15
Exploring Cyberattacks and Threats
As an aspiring network professional, it’s essential to understand the fundamentals of various types of cyberattacks, how they are performed by hackers, and the goal of the attack on a target. Security has become everyone’s concern, whether you’re beginning a career in the field of IT or already a seasoned professional. Each day, hackers are exploiting systems within organizations around the world and cybersecurity professionals are working continuously to create a proactive approach to prevent these attacks and stop hackers. Hence, network professionals, who are the architects of designing, implementing, and maintaining network infrastructure, also need to have a foundation in security threats and attacks.
In this chapter, you will learn how various types of network-based attacks are performed by threat actors and their impact on the confidentiality, integrity, and availability of systems and resources. Additionally, you will learn how hackers can perform wireless-based attacks to compromise both personal and enterprise wireless networks. Lastly, you will learn how threat actors can hack the human minds of their victims to trick them into revealing sensitive information.
In this chapter, we will cover the following topics:
- Exploring network-based attacks
- Understanding wireless attacks
- Delving into human and environmental attacks
Let’s dive in!
Exploring network-based attacks
Threat actors such as hackers always look for security vulnerabilities in the systems and networks of their targets. A seasoned hacker will attempt to compromise the low-hanging fruits, as these are the security flaws that are easy to exploit on a system and do not require too much complexity in setting up the attack. Quite often, many people think security vulnerabilities are found only on applications and operating systems, but not on the network and its protocols. In the early days of the internet, many networking protocols were not designed with security features since it was not a concern as it is in today’s world. Many of these unsecure network protocols make up the Transmission Control Protocol/Internet Protocol (TCP/IP) networking model, which is implemented on every device that’s connected to a network. Therefore, the TCP/IP networking model contains a lot of vulnerabilities that can easily be exploited by hackers on a network, allowing them to perform various types of network-based attacks.
In this section, you will explore various types of network-based attacks that are common within the cybersecurity and networking industry.
Denial of service
A Denial-of-Service (DoS) attack is a common network-based attack that exploits the vulnerabilities within TCP/IP. This allows an attacker to compromise the availability of a network service or resource, thus preventing access to the resource from legitimate users on the network. For instance, imagine an organization has a web server on the internet that’s hosting an e-commerce application that allows the company to sell its products to anyone online. Each potential customer uses the web browser on their computer to send an HTTP request message to the e-commerce web server, instructing the server to send its home page to the client. For each HTTP request message that is received on the server, computing resources such as CPU, memory, storage, and network bandwidth are allocated to process and respond to the user.
As more users send HTTP request messages to the server, the server allocates available computing resources to quickly process and respond to each message. If a hacker sends thousands of unsolicited HTTP request messages to the server, the server will continue to allocate any available computing resources to process each message. Simply put, the CPU and memory utilization will increase quickly, causing the server to be occupied with processing the bogus requests from the hacker and not responding to legitimate requests from the potential customers on the network. Overall, as this malicious activity continues, the server will eventually stop responding to any request message because it’s too busy processing a huge amount of unsolicited messages, therefore denying legitimate users access to the services provided by the server.
The following diagram displays a hacker performing a DoS attack on a single server:
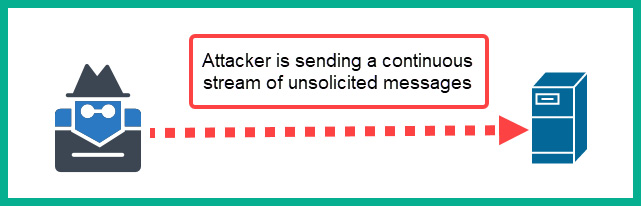
Figure 15.1 – DoS attack
As shown in the preceding diagram, the source of the attack is originating from a single geographic location – this is typically a single source IP address. Therefore, cybersecurity professionals can easily identify the source of the traffic by inspecting the source IP address within the IP header of the packet, then implementing an Access Control List (ACL) to restrict traffic. This ACL can be implemented on the edge router or firewall on the organization’s perimeter network.
Launching a single DoS attack against a target can easily be mitigated. Additionally, the goal of performing a DoS attack is to ensure the target resources or services are unavailable to legit users. Sometimes, an organization may implement various technologies to ensure its critical servers are resilient against failures and cyberattacks. Therefore, a network and server may continue to provide services and resources to legitimate users while being under a DoS attack. In this situation, the threat actor will soon realize their attack is not creating a major impact, as expected, and that the target is still up and running.
However, if a group of hackers from different geographic locations all coordinate and launch a DoS attack on the same target, this is commonly referred to as a Distributed Denial-of-Service (DDoS) attack. A DDoS is an amplified version of a DoS attack as it originates from multiple, different geographic locations at the same time, and it is quite difficult to stop. While a cybersecurity professional will be able to determine the security incident that’s happening, blocking all the source IP addresses can be quite challenging as there can be hundreds or even thousands of source IP addresses.
The following diagram shows a DDoS attack being performed against a single target:
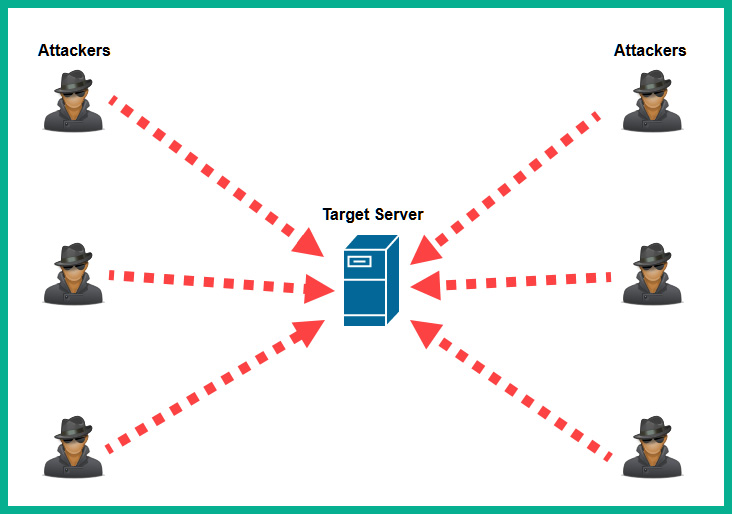
Figure 15.2 – DDoS attack
Sometimes, organizations are unable to stop or mitigate a massive DDoS attack and have to resort to disconnecting the affected server. This means disconnecting the affected server from the internet for a while before re-connecting it again. Hence, it is important to implement next-generation firewalls and internet security solutions with the capabilities of detecting and mitigating these attacks.
However, keep in mind that many seasoned hackers will attempt to fake their identity by changing their real source IP address to a fake IP address; this is known as IP spoofing. This technique is commonly used by hackers to prevent their real location or IP address from being known by cybersecurity professionals and law enforcement.
