
Part I: Code and Cryptogram Strategies
26
Caesar / Shift Ciphers often use a keyword. In this case, you
write a word at the start of the cipher, and then you write the
remainder of the alphabet in order. Figure 2-3 shows you an
example; the keyword here is SPHINX.
Figure 2-3: A Caesar / Shift Cipher with SPHINX as the keyword.
If the keyword has repeating letters, only the first instance of
each letter is used (so LONDON TOWN would be written as
LONDTW).
A Caesar / Shift Cipher with a keyword often ends up coding
letters as themselves by the end of the alphabet, so it’s
common for X = X, Y = Y, and Z = Z, unless these letters appear
in the keyword. This coding is an unusual feature of these par-
ticular ciphers.
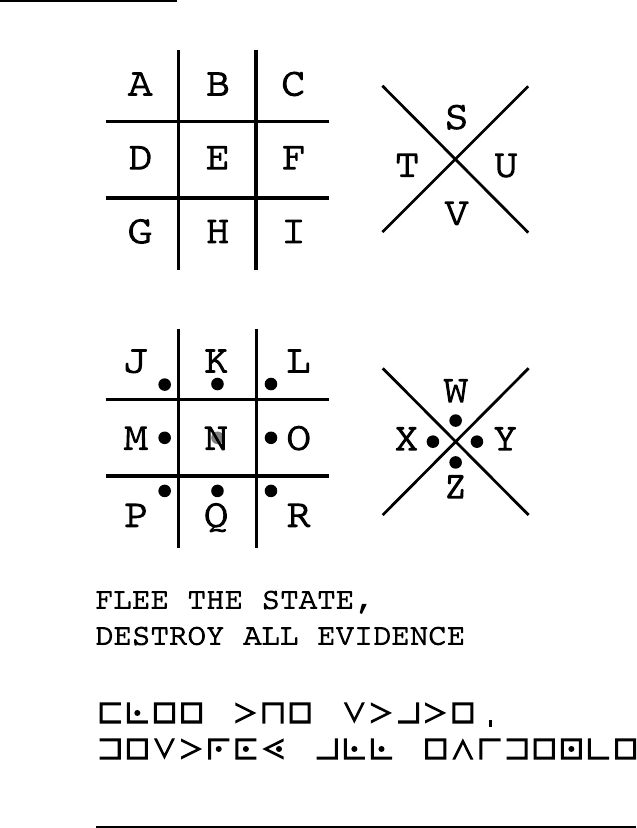
Masonic Ciphers
Chapter 8 contains a bevy of ciphers used by Freemasons
over the centuries. One is the Masonic Cipher, which is also
known as the Pigpen Cipher (because the grid looks like
a pigpen — you be the judge!). We also present you with
the Cypher of the Rose Croix, and other special substitution
ciphers made with Masonic symbols and alphabets, such as
Malachim and Celestial.
The Masonic Cipher is a variety of substitution cipher — each
letter is substituted by a symbol. If you use this cipher to
send and receive messages, you can create the code symbols
in a way that makes it very easy to remember how to con-
struct and re-create the key. See Figure 2-4 for an example of a
Masonic Cipher.
Chapter 2: Simplifying Codes and Cryptograms
27
Figure 2-4: An example of the Masonic Cipher.
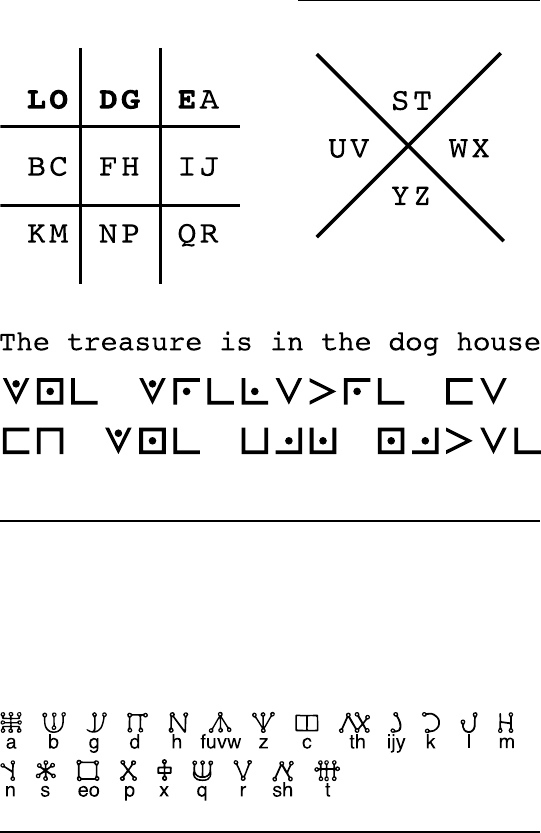
You can also use keywords within a Masonic Cipher to further
complicate matters. In this format, pairs of letters are written
into each location, as in Figure 2-5. First write the keyword (in
this case, LODGE) and then write the remainder of the alpha-
bet into the grids in letter pairs. The second letter in each pair
is enciphered with a dot.
