16
An Enhanced Security of Women and Children Using Machine Learning and Data Mining Techniques
Nanda R. Wagh* and Sanjay R. Sutar
Information Technology, Dr. Babasaheb Ambedakar Technological University, Lonere, India
Abstract
This chapter studies the security framework for women and children, which permits prompt reactions in any provocation in broad daylight puts and proposed work. Women everywhere all over the world are confronting untrustworthy physical badgering and Children can’t be left unattended at a get-together or outside the home. Our undertaking tackles both issues. A convenient gadget that will have a weight switch. When an attacker is going to assault the women/kid or when they detect any frailty from a more interesting, he/she would then be able to squeeze the gadget by pressing or packing it. In a split second, the weight sensor detects this weight, and a customary SMS, with the casualty’s area, will be sent to their folks/gatekeepers PDA numbers put away in the gadget while buying it, trailed by a call. On the off chance that the call is unanswered for a delayed time, a call will be diverted to the police, and a similar message will be sent. The principle highlight of our framework is less reaction time will be required for helping the person in question.
Keywords: Child security, women security, security framework, artificial intelligence
16.1 Introduction
Since the most recent couple of decades, the status of women in India has been experiencing part of changes. To remain part of quick life, women likewise work a ton to endure and bolster their family. They work at better places like BPOs; call focuses, IT firms, and thus numerous spots like it. Yet, even the present women are as confronting numerous social difficulties in India and are frequently casualties of rough violations. Thomson Reuters had said that as per the worldwide survey, India is indeed the fourth greatest visibly terrible nation in the world and perhaps the most troubling nation for women among these 20 rising nations. Step by step, the attacks on women are increasing, and often the females are not prepared to take their flexible and toggle up to the police; this system would allow women in that kind of situations to learn about offenses and, additionally, to send their particular area to the police to close their heads. The Delhi Nirbhaya incident that brought the whole nation in motion was the strongest catalyst for this initiative. This was extremely important that the women needed a shift. Females are battling against men in every viewpoint of the community in the present predicament. Females are contributing 50% to the development of the nation. In either case, women are afraid to get these sorts of female harassment incidents to extend point by point. It also is necessary to ensure the wellbeing of women. Its mission is based around for a safety system that is structured primarily aim of providing women and children with real policing or wellbeing so that they can never feel helpless in the face of these anxiety issues [2–4].
16.2 Related Work
16.2.1 WoSApp
WoSApp [1] furnishes women with a dependable method to put a crisis call to the police. The client can, without much of a stretch, trigger the calling capacity by a straightforward cycle emergency signal screen. The framework helps women at the hour of emergency. This application additionally guarantees the inquiry concerning the client’s area and whom to contact. The client should shake her telephone, and a crisis message with her GPS organizes and preselected crisis contact will be sent to the police.
16.2.2 Abhaya
This System utilizes GPS for distinguishing the area of the individual in a tough situation. The framework contains modules that incorporate area following and enlistment of clients and their crisis contact list. It improves mostly in the live follow-up of the region of the accident using GPS across several of the engaged contacts that receive an alert from both the core device. As the root gadget area quickly changes, the GPS recognizes the specific area. The client must tap on the crisis button then the current precise area will be sent to the closest police headquarters and loved one’s part [3].
16.2.3 Women Empowerment
Different existing applications are explicit just for crisis call when they might be in danger, a few applications contain total assets for survivors of aggressive behavior at home, just as an approach to get help when you need it [10]. In any case, this Application will give data about aggressive behavior at home counteraction laws, wellbeing tips for women. To utilize the versatile Application, the client needs to enroll. All data of the client is paired in the cloud information base. The GPS framework on the advanced mobile phone of the client will find an accurate situation of the person in question. The GPS arrangement of portable will find a definite situation of the person in question. The Emergency Call System helps the casualty sends messages to the police and relatives that content area and time with this versatile Application makes an impression on pre-chosen contacts when the force catch of the telephone is pushed twice. The message contains the client’s GPS area and is conveyed at regular intervals with refreshed directions [11].
