Chapter 3 Encryption Ciphers and Methods
IN THIS CHAPTER, YOU WILL LEARN ABOUT THE FOLLOWING:
✓ WEP
✓ TKIP
✓ CCMP
✓ WPA/WPA2
✓ Proprietary Layer 2 implementations
Over the years people have created many ways to secure data for many purposes. In this chapter, you will learn about the various encryption algorithms that are used to secure wireless networks. You will see how encryption ciphers work to create encrypted data from plaintext data. This chapter will also discuss the encryption methods that are part of the 802.11-2012 standard, and the ciphers that they use. When data is encrypted, additional overhead is added to the frames. In this chapter, you will also see the MAC Protocol Data Unit (MPDU) format of Wired Equivalent Privacy (WEP), Temporal Key Integrity Protocol (TKIP), and Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) encrypted frames.
Encryption Basics
One of the major concerns with wireless networking has always been the fact that wireless communications use what is referred to as an unbounded medium. The wireless signal radiates away from the transmitting device in all directions, unlike a wired signal, which travels along the path of the cable. In other words, the RF physical medium is not limited to a cable and has no set boundaries. Since wireless is unbounded, and the signal can essentially be heard by anyone within listening range, measures need to be taken to secure the transmission so that only the intended recipients can understand the message. Therefore, data privacy should be considered mandatory. All essential data must be encrypted prior to transmission and then decrypted after being received.
Chapter 1, “WLAN Security Overview,” introduced the concept of cryptology. To review this concept briefly, the goal of cryptology is to process a piece of information, often referred to as plaintext, through an algorithm, often referred as a cipher, and transform the plaintext into encrypted text, which is also known as ciphertext. This ciphertext can then be decrypted, or converted back into plaintext, only by someone who knows the cipher.
The cipher is the process or algorithm that transforms the plaintext into encrypted text. One of the earliest ciphers, the Caesar cipher, is named after Julius Caesar. The Caesar cipher is a type of substitution cipher in which each letter of the alphabet is replaced by a different letter. When writing a message, Caesar shifted the alphabet by three characters to encrypt and protect his messages. Figure 3.1 shows the plaintext alphabet along with the shifted cipher key. The figure also shows a sample message in both plaintext and its ciphertext.
FIGURE 3.1 Example of the Caesar cipher

Ciphers have come a long way since the Caesar cipher. Present-day ciphers use mathematical calculations along with multiple repetitions or transformation rounds, with each round typically consisting of several processing steps.
Symmetric and Asymmetric Algorithms
Most cipher algorithms can be categorized as either a symmetric algorithm or an asymmetric algorithm. When using a symmetric algorithm, both the encrypting and decrypting parties share the same key. To ensure the privacy of a symmetric algorithm encrypted communication, the key needs to be kept secret. A potential problem with this is that the key must be shared between two or more parties prior to establishing the secure communications channel. Therefore, it is necessary to have a secure method of sharing the key. WEP, TKIP, and CCMP are encryption methods that all use symmetric algorithms.
Instead of using a single shared key, asymmetric algorithms use a pair of keys. As shown in Figure 3.2, one key is used for encryption and the other is used for decryption. The decryption key is typically kept secret and is known as the private key, or “secret key.” The encryption key is shared and is referred to as the public key. The premise is that if you wanted to send someone an encrypted message, you would obtain and use the public key to encrypt the message. The public key is only good for encrypting the message and cannot be used to decrypt the message. So even though many people could have the public key, none of them would be able to decrypt your message. Only someone with the private key would be able to decrypt it. Public key cryptography builds on the use of asymmetric encryption and digital signatures. Some methods of EAP authentication use digital certificates based on the X.509 standard for a public key infrastructure (PKI).
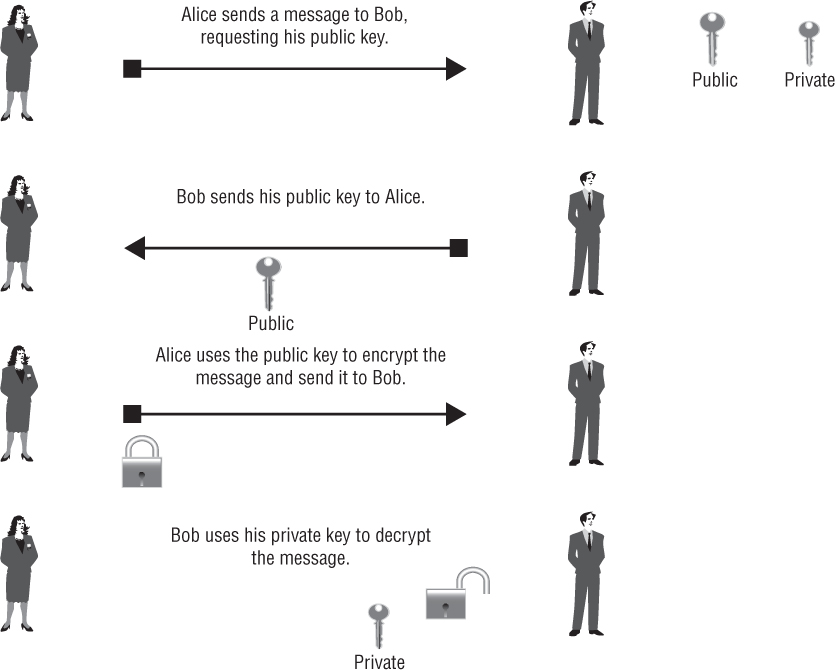
Symmetric algorithms generally require less computer processing power than asymmetric algorithms and, therefore, are typically much faster. However, the problem still exists that, with a symmetric algorithm, the key must be exchanged prior to the establishment of the secure communications, whereas with an asymmetric algorithm, the shared key that is used to decrypt the message never needs to be disclosed. Each method has benefits and drawbacks.
Stream and Block Ciphers
During the cryptographic process, the plaintext needs to be combined with random data bits to create the ciphertext. One common way of performing this task is sequentially, on a bit-by-bit basis. Ciphers that use this technique are known as stream ciphers. A stream cipher is a symmetric key cipher where plaintext bits are combined with a pseudorandom cipher bit stream called the keystream. The keystream is generated when some sort of seed is used to feed the stream cipher algorithm. For example, WEP encryption uses a static key that feeds the ARC4 stream cipher, which then generates the pseudorandom keystream. The stream cipher then combines the plaintext with the keystream, typically using a Boolean Exclusive-OR (XOR) operation. Stream ciphers are often used when the plaintext is not consistently one size, such as the data transmitted on a wireless LAN.
