
Chapter 2: Simplifying Codes and Cryptograms
31
3. Draw your zigzag with a number of points on the top
rail equal to
1
⁄6 of the total letters.
4. Place your letters across the grid. One sixth go on the
top rail, a third fit on the second rail, the next third
fit on the third rail, and the final sixth fit along the
bottom rail.
For a five-rail cipher:
1. Count the letters in the cipher.
2. Divide the letters into eight equal parts.
3. Draw your zigzag with a number of points on the top
rail equal to
1
⁄8 of the total letters.
4. Place your letters across the grid. One eighth go on
the top rail; a quarter fit on each of the second, third,
and fourth rails; and the final eighth fit along the
bottom rail.
The Rail Fence Ciphers in this book have all been designed to
fit neatly into the two-, three-, four- and five-rail patterns, with
no pesky extra letters. If you try to apply this solving method
on Rail Fence Ciphers elsewhere, you may be out by one. You
can normally sort it out by trial and error.
Rail Fence Ciphers sometimes include the spaces between
words as blank characters in the cipher. We don’t have
this variety in this book, but you may come across them
elsewhere.
Keyboard Ciphers
Keyboard Ciphers are created with some of our favorite bits
of technology — our cellphones and computer keyboards!
These puzzles are in Chapter 10.
Text Message Ciphers
Text Message (or SMS) Ciphers make use of your phone.
Multiple letters occupy each number key on a phone; the
2 key has the letters ABC written on it, for example.
Part I: Code and Cryptogram Strategies
32
These letters have long been used to create memorable
phone numbers. You know the sort of thing: “Call 1-800-MORE-
COFFEE now for more coffee!” This is a simple letter-to-number
encryption of the phone number 1-800-6673-263333.
In this book, however, we go in the opposite direction, from
number to letter.
You’re probably already all too familiar with using your cell-
phone keypad to type text messages. Most phones use predic-
tive text now, in which the phone’s software guesses at what
you mean when you input a certain number sequence. This
guess is based on common words used in English.
For example, to type HOME, you press 4663. However, this
combination of number keys also encodes the words GOOD,
GONE, HOOD, HOOF, and several less-common words.
The fiendish Text Message Ciphers in this book take advan-
tage of this ambiguity. They’re simply a collection of numbers,
made to type a secret message. Your job is to figure out what
the intended words are!
Look for common patterns, such as 843 (THE), 263 (AND), and
8438 (THAT) within these ciphers.
Because each number can represent three or four different
letters (unlike in a substitution cipher, where each symbol
represents a single letter), you have to try several letter
options for each word.
The context of the message helps you decipher these puzzles.
For example, with the message 7323 8447 2665, the first two
words are pretty easy to pin down: READ THIS. However,
2665 is more problematic; it can be COOL, COOK, or BOOK.
Obviously, the first two words indicate that the correct mes-
sage is READ THIS BOOK, because READ THIS COOL doesn’t
make sense. (Or does it? Maybe we can start a new fad here!)
Use your cellphone to help crack these codes. Start a new
text message (that you won’t send to anyone), and type in the
numbers to see which words are options.

Chapter 2: Simplifying Codes and Cryptograms
33
Be careful, though — the phone’s dictionary is very limited.
Foreign words, unusual words, and proper nouns generally
aren’t included.
Typewriter Ciphers
Humans have a long history of using “code machines” to physi-
cally create a cipher. Strips of paper wrapped around rods
(scytales) and pivoting cardboard circles for offsetting alphabets
are just a couple of these devices, and you can go right up to the
incredibly complex Enigma machine used during World War II,
not to mention modern computer encryption methods.
In this book, some ciphers use a typewriter or computer
keyboard as the method of encryption. The concept is quite
simple — you simply shift which key you press by a set
movement.
For example, you may type your message by using the keys
one up and to the left of your intended letters. Or perhaps you
move one key down and to the right. Check out Figure 2-8 for
examples of these Typewriter Ciphers.
