Chapter 5 802.11 Layer 2 Dynamic Encryption Key Generation
IN THIS CHAPTER, YOU WILL LEARN ABOUT THE FOLLOWING:
✓ Advantages of dynamic encryption
The 802.11-2012 standard defines two classes of security methods using pre-RSNA and RSNA algorithms. Pre-RSNA methods use static WEP encryption and the legacy authentication methods that were discussed in Chapter 2, “Legacy 802.11 Security.” RSNA security methods use either TKIP/ARC4 or CCMP/AES encryption, dynamic key management procedures, and the PSK and 802.1X authentication methods that were discussed in Chapter 4, “802.1X/EAP Authentication.” In this chapter, you will learn that there is a symbiotic relationship between PSK/802.1X authentication and the generation of dynamic encryption keys. You will also learn about dynamic WEP, which was a short-term, nonstandard method of dynamic encryption, as well as the standards-based dynamic encryption key management methods that are widely deployed in today’s enterprise WLANs.
Advantages of Dynamic Encryption
Although the 802.1X/EAP framework does not require encryption, it highly suggests the use of encryption to provide data privacy. You have already learned that the purpose of 802.1X/EAP is authentication and authorization. If a supplicant is properly authenticated by an authentication server using a Layer 2 EAP protocol, the supplicant is allowed through the controlled port of the authenticator and communication at the upper layers of 3–7 can begin for the supplicant. 802.1X/EAP protects network resources so that only validated supplicants are authorized for access. However, as shown in Figure 5.1, an outstanding by-product of 802.1X/EAP can be the generation and distribution of dynamic encryption keys. Later in this chapter, you will see that dynamic encryption keys can also be generated as a by-product of PSK authentication.
EAP protocols that utilize mutual authentication provide “seeding material” that can be used to generate encryption keys dynamically. Mutual authentication is required to generate unique dynamic encryption keys. EAP-TLS, EAP-TTLS, EAP-FAST, EAP-LEAP, EAP-PEAP, and other versions of EAP utilize mutual authentication and can provide the seeding material needed for dynamic encryption key generation. EAP-MD5 cannot generate dynamic keys because EAP-MD5 uses only one-way authentication.
Legacy WLAN security involved the use of static WEP keys. The use of static keys is typically an administrative nightmare, and when the same static key is shared among multiple users, the static key is easy to compromise via social engineering. The first advantage of using dynamic keys rather than static keys is that they cannot be compromised by social engineering attacks because the users have no knowledge of the keys. The second advantage of dynamic keys is that every user has a different and unique key. If a single user’s encryption key was somehow compromised, none of the other users would be at risk because every user has a unique key. The dynamically generated keys are not shared between the users.
FIGURE 5.1 802.1X/EAP and dynamic keys
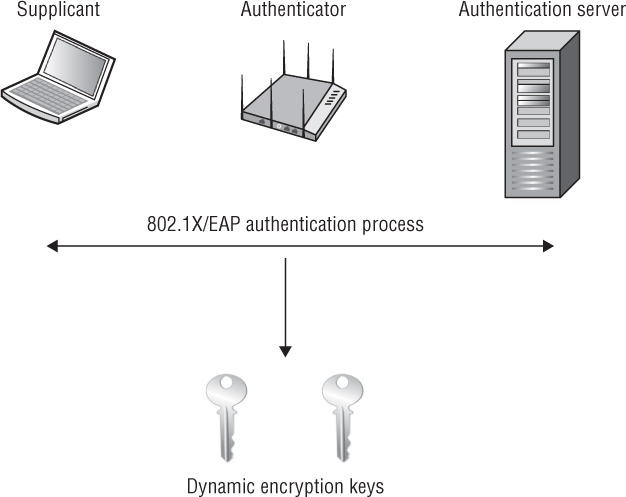
In 2004, the 802.11i security amendment was ratified, defining stronger encryption and better authentication methods. The 802.11i amendment, which is now part of the 802.11-2012 standard, fully defines robust security network association (RSNA), which is discussed later in this chapter. RSNA security methods use either TKIP/ARC4 or CCMP/AES encryption. Before TKIP/ARC4 or CCMP/AES was used, WLAN vendors offered a dynamic key generation security solution using WEP encryption. Many of these solutions were proprietary and did not offer vendor interoperability. Dynamic WEP has never been defined as any part of 802.11 security and was intended only as a stop-gap dynamic encryption solution until the stronger encryption methods of TKIP/ARC4 or CCMP/AES became available.
Dynamic WEP encryption keys were generated as a by-product of the 802.1X/EAP process. Dynamic WEP was a nonstandard and legacy encryption solution that was mostly used with autonomous access points prior to the availability of TKIP/ARC4 and CCMP/AES dynamic encryption. Within the 802.1X framework, the autonomous AP would be considered the authenticator. As shown in step 2 of Figure 5.2, after an EAP frame exchange where mutual authentication is required, both the authentication server and the supplicant now have information about each other due to the mutual authentication exchange of credentials. As shown in step 2, this newfound information is used as seeding material or keying material to generate a matching dynamic encryption key for both the supplicant and the authentication server. These dynamic keys are generated per session per user, meaning that every time a supplicant authenticates, a new key is generated and every user has a unique and separate key. This dynamic WEP session key is often referred to as the unicast key because it is the dynamically generated WEP key that is used to encrypt and decrypt all unicast 802.11 data frames.
FIGURE 5.2 Dynamic WEP process
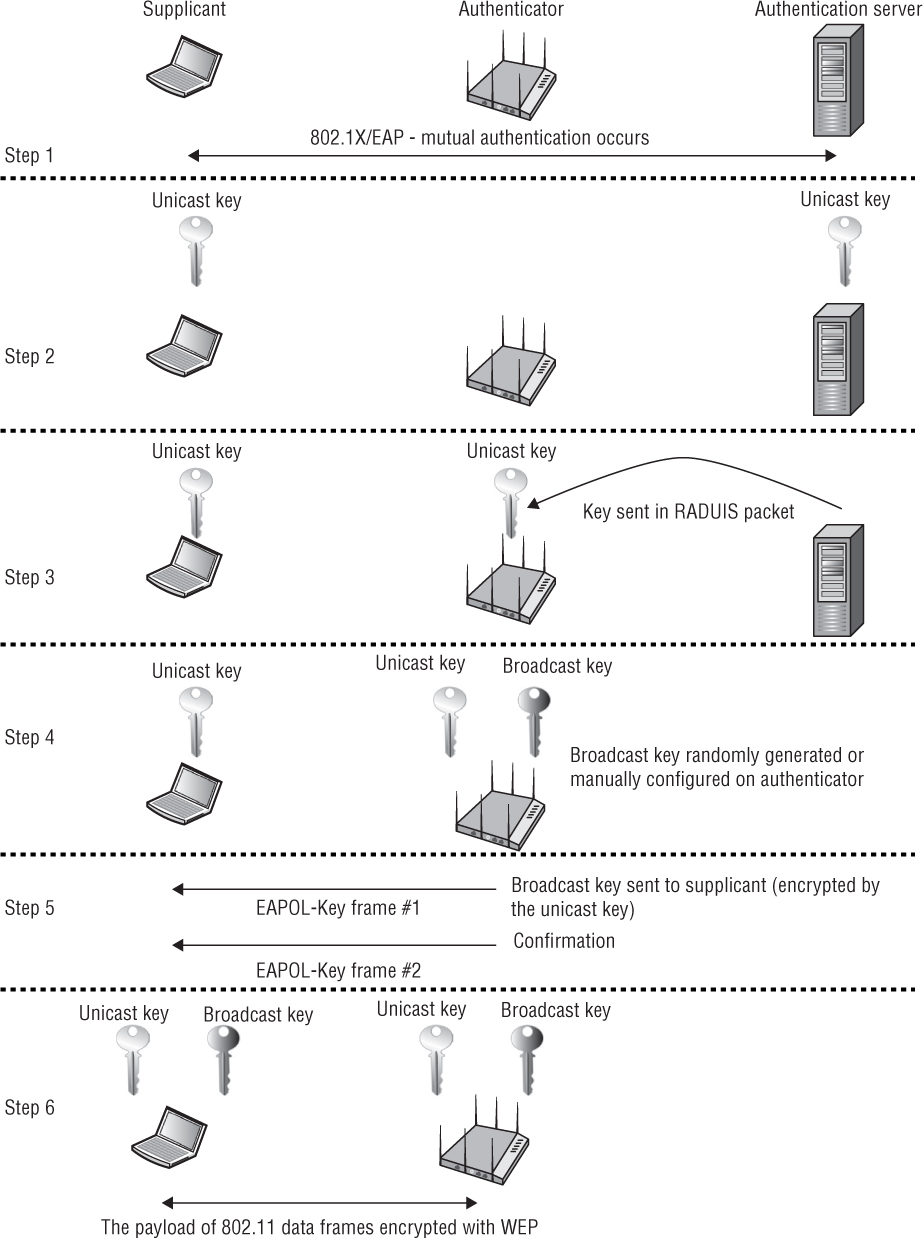
As shown in step 3, after the unicast key is created, the authentication server delivers its copy of the unicast key encapsulated inside a RADIUS packet to the authenticator. The access point and the client station now both have unique unicast keys that can be used to encrypt and decrypt unicast 802.11 data frames. A second key exists on the access point known as the broadcast key. As depicted in step 4, the broadcast key can be manually configured on the access point or can be randomly generated. The broadcast key is used to encrypt and decrypt all broadcast and multicast 802.11 data frames. Each client station has a unique and separate unicast key, but every station must share the same broadcast key. As step 5 shows, the broadcast key is delivered from the access point to the client station in a unicast frame encrypted with the client station’s unique unicast key. When dynamic WEP is deployed, a two EAPOL-Key frame exchange always follows the EAP frame exchange. The two EAPOL-Key frames are both sent by the authenticator to the supplicant. The first EAPOL-Key frame carries the broadcast key from the access point to the client. The second EAPOL-Key frame is effectively a confirmation that the keys are installed and that the encryption process can begin. Once the client station has both the unicast and broadcast keys, the MAC service data unit (MSDU) payload of all 802.11 data frames will then be protected using WEP encryption.
Dynamic WEP
In this exercise, you will use a protocol analyzer to view the 802.11 frame exchanges used to create dynamic WEP keys.
To perform this exercise, you need to first download the PEAP_WEP.PCAP file from the book’s online resource area, which can be accessed at www.sybex.com/go/cwsp2e.
After the file is downloaded, you will need packet analysis software to open it. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
Using the packet analyzer, open the PEAP_WEP.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
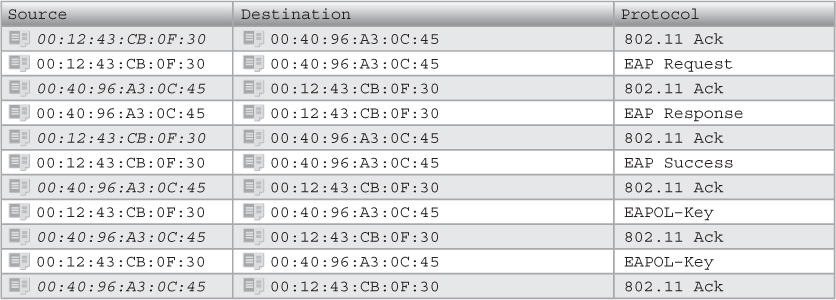
Observe that the EAP frame exchange in packets 346–389 is using EAP-PEAP. The access point (authenticator) MAC address is 00:12:43:CB:0F:30. The client radio (supplicant) MAC address is 00:40:96:A3:0C:45.