Boolean logic is a mathematical way to compare or combine bits. As shown in Table 3.1, an Exclusive-OR (XOR) will generate a 0 when both of the input values are the same and will generate a 1 when both of the input values are different. When an XOR is used with a shared key, the same key will successfully encrypt and then decrypt the data.
Input 1 |
Input 2 |
XOR output |
0 |
0 |
0 |
0 |
1 |
1 |
1 |
0 |
1 |
1 |
1 |
0 |
Another common method of creating the ciphertext is using a block cipher. Unlike stream ciphers, which operate on one bit at a time, a block cipher takes a fixed-length block of plaintext and generates a block of ciphertext of the same length. A block cipher is a symmetric key cipher operating on fixed-length groups of bits, called blocks. For example, a block cipher will use a 128-bit block of input of plaintext, and the resulting output would be a 128-bit block of ciphertext. The fixed length of the blocks is referred to as the block size, with block sizes often ranging from 64 bits up to 256 bits. Most block ciphers are designed to apply a simpler function repeatedly to the block. Each iterative process or function is referred to as a round. Depending on the specific block cipher, the round function could be repeated as many as a few dozen times. In most instances, the greater the number of rounds, the greater the level of security; however, performance will be effected due to the time needed to perform the rounds.
RC4/ARC4
RC4 is a stream cipher that was designed by Ron Rivest of RSA Security in 1987. The RC in RC4 stands for Rivest Cipher or Ron’s Code. RC4 was originally a trade secret; however, a description of it was anonymously leaked on the Internet in September 1994. After the code was leaked and confirmed to be genuine, and the algorithm was known, it was clearly no longer a trade secret. Although the algorithm was no longer a trade secret, the name “RC4” was trademarked and could only be used with permission. RSA never released the algorithm, so unofficial versions of it are often referred to as Arcfour or ARC4, which stands for “Alleged RC4.” ARC4 is fast and simple, and it is widely used in protocols such as WEP and Secure Sockets Layer (SSL). Due to weaknesses in the cipher, it is not recommended for use in newer networks.
RC5
RC5 is a symmetric block cipher that was designed by Ron Rivest in 1994, and a U.S. patent was granted for it in May 1997. RC5 allows for a variable block size, a variable key size, and a variable number of rounds. The block size can be set to 32, 64, or 128 bits; the key size can range from 0 bits to 2040 bits; and the number of rounds can range from 0 to 255. A key table is created, with the size of the table varying depending on the number of rounds that will be performed. When the user-provided secret key is entered, a key-expansion routine will expand the user-provided key to fill the key table. This key table is used for both encryption and decryption.
DES
Data Encryption Standard (DES) is a symmetric block cipher that was developed in the early 1970s. In 1976, it was selected by the National Bureau of Standards (NBS), currently known as the National Institute of Standards and Technology (NIST), as part of the official Federal Information Processing Standards (FIPS) for the United States. DES uses a 56-bit symmetric key, and it is now considered to be insecure, primarily due to the key size being too small. Multiple groups have successfully cracked DES using what are known as brute-force attacks, sequentially trying every possible key. DES has a 64-bit block size and a 64-bit key; however, 8 bits are used for checking parity and are discarded, so the effective key length is 56 bits. DES performs 16 identical rounds on each block.
NOTE
The history of DES is very interesting. A quick search on the Internet will reveal that the National Security Agency (NSA) was accused of tampering with it and covertly weakening the algorithm. These accusations were later shown to be false.
3DES
Triple Data Encryption Algorithm (TDEA), also known as Triple DES (3DES), is a symmetric block cipher published in 1998. 3DES uses a key bundle, which is made up of three DES keys (K1, K2, and K3), each with an effective key length of 56 bits. Like DES, each key is made up of 64 bits; however, 8 bits are used for checking parity and are discarded. 3DES is essentially DES run three different times using three keys. Therefore, it performs 48 DES-equivalent rounds on each block. 3DES defines three keying options:
Keying Option 1 All three keys are unique.
Keying Option 2 K1 and K2 are unique, but K3 = K1.
Keying Option 3 All three keys are identical; K1 = K2 = K3.
Keying option 1 is the strongest, because all three keys are unique, giving it an effective key size of 168 bits. Keying option 3 is the weakest, and it is essentially equal to very slow DES. Remember that with a symmetric algorithm, the same key that encrypts the data also decrypts the data. With 3DES, the first pass with K1 encrypts the data, the second pass with K2 actually decrypts the data, and the third pass with K3 encrypts the data again. Keying option 2 provides an effective key size of 112 bits. In 1999, DES was reaffirmed by FIPS for the fourth time, with 3DES the preferred method and single DES permitted only in legacy systems.
AES
Advanced Encryption Standard (AES) is an encryption standard adopted by the U.S. government. AES uses an algorithm that is a symmetric block cipher that supports three key sizes of 128, 192, and 256 bits. These different key lengths are referred to as AES-128, AES-192, and AES-256. AES was announced in November 2001 by NIST as FIPS 197. Although FIPS 197 specifies AES, it is just an algorithm that can be incorporated into many types of security solutions. For example, AES can be used by an IPsec VPN as well as in WPA2 security. It is based on the Rijndael algorithm, which was developed by two Belgian cryptographers, Vincent Rijmen and Joan Daemen. AES is used by the 802.11 encryption protocol CCMP, which officially became part of wireless security when 802.11i was ratified in June 2004. Remember that 802.11i is now part of the 802.11-2012 standard.
AES uses a fixed block size of 128 bits, which is actually a 4×4 array of bytes, called a state. The number of rounds performed on the block varies depending on the key sizes. AES-128 performs 10 rounds, AES-192 performs 12 rounds, and AES-256 performs 14 rounds. The 802.11ad-2012 amendment defines Very High Throughput (VHT) enhancements using the unlicensed frequency band of 60 GHz. The 802.11ad-2012 amendment standardized on the use of Galois/Counter Mode Protocol (GCMP), which uses AES cryptography. However, GCMP calculations can be run in parallel and are computationally less intensive than the cryptographic operations of CCMP. The extremely high data rates defined by 802.11ad need GCMP because it is more efficient than CCMP.
WLAN Encryption Methods
The 802.11-2012 standard defines three encryption methods that operate at Layer 2 of the OSI model: WEP, TKIP, and CCMP. The information that is being protected by these Layer 2 encryption methods is data found in the upper Layers of 3–7. Layer 2 encryption methods are used to provide data privacy for 802.11 data frames. The technical name for an 802.11 data frame is a MAC Protocol Data Unit (MPDU). The 802.11 data frame, as shown in Figure 3.3, contains a Layer 2 MAC header, a frame body, and a trailer, which is a 32-bit CRC known as the frame check sequence (FCS). The Layer 2 header contains MAC addresses and the duration value. Encapsulated inside the frame body of an 802.11 data frame is an upper-layer payload called the MAC Service Data Unit (MSDU). The MSDU contains data from the Logical Link Control (LLC) and Layers 3–7. A simple definition of the MSDU is that it is the data payload that contains an IP packet plus some LLC data. The 802.11-2012 standard states that the MSDU payload can be anywhere from 0 to 2,304 bytes. The frame body may actually be larger due to encryption overhead.
