Chapter 12 Wireless Security Risks
IN THIS CHAPTER, YOU WILL LEARN ABOUT THE FOLLOWING:
✓ Denial of Service (DoS) attacks
✓ Management interface exploits
✓ Guest access and WLAN hotspots
802.11 wireless networking is inherently insecure due to the use of a shared and unbounded medium—radio frequency (RF) signals. Unlike traditional bounded, or wired, networks, the medium used by wireless networks extends beyond the confines of your office or home and even beyond your campus and property as far as the signal can propagate. Essentially, your network is shared with not only the computers and other devices on your cables but also with any other 802.11 devices on the same frequency channel. 802.11 transmissions can be monitored by any third party not participating in the WLAN conversations. This lack of signal containment makes wireless networking inherently insecure. Wi-Fi technology is now an everyday part of our global society. New networks are increasingly wireless by default and wired by exception. Access points and client devices have become less expensive and are sold by popular retail outlets and even in vending machines. The increased use of 802.11 wireless technology has made it easier for workers to be more productive in the office and on the road. As the popularity of WLANs continues to grow, so does the potential for WLAN attacks and security risks. In this chapter, we will examine the risks involved with the use of 802.11 wireless networking and discuss some of the ways to mitigate these risks.
Unauthorized Rogue Access
The corporate WLAN is an authorized wireless portal to network resources. In Chapter 4, “802.1X/EAP Authentication” we discussed the proper 802.1X/EAP mechanisms that should be used to authenticate users before they are authorized through the corporate WLAN portal. However, more often than not, there is nothing to prevent a trusted individual or intruder from installing their own unauthorized wireless portal into the network backbone. A big buzz phrase in Wi-Fi security has always been the rogue access point or rogue device. A rogue access device is any WLAN radio that is connected to the wired infrastructure but is not under the management of proper network administrators. A rogue device is any unauthorized WLAN portal to network resources.
Rogue Devices
It is not uncommon for a company to have a wireless network installed within their facilities and not even know about its existence. The individuals usually responsible for installing rogue access points (APs) are not hackers; they are employees not realizing the consequences of their actions. Wi-Fi networking has become ingrained in our society, and the average employee has become accustomed to the convenience and mobility that Wi-Fi offers. As a result, employees often install their own wireless devices in the workplace because the company for which they work has yet to deploy an enterprise wireless network or they are not aware of the corporate policy forbidding installation of WLAN devices. The problem is that, while these self-installed access points might provide the wireless access that the employees desire, they are rarely secured. Any consumer-grade Wi-Fi router or access point can be plugged into a live data port. The rogue access point is a potential open and unsecured gateway straight into the wired infrastructure that the company wants to protect (see Figure 12.1).
FIGURE 12.1 Rogue access point
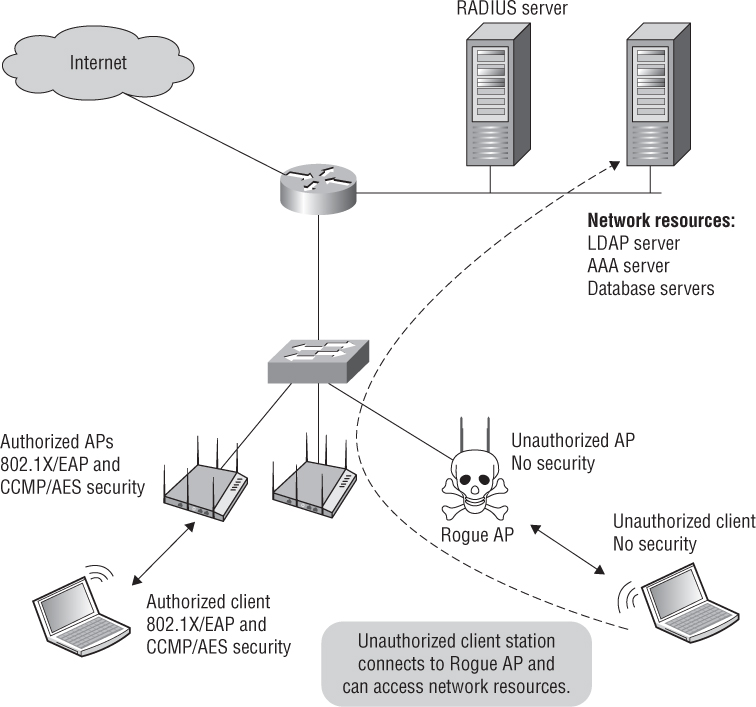
Although it is true that in some industries corporate espionage exists and in some government deployments dedicated attackers can be found, the vast majority of rogue devices are not installed for these malicious purposes. The majority of rogue devices are placed on networks by approved network users, employees, contractors, and visitors. Employees, contractors, and visitors are granted physical access to the buildings on a daily basis, something a dedicated attacker is not given. These “trusted” individuals rarely place rogue devices for malicious purposes. They place them to extend their wireless coverage or provide wireless coverage in areas that they feel it should exist without organizational permission. Some of the “trusted” individuals do not know that they are doing anything wrong due to the lack of an enforced security policy or training covering the use of wireless devices. They are simply uninformed about the risks of such device use.
Other members of this “trusted” group know that what they are doing is against policy but believe their need for wireless networking is more important than written policy. This subgroup will often take measures to hide the rogue access points or laptops under their desks, in boxes, or behind furniture. Rogue devices are even found in server rooms, having been placed there by the IT staff against policy. Although only a single open portal is needed to expose network resources, many large companies have discovered literally dozens of rogue access points installed by employees and/or contractors. Most of the rogue devices that are installed by employees are actually not access points but are instead consumergrade Wi-Fi routers that can be purchased inexpensively and brought into the workplace.
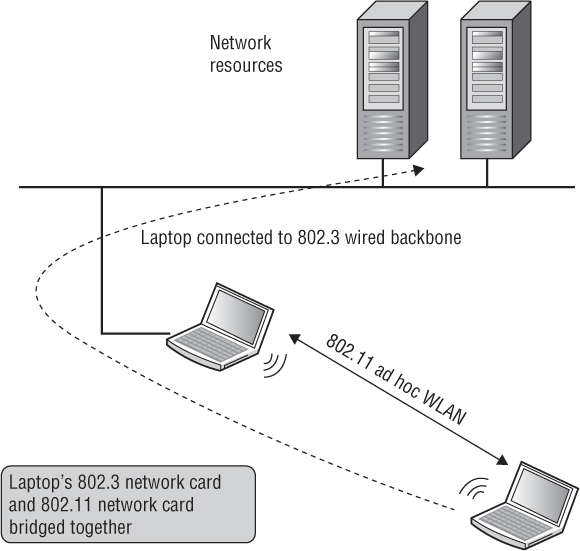
Probably the most overlooked rogue device is the ad hoc wireless network. The technical term for an 802.11 ad hoc WLAN is an independent basic service set (IBSS). The 802.11 radios communicating within an IBSS network consist solely of client stations, and no access point is deployed. An IBSS network that consists of just two stations (STAs) is analogous to a wired crossover cable. An IBSS, however, can have multiple client stations in one physical area communicating in an ad hoc fashion. Unfortunately, ad hoc networks also have the potential of providing rogue access into the corporate network. Very often an employee will have a laptop or desktop plugged into the wired network via an Ethernet network adapter. On that same computer, the employee has a Wi-Fi radio and has set up an ad hoc Wi-Fi connection with another employee. As shown in Figure 12.2, the Ethernet connection and the Wi-Fi can be bridged together—an intruder might access the ad hoc wireless network and then potentially route their way to the Ethernet connection and get onto the wired network.
Another common rogue type is the wireless printer. Many printers now have 802.11 radios with a default configuration of ad hoc mode. Attackers can connect to these printers using the printer manufacturer’s administrative tools, downloadable from the company’s website. Then, using these tools, attackers can upload their own firmware to your printer, thus allowing them to bridge the wired and wireless connections of your printer to gain access to your wired network, without the use of an access point. Many 802.11 wireless camera security systems can be breached in a similar manner.
FIGURE 12.2 Bridged ad hoc WLAN
As previously mentioned, the individuals most often responsible for installing rogue access points are not hackers but instead are employees. The employees leave an open wireless portal for anyone to pass through. Because rogue devices are unauthorized WLAN portals, all of your network resources are potentially exposed. If network resources are exposed, the following risks exist:
Data Theft Corporate data on database servers can be compromised. Credit card information, corporate trade secrets, personnel information, and medical data can all be stolen if exposed via a rogue device. Any data stored on network servers or desktop workstations is entirely at risk. Data theft is usually the most common risk associated with rogue access.
Data Destruction Destruction of data can also occur. Databases can be erased and drives can be reformatted.
Loss of Services Network services can also be disabled. Even if no data was stolen or destroyed, imagine the loss of productivity and the potential losses if email services were disabled by an attacker through a rogue AP.
Malicious Data Insertion An attacker can use the unauthorized portal to upload viruses and pornography. Remote control applications and keystroke loggers can also be uploaded to network resources and used to gather information at a later date. Attackers have been known to upload illegally copied software and set up illegal FTP servers to distribute the illegal software.
Third-Party Attacks Once an attacker has accomplished rogue access, your wired network can be used as a launching pad for third-party attacks against other networks across the Internet. Distributed denial-of-service (DDoS) attacks against other corporate networks can be launched from your network infrastructure. Spammers long ago figured out that they can use a rogue AP as the originating source to send spam.
