CHAPTER 52. Upgrading from Bridges and Hubs to Routers and Switches
SOME OF THE MAIN TOPICS IN THIS CHAPTER ARE
Growing Beyond a Small LAN 974
You can use many kinds of network devices to expand a local area network (LAN) or to connect it to a wide area network (WAN). They range from simple repeaters to devices with more intelligence, such as bridges, routers, and switches. For the most part, traditional bridges have been replaced with switches. Both segregate network traffic to specific ports, but switches do so on a computer-by-computer basis, whereas traditional bridges do so based on LAN segments.
Note
Hubs, low-end repeaters, and simple bridges are generally not the best choice for networks today. Instead, switches have pretty much replaced them in the marketplace. Where hubs or multiport repeaters still exist, they’re being replaced as applications and workstations require more and more bandwidth.
As a small LAN grew in the past, it was common to use bridges to segment a few small workgroups. Bridges were used to isolate local traffic among groups of users and thus cut down on the overall traffic on the LAN. However, depending on the kind of network (for example, ARCnet, Ethernet, or Token-Ring), there are limits to how many bridges (repeaters) could be used in a LAN. In addition to their usefulness in solving network traffic congestion problems, you can use routers or switches to solve several other problems: expanding the LAN beyond the size that bridges allow and connecting the LAN to other LANs to create a larger local network, or for a connection to a WAN, such as the Internet. In short, switches and routers offer the following benefits:
![]() Switches enable you to expand the LAN because they greatly limit the collision domain and switch traffic from one port to another, avoiding broadcasting packets unnecessarily on ports that don’t have a route to the packet’s destination.
Switches enable you to expand the LAN because they greatly limit the collision domain and switch traffic from one port to another, avoiding broadcasting packets unnecessarily on ports that don’t have a route to the packet’s destination.
![]() Routers enable you to connect to a much larger collection of networks, such as the Internet, and enable you to organize a large LAN into a hierarchical address space and many subnets.
Routers enable you to connect to a much larger collection of networks, such as the Internet, and enable you to organize a large LAN into a hierarchical address space and many subnets.
![]() You can find out more about how routers and switches function by reading Chapter 8, “Network Switches,” and Chapter 10, “Routers.”
You can find out more about how routers and switches function by reading Chapter 8, “Network Switches,” and Chapter 10, “Routers.”
A traditional bridge has just about outlived its usefulness in a modern network. Instead, switches (which are really glorified multiple bridges all in one box) and routers can be used to better segment a LAN and limit unnecessary network traffic on local LAN segments.
Note
The term bridge is used in this chapter to refer to a legacy device that connects several network segments and is used to limit network traffic to local segments.
Other types of bridges exist that are important in networking today. For example, there are translational bridges that can convert frames from one format to another, enabling you to connect different types of LANs. Another example is a SCSIto–Fibre Channel bridge that enables you to connect legacy SCSI devices to a Fibre-Channel network, thus preserving your investment in older disks, tape drives, and so on.
In this chapter, the possibilities offered by upgrading to switches and routers are discussed, along with information you must consider when bringing such devices into your LAN.
Growing Beyond a Small LAN
Several chapters in this book cover the basic devices used to interconnect network segments: repeaters, bridges, switches, and routers. Each of these devices builds on the one previous to it so that together they span a continuum of functionality that you can use to solve problems with a LAN or WAN. Standard bridges were developed to enable you to extend the reach of a LAN and to limit traffic to local segments, therefore building on the function of repeaters. Switches took this concept further by enabling each workstation or server to have its own physical LAN segment, thus limiting the broadcast domain (just the workstation and the switch). Routers enable you to extend the reach of a LAN by connecting it to a wide area network.
Note
A switch that operates in full-duplex mode eliminates the collision domain between the switch port and the device attached to it. Instead of using the same set of wires for transmitting and receiving data (half-duplex), full-duplex switches use separate wires for transmitting and receiving, so both ends of the path can be sending information at the same time. Thus, a switch port and network card operating in full-duplex mode can essentially double the network bandwidth.