16.2.4 Nirbhaya
This portable Application communicates something specific with the client’s GPS directions to a rundown of crisis contacts when a catch on the application screen is contacted. The directions are refreshed and hit with each 300 m change in the area. Furthermore, it is complimentary and open-source, permitting upgrades and customizations to be made effectively for fast replication of the Application in different wards [15].
16.2.5 Glympse
This application is possible for the client to share areas utilizing GPS following continuously with loved ones. This Application needn’t bother with any signup and needn’t bother with any contact to oversee [17, 22, 25].
16.2.6 Fightback
This application is created by the Mahindra group. In prior days, this Application was not complimentary; the client needs to make up for this Application. This Application makes an impression on your companion or contacts that “Client is in a tough situation” utilizing Email, GPS, SMS, and GPRS. This application chips away at portable, which upholds Android Java Programming. The Application will likewise send SMS of area and Map [21].
16.2.7 Versatile-Based
Women Safety Application Many portable based application have been created for women’ security like VithU application, Stun firearm application, Fightback application, and so on. These are the crisis application produced for women’s security [14, 18, 19, 23].
16.2.8 RFID
GSM granted younger students a security framework. This framework expects to give complete security to younger students. Range and Obstacle recognition and mishap identified sensors are embedded on the front surface of the transport to evade impact with another vehicle on the road. Every understudy is labeled with an exceptional code. Two counters were utilized at the passageway and leave the area of the transport. Remote correspondence innovation (IEEE 802.4.15) is utilized to illuminate the status regarding the transport to the school staff and head [24].
16.2.9 Self-Preservation Framework for Women With Area Following and SMS Alarming Through GSM Network
This framework contains a stunning instrument to deliver non-deadly electric stun in crisis circumstances to stop the aggressor when the trigger key on the band is pressed [26].
16.2.10 Safe: A Women Security Framework
This framework comprises three principal segments, specifically an android application, a fundamental gadget, and a compact camera. Together these gadgets will fill in as a powerful security framework primary gadget which comprises of Raspberry Pi incorporated GPS shield alongside physically work pepper splash. Android application can be utilized in two potential manners by which it will either utilize a telephone GPS framework, or it will utilize GPS arrangement of fundamental gadget to catch location [28].
16.2.11 Intelligent Safety System For Women Security
In this paper, they portray at whatever point we feel perilous, she will press the catch of gadget, that occasion will be perceived by the LPC2148 regulator. At that point regulator will produce a control signal for the GPS framework; it will impart control sign through MAX 232 to the GPS module. GPS will get enacted, so it will follow the specific area of the person in question and send this data back ARM regulator through the MAX 232 interface [30].
16.2.12 A Mobile-Based Women Safety Application
In the proposed framework, with the press of one catch, individuals can alarm chosen contacts that the individual is in harm’s way and offer the area. The individual wellbeing application requires the name and number of the individual who is to be reached during the crisis. Clients can include numerous individuals in the crisis contacts list. These are the individuals who will get notices or SMS if there should arise an occurrence of an emergency [29].
16.2.13 Self-Salvation—The Women’s Security Module
If any individual needs to endeavor, women, then squeezing a catch will send ready messages to the guardians or companions’ telephone numbers and the closest police headquarters. The strategy for security is through GPRS; we can follow the women/vehicle position. By sending SMS “TRACK” to the current telephone number, we can get the pic [32].
16.3 Issue and Solution
16.3.1 Inspiration
The strongest influence for that kind of system has been the case of Hyderabad as well as the case of Delhi Nirbhaya, which sets the whole nation into action. Something else which persuaded us is that the women going to obscure spots don’t know about Red Alert Areas. On the off chance that they know about Red ready zones, at that point, they can be set up with preventive measures. The women’s wellbeing application will furnish an alert with a warning and crisis help. Such ace applications can be utilized any place. This venture proposes another model for females’ security openly puts which expects to give the 100% safe condition. Each lady must not hesitate to travel to any place by giving her the warning identified with the red ready region and giving the crisis board enacted at whatever point she will move to the red ready zone by thusly giving her the wellbeing at each progression [5–9].