Rogue Prevention
In Chapter 15, “Wireless Security Policies,” we will discuss corporate policies that ban employees from installing unauthorized APs. In addition to unauthorized APs, many government agencies and corporations ban the use of ad hoc networks. The ability to configure an ad hoc network can be disabled on most enterprise laptops. Endpoint WLAN security software can also be installed on WLAN client devices to prevent bridging between 802.11 client radios and 802.3 Ethernet radios.
Policy is a great start. However, beyond physical security or wired port control, there is nothing to prevent an intruder from connecting their own rogue AP via an Ethernet cable into any live data port provided in a wall plate. The best way of preventing rogue access is wired port control. The main focus of Chapter 4 was how 802.1X/EAP security is used for authentication and authorization via the WLAN. It should be noted that 802.1X/EAP can also be used to authorize access through wired ports on an access layer switch. EAP-PEAP and EAP-TLS can be used for wired 802.1X/EAP authentication to control wired side access. When 802.1X/EAP is used for port control on an access layer switch, desktop clients function as the supplicant requesting access. Some WLAN vendor APs can also function as a supplicant and cannot forward user traffic unless the approved AP is authenticated. As depicted in Figure 12.3, unless proper credentials are presented at Layer 2, upper-layer communications are not possible through the wired port. A rogue device cannot act as a wireless portal to network resources if the rogue device is plugged into a managed port that is blocking upper-layer traffic. Therefore, a wired 802.1X/EAP solution is an excellent method for preventing rogue access.
It should be noted that many businesses do not use a wired 802.1X/EAP solution for wired port control. Therefore a WLAN monitoring solution known as a wireless intrusion detection system (WIDS) is always needed to detect potential rogue devices. Most WIDS vendors prefer to call their products wireless intrusion prevention systems (WIPSs). The reason that they refer to their products as prevention systems is that they are all now capable of mitigating attacks from rogue access points and rogue clients.
NOTE
In Chapter 14, “Wireless Security Monitoring,” you will be introduced to the concept of classification, which is used by wireless intrusion detection systems (WIDSs) to differentiate between authorized devices and rogue devices. A more detailed discussion of methods of rogue detection, classification, and mitigation is also found in that chapter.
FIGURE 12.3 Wired 802.1X/EAP prevents rogue access.

WIPS solutions use several methods to effectively terminate, suppress, and contain communications from rogue devices. The most common method of rogue containment uses a known Layer 2 DoS attack against the rogue device as a countermeasure. Rogue APs and ad hoc clients can be effectively contained until they are located and removed. Another method of rogue mitigation uses the Simple Network Management Protocol (SNMP). Most WIPSs can determine that the rogue AP is connected to the wired infrastructure and may be able to use SNMP to disable the managed switch port that is connected to the rogue AP. If the switch port is closed, the attacker cannot attack network resources that are behind the rogue AP. This method of rogue AP mitigation is known as port suppression.
Eavesdropping
Just as human conversations can be overheard by any third party within hearing range of the speakers’ voices, WLAN communications between two 802.11 radios can be overheard by any third-party 802.11 station on the same frequency channel. Because the RF medium is half-duplex, and therefore a shared medium, only one 802.11 station can transmit at any given time. However, any 802.11 radio within listening range can monitor any active 802.11 transmissions. WLAN communications can be monitored via two eavesdropping methods: casual eavesdropping and malicious eavesdropping.
Casual Eavesdropping
Casual eavesdropping is sometimes referred to as WLAN discovery. Casual eavesdropping is accomplished by simply exploiting the 802.11 frame exchange methods that are clearly defined in the 802.11-2012 standard. As we discussed in Chapter 2, “Legacy 802.11 Security,” in order for an 802.11 client station to be able to connect to an access point, it must first discover the access point. A station discovers an access point by either listening for an AP (passive scanning) or searching for an AP (active scanning). In passive scanning, the client station listens for 802.11 beacon management frames that are continuously sent by the access points.
A casual eavesdropper can simply use any 802.11 client radio to listen for 802.11 beacon management frames and to discover Layer 2 information about the WLAN. Some of the information found in beacon frames includes the service set identifier (SSID), MAC addressing, supported data rates, and other basic service set (BSS) capabilities. All of this Layer 2 information is in cleartext and can be seen by any 802.11 radio.
In addition to scanning passively for APs, client stations can actively scan for them. In active scanning, the client station transmits management frames known as probe requests. The access point then answers back with a probe response frame that basically contains all of the same Layer 2 information that can be found in a beacon frame. A probe request without the SSID information is known as a null probe request. If a directed probe request is sent, all APs that support that specific SSID and hear the request should reply by sending a probe response. If a null probe request is heard, all APs, regardless of their SSID, should reply with a probe response.
Casual eavesdroppers can discover 802.11 networks using software tools that send null probe requests. Casual eavesdropping is typically considered harmless and is also often referred to as wardriving. Wardriving is strictly the act of looking for wireless networks, usually while in a moving vehicle. The term wardriving was derived from wardialing from the 1983 film WarGames. Wardialing was an old technique employed by hackers using computer modems to scan thousands of telephone numbers automatically to search for other computers with which they could connect.
Wardiving is now considered an outdated term and concept. In the very early days of Wi-Fi, wardriving was a hobby and sport for techno-geeks and hackers looking to find WLANs. Wardriving competitions were often held at hacker conventions to see who could find the most WLANs. While the sport of wardriving has faded into the past, millions of individuals now use WLAN discovery tools to still find available Wi-Fi networks. A more current term would be WLAN discovery. In the early days of Wi-Fi, the original WLAN discovery software tool was a freeware program called NetStumbler. Although still available as a free download, NetStumbler has not been updated in many years. However, many newer WLAN discovery tools exist that operate on a variety of operating systems. Figure 12.4 depicts a very popular WLAN discovery tool, inSSIDer, which is available from www.metageek.net.
FIGURE 12.4 inSSIDer WLAN discovery tool

The original intent of wardriving was to find an open WLAN to gain free wireless access to the Internet. WLAN discovery tools send out null probe requests across all license-free 802.11 channels with the hope of receiving probe response frames containing wireless network information, such as SSID, channel, encryption, and so on. By design, the very nature of 802.11 passive and active scanning is to provide the identifying network information that is accessible to anyone with an 802.11 radio. Because this is an inherent and necessary function of 802.11, wardriving is not a crime. The legality of using someone else’s wireless network without permission is often unclear, but be warned that people have been arrested and prosecuted as a result of these actions. An alarming decision about the use of networks owned by others was reached in March 2011. The Hague Court ruled that they were no longer going to prosecute as a criminal offense the unauthorized use of networks belonging to others if the person using the network without permission only used it to access the Internet, even if the access was gained by extraordinary means. The ruling does leave the opportunity for civil action. Every nation has its own laws covering such actions.
NOTE
We do not encourage or support the efforts of using wireless networks that you are not authorized to use. We recommend that you connect only to 802.11 wireless networks that you are authorized to access.
Malicious Eavesdropping
Malicious eavesdropping is the unauthorized use of protocol analyzers to capture wireless communications and is typically considered illegal. Most countries have some type of wiretapping law that makes it a crime to listen in on someone else’s phone conversation. Additionally, most countries have laws making it illegal to listen in on any type of electromagnetic communications, including 802.11 wireless transmissions. Protocol analysis and packet analysis are used to diagnose problems in network communications, identify traffic patterns, and find bottlenecks. Many commercial and freeware 802.11 protocol analyzers exist that allow wireless network administrators to capture 802.11 traffic, for the purpose of analyzing and troubleshooting their own wireless networks. A protocol analyzer is a passive device that operates in an RF monitoring mode to capture any 802.11 frame transmissions within their range. Commercial and freeware WLAN protocol analyzers are widely available. In earlier chapter exercises, you used a popular freeware protocol analyzer, Wireshark, to view 802.11 frame captures.
A WLAN protocol analyzer is meant to be used as a diagnostic tool. However, an attacker can use a WLAN protocol analyzer as a malicious listening device for unauthorized monitoring of 802.11 frame exchanges. Encryption is the best protection against unauthorized monitoring of the WLAN. Although all Layer 2 information is always available, WPA2 encryption provides data privacy for all the Layer 3–7 information.
Eavesdropping Risks
Because malicious eavesdropping is a passive attack, it should be understood that a WIDS/WIPS solution will not be able to detect a protocol analyzer because it is not a transmitting device. The WLAN protocol analyzer is only a listening device and will go undetected. Because protocol analyzers capture 802.11 frames passively, a wireless intrusion detection system (WIDS) cannot detect malicious eavesdropping, and the attacker cannot be located.
802.11 frames can be passively monitored and data can be captured from great distances well beyond the limits of corporate buildings and property lines. An attacker does not need physical access to buildings or property to perform malicious eavesdropping. WLANs cannot be hidden from the outside world when the RF signal propagates beyond property lines. Even if a strong RF signal does not propagate from beyond your own walls, an eavesdropper could use a high gain antenna to amplify a weak signal and still be able to monitor 802.11 frame transmissions passively from locations beyond your physical control and well out of sight. 802.11 frames can be passively captured with a protocol analyzer from a distance of many miles if the attacker has a clear RF line of sight, and the attacker will remain undetected.
Many people believe that if their data is encrypted, they have nothing else that an attacker may wish to collect. That belief brings with it a false sense of security. All Layer 2 information is still seen in cleartext, and this information can be gathered passively using a WLAN protocol analyzer. MAC addresses and Layer 2 discovery protocols can be seen in the clear.