The following diagram shows an attacker who is spoofing their IP address:
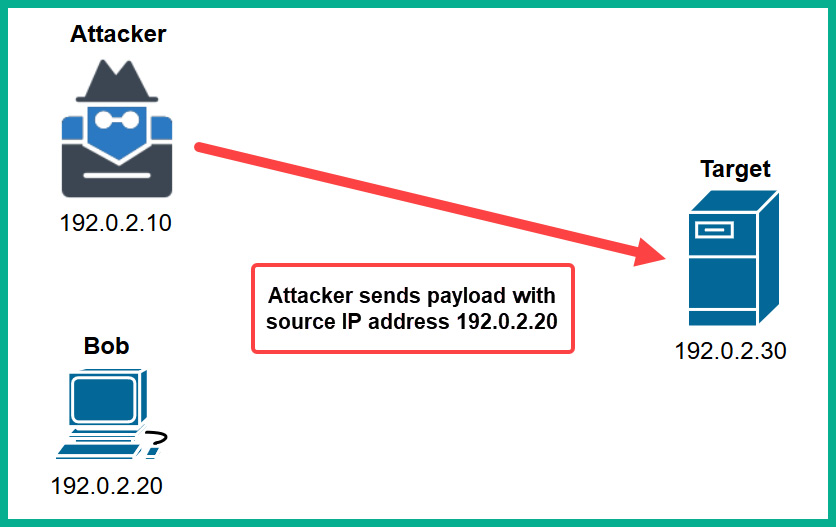
Figure 15.3 – IP spoofing
Hackers commonly use IP spoofing to perform a Reflected DDoS attack on their target. In a Reflected DDoS attack, the hackers spoof the target’s IP address and set it as their own, then use the spoofed IP address to flood unsolicited packets to a public server such as a Domain Name System (DNS) server, which commonly responds to DNS query messages. When the public server receives unsolicited packets from the hackers, it will respond to the spoofed IP address that belongs to the actual target.
The following diagram shows a Reflected DDoS attack:
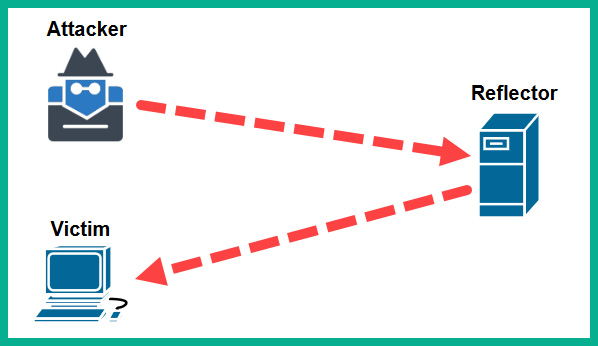
Figure 15.4 – Reflected DDoS attack
As shown in the preceding diagram, a threat actor has spoofed the IP address of the target server, then sent lots of DNS query messages to a public DNS server that responds to each query. The responses from the DNS server are sent to the actual target machine, thus creating a reflected attack. Additionally, hackers can use multiple reflectors to create an Amplified DDoS attack, as shown here:
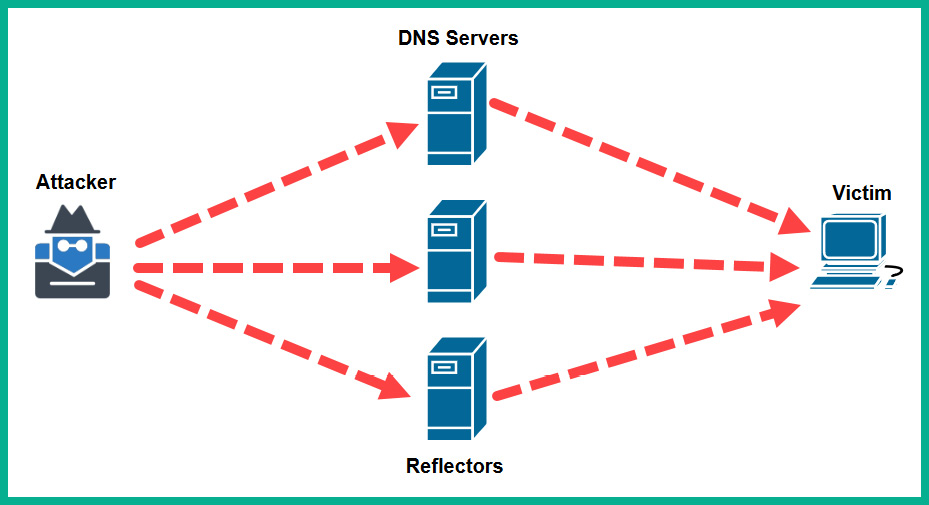
Figure 15.5 – Amplified DDoS attack
As shown in the preceding diagram, an infected machine is sending multiple request messages to multiple public servers on the internet. Each public server will respond to the spoofed IP address, so all the responses are sent to the target machine. Hackers do not necessarily choose one specific attack; they can use a combination or chain of attacks to compromise their targets. Most commonly, hackers do not launch DoS attacks from their machines – they’re usually launched from multiple malware-infected machines on the internet.
Next, you will learn how hackers infect hundreds of machines on the internet and create an army of infected systems.
Botnets
Let’s imagine a hacker wants to compromise the availability of a public web server on the internet. Using a DoS attack may affect the availability of the web server for any legitimate user. However, if the web server is resilient, the DoS from the attacker’s machine may not be powerful enough to have a massive impact. Since the attacker is determined to compromise the availability of the target, the hacker can set up Command and Control (C2) operations to centrally control a group of infected machines on the internet to perform the attack, as instructed by the hacker.
When setting up C2 operations, the hacker will need to infect as many systems as possible on the internet with a bot. A bot is simply a type of malware that infects a system such as a computer or a server, allowing the hacker to take control and instruct the compromised system to perform malicious actions on other systems, making it a zombie. Typically, a hacker can compromise and install malware on trusted and popular web servers on the internet. Whenever an unaware user visits any of these malware-infected servers with their device, the bot is downloaded and installed on the user’s machine. As more systems become infected with bots, it creates a huge network of infected systems known as a botnet, which is centrally managed by the hacker using a C2 server.
The following diagram shows a botnet that is being managed by a single hacker on the internet:
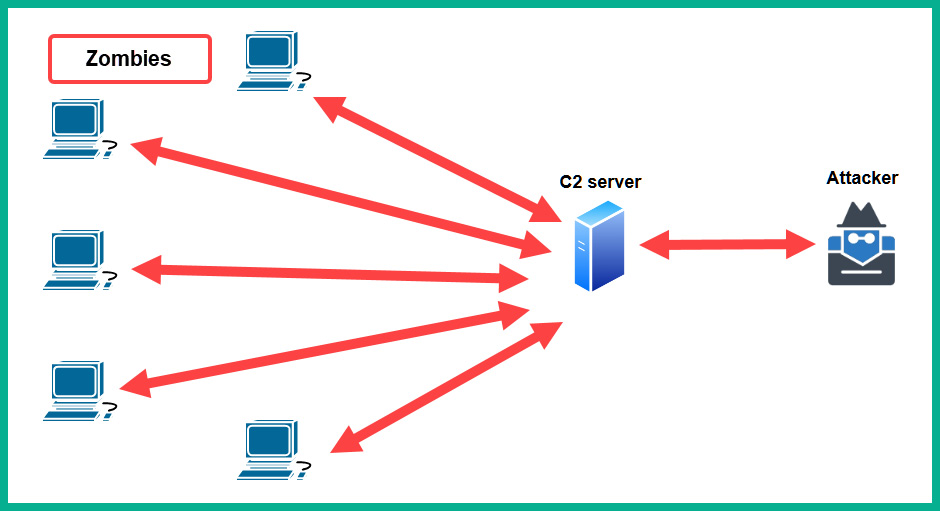
Figure 15.6 – Botnet
As shown in the preceding diagram, the botnet is metaphorically a robot army that awaits the instructions from the C2 server that is managed by the hacker. Whenever the hacker wants to launch a DDoS attack against a public server, the hacker connects to the C2 server and sends the instructions (commands). The C2 server will forward these instructions to any bot that lives on the internet, and they will execute the instructions and perform the attack on the target.
Next, you will learn about a Layer 2 attack that is commonly used by hackers, mostly on internal networks, to intercept data on unsecure communication channels.