Notice the two EAPOL-Key frames in packets 391 and 393 that are being sent from the access point to the client.
Notice that all 802.11 data frames are encrypted using a WEP key that was dynamically generated.
Click on packet 395. Typically the packet details window appears in the lower section of the screen. This section contains annotated details about the selected frame. In this window, locate and expand the IEEE QoS Data Frame header. Locate the WEP parameters field to verify the use of WEP encryption.
Robust Security Network (RSN)
The 802.11i amendment, which was ratified and published as IEEE Std. 802.11i-2004, defined stronger encryption and better authentication methods. The 802.11i security amendment is now part of the 802.11-2012 standard. The 802.11-2012 standard defines what is known as a robust security network (RSN) and robust security network associations (RSNAs).
A security association is a set of policies and keys used to protect information. A robust security network association (RSNA) requires two 802.11 stations (STAs) to establish procedures to authenticate and associate with each other as well as create dynamic encryption keys through a process known as the 4-Way Handshake. This association between two stations is referred to as an RSNA. In other words, any two radios must share dynamic encryption keys that are unique between those two radios. CCMP/AES encryption is the mandated encryption method, whereas TKIP/ARC4 is an optional encryption method. As you have already learned, only CCMP/AES can be used for 802.11n and 802.11ac data rates.
Anyone who has passed the CWNA certification exam is familiar with the WLAN topologies of a basic service set (BSS) and an independent basic service set (IBSS). The basic service set (BSS) is the cornerstone topology of an 802.11 network. The communicating devices that make up a BSS are solely one AP with one or more client stations. Client stations join the AP’s wireless domain and begin communicating through the AP. Stations that are members of a BSS have a Layer 2 connection and are called associated. The 48-bit (6-octet) MAC address of an access point’s radio is known as the basic service set identifier (BSSID). The BSSID address is the Layer 2 identifier of each individual BSS. Most often, the BSSID is the MAC address of the access point. Do not confuse the BSSID address with the SSID. The service set identifier (SSID) is the logical WLAN name that is user configurable, while the BSSID is a Layer 2 MAC address used to identify a basic service set (BSS).
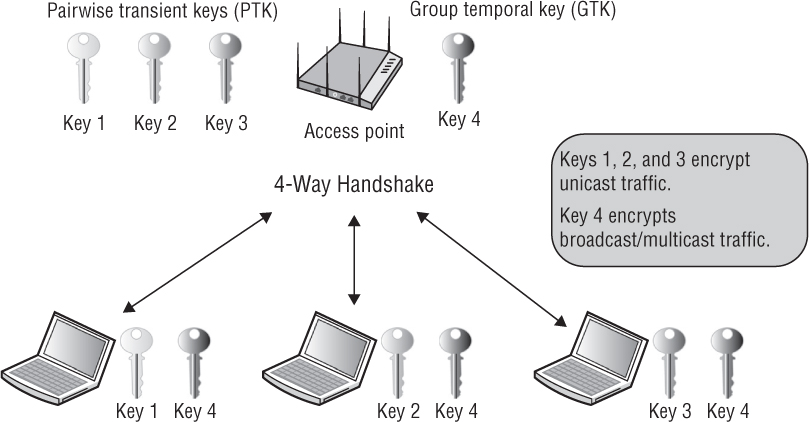
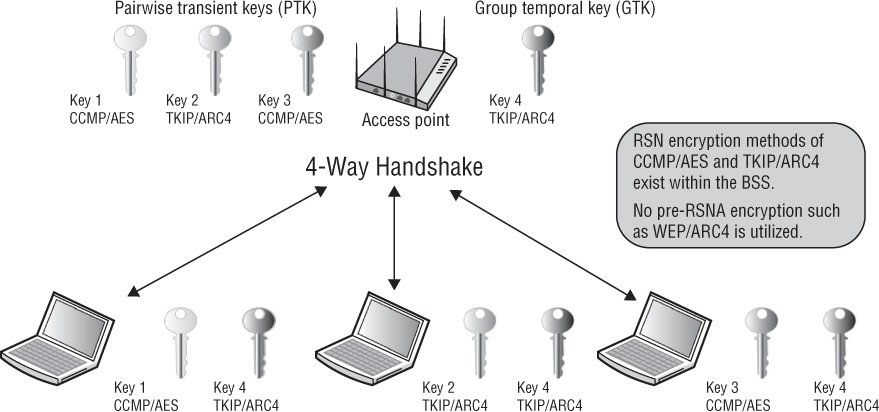
When RSN security associations are used within a BSS, all of the client station radios have unique encryption keys that are shared with the radio of the access point. As shown in Figure 5.3, all the client stations have undergone a unique RSNA process called the 4-Way Handshake where the access point and each client radio has either a unique dynamic TKIP/ARC4 or CCMP/AES key that is shared between the client radio and the access point radio. This key is called the pairwise transient key (PTK) and is used to encrypt/decrypt unicast traffic. All the stations share a broadcast key called the group temporal key (GTK), which is used to encrypt/decrypt all broadcast and multicast traffic. You will learn more about the PTK and GTK keys later in this chapter in the section “4-Way Handshake.”
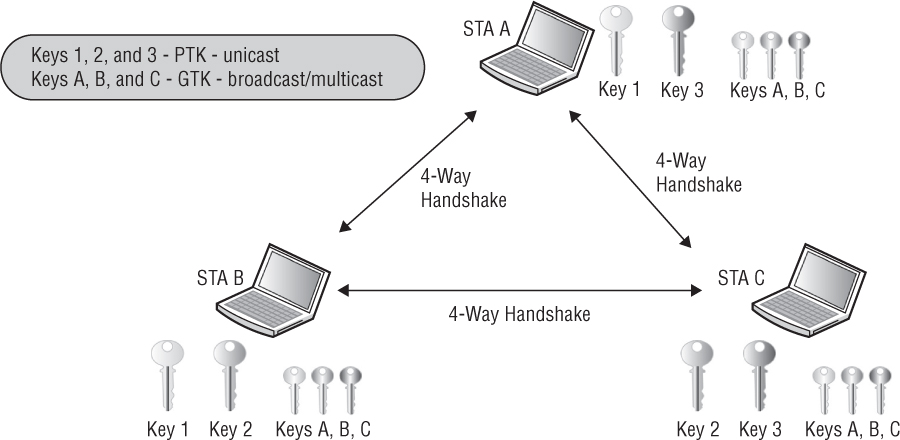
The 802.11 standard also defines a WLAN topology called an independent basic service set (IBSS). The radio cards that make up an IBSS network consist solely of client stations (STAs), and no access point is deployed. An IBSS network that consists of just two STAs is analogous to a wired crossover cable. An IBSS can, however, have multiple client stations in one physical area communicating in an ad hoc fashion. As you can see in Figure 5.4, all the stations within an IBSS have undergone a unique RSNA process (called the 4-Way Handshake) with each other, because all unicast communications are peer to peer. Each station has either a unique dynamic TKIP/ARC4 or CCMP/AES pairwise transient key (PTK) that is shared with any other station within the IBSS. In an IBSS, each STA defines its own group temporal key (GTK), which is used for its broadcast/multicast transmissions. Each IBSS station will use either the 4-Way Handshake or the Group Key Handshake to distribute its transmit GTK to its peer stations. PSK authentication is used within the IBSS to seed the 4-Way Handshake. Therefore, every time a client joins an IBSS with a peer station, the client must reauthenticate and create new keys.
FIGURE 5.4 RSNA within an IBSS
A robust security network (RSN) is a network that allows for the creation of only robust security network associations (RSNAs). In other words, a basic service set (BSS) where all the stations are using only TKIP/ARC4 or CCMP/AES dynamic keys for encryption would be considered an RSN. Robust security only exists when all devices in the service set use RSNAs. As shown in Figure 5.5, all the stations within the BSS have established an RSNA that resulted in either TKIP/ARC4 or CCMP/AES unique dynamic keys. Because only RSNA security is in use, the pictured BSS would be considered a robust security network. Note that the group temporal key (GTK) uses TKIP/ARC4 to encrypt/decrypt broadcast and multicast traffic within the robust security network BSS. Although the majority of modern-day WLANs radios use CCMP/AES encryption, older radios that only support TKIP/ARC4 still exist. If only one TKIP/ARC4 client station is associated within the BSS, the lowest common dominator method of TKIP encryption would be used for broadcast and multicast traffic.
FIGURE 5.5 Robust security network
As you learned in Chapter 2, a pre-RSN security network uses static WEP encryption and legacy authentication methods. A WLAN that uses dynamic WEP encryption keys would also be considered as using pre-RSN security, but the use of dynamic WEP was never defined by either the IEEE or the Wi-Fi Alliance. The 802.11-2012 standard does allow for the creation of pre-robust security network associations (pre-RSNAs) as well as RSNAs. In other words, legacy security measures can be supported in the same basic service set (BSS) along with RSN-security-defined mechanisms. A transition security network (TSN) supports RSN-defined security as well as legacy security, such as WEP, within the same BSS. As you can see in Figure 5.6, some of the stations within the BSS have established an RSNA that resulted in either TKIP/ARC4 or CCMP/AES unique dynamic keys. However, some of the stations are using static WEP keys for encryption. Because both RSNAs and pre-RSNAs are in use, the pictured BSS would be considered a transition security network. Note that the group temporal key (GTK) uses a static WEP key to encrypt/decrypt broadcast and multicast traffic within the transition security network BSS. Although the majority of modern-day WLAN radios use CCMP/AES encryption, older radios that only support WEP still exist. If only one WEP client station is associated within the BSS, the lowest common dominator method of WEP encryption would be used for broadcast and multicast traffic.
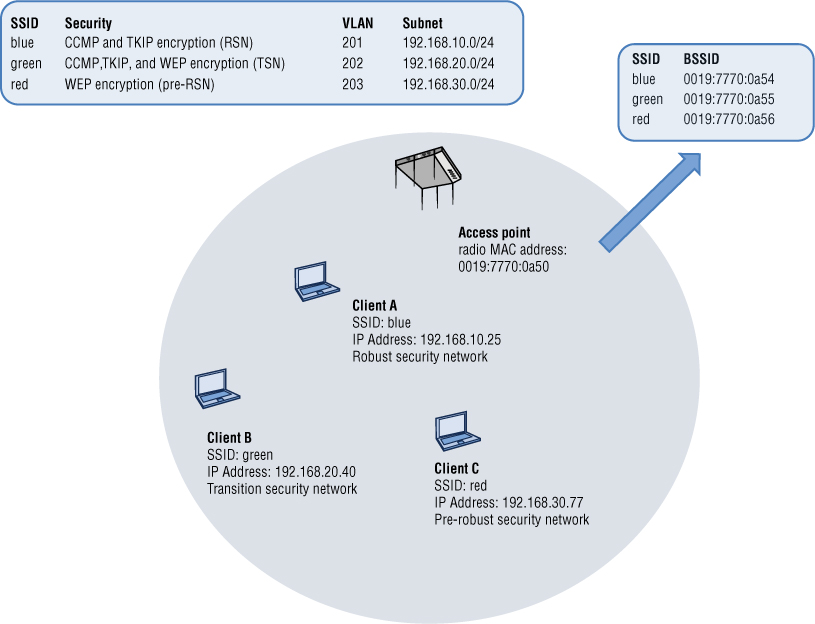
As you learned earlier in this chapter, each WLAN has a logical name (SSID) and each WLAN BSS has a unique Layer 2 identifier, the basic service set identifier (BSSID). The BSSID is typically the MAC address of the access point’s radio card if only one SSID is being transmitted. However, most WLAN vendors offer the capability to transmit multiple SSIDs from an access point radio. Client devices typically get confused when they see multiple SSIDs all tied to the same MAC address; therefore, if multiple SSIDs are transmitted from the same AP radio, multiple BSSIDs are also needed. As shown in Figure 5.7, the multiple BSSIDs are effectively virtual MAC addresses that are incremented or derived from the actual physical MAC address of the AP radio. Effectively, multiple basic service sets exist within the same coverage cell area of the access point. As shown in Figure 5.7, because each SSID may have been configured with different security, an RSN WLAN, a pre-RSNA WLAN, and a TSN WLAN can all exist within the same coverage area of an access point.