FIGURE 3.3 802.11 MAC Protocol Data Unit (MPDU)
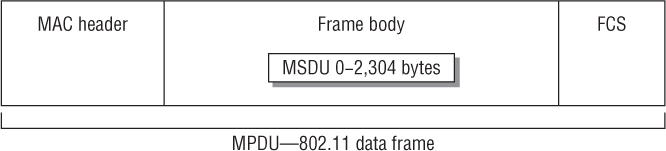
WEP, TKIP, CCMP, and other proprietary Layer 2 encryption methods are used to encrypt the MSDU payload of an 802.11 data frame. Therefore, the information that is being protected is the upper Layers of 3–7, which is more commonly known as the IP packet.
It should be noted that many types of 802.11 frames are either never encrypted, or typically not encrypted. 802.11 management frames only carry a Layer 2 payload in their frame body, so encryption is not necessary for data security purposes. However, wireless denial of service (DoS) attacks often use spoofed or impersonated management frames, which led to the development of 802.11w, also known as management frame protection. 802.11w makes wireless DoS attacks more difficult. 802.11 control frames only have a header and a trailer; therefore, encryption is not necessary. Some 802.11 data frames, such as the null function frame, actually do not have an MSDU payload. Non-data-carrying data frames have a specific function, but they do not require encryption. Only 802.11 data frames with an MSDU payload can be encrypted. As a matter of corporate policy, 802.11 data frames should always be encrypted for data privacy and security purposes.
WEP, TKIP, and CCMP are encryption methods that all use symmetric algorithms. WEP and TKIP use the ARC4 cipher, whereas CCMP uses the AES cipher. The current 802.11-2012 standard defines WEP as a legacy encryption method for pre-RSNA security. TKIP and CCMP are considered to be robust security network (RSN) encryption protocols. The 802.11ad-2012 amendment standardized the use of Galois/Counter Mode Protocol (GCMP), which uses AES cryptography. GCMP is also considered an optional encryption method for 802.11ac radios. However, none of the chipset vendors have implemented GCMP in the first several generations of 802.11ac radios. Hardware upgrades for both access points and client radios will be required for GCMP to be used with 802.11ac radios.
WEP
Wired Equivalent Privacy (WEP) is a Layer 2 security protocol that uses the ARC4 streaming cipher. The original 802.11 standard defined both 64-bit WEP and 128-bit WEP as supported encryption methods. The current 802.11-2012 standard still defines WEP as a legacy encryption method for pre-RSNA security. The Wi-Fi Alliance has been certifying 802.11 radios using WEP encryption since 2000. You learned about WEP encryption in Chapter 2, “Legacy 802.11 Security.”
For a brief review of the WEP encryption process, recall that a 24-bit cleartext initialization vector (IV) is randomly generated and combined with the static secret key. As shown in Figure 3.4, the static key and the IV are used as WEP seeding material through the pseudorandom ARC4 algorithm that generates the keystream. The pseudorandom bits in the keystream are then combined with the plaintext data bits by using a Boolean XOR process. The end result is the WEP ciphertext, which is the encrypted data. WEP also runs a cyclic redundancy check (CRC) on the plaintext data that is to be encrypted and then appends the Integrity Check Value (ICV) to the end of the plaintext data. The ICV is used for data integrity and should not be confused with the IV, which is a part of the seeding material for the ARC4 cipher.
FIGURE 3.4 WEP encryption process
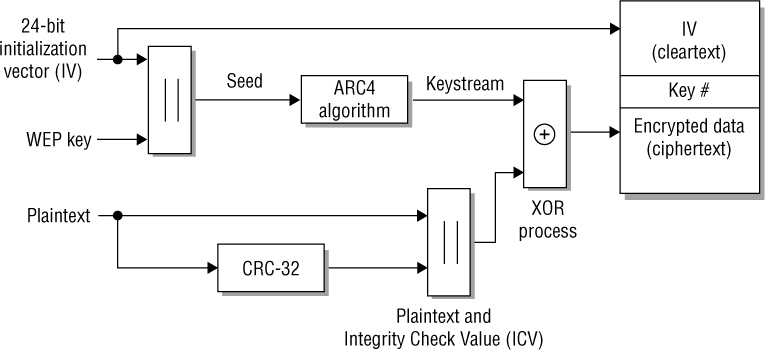
WEP encryption is covered extensively in Chapter 2, therefore, rather than exploring the topic again in great detail, we will direct you back to Chapter 2.
WEP MPDU
The encryption and decryption process for WEP is the same whether you are using WEP-40 or WEP-104. Figure 3.5 shows the WEP frame body, which contains an encrypted MSDU. To create the WEP-encrypted MSDU, WEP runs a CRC on the plaintext data that is to be encrypted and then appends the ICV to the end of the plaintext data. The ICV adds 32 bits (4 octets) of overhead to an 802.11 data frame. The data and ICV are then encrypted. WEP can be configured with up to four different keys. A Key ID identifies which WEP key was combined with the system-generated 24-bit IV to perform the encryption. This 24-bit IV is combined with the KEY ID and 6 bits of padding to create a 32-bit IV. The IV adds 32 bits (4 octets) of overhead to the frame body of an 802.11 data frame. The IV is not encrypted and is appended to the front of the encrypted MSDU payload.
