Chapter 2
Simplifying Codes and
Cryptograms
In This Chapter
▶ Finding out how to solve the puzzles in this book
▶ Investigating letter frequency analysis
P
eople have been hiding their messages from prying eyes
for millennia. Their methods became more complex as
time went on, and encryption is still a vital part of modern life.
You can read more about the history of codes and ciphers in
Chapter 1.
Ingenious people have devised many ciphers over the years,
and no doubt there are more ciphers to come! In this book we
include several different types of ciphers and several variations
on these types. We hope you enjoy this selection!
The ciphers in this book are
✓ Cryptograms with Letter Substitutions (Chapter 4)
✓ Cryptograms with Number Substitutions (Chapter 5)
✓ Cryptograms with Symbol Substitutions (Chapter 6)
✓ Caesar / Shift Ciphers (Chapter 7)
✓ Masonic Ciphers (Chapter 8)
✓ Rail Fence Ciphers (Chapter 9)
✓ Keyboard Ciphers (Chapter 10)
✓ Assorted Ciphers (Chapter 11)
✓ Anagrams and Other Cryptic Riddles (Chapter 12)
✓ Double Level Puzzles (Chapter 13)
Part I: Code and Cryptogram Strategies
22
We also include a very handy collection of hints in Chapter 14.
If you’re really stuck, look there before giving in to the allure
of the answers (Chapter 15).
This book is a bit unusual, too, because in Chapter 3 we pres-
ent you with three conspiracy stories, set in different times in
American history. These stories have been heavily censored
by the government — your task is to decipher the puzzles
in the book in order to gain access to these secret files. All
the puzzles are numbered carefully so you can easily see
which puzzle goes where.
If you prefer to do puzzles for fun without worrying about
solving the conspiracy stories, that’s perfectly fine too, of
course! We include a lot of cryptograms that aren’t related to
the Chapter 3 stories, and the story-related ciphers are enjoy-
able to crack even if you don’t solve the conspiracy.
Considering Cryptography Terms
Although they’re often used to mean the same thing, strictly
speaking a code is quite different from a cipher. Consider
these definitions:
✓ A code is a whole new language. Entire words are
encoded by a number, symbol, or another word. For
example, CONSPIRACY may be encoded as 32, u, or
falcon. A code book is required to crack a code, and it
basically functions as a dictionary of the code’s language.
Codes are very hard to crack, but the need for code books
is their weakness — if a code book falls into the wrong
hands, your code is useless and your plans are discovered!
✓ A cipher is a way of rearranging or replacing the letters
in a message. In substitution ciphers, each letter of the
alphabet (and sometimes the numbers and punctuation)
are replaced by another letter, number, or symbol. The
letter D may be enciphered as R, 9, or ✲, for example.
Ciphers can be easier to crack than a code, but they’re
also more secure. You can often memorize the key to
a cipher, so you don’t need written instructions. That
eliminates the major security failing of codes. Ciphers

Chapter 2: Simplifying Codes and Cryptograms
23
are also easy to change regularly, which is an important
strategy if you really rely on encryption (as opposed to
those of us who just enjoy the mental workout for fun).
Although we use the words code, decode, and encode in this
book interchangeably with cipher, decipher, and encipher, rest
assured that all the puzzles in this book are ciphers.
Before you dive into the puzzles, familiarize yourself with a
few terms for this book:
✓ Plaintext is the secret message that you need to discover;
the English is written out plain so anyone can read it.
You typically see plaintext written in lowercase letters,
especially within encryption keys.
✓ Ciphertext is the encrypted message. You usually see
ciphertext written in UPPERCASE letters.
✓ A keyword is a vital, or key, word or phrase that’s used to
further complicate a cipher and helps to decode a cipher.
✓ In a substitution cipher, the letters of the alphabet are sub-
stituted with other letters, numbers, or symbols.
✓ In a transposition cipher, the letters of the message are
rearranged into a new order according to a set pattern
instead of being changed into other symbols.
✓ A pattern word is any word with repeated letters and is
invaluable for cracking ciphers. PEOPLE and THAT are
two pattern words, having the pattern 1 2 - 1 - 2, and
1 - - 1, respectively. 1 and 2 refer to the repeating code
letters in an encrypted word.