FIGURE 5.6 Transition security network
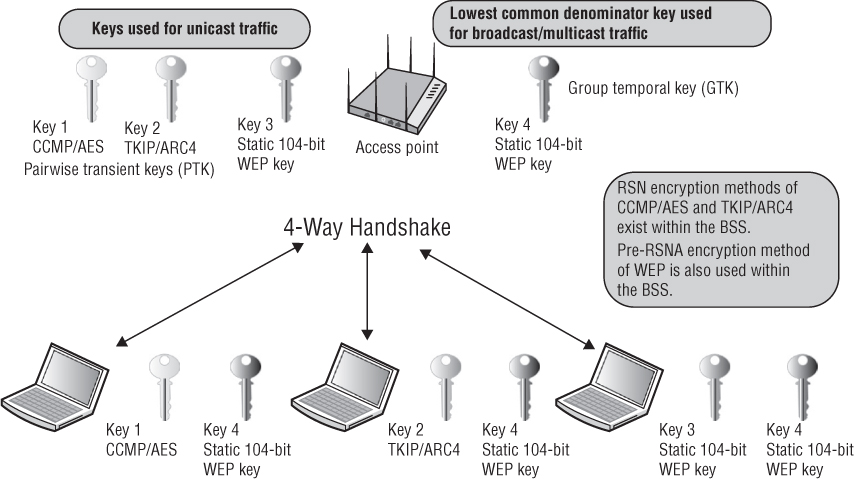
FIGURE 5.7 RSN, pre-RSN, and TSN within the same AP cell
RSN Information Element
Within a BSS, how can client stations and an access point notify each other about their RSN capabilities? RSN security can be identified by a field found in certain 802.11 management frames. This field is known as the robust security network information element (RSNIE) and is often referred to simply as the RSN information element. An information element is an optional field of variable length that can be found in 802.11 management frames. The RSN information element can identify the encryption capabilities of each station. The RSN information element will also indicate whether 802.1X/EAP authentication or preshared key (PSK) authentication is being used.
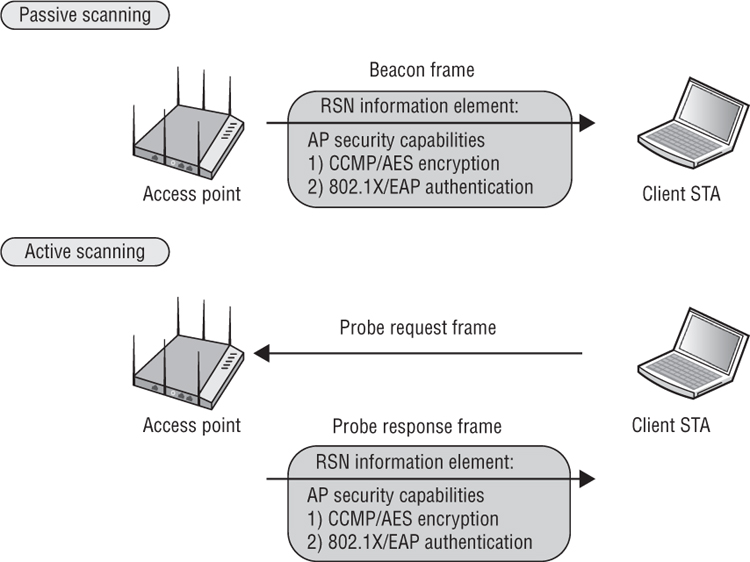
The RSN information element field is always found in four different 802.11 management frames: beacon management frames, probe response frames, association request frames, and reassociation request frames. The RSN information element can also be found in reassociation response frames if 802.11r capabilities are enabled on an AP and roaming client. Within a basic service set, an access point and client stations use the RSN information element within these four management frames to communicate with each other about their security capabilities prior to establishing association. As shown in Figure 5.8, access points will use beacons and probe response frames to inform client stations of the AP security capabilities.
FIGURE 5.8 Access point RSN security capabilities
As you can see in Figure 5.9, client stations use the association request frame to inform the access point of the client station security capabilities. When stations roam from one access point to another access point, they use the reassociation request frame to inform the new access point of the roaming client station’s security capabilities. The security capabilities include supported encryption cipher suites and supported authentication methods.
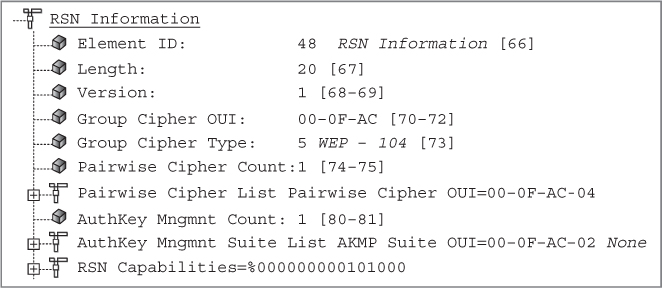
All 802.11 radios will use one cipher suite for unicast encryption and another cipher suite for encrypting multicast and broadcast traffic. Pairwise unicast encryption keys are created that are unique between two stations—the AP and a single client station. The pairwise cipher suite of the RSN information element contains the cipher suite information used by stations for unicast traffic. The cipher suite selector 00-0F-AC-04 (CCMP) is the default cipher suite value. The cipher suite selector 00-0F-AC-02 (TKIP) is optional. A group key is also created that is shared by all stations for broadcast and multicast traffic. The Group Cipher Suite field of the RSN information element contains the cipher suite information used by the BSS to protect broadcast/multicast traffic. The actual creation process of the pairwise and group keys is discussed later in this chapter in the section “4-Way Handshake.”
FIGURE 5.9 Client station RSN security capabilities
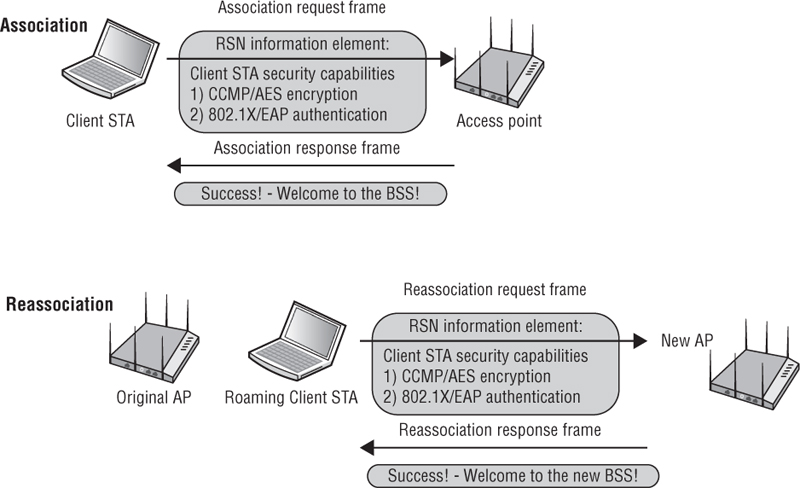
Figure 5.10 shows a capture of a beacon frame from an access point configured to use only CCMP/AES encryption. The RSN information element indicates that CCMP/AES encryption is being used for both the group cipher suite and the pairwise cipher suite. The access point is using the RSN information element to inform all client stations that the AP will be using CCMP encryption for all broadcast/multicast and will also be using CCMP/AES encryption for any unicast traffic. Any client station must support those exact ciphers for the client stations to be able to establish a robust secure network association (RSNA) with the AP and to create dynamic encryption keys. In other words, the client stations must support CCMP/AES encryption to be allowed to join the AP’s basic service set.
Figure 5.11 shows a beacon frame from an access point configured to support both CCMP/AES and TKIP/ARC4 encryption. The RSN information element indicates that TKIP encryption is being used for the group cipher suite. CCMP/AES is the default cipher for the pairwise cipher suite. The access point is using the RSN information element to inform all client stations that the AP will support either CCMP/AES or TKIP/ARC4 encryption for any unicast traffic. However, only TKIP/ARC4 encryption can be used for broadcast/multicast traffic. In this situation, the client stations must support either CCMP or TKIP to be allowed to join the AP’s basic service set. Because all the stations share a single group encryption key for broadcast and multicast traffic, the lowest common denominator must be used for the group cipher. In this case, the group cipher is TKIP.
FIGURE 5.10 RSN Information element—CCMP pairwise and CCMP group cipher
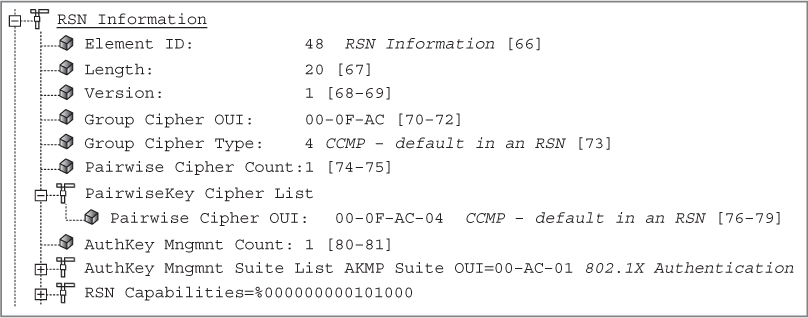
FIGURE 5.11 RSN information element—CCMP pairwise and TKIP group cipher
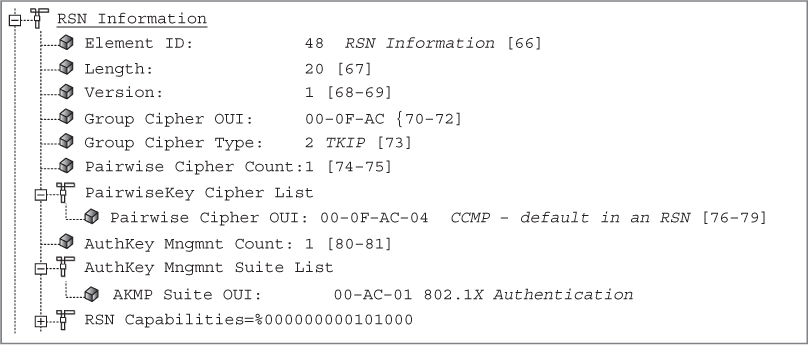
The cipher suite selectors 00-0F-AC-01 (WEP-40) and 00-0F-AC-05 (WEP-104) are used as a group cipher suite in a transition security network (TSN) to allow pre-RSNA devices to join a BSS. For example, an access point might support CCMP, TKIP, and WEP encryption. WPA2-capable clients will use CCMP encryption for unicast traffic between the client STA and the AP. WPA-capable clients will use TKIP encryption for unicast traffic between the client STAs and the AP. Legacy clients will use WEP encryption for unicast traffic between the client STAs and the AP. All of the clients will use WEP encryption for the broadcast and multicast traffic. Because all the stations share a single group encryption key for broadcast and multicast traffic, the lowest common denominator must be used for the group cipher. In the case of a TSN, the group cipher is WEP.