To quickly summarize:
![]() Repeaters are simple devices that connect network segments (usually two segments). They repeat all traffic by regenerating and attenuating a signal, allowing the standard distance limitation to be extended. They do not, however, do anything to help segment network traffic patterns. Repeaters are used to expand a LAN when it grows beyond the limitations imposed by a single network segment. Multiport repeaters function in the same way, but resemble a hub in that more than one segment can be connected to a multiport repeater. However, multiport repeaters are typically used in much older environments that use coaxial cables for the network media and use BNC connectors. Most hubs have RJ-45 jacks and receive twisted-pair wiring with RJ-45 modular connectors. If your network still uses repeaters of this type, you’re long overdue for an upgrade.
Repeaters are simple devices that connect network segments (usually two segments). They repeat all traffic by regenerating and attenuating a signal, allowing the standard distance limitation to be extended. They do not, however, do anything to help segment network traffic patterns. Repeaters are used to expand a LAN when it grows beyond the limitations imposed by a single network segment. Multiport repeaters function in the same way, but resemble a hub in that more than one segment can be connected to a multiport repeater. However, multiport repeaters are typically used in much older environments that use coaxial cables for the network media and use BNC connectors. Most hubs have RJ-45 jacks and receive twisted-pair wiring with RJ-45 modular connectors. If your network still uses repeaters of this type, you’re long overdue for an upgrade.
![]() Bridges are similar to repeaters except that they apply a little intelligence to the packet-forwarding process: Bridges learn MAC addresses of devices on each segment when they make an initial transmission. From then on, a bridge will not pass traffic to another segment if it knows the recipient is on the segment local to the transmission. Bridges are helpful for expanding a LAN and can be used to group collections of computers and servers that commonly interact to lower overall bandwidth consumption.
Bridges are similar to repeaters except that they apply a little intelligence to the packet-forwarding process: Bridges learn MAC addresses of devices on each segment when they make an initial transmission. From then on, a bridge will not pass traffic to another segment if it knows the recipient is on the segment local to the transmission. Bridges are helpful for expanding a LAN and can be used to group collections of computers and servers that commonly interact to lower overall bandwidth consumption.
![]() Routers work like bridges in that they’re selective about which packets get forwarded on which ports. However, whereas bridges operate at layer 2 of the OSI reference model (the Data Link layer) and look only at the flat namespace provided by the MAC addresses, routers operate at layer 3 (the Network layer) and make decisions based on the addressing scheme provided by a higher-level networking protocol. Bridges are typically used to create larger local area networks. Connecting a LAN to other LANs or to a larger WAN can be done using a router.
Routers work like bridges in that they’re selective about which packets get forwarded on which ports. However, whereas bridges operate at layer 2 of the OSI reference model (the Data Link layer) and look only at the flat namespace provided by the MAC addresses, routers operate at layer 3 (the Network layer) and make decisions based on the addressing scheme provided by a higher-level networking protocol. Bridges are typically used to create larger local area networks. Connecting a LAN to other LANs or to a larger WAN can be done using a router.
![]() Switches are the current technology for connecting network LAN segments as well as for connecting individual network nodes to the network. Switches operate like bridges in that they keep track of which network node is located on each port by remembering MAC addresses kept in system memory. When retransmitting an incoming packet, the switch will send it out only on a port that will get it to its destination, provided that it has already learned the destination’s MAC address. Whereas bridges usually have only two ports, switches are like hubs and contain many ports. Most switches will allow for full-duplex operation, thus effectively doubling the available network bandwidth for a single node connected on a segment. In a sense, a switch operates like a collection of bridges. And don’t forget that you can connect one switch to another to further localize network traffic. A LAN today can consist of multiple layers of switches that eventually connect to a router.