As discussed in Chapter 2, a legacy security measure is MAC filtering. MAC filtering is the blocking of all MAC addresses from connecting unless they are specifically allowed or, alternately, allowing all MAC addresses unless they are specifically denied access. As stated earlier, the MAC addresses of WLAN devices are visible each time a device transmits any type of frame. Since the MAC addresses can be seen by any device on the same channel, an attacker can document their use. Anyone with a WLAN protocol analyzer can capture 802.11 frame exchanges between an AP and a client and see the MAC addressing that is used for the Layer 2 communications. Simply put, MAC filters do not offer any real measure of security for wireless transmissions.
Wired leakage is also a security risk and a type of information that an attacker can use to gain access to your network or data. Wired leakage often occurs when wired stations, servers, or infrastructure devices use a broadcast protocol to communicate or to find other devices with which to replicate. Access points may forward broadcast and multicast traffic from the wired infrastructure. Layer 2 discovery protocols, such as the Link Layer Discovery Protocol (LLDP) or the Cisco Discovery Protocol (CDP), will reveal information about the wired network as well as what can be seen wirelessly. Again, passively using protocol and packet analysis will not deter a potential attacker from gaining valuable information about your infrastructure.
If encryption is not being used, the Layer 3–7 payload of any 802.11 data frame will also be exposed. Any cleartext communications such as email and Telnet passwords can be captured if no encryption is provided. Furthermore, any unencrypted 802.11 frame transmissions can be reassembled at the upper layers of the OSI model. For example, email messages can be reassembled and therefore read by an eavesdropper. Web pages and instant messages can also be reassembled. VoIP packets can be reassembled and saved as a WAV sound file. Malicious eavesdropping of this nature is highly illegal. Because of the passive and undetectable nature of this attack, encryption must always be implemented to provide data privacy.
Eavesdropping Prevention
How can you stop attackers and others from gaining access to your exposed information? The easiest and most important method of protection against malicious eavesdropping attacks is to use encryption. Encryption provides the data privacy necessary to protect the MAC Service Data Unit (MSDU) upper layer payload of 802.11 data frames. A strong, dynamic encryption solution—such as CCMP/AES—is a mandatory requirement to protect the Layer 3–7 payload.
To prevent anyone other than intended recipients from hearing your transmissions, you can use RF shielding to stop transmissions from exiting or entering your building. Mylar films can be placed on all of your windows, stopping signals from escaping through them. Special paint or wallpapers can be used to do the same for your walls, essentially making your building a Faraday cage. A Faraday cage, also known as a Faraday shield, is an enclosure made of a wired mesh or other conductive material to contain electric fields such as RF signals. Faraday shields can be built into the walls of buildings, but the construction costs are very high. Usually only well-funded and extremely security-conscious organizations, such as government offices and military institutions, go through the time and expense and take these measures to contain RF transmissions from exposure to the outside world.
The bottom line is that because 802.11 technology operates at Layers 1 and 2 of the OSI model, there is virtually no way to protect those two layers from eavesdropping. To prevent some Layer 2 wired leakage, we highly recommended that you disable Layer 2 discovery protocols such as CDP.
However, the number one priority should always be to protect the MAC Service Data Unit (MSDU) upper layer payload of 802.11 data frames. Strong, dynamic encryption solutions, such as CCMP/AES, should always be considered mandatory requirements to protect the Layer 3–7 payload and provide data privacy.
Authentication Attacks
As you learned earlier, the usual purpose of an 802.11 wireless network is to act as a portal into an 802.3 wired network. It is therefore necessary to protect that portal with very strong authentication methods so that only legitimate users with the proper credentials will be authorized to access network resources.
Authentication is the method of verifying the presented identity and credentials. Once the method of authentication has been determined by an attacker, they can begin to try to break the authentication process. Some forms of authentication are stronger than others. There are some forms of authentication that are very easy to break and should not be used in secure environments. There are others that are very complex, which are better suited to more secure environments. The type of authentication used is often dictated by things other than the security requirements of the transmissions and environments, such as ease of use, cost, device types, firmware used, regulations policy, and legacy deployments.
In Chapter 2, you learned about Open System authentication, which essentially validates all clients. As you have also already learned, stronger authorization to access network resources can be achieved by either an 802.1X/EAP authentication solution or the use of PSK authentication. The 802.11-2012 standard does not define which type of EAP authentication method to use, and all flavors of EAP are not equal. Some types of EAP authentication methods are more secure than others. As a matter of fact, Cisco’s Lightweight Extensible Authentication Protocol (LEAP), once one of the most commonly deployed 802.1X/EAP solutions, is susceptible to an offline dictionary attack. The hashed password response during the LEAP authentication process is crackable. An attacker merely has to capture a frame exchange when a LEAP user authenticates and then run the capture file through an offline dictionary attack tool, as shown in Figure 12.5. The password can be derived in a matter of seconds. The username is also seen in cleartext during the LEAP authentication process. After the attacker gets the username and password, they are free to impersonate the user by authenticating onto the WLAN and then accessing any network resources that are available to that user. It should be noted that weaker VPN solutions such as PPTP using MS-CHAPv2 authentication are also susceptible to offline dictionary attacks. Stronger EAP authentication protocols that use “tunneled authentication” are not susceptible to offline dictionary attacks.
FIGURE 12.5 Offline dictionary attack
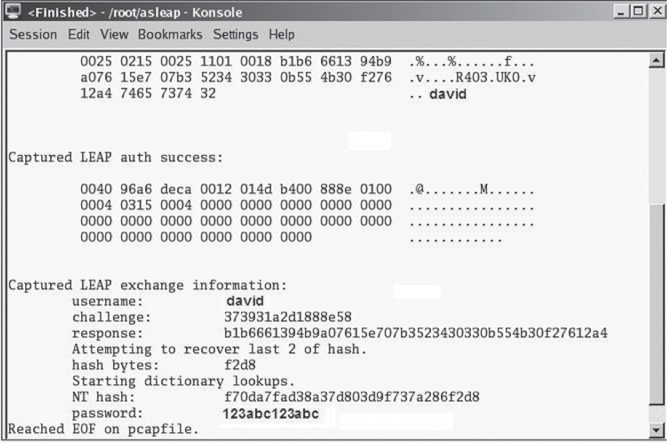
The biggest risk with any authentication attack is that all network resources become vulnerable if the authentication credentials are compromised. The risks of authentication attacks are similar to rogue access points. If an authorized WLAN portal can be compromised and the authentication credentials can be obtained, the following risks also apply:
Data theft
Data destruction
Loss of services
Malicious data
Third-party attacks
Due to the existence of these severe risks, it is necessary to secure the corporate WLAN infrastructure properly with an 802.1X/EAP solution that uses a RADIUS server and the tunneled authentication EAP protocols discussed in Chapter 4. Multifactor authentication, also known as two-factor authentication, also increases the difficulty of cracking security immensely by adding another set of required credentials. WPA-Enterprise and WPA2-Enterprise certified solutions are almost always a necessity for the strong authentication security that is required in the workplace.
Because most home users do not have a RADIUS server in their house, weaker WPA/WPA2-Personal authentication methods are normally used. PSK authentication using a static passphrase was never intended to be used in the enterprise.
WPA/WPA2-Personal, using preshared keys, is a weak authentication method that is vulnerable to an offline brute-force dictionary attack. Shared keys or passphrases are also easily obtained through social engineering techniques. Social engineering is the act of manipulating people into performing actions or divulging confidential information. Hacking utilities are available that can derive the WPA/WPA2 passphrase by using an offline brute-force dictionary attack. An attacker who obtains the passphrase can associate with the WPA/WPA2 access point and access network resources. The biggest risk with any authentication attack is that all network resources could become vulnerable if the authentication credentials are compromised.
Even worse is that after obtaining the passphrase, the hacker can begin to decrypt the dynamically generated TKIP/RC4 or CCMP/AES encryption key. In Chapter 6, “PSK Authentication,” you learned that the passphrase is used to derive the pairwise master key (PMK), which is used with the 4-Way Handshake to create the final dynamic encryption keys. If a hacker has the passphrase and captures the 4-Way Handshake, they can re-create the dynamic encryption keys and decrypt traffic. WPA/WPA2-Personal is not considered a strong security solution for the enterprise because if the passphrase is compromised, the attacker can not only access network resources, they can also decrypt traffic. Because of these risks, a static PSK authentication solution should never be used in the enterprise.
CloudCracker is an online password cracking tool for deriving the keys used in PSK networks. CloudCracker can also be used to crack different password hashes. An administrator can simply upload the corresponding 4-Way Handshake file, enter the SSID, and start the tool. CloudCracker uses an extremely large dictionary of nearly 300 million words in cracking the passphrases. CloudCracker can be found at www.cloudcracker.com. A policy mandating very strong passphrases of 20 characters or more should always be in place whenever a WPA/WPA2-Personal solution is deployed. Furthermore, because passphrases are static, they are susceptible to social engineering attacks. To prevent social engineering attacks, policy must dictate that only the administrator have knowledge of any static passphrases and that the passphrases are never shared with end users.
Denial-of-Service Attacks
Denial-of-service (DoS) attacks are not by themselves an attempt to gain access to your information or data. A DoS attack against a WLAN is an attack that effectively disables the WLAN. With the proper tools, any individual with ill intent can temporarily disable a Wi-Fi network by preventing legitimate users from accessing network resources. For mission-critical systems, this is a serious security concern. If the WLAN goes down, any application or network resource being accessed through the WLAN is no longer available. The wireless VoIP phone conversation comes to an abrupt end, communications with your database server are no longer possible, and wireless access to an Internet gateway has been closed. DoS attacks can be either malicious attempts to disrupt your WLAN or of an accidental nature. DoS attacks can also be used to jump-start other attacks such as wireless hijacking and Wi-Fi phishing.