Figure 5.12 shows a capture of a beacon frame from an access point configured to support CCMP/AES, TKIP/ARC4, and static WEP/ARC4 encryption using a 40-bit static key. The RSN information element indicates that WEP-40 encryption is being used for the group cipher suite. CCMP/AES is the default cipher for the pairwise cipher suite. The access point is using the RSN information element to inform all client stations that the AP can support CCMP/AES, TKIP/ARC4 encryption, or WEP-40 for any unicast traffic. However, only WEP-40 encryption can be used for broadcast/multicast traffic. In this situation, the client stations can support CCMP/AES, TKIP/ARC4, or WEP-40 and be allowed to join the AP’s basic service set.
FIGURE 5.12 RSN information element—CCMP pairwise and WEP-40 group cipher
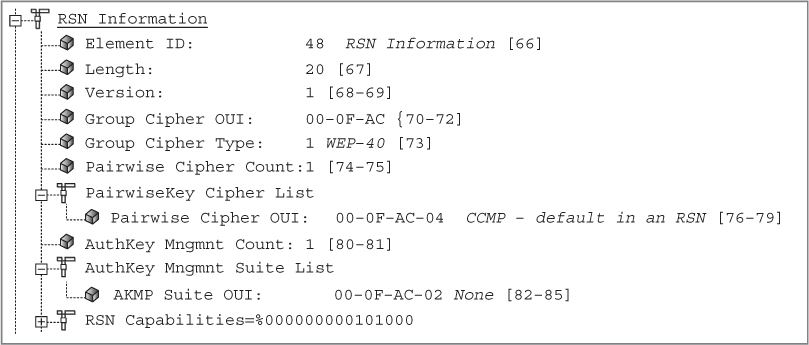
The RSN information element can also be used to indicate what authentication methods are supported. The authentication key management (AKM) suite field in the RSN information element indicates whether the station supports either 802.1X authentication or PSK authentication. If the AKM suite value is 00-0F-AC-01, authentication is negotiated over an 802.1X infrastructure using an EAP protocol. If the AKM suite value is 00-0F-AC-02 (PSK), then PSK is the authentication method that is being used.
Figure 5.13 shows a capture of an association request frame from a client station configured to 802.1X/EAP. The AKM suite field in the RSN information element indicates that 802.1X is the chosen authentication method.
FIGURE 5.13 RSN information element—AKM suite field: 802.1X
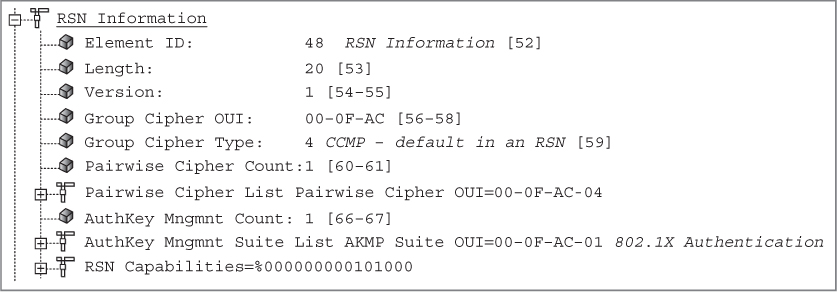
Client radios and access point radios use the RSN information element to inform each other about their RSN security capabilities. The access point uses beacons and probe response frames to educate clients about the authentication and encryption methods that are supported by the AP. Client stations use association request and reassociation request frames to educate the AP about the authentication and encryption methods that are supported by the client. After the exchange of RSN information, the radios can proceed with PSK or 802.1X authentication and then create dynamic encryption keys.
TIP
We further discuss the RSN information element in Chapter 7, “802.11 Fast Secure Roaming.”
Authentication and Key Management (AKM)
The 802.11-2012 standard defines authentication and key management (AKM) services. AKM services consist of a set of one or more algorithms designed to provide authentication and key management, either individually or in combination with higher-layer authentication and key-management algorithms, which are often outside the scope of the 802.11-2012 standard. Non-IEEE-802 protocols may be used for AKM services. Many of these non-IEEE-802 protocols are defined by other standards organizations, such as the Internet Engineering Task Force (IETF). In Chapter 4, you learned about the various EAP protocols used within an 802.1X framework for authentication. EAP protocols are also used during AKM services. An authentication and key management protocol (AKMP) can be either a preshared key (PSK) or an EAP protocol used during 802.1X authentication. The 802.11-2012 standard also defines a third type of AKMP called Simultaneous Authentication of Equals (SAE), which could be the future replacement for PSK authentication. SAE is discussed in greater detail in Chapter 6, “PSK Authentication.”
As you have previously learned, the main goal of 802.1X/EAP within a WLAN is twofold:
Authentication Validate the credentials of a client station seeking access to network resources via the WLAN portal.
Authorization Grant access for the client station to network resources via the WLAN portal.
You also have learned that the goal of encryption is to provide data privacy for the MSDU payload in 802.11 data frames. AKM services require both authentication processes and the generation and management of encryption keys. Although authentication and encryption have different goals and are different processes, they are linked together in AKM services. In other words, an authentication process is necessary to generate dynamic encryption keys. The 802.1X/EAP and PSK authentication processes generate the seeding material needed to create dynamic encryption keys. Furthermore, until dynamic encryption keys are created, the controlled port of an 802.1X authenticator will not open. As shown in Figure 5.14, a symbiotic relationship exists between authentication and dynamic encryption. Authorization is not finalized until encryption keys are created and encryption keys cannot be created without authentication.
FIGURE 5.14 Authentication and key management (AKM)—overview
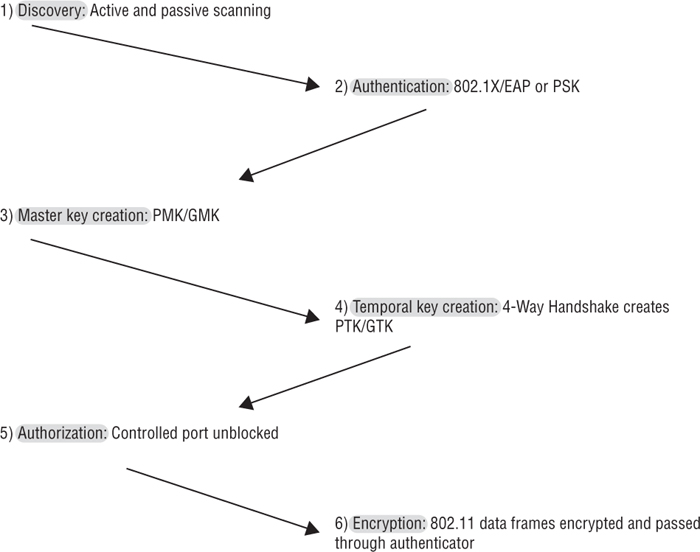
When an 802.1X/EAP authentication solution is used, AKM operations include the following:
Secure Channel The 802.11-2012 standard makes the assumption that the authenticator and authentication server (AS) have established a secure channel. The security of the channel between the authenticator and the AS is outside the scope of the 802.11-2012 standard. Authentication credentials must be distributed to the supplicant and authentication server prior to association. Many of the processes were discussed in Chapter 4.
Discovery As shown in Figure 5.15, a client station discovers the access point’s security requirements by passively monitoring for beacon frames or through active probing. The access point’s security information can be found in the RSN information element field inside beacon and probe response frames. The client station security requirements are delivered to the AP in association and reassociation frames.
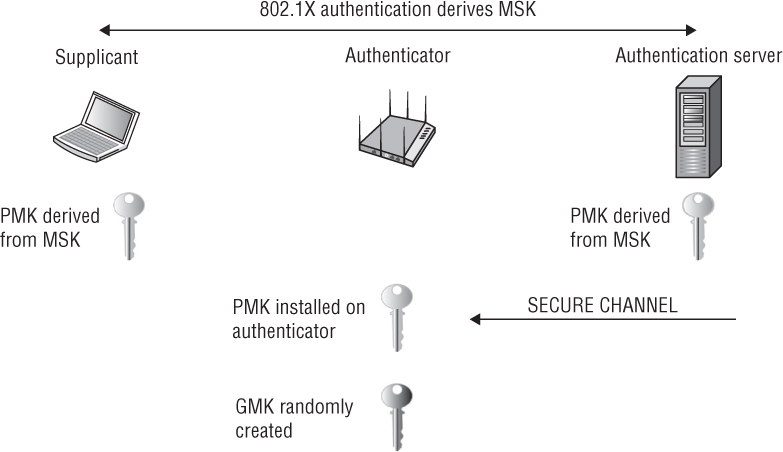
Authentication As shown in Figure 5.16, the authentication process starts when the AP’s authenticator sends an EAP-Request or the client station supplicant sends an EAPOL-Start message. As you learned in Chapter 4, EAP authentication frames are then exchanged between the supplicant and authentication server via the authenticator’s uncontrolled port. The supplicant and the authentication server validate each other’s credentials. The controlled port remains blocked.
FIGURE 5.15 Authentication and key management (AKM)—discovery component
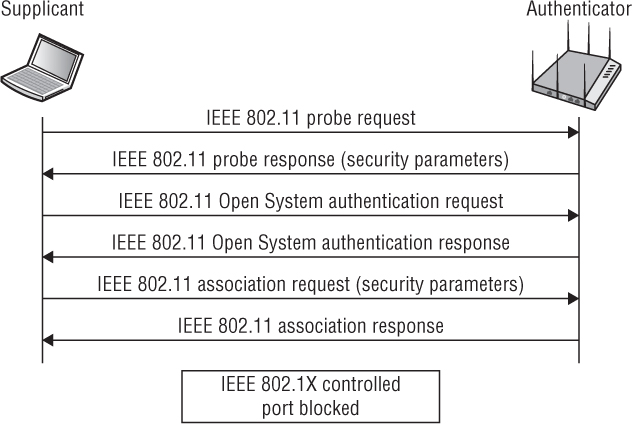
FIGURE 5.16 Authentication and key management (AKM)—authentication and master key generation component
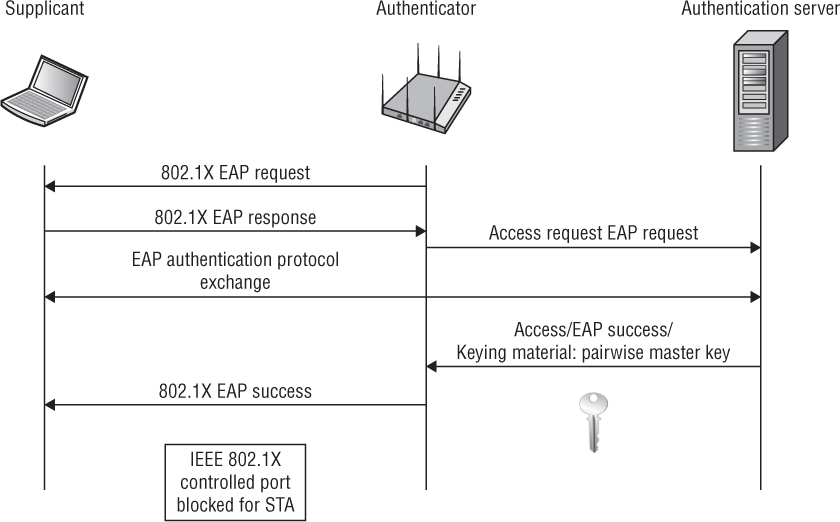
Master Key Generation As you can see in Figure 5.16, the supplicant and authentication server generate a master encryption key called the pairwise master key (PMK). The PMK is sent from the authentication server to the authenticator over the secure channel described earlier. The controlled port is still blocked.