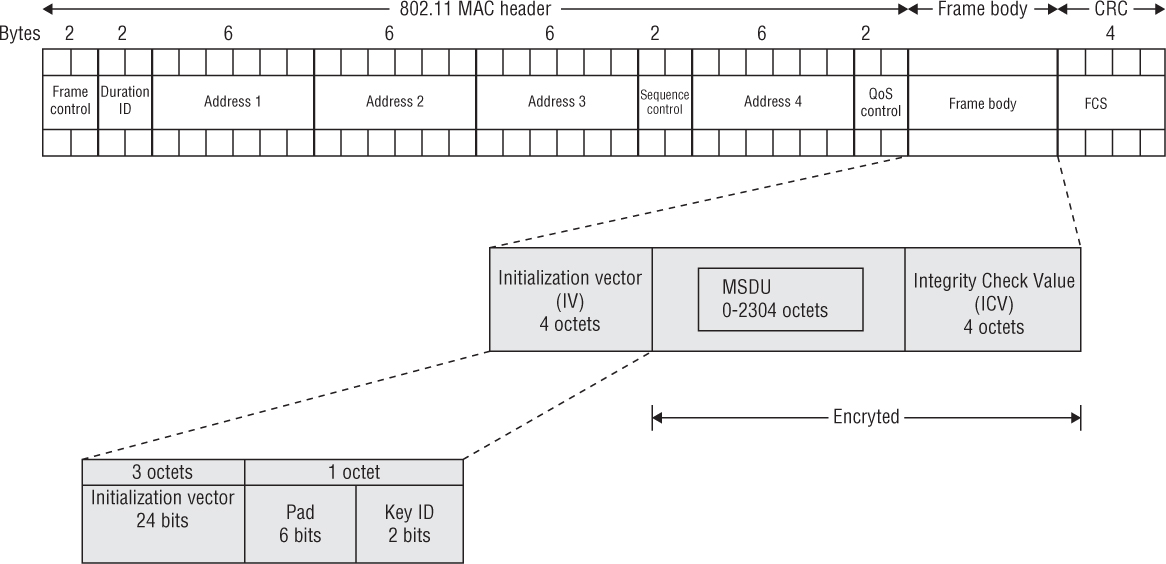
Remember that WEP encrypts the MSDU upper-layer payload that is encapsulated in the frame body of an MPDU. The MSDU payload has a maximum size of 2,304 bytes. Because the IV adds 4 octets and the ICV also adds 4 octets, when WEP is enabled, the entire size of the body inside an 802.11 data frame is expanded by 8 bytes to a maximum of 2,312 bytes. In other words, WEP encryption adds 8 bytes of overhead to an 802.11 MPDU.
TKIP
Temporal Key Integrity Protocol (TKIP) is a security protocol developed by the Wi-Fi Alliance in 2002. It was designed to replace WEP after its encryption was broken. WPA was designed to replace WEP, however, using the existing WLAN hardware. This meant that WPA was restricted to using the existing ARC4 algorithm that was used by WEP. When TKIP was introduced, most legacy 802.11 radios could implement TKIP with a firmware upgrade, but not all legacy APs and STAs were upgradeable. WPA and TKIP were designed to be around for 5 years, allowing the 802.11i amendment time to become ratified and implemented in the industry. As you have already learned, TKIP has been phased out and is not a supported encryption method for 802.11n or 802.11ac data rates. For a brief review of the TKIP encryption process, recall that TKIP uses a 128-bit temporal key, plus a 48-bit TKIP sequence counter (TSC), and the transmit address (TA) as seeding material, mixed together in the two-phase key-mixing process. This seed is then fed through the ARC4 algorithm to generate the keystream. The keystream is then combined with the plaintext to create the encrypted ciphertext. The Message Integrity Code (MIC) is computed and added to the end of the MSDU payload as the data integrity check. TKIP encryption is covered extensively in Chapter 2. Therefore, rather than exploring the topic again in great detail, we will direct you back to Chapter 2.
TKIP MPDU
Figure 3.6 shows the TKIP MPDU. The first 32 bytes are the 802.11 MAC header, which does not change. The encrypted frame body is made up of five key pieces:
IV/Key ID
Extended IV
MSDU payload
MIC
ICV
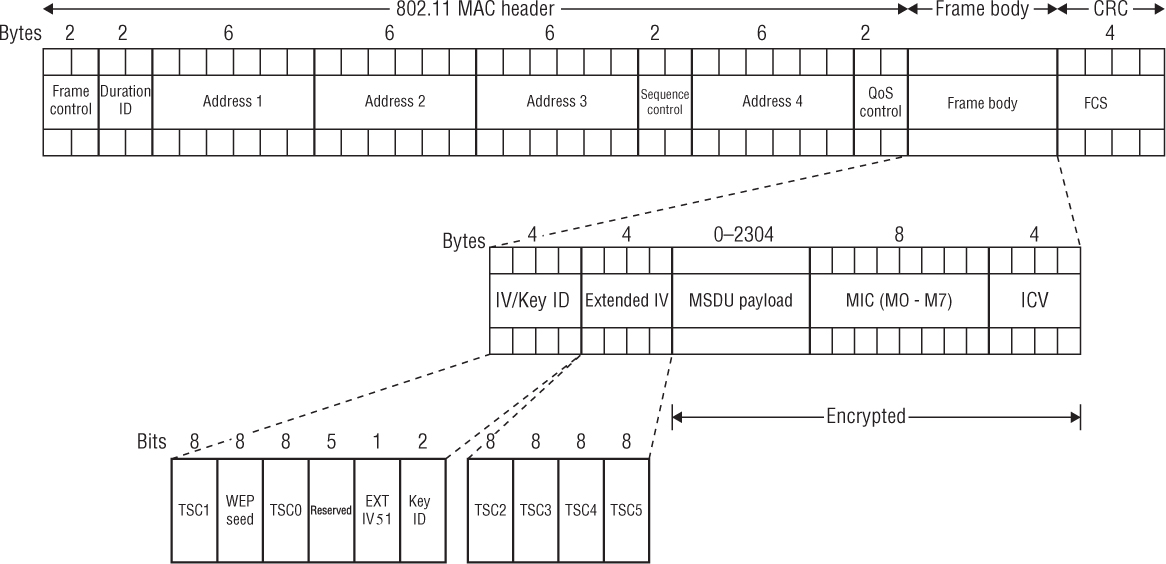
It begins with the IV/Key ID combination. This is 4 octets in size and is similar to the IV/KEY ID that is found in WEP. TSC0 and TSC1, the first 2 octets of the 48-bit TKIP sequence counter (TSC0 and TSC1), make up part of the IV/Key ID. If TKIP is being used, which is the case in this example, the Extended IV field is set to 1, indicating that an extended IV of 4 octets will follow the original IV. The Extended IV is 4 octets and is made up of the other 4 octets of the 48-bit TKIP sequence counter (TSC2 through TSC5). Both the original IV and the Extended IV are not encrypted. The 8 bytes that comprise the IV/Key ID and Extended IV could be considered a TKIP header.
After the original IV and the Extended IV comes the MSDU payload, followed by the 8 MIC octets, which are then followed by the 32-bit Integrity Check Value (ICV) that was calculated on the MPDU. The MSDU upper-layer payload as well as the MIC and ICV are all encrypted. The frame is then completed by adding the 32-bit frame check sequence (FCS) that is calculated over all the fields of the header and frame body.