Switches are the current technology for connecting network LAN segments as well as for connecting individual network nodes to the network. Switches operate like bridges in that they keep track of which network node is located on each port by remembering MAC addresses kept in system memory. When retransmitting an incoming packet, the switch will send it out only on a port that will get it to its destination, provided that it has already learned the destination’s MAC address. Whereas bridges usually have only two ports, switches are like hubs and contain many ports. Most switches will allow for full-duplex operation, thus effectively doubling the available network bandwidth for a single node connected on a segment. In a sense, a switch operates like a collection of bridges. And don’t forget that you can connect one switch to another to further localize network traffic. A LAN today can consist of multiple layers of switches that eventually connect to a router.
From this summary, you can see that it’s easy to use repeaters or bridges to grow the small LAN, but when it becomes necessary to expand beyond certain limits or when it becomes necessary to make a connection to a larger LAN, you must incorporate routers or switches. Growth is not the only reason you might want to use a router or switch, however. These devices also can be used in a small LAN. For example, a small LAN that’s experiencing network traffic congestion might find relief by replacing the hubs in the LAN with switches to cut down on the overall network traffic. Indeed, if you look at the price of a switch today, the benefits you will achieve in network bandwidth are well worth the price. When users begin to complain about network response time in a network that uses hubs, you should definitely consider replacing hubs with switches.
In addition to connecting LANs to larger networks such as the Internet, routers can be used in a campus LAN to allow network administrators to logically group network segments using the addressing scheme provided by TCP/IP (subnetting), for example.
Segmenting the Network Can Improve Performance
You might need to segment devices on the network for many different reasons. These include the following:
![]() Topology limitations—You need to add more nodes to the network but the expansion will break distance limitations or maximum nodes-per-segment rules. This is usually the case only in older Ethernet LANs where the broadcast domain was constrained by the round-trip time.
Topology limitations—You need to add more nodes to the network but the expansion will break distance limitations or maximum nodes-per-segment rules. This is usually the case only in older Ethernet LANs where the broadcast domain was constrained by the round-trip time.
![]() For more information about topology limitations, refer to Chapter 13, “Ethernet: The Universal Standard.”
For more information about topology limitations, refer to Chapter 13, “Ethernet: The Universal Standard.”
![]() Networking protocol limitations—Address space is fragmented and you need to connect segments that have different network addresses. This can happen when two companies merge and both already have an address space in place for their respective networks. It’s much easier to simply place one or more routers between the two networks than it is to reassign network addresses to the many devices on the network. When using DHCP to configure workstations, this might not be a limitation, provided that you have an address space that can accommodate all the devices that will be placed on the larger network. You can also use network address translation (NAT), as covered in Chapter 45, “Firewalls.”
Networking protocol limitations—Address space is fragmented and you need to connect segments that have different network addresses. This can happen when two companies merge and both already have an address space in place for their respective networks. It’s much easier to simply place one or more routers between the two networks than it is to reassign network addresses to the many devices on the network. When using DHCP to configure workstations, this might not be a limitation, provided that you have an address space that can accommodate all the devices that will be placed on the larger network. You can also use network address translation (NAT), as covered in Chapter 45, “Firewalls.”
![]() Network bandwidth limitations—When a few high-performance servers or workstations consume too much of the segment’s available bandwidth, it’s time to segment the LAN (create additional subnets) and thus limit network traffic to smaller segments that contain fewer devices.
Network bandwidth limitations—When a few high-performance servers or workstations consume too much of the segment’s available bandwidth, it’s time to segment the LAN (create additional subnets) and thus limit network traffic to smaller segments that contain fewer devices.
![]() Security reasons—An Ethernet adapter set to promiscuous mode can intercept all packets that are sent out on a particular segment, for example. You need to place a few high security workstations on their own segment, yet allow some kind of connection to the rest of the network. Keep in mind that in an Ethernet network that uses hubs as a wiring concentrator, every device on the hub (or hubs) can see every network frame that’s broadcast on the LAN. It isn’t difficult to download a program from an Internet source to read every packet that passes through the network.
Security reasons—An Ethernet adapter set to promiscuous mode can intercept all packets that are sent out on a particular segment, for example. You need to place a few high security workstations on their own segment, yet allow some kind of connection to the rest of the network. Keep in mind that in an Ethernet network that uses hubs as a wiring concentrator, every device on the hub (or hubs) can see every network frame that’s broadcast on the LAN. It isn’t difficult to download a program from an Internet source to read every packet that passes through the network.