On-path attack
An on-path attack or Man-in-the-Middle (MiTM) attack is a common network-based attack that occurs on an internal network within an organization. A hacker uses an on-path attack to intercept traffic over a communication channel, such as a wired or wireless network, to capture sensitive or confidential information that’s transmitted over the network. As you have learned thus far, many networking protocols are responsible for communication between systems over a network. However, many common unsecure network protocols are used on modern networks. Unsecure network protocols do not provide data security features such as data encryption when transmitting a message over a network. This creates an opportunity for a threat actor who has gained unauthorized access to a network to intercept and capture confidential data.
The following diagram shows an attacker’s machine connected to a network:
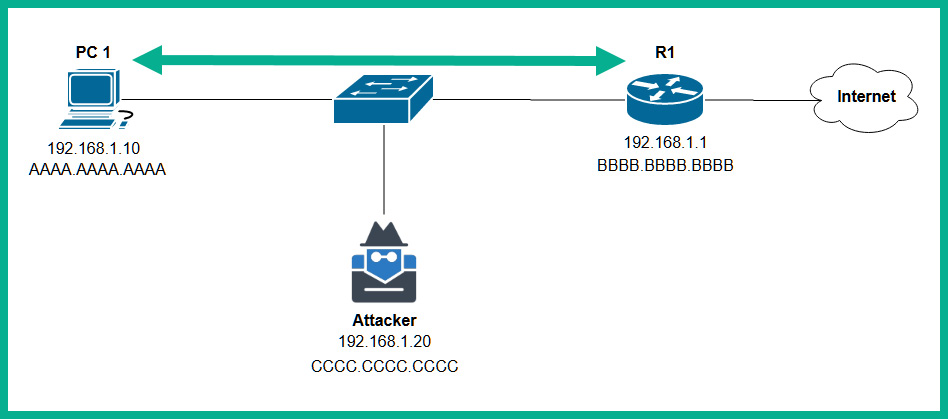
Figure 15.7 – Attacker’s machine on a network
As shown in the preceding diagram, the attacker’s machine is connected to the same network switch as PC 1 and the router. If PC 1 has to forward traffic to the internet, the traffic is sent to the switch and then to the router. The switch inspects the destination Media Access Control (MAC) address within the frame header, then forwards the message directly to the router. For the attacker’s machine to intercept the traffic between PC 1 and the router, the attacker will need to exploit the security vulnerabilities within the Address Resolution Protocol (ARP).
Important note
ARP is a common network protocol that allows systems to resolve IP addresses to MAC addresses.
The attacker needs to perform ARP poisoning on the ARP caches on PC 1 and the router by sending gratuitous ARP messages to both devices. For instance, the attacker machines send gratuitous ARP messages to PC 1, which contain the IP address of the router and the MAC address of the attacker’s machine. This technique poisons the ARP cache of PC 1 into thinking the router is now associated with the MAC address of the attacker’s machine. Therefore, if PC 1 has to send any packets to the router, it will insert the attacker’s MAC address as the destination’s MAC address within the packet. Once the packet leaves PC 1 and is received by the switch on the network, the switch will then forward the packet to the attacker’s machine.
Additionally, the attacker sends gratuitous ARP messages to the router to poison its ARP cache. The attacker machine creates gratuitous ARP messages that contain the IP address of PC 1 and the MAC address of the attacker’s machine. Once the router receives and processes these messages, the router’s ARP cache will automatically update to associate the attacker’s MAC address with the IP address of PC 1. Therefore, many packets from the router to PC 1 will be sent to the attacker’s machine on the network, hence allowing the attacker’s machine to intercept bi-directional communication between PC 1 and the router.
The following are the technical phases during an on-path attack in a network:
- The attacker machine is connected to the network but does not intercept the packets between PC 1 and the router, as shown here:
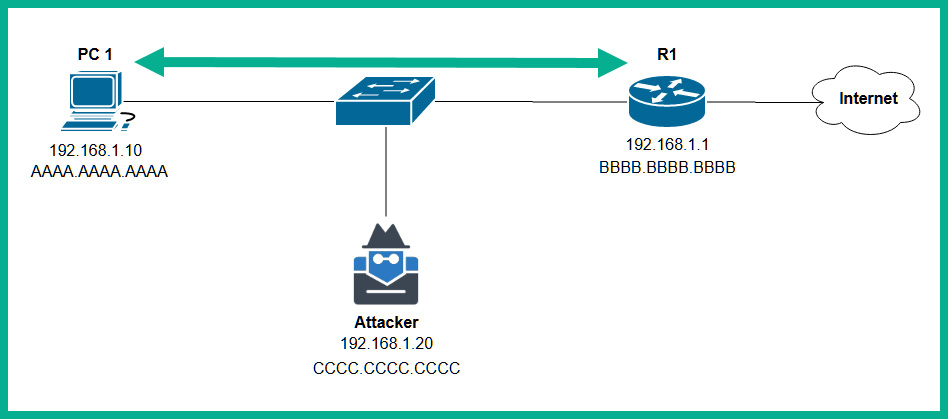
Figure 15.8 – Phase 1
- The attacker machine sends a gratuitous ARP message to both PC 1 and the router that contains false IP-to-MAC address information. The attacker machine sends a gratuitous ARP message to PC 1 with 192.168.1.1 -> CC-CC-CC-CC-CC-CC and to the router with 192.168.1.10 -> CC-CC-CC-CC-CC-CC, as shown here:
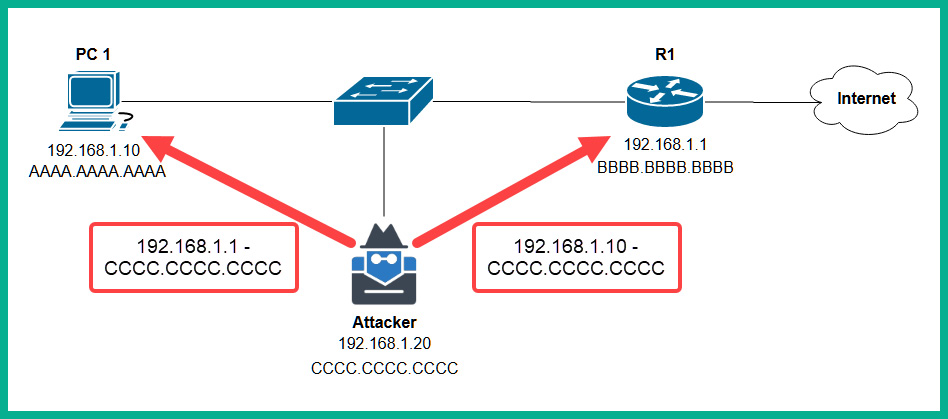
Figure 15.9 – Phase 2
- Once the ARP caches on both PC 1 and the router have been poisoned with false information, whenever they forward messages to each other, the messages are sent to the attacker’s machine, as shown here:
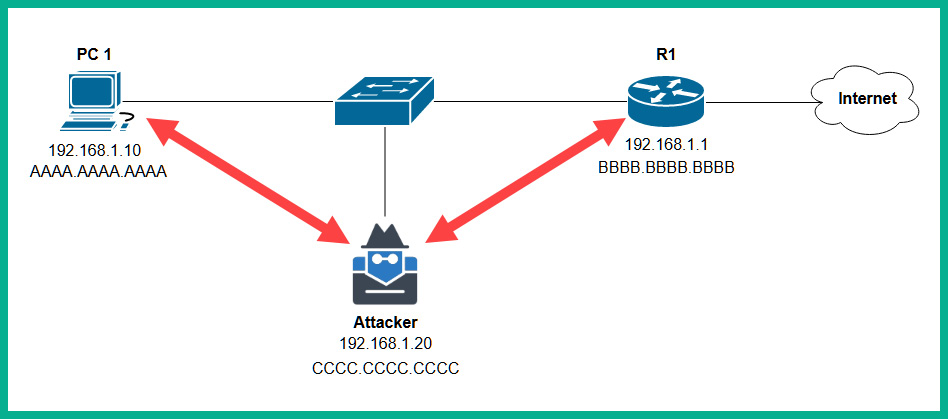
Figure 15.10 – Phase 3
- Lastly, the attacker machine is also configured to forward messages between PC 1 and the router to reduce the likelihood of the messages being intercepted by a hacker on the network.