Because of the extra overhead from the IV (4 bytes), Extended IV (4 bytes), MIC (8 bytes), and ICV (4 bytes), a total of 20 bytes of overhead is added to the frame body of a TKIP encrypted 802.11 data frame. When TKIP is enabled, the entire size of the frame body inside an MPDU is expanded by 20 bytes to a maximum of 2,324 bytes. In other words, TKIP encryption adds 20 bytes of overhead to an 802.11 MPDU.
CCMP
Counter Mode with Cipher-Block Chaining Message Authentication Code Protocol (CCMP) is the security protocol that was created as part of the 802.11i security amendment and was designed to replace TKIP and WEP. CCMP uses the AES block cipher instead of the ARC4 streaming cipher used by WEP and TKIP. As mentioned earlier, the IEEE 802.11-2012 standard defines two RSNA data confidentiality and integrity protocols: TKIP and CCMP, with CCMP support mandatory. CCMP is mandatory for RSN compliance. In September 2004, the Wi-Fi Alliance introduced version 2 of the Wi-Fi Protected Access certification, called WPA2, which requires the use of CCMP/AES encryption. Because the AES cipher is processor-intensive, older legacy 802.11 devices that only supported WEP and TKIP in most cases had to be replaced with newer hardware to support CCMP/AES encryption processing.
CCMP is made up of many components that provide different functions. Before going any further in this section, there are numerous acronyms and abbreviations relating to CCMP to which you need to be introduced. These acronyms and abbreviations are commonly used in the wireless industry and in the IEEE 802.11-2012 standard. Since CCMP is made up of many different components, it is common to reference the components individually. CounterMode is often represented as CTR. The CTR is used to provide data confidentiality. The acronym for Cipher-Block Chaining is CBC. You should also be familiar with CBC-MAC, which is the acronym for Cipher-Block Chaining Message Authentication Code. The CBC-MAC is used for authentication and integrity.
The full phrase of Counter Mode with Cipher-Block Chaining Message Authentication Code Protocol is represented by the acronym of CCMP. However, the shorter phrase of CTR with CBC-MAC is also sometimes represented by the CCMP acronym.
Some references to CCMP leave off the letter P and use the term CCM when referencing the block cipher and not the actual protocol. CCMP is based on the CCM of the AES encryption algorithm. CCM combines CTR to provide data confidentiality and CBC-MAC for authentication and integrity. In simpler words, the CCM process uses the same key for encrypting the MSDU payload and provides for a cryptographic integrity check. The integrity check is used to provide data integrity for both the MSDU data and portions of the MAC header of the MPDU.
CCM is used with the AES block cipher. Although it is capable of using different key sizes, when implemented as part of the CCMP encryption method AES uses a 128-bit key and encrypts the data in 128-bit blocks.
The inputs used by the CCMP encryption/data integrity process include the following:
Temporal Keys Just like TKIP, CCMP starts with a 128-bit temporal key. The 128-bit temporal key can either be a pairwise transient key (PTK) used to encrypt unicast traffic or a group temporal key (GTK) used to encrypt broadcast and multicast traffic.
Packet Number The 48-bit packet number (PN) is much like a TKIP sequence number. The PN uniquely identifies the frame and is incremented with each frame transmission. This protects CCMP from replay and injection attacks.
Nonce A nonce is a random numerical value that is generated one time only. A 104-bit unique nonce is constructed from the packet number (PN), priority data used in QoS, and the transmitter address (TA). Do not confuse this nonce with the nonces used during the 4-Way Handshake process described in Chapter 5.
802.11 data frame (MPDU) The frame body encapsulates the MSDU upper-layer payload that will be encrypted and protected by a MIC. The MPDU header, also known as the MAC header, will not be encrypted but is partially protected by the MIC.
AAD Additional authentication data (AAD) is constructed from portions of the MPDU header. This information is used for data integrity of portions of the MAC header. Receiving stations can then validate the integrity of these MAC header fields.
Figure 3.7 shows the CCMP encryption and data integrity process. It will be helpful to refer to this figure as you read about the steps CCMP performs.
FIGURE 3.7 CCMP encryption and data integrity process
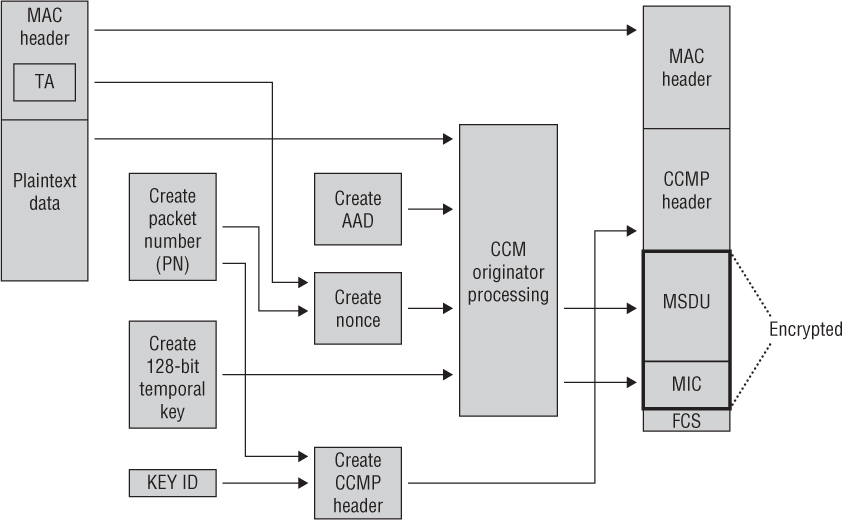
CCMP encrypts the payload of a plaintext MPDU using the following steps:
A 48-bit PN is created. Packet numbers increment with each individual MPDU, although they remain the same for retransmissions.