Temporal Key Generation and Authorization As shown in Figure 5.17, a 4-Way Handshake frame exchange between the supplicant and the authenticator utilizing EAPOL-Key frames is used to generate temporary encryption keys that are used to encrypt and decrypt the MSDU payload of 802.11 data frames. The 4-Way Handshake will be discussed in detail in the next section of this chapter. Once the temporal keys are created and installed, the controlled port of the authenticator opens, and the supplicant can then send encrypted 802.11 data frames through the controlled port onward to network resources.
FIGURE 5.17 Authentication and key management (AKM)—temporal key generation and authorization
Authentication and Key Management
In this exercise, you will use a protocol analyzer to view all the 802.11 frame exchanges used during AKM services.
To perform this exercise, you need to first download the AKM.PCAP file from the book’s online resource area, which can be accessed at www.sybex.com/go/cwsp2e.
After the file is downloaded, you will need packet analysis software to open it. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
Using the packet analyzer, open the AKM.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
Observe the beacon and probing frames in packets 196–199. Normal open system authentication and association occurs during frames 201–207.
Observe packets 209–253 which show the EAP authentication frames that are exchanged between the supplicant and authentication server via the authenticator’s uncontrolled port. The supplicant and the authentication server validate each other’s credentials. The controlled port remains blocked.
Observe packets 255–261. A 4-Way Handshake exchange between the supplicant and the authenticator utilizing EAPOL-Key frames is used to generate temporary encryption keys. Notice that all 802.11 data frames are now encrypted.
As you can see, a good portion of AKM is the authentication process. In the next sections of this chapter, you will learn in greater detail about the generation of both master and temporary keys, which is the other key component of AKM. Remember that authentication and encryption key management are dependent on each other.
RSNA Key Hierarchy
AKM services also include the creation of encryption keys. Some of the encryption keys are derived from the authentication process, some of the keys are master keys, and some are the final keys that are used to encrypt/decrypt 802.11 data frames. As Figure 5.18 shows, a total of five keys make up a top-to-bottom hierarchy that is needed to establish a final robust security network association (RSNA). This key hierarchy includes a key derived from either an 802.1X/EAP authentication or derived from PSK authentication. One set of keys is considered to be group keys, which are keys that are used to protect multiple destinations. Another set of keys is considered to be pairwise. A pairwise relationship can be defined as two entities that are associated with each other: for example, an access point (AP) and an associated station (STA), or two stations communicating in an independent basic service set (IBSS).
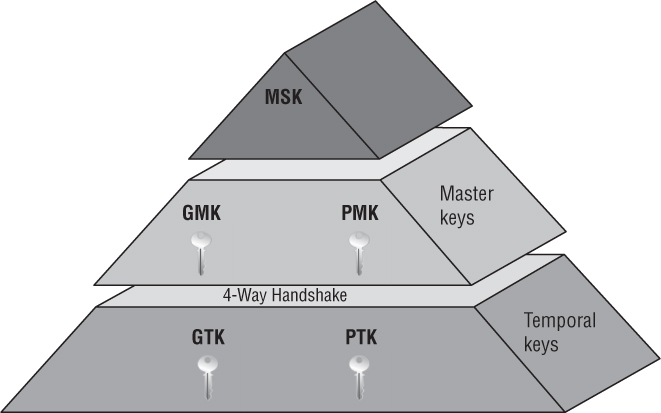
Master Session Key (MSK)
At the top of the RSNA key hierarchy is the master session key (MSK), which is also sometimes referred to as the AAA key. The MSK is generated either from an 802.1X/EAP process or is derived from PSK authentication. You will learn how the master session key (MSK) is derived from PSK authentication later in this chapter in the section “Passphrase-to-PSK Mapping.” When an 802.1X/EAP infrastructure is deployed, both the authentication server and the supplicant will know information about each other after the mutual authentication exchange of credentials. The MSK is the keying material that is derived from the EAP process and exported by the EAP method to the supplicant and authentication server. The MSK is at least 64 octets in length. How the MSK is generated from the EAP process is outside of the scope of the 802.11-2012 standard and is EAP method specific.
Master Keys
After the creation of the MSK as a result of 802.1X/EAP, two master keys are created. Try to think of the MSK as seeding material or keying material that is a result of 802.1X/EAP mutual authentication. The MSK seeding material is then used to create a master key called the pairwise master key (PMK).
The PMK is derived from the MSK seeding material. The PMK is simply computed as the first 256 bits (bits 0–255) of the MSK. Because the PMK is derived from the MSK seeding material, a PMK now resides on both the supplicant and the authentication server. Effectively a portion of the MSK seeding material becomes the PMK. A new, unique PMK is generated every time a client authenticates or reauthenticates. It is very important to understand that when 802.1X/EAP is used, every client’s PMK is unique to that individual client.
As shown in Figure 5.19, the PMK is then sent from the authentication server over a secure channel to the authenticator. The security of the channel between the authenticator and the AS is outside the scope of the 802.11-2012 standard. A PMK is now installed on both the client station, which is the supplicant, and the access point, which is the authenticator.
Another master key, called the group master key (GMK), is randomly created on the access point/authenticator. Any GMK may be regenerated at a time interval configured on the AP to reduce the risk of the GMK being compromised.
Keep in mind that master keys are not used to encrypt or decrypt 802.11 data. The master keys are now the seeding material for the 4-Way Handshake process. The 4-Way Handshake is the final process that is used to create the keys that are used to encrypt and decrypt data. The keys generated from the 4-Way Handshake are called the pairwise transient key (PTK) and the group temporal key (GTK). The pairwise master key (PMK) is used to create the pairwise transient key (PTK), and the group master key (GMK) is used to create the group temporal key (GTK). In other words, the master keys are used to produce the temporal keys that are used to encrypt 802.11 data frames. The 4-Way Handshake process used to create the temporal encryption keys can begin when the GMK is created and installed on the authenticator, and the PMK is created and installed on both the supplicant and authenticator.
Temporal Keys
As you will learn, the 4-Way Handshake process creates temporal keys that are used by the client station and the access point to encrypt and decrypt 802.11 data frames. The pairwise transient key (PTK) is used to encrypt all unicast transmissions between a client station and an access point. As discussed earlier in this chapter, each PTK is unique between each individual client station and the access point. Every client station possesses a unique PTK for unicast transmissions between the client STA and the AP. PTKs are used between a single supplicant and a single authenticator.
The group temporal key (GTK) is used to encrypt all broadcast and multicast transmissions between the access point and multiple client stations. Although the GTK is dynamically generated, it is shared among all client STAs for broadcast and multicast frames. The GTK is used between all supplicants and a single authenticator.
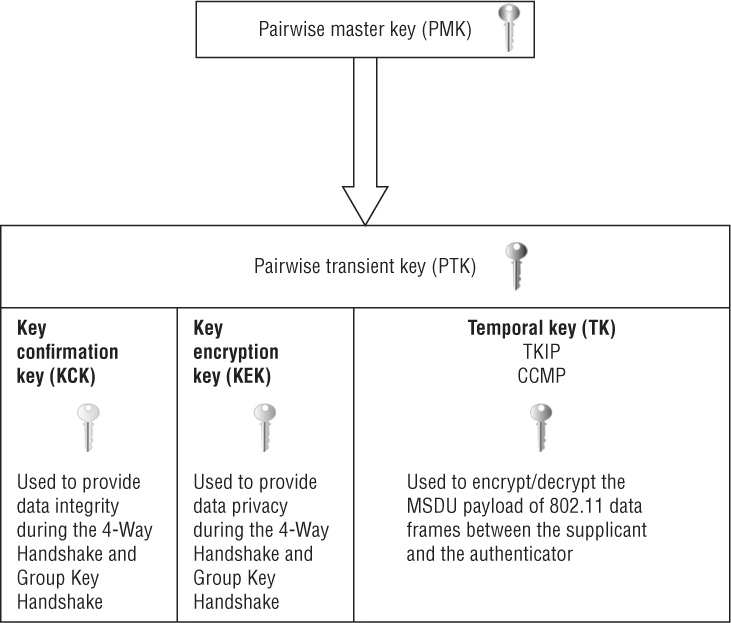
As shown in Figure 5.20, the pairwise transient key (PTK) is derived from the pairwise master key (PMK). The PTK is composed of three sections:
Key Confirmation Key (KCK) The KCK is used to provide data integrity during the 4-Way Handshake and Group Key Handshake.
Key Encryption Key (KEK) The KEK is used by the EAPOL-Key frames to provide data privacy during the 4-Way Handshake and Group Key Handshake.
Temporal Key (TK) The TK is the temporal encryption key used to encrypt and decrypt the MSDU payload of 802.11 data frames between the supplicant and the authenticator.
FIGURE 5.20 Pairwise transient key (PTK)
As shown in Figure 5.21, the group temporal key (GTK) is derived from the group master key (GMK). The GTK is a temporal key used to provide data privacy for broadcast/multicast communication. GTKs are used between a single authenticator and all the supplicants that are communicating with the authenticator.
FIGURE 5.21 Group temporal key (GTK)
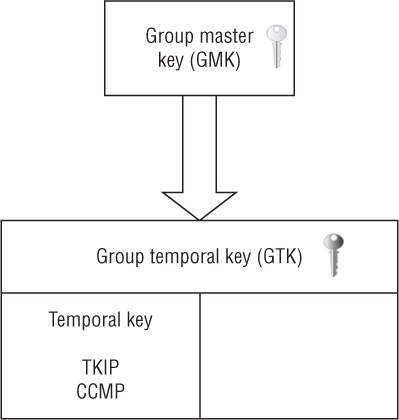
It should be understood that the PTK/GTKs used for encryption are either CCMP/AES or TKIP/ARC4 as defined by the 802.11-2012 standard. However, the 4-Way Handshake can also be used to generate keys for proprietary encryption methods.
4-Way Handshake
The 802.11-2012 standard requires that EAPOL-Key frames be used to exchange cryptographic information between radios. Most of these exchanges are between a client STA supplicant and an authenticator, which is usually an access point. EAPOL-Key frames are used during a variety of frame exchanges that are used to create dynamic encryption keys:
4-Way Handshake
Group Key Handshake
PeerKey Handshake
TDLS PeerKey Handshake
As already mentioned, the 4-Way Handshake is a final process used to generate pairwise transient keys for encryption of unicast transmissions and a group temporal key for encryption of broadcast/multicast transmissions.