Punctuation is often found as one of the encrypted characters
in these ciphers, and uppercase letters can be encoded differ-
ently from lowercase letters. So if you see a message that has
an odd mix of numbers, letters, and punctuation, you may be
looking at a keyboard code.
Figure 2-8: An “up and left” shift encodes R into 4, and a “down and right”
shift encodes P into the character ;.
Assorted Ciphers
You can find a ton of different codes and ciphers out in the
world; we only scratch the surface in this book! Chapter 11 is

Part I: Code and Cryptogram Strategies
34
our chance to broaden the field and show you a range of codes
and ciphers that aren’t anywhere else in the book. We include
the Atbash Cipher, Caesar Box Cipher, Twisted Path Box
Cipher, Newspaper Codes, and a few Columnar Transpositions
(described in the later section on Double Level Puzzles).
Atbash Ciphers
The Atbash Cipher is one of the oldest and simplest ciphers.
It was originally used with the Hebrew alphabet. You simply
wrap the alphabet around on itself, so A = Z and Z = A, B = Y
and Y = B, and so on. Figure 2-9 shows you what it looks like.
Figure 2-9: Atbash Ciphers wrap the alphabet around on itself.
Caesar Box Ciphers
The Caesar Box Cipher is another cipher used by Julius
Caesar. It’s a transcription cipher rather than a substitution
cipher, which means the letters in the message aren’t altered,
but their positions are muddled up.
The Caesar Box Cipher works best for messages with a square
number of letters (for example, 3 x 3 = 9, 4 x 4 = 16, 5 x 5 = 25,
and so on). You can add null letters to the end of a message
to pad it to the correct length, or the grid can be a rectangle
rather than a square.
The plaintext is written down the columns of the grid, and
then read off in rows. This forms the ciphertext. Figure 2-10
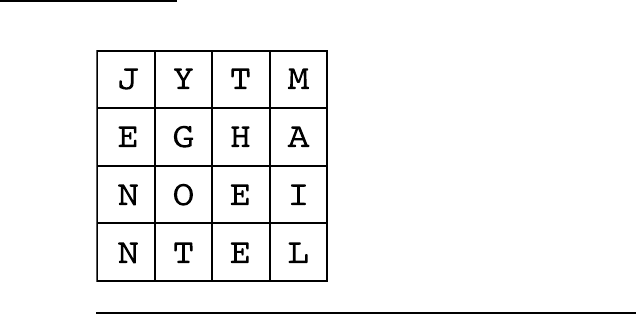
shows the message JENNY GOT THE EMAIL.
Then the letter groups are read off in rows, resulting in an
encoded message of JYTM EGHA NOEI NTEL.
To crack a Caesar Box Cipher, first figure out the number of
letters.
Box ciphers are sometimes presented with letters in groups,
which is also a hint as to the grid size. For example, if you see
seven groups of seven letters in the ciphertext, you need to
draw up a 7 x 7 grid.
Chapter 2: Simplifying Codes and Cryptograms
35
Figure 2-10: A Caesar Box Cipher with a 4 x 4 grid.
If the letters haven’t been presented in groups, you may need
to count them to get the total.
If you end up with 25 letters, draw up a 5 x 5 box. Write the
cipher in, row by row, and then read down the columns to dis-
cover the message.
Some box ciphers are laid out in rectangles, so if you have 24
letters, for example, you may be looking at a 6 x 4 grid.
Twisted Path Ciphers
Twisted Path Ciphers are transcription ciphers that are a
variation on the Caesar Box Ciphers. Instead of reading off the
message in columns from top to bottom, the message is writ-
ten in a path inside the box. The path may be a spiral (clock-
wise or counterclockwise), or up and down the columns, or in
a reverse order. Figure 2-11 shows you a few examples. Note
how each cipher reads quite differently, although they all
encode the same message.
Newspaper Codes
In distant days in England, sending a letter was quite expen-
sive, but posting a newspaper was free! Clever people soon
figured out a way to send news to friends and family, free of
charge. They used a pin to poke a tiny hole above or below
letters on a newspaper page. By holding the newspaper up to
the light, it was easy to see the pin-pricked letters and read
the hidden message.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