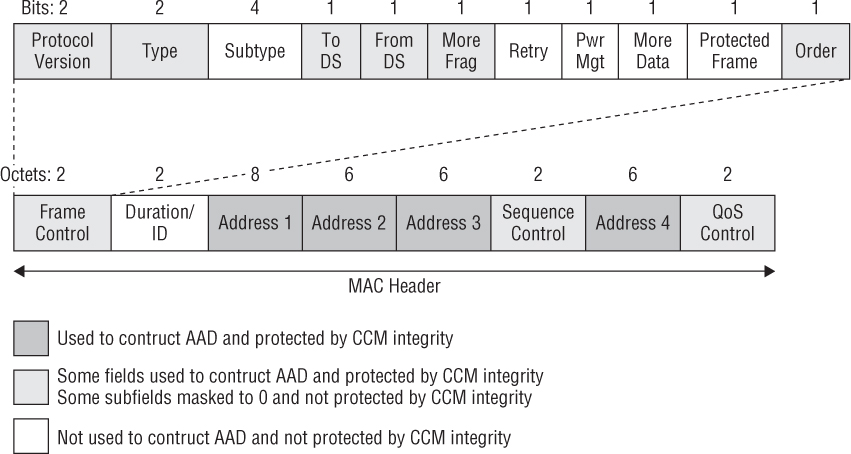
As shown in Figure 3.8, certain fields in the MPDU header are used to construct the AAD. The MIC provides integrity protection for these fields in the MAC header as well as for the frame body. All of the MAC addresses, including the BSSID, are protected. Portions of the other fields of the MAC header are also protected. Receiving stations will validate the integrity of these protected portions of the MAC header. For example, the frame type and the distribution bits that are subfields of the Frame Control field are protected. Receiving stations will validate the integrity of these protected portions of the MAC header. The AAD does not include the header Duration field, because the Duration field value can change due to normal IEEE 802.11 operation. For similar reasons, several subfields in the Frame Control field, the Sequence Control field, and the QoS Control field are masked to 0 and therefore are not protected. For example, the Retry bit and Power Management bits are also masked and are not protected by CCM integrity.
FIGURE 3.8 Additional authentication data (AAD)
A nonce is created from the PN, the TA, and priority data used in QoS.
The 8-octet CCMP header is constructed. The CCMP header includes the Key ID and the PN, which is divided into 6 octets. You will notice that the construction of the CCMP header is basically identical to the 8-octet TKIP header.
The CCM module, which uses the AES clock cipher, will now be used to create a data integrity check and encrypt the upper-layer data. The 128-bit temporal key, the nonce, the AAD, and the plaintext data are then processed to create an 8-byte MIC. The MSDU payload of the frame body and the MIC are then encrypted in 128-bit blocks. This process is known as CCM originator processing.
The original MAC header is appended to the CCMP header, the encrypted MSDU, and the encrypted MIC. A FCS is calculated over all of the fields of the header and entire frame body. The resulting 32-bit CRC is then placed in the FCS field.
CCMP MPDU
Figure 3.9 shows the CCMP MPDU. The first 32 bytes are the 802.11 MAC header, which does not change. The frame body consists of the CCMP header, the MSDU upper-layer payload, and the MIC. The CCMP header includes the Key ID and the PN, which is divided into 6 octets. You will notice that the format of the CCMP header is basically identical to the format of the 8-octet TKIP header (IV/Extended IV). The CCMP header is not encrypted. The MSDU payload and the 8-byte MIC are encrypted.
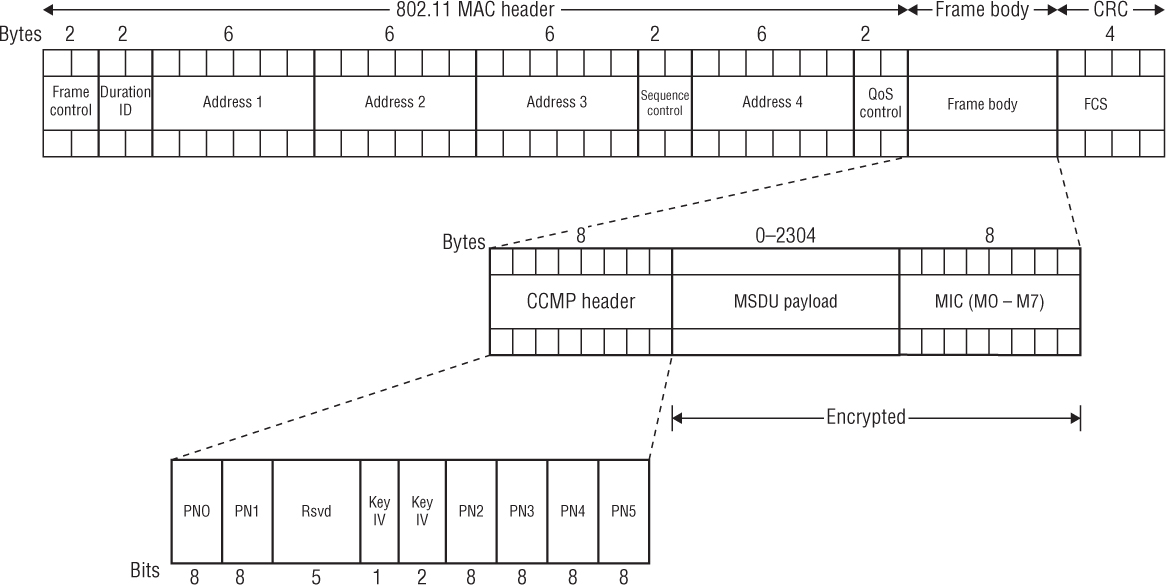
The overhead that results from CCMP encryption includes CCMP header (8 bytes) and the MIC (8 bytes). When CCMP is enabled, the entire size of the frame body inside an MPDU is expanded by 16 bytes to a maximum of 2,320 bytes. In other words, CCMP encryption adds 16 bytes of overhead to an 802.11 MPDU.
CCMP Encrypted Frames
In this exercise, you will use a protocol analyzer to view 802.11 data frames encrypted with CCMP.
To perform this exercise, first download the following file from the book’s online resource area, which can be accessed at www.sybex.com/go/cwsp2e:
CCMP_FRAMES.PCAP
After the file is downloaded, you will need packet analysis software to open this file. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
Click on one of the beacons with the source address of 00:1A:1E:94:4C:32. Typically the Packet Details pane appears in the lower section of the screen. This section contains annotated details about the selected frame. In this window, locate and expand the IEEE 802.11 Wireless LAN Management Frame section. In this section, expand the Tagged Parameters section, and then expand Tag: RSN Information. Here you will see AES (CCM) listed as the cipher suite type.
WPA/WPA2
Prior to the ratification of the 802.11i amendment, the Wi-Fi Alliance introduced the Wi-Fi Protected Access (WPA) certification. WPA was a snapshot of the not-yet-released 802.11i amendment, but only supported TKIP/ARC4 dynamic encryption key generation. 802.1X/EAP authentication was required in the enterprise, and passphrase authentication was required in a SOHO environment. TKIP was designed as a stopgap measure, with an expected limited lifespan (5 years), until 802.11i was finalized. Numerous publicly announced attacks have shown that there are flaws in TKIP and that it is able to be exploited. The Beck-Tews attack can recover plaintext from an encrypted short packet, recover the MIC key, and inject forged frames. However, the attack has a limitation in that the targets are restricted to WPA implementations that support WMM QoS features. The Ohiagi/Morii attack further enhances the Beck-Tews attack with a man-in-the-middle-approach. It should be noted that these attacks do not recover the encryption key but instead are used to recover the MIC checksum used for packet integrity.