Network professionals can configure the Dynamic ARP Inspection (DAI) security feature on supported network switches to prevent on-path attacks and prevent devices from sending fake ARP messages on the network. DAI is a Layer 2 security mechanism on network switches that prevents hackers from spoofing their MAC address and performing on-path attacks. With DAI enabled on a Layer 2 network, only legitimate ARP requests and responses are permitted on the network.
DNS-based attack
DNS is a common network protocol that allows devices to resolve a Fully Qualified Domain Name (FQDN) or hostname to an IP address. As you already know, each device on a network has an IP address that allows end-to-end communication between hosts. For instance, if you want to visit www.cisco.com using your computer, a DNS query is sent to your preferred DNS server to request the IP address of the domain name. If the DNS server has the record, it responds to your computer with the IP address of www.cisco.com. Once your computer has the IP address of Cisco’s web server, it will insert the IP address as the destination address of the packet.
The following diagram shows the sequence of events during a DNS query:
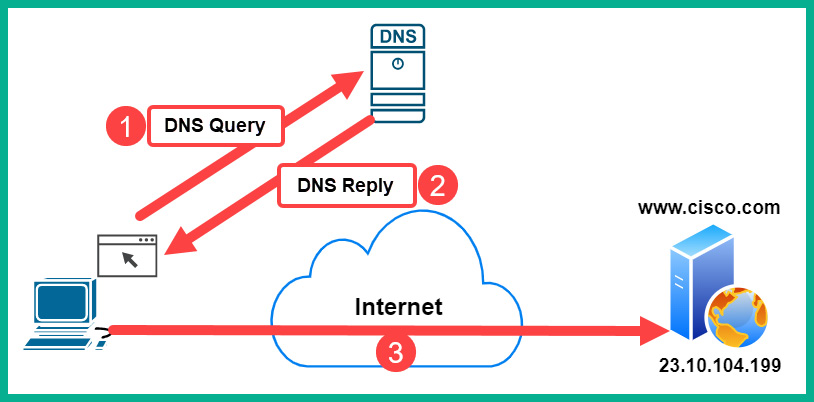
Figure 15.11 – DNS query
Imagine if you needed to remember the IP addresses of each web server on the internet that you wanted to visit; it would be quite challenging to remember these logical addresses. However, DNS servers are like online directory servers that contain a list of well-known domain names and their associated IP addresses. Therefore, your computer does not need a long list of hostname-to-IP address entries stored in a file on the local drive, which requires frequent updates for any changes to be made on the internet. Rather, you can configure your computer to send all its DNS query messages to a trusted, online DNS server on the internet.
The following are some examples of trusted DNS servers on the internet:
- Cloudflare DNS: https://1.1.1.1/
- Quad9 DNS: https://www.quad9.net/
- Cisco’s OpenDNS: https://www.opendns.com/
- Google Public DNS: https://developers.google.com/speed/public-dns
Imagine that a DNS server has been misconfigured with default configurations, a weak password, or maybe the underlying operating system contains known security vulnerabilities and a hacker can exploit those security flaws and gain control of the DNS server. The hacker can perform various types of DNS-based attacks, such as the following:
- DNS poisoning
- DNS hijacking
- Domain hijacking
DNS poisoning is a type of attack that allows the hacker to modify the DNS cache on their victims’ system by sending fake DNS response messages that contain a common FQDN that matches a fake IP address. For instance, if a potential victim visits www.google.com a few times per day, the victim’s system will initially query the IP address of www.google.com by sending a DNS query to their trusted DNS server and cache the response from it. Therefore, if the user wants to visit the same website later, the system does not resend another DNS query but checks the local DNS cache on their computer for the IP address. However, a hacker who sends fake DNS response messages to a victim’s system can modify these entries within the DNS cache. Therefore, if the victim wants to visit www.google.com once more, the system checks the local DNS cache for the IP address and will use the IP address from the fake DNS response, directing the victim to a fake web server on the internet. DNS poisoning attacks are commonly used by hackers to redirect their victims to phishing websites and malware-infected servers on the internet.
DNS hijacking is another type of DNS-based attack that allows a hacker to modify the DNS server configurations on a victim’s device. For instance, the hacker can set up a DNS server on the internet with lots of entries from popular FQDNs, such as www.google.com, www.yahoo.com, www.microsoft.com, and other most-visited websites on the internet, but each FQDN is matched with a fake IP address that is assigned to a phishing website or a malware-infected web server on the internet. In this type of attack, the hacker manages their DNS server and its entries. Since the hacker changes the DNS server settings on the victim’s system, all DNS queries will be sent to the hacker’s DNS server.
Lastly, in a domain hijacking attack, the hacker can take control and ownership of a legitimate domain name and modify the DNS records that are associated with the domain. For instance, if a user purchases a domain name from a trusted domain registrar but does not secure their user account properly, a hacker can attempt to take over the user’s account and their domain name. Once a hacker takes control of a legitimate domain name, they can create, delete, and modify DNS records and ensure users are redirected to untrusted websites on the internet. Additionally, the hacker can transfer the domain name to another domain registrar that’s preferred by the hacker.
VLAN hopping
As you learned in Chapter 9, Routing and Switching Concepts, a Virtual Local Area Network (VLAN) provides a lot of benefits to organizations, such as improving network performance and security, reducing the cost of network infrastructure, and creating smaller broadcast domains without the need for separate dedicated networking devices. As an aspiring network professional, it’s important to understand the security risks that are involved if switch interfaces/ports have been misconfigured with VLAN IDs.
VLAN hopping is a common Layer 2-based attack that allows a hacker to exploit a misconfigured switch port, allowing the hacker to access multiple VLANs simultaneously on the network. For instance, switch ports that are connected to end devices such as computers, servers, and printers are statically configured as access ports. Access ports are used to assign and transport only one piece of data, known as VLAN traffic, except for voice and data VLANs, which are assigned to the same access port on a switch.