The good news is that monitoring systems exist that can detect and identify DoS attacks immediately. The bad news is that usually nothing can be done to prevent DoS attacks other than locating and removing the source of the attack. DoS attacks can be targeted against the entire WLAN or can be targeted against individual access points or individual WLAN clients.
Layer 1 DoS Attacks
A DoS attack to a WLAN is most easily accomplished at Layer 1 in the RF environment. Layer 1 DoS attacks are a result of radio frequency interference. What can cause Layer 1 DoS? Layer 1 DoS can result from either intentional interference or unintentional interference.
Denial of service at Layer 1 usually occurs as an unintentional result of transmissions from non-802.11 devices. All sorts of devices transmit in the very crowded 2.4 GHz ISM band. RF video cameras, baby monitors, cordless phones, and microwave ovens are all potential sources of interference. The whole point of a spectrum analysis site survey is to identify and eliminate these sources of interference. But what if an employee forgets about corporate policy and employs a leaky microwave oven or a 2.4 GHz cordless phone after the original site survey was performed? Microwave ovens typically operate at 800 to 1,000 watts. Although microwave ovens are shielded, they can become leaky over time. A received signal of –60 dBm is about 1 millionth of 1 milliwatt and is considered a very strong signal for normal 802.11 communications. If a 1,000 watt microwave oven is even 0.000000001 percent leaky, the oven will interfere with the 802.11 radio.
Unintentional interference may cause continuous DoS; however, the disruption of service is often sporadic. This disruption of service will upset the performance of Wi-Fi networks used for data applications and can completely disrupt VoWiFi communications within a WLAN. At the very least, unintentional interference will result in retransmissions that negatively affect WLAN performance. The majority of unintentional interfering devices transmit in the 2.4 GHz ISM frequency band, and 2.4 GHz cordless phones, Bluetooth devices, medical equipment, and many other devices can cause unintentional interference in the 2.4 GHz ISM band. The 5 GHz UNII bands are less susceptible to unintentional interference. 5 GHz cordless phones often cause interference with the five channels of the 5 GHz UNII-3 band.
Now let’s examine deliberate attempts to disrupt wireless networking at Layer 1. If the RF medium can be accidentally interfered with, it can also be purposely jammed at Layer 1. Intentional interference can be accomplished using a wide-band jamming device or a narrow-band jamming device. A wide-band jammer transmits a signal that raises the noise floor for most of the entire frequency band and therefore disrupts communications across multiple channels. As shown in Figure 12.6, there are companies that sell wide-band jammers as security tools for enforcing no Wi-Fi zones. Most of these jamming devices transmit in the 2.4 GHz frequency range, but 5 GHz jammers exist as well. The use of such devices is usually illegal in most countries.

Narrow-band or single-channel jamming can also be done with commercially available devices. Figure 12.7 shows a signal generator that is normally used for legitimate testing purposes, such as to provide a power source to measure coax cable loss with a wattmeter. However, what is to prevent a villainous individual from transmitting a 1 watt (+30 dBm) signal via an ordinary antenna? The signal generator would then be transformed into a jamming device that will overtake most 802.11 radios that transmit at a maximum of 100 mw (+20 dBm). Higher-gain antennas can be combined with the signal generator to achieve more radiated power and extend the range of the DoS attack. Unidirectional antennas can be used to focus a Layer 1 DoS jamming attack.
FIGURE 12.7 RF signal generator and wattmeter

For much less money, an attacker could use the Queensland Attack to disrupt an 802.11 WLAN. What if an 802.11 radio could be placed in a “continuous transmit” state? In this scenario, the radio would not actually be sending data or modulating data, but would be sending out a constant RF signal much like a narrow-band signal generator. Other 802.11 radios never get to access the medium because whenever they perform a clear channel assessment, the medium is occupied by the continuous transmitter. Researchers at Queensland University in Australia discovered that this attack is indeed feasible. As shown in Figure 12.8, a major chipset manufacturer of 802.11b radios produced a software utility that placed the radios in a continuous transmit state for testing purposes. This utility can also be used for malicious purposes and is often referred to as the Queensland Attack. An 802.11b radio operating in a continuous transmit state at 30 mW may not be as large a threat as a 1 watt jammer; however, any 2.4 GHz 802.11 radios within range of the malicious radio will be affected.
FIGURE 12.8 Testing utility used for Queensland Attack

Why do jamming attacks, both accidental and intentional, cause a denial of service? Because of the half-duplex nature of the RF medium, it is necessary to ensure that at any given time only one 802.11 radio has control of the medium. Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) is a process used to ensure that only one 802.11 radio is transmitting at a time on the medium. One major component of the CSMA/CA method of medium contention is physical carrier sense.
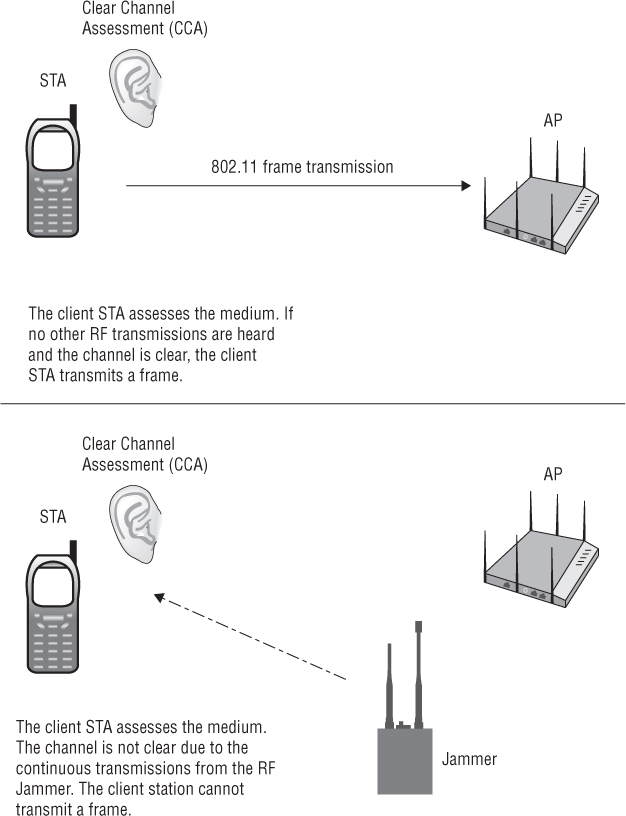
Physical carrier-sensing is performed constantly by all stations that are not transmitting or receiving. When a station performs a physical carrier sense, it is actually listening to the channel to see whether any other transmitters are taking up the channel. Physical carrier sense has two purposes. The first purpose is to determine whether a frame transmission is inbound for a station to receive. If the medium is busy, the radio will attempt to synchronize with the transmission. The second purpose is to determine whether the medium is busy before transmitting. This is known as the clear channel assessment (CCA). As shown in Figure 12.9, the CCA involves listening for 802.11 RF transmissions at the Physical layer. The medium must be clear before a station can transmit. However, if the medium is not clear (based on sensing RF transmissions that exceed predefined energy thresholds), the 802.11 radio will defer for a defined amount of time and then perform the CCA once again to listen for a clear medium before transmitting. However, if there is a “continuous” RF transmission that is constantly heard during the CCA intervals, 802.11 transmissions will completely cease until the signal is no longer present. If 802.11 transmissions cease due to an interfering RF signal, the result is a denial of service to the WLAN.
FIGURE 12.9 Clear channel assessment (CCA)
Whether intentional or unintentional, a Layer 1 attack may also result in a partial DoS attack. Every time an 802.11 radio transmits a unicast frame, if the frame is received properly, the 802.11 radio that received the frame will reply with an acknowledgment (ACK) frame. If the ACK is received, the original station knows that the frame transfer was successful. All unicast 802.11 frames must be acknowledged. Broadcast and multicast frames do not require an acknowledgment. If any portion of a unicast frame is corrupted, the cyclic redundancy check (CRC) will fail and the receiving 802.11 radio will not send an ACK frame to the transmitting 802.11 radio. If an ACK frame is not received by the original transmitting radio, the unicast frame is not acknowledged and will have to be retransmitted. RF devices that just transmit intermittently can disrupt with 802.11 transmissions. The intermittent RF interferer will cause corruption of 802.11 unicast frames that are being transmitted and result in Layer 2 retransmissions. An increase in Layer 2 retransmissions will result in decreased throughput and increased latency. While this might not be as traumatic as a continuous transmitting device causing a complete denial of service, the WLAN performance is still adversely affected.
Taking out the entire band or a single channel for only a few seconds breaks all the communications of any upper-layer applications being used over the WLAN. When the attack is stopped, client stations must locate the AP again, authenticate/associate, get an IP address, and reestablish the application session.
Jamming attacks are often used to kick-start other types of attacks. Jamming can force client stations to reauthenticate. A protocol analyzer can then be used to capture the authentication process of clients using a weak method of authentication, such as LEAP or WPA/WPA2-Personal. The information needed to proceed with an offline dictionary attack has been captured. Narrow-band jamming can also be used to jump-start wireless hijacking, man-in-the-middle, and Wi-Fi phishing attacks described later in this chapter.
If you suspect that sources of interference are causing problems for your network, you can find them using a spectrum analyzer. A spectrum analyzer is a frequency domain measurement and troubleshooting tool. A spectrum analyzer can help identify and locate an interfering transmitter. Spectrum analyzers will be discussed in greater detail in Chapter 14.
Layer 2 DoS Attacks
The more common type of DoS attacks that originate from hackers are Layer 2 DoS attacks. A wide variety of Layer 2 DoS attacks exist that are a result of tampering with 802.11 frames and retransmitting them into the air. The most common involves spoofing disassociation or deauthentication management frames. Let’s examine some of the more common Layer 2 intentional DoS attacks.