The 4-Way Handshake uses four EAPOL-Key frame messages between the authenticator and the supplicant for six major purposes:
Confirm the existence of the PMK at the peer station.
Ensure that the PMK is current.
Derive a new pairwise transient key (PTK) from the PMK.
Install the PTK on the supplicant and the authenticator.
Transfer the GTK from the authenticator to the supplicant and install the GTK on the supplicant and, if necessary, the authenticator.
Confirm the selection of the cipher suites.
802.1X/EAP authentication is completed when the access point sends an EAP-Success frame and the AP can now initiate the 4-Way Handshake. Keep in mind that the authentication process has already generated the master keys (PMK and GMK), which will be used by the 4-Way Handshake to derive the temporal keys.
Before we explain the 4-Way Handshake process, it is necessary to define several key terms. The 4-Way Handshake uses pseudo-random functions. A pseudo-random function (PRF) hashes various inputs to derive a pseudo-random value. The PMK is one of the inputs combined with other inputs to create the pairwise transient key (PTK). Some of the other inputs used by the pseudo-random function are called nonces. A nonce is a random numerical value that is generated one time only. A nonce is used in cryptographic operations and is associated with a given cryptographic key. In the case of the 4-Way Handshake, a nonce is associated with the PMK. A nonce is only used once and is never used again with the PMK. Two nonces are created by the 4-Way Handshake: the authenticator nonce (ANonce) and the supplicant nonce (SNonce).
To create the pairwise transient key, the 4-Way Handshake uses a pseudo-random function that combines the pairwise master key, a numerical authenticator nonce, a supplicant nonce, the authenticator’s MAC address (AA), and the supplicant’s MAC address (SPA).
The following is a simplified depiction of the formula used by the pseudo-random function (PRF) to derive a pairwise transient key:
PTK = PRF (PMK + ANonce + SNonce + AA + SPA)
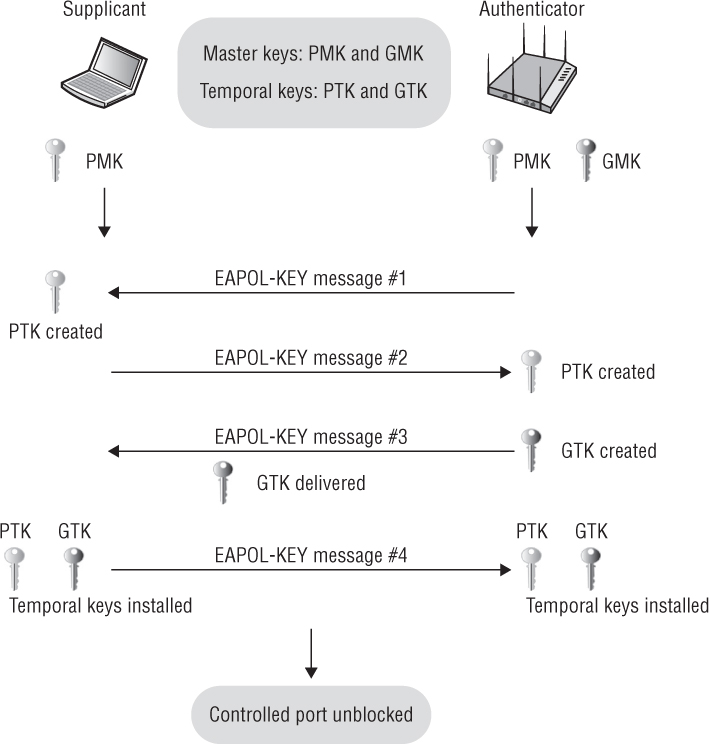
As Figure 5.22 shows, the 4-Way Handshake consists of the following steps:
4-Way Handshake Message 1 The authenticator and supplicant each randomly create their respective nonces. The authenticator sends an EAPOL-Key frame containing an ANonce to the supplicant. The supplicant now has all the necessary inputs for the pseudo-random function. The supplicant derives a PTK from the PMK, ANonce, SNonce, and MAC addresses. The supplicant is now in possession of a pairwise transient key that can be used to encrypt unicast traffic.
4-Way Handshake Message 2 The supplicant sends an EAPOL-Key frame containing an SNonce to the authenticator. The authenticator now has all the necessary inputs for the pseudo-random function. The supplicant also sends its RSN information element capabilities to the authenticator and a message integrity code (MIC). The authenticator derives a PTK from the PMK, ANonce, SNonce, and MAC addresses. The authenticator also validates the MIC. The authenticator is now in possession of a pairwise transient key that can be used to encrypt unicast traffic.
4-Way Handshake Message 3 If necessary, the authenticator derives a GTK from the GMK. The authenticator sends an EAPOL-Key frame to the supplicant containing the ANonce, the authenticator’s RSN information element capabilities, and a MIC. The EAPOL-Key frame may also contain a message to the supplicant to install the temporal keys. Finally, the GTK will be delivered inside this unicast EAPOL-Key frame to the supplicant. The confidentiality of the GTK is protected because it will be encrypted with the PTK.
4-Way Handshake Message 4 The supplicant sends the final EAPOL-Key frame to the authenticator to confirm that the temporal keys have been installed.
Controlled Port Unlocked The virtual controlled port opens on the authenticator, and now, encrypted 802.11 data frames from the supplicant can pass through the authenticator and on to their final destination. All unicast traffic will now be encrypted with the PTK, and all multicast and broadcast traffic will now be encrypted with the GTK.
FIGURE 5.22 The 4-Way Handshake
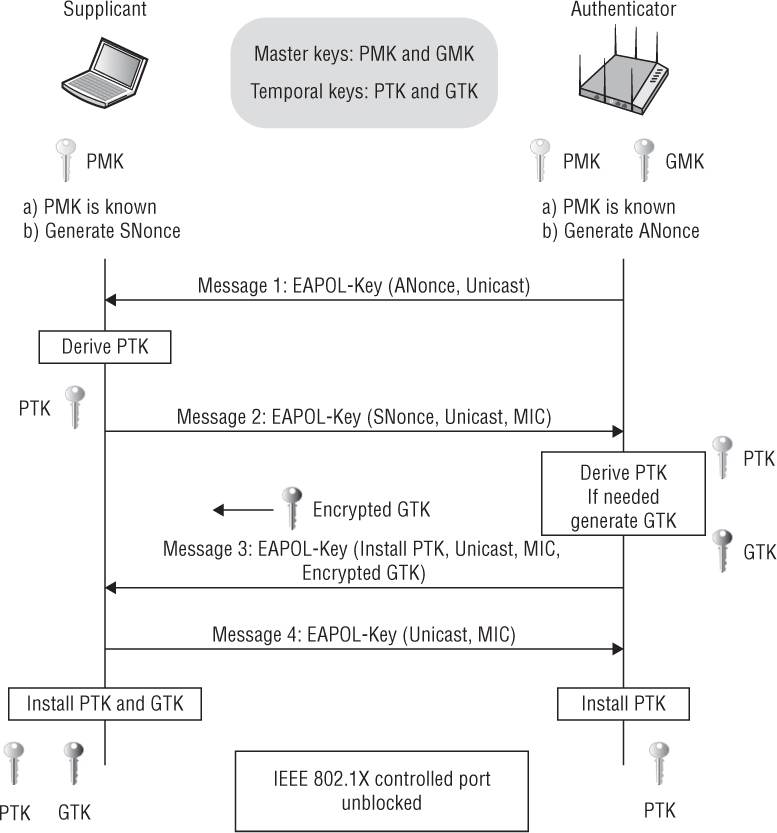
The 4-Way Handshake
In this exercise, you will use a protocol analyzer to view the 4-Way Handshake EAPOL-Key frames that are used to generate the temporal keys used for encryption.
To perform this exercise, you need to first download the 4WAY_HANDSHAKE.PCAP file from the book’s online resource area, which can be accessed at www.sybex.com/go/cwsp2e.
After the file is downloaded, you will need packet analysis software to open it. If you do not already have a packet analyzer installed on your computer, you can download Wireshark from www.wireshark.org.
Using the packet analyzer, open the 4WAY_HANDSHAKE.PCAP file. Most packet analyzers display a list of capture frames in the upper section of the screen, with each frame numbered sequentially in the first column.
Observe the EAP-Success frame at packet 66. At this point, 802.1X/EAP authentication is completed, and the AP can now initiate the 4-Way Handshake. The access point (authenticator) MAC address is 00:12:43:CB:0F:30. The client station (supplicant) MAC address is 00:40:96:A3:0C:45.
Observe the EAPOL-Key frames of the 4-Way Handshake in packets 68, 70, 72, and 74. Open the first EAPOL-Key frame in packet 68. Notice that the AP is sending the client station an ANonce.
Open the second EAPOL-Key frame in packet 70. Notice that the client station is sending the AP an SNonce, an RSN information element, and a MIC.
Open the third EAPOL-Key frame in packet 72. Notice the AP is sending the supplicant a MIC and instructions to install the temporal keys.
Open the fourth EAPOL-Key frame in packet 74. The supplicant is now sending a message to the authenticator that the temporal keys are installed.
Group Key Handshake
The 802.11-2012 standard also defines a two-frame handshake that is used to distribute a new group temporal key (GTK) to client stations that have already obtained a PTK and GTK in a previous 4-Way Handshake exchange. The Group Key Handshake is used only to issue a new group temporal key (GTK) to client stations that have previously formed security associations. Effectively, the Group Key Handshake is identical to the last two frames of the 4-Way Handshake. Once again, the purpose of the Group Key Handshake is to deliver a new GTK to all client stations that already have an original GTK generated by an earlier 4-Way Handshake.
The authenticator can update the GTK for a number of reasons. For example, the authenticator may change the GTK on disassociation or deauthentication of a client station. WLAN vendors may also offer a configuration setting to trigger the creation of a new GTK based on a timed interval.
As shown in Figure 5.23, the Group Key Handshake consists of the following steps:
Group Key Handshake Message 1 The authenticator derives a new GTK from the GMK. The new GTK is sent in a unicast EAPOL-Key frame to the supplicant. The confidentiality of the new GTK is protected because it will be encrypted with the original PTK from the initial 4-Way Handshake. The authenticator also sends a message integrity code (MIC). The supplicant validates the MIC when it receives the EAPOL-Key frame. The supplicant decrypts and installs the new GTK.
Group Key Handshake Message 2 The supplicant sends an EAPOL-Key frame to the authenticator to confirm that the GTK has been installed. The supplicant also sends a message integrity code (MIC). The authenticator validates the MIC when it receives the EAPOL-Key frame.