The following diagram shows access ports on a switch and their associated VLANs:
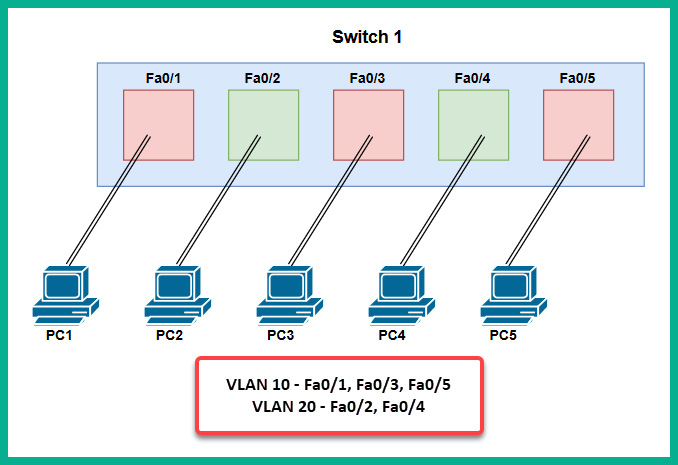
Figure 15.12 – Access ports
When two switches are interconnected, network professionals configure the interface of both switches as a trunk, which allows multiple VLANs to send their traffic between switches, as shown here:
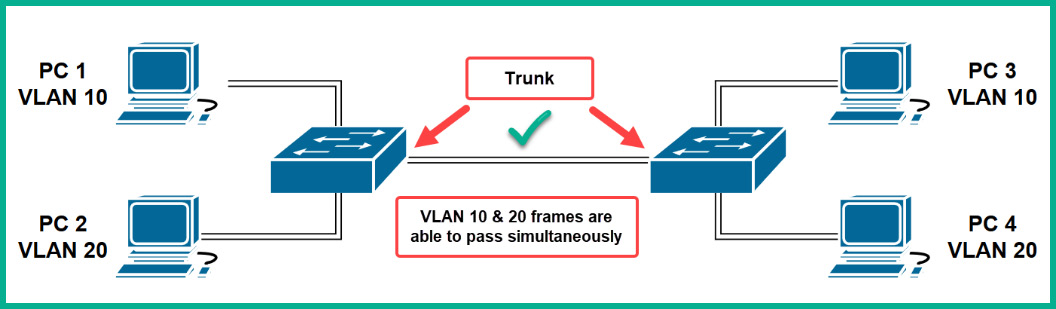
Figure 15.13 – Trunk interfaces
Sometimes, IT and network professionals do not always utilize best practices when configuring switch interfaces. For instance, Cisco switches use the Dynamic Trunking Protocol (DTP) to automatically negotiate the interface mode when another device is connected, regardless of whether the interface becomes an access port or a trunk port. DTP is a Cisco-proprietary protocol that’s enabled by default on Cisco devices. Sometimes, the security vulnerability of this protocol is underestimated by network professionals.
The following are the various modes on a Cisco switch port:
- switchport mode access: This command is used to statically configure the administrative and operational mode as an access port
- switchport mode trunk: This command is used to statically configure the administrative and operational mode as a trunk port
- switchport mode dynamic auto: This command is used to allow the port to convert the operational mode into an access or trunk port
- switchport mode dynamic desirable: This command sets the negotiation mode to actively attempt to convert the port into a trunk port
The following table shows the possibilities if two switches are interconnected with various administrative modes on their ports:
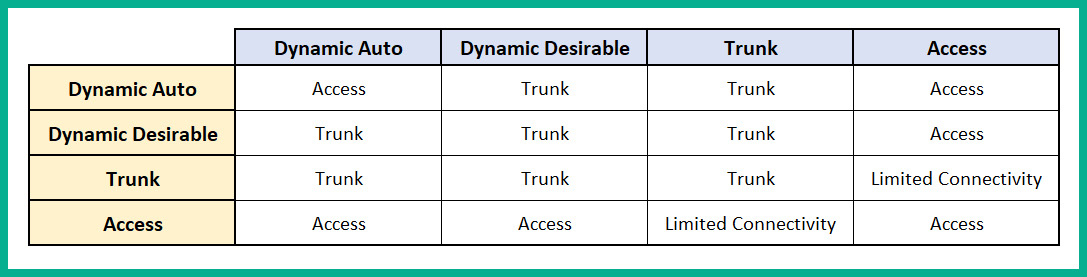
Figure 15.14 – DTP negotiation chart
By default, Cisco switches use switchport mode dynamic auto on all their interfaces. If a hacker connects their attacker machine to a misconfigured switch port, the hacker can inject fake DTP messages into the switch port, causing the interface to flip into a trunk state. This allows the hacker to access all the VLANs on the network.
The following diagram shows an attacker’s machine connected to a misconfigured port on a switch, which means it can convert the port into an unauthorized trunk port:
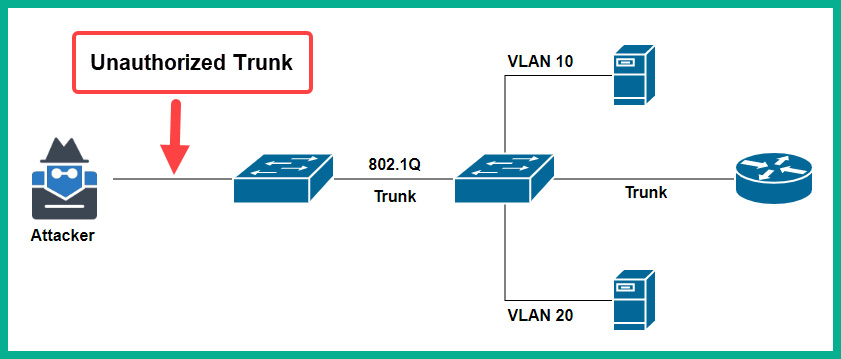
Figure 15.15 – Unauthorized trunk port
To mitigate this type of security vulnerability on switches, you can statically configure an interface as an access or trunk port. Statically configuring the interfaces will prevent the administrative mode from unexpectedly changing. Additionally, network professionals should disable any port negotiation features such as DTP when possible on the entire switch or the port of the device as applicable. On Cisco switches, the switchport nonegotiate command is used to prevent DTP frames from being generated on an interface.
Rogue DHCP
Dynamic Host Configuration Protocol (DHCP) is a common network protocol and IP service that allows network professionals to automatically distribute IP addresses to clients on a network. For instance, when a client connects to a network, they will need an IP address, subnet mask, default gateway, and DNS server configuration that allows them to communicate with other systems. Network professionals can manually assign and configure IP addresses on each device that connects to a network. However, this task can become complex and overwhelming since they need to manually keep track of the IP addresses that are assigned to each device to prevent duplication and human error. Additionally, if the IP addressing scheme within the organization needs to be modified, the network professional will need to manually change the IP addresses on each system accordingly.
Implementing a DHCP server on the network mitigates all these challenges, allowing the DHCP server to automatically distribute available IP addresses from a pool to each client device that connects to the network. Additionally, the DHCP server maintains records of the IP addresses that have been assigned to each client and their lease time. This prevents any IP addresses that have been assigned to devices on the network from being duplicated.
As you may recall from Chapter 6, Exploring Network Protocols and Services, DHCP uses the following messages between a client and DHCP server during a 4-way handshake:
- DHCP Discover
- DHCP Offer
- DHCP Request
- DHCP Acknowledgement
A hacker who has gained unauthorized access to a network can install a network implant as a rogue DHCP server within an organization. The rogue DHCP server will provide a fake default gateway IP address to clients, causing the user’s traffic to be redirected through a machine that’s owned by the hacker. This allows the hacker to intercept packets easily from the victims. Additionally, the rogue DHCP server provides IP addresses for a fake DNS server that’s managed by the hacker, causing victims to visit malware-infected web servers.