Note
Security is an important topic in computer networks today. For more information about the issues you should consider, refer to Chapter 42, “Basic Security Measures Every Network Administrator Needs to Know,” and Chapter 44, “Security Issues for Wide Area Networks.” Other chapters that might help you understand how to protect your network include Chapter 45, “Firewalls,” and Chapter 46, “Virtual Private Networks (VPNs) and Tunneling.”
![]() Geographically distant connections—It’s best to segment each geographic location to ensure that unnecessary traffic isn’t being sent across the remote connection and wasting valuable bandwidth. Some routers provide a dial-up function so that a dedicated link isn’t necessary, providing an inexpensive way to use routers to connect branch offices.
Geographically distant connections—It’s best to segment each geographic location to ensure that unnecessary traffic isn’t being sent across the remote connection and wasting valuable bandwidth. Some routers provide a dial-up function so that a dedicated link isn’t necessary, providing an inexpensive way to use routers to connect branch offices.
Depending on which combination of these reasons applies to your situation, a router or switch might be the solution you need to segment the network.
Connecting Remote Locations
When a business expands geographically, you’ll find that using bridges to connect remote locations isn’t a feasible solution. There are many different technologies from which you can choose today—from simple dedicated lines to ATM and Frame Relay—to connect geographically distant locations. For these connections, you’ll find it necessary to incorporate routers or switches. You’ll also find these methods of transport expensive. Today, it isn’t unreasonable to consider connecting the local network to the Internet with a router that provides virtual private network (VPN) capabilities. Thus, by using an inexpensive connection to the Internet (far cheaper than using leased dedicated lines), you can still provide a secure channel to remote branch locations.
![]() ATM (Asynchronous Transfer Mode) and Frame Relay are very common protocols used to send data across long distances. You can learn more about these in Chapter 15, “Dedicated Connections.”
ATM (Asynchronous Transfer Mode) and Frame Relay are very common protocols used to send data across long distances. You can learn more about these in Chapter 15, “Dedicated Connections.”
When to Use a Router
Routers are similar to bridges only in the fact that they can both be used to connect multiple network segments. Whereas bridges make all their decisions based on the MAC address of a particular network packet, routers access the addressing information provided by a higher-level protocol to decide how to best forward a packet. Using the OSI reference model (see Appendix A, “Overview of the OSI Seven-Layer Networking Reference Model”), you can see that the bridge operates at layer 2, the Data Link layer, whereas routers operate at layer 3, the Network layer. With bridges, the address space is flat: It’s simply the MAC addresses associated with nodes on each segment, each one unique. For protocols operating at the Network layer, the address space becomes more complicated because there must be a mechanism for identifying the network as well as the individual node.
Note
To be more specific, routers operate at layer 3 of the OSI model by using higher-level addresses (such as IP) to make routing decisions. However, when the network frame reaches a router that can deliver it to its final destination, the router uses the MAC address to communicate with the destination node connected to the router’s port. The Address Resolution Protocol (ARP) is used on local segments to translate between IP addresses and MAC addresses. For more information about ARP, refer to Chapter 24, “Overview of the TCP/IP Protocol Suite.”
When to Use a Switch
Switches are one of the fastest growing categories of network equipment. They can act as a wiring concentrator for a LAN just as a hub does, but they also can make available a much larger bandwidth to clients because they selectively forward traffic from one port to another based on the destination address of each packet. When you use a switch with only one node attached to each port, you are in effect creating a collection of broadcast domains that consist of only two network nodes: the switch and the client node connected to the port. For network adapters and switches that support full-duplex operation, the effective bandwidth is doubled for each client and there is no broadcast domain between the two.
From Bridges to Routers
Routers are inherently slower than bridges when it comes to forwarding network packets. This is because a router must read further into each network frame to get Network layer addressing information, whereas a bridge merely looks at a fixed location for the MAC address. Hubs, bridges, and switches can be set up in a short amount of time and usually require little or no configuration.
