Assessment Test
1. At which layer of the OSI model does 802.11 technology operate? (Choose all that apply.)
A. Session
B. Network
C. Physical
D. Presentation
E. Transport
2. PSK authentication using ARC4 encryption is mandatory in which of the following? (Choose all that apply.)
A. WPA-Personal
B. WPA Enterprise
C. WPA-2 SOHO
D. WPA-2 Enterprise
E. WPA2-Personal
3. 802.11 pre-RSNA security defines which wireless security solution?
A. Dynamic WEP
B. 802.1X/EAP
C. 128-bit static WEP
D. Temporal Key Integrity Protocol
E. CCMP/AES
4. Which one of the following technologies can be used to provide the access security needed to expand outside of the organization’s network?
A. SAM
B. Auth
C. SAML
D. CRM
E. OAuth
5. Which of the following is a self-service process for an employee to provision a BYOD device to connect to the secure corporate network?
A. Captive Portal
B. 802.1X/EAP Configurator
C. MDM
D. Over-the-air management
E. Onboarding
6. Which of the following encryption methods uses asymmetric communications?
A. WEP
B. TKIP
C. Public key cryptography
D. CCMP
7. For an 802.1X/EAP solution to work properly with a WLAN, which two components must both support the same type of encryption?
A. Supplicant and authenticator
B. Authorizer and authenticator
C. Authenticator and authentication server
D. Supplicant and authentication server
8. Which of these types of EAP do not use tunneled authentication? (Choose all that apply.)
A. EAP-LEAP
B. EAP-PEAPv0 (EAP-MSCHAPv2)
C. EAP-PEAPv1 (EAP-GTC)
D. EAP-FAST
E. EAP-TLS (normal mode)
F. EAP-MD5
9. What type of WLAN security is depicted by this graphic?
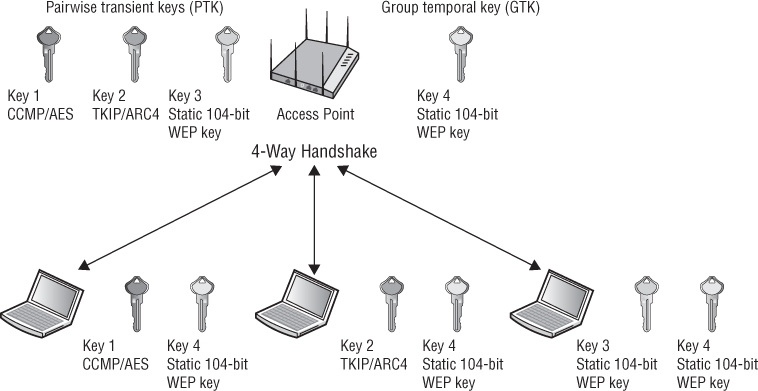
A. RSN
B. TSN
C. VPN
D. WPS
E. WMM
10. The 802.11-2012 standard defines authentication and key management (AKM) services. Which of these keys are part of the key hierarchy defined by AKM? (Choose all that apply.)
A. MSK
B. GTK
C. PMK
D. ACK
E. ATK
11. Which of these Wi-Fi Alliance security certifications are intended for use only in a home office environment? (Choose all that apply.)
A. WPA-Personal
B. WPA-Enterprise
C. WPA2-Personal
D. WPA2-Enterprise
E. WPS
12. Which of these fast secure roaming (FSR) methods requires an authenticator and supplicant to establish an entire 802.1X/EAP exchange prior to the creation of dynamic encryption keys when a supplicant is roaming?