16.3.2 Issue Statement and Choice of Solution
Women in homes, on roads, openly ships, or in workplaces are not generally protected. There have been numerous instances of lewd behavior toward little children to mature age women. We live in such a general public that it is important to be ready for our security from all perspectives. The decision of making a versatile application is to accomplish the issue articulation because of the way that a cell phone is typically conveyed by an individual, so than a different equipment gadget that could be lost [12–13].
Starting here, the accompanying pipeline was received to construct an answer:
- Collection of data
- Preprocessing of data
- Simulation
- Assessment
- Forecast.
16.4 Selection of Data
A significant proportion of the quality of and access used for misconduct examinations include loads and loads of nitty-gritty instances, with quantities varying about 100,000 to 100,000,000 records, as they are mainly generated by the surrounding police department, that includes a good mechanized system for processing, organizing, and discharging this important information around a defined area [16, 20, 27].
For both the structural portion, a formula was used that selects the appropriate range and longitude restrictions depending on the number of times of the edge and the separation of the graph. As in Figure 16.1, the first dataset was represented.
We provided details on a temporal calculation between 2002 to 2019. Obtaining them by month, it was feasible to verify that not every year had a relevant or useful proportion of information, such that the method could select only data between both the focused set, as can be imagined in Figure 16.2 [31, 33–35].
If useful geographical and situational knowledge was selected at the next level, designers created the heat maps.

Figure 16.1 Option of boundary space measurements for the Delhi database. (a) will be the first database with all information, whereas (b) is the database with some of the most valuable information.
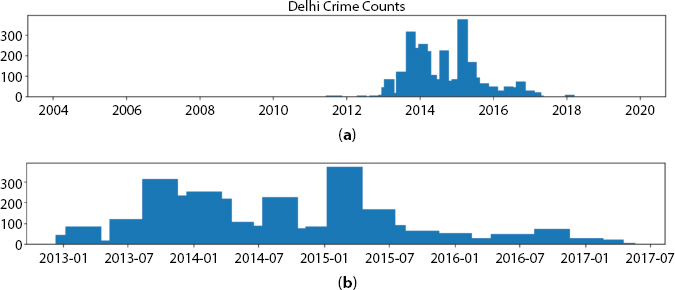
Figure 16.2 Selection of boundary for worldwide calculation of the Delhi dataset. (a) will be the first database for all records operating between 2002 and 2019, whereas (b) displays details chosen between 2013 and 2017.
16.5 Pre-Preparation Data
Throughout the pre-preparing phase of data, developers have defined the spatial and worldly variability of our collected data to construct heat maps. The scale of the 32 by 32 matrix was regularly used in this study. Such attributes tend to be powerful for just a little database but, as described earlier, two-fold directions required further space between cells because they only needed one event on that location and day-to-day complexity was used, even with lots of lacking quality between days, on the premises that with the data support development used below, we achieved several excellent results and after added each one of those examples that fell in a similar organize on a similar fleeting granularity as exhibited in Figure 16.3 [36, 37].
Throughout the context of developing the heat maps, we certainly had a lot of lacking day-to-day maps that could talk too hard while piling them into some kind of progression of details for the ConvLSTM design. One approach may be to consider null-esteemed heat maps for these situations even though we formerly had an enormous amount of negligible networks doing this method would start adding to show regularization to nonexistent.
The technique is used only to fill this void to reassemble the absent heat maps using a straight addition between first and next thermal mapping of the information sets using the all-out missing time as a separate variable. With that same knowledge growth method, this was feasible to increase the database from 586 double guides to 1,546 regular maps.
Since dynamically rendering the required heat maps, the surface estimate was discretionarily chosen to turn them into simultaneous guides (Figure 16.4) as we reported that the model would work with dangerous and quasi-unsafe hotspot forecasts.

Figure 16.3 Shows heatmap.