These exploits and others can usually be prevented by changing TKIP settings, such as keying intervals on a WLAN controller or AP; however, the proper solution is to stop using TKIP and upgrade to CCMP with AES. TKIP has provided WLAN data privacy for more than the five years for which it was intended. WLANs should now be protected with CCMP to provide the necessary data privacy and data integrity.
The further migration from TKIP to CCMP can be seen in the IEEE 802.11n amendment, IEEE 802.11ac amendment, and IEEE 802.11-2012 standard, which all state that High Throughput (HT) or Very High Throughput (VHT) data rates are not allowed to be used if WEP or TKIP is enabled. The Wi-Fi Alliance also began requiring that all HT radios not use TKIP when using HT or VHT data rates. Starting on September 1, 2009, the Wi-Fi Alliance began testing 802.11n APs and client STAs for compliance with this requirement. This compliance was automatically applied to VHT APs and client STAs when 802.11ac was ratified. WLAN vendors still need to provide support for TKIP and WEP, but this support will only be with data rates up to 54 Mbps.
WPA2 is a Wi-Fi Alliance certification that is a mirror of the IEEE 802.11i security amendment. Testing of WPA2 interoperability certification began in September 2004. WPA2 incorporates the AES algorithm in CCMP, providing government-grade security based on the NIST FIPS 140-2 compliant AES encryption algorithm. WPA2 supports 802.1X/EAP authentication or preshared keys, and is backward-compatible with WPA.
Future Encryption Methods
As with any active technology, enhancements and advancement of the technology is commonplace, especially when security is involved. Counter Mode with CBC-MAC Protocol (CCMP) is at the core of the WPA2 certification. CCMP with AES was originally implemented with 54 Mbps WLANs and remained essentially unchanged with the introduction of newer PHY technologies, such as 802.11n and 802.11ac.
Cryptographic suites consist of much more than just the encryption algorithm. CCM defines a specific way of using AES encryption. CCM divides the data that is being encrypted into 16 byte blocks or chunks, and then links or chains them together. The ciphertext output of the first chunk is used as part of the encryption of the second chunk, which is then used as part of the encryption of the third chunk, and so on. This is where the term cipher block chaining (CBC) comes from. Additionally, due to technical reasons, CCMP requires that two AES operations be performed for each chunk. The sequential aspect of this process, along with the dual processes, requires a large number of AES operations, leading to a concern as to whether CCMP will be capable of keeping up with the faster WLAN gigabit rates that are being introduced.
Galois/Counter Mode (GCM) is significantly more efficient and faster than CCM. Like CCM, GCM uses the same AES encryption algorithm, however it is applied differently. GCM only needs a single AES operation per block, immediately reducing the encryption process by half. Additionally, GCM does not link or chain the blocks together. Since each block is not dependent on the previous block, they are independent of each other, and can be processed simultaneously using parallel circuits.
Galois/Counter Mode Protocol (GCMP) is not backward-compatible with existing Wi-Fi equipment and thus requires new hardware. GCMP has already been specified in the 802.11ad amendment, and is optional in 802.11ac. It will likely be seen in other technologies in the future.
Another technology, Suite B, is a suite of cryptographic algorithms specified by the National Institute of Standards and Technology (NIST) and is approved by the U.S. National Security Agency (NSA) for protecting classified and unclassified National Security Systems. Suite B consists of four encryption algorithms:
Advanced Encryption Standard (AES) Block Encryptions with key sizes of 128 or 256 bits used with either with Counter Mode (CTR) or Galois/Counter Mode (GCM)
Elliptic Curve Digital Signature Algorithm (ECDSA)
Elliptic Curve Diffie-Hellman (ECDH) Key Exchange
Secure Hash Algorithm (SHA) using SHA-256 and SHA-384
Suite B was announced in 2005. As of this writing, only a couple of WLAN vendors have provided Suite B–capable products.
Proprietary Layer 2 Implementations
In addition to the security and encryption standards, it is worthwhile to mention that there have also been vendor-specific products that have provided authentication and encryption for WLANs. Since these vendor-specific products have been based on industry-standard security and authentication technologies, they are better referred to as proprietary implementations rather than as proprietary solutions. These proprietary implementations required the installation of custom supplicant software on the client, which then used authentication and encryption standards to communicate with the authenticator and authentication server on the network. The proprietary implementations historically provided higher levels of security than was found on a typical 802.11 network. These products were designed and marketed to organizations that needed extremely high levels of security, usually government and military agencies. Most proprietary products were FIPS 140-2 compliant and incorporated standards such as AES 128, 192, and 256.
xSec was a Layer 2 protocol that provided a unified framework for securing both wired and wireless connections. xSec was jointly developed by Aruba Networks and Funk Software, a division of Juniper Networks. xSec implemented a FIPS-compliant mechanism for providing identity-based security. xSec used the AES-CBC-256 with HMAC-SHA1 algorithm, which provided for a 256-bit encryption key and even stronger data integrity. It was based on the IEEE 802.1X framework and supported many versions of EAP. xSec provided an extremely secure connection from the client, through the access point, all the way to an Aruba Networks WLAN controller.
Fortress Technologies was another company that used proprietary client software to enable secure communications between the wireless device and the Fortress Technologies controller or bridge, which was either connected to the wired network or provided wireless backhaul. The Fortress Technologies solution also used proprietary Fortress encryption that could use a 256-bit AES encryption key and stronger data integrity.
Summary
In this chapter, you learned about five different encryption ciphers: RC4, RC5, DES, 3DES, and AES. We discussed how symmetric and asymmetric algorithms function, as well as how stream and block ciphers are used to process plaintext data into ciphertext. We also covered the three different encryption technologies that are used in the 802.11 standard:
WEP uses a 24-bit IV and a static key as the seed that is fed through the ARC4 algorithm to generate a keystream. The keystream is combined with the plaintext data bits to create the ciphertext. The ICV is calculated and appended as the data integrity check.
TKIP uses a 128 bit temporal key + 48-bit TSC + TA address as the seeding material mixed together in the two-phase key-mixing process. The seed is then fed through the ARC4 algorithm to generate the keystream that is combined with the plaintext data bits to create the ciphertext. The MIC is also calculated and added as the data integrity check.
CCMP uses a 128-bit temporal key + the AAD + a nonce as the seed for the AES block cipher. No key mixing is needed due to the strength of the AES algorithm. Data is encrypted in 128-bit blocks. A MIC is also calculated and added for integrity. The CCMP MIC is stronger than the TKIP MIC.