FIGURE 5.23 The Group Key Handshake
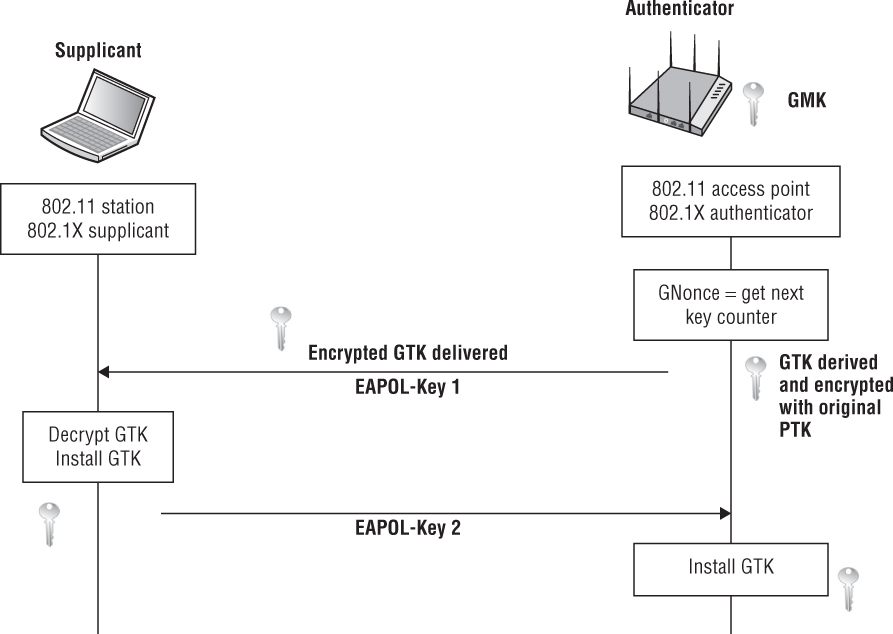
Please do not confuse Group Key Handshake with the two EAPOL-Key frame exchange that is used to distribute dynamic WEP keys. Although both handshakes use a two EAPOL-Key frame exchange, each handshake has an entirely different purpose. Also remember that dynamic WEP is proprietary and that the two EAPOL-Key frame exchange used by dynamic WEP is not an RSN security association.
PeerKey Handshake
Most WLAN communications do not involve peer-to-peer applications between clients; however, peer-to-peer connectivity within a BSS is possible. If two client stations are associated to an AP, peer-to-peer communications from one client station to another client station can occur as long as the traffic is forwarded through the AP. One client station would have to send a unicast frame to the AP, which would then be forwarded through the AP to a peer client station (STA).
Unlike a typical peer-to-peer communications within a BSS, the 802.11-2012 standard defines a method that gives client stations the option to securely communicate with each other in a BSS without sending their frames through the access point. After client STAs have already established individual security associations with an access point, a station-to-station link (STSL) can also be established. An STSL is a direct link established between two stations while associated to a common access point.
The client stations within the BSS use a PeerKey Handshake management protocol to create PeerKeys that are unique to two client STAs so that they can communicate directly and securely in a station-to-station link (STSL) within the BSS. The PeerKey Handshake is used to establish security for data frames passed directly between two STAs associated with the same AP. The AP must establish an RSNA with each STA prior to the PeerKey Handshake.
The PeerKey Handshake is actually two different handshakes:
SMK Handshake This frame exchange is used by the two peer stations to create a master key called the STSL master key (SMK). One of the client stations must initiate this exchange through the AP to create the SMK with another client station that is also associated to the AP.
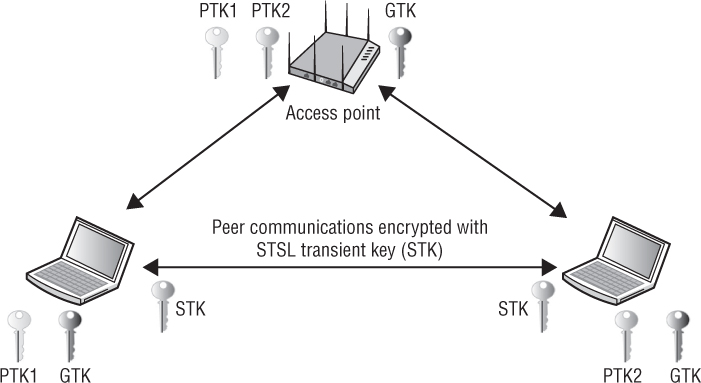
4-Way STK Handshake This frame exchange uses the SMK as seeding material to create an STSL transient key (STK). The STK is the final key that is used to encrypt the unicast communications between the two peer client stations while they are still associated to the AP.
As shown in 5.24, the peer stations will remain associated to the AP and use the STK for secure STSL communications. The stations can also still securely communicate within the AP using their original unique pairwise transient keys (PTKs).
Although originally defined by the 802.11i-2004 security amendment, widespread use of the PeerKey Handshake never happened. The 802.11z-2010 amendment defined enhanced mechanisms for tunneled direct link setup (TDLS) between two peer stations within a BSS.
FIGURE 5.24 Station-to-station link (STSL)
TDLS Peer Key Handshake
The 802.11z-2010 amendment that defined enhanced mechanisms for direct link communications between two client stations while connected to an AP is now part of the 802.11-2012 standard. 802.11z defines a tunneled direct link setup (TDLS) security protocol. The Wi-Fi Alliance also introduced Wi-Fi CERTIFIED TDLS as a certification program for devices using TDLS to connect directly to one another after they have joined a traditional Wi-Fi network (BSS). One of the intended goals of TDLS is to boost performance for applications such as multimedia streaming between WLAN clients by bypassing congested APs. For example, two TDLS-linked devices can temporarily leave the channel of the AP to which they are associated, and dynamically switch to a 40 MHz channel in the 5 GHz band for a private conversation. Even when the private direct link is switched to a different channel, the client STAs periodically switch back to the home channel to maintain connectivity with the AP, which is unaware of the TDLS setup. TDLS is currently being used for streaming high-definition video between clients and Wi-Fi-enabled televisions.
The TDLS Peer Key security protocol is executed between the two non-AP client stations that intend to establish an RSNA for direct-link communication. The TDLS Peer Key (TPK) Handshake occurs as part of the TDLS direct-link setup procedure. The TPK security association (TPKSA) is the result of the successful completion of the TDLS Peer Key Handshake protocol, which derives keys for providing confidentiality and data origin authentication.
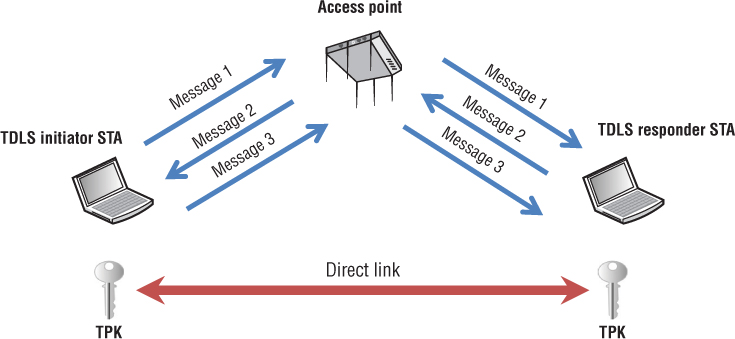
The TDLS Peer Key Handshake consists of three messages between a TDLS initiator client station and a TDLS responder client station. As shown in Figure 5.25, this three-way handshake exchange is communicated through the AP to which the clients are associated. At the end of the exchange, each client station has a copy of the unicast TDLS Peer Key (TPK) and the clients can now have an encrypted direct link for sidebar communications. Keep in mind that both clients remain associated with the original AP and the clients can still communicate with other devices using normal BSS communications.
FIGURE 5.25 TDLS Peer Key Handshake
RSNA Security Associations
Security associations can be defined as group policies and keys used to protect information. A robust security network association (RSNA) requires two 802.11 stations (STAs) to establish procedures to authenticate and associate with each other as well as create dynamic encryption keys through a 4-Way Handshake. This association between two STAs is referred to as an RSNA. The 802.11-2012 standard defines multiple RSNA security associations that are established during the many procedures already discussed in this chapter:
Pairwise Master Key Security Association (PMKSA) The conditions resulting from a successful 802.1X authentication exchange between the supplicant and authentication server or from a preshared key (PSK).
Pairwise Transient Key Security Association (PTKSA) The conditions resulting from a successful 4-Way Handshake exchange between the supplicant and authenticator.
Group Temporal Key Security Association (GTKSA) The conditions resulting from a successful group temporal key (GTK) distribution exchange via either a 4-Way Handshake or a Group Key Handshake.
STSL Master Key Security Association (SMKSA) An SMKSA is the result of a successful SMK Handshake by the initiator STA. It is derived from parameters provided by the access point and the client stations.
STSL Transient Key Security Association (STKSA) The STKSA is a result of the successful completion of the 4-Way STK Handshake. This security association is bidirectional between the initiator and the peer STAs. The STKSA is used to create session keys to protect the station-to-station link.
TDLS Peer Key Security Association (TPKSA) The conditions resulting from a successful completion of the TDLS Peer Key Handshake. Two non-AP STAs establish a secure directlink communication while remaining in a BSS. The security association is bidirectional between the TDLS initiator STA and the TDLS responder STA. The TPKSA is used to create session keys to protect this TDLS session.
Passphrase-to-PSK Mapping
As discussed earlier, an authentication and key management protocol (AKMP) can either be derived from an EAP protocol used during 802.1X or by a preshared key (PSK). When a PSK authentication solution is used, AKM operations include the following:
Discovery A client station discovers the access point’s security requirements by passively monitoring for beacon frames or through active probing. The access point’s security information can be found in the RSN information element field inside beacon and probe response frames. The client station security requirements are delivered to the AP in association and reassociation frames.
Negotiation The client STA associates with an AP and negotiates a security policy. The preshared key (PSK) becomes the pairwise master key (PMK).
Temporal Key Generation and Authorization The 4-Way Handshake exchange between the supplicant and the authenticator utilizing EAPOL-Key frames is used to generate temporary encryption keys that are used to encrypt and decrypt the MSDU payload of 802.11 data frames. Once the temporal keys are created and installed, the controlled port of the authenticator opens and the supplicant can now send traffic through the controlled port onward to network resources.
The PSK authentication used during RSNA is often known by the more common name of WPA-Personal or WPA2-Personal. PSK authentication was initially intended as a simple security solution for home users who do not have the resources to deploy full-blown 802.1X/EAP security with a RADIUS server. However, PSK authentication is commonplace in many enterprise deployments despite known security risks. WPA2-Personal and PSK authentication are discussed in greater detail in Chapter 6.
A WPA/WPA2 preshared key is a static key that is configured on the access point and all the clients. The same static PSK is used by all members of the basic service set (BSS). The RSNA PSK is 256 bits in length or 64 characters when expressed in hex. Most end users are not comfortable configuring an AP and client stations with a long, 64-character hexadecimal key. Most end users are, however, very comfortable configuring short ASCII passwords or passphrases. Therefore, a passphrase-PSK mapping formula is defined by the 802.11-2012 standard to allow end users to use a simple ASCII passphrase that is then converted to the 256-bit PSK. The PSK is generated using a password-based key generation function (PBKDF).
Here is the formula to convert a passphrase to a PSK:
PSK = PBKDF2(PassPhrase, ssid, ssidLength, 4096, 256)
The PassPhrase is a sequence of between 8 and 63 ASCII-encoded characters. The limit of 63 is mandated so as to differentiate between an ASCII passphrase and a PSK that is 64 hexadecimal characters.
Each character in the passphrase must have an encoding in the range of 32 to 126 (decimal), inclusive.
ssid is the SSID of the ESS or IBSS where this passphrase is in use, encoded as an octet string used in the beacon and probe response frames for the ESS or IBSS.
ssidLength is the number of octets of the ssid.
4096 is the number of times the passphrase is hashed.
256 is the number of bits output by the passphrase mapping.
As you can see, a simple passphrase is combined with the SSID and hashed to produce a 256-bit PSK.