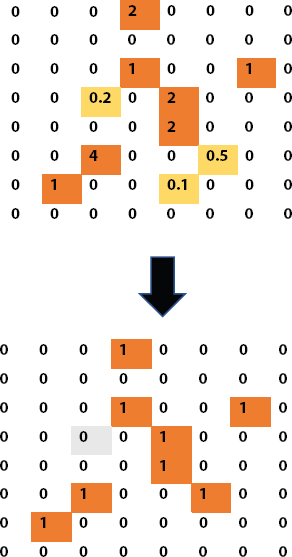
Figure 16.4 Example of transformation from a heatmap into a double guide utilizing a 0.5 limit.
16.5.1 Simulation
Planning and goal sets were created by collecting 16 day-by-day significantly vary manuals and using the preceding as a goal for 576 fictional categories. It is essential and necessary to say that the inaccurate graphs that have been produced have been missed once they’ve been selected as a goal so they do not transform into an actual situation.
And for training and testing sets separating, the option amount based on the related temporal details during 2013 and 2017, where even the experiment before the actual practically 50% of 2016 was chosen to plan the model and the corresponding term to accept it.
16.5.2 Assessment
No matter how we handle the structure problem, we can’t allow a flexible edge like 0.5 and consider all the values across this line to be regarded as hazards and all below impartial cores. We’re effective in predicting places that have greater probabilities of even an incident happening and don’t necessarily know that misconduct is going to be happening. Besides that, designers prepared big, scanty networks so it’s normal that all the standards will turn to empty is shown in Figure 16.5 [38].

Figure 16.5 Binary anticipated guides utilizing various percentiles to characterize unsafe zones.
After selecting the percentile respect and turning over basic outcomes into some kind of two-fold guideline, we calculate the performance against both the real tutorial. To not hit the forecasting too harshly against both the failed results that could clear the way for a shift in the system such that we wind up with a completely overrated estimate, we offer some value for the predicted cellular in the adjacent hotspot zones as we haven’t missed to such an amount (see Figure 16.6).
| Label | Predicated | True |
| Correct | 01 | 01 |
| Neutral | 00 | 00 |
| False Positive Neighbor | 01 | 00 with true neighbor 01 |
| False Negative Neighbor | 00 | 01 with predicted 01 |
| False Positive | 01 | 0.0 |
| False Negative | 00 | 1.0 |
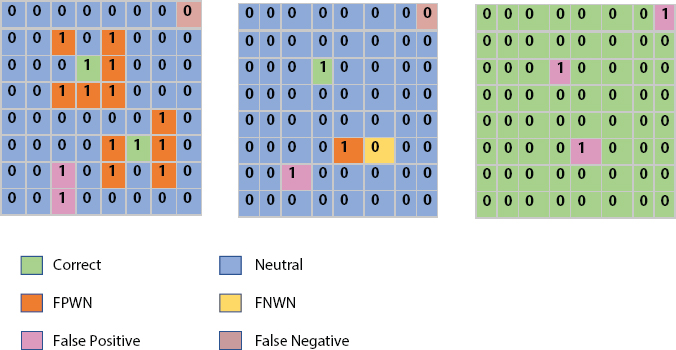
Figure 16.6 Label forecast by characterized percentile edge.
Rather than the four characterization names, we have six:
The accompanying table speaks to the marks for every arrangement:
Given this table, we check every one of those names for each anticipated cell as found in Figure 16.17 [39].
For the model above we have the accompanying outcomes relying upon the chose percentile esteem:
The less the percentile level, the larger the proportion of cells we label as dangerous and the higher is the accuracy of our design, but is it feasible?
| Label | p = 0.5 | p = 0.6 |
| Correct | 02 | 01 |
| Neutral | 48 | 59 |
| False Positive Neighbor | 11 | 1.0 |
| False Negative Neighbor | 00 | 1.0 |
| False Positive | 02 | 1.0 |
| False Negative | 01 | 1.0 |

Figure 16.7 Model evaluation against different category levels. It is feasible to remember that the greater the percentile permissible limit, the higher the efficiency (dark line) but the more false-positive will get.