The frame formats of each of these encryption technologies were reviewed. The relationship between the Wi-Fi Alliance certifications (WPA/WPA2) and the 802.11 encryption technologies was also discussed.
A couple of new encryption technologies were also introduced and explained: Galois/Counter Mode Protocol (GCMP) and Suite B.
Exam Essentials
Know the two categories of algorithms. Understand the differences between symmetric and asymmetric algorithms and how they are used when encrypting and decrypting data.
Know the process of how public key and private key encryption works. Understand that the public key is available to anyone and is used to encrypt the data, whereas the private key is kept secret and is used to decrypt the data.
Describe stream and block ciphers. Explain the process used by stream and block ciphers to encrypt the plaintext, along with how a Boolean XOR is incorporated in the process.
Define RC4, ARC4, RC5, DES, 3DES, and AES. Be able to explain the differences and similarities of all six of these algorithms.
Define WEP, TKIP, CCMP, and GCMP. Be able to explain the differences and similarities between these four security protocols. Understand the individual encryption and data integrity processes associated with each security protocol.
Describe the frame MPDU format. Explain the differences and similarities between the MPDU frame formats of the three 802.11 security protocols. Explain why the frame sizes vary and which portions of the frame are actually encrypted.
Explain the relationship between WPA/WPA2 and 802.11. Understand how the 802.11 standard relates to the Wi-Fi Alliance certification. Know which 802.11 security protocols are required for the Wi-Fi Alliance certifications.
Review Questions
1. CCMP/AES encryption adds an extra _________ of overhead to the body of an 802.11 data frame.
A. 16 bytes
B. 12 bytes
C. 20 bytes
D. 10 bytes
E. None of the above
2. TKIP/ARC4 encryption adds an extra _________ of overhead to the body of an 802.11 MPDU.
A. 16 bytes
B. 12 bytes
C. 20 bytes
D. 10 bytes
E. None of the above
3. An HT client STA is transmitting to an HT AP using modulation and coding scheme (MCS) #12 that defines 16-QAM modulation, two spatial streams, a 40-MHz bonded channel, and an 800 ns guard interval to achieve a data rate of 162 Mbps. According to the IEEE, which types of encryption should be used by the HT client STA? (Choose all that apply.)
A. Static WEP
B. Dynamic WEP
C. TKIP/ARC4
D. CCMP/AES
E. All of the above
4. CCMP/AES uses a _________ temporal key and encrypts data in _________ blocks.
A. 128-bit, 128-bit
B. 128-bit, 192-bit
C. 192-bit, 192-bit
D. 192-bit, 256-bit
E. 256-bit, 256-bit
5. When using an encryption suite that implements an asymmetric algorithm, which of the following statements is true? (Choose all that apply.)
A. Both the encrypting and decrypting parties share the same key.
B. Asymmetric algorithms generally are faster than symmetric algorithms.
C. Asymmetric algorithms generally are slower than symmetric algorithms.
D. Public and private encryption keys must be generated.
6. Andy calls the help desk for assistance with sending an encrypted message to Chris. Without knowing what type of security protocol and encryption Andy and Chris are using, which of the answers here could make the following scenario true?
In order for Andy to send an encrypted message successfully to Chris, Andy is told to enter ________________ on his computer; Chris needs to enter ________________ on his computer. (Choose all that apply.)
A. A public key, the companion private key
B. A private key, the companion public key
C. An asymmetric key, the same asymmetric key
D. A symmetric key, the same symmetric key
7. The IEEE 802.11-2012 standard states which of the following regarding 802.11n data rates and encryption? (Choose all that apply.)
A. WEP and TKIP must not be used.
B. CCMP can only be used.
C. WEP cannot be used; however, TKIP can be used if also using 802.1X.
D. Any encryption defined by the standard is allowed.
8. Given that CCMP uses a MIC for data integrity to protect the frame body and portions of the MAC header, what information needs to be constructed to protect certain fields in the MAC header?
A. Nonce
B. Extended IV
C. ICV
D. AAD
E. PN
F. IV
9. Which of the following is a FIPS encryption standard that uses a single 56-bit symmetric key? (Choose all that apply.)
A. RC4
B. RC5
C. DES
D. 3DES
E. AES
10. CCMP is an acronym made up of multiple components. Which of the following is an expanded version of this acronym? (Choose all that apply)
A. Counter Mode with Cipher-Block Chaining Message Authentication Code Protocol
B. Counter Message with Cipher-Block Chaining Mode Authentication Code Protocol
C. CTR with CBC-MAC Protocol
D. Counter Mode with CBC-MAC Protocol
E. None of these is accurate.
11. Which of the following is a random numerical value that is generated one time only and is used in cryptographic operations? (Choose all that apply.)
A. Pseudo-random function (PRF)
B. One-time password (OTP)
C. Single sign-on (SSO)
D. Throw-away variable (TV)
E. Nonce
12. Which of the following are Layer 2 encryption methods defined by the 802.11-2012 standard? (Choose all that apply.)
A. WEP
B. WPA
C. WPA2
D. TKIP
E. CCMP
F. GCMP
13. Which of the following encryption methods use symmetric algorithms? (Choose all that apply.)
A. WEP
B. TKIP
C. Public-key cryptography
D. CCMP
14. The Rijndael algorithm was the foundation for which of the following ciphers?
A. TKIP
B. DES
C. AES
D. CCMP
E. 3DES
15. A data integrity check known as Message Integrity Code (MIC) is used by which of the following? (Choose all that apply.)
A. WEP
B. TKIP
C. CCMP
D. AES
E. DES
16. Given that additional authentication data (AAD) is constructed from portions of the MPDU header and that the information is used for data integrity, which fields of the MAC header comprise the AAD? (Choose all that apply.)
A. Frame Control field
B. Transmitter address
C. Sequence Control field
D. Receiver address
E. Destination address
F. BSSID
17. Which of the following are encryption algorithms specified by the IEEE 802.11-2012 standard to be used for data encryption? (Choose all that apply.)
A. ARC4
B. RC5
C. IPsec
D. DES
E. 3DES
F. AES
18. The CCMP header is made up of which of the following pieces? (Choose all that apply.)
A. PN
B. TTAK
C. TSC
D. Key ID
E. MIC
19. 3DES has effective key sizes of how many bits? (Choose all that apply.)
A. 56
B. 64
C. 112
D. 128
E. 168
F. 192
20. AES supports three key lengths of 128, 192, and 256. The number of rounds performed for AES-128 is _______, for AES-192 is _______, and for AES-256 is _______. (Choose all that apply.)
A. 8
B. 10
C. 12
D. 14
E. 16