Many of the intentional DoS attacks found here at Layer 2 use combinations of basic wireless networking requirements and the manipulation of what is required by wireless transmissions for them to succeed. For a client STA to pass data within the basic service set (BSS), it must be authenticated and associated. Without authentication, there is neither association nor Layer 2 connection.
An 802.11 management frame, called a deauthentication frame, is sometimes used by client stations and APs to sever communications at Layer 2. An 802.11 deauthentication frame is a notification and not a request. If a station wants to deauthenticate from an AP, or an AP wants to deauthenticate from stations, either device can send a deauthentication frame. Because authentication is a prerequisite for association, a deauthentication frame will automatically cause a disassociation to occur.
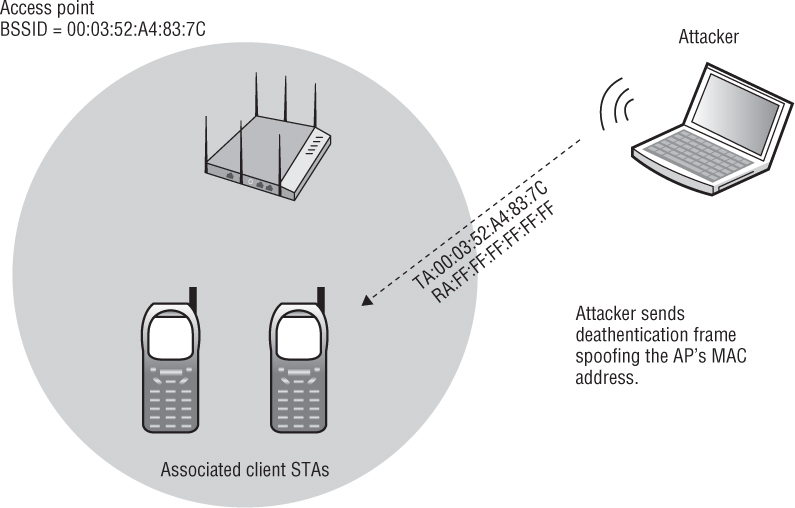
Sadly, deauthentication frames can easily be spoofed, and a deauthentication attack can be launched against a single device or the entire BSS. An attacker simply observes the MAC addresses of client stations and access points using a protocol analyzer. The attacker then uses a hex editor to edit a previously captured deauthentication frame. As shown in Figure 12.10, the attacker can edit the 802.11 header and spoof the MAC address of an access point or a client in either the transmitter address (TA) field or the receiver address (RA) field. The attacker then retransmits the spoofed deauthentication frame repeatedly. The station that receives the spoofed deauthentication frame thinks it is coming from another legitimate station and disconnects at Layer 2. Unicast deauthentication frames can be used as an attack against a single client or multiple clients can be deauthenticated if the destination address is a broadcast address.
FIGURE 12.10 Deauthentication attack
Disassociation attacks work in the same manner and are equally effective for the attacker. Just like deauthentication, disassociation is a notification, not a negotiation. Disassociation management frames can also be spoofed and thereby accomplish the same result as a deauthentication attack.
Let’s discuss some other Layer 2 DoS attacks that can be accomplished by simply editing 802.11 frames and retransmitting them into the air. Once such attack is called illegal channel beaconing. This attack uses a spoofed beacon frame transmitted on the same real channel as the legitimate AP, so that the associated client stations will hear the spoofed beacon. The spoofed beacon uses the same SSID, but the channel field has been edited to display a nonexistent, or illegal, channel. For example, there are 14 channels available for use in the 2.4 GHz range, none of which are used in the spoofed beacon. The attacker’s beacon could be telling the client STAs that the AP is on channel 0 or channel 432 or some other unused channel number, when in reality the attacker is beaconing on the same real channel used by the legitimate devices. The drivers of some WLAN vendor radios cannot interpret the illegal channel, and a denial of service is the result.
Probe requests and responses are management frames and can be spoofed just as beacons can be spoofed to disrupt network connectivity. If an attacker sends probe response frames to a victim station, even if it is already associated with a real AP, that station will assume that it should try to connect to that AP. The stations that fall victim to this attack did not send a probe request frame looking for this AP but will try to connect to it anyway. This attack is called a probe response flood.
Many Layer 2 DoS attacks are flooding attacks that use management or control frames to overwhelm an access point or client station. An example of a Layer 2 flooding involves an attack on an AP’s association table. The 802.11-2012 standard defines the maximum number of client associations to an access point radio as 2,007. In reality, no access point radio would ever want 2,007 clients associations, but in theory it is possible. Most vendors offer settings on APs or WLAN controllers to limit the number of active client associations to an AP for capacity purposes. For example, an administrator might set the maximum number of client associations to 75 per access point radio. An attacker can flood an AP with bogus association request frames and fill up the AP’s association table. Then, when any legitimate client attempts to associate, the legitimate clients are denied association because the maximum has already been reached. This attack is called an association flood.
Another Layer 2 DoS attack is called FakeAP. This software tool generates thousands of counterfeit management advertising fake SSIDs and BSSIDs. The original intent was to hide a real access point in plain sight among all the fake APs to confuse any wardrivers, script kiddies, or other undesirables. The problem is that the FakeAP tool can also be used for a DoS attack. Legitimate client stations may spend time attempting to associate to the APs that do not exist. Additionally, the extra airtime consumption within the service set area will degrade the performance of the WLAN.
As mentioned earlier is this chapter, Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) is the process used to ensure that only one 802.11 radio is transmitting at a time on the medium. Another major component of the CSMA/CA method of medium contention is virtual carrier sense. Virtual carrier sense uses a timer mechanism known as the network allocation vector (NAV) or the NAV timer. The NAV timer maintains a prediction of future traffic on the medium based on Duration value information seen in a previous frame transmission. When an 802.11 radio is not transmitting, it is listening. As shown in Figure 12.11, when the listening radio hears a frame transmission from another station, it looks at the Layer 2 header of the frame and determines whether the Duration/ID field contains a Duration value or an ID value. If the field contains a Duration value, the listening station will set its NAV timer to this value. The listening station will then use the NAV as a countdown timer, knowing that the RF medium should be busy until the countdown reaches 0. This process essentially allows the transmitting 802.11 radio to notify the other stations that the medium will be busy for a period of time (the Duration/ID value). The stations that are not transmitting listen and hear the Duration/ID value, set a countdown timer (NAV), and wait until their timer hits 0 before they can contend for the medium and eventually transmit on the medium. A station cannot contend for the medium until its NAV timer is 0, nor can a station transmit on the medium if the NAV timer is set to a nonzero value.
FIGURE 12.11 Virtual carrier sense

The Duration value can be set from 0 to 32767. Most frames do not approach the limit. If an attacker is not contending for the medium but simply transmitting frames with spoofed Duration/ID field values set near the upper limit, an attack known as the virtual-carrier attack will disrupt the WLAN. By selecting a value near the limit such as 29000, the attacker knows that stations are not likely to ignore the spoofed frame. Some stations will ignore values over 30000. The high value used by the attacker will cause stations in the area hearing it to set their NAV timer to that high number. The victims then must count down from that number to zero. Once they reach zero, the stations listen to the medium again, and they hear another spoofed frame from the attacker and reset their NAV timers, thus starting the process all over. In this case, the victim stations would never be allowed access to the medium. The attacker is simply winning the contention for the medium by using spoofed Duration values and causing everyone else to remain idle during the attacker’s transmissions.
Most Layer 2 DoS attacks are not doing anything “special.” The attackers are merely exploiting the way that 802.11 communications function at Layer 2 to disrupt legitimate traffic. As mentioned earlier, numerous Layer 2 DoS attacks exist such as association floods, reassociation floods, authentication floods, EAPOL floods, and PS-Poll floods. All of these attacks are accomplished by simply editing 802.11 frames and retransmitting them to disrupt Layer 2 communications.
MAC Spoofing
All 802.11 radios have a physical address known as a MAC address. This address is a 12-digit hexadecimal number that is seen in cleartext in the Layer 2 header of 802.11 frames. Wi-Fi vendors provide MAC filtering capabilities on their access points and WLAN controllers. Usually, MAC filters are configured to apply restrictions that will allow traffic only from specific client stations to pass through. These restrictions are based on their unique MAC addresses. All other client stations whose MAC addresses are not on the allowed list will not be able to pass traffic through the virtual port of the access point and onto the distribution system medium.
As you learned in Chapter 2, MAC addresses can be spoofed, or impersonated, and any amateur hacker can easily bypass any MAC filter by spoofing an allowed client station’s address. MAC addresses of WLAN devices can be spoofed within any operating system. MAC spoofing can often be achieved in the Windows operating system by simply editing the wireless radio’s MAC address in Device Manager or by performing a simple edit in the Registry. Third-party software utilities, such as SMAC (described in a moment), can also be used to accomplish MAC spoofing. MAC spoofing renders MAC filters useless as a form of security on wireless networks, since MAC addresses are always visible to anyone on the same channel and in the same area.