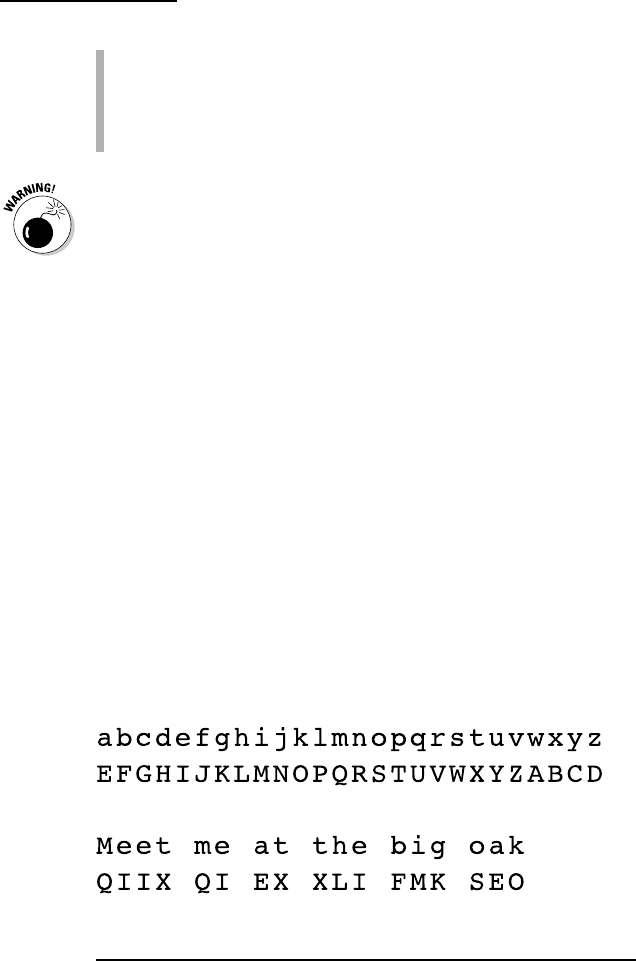
Figure 2-1 gives you an example of plaintext (lowercase) and
ciphertext (uppercase) encryption, with a keyword of NEW
YORK. The rest of the alphabet, minus the letters in NEW
YORK, is filled in after the keyword.
Figure 2-1: An example of plaintext and ciphertext encryption.
In this particular cipher, the message LEAVE TOWN would be
enciphered as FONTO QIUH.

Part I: Code and Cryptogram Strategies
24
Solving the Ciphers in This Book
In this section we take you through each puzzle type in this
book and give you a few handy strategies for solving them.
Cryptograms with Letter, Number,
and Symbol Substitutions
In any substitution cipher, each letter of the alphabet is sub-
stituted for other symbols. These symbols may be letters,
numbers, or symbols.
You can work with other complex variations (in which one
message has multiple encodings, for example), but in this book
we concentrate on simple substitution ciphers. Chapter 4 con-
tains letter substitutions, Chapter 5 has number substitutions,
and Chapter 6 has symbol substitution ciphers.
When approaching a substitution cipher, here are some
basics to keep in mind:
✓ Use a pencil and eraser!
✓ Look for single-letter words. They’re almost always A or I.
✓ Count how many times each symbol appears in the cipher,
and write it down. The most frequent letter is likely to be
E — but T, O, and A are also good contenders.
✓ A letter is never encoded as itself: D = D for example.
(Caesar Ciphers with keywords are a rare exception to
this rule.)
✓ Two-letter words almost always have one vowel and one
consonant.
✓ Look for the two most common three-letter words: AND
and THE.
✓ Look for pattern words, especially THAT, which is the
most common four-letter word. (See the previous section
for a definition of pattern words.)
✓ Pencil in your guesses, and look for clashing letter com-
binations (for example, you can be sure that KVC isn’t the
start of any English word).
Chapter 2: Simplifying Codes and Cryptograms
25
✓ After writing a decrypted letter above its cipher, read
through the whole encrypted message and write that
letter wherever the cipher letter appears in the message.
For example, if you find that K = A, go through the cipher-
text and write an A over every K.
Seeing all the instances of one letter in a ciphertext is sur-
prisingly difficult to do. That’s probably because you read
by seeing the whole shape of a word; most people don’t read
by looking at each individual letter in succession. So read
through the ciphertext several times, and be prepared to
keep finding instances popping out at you!
For more hints on how to crack substitution ciphers, read the
later section about letter frequency analysis.
Caesar / Shift Ciphers
A Caesar / Shift Cipher was widely used by the Roman
emperor Julius Caesar. Chapter 7 is the place to go for
these puzzles.
With a Caesar / Shift Cipher, all the letters in the alphabet are
shifted by a set amount (such as +5, or –2). To create a
Caesar / Shift Cipher, you write the cipher alphabet in order
under the plain alphabet, wrapping it around from Z to A until
all letters are assigned. Figure 2-2 shows you an example of a
Caesar / Shift Cipher.
Figure 2-2: An example of a Caesar / Shift Cipher with a +4 shift.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