We ought to identify the perfect balance among hazard characterization and design accuracy to get the best end-customer satisfaction.
Along those same sections, between each of these names, are one of the most important ones to take a look at? Noah at that. Al states in the article that Right, False Negative Neighbor, and False Negative should be considered during the evaluation of the model. The aim is to determine the equilibrium among False Negative Vs. Right + False Negative Neighbor Rate and Accuracy.
Figure 16.7 shows the percentile models based which varies from the 85th to the 99th limit. The larger the quality, the more false negative (fn we have despite the growing accuracy of the design. This occurs on the basis that we consider further impartial cells (True Negatives) to be right. These cells are exceptionally imperative to reliable identification because we need to monitor the user in a sheltered area while refraining from displaying such a vast number of spots as hazardous, although most not quite as dangerous.
16.5.3 Forecast
There are some suggested principles for Noah et al. to allow the forecast in such a way that people have a clear understanding of the yielding made. The best approach is usually to display the cells called dangerous with one highlighting and at the same time silencing the others while the next direction is to characterize a list of limit values for each phone.
So the general rule for model expectations is as follows:
- Foresee a lone instance or a group as a whole.
- Transform basic attributes to distinct ones using the surface list described.

Figure 16.8 Heatmaps assumptions using several edges. (a) uses the 96th percentile while (b) uses the 99th percentile.
Figure 16.8 displays two versions using the 96th and 99th edges as dangerous values covered in red. Unique features are produced using specific threshold options such as the 91st, 75th, and 25th percentile.

Figure 16.9 Large-goal heatmap from over Delhi region. The rose-colored region of risk is regarded by the estimate. The Darker Dab refers to the corruption that occurred in that area on a particular timeline.
The surrounding’s effect of the shock absorption on the Convolutional Network is regarded as an important problem to the system. Zero insulation might not be the most optimal way of handling extremes, specifically on tiny images like heat maps, and it should be ignored when it comes to making because they barely translate to the actual world.
Another solution to increasing the maximize objective is to use the asymmetric injection method and expand the number of the heatmap providing an even more optimized target because the last user is added as shown in Figure 16.9.
16.6 Application Development
16.6.1 Methodology
When the females are signed in and she goes to an obscure area, the current criminal dataset checks whether the current area matches its dataset or not, and on the off chance that it is coordinated, it informs her that the region is wrongdoing inclined zone. At the point when she gets to know wrongdoing inclined territory, she would have an elective. Possibly she would abstain from going there or she would need to be set up with well-being measures, here Proposed Application can end up being useful for her. On the off chance that she goes to the wrongdoing inclined region and she associates any sort with the threat from outsiders at that point, she is furnished with the assistance button in the application. After squeezing the assistance button, a message will be created. The created message comprises of the scope and longitude of her present area just as a slogan of “I am in a tough situation. Please Help” will likewise be sent. The produced message will be sent to the enlisted crisis contacts shown in Figure 16.10.
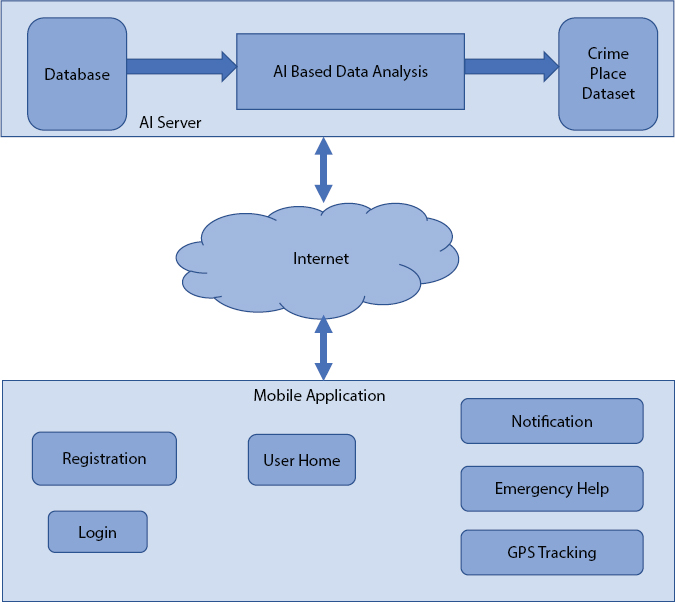
Figure 16.10 Shows flow chart of proposed application system.