A. PMK caching
B. Opportunistic key caching
C. Fast BSS transition
D. Preauthentication
13. What is the main WLAN security risk shown in this graphic?
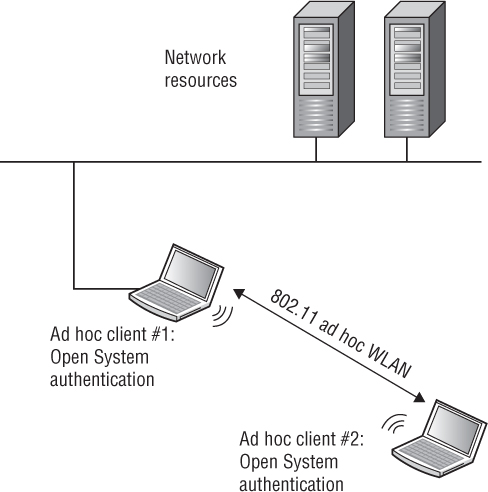
A. The ad hoc clients are not using encryption.
B. The ad hoc clients are using weak authentication.
C. The ad hoc clients are not communicating through an access point.
D. The ad hoc client #1 Ethernet card is connected to an 802.3 wired network.
14. Which components of 802.11 medium contention can be compromised by a DoS attack? (Choose all that apply.)
A. Physical carrier sense
B. Interframe spacing
C. Virtual carrier sense
D. Random backoff timer
15. After viewing this graphic, determine which type of WLAN attack tool could be used to create this Layer 1 denial of service to the WLAN.
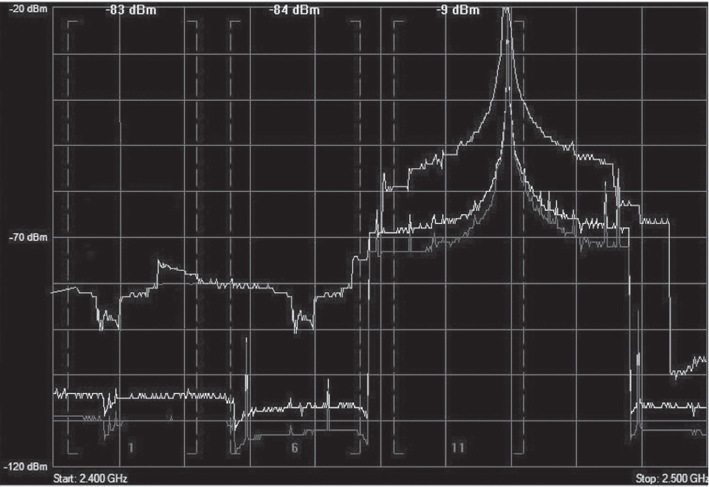
A. All-band hopping jammer
B. Wide-band jammer
C. Narrow-band jammer
D. Queensland software utility
E. Packet generator
16. Bill is designing a WLAN that will use an integrated WIPS with dedicated full-time sensors. The WLAN predictive modeling software solution that Bill is using has recommended a ratio of one dedicated sensor for every six access points. Bill needs to make sure that the entire building can be monitored at all times, and he is also concerned about the accuracy of location tracking of rogue devices. What considerations should Bill give to sensor placement in order to properly meet his objectives? (Choose all that apply.)
A. Installing the sensors in a straight line
B. Installing the sensors in a staggered arrangement
C. Installing sensors around the building perimeter
D. Increasing the transmit power
E. Installing more sensors
17. Which of these WIDS/WIPS software modules allows an organization to monitor WLAN statistics on hidden nodes, excessive Layer 2 retransmissions, excessive wired to wireless traffic, and excessive client roaming? (Choose all that apply.)
A. Spectrum analysis
B. Protocol analysis
C. Forensic analysis
D. Signature analysis
E. Performance analysis
18. When deploying 802.1X/EAP security, which IETF standard RADIUS attribute can be used to encapsulate up to 255 custom RADIUS attributes?
A. (11) Filter-id
B. (26) Vendor-Specific
C. (79) EAP-Message
D. (80) Message-Authenticator
E. (97) Frame-Encapsulator
19. Identify the protocols that are normally used to manage WLAN infrastructure devices securely. (Choose all that apply.)
A. HTTPS
B. Telnet
C. SSH2
D. TLS
E. IPsec
F. CCMP/AES
20. What type of WLAN security policy defines WLAN security auditing requirements and policy violation report procedures?
A. Functional policy
B. General policy
C. Protocol policy
D. Performance policy
Answers to Assessment Test
1. C. The IEEE 802.11-2012 standard only defines communication mechanisms at the Physical layer and MAC sublayer of the Data-Link layer of the OSI model. For more information, see Chapter 1.
2. A. The security used in SOHO environments is preshared key (PSK) authentication; however, WPA-2 defines CCMP/AES encryption. The Wi-Fi Alliance WPA-Personal and WPA2-Personal certifications both use the PSK authentication method; however, WPA-Personal specifies TKIP/ARC4 encryption and WPA2-Personal specifies CCMP/AES. WLAN vendors have many names for PSK authentication, including WPA/WPA2-Passphrase, WPA/WPA2-PSK, and WPA/WPA2-Preshared Key. For more information, see Chapter 2.