No two devices should ever have the same MAC address configured on them from the manufacturer. The organizationally unique identifier (OUI) address is the first three octets of the MAC address that identifies the manufacturer of the radio. The remaining octets of the MAC address are unique and are used to identify the individual radio. The existence of two radios with the same MAC address should not happen because vendors are very careful to avoid this in the manufacturing process to prevent address conflicts. Attackers, on the other hand, use duplicate MAC addressing to their advantage. By cloning a MAC address an attacker can bypass MAC filters. The filter cannot distinguish between a legitimate device and a spoofed device, thereby allowing them access to spoofed devices. The MAC filter has no way of knowing that more than one device is using the same addressing. Frames from either device—the real one or the attackers—are accepted by the network. Traffic leaving the network bound for either device is transmitted into the air. Both devices receive the frames but only the one expecting it processes the data. This happens because the devices are using different sockets. If the attacker is in close proximity to the cloned device, the attack may go undetected by some WIPS solutions that only use sensor location to trigger a MAC spoof–based alarm. To be able to detect spoofing more efficiently, better WIPS products also look at the sequence numbers of the frames being transmitted by the devices. If they are out of sequence, an alarm can be triggered, alerting a WLAN administrator to the MAC spoofing attack.
One place where a MAC spoofing attack is still used with great effect is at public-access WLAN hotspots. A MAC piggy-backing attack is used to circumvent the hotspot captive portal login requirements. The attacker is not trying to break into a network to steal data but rather to exploit the way the hotspot’s captive portal works to gain free Internet access. Captive portal authentication solutions are usually the only security provided for guest WLANs and public-access hotspots. Once a station connects to the hotspot SSID and gets an IP address, the user opens their browser. Rather than going to their normal home page, the user is redirected to the captive portal web login page. This page may have a simple terms-of-use agreement or may require credentials to access the Internet beyond the captive portal page. The required credentials could be a username and password or credit card information. When the captive portal is satisfied that the user has the correct information to gain Internet access—password, credit card, and so on—the captive portal authentication allows the user access to a gateway to the Internet. The only security beyond this point is a common MAC filter allowing access for users who have authenticated via the captive portal login page. An attacker uses a WLAN protocol analyzer to determine which stations are passing data frames through the AP, indicating the captive portal has approved their MAC addresses to do so. Then the attacker clones the MAC address of a station passing data through the AP onto their wireless radio. The attacker can then connect to the AP and pass data as well because the AP and its captive portal believe the attacker is an approved device. MAC piggy-backing is not normally considered a malicious attack, but the attack could be considered as theft of services if the hotspot requires payment for access.
If MAC addresses are designated by the manufacturer of the radios and no two MAC addresses should ever be the same, how are attackers able to change them? Attackers and users alike can change MAC addresses very easily using utilities within the operating system or programs designed to allow this change. As shown in Figure 12.12, changing the MAC address through the Windows OS can be done by directly editing the Registry value for the radio’s MAC address and rebooting the system. When the system comes back up, the radio will be using the new cloned MAC address.
FIGURE 12.12 MAC address Registry settings

As shown in Figure 12.13, many WLAN radios will allow a change of the MAC address to be made in the GUI without a system reboot. This option is typically found in the Advanced settings of the networking properties of the radio’s MAC address.
FIGURE 12.13 MAC address: networking settings

If the attacker does not wish to edit the Registry directly and the radio they are using does not have the option to configure a locally assigned MAC address, programs are available that will allow the user to change the MAC address despite the other limitations. One such program is SMAC from KLC Consulting. As shown in Figure 12.14, SMAC has the ability to set specific MAC addresses as well as the ability to generate MAC addresses based on known OUI structures from several vendors. It also keeps track of recently used MAC addresses for future use.

Because of spoofing and because of all the administrative work that is involved with setting up MAC filters, MAC filtering is not considered a reliable means of security for wireless enterprise networks and should be implemented only if stronger security is not available or in addition to some stronger form of security as part of a multifactor security plan.
Wireless Hijacking
An attack that often generates a lot of press is wireless hijacking, also known as the evil twin attack. The attacker configures access point software on a laptop, effectively turning a Wi-Fi client radio into an access point. Some small Wi-Fi USB devices also have the ability to operate as an AP. The access point software on the attacker’s laptop is configured with the same SSID that is used by a public-access hotspot. The attacker’s access point is now functioning as an evil twin AP with the same SSID but is transmitting on a different channel. The attacker then sends spoofed disassociation or deauthentication frames, forcing client stations associated with the hotspot access point to roam to the evil twin access point. At this point, the attacker has effectively hijacked wireless clients at Layer 2 from the original access point. Although deauthentication frames are usually used as one way to start a hijacking attack, RF jammers can also be used to force any clients to roam to an evil twin AP.
The evil twin AP will typically be configured with a Dynamic Host Configuration Protocol (DHCP) server available to issue IP addresses to the clients. At this point, the attacker will have hijacked the client stations at Layer 3. The attacker has a private WLAN network and is free to perform peer-to-peer attacks on any of the hijacked clients. The user’s computer could, during the process of connecting to the evil twin, fall victim to the DHCP attack, an attack that exploits the DHCP process to dump root kits or other malware onto the victim’s computer in addition to giving them an IP address as expected.
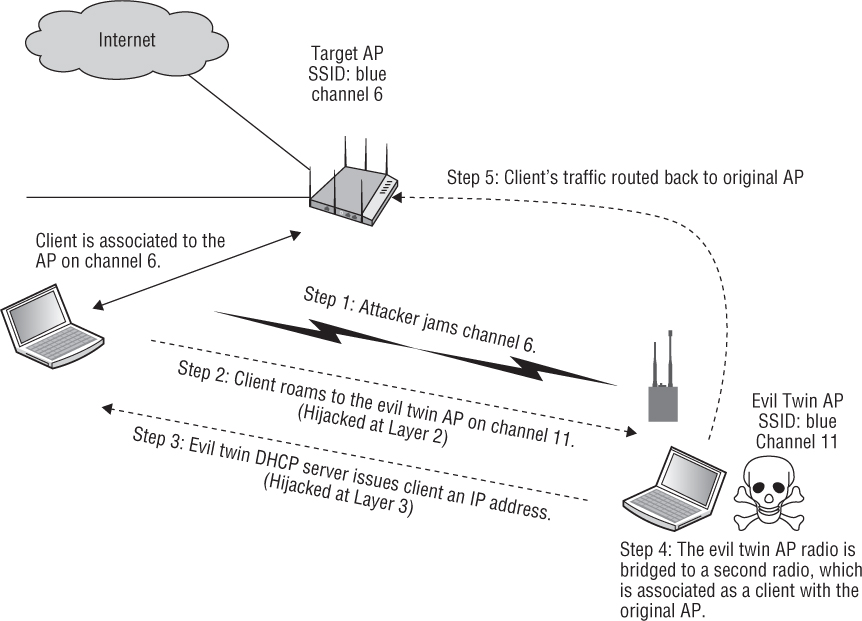
The attacker may also be using a second wireless radio with their laptop to execute what is known as a man-in-the-middle attack, as shown in Figure 12.15. The second WLAN radio is associated with the original access point as a client. In operating systems, network adapters can be bridged together to provide routing. The attacker has bridged together their second wireless radio with the Wi-Fi radio that is being used as the evil twin access point. After the attacker hijacks the users from the original AP, the traffic is then routed from the evil twin access point through the second Wi-Fi radio, right back to the original access point from which the users have just been hijacked. The result is that the users remain hijacked; however, they still have a route back through the gateway to their original network, so they never know they have been hijacked. The attacker can therefore sit in the middle and execute peer-to-peer attacks indefinitely while remaining completely unnoticed.
FIGURE 12.15 Wireless hijacking/man-in-the-middle attack
These attacks can take another form in what is known as the Wi-Fi phishing attack. The attacker may also have web server software and captive portal software. After the users have been hijacked to the evil twin access point, they will be redirected to a login web page that looks exactly like the hotspot’s login page. Then the attacker’s fake login page may request a credit card number from the hijacked user. Phishing attacks are common on the Internet and are now appearing at your local hotspot.
The only way to prevent a hijacking, man-in-the-middle, or Wi-Fi phishing attack is to use a mutual authentication solution. Mutual authentication solutions not only validate the user connecting to the network, but they also validate the network to which the user is connecting. 802.1X/EAP authentication solutions require that mutual authentication credentials be exchanged before a user can be authorized. A user cannot get an IP address unless authorized; therefore, users cannot be hijacked.
Encryption Cracking
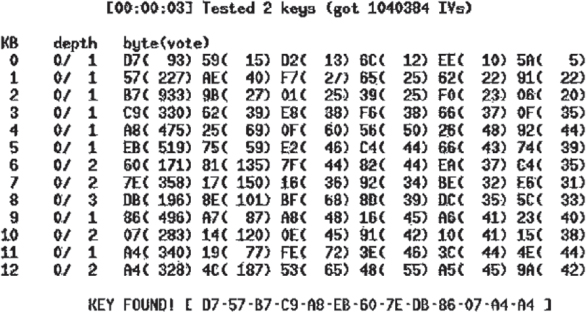
Encrypting transmitted information is extremely important in wireless communications, since the medium is shared and unbounded. If any degree of data privacy is to be expected, some form of encryption should be used—the stronger, the better. Earlier wireless networks used no encryption at all or they used Wired Equivalent Privacy (WEP) to encrypt the transmissions. As you learned in Chapter 2, WEP is a Layer 2 encryption method that does indeed provide data privacy when encrypting the Layer 3–7 data payload known as the MAC Service Data Unit (MSDU). Unfortunately, WEP has been cracked, and software tools exist that can derive the static WEP key from 802.11 data frame traffic that has been captured using a protocol analyzer. Older WEP cracking software could take days to run because the number of Initialization Vectors (IVs) needed to crack the key is relatively high. WEP uses either a 40-bit secret key or a 104-bit secret key to protect the data. No matter which secret key length is used, 40-bit or 104-bit, WEP only uses a 24-bit IV. If an attacker gathers enough IVs they can crack 64-bit and 128-bit WEP in minutes. An attacker would need to capture about 500,000 IVs to be able to crack the WEP key. In a SOHO environment, this could take weeks of captures. In an enterprise, with a larger traffic volume than SOHO networks, this could still take days.