16.6.2 AI Model
Artificial Intelligence is a simulation of inductive logic designed by machines, in specific computer servers. It depends on the thought of building machines fit for intuition, acting, and learning like people. SVM calculation is a piece of AI and Artificial Intelligence. Characterization is given in Support Vector Machine Algorithm. Here in this paper SVM calculation encourages our application to recognize the wrongdoing related spots. This calculation causes the framework to produce an alarm to the client after the recognizable proof of the specific recorded wrongdoing place.
16.6.3 Innovations Used The Proposed Application Has Utilized After Technologies
- HTML for Front End creating.
- JAVA for Client and Server-side.
- MySQL for Back End and Processing.
- Visual Studio for Server-side handling.
- Android SDK to construct an Application upheld by Android.
16.7 Use Case For The Application
16.7.1 Application Icon
The figure below outlines the overall perspective on symbols of different android applications. Our application has been named as Proposed Application (Safetyapp for Women: a non-Magnanimous Shield) shown in Figure 16.11.

Figure 16.11 Shows icon of application.
16.7.2 Enlistment Form
An enrollment structure is a rundown of fields that a client will include information into and submit it to a worker. To give security administration, the worker requires a portion of the fundamental subtleties of the client. The client needs to fill the necessary subtleties and tap on the Submit button. From that point onward, the client will be heading off to the Login page and continue with their email ID and secret key for venturing into the application. The Emergency contact is spared in the Registration structure which is named “Enter Mobile no.” shown in Figure 16.12.

Figure 16.12 Shows form of registration.
16.7.3 Login Form
When the application is installed, the login page will be shown. For login, enrollment is required so tap on New client alternative shown in Figure 16.13.
16.7.4 Misconduct Place Detector
When the client enters where she will be going, results would be that either the spot is exceptionally wrongdoing inclined or not as indicated by the dataset. Her area will be accessible on the guide and the close by wrongdoing zones will be featured by Google map pin, portrayed as following shown in Figure 16.14:

Figure 16.13 Shows login page.

Figure 16.14 Misconduct place finder.
- Green shows the user’s current area
- Red shows the horror inclined zone
- Orange shows the moderate wrongdoing inclined zone
- Yellow shows the low wrongdoing zone.
Figure 16.15 portrays the wrongdoing zones of that specific zone contingent on the current area of the client.
16.7.5 Help Button
Below picture portrays the screen capture of the message that the client will send after clicking HELP BUTTON shown in Figures 16.16 and 16.17.
Beneath picture portrays the screen capture of the message that the registered contact will get.
The picture beneath portrays the screen capture where the client area will be followed, from the collector’s message shown in Figure 16.18.

Figure 16.15 Location recognized on map.

Figure 16.16 Show message sent by user.

Figure 16.17 Shows received message to enrolled contact.

Figure 16.18 Location of client.
16.8 Conclusion
Multiple measures have been adopted out there using deep learning models to classify corruption using heat maps. This future prospectus to assist by suggesting the approach that best matched the resources that we had for this study, and at the same time assessing what and why usually negotiated did not perform. This versatile application is useful for women. Utilizing PROPOSED APPLICATION can lessen the cases occurring in the public arena. With the assistance of this application, women will get cautions about the obscure spots. With the goal that she will be prepared as of now for any circumstance. The application can be additionally utilized for Machine Learning that can be applied to screen the sound created by encompassing and characterize the word, make examinations, and consequently distinguish the degree of danger.
References
1. Chand, D., Nayak, S., Bhat, K.S., Parikh, S., Singh, Y., Kamath, A., A Mobile Application for Women’s Safety: WoSApp. IEEE Region Conference, Macao, 2015.