The following diagram shows a hacker connecting their rogue DHCP server to a network with a legitimate DHCP server:
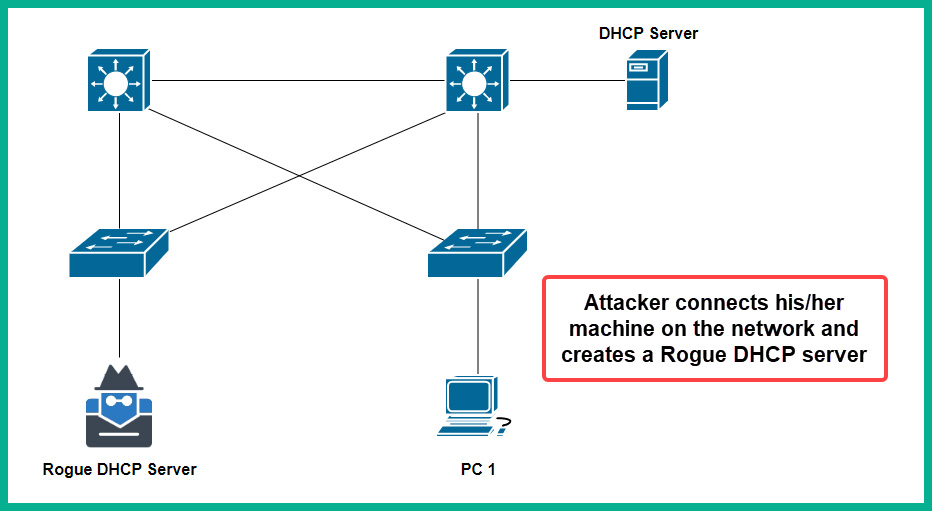
Figure 15.16 – Rogue DHCP server
Typically, the hacker will attempt to compromise the availability of the legitimate DHCP server to prevent it from sending DHCP Offer and DHCP Acknowledgment messages to clients that are requesting IP addresses or attempting to renew their leases. Once the legitimate DHCP server is offline or unavailable, whenever a client sends a DHCP Discover message on the network, the rogue DHCP server will respond with a DHCP Offer, thus providing the unaware client with fake IP addresses for the default gateway and DNS servers.
To mitigate rogue DHCP servers on a network, network professionals commonly implement the DHCP Snooping security feature within Cisco switches. DHCP Snooping sets all the ports on a Cisco switch as untrusted ports to prevent any inbound DHCP Offer and DHCP Acknowledgement messages from entering the network from untrusted sources. Therefore, the network professional configures the interface that is connected to the legitimate DHCP server as a trusted port, allowing the DHCP server to respond to clients on the network.
Password attacks
Whether you’re creating an account on your local computer or an online account on your favorite website, setting a password reduces the likelihood of an unauthorized person gaining access to your account. However, various techniques are used by hackers to retrieve their victim’s user credentials – that is, their username and password. Long ago, passwords were enough to prevent hackers and other malicious users from performing account takeovers and gaining unauthorized access to systems. However, nowadays, hackers can easily retrieve someone’s user credentials using various techniques, such as social engineering the victim into revealing their username and password for their online email account, social media profile, or banking platform.
Typically, when a user is creating a password for their account, their username is commonly stored in plaintext while their password is sent through a hashing algorithm to create a one-way digest (hash) of the password before it’s stored in a database. Therefore, the plaintext password is not stored in the database but the digest (hash) of the password is. Since the digest (hash) is a one-way function, it’s considered to be irreversible, so the owners of the system that store the digest (hash) do not know the actual plaintext password. For instance, the newer versions of the Windows operating system use the New Technology LAN Manager (NTLM) algorithm, which converts the user’s password into an NTLM hash, which is stored in the Security Account Manager (SAM) database on Windows-based operating systems.
Important note
The SAM file is stored in the C:WindowsSystem32config location within Microsoft Windows operating systems.
Systems that are connected to a network, such as servers and networking devices, are susceptible to online password attacks. IT professionals commonly configure servers and networking devices with remote access management using various networking protocols such as Remote Desktop Protocol (RDP) and Secure Shell (SSH) to name a few. While remote access protocols are enabled on servers and networking devices, a hacker who’s on the network can easily perform a port and service scan to determine which systems have remote access services running. This allows the hacker to perform an online password attack on the target with the enabled remote access service, by launching common user credentials over the network to open a service port on the target.
It’s always recommended to use strong and complex passwords, but this is not always practiced by many professionals within various industries, even in the IT industry. Such malpractices often lead to a hacker gaining unauthorized access to a critical system due to missing or default passwords. A good practice is to implement a lockout policy that measures the number of failed login attempts for the username and locks the account as a warning of suspicious activities. For instance, three failed login attempts within a specific period can trigger the policy to lock the account, thus reducing the likelihood of the hacker being able to compromise the user account.
What if a file or folder is password protected? Hackers can perform offline password attacks, which focus on retrieving the password for a password-protected file such as a document that’s on a stored drive, such as a USB flash drive or local storage drive. In an offline password attack, the hacker will need to retrieve the digest or hash value of the password that was used to encrypt or lock the file.
Various tools are created by hackers, security researchers, and cybersecurity professionals to perform online and offline password-based attacks. Some of these tools are designed to perform brute-force attacks, such as attempting every possible combination of a password against the target, while other tools use a dictionary, which is a wordlist containing many possible words, where one of them is likely to be the real password. These wordlist/dictionary files can easily be generated and found on the internet.
Important note
The SecLists repository is well-known within the cybersecurity community as it contains wordlists that contain popular and common usernames and passwords that are used during security assessments: https://github.com/danielmiessler/SecLists.
Hence, IT professionals must configure their systems with password policies to enforce the following:
- Password complexity
- Password expiration
- Password recovery
- Password history
- Password reuse
- Password length
- Disablement
- Lockout
Within large organizations, using the Active Directory Domain Services (AD DS) role within Microsoft Windows Server allows IT professionals to create password policies in the form of a Group Policy Object (GPO) that’s applied to groups, users, and computer accounts. This allows IT professionals to easily manage password policies within the organization.
Having completed this section, you have learned about common network-based attacks and threats that can compromise systems within an organization. Next, you will explore various types of wireless-based attacks that are commonly performed by threat actors.
Understanding wireless attacks
Wireless networking has advanced over the years and become a major convenience for many users within organizations and at home. Wireless networking allows users to connect a mobile device with a wireless network interface card to an access point, which provides access to resources and services on a wired network. Users no longer need to sit in a stationary position while using their computers; they can connect their laptops and smartphones to access points and use the internet and share resources with others on their network.
In a wired network, a hacker will need physical access to the network cables and network devices to install a network implant. However, the radio frequency that’s emitted from an access point covers a small geographic area, such as around a building or house. This allows hackers to sit within the vicinity of a wireless network that belongs to an organization and attempt various wireless attacks, such as the following:
- Rogue access points and evil twins
- De-authentication attacks
Over the next few subsections, you will explore the preceding types of wireless attacks.
Rogue access points and evil twins
Hackers can use their laptops, microcomputers such as a Raspberry Pi, or even microcontrollers such as an ESP8266 to perform wireless attacks on IEEE 802.11 networks. Typically, hackers can create a fake access point using their laptop or Raspberry Pi device to create a wireless network to trick victims into connecting to it. Typically, the Service Set Identifier (SSID) or wireless network name is set to lure users into connecting to the rogue access point. When a victim connects their device to the rogue access point, the hacker can intercept and redirect traffic to malicious websites.
Another common technique is where a hacker can sit outside an organization, perform a wireless network discovery scan to determine the organization’s SSIDs, then set up an evil twin access point within the same SSID as the one used by the organization. This technique simply disguises the fake access point as a trusted access point because it’s broadcasting the same SSID or network name as the organization.