Part I: Code and Cryptogram Strategies
28
Figure 2-5: A Masonic Cipher with the keyword LODGE.
Some 19th century Masons used magical writing systems, such
as Celestial and Malachim. These symbol systems are based on
Hebrew, and they generally represent sounds rather than fixed
letters. Figure 2-6 includes a table of the English letters and
sounds that most closely correspond to the Malachim symbols.
Figure 2-6: The phonetic Malachim alphabet.
To solve a Malachim or other special font Masonic Cipher, you
occasionally have to choose between two or more sounds for
a single symbol. Generally the two letters are closely related in
pronunciation, such as v and w. The encryption is a phonetic
encryption rather than a straight symbol substitution. (The
Malachim letter we mark as x should technically be ts or tz.
We use x for the sake of utility — in English you simply need x
more than tz.)
Chapter 2: Simplifying Codes and Cryptograms
29
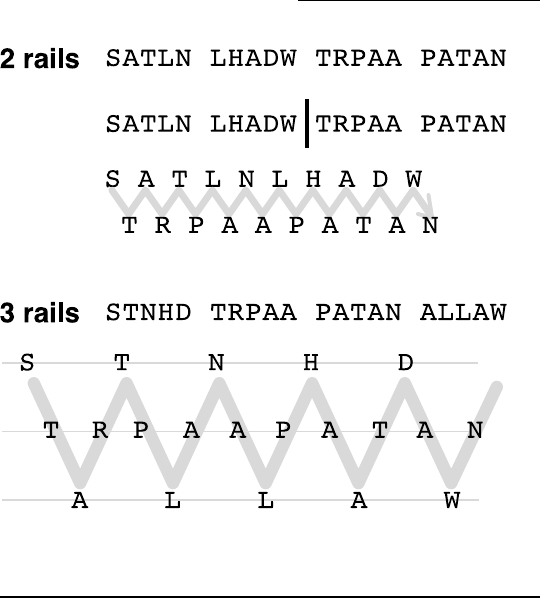
Rail Fence Ciphers
A Rail Fence Cipher is a transposition cipher. The letters in
the message aren’t changed, but their positions are altered.
Unless you know the encryption method, these ciphers can be
very difficult to crack. You can find them in Chapter 9.
To decipher these codes, you need to know the number of
rails. With a two-rail cipher, you simply divide your ciphertext
into halves, and then write the second half underneath the
first half, slightly offset. Then you can read off the plaintext
by alternating between the top and bottom rails of your
letter fence. Figure 2-7 shows you an example of a two-rail
cipher.
For ciphers with more than two rails, the process is more
complicated because you have to figure out how many letters
to have in each rail to crack the code. The number of “points”
of the zigzag in the top row is the most important thing to
figure out.
To solve these ciphers, try drawing a zigzag onto a lined piece
of paper with a colored pencil or highlighter pen. Then write
the ciphertext from left to right and top to bottom in order,
following the zigzag path. The horizontal lines on your page
will help you keep everything lined up (so if you aren’t using
lined paper, draw some horizontal lines!). These lines are
the rails.
A three-rail cipher is drawn over three lines, a four-rail cipher
is drawn over four lines, and so on. Figure 2-7 shows two
examples of Rail Fence Ciphers.
If a message has too few letters to fit into the chosen rail pat-
tern (a fairly common occurrence) dummy letters are added
to the end of the message to pad it out. So don’t be put off if
an X or other random letter or two appears at the end of your
message.
Draw the zigzag so the last section is just coming up to —
but stops just short of — another point. Refer to the way the
zigzags are drawn in Figure 2-7.
Part I: Code and Cryptogram Strategies
30
Figure 2-7: Two- and three-rail Fence Ciphers of the message
START PLAN ALPHA AT DAWN.
The following sets of steps show you the way to crack the
bigger, and harder, Rail Fence Ciphers.
For a three-rail cipher:
1. Count the letters in the cipher.
2. Divide the letters into four equal parts.
3. Draw your zigzag with a number of points on the top
rail equal to
1
⁄4 of the total letters.
4. Place your letters across the grid. One quarter go on
the top rail, half fit on the middle rail, and the final
quarter fit along the bottom rail.
For a four-rail cipher:
1. Count the letters in the cipher.
2. Divide the letters into six equal parts.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