NOTE
Throughout this study guide, you will be presented with various formulas. You will not need to know these formulas for the CWSP certification exam. The formulas are in this study guide to demonstrate concepts and to be used as reference material.
Roaming and Dynamic Keys
Every time a client station roams from one access point to another, the client STA will send a reassociation request frame to initiate the roaming handoff. The client station uses the RSN information element to inform the access point about the client’s security capabilities, including supported encryption cipher suites and supported authentication methods.
Every time a client roams, unique encryption keys must be generated using a 4-Way Handshake process between the access point and the client STA. As you have already learned, either an 802.1X or PSK authentication process is needed to produce the pairwise master key (PMK) that seeds the 4-Way Handshake. Therefore, every time a client roams, the client must reauthenticate.
Roaming can be especially troublesome for VoWiFi and other time-sensitive applications when using a WPA-Enterprise or WPA2-Enterprise security solution, which requires the use of a RADIUS server. Due to the multiple frame exchanges between the authentication server and the supplicant, an 802.1X/EAP authentication often takes 700 milliseconds or longer for the client to authenticate. VoWiFi requires a handoff of 150 milliseconds or less to avoid a degradation of the quality of the call or, even worse, a loss of connection. An ideal roaming handoff time for VoWiFi is 50 milliseconds. One advantage of using WPA/WPA2-Personal is that PSK authentication does not have the latency issues of 802.1X/EAP. PSK authentication only requires the 4-Way Handshake exchange, and the roaming handoff can occur in typically 40 to 60 milliseconds.
The 802.11r-2008 amendment is known as the fast basic service set transition (FT) amendment and is now part of the IEEE 802.11-2012 standard. The technology is more often referred to as fast secure roaming because it defines faster handoffs when roaming occurs between cells in a WLAN using 802.1X/EAP. You can find a detailed discussion about fast BSS transition methods in Chapter 7.
Summary
It is important to remember that authentication and key management (AKM) uses the authentication and encryption processes together to provide authorized protection for the WLAN portal as well as data privacy for the 802.11 data frames. The authentication and encryption key generation processes are linked together and are dependent on each other. Many vendors initially linked authentication and encryption together using dynamic WEP. However, dynamic WEP security was proprietary and still susceptible to WEP-cracking attacks. The 802.11-2012 standard now defines robust security network associations (RSNAs), which require two 802.11 stations (STAs) to establish procedures to authenticate and associate with each other as well as create dynamic encryption keys through the 4-Way Handshake process. RSNAs use either TKIP/ARC4 or CCMP/AES encryption protocols. Dynamic keys prevent social engineering attacks, and all client STAs have unique keys.
Exam Essentials
Explain dynamic WEP. Be able to explain processes used to generate dynamic WEP keys. Understand that dynamic WEP is not the same as RSNA dynamic key management.
Describe the differences between an RSN, TSN, and pre-RSN security network. Understand that a robust security network utilizes only TKIP/ARC4 and CCMP/AES encryption. A TSN can use TKIP/ARC4, CCMP/AES, and legacy encryption such as WEP. A pre-RSN security network only uses legacy encryption.
Explain the purpose of the RSN information element field. Know what type of security capability information is in the RSNIE. Know which 802.11 management frames are used to deliver the RSNIE and how the management frames are used.
Understand the concept of AKM. Describe the symbiotic relationship between authentication and dynamic encryption. Understand that an 802.1X/EAP or PSK process provides the seeding material to generate dynamic encryption keys.
Describe the RSNA key hierarchy. Understand the relationship between all the various keys. Know the difference between master and temporal keys. Explain the difference between pairwise and group keys. Know the three keys that comprise a PTK.
Explain all phases of the 4-Way Handshake in detail. Understand that the 4-Way Handshake is used to produce the final temporal keys used for encryption. Know the purpose of each EAPOL-Key frame. Explain all of the components needed to create a PTK.
Explain the purpose of the Group Key Handshake. Understand that the Group Key Handshake is used to create a new GTK for broadcast/multicast traffic after a previous 4-Way Handshake has already occurred.
Understand the concept of RSN security associations. Explain all the different security associations, why they are needed, and when they occur.
Describe passphrase-to-PSK mapping. Explain how a PSK is derived from a passphrase and why. Understand the relationship between PSK authentication and the 4-Way Handshake.
Review Questions
1. What must occur in order for dynamic TKIP/ARC4 or CCMP/AES encryption keys to be generated? (Choose all that apply.)
A. Shared Key authentication and 4-Way Handshake
B. 802.1X/EAP authentication and 4-Way Handshake
C. Open System authentication and 4-Way Handshake
D. PSK authentication and 4-Way Handshake
2. Which encryption types can be used to encrypt and decrypt unicast traffic with the pairwise transient key (PTK) that is generated from a 4-Way Handshake? (Choose all that apply.)
A. Temporal Key Integrity Protocol
B. 3-DES
C. Dynamic WEP
D. CCMP
E. Proprietary encryption
F. Static WEP
3. View the frame capture of the 4-Way Handshake in the graphic shown here. Which EAPOL-Key message frame is displayed?
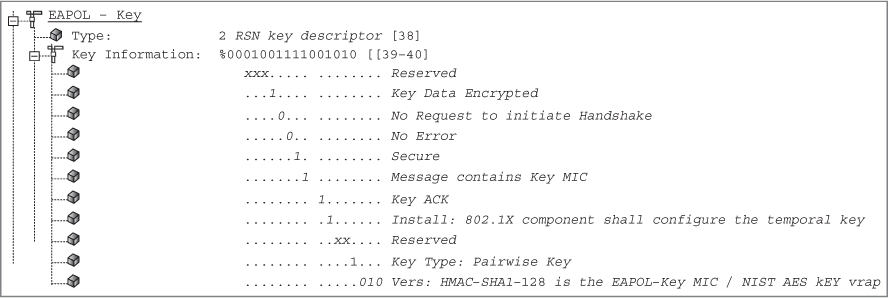
A. 4-Way Handshake message 1
B. 4-Way Handshake message 2
C. 4-Way Handshake message 3
D. 4-Way Handshake message 4
4. What are the keys that make up a pairwise transient key? (Choose all that apply.)
A. STK
B. KEK
C. SMK
D. TK
E. KCK
5. What are some of the variables that are used during the 4-Way Handshake to produce a pairwise transient key (PTK)? (Choose all that apply.)
A. Pairwise master key
B. Master session key
C. Group master key
D. Nonces
E. Authenticator MAC address
6. After viewing the frame capture in the graphic shown here, identify which type of encryption method is being used.
A. TKIP
B. CCMP
C. xSec
D. Fortress
E. WEP
F. AES
7. After viewing the frame capture in the graphic shown here, identify which type of security network is being used.
A. Robust security network
B. Rotund security network
C. Transition security network
D. WPA security network
8. In a robust security network (RSN), which 802.11 management frames are used by an access point to inform client STAs about the RSNA security capabilities of the access point and effectively the BSS? (Choose all that apply.)
A. Beacon management frame
B. Probe request frame
C. Probe response frame
D. Association request frame
E. Reassociation response frame
F. Reassociation request frame
G. Association response frame
9. The ___________ key is used to encrypt/decrypt unicast 802.11 frames, and the ___________ key is used to encrypt/decrypt broadcast and multicast 802.11 frames.
A. Group Master, Group Temporal
B. Pairwise Master, Group Temporal
C. Master Session, Pairwise Transient
D. Pairwise Transient, Group Temporal
E. Pairwise Master, Pairwise Transient
10. In a robust security network (RSN), which 802.11 management frames are used by client stations to inform an access point about the RSNA security capabilities of the client STAs? (Choose all that apply.)
A. Beacon management frame
B. Probe request frame
C. Probe response frame
D. Association request frame
E. Reassociation response frame
F. Reassociation request frame
G. Association response frame
11. Bob’s access point has been configured with the following settings:
Management VLAN 800 - Interface:
192.168.80.5/24
User VLANS:
VLAN 201
VLAN 202
VLAN 203
SSIDs:
SSID-1: (employee) security: (802.1X/EAP/CCMP) - VLAN 201 - BSSID
(00:08:12:43:0F:30)
SSID-2 (voice) security: (PSK/TKIP and WEP) - VLAN 202 - BSSID
(00:08:12:43:0F:31)
SSID-3: (guest) security: (WEP) - VLAN 203 - BSSID (00:08:12:43:0F:32)
Based on the settings on Bob’s access point, what type of WLAN security exits within the coverage area of the AP? (Choose all that apply.)
A. Closed security network
B. Transition security network
C. Pre-RSNA security network
D. Open security network
E. Robust security network
12. Which authentication methods provide the seeding material that is needed by the 4-Way Handshake to create temporal keys for encrypting 802.11 MSDU payloads? (Choose all that apply.)
A. Shared Key authentication
B. PSK
C. 802.1X/EAP
D. Captive Portal
E. WPA2-Personal
13. Client stations must authenticate and create new dynamic encryption keys under which conditions? (Choose all that apply.)
A. When probing a BSS
B. When joining a BSS
C. When joining an IBSS
D. When roaming to a new BSS
E. When leaving a BSS
14. When RSN security is in place, which security handshake is used to distribute keys to encrypt broadcast/multicast traffic even though a previous security association has already occurred?
A. PeerKey Handshake
B. Group Key Handshake
C. 4-Way Handshake
D. 2-Way Handshake
15. When two client stations are already associated to an AP, which handshake is used to create a different unicast key that the two client stations can use for a private conversation while they remain associated to the AP?
A. Mesh Group Key Handshake
B. Group Key Handshake
C. 4-Way Handshake
D. 2-Way Handshake
E. TDLS Peer Key Handshake
16. After viewing the frame capture shown here, identify the type of authentication method being used.
A. EAP-TTLS
B. Open System
C. PSK
D. EAP-TLS
E. PEAP
17. What type of RSNA security association is established as the result of a successful 802.1X authentication exchange between the supplicant and authentication server, or from a preshared key (PSK)?
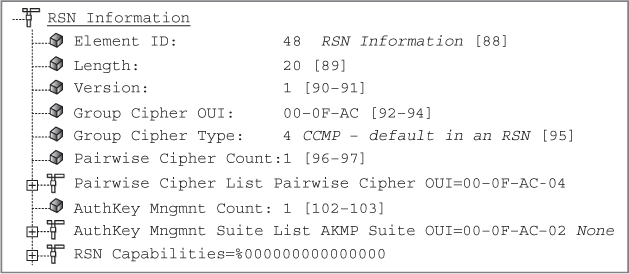
A. PMKSA
B. GMKSA
C. SMKSA
D. PTKSA
18. What are the advantages of using dynamic encryption keys instead of static keys? (Choose all that apply.)
A. Every client STA has a unique unicast key.
B. Dynamic encryption uses compression.
C. All client STAs share a broadcast/multicast key.
D. Authentication is optional with dynamic encryption.
19. What operations must occur before the virtual controlled port of the authenticator becomes unblocked? (Choose all that apply.)
A. 802.1X/EAP authentication
B. 4-Way Handshake
C. 2-Way Handshake
D. RADIUS proxy
20. What are some of the purposes of the 4-Way Handshake? (Choose all that apply.)
A. Transfer the GTK to the supplicant.
B. Derive a PTK from the PMK.
C. Transfer the GMK to the supplicant.
D. Confirm cipher suites.