Cybersecurity professionals use various tools and strategies to locate rogue wireless devices, such as unauthorized wireless clients and access points within the vicinity. The following screenshot shows the output of a popular wireless security assessment tool known as Aircrack-ng that’s discovering all wireless networks within the vicinity that are operating on the 2.4 GHz frequency:
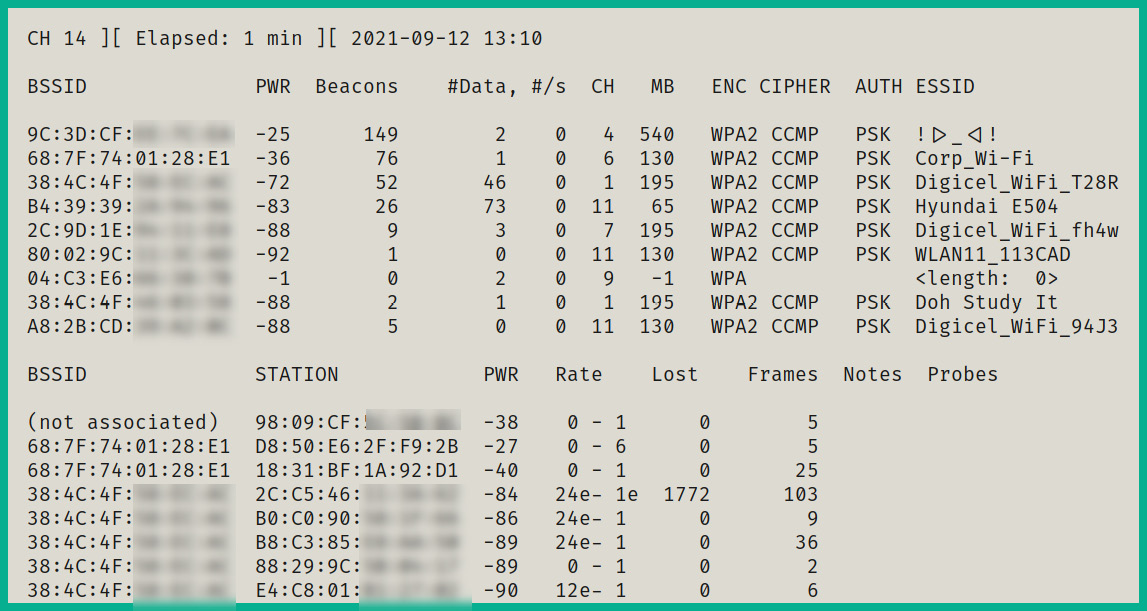
Figure 15.17 – Discovering wireless network
As shown in the preceding screenshot, the upper portion shows the Basic Service Set Identifier (BSSID) of an access point; the BSSID is the MAC address of the device. Additionally, the power level (PWR) indicates the approximate distance between the access point and your device. The Beacons column indicates the number of beacons captured from the access point. You can see the channel (CH), encryption (ENC), cipher, authentication method (AUTH), and the name of the wireless network as the Extended Service Set Identifier (ESSID). The lower region of the screenshot shows which stations (clients) are connected to a specific access point via the BSSID value.
Tip
To learn more about Aircrack-ng, please visit https://www.aircrack-ng.org/.
Aircrack-ng is one of many popular tools within the industry that helps cybersecurity professionals during their wireless security assessments. However, network professionals can use this tool to determine whether a rogue wireless access point is within the vicinity or not.
Deauthentication attacks
As mentioned previously, if a hacker wants to trick the users of an organization into connecting to a wireless network that’s owned and managed by the hacker, implementing an evil twin allows the hacker to configure the same SSID as the organization. However, the employees’ wireless devices that are currently associated with the legitimate access point will not automatically disassociate and join the evil twin wireless network created by the hacker. Therefore, the hacker will need to use a technique to knock off (disassociate) currently associated wireless clients from the legitimate access point.
A hacker can use a deauthentication attack to disassociate (disconnect) wireless clients from the target access point that’s owned by the organization, causing them to associate with the evil twin access point that’s within the vicinity. By default, when wireless clients are disassociated from an access point, they will attempt to re-establish an association with the same access point that they were previously connected to. However, since a disassociation attack focuses on targeting a specific access point based on its BSSID, all previously associated clients will automatically connect to any nearby access points that are broadcasting the same SSID, hence connecting to the evil twin that’s owned and managed by the hacker.
Hackers can launch a deauthentication attack that targets a wireless network indefinitely or sends a few disassociation wireless frames for a few seconds or minutes. Some enterprise wireless access points can detect rogue access points, evil twins, and deauthentication attacks that are occurring within the vicinity. Additionally, cybersecurity professionals can use various tools such as Aircrack-ng and TCPdump to detect wireless deauthentication attacks on their network and the source of the attack.
Having completed this section, you have learned about rogue access points, evil twins, and deauthentication attacks on wireless networks. Next, you will explore social engineering attacks.
Delving into human and environmental attacks
As more people and organizations are using the internet, hackers are always looking for new and sophisticated techniques to trick their potential victims into revealing their user credentials for their online user accounts on popular websites, such as those for e-commerce, payment transactions, and banking. Additionally, hackers are noticing that organizations are investing a lot into fortifying their network infrastructure with countermeasures against common cyberattacks and newly emerging threats. Due to this, companies are implementing a multi-layered approach using security solutions, technologies, people, and strategies to create a Defense in Depth approach.
Social engineering
Seasoned hackers will not attempt to compromise an organization’s internal network while launching the attack from the internet, external to the organization’s network infrastructure. Instead, they will attempt to compromise the network from the inside. Hackers commonly use a technique that does not always require the use of a computer but one that is designed to hack the human brain. Since the human mind does not contain traditional antivirus programs or cyber-threat detection solutions like a computer system does, each person has a consciousness, which allows them to make their own decisions and choices each day. The technique of social engineering allows a hacker to psychologically trick a person into revealing confidential information such as user credentials or performing an action such as downloading a malware-infected file onto their computer.
For instance, a hacker can make a call to the target organization’s customer service department while pretending to be an IT professional within the company. They tell the user they’re from IT, that a virus is currently on the company’s network, and that they are working quickly to contain it before it infects other systems. They also tell the user to quickly download and install an update from a custom URL, before their system gets infected with the virus and all their data is lost permanently. If the user does not pause and think through the situation thoroughly, the user may just install malware created by the hacker to provide backdoor access to the compromised system and network. This is a type of social engineering attack known as vishing; it’s performed over a telephone system where the attacker calls the potential victim while pretending to be someone trustworthy.
A social engineering attack is only successful if the victim reveals sensitive information or performs the intended action that’s expected by the hacker. However, the following are common key elements that improve the success of a social engineering attack:
- Authority: Pretending to be someone with higher authority can convince the potential victim into revealing sensitive information or performing the desired action
- Intimidation: Inflicting fear in a potential victim with the expectation that the person will comply
- Consensus: This element focuses on tricking the potential victim into thinking everyone is doing the same action and that it’s quite normal for them to do the same, which is incorrect
- Scarcity: Implying scarcity involves telling the potential victim there’s limited time to perform an action and if that time runs out, there will be huge consequences
- Urgency: Applying urgency to a situation denotes the importance or priority of the situation
- Familiarity: Creating a familiar situation with the potential victim such as discussing a past mutual experience can help build trust
- Trust: Once the hacker establishes trust with the victim, it’s easy to take advantage of it
Next, you will discover various types of social engineering attacks.
Types of social engineering attacks
In phishing, the attacker sends fake email messages while pretending to be from a trusted organization and is requesting the user to click a link to a malware-infected web server or to a fake website to capture their user credentials. Additionally, malware-infected attachments are sent within phishing emails by an attacker with a message instructing the potential victim to open the attachment.