3. C. The original 802.11 standard ratified in 1997 defined the use of a 64-bit or 128-bit static encryption solution called Wired Equivalent Privacy (WEP). WEP is considered pre-RSNA security. Dynamic WEP was never defined under any wireless security standard. The use of 802.1X/EAP, TKIP/ARC4, and CCMP/AES are all defined under the current 802.11-2012 standard for robust network security (RSN). For more information, see Chapter 2.
4. C. Two technologies, Security Assertion Markup Language (SAML) and open standard for authorization (OAuth), can be used to provide the access security needed to expand outside of the organizations network. SAML provides a secure method of exchanging user security information between your organization and an external service provider, such as a third-party cloud-based customer relationship management (CRM) platform. OAuth is different from SAML because it is an authorization standard and not an authentication standard. For more information, see Chapter 10.
5. E. The main purpose of onboarding solutions is to provide an inexpensive and simple way to provision employee personal WLAN devices onto a secure corporate SSID. For more information, see Chapter 10.
6. C. WEP, TKIP, and CCMP use symmetric algorithms. WEP and TKIP use the ARC4 algorithm. CCMP uses the AES cipher. Public key cryptography is based on asymmetric communications. For more information, see Chapter 3.
7. A. An 802.1X/EAP solution requires that both the supplicant and the authentication server support the same type of EAP. The authenticator must be configured for 802.1X/EAP authentication, but it does not care which EAP type passes through. The authenticator and the supplicant must support the same type of encryption. The 802.1X/EAP process provides the seeding material for the 4-Way Handshake process that is used to create dynamic encryption keys. For more information, see Chapter 4.
8. A, E, F. Tunneled authentication is used to protect the exchange of client credentials between the supplicant and the AS within an encrypted TLS tunnel. All flavors of EAP-PEAP use tunneled authentication. EAP-TTLS and EAP-FAST also use tunneled authentication. While EAP-TLS is highly secure, it rarely uses tunneled authentication. Although rarely supported, an optional privacy mode does exist for EAP-TLS, which can be used to establish a TLS tunnel. EAP-MD5 and EAP-LEAP do not use tunneled authentication. For more information, see Chapter 4.
9. B. A transition security network (TSN) supports RSN-defined security as well as legacy security such as WEP within the same BSS. Within a TSN, some client stations will use RSNA security using TKIP/ARC4 or CCMP/AES for encrypting unicast traffic. However, some legacy stations might use static WEP keys for unicast encryption. All of the clients will use WEP encryption for the broadcast and multicast traffic. Because all the stations share a single group encryption key for broadcast and multicast traffic, the lowest common denominator must be used for the group cipher. For more information, see Chapter 5.
10. A, B, C. AKM services defines the creation of encryption keys. Some of the encryption keys are derived from the authentication process, some of the keys are master keys, and some are the final keys that are used to encrypt/decrypt 802.11 data frames. The keys include the master session key (MSK), group master key (GMK), pairwise master key (PMK), group temporal key (GTK), and pairwise transient key (PTK). For more information, see Chapter 5.
11. A, C, E. WPA/WPA2-Enterprise solutions use 802.1X/EAP methods for authentication in enterprise environments. Most SOHO wireless networks are secured with WPA/WPA2-Personal mechanisms. WPA-Personal and WPA2-Personal both use the PSK authentication methods. PSK authentication is sometimes used in the enterprise, but is not recommended due to known weaknesses. Wi-Fi Protected Setup (WPS) defines simplified and automatic WPA and WPA2 security configurations for home and small-business users. Users can easily configure a network with security protection by using a personal identification number (PIN) or a button located on the access point and the client device. WPS is intended only for SOHO environments and is not meant to be used in the enterprise. For more information, see Chapter 6.
12. D. The 802.11-2012 standard defines two fast secure roaming mechanisms called preauthentication and PMK caching. Most WLAN vendors currently use an enhanced method of FSR called opportunistic key caching. The 802.11r-2008 amendment defines more complex Fast BSS transition (FT) methods of FSR. PMK caching, opportunistic key caching (OKC), and fast BSS transition (FT) all allow for 802.1X/EAP authentication to be skipped when roaming. Preauthentication still requires another 802.1X/EAP exchange through the original AP prior to the client roaming to a new target AP. For more information, see Chapter 7.