Routers require that the network administrator configure networking information for each port that’s used. The command set available to configure a router is quite large because it’s a very flexible device and can be confusing for a novice. The kinds of information you need to configure a new router are
![]() A list of the network protocols for which you’ll be using the router. For example, TCP/IP or IPX/SPX.
A list of the network protocols for which you’ll be using the router. For example, TCP/IP or IPX/SPX.
![]() The routing protocol that you’ll use for each network protocol. For example, RIP.
The routing protocol that you’ll use for each network protocol. For example, RIP.
![]() Whether or not you’ll need to set filters to block certain addresses or IP or UDP ports—a technique used to create a simple firewall.
Whether or not you’ll need to set filters to block certain addresses or IP or UDP ports—a technique used to create a simple firewall.
![]() Information about the address space used on each segment the router will connect.
Information about the address space used on each segment the router will connect.
![]() For additional information about routing protocols, refer to Chapter 33, “Routing Protocols.”
For additional information about routing protocols, refer to Chapter 33, “Routing Protocols.”
Network Protocol Issues
In many networks, more than one network protocol is used on the same medium. To do their job, routers need configuration information about each protocol for each port. For example, because each port on the router connects to a different network segment, each port must have a unique network address that it can use to communicate on the segment. If you plan to restrict some segments for security or other reasons, you’ll need to create a set of access control lists (ACLs) for each port, which indicate which frames are allowed through, in both directions.
![]() Using routers to restrict network traffic is often referred to as packet filtering. For more information about this technology, refer to Chapter 45.
Using routers to restrict network traffic is often referred to as packet filtering. For more information about this technology, refer to Chapter 45.
When using a router to connect to a larger WAN, you’ll probably be faced with having to configure a port on the router that uses a WAN protocol, such as Frame Relay, in addition to protocols you’re already familiar with on your network. With a WAN connection, you’ll have to coordinate your activities with other system administrators to ensure that the router is configured with the correct information for the larger network.
Network Addressing Issues
Because the router makes decisions based on a higher-level networking protocol, such as IP, you’ll have to take into consideration your current address space when you decide to introduce a router into the network. If you’re adding new segments to the LAN and have the freedom to choose a new network address, this can be an easy task. If you’re going to take an existing LAN and use a router to separate it into more manageable segments, you have two possible choices. You can use your original network address for one segment and create new networks on the remaining segments or you can use subnetting.
Note
To connect to the Internet, you’ll have to obtain an IP address that is valid on the Internet. Due to the rapid growth of the Internet, the addresses supported by IP version 4 (IPv4) are slowly becoming exhausted. When IPv6 (IPng) becomes widely implemented, the fields that store IP addresses will increase from 32 bits to 128 bits. This single factor will increase the available addresses from 232 (about 4.29 billion) to 2128 (about 340 undecillion—and for reference, 1 undecillion is a 1 followed by 36 zeros!) so that just about every grain of sand on the Earth can have its own IP address. Until then, it’s becoming more common to use a set of reserved IP addresses that are valid only on your local network, and to use fewer IP addresses to access the Internet. The technique called network address translation (NAT) makes this possible. This method also helps to keep outsiders from gaining knowledge about the addresses of your clients, and that helps increase security at your site. To understand how NAT works and the addresses you can use on the local network, refer to Chapter 45.
Regardless, you’ll have to then reconfigure each client with new addressing information. If you’re using DHCP, the process is made simpler because you can make the changes at a central location and have clients request the new information after the changes have been made. DHCP is the most prevalent method used today to configure workstations and other non-server devices on a network.
If you’re going to use a router to connect your LAN to a larger corporate network, you might not have to make any addressing changes on your network, depending on the company’s overall network plan. You’ll still have to configure the ports, however. If you’re going to connect the LAN to the Internet, using a router configured as a firewall might be something to consider.