The following screenshot shows a phishing email that seems to be originating from a popular e-commerce website:
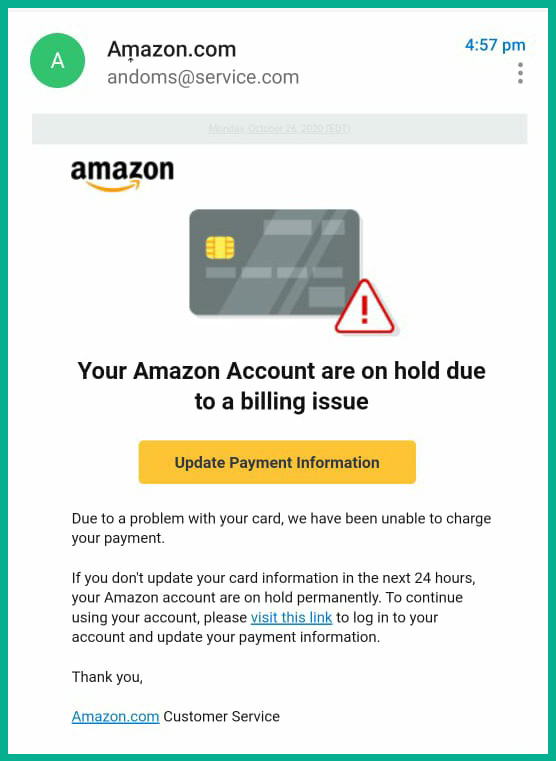
Figure 15.18 – Phishing email
As shown in the preceding screenshot, most of the email message looks trustworthy as the company’s logo, fonts, and colors are used. However, the sender’s details show that the message didn’t originate from Amazon’s domain name – the sender’s name contains an unusual character that looks very similar to an “m,” as shown here:
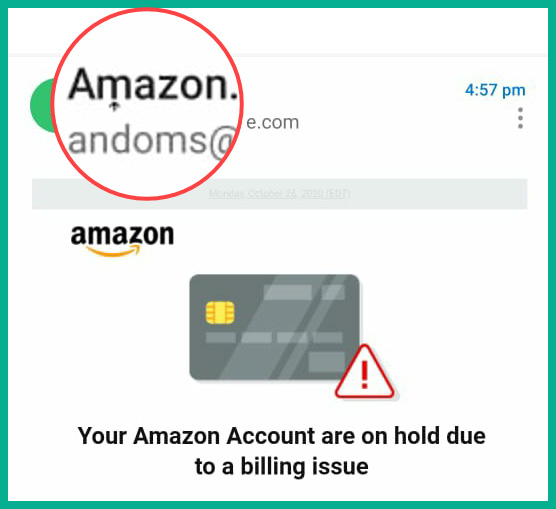
Figure 15.19 – Sender’s name in the phishing email
A spear-phishing attack is designed for a specific target audience or group of people of similar interest, such as all users who are customers of a specific bank. A spear-phishing email is crafted carefully so that it seems to be very believable to anyone who reads it, especially the target audience or group. For instance, the hacker can create a fake website that looks exactly like a specific bank’s website, then create and send an email to all customers of the bank with instructions stating that their passwords need to be changed immediately; they will tell them to click the link provided within the email to change their passwords. A user who clicks the link within the spear-phishing email will be directed to a web page that looks exactly like their bank’s website. When they enter their user credentials on the fake website, they will be saved for the hacker to use, and the user will be redirected to the real website of the bank. Spear-phishing attacks are usually more successful than regular phishing emails because they are designed to be more believable.
Whaling is another type of phishing attack that is used by hackers to target the high-profile employees of an organization, such as the Chief Executive Officer (CEO). The high-profile employees of an organization usually have lots of authority within the company and a lot of technical privileges assigned to their user’s accounts on the network. For instance, if a hacker were to trick a CEO into providing their user credentials for the online banking platform, the hacker can sell money. If the hacker can gain the user credentials of the CEO domain account within the company, the hacker can access the email mailbox of the user, read confidential messages, and perform administrative actions on their computer.
The following are additional types of social engineering attacks:
- Vishing: This type of social engineering attack is performed over a telephone system where the attacker calls the potential victim while pretending to be someone from a trusted organization.
- Smishing: This type of social engineering attack is performed by sending the potential victim a phishing message via Short Message Service (SMS).
- Tailgating: This is where an unauthorized person attempts to gain access to a secure area within a company when an employee does not close a door properly, thus allowing the unauthorized person to tail the employee through the secure area. With tailgating, no one knows that the malicious actor “slipped” into the secure area through a door that was slowly closing.
- Piggybacking: With piggybacking, someone from the secured area holds the doors open for the malicious actor to help them. Often, the malicious actor will have their hands/arms full of boxes or carrying something.
- Shoulder surfing: This technique is commonly used by people who are looking over a user’s shoulder while they are entering confidential or sensitive data into their computer. Shoulder surfing involves the attacker intending to gain the user credentials of the potential victim.
- Dumpster diving: Disposing of documents or devices that contain sensitive and confidential information can lead to impersonation. Some hackers will check a person’s trash for any documents or devices for data and attempt to use that data for identity theft or to gain unauthorized access to their online accounts.
Having completed this section, you have learned about the fundamentals of social engineering attacks and various types of attacks. Now, let’s summarize this chapter.
Summary
In this chapter, you have explored common types of network-based attacks such as DDoS, botnets, on-path, and even DNS-based attacks. Additionally, you learned how hackers use various techniques to trick users on a wireless network into connecting to a rogue access point that’s owned and managed by the hacker. Lastly, you discovered how hackers can use social engineering to trick a person into revealing sensitive information or performing an action.
I hope this chapter has been informative for you and is helpful in your journey toward learning networking and becoming a network professional. In the next chapter, Chapter 16, Implementing Network Security, you will learn how to implement various network security solutions to mitigate various types of cyberattacks and threats.
Questions
The following is a short list of review questions to help reinforce your learning and help you identify areas that may require some improvement:
- Which of the following types of attacks focuses on compromising the availability of a server?
A. On-path
B. Phishing
C. DDoS
D. All of the above
- Which type of network-based attack is needed to intercept communication between two or more devices?
A. VLAN hopping
B. On-path
C. DNS
D. DHCP
- Which of the following attack is needed for a MiTM attack to be successful?
A. Phishing
B. Rogue DHCP server
C. VLAN hopping
D. ARP poisoning
- Which of the following attacks best describes a hacker modifying the DNS cache on their victim’s system by sending fake DNS response messages?
A. DNS poisoning
B. DNS hijacking
C. DNS flooding
D. Domain hijacking
- Which of the following allows a hacker to gain unauthorized access to another VLAN on the network?
A. VLAN access port
B. VLAN hijacking
C. VLAN hopping
D. All of the above
- Which of the following messages are blocked on untrusted ports when DHCP Snooping is enabled on a network? (Choose two)
A. DHCP Offer
B. DHCP Request
C. DHCP Acknowledgement
D. DHCP Discover
- Which type of attack can a hacker perform to force wireless clients to disconnect from an access point?
A. Rogue access point
B. Brute-force
C. Disassociation
D. Deauthentication
- Which of the following attacks is performed using a telephone to trick a user into installing a malware-infected file?
A. Social engineering
B. Vishing
C. Smishing
D. Spear-phishing
- Which of the following attacks allows a hacker to take control of a trusted domain name on the internet?
A. DNS poisoning
B. DNS hijacking
C. DNS flooding
D. Domain hijacking
- Which technique does a hacker use to change their identity on a Layer 2 network?
A. Hostname spoofing
B. MAC spoofing
C. IP spoofing
D. All of the above
Further reading
To learn more about the topics that were covered in this chapter, check out the following links:
- Network Attacks and Network Security Threats: https://www.cynet.com/network-attacks/network-attacks-and-network-security-threats/
- Wireless attacks and mitigation: https://resources.infosecinstitute.com/topic/wireless-attacks-and-mitigation/
- Social engineering: https://www.techtarget.com/searchsecurity/definition/social-engineering