2. Punjabi, S., Chaure, S., Ravale, U., Reddy, D., Smart Intelligent System for Women and Child Security. IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference, Vancouver, BC, pp. 451–454, 2018.
3. Yarabothu, Y. and Thota, B., Abhaya: An Android App For The Safety Of Women. IEEE 12th India International Conference, Electronics, Energy, Environment, Communication, Computer Control, Jamia Millia Islamia, New Delhi, India, December 2015.
4. Mahajan, M., Reddy, K., Rajput, M., Design and implementation of a rescue system for the safety of women. International Conference on Wireless Communications, Signal Processing and Networking, Chennai, India, pp. 1955–1959, 2016.
5. Harikiran, G.C., Menasinkai, K., Shirol, S., Smart Security solution for women based on Internet of Things(IoT). International Conference on Electrical, Electronics and Optimization Techniques, Chennai, India, pp. 3551–3554, 2016.
6. Sharma, K. and More, A., Android Application for women security system. Int. J. Adv. Res. Comput. Eng. Technol., 5, 3, 725–729, March 2016.
7. Sharma, K. and More, A., Advance Woman Security System based on Android. Int. J. Innov. Res. Sci. Technol., 2, 12, 478–488, May 2016.
8. Paradkar, A. and Sharma, D., All in one Intelligent Safety System for Women Security. Int. J. Comput. Appl., 130, 11, 33–40, November 2015.
9. Mahmud, S.R., Maowa, J., Wibowo, F.W., Women Empowerment: One Stop Solution for Women. 2nd International Conferences on Information Technology, Information Systems and Electrical Engineering, Yogyakarta, pp. 485–489, 2017.
10. Bankar, S.A., Basatwar, K., Divekar, P., Sinha, P., Gupta, H., Foot Device for Women Security. 2nd International Conference on Intelligent Computing and Control System, pp. 345–347, 2018.
11. Pathak, S., Raja, R., Sharma, V., Ramya Laxmi, K., A Framework Of ICT Implementation On Higher Educational Institution With Data Mining Approach. Eur. J. Eng. Res. Sci., 4, 5, 2019.
12. Pressman, R.S., Software Engineering: A Practitioner’s Approach, Seventh Edition, pp. 1–888, McGraw-Hill International edition, New Delhi, 2010.
13. Abdul Kalam, A.P.J. and Rajan, Y.S., India 2020—A Vision for the New Millennium, Penguin Books India Pvt Limited, 11 Community Centre Panchasheel Park New Delhi 110017 India, Published by Penguin Books, 2002.
14. http://www.un.org/womenwatch/confer/beijing/reports, Report of the Fourth World Conference on Women, New York, United Nations, 1995 (A/CONF.177/20/Rev.1)
15. http://www.nirbhaya.mobi, Nirbhaya: Be Fearless
16. https://www.guardly.com, Android App developed by Guardly Corp. “GUARDLY”.
17. https://www.glympse.com, Android app developed by Glympse Corp. “GLYMPSE- SHARE GPS LOCATION”
18. http://apps/who/int/iris/bitstream/10665/85239/1/9789241564625_eng.pdf, World Health Organization, Global and Regional estimates of violence against women.
19. http://timesofindia.indiatimes.com/topic/mobile-apps-for-women’s-safety
20. https://play.google.com/store/apps/details?id=com.startv.gumrah, VithU: V Gumrah Initiative on the Google Play Store, Google Play Store, Mountain View, California, United States, 2017.
21. http://www.fightbackmobile.com/welcome, Android app developed by Canvas M Technologies named “FIGHTBACK”, Google Play Store, Mountain View, California, United States, 2021.
22. Chougula, B., Naik, A., Monu, M., Patil, P., Das, P., Smart Girl Security System. Int. J. Appl. Innov. Eng. Manage. (IJAIEM), 3, 4, 281–284, April 2014.