13. D. Probably the most overlooked rogue device is the ad hoc wireless network. The technical term for an 802.11 ad hoc WLAN is an independent basic service set (IBSS). The radio cards that make up an IBBS network consist solely of client stations, and no access point is deployed. The more common name for an IBSS is an ad hoc wireless network. An Ethernet connection and a Wi-Fi card can be bridged together—an intruder might access the ad hoc wireless network and then potentially route their way to the Ethernet connection and get onto the wired network. For more information, see Chapter 12.
14. A, C. 802.11 uses a medium contention process called Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA). To ensure that only one radio card is transmitting on the half-duplex RF medium, CSMA/CA uses four checks and balances. The four checks and balances are virtual carrier sense, physical carrier sense, the random back-off timer, and interframe spacing. Virtual carrier sense uses a timer mechanism known as the network allocation vector (NAV) timer. Physical carrier sense uses a mechanism called the clear channel assessment (CCA) to determine whether the medium is busy before transmitting. Virtual carrier sense is susceptible to a DoS attack when an attacker manipulates the duration value of 802.11 frames. Physical carrier sense is susceptible to DoS when there is a continuous transmitter on the frequency channel. For more information, see Chapter 12.
15. C. A Layer 1 DoS attack can be accomplished using a wide-band jamming device or narrow-band jamming device. A wide-band jammer transmits a signal that raises the noise floor for most of the entire frequency band and therefore disrupts communications across multiple channels. The graphic shows a spectrum analyzer view of the narrow-band jammer that is disrupting service on several channels but not the entire frequency band. For much less money, an attacker could also use the Queensland Attack to disrupt an 802.11 WLAN. A major chipset manufacturer of 802.11b radio cards produced a software utility that placed the radios in a continuous transmit state for testing purposes. This utility can also be used for malicious purposes and can send out a constant RF signal much like a narrow-band signal generator. For more information, see Chapter 13.
16. B, C, E. Every WLAN vendor has their own sensor deployment recommendations and guidelines; however, a ratio of one sensor for every three to five access points is highly recommended. Full-time sensors are often placed strategically at the intersection points of three AP coverage cells. A common mistake is placing the sensors in a straight line as opposed to staggered sensor arrangement, which will ensure a wider area of monitoring. Another common sensor placement recommendation is to arrange sensors around the perimeter of the building. Perimeter placement increases the effectiveness of triangulation and also helps to detect WLAN devices that might be outside the building. Some of the better WLAN predictive modeling software solutions will also create models for recommended sensor placement. For more information, see Chapter 14.
17. B, E. Although the main purpose of an enterprise WIDS/WIPS is security monitoring, information collected by the WIPS can also be used for performance analysis. Since everything WLAN devices transmit is visible to the sensors, the Layer 2 information gathered can be used to determine the performance level of a WLAN, including capacity and latency. The Layer 2 information can also be gathered using standard protocol analysis. For more information, see Chapter 14.
18. B. RADIUS vendor-specific attributes (VSAs) are derived from the IETF attribute (26) Vendor-Specific. This attribute allows a vendor to create any additional 255 attributes however they wish. Data that is not defined in standard IETF RADIUS attributes can be encapsulated in the (26) Vendor-Specific attribute. For more information, see Chapter 9.
19. A, C. Secure Shell, or SSH, is typically used as the secure alternative to Telnet. SSH2 implements authentication and encryption using public key cryptography of all network traffic traversing between a host and a WLAN infrastructure device. HTTPS is essentially an SSL session that uses the HTTP protocol and is implemented on network devices for management via a graphical user interface (GUI). For more information, see Chapter 8.
20. B. When establishing a wireless security policy, you must first define a general policy. A general wireless security policy establishes why a wireless security policy is needed for an organization. General policy defines a statement of authority and the applicable audience. General policy also defines threat analysis and risk assessments. General policy defines internal auditing procedures as well as the need for independent outside audits. WLAN security policy should be enforced, and clear definitions are needed to properly respond to policy violations. For more information, see Chapter 15.