As shown in Figure 12.16, modern freeware cracking tools can now break through WEP protected frames in a matter of minutes and obtain the static WEP key. Modern cracking tools now use an injection attack that forces devices to generate the IVs much faster than regular traffic requires. The injection attacks often use Address Resolution Protocol (ARP) flooding to force this to happen. Now cracking 128-bit WEP keys can be done in a few minutes versus the days and weeks of older tools that employed large capture files and brute-force attacks. Once an attacker has obtained the WEP key, they can connect to the WLAN and decode the data captured offline or decode data frames in real time.
Network managers abandoned WEP for newer, more secure dynamic encryption methods. To improve on the security offered by WEP, the Temporal Key Integrity Protocol (TKIP) was developed. TKIP uses 48-bit IVs, time-bound keys, and the RC4 algorithm for an improvement over the security offered by WEP. TKIP encryption is no longer considered secure and is not supported for any 802.11n or 802.11ac data rates. Modern-day WLAN radios use dynamic CCMP encryption, which uses the 128-bit AES cipher.
Peer-to-Peer Attacks
A commonly overlooked risk is the peer-to-peer attack. As you learned in earlier chapters, an 802.11 client station can be configured in either infrastructure mode or ad hoc mode. When configured in ad hoc mode, the wireless network is known as an independent basic service set (IBSS) and all communications are peer-to-peer without the need for an access point. Because an IBSS is by nature a peer-to-peer connection, any user who can connect wirelessly with another user can gain access to any resource available on either computer. A common use of ad hoc networks is to share files on the fly. If shared access is provided, files and other assets can accidentally be exposed. A personal firewall is often used to mitigate peer-to peer attacks. Some client devices can also disable this feature so that the device will connect only to certain networks and will not associate to a peer-to-peer without approval.
Users who are associated to the same access point are potentially just as vulnerable to peer-to-peer attacks as IBSS users. Properly securing your wireless network often involves protecting authorized users from each other, because hacking at companies is often performed internally by employees. Any users associated to the same AP who are members of the same basic service set (BSS) and are in the same VLAN are susceptible to peer-to-peer attacks because they reside in the same Layer 2 and Layer 3 domains. In most WLAN deployments, Wi-Fi clients communicate only with devices on the wired network, such as email or web servers, and peer-to-peer communications are not needed. Therefore, most enterprise AP vendors provide some proprietary method of preventing users from inadvertently sharing files with other users or bridging traffic between the devices. If connections are required to other wireless peers, the traffic is routed through a Layer 3 switch or other network device before passing to the desired destination station.
Client isolation is a feature that can often be enabled on WLAN access points or controllers to block wireless clients from communicating with other wireless clients on the same wireless VLAN. Client isolation, or the various other terms used to describe this feature, usually means that packets arriving at the AP wireless interface are not forwarded back out of the wireless interface to other clients. This isolates each user on the wireless network to ensure that a wireless station cannot be used to gain Layer 3 or higher access to another wireless station. The client isolation feature is usually a configurable setting per SSID linked to a unique VLAN. With client isolation enabled, client devices cannot communicate directly with other client devices on the wireless network, as shown in Figure 12.17.

NOTE
Although client isolation is the most commonly used term, some vendors instead use the terms peer-to-peer blocking or public secure packet forwarding (PSPF). Not all vendors implement client isolation in the same fashion. Some WLAN vendors can only implement client isolation on an SSID/VLAN pair on a single access point, whereas others can enforce the peer-blocking capabilities across multiple APs.
Management Interface Exploits
One of the main goals of attackers is to gain access to administrative accounts or root privilege. Once they gain that access, they can run several attacks against networks and individual devices. On wired networks these attacks are launched against firewalls, servers, and infrastructure devices. In wireless attacks, these are first launched against access points or WLAN controllers and subsequently against the same targets as in wired attacks. Wireless infrastructure hardware such as autonomous access points and WLAN controllers can be managed by administrators via a variety of interfaces, much like managing wired infrastructure hardware. Devices can typically be accessed via a web interface, a command-line interface, a serial port, a console connection, and/or Simple Network Management Protocol (SNMP). It is imperative that these interfaces be protected. Interfaces that are not used should be disabled. Strong passwords should be used, and encrypted login capabilities such as Hypertext Transfer Protocol Secure (HTTPS) should be used if available.
Lists of all the default settings of every major manufacturer’s access points exist on the Internet and are often used for security exploits by hackers. It is not uncommon for intruders to use security holes left in management interfaces to reconfigure access points. Legitimate users and administrators can find themselves locked out of their own wireless networking equipment. After gaining access via a management interface, an attacker might even be able to initiate a firmware upgrade of the wireless hardware and, while the upgrade is being performed, disable the equipment’s power source. This attack could likely render the hardware useless, requiring it to be returned to the manufacturer for repair.
Many WLAN devices often have settings that allow for remote administration via the Internet. Although these settings are intended for legitimate administrators, an attacker may use remote access to management interfaces to perform the same attacks just described. Remote access should either be turned off or locked down tight.
Policy often dictates that all WLAN infrastructure devices be configured from only the wired side of the network. If an administrator attempts to configure a WLAN device while connected wirelessly, the administrator could lose connectivity due to configuration changes being made. Some WLAN vendors offer secure wireless console connectivity capabilities for troubleshooting and configuration.
Vendor Proprietary Attacks
Hackers often find holes in the firmware code used by specific WLAN access points and WLAN controller vendors. New WLAN vulnerabilities and attacks are discovered on a regular basis, including vendor proprietary attacks. Many of these vendor-specific exploits are in the form of buffer overflow attacks. When these vendor-specific attacks become known, the WLAN vendor usually makes a firmware fix available in a timely manner. Once the exploits are discovered, the affected WLAN vendor will make safeguard recommendations on how to avoid the exploit. In most cases the WLAN vendor will release a patch that can fix the problem. These attacks can be best avoided by staying informed through your WLAN vendor’s support services.
Physical Damage and Theft
An important aspect of the installation of wireless equipment is the “pretty factor.” The majority of businesses prefer that all wireless hardware remain completely out of sight. Aesthetics is extremely important in retail environments and in the hospitality industry (restaurants and hotels). Any business that is dealing with the public will require that the Wi-Fi hardware be hidden or at least secured. Many vendors are designing better-looking access points and antennas. Some vendors have even camouflaged access points to resemble smoke detectors. Indoor enclosures that are mounted in place of ceiling tiles are also often used to conceal access points. It should also be noted that most enclosure units can be locked to help prevent physical damage or theft of expensive Wi-Fi hardware.
Client devices such as VoWiFi phones and WLAN barcode scanners are often easily stolen. Several companies such as AeroScout and Ekahau provide a WLAN real-time location system (RTLS), which can track the location of any 802.11 radio device as well as active Wi-Fi RFID tags with great accuracy. The components of an overlay WLAN RTLS solution include the preexisting WLAN infrastructure, preexisting WLAN clients, Wi-Fi RFID tags, and an RTLS server. Additional RTLS WLAN sensors can be added to supplement the preexisting WLAN APs.
Active RFID tags and/or standard Wi-Fi devices transmit a brief signal at a regular interval, adding status or sensor data if appropriate. Figure 12.18 shows an active RFID tag attached to heathcare monitoring equipment. The signal is received by standard wireless APs (or RTLS sensors), without any infrastructure changes needed, and is sent to a processing engine that resides in the RTLS server at the core of the network. The RTLS server uses signal strength and/or time-of-arrival algorithms to determine location coordinates.
FIGURE 12.18 Active 802.11 RFID tag

Courtesy of Ekahau
As pictured in Figure 12.19, a software application interface is then used to see location and status data on a display map of the building’s floor plan. The RTLS application can be used to define zones on the floor plan that will trigger alarms if client devices or RFID tags leave a certain area or zone. An RTLS solution can greatly reduce theft of WLAN devices as well as any company assets with an attached RFID tag.

Courtesy of Ekahau
Social Engineering
Social engineering or “hacking the user” is a very real threat to all networks. Social engineering involves getting users to reveal information without knowing they have done so. It also may involve gaining information from public sources such as the target’s website or corporate reports. Another effective social engineering attack is dumpster diving—going through the target’s trash looking for information. This once was a big problem for credit cards. Retailers used carbon papers and physical imprints of the customer’s card as part of the transaction. The carbon papers would be discarded by the clerks and later deposited in common garbage dumpsters. People wanting to use the credit card numbers of others would go through the trash in the dumpster to find the carbon papers and thus the credit card numbers.
Phishing is also a social engineering attack. Phishing is a criminal process used to acquire sensitive information fraudulently, such as usernames, passwords, and credit card information, by masquerading as a valid authority during electronic communication. Many of us have gotten the infamous email “I am in another country and need help getting my millions out, and I will share the money with you for your help.” Perhaps you received the email from a bank or government office asking for your personal information or bank account numbers. Why do these obvious junk emails, phone calls, and letters continue to be sent? These scams continue because some unfortunate people respond to them, giving the criminals the information or money they desire. The Wi-Fi phishing attack discussed earlier in this chapter uses wireless hijacking techniques and a bogus captive portal to perpetrate a similar scam.
