Company corporate headquarters and presented documentation to ACME management based on the WLAN penetration testing that was performed during the audit. ACME management was not pleased and decided to call the police and have the WLAN security auditor arrested. What documentation did the auditor fail to obtain prior to the WLAN security audit?
A. Written corporate policy
B. Liability waiver
C. Statement of work
D. Nondisclosure agreement
E. Network topology map
4. What would be the intended purpose of simulating Layer 2 deauthentication attacks as part of a WLAN audit?
A. Audit Layer 1
B. Audit Layer 2
C. Audit the wired infrastructure
D. Audit the WIPS
5. Management has asked the WLAN administrator to perform a thorough WLAN security audit. The administrator explains that a wired-side audit is necessary to ensure a secure WLAN. What procedures should be followed during the wired-side portion of a WLAN audit? (Choose all that apply.)
A. Audit firewall policies and rules
B. Audit WLAN management interfaces
C. Audit core Layer 3 switch
D. Audit application services
6. What are some of the recommendations that might be made to a customer after a successful WLAN security audit? (Choose all that apply.)
A. Physical security
B. Employee training
C. Dynamic RF configuration
D. Monitoring capabilities
E. AP and client power settings
7. Which of these tools are required for a proper WLAN security audit? (Choose all that apply.)
A. Spectrum analyzer
B. WLAN protocol analyzer
C. WLAN penetration testing software tools
D. Global positioning sensor (GPS)
E. Cameras
8. The management at the ACME Corporation has asked Bob to perform a WLAN security audit. Bob informs management that he will need to purchase a Yagi antenna for the audit. What reasons should Bob give management to justify the purchase of the Yagi antenna? (Choose all that apply.)
A. Attackers do not need physical access to the facility.
B. Yagi antennas are used in high multipath areas.
C. RF signals can be amplified from great distances.
D. Yagi antennas are used for indoor audits.
E. Spectrum analyzers require directional antennas.
9. As an auditor you have been asked to determine if the WLAN access points and client devices have been configured with the proper encryption. What should you use to answer this question for your customer? (Choose all that apply.)
A. Written corporate security policy
B. WLAN protocol analyzer
C. Aircrack-ng
D. coWPAtty
E. Asleap
10. What is some of the proper documentation needed prior to the WLAN security audit?
A. Statement of work
B. Liability waiver
C. Nondisclosure agreement
D. All of the above
11. A thorough security audit was conducted when a WLAN was deployed over 12 months ago and found no security issues. Recently, the organization failed to meet an industry compliance that the WLAN initially was able to meet due to security failures. What should have been done to help prevent the noncompliance issue the company now faces? (Choose all that apply.)
A. Update to the corporate security policy.
B. Remove all WLAN devices from the network.
C. Upgrade all firmware.
D. Perform a periodic WLAN audit.
12. As part of an audit and covered in the statement of work and nondisclosure agreements, you have been asked to determine if an outsider with no inside access or information would be able to gain access to the WLAN used in your client’s WPA2-Personal protected warehouse. Which tools should you use to provide the answer? (Choose all that apply.)
A. WLAN protocol analyzer
B. Aircrack-ng
C. Dictionary file
D. NetStumbler
E. coWPAtty
F. Asleap
13. What would be the intended purpose of using a third-party AP as part of a WLAN audit?
A. Audit Layer 1.
B. Audit Layer 2.
C. Audit the wired infrastructure.
D. Audit the WIPS.
14. Users have recently been complaining about lost connections at various times of the day. An original site survey was conducted that initially confirmed connectivity in all areas of the facility. Which tools must you use as part of your audit to determine the unexplained cause of loss connectivity? (Choose all that apply.)
A. High-gain Yagi antenna
B. Low-gain dipole antenna
C. WLAN protocol analyzer
D. Spectrum analyzer
E. Rainbow table
15. While conducting a WLAN security audit, you find an access point being used by employees on the network configured with all of the correct corporate security settings. This AP is not on the authorized AP list of the company’s WIPS but is configured securely and according to corporate written security policy. What should you do about this AP?
A. Unplug it from the wired LAN immediately.
B. Include it in your report to the company.
C. Nothing; it is secured by company standard.
D. Crack its security and decode the data.
16. What is the main purpose of using a WLAN protocol analyzer during the Layer 2 analysis of a WLAN security audit? (Choose all that apply.)
A. Identifying unauthorized devices
B. Auditing the wired infrastructure
C. Performing penetration testing
D. Validating security compliance of authorized devices
E. Auditing the WIPS
17. During a WLAN audit, you see an AP deployed in a common hallway of a multitenant building. This AP provides coverage to a small meeting room used by your customer. It was deployed there to keep the small meeting room from looking cluttered and is using the appropriate authentication and encryption as defined by the written company security policy. Is this AP a risk to the company’s network?
A. Yes, it is not on company property.
B. No, it is using required security settings.
18. When conducting a WLAN security audit, which of the following items would be of the least amount of use to the auditor?
A. Physical access to the building
B. Floor plan
C. Security escort
D. Ladder or lift
E. All of these are useful.
19. As an auditor, you have been asked to determine if the WLAN access points and client devices have been configured with EAP-TTLS authentication. What should you use to answer this question for your customer?
A. WLAN discovery tool
B. WLAN protocol analyzer
C. Aircrack-ng
D. coWPAtty
E. Asleap
20. Another auditor tells you that they use the same toolkit to conduct audits as they use to conduct WLAN site survey work. Why would they do this since they are performing two different types of work?
A. Many auditors cannot afford a proper auditing kit.
B. The two types of work are similar enough to use the same tools.
C. They have never been shown how to conduct an audit.
D. Their scope of work document limits them to passive auditing.