23. Bhilare, P., Mohite, A., Kamble, D., Makode, S., Kahane, R., Women Employee Security System using GPS And GSM Based Vehicle Tracking. Int. J. Res. Emerg. Sci. Technol., 2, 1, 65–71, Jan-2015.
24. Vidyasagar, K., Balaji, G., Narendra Reddy, K., RFID-GSM imparted School children Security System. Commun. Appl. Electron. (CAE), 4 Foundation of Computer Science FCS, New York, USA, 2, 2, 17–21, 2015.
25. Al-Suwaidi, G.B. and Zemerly, M.J., Locating friends and family using mobile phones with a global positioning system (GPS). IEEE/ACS International Conference on Computer Systems and Applications, 2009.
26. Vijaylashmi, B., Renuka, S., Pooja Chennur, S., Self Defence System for Women With Location Tracking and SMS Alerting Through GSM Network. Patil Int. J. Res. Eng. Technol.(IJRET), 57–60, 04, 05.
27. Monisha, D.G., Monisha, M., Pavithra, G., Subhashini, R., Women Safety Device And Application-Femme. Indian J. Sci. Technol., 9, 10, 1–6, March 2016.
28. Lokesh, S. and Gadgil, A., Safe: A Women Security System, in: Electronic and Telecommunication, Savitribai Phule Pune University, Pune, Maharastra, India-411052, 112, 2020.
29. Anandjatti, M., Alisha, R.M., Vijayalakshmi, P., Sinha, S., Design and Development of An IoT Based Wearable Device for the Safety and Security of Women and Girk Children. IEEE International Conference on Recent Trends in Electronics Information Communication Technology, India, May 20–21, 2016.
30. Raja, R., Kumar, S., Rashid, Md., Color Object Detection Based Image Retrieval using ROI Segmentation with Multi-Feature Method. Wirel. Pers. Commun. Springer J., 112, 1–24, 2020.
31. Mandapati1, S., Pamidi, S., Ambati, S., A Mobile Based Women Safety Application. IOSR J. Comput. Eng., 17, 29–34, 2015.
32. Nagaraju, J. and Sadanandam, V., Self Salvation—The Women’s Security Module. Int. J. Innov. Res. Electron. Commun., 3, 13–19, January 2016.
33. Holm, N. and Plynning, E., Spatio-temporal prediction of residential burglaries using convolutional LSTM neural networks, KTH ROYAL INSTITUTE OF TECHNOLOGY, SCHOOL OF ARCHITECTURE AND THE BUILT ENVIRONMENT, Sweden, 2018.
34. Schlegel, U., Universität Konstanz Department of Computer Science Master Thesis, Universität Konstanz, Konstanz, Baden-Württemberg, Germany, 2018.
35. Stalidis, P., Semertzidis, T., Daras, P., Examining Deep Learning Architectures for Crime Classification and Prediction, Cornell University, New York, pp. 1–12, 2018, Retrieved from http://arxiv.org/abs/1812.00602.
36. Wang, B., Zhang, D., Zhang, D., Brantingham, P.J., Bertozzi, A.L., Deep Learning for Real-Time Crime Forecasting, pp. 33–36, Springer Nature, Switzerland, 2017, Retrieved from http://arxiv.org/abs/1707.03340.
37. Zhang, J., Zheng, Y., Qi, D., Deep Spatio-temporal residual networks for citywide crowd flow prediction. 31st AAAI Conference on Artificial Intelligence, AAAI 2017, pp. 1655–1661, 2017.
38. Jain, S., Mahmood, Md. R., Raja, R., Laxmi, K.R., Gupta, A., Multi-Label Classification for Images with Labels for Image Annotation. SAMRIDDHI: A J. Phys. Sciences, Eng. Technol., 12, Special Issue (3), 183–188, 2020.
39. Mahmood, Md. R., Raja, R., Gupta, A., Jain, S., Implementation of Multi Sensor and Multi-Functional Mobile Robot for Image Mosaicking. SAMRIDDHI: A Journal of Physical Sciences, Engineering and Technology, 12, Special Issue (3), 189–196, 2020.
- *Corresponding author: [email protected]