Computer network users sometimes are even more careless with corporate information and device security. People are often more concerned with ease of use than they are with security. Users will often keep the same simple passwords for months or years. Their passwords can be found written on sticky notes under their keyboards or stuck to their monitors. No matter how much money is spent on security equipment and software or even on security guards, users still may carelessly or unwittingly give attackers information that will compromise security measures. For example, a call can be placed to users stating that the caller is from the IT security team. The caller may tell the user that some unapproved software or freeware that is not allowed has been detected on their machine. The caller tells the user they want to help the user become compliant with corporate policy and, that by giving them their username and password, the caller will be able to remove the suspicious software from their machine without the caller having to report it as a policy violation to the user’s manager. Desperate to avoid trouble, users may comply with the attacker’s requests.
Users cannot all be trained security professionals. How can we train our users to be more security conscious as they travel with company laptops? We can train them to make sure their personal firewalls are always on and that their antivirus software is up to date and running, and to recognize social engineering attacks and report them to corporate security teams as soon as possible.
A variant of these attacks is called reverse social engineering. This is a process by which an attacker poses as someone in authority and gives the user bogus information rather than trying to get information from the user. The users are almost always the weakest link in network security.
The best defense against social engineering attacks are strictly enforced policies to prevent confidential information from being shared. Any information that is static is extremely susceptible to social engineering attacks. WEP encryption uses a static key, and WPA/WPA2-Personal requires the use of a static PSK or passphrase. You should avoid both of these security methods because of their static nature.
Guest Access and WLAN Hotspots
When you are using the WLAN at an Internet cafe, coffee shop, airport, hotel, and other public WLAN hotspots, you are not as protected as you are as when you are using your organization’s WLAN where security measures have been taken to protect your wireless communications. Hotspots are often breeding grounds for peer-to-peer attacks, viruses, hijacking, data theft or manipulation, eavesdropping attacks, and other malicious events. So what makes these convenient connections so vulnerable to attacks? There is no real security provided by the hotspot’s host. The hotspots may be using a captive portal requiring users to agree to the terms of use statement prior to granting the connection. Captive portal authentication is considered to be a weak authentication method but is normally adequate for simply authorizing users to access a gateway to the Internet. However, public-access WLANs do not offer an encryption solution. Additionally, most companies now offer guest WLAN access at their place of business and encryption is rarely used. All 802.11 data frames are therefore unencrypted and susceptible to malicious eavesdropping attacks.
Hotspots do not deploy wireless intrusion prevention systems (WIPS) to protect users either. Thus there is also no security monitoring of the insecure WLAN connectivity. The vast majority of hotspots users are not security conscious as they travel, making them vulnerable to attack as well.
Knowing that hotspots are the “wild west of Wi-Fi,” we can implement a remote access policy for all corporate employees who access hotspots and other non-corporate guest Wi-Fi networks. End users will be taking their laptops and handheld devices off site and away from company grounds. Most users will likely use wireless networks at home and at wireless hotspots to access the Internet. By design, many of these remote wireless networks have absolutely no security in place, and it is imperative that a remote access WLAN policy be strictly enforced. This policy should include the required use of an IPsec VPN solution to provide device authentication, user authentication, and strong encryption of all wireless data traffic. Hotspots are prime targets for malicious eavesdropping attacks.
Personal firewalls should also be installed on all remote computers to prevent peer-to-peer attacks. Personal firewalls will not prevent hijacking attacks or peer-to-peer attacks, but will prevent attackers from accessing most critical information. Endpoint WLAN policy enforcement software solutions exist that force end users to use VPN and firewall security when accessing any wireless network other than the corporate WLAN. The remote access policy is mandatory because the most likely and vulnerable location for an attack to occur is at a public-access hotspot.
The problem is that many consumers and guest users are not savvy enough to know how to use a VPN solution when connected to an open guest WLAN. As a result, there is a recent trend to provide encryption and better authentication security for WLAN guest users. Encrypted guest access is discussed in more detail in Chapter 10, “BYOD and Guest Access.”
Summary
Due to the unbounded functionality of wireless networking exposing Layers 1 and 2 to anyone within listening range and on the same frequency, there are many more risks involved in its use than are found in traditional bounded networking. Strong security measures exist for WLAN communications that should be employed to mitigate the risks involved in 802.11 communications. WLAN administrators should have a thorough understanding of all of the WLAN security risks and potential attacks. Thorough comprehension of all WLAN threats will ultimately result in the better decisions when choosing 802.11 security solutions for the enterprise.
Exam Essentials
Understand the risk of the rogue access point. Be able to explain why the rogue AP and other rogue devices provide a portal into network resources. Understand that hackers are usually not the source of rogue devices.
Define peer-to-peer attacks. Understand that peer-to-peer attacks can happen via an AP or through an ad hoc network. Explain how to defend against the attack.
Know the risks of eavesdropping. Explain the difference between casual and malicious eavesdropping. Explain why encryption is needed for protection.
Define authentication and hijacking attacks. Explain the risks behind these attacks. Understand that a strong 802.1X/EAP solution is needed to mitigate these attacks.
Explain wireless denial-of-service attacks. Know the difference between Layer 1 and Layer 2 DoS attacks. Explain why these attacks cannot be mitigated and can only be monitored.
Understand management interface exploits. Explain the reasons for hardening the WLAN infrastructure for authorized and secure administration only.
Understand the concept of social engineering. Know that end users are always the weakest link in WLAN security. Explain why end users need to be trained to recognize social engineering attacks. Understand that any type of static password, passphrase, or shared encryption key is always susceptible to a social engineering attack.
Review Questions
1. When an attacker passively captures and examines wireless frames from a victim’s network, what type of attack is taking place?
A. Injection
B. Data destruction
C. Frame manipulation
D. Man in the middle
E. Eavesdropping
2. Which of these attacks are considered denial-of-service attacks? (Choose all that apply.)
A. Man-in-the-middle
B. Jamming
C. Deauthentication spoofing
D. MAC spoofing
E. Peer-to-peer
3. The majority of rogue devices are placed by whom? (Choose all that apply.)
A. Attackers
B. Wardrivers
C. Employees
D. Contractors
E. Visitors
4. Which of these attacks would be typically associated with malicious eavesdropping? (Choose all that apply.)
A. NetStumbler
B. Peer-to-peer
C. Protocol analyzer capture
D. Packet reconstruction
E. PS polling attack
5. What are some of the risks if a rogue device goes undetected?
A. Data theft
B. Data destruction
C. Loss of network services
D. Data insertion
E. Third-party attacks
F. All of the above
6. Which of these can cause unintentional RF jamming attacks against an 802.11 wireless network? (Choose all that apply.)
A. Microwave oven
B. Signal generator
C. 2.4 GHz cordless phones
D. 900 MHz cordless phones
E. Deauthentication transmitter
7. Which of these attacks are wireless users susceptible to at a public-access hotspot? (Choose all that apply.)
A. Wi-Fi phishing
B. Happy AP attack
C. Peer-to-peer attack
D. Malicious eavesdropping
E. 802.11 reverse ARP attack
F. Man-in-the-middle
G. Wireless hijacking
8. Which of these encryption technologies have been cracked? (Choose all that apply.)
A. 64-bit static WEP
B. 128-bit Dynamic WEP
C. CCMP/AES
D. 128-bit static WEP
9. Which of these attacks are considered Layer 2 denial-of-service attacks? (Choose all that apply.)
A. Deauthentication spoofing
B. Jamming
C. Virtual carrier attacks
D. PS-Poll floods
E. Authentication floods
10. What type of security solution can be used to prevent rogue WLAN devices from becoming an unauthorized portal to a wired network infrastructure? (Choose all that apply.)
A. 802.1X/EAP
B. Port control
C. WIPS
D. CCMP/AES
E. WIDS
11. What can happen when an intruder compromises the preshared key used during WPA/WPA2-Personal authentication? (Choose all that apply.)
A. Decryption
B. Eavesdropping
C. Spoofing
D. Encryption cracking
E. Access to network resources
12. What is another name for a wireless hijacking attack?
A. Wi-Fi phishing
B. Man-in-the-middle
C. Fake AP
D. Evil twin
E. AirSpy
13. MAC filters are typically considered to be a weak security implementation because of what type of attack?
A. Spamming
B. Spoofing
C. Phishing
D. Cracking
E. Eavesdropping
14. Which components of Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) can be compromised by a denial-of-service attack? (Choose all that apply.)
A. NAV timer
B. Interframe spacing
C. Clear channel assessment
D. Random backoff timer
15. What security can be used to stop attackers from seeing the MAC addresses used by your legitimate 802.11 WLAN devices?
A. MAC spoofing
B. VPN tunneling
C. CCMP/AES encryption
D. Use 802.1X authentication
E. None of the above
16. Wired leakage occurs under which of the following circumstances?
A. When weak wireless encryption is used
B. When weak wireless authentication is used
C. When wired broadcast traffic is passed through an AP
D. When wired unicast traffic is passed through an AP
E. When the protection mode is disabled on an AP
17. Which of these attacks can be mitigated with a mutual authentication solution? (Choose all that apply.)
A. Malicious eavesdropping
B. Deauthentication
C. Man-in-the-middle
D. Wireless hijacking
E. Authentication flood
18. Wireless intrusion prevention systems (WIPSs) are unable to detect which of the following attacks?
A. Association flood
B. Malicious eavesdropping
C. Management frame fuzzing
D. Injection attacks
E. Null probe attacks
19. Name two types of rogue devices that cannot be detected by a Layer 2 wireless intrusion prevention system (WIPS).
A. 900 MHz radio
B. 802.11h-compliant device
C. FHSS radio
D. 802.11b routers
E. 802.11g mixed-mode device
20. What type of solution can be used to perform countermeasures against a rogue access point?
A. WPA-Enterprise
B. 802.1X/EAP
C. WIPS
D. TKIP/RC4
E. WINS