Other Router Management Issues
Routers are very much like smart PCs that have been customized to perform the routing function efficiently. They have CPUs, memory, and I/O ports just like an ordinary PC. They also have an operating system, which is subject to periodic updates by the manufacturer. So, in addition to learning how to configure the router, you’ll also need to become familiar with the commands used for such functions as saving a copy of the system image to a server for backup purposes and performing troubleshooting and testing.
Managing a network that uses routers can seem a difficult task at first. However, by enabling you to organize your network according to the hierarchical network address spaces used by upper-level network protocols, the initial configuration problems will be worth the effort.
Tip
The best way to learn how to configure your router is to read the documentation. The most popular routers today for LANs are made by Cisco Systems. Its documentation site, which you can reach online at http://www.cisco.com/univercd/home/home.htm or at http://www.cisco.com/en/US/support/index.html, provides documentation for almost all of Cisco’s products. On this page, select Cisco IOS Software and you’ll find a wealth of information about router setup and configuration. Because of the in-depth content, you can use this site to learn not just about configuring Cisco routers, but also the concepts behind protocols and other information that can be helpful no matter what kind of router is used on your network. For students, this is an excellent source of information.
Using a Router to Segment the Network
Like bridges, routers can be used to isolate traffic between network segments. Unlike bridges, routers further reduce network bandwidth use because they do not pass broadcast messages from one segment to another unless programmed to do so. A router also does not have to take time to learn which nodes are connected to each segment. The information it needs is configured in advance—the administrator assigns protocols and addresses to each port. Routing protocols also use various methods to update each other about network topology as it changes.
One very important reason why routers are used to help organize a network into segments is that routers enable you to connect many network segments. Whereas bridges are limited to a few thousand nodes, depending on the topology used, routers can enable the LAN to be connected to an infinitely larger WAN, such as the Internet.
The internal processing that routers must perform make them slower than bridges (although that might not be the case with most high-end routers being manufactured today), which need to examine only a small amount of data in the packet header. Although this performance difference will not be noticed on network segments with only moderate traffic use, you might find that you need to place routers at only strategic locations throughout the network, retaining switches for connecting other computers or network segments. Remember that you can connect individual computers to a switch port or use the port to connect to other switches.
The method you use will depend on the usage patterns that can be monitored for each segment and the cost of the links used to connect different segments. Another thing to consider is that many of the high-end routers available today operate at what is called “wire speed.” That means they can route packets at virtually the same speed as the network medium, with just the very slightest delay for processing time.
Connecting to a Larger WAN or the Internet
When connecting the LAN to a WAN, a router is required. When connecting to the Internet, for example, you cannot use a bridge or a repeater. The Internet is composed of a hierarchical IP address space and a router is needed to participate in this hierarchy. Or you might plan to use a dedicated line of some sort to connect to a larger corporate network. In that case, placing a router between your LAN and the WAN hardware, such as an ATM switch connection, will help reduce the traffic that crosses the expensive dedicated connection by keeping local traffic confined to the local network segments.
Note
There are two situations in which a router is not needed to make an Internet connection. The first is if you have a modembased dial-up connection. Although it’s possible to set up routing tables in operating systems such as Windows and Unix/Linux, this isn’t really a practical method for connecting a small office LAN to the Internet due to the very limited speed.
The other situation is when you use a broadband connection, such as a cable or DSL modem. In this case, you can connect the high-bandwidth modem to a single computer and then set up routing tables so that other computers can send and receive traffic through the computer, which operates as a router. However, there’s a better idea in a Small Office/Home Office (SOHO) or Remote Office Branch Office (ROBO) environment or a home environment where everyone from the parents to the kids have their own computers: Purchase an inexpensive 4–6 port router (for less than $100 in most cases) that you can connect to the cable/DSL modem. These types of routers require very little knowledge about computers and can usually be set up in less than a half-hour. For more information about configuring a SOHO environment, see Chapter 16, “Digital Subscriber Lines (DSL) Technology,” Chapter 17, “Using a Cable Modem,” and Chapter 50, “Troubleshooting Small Office and Home Office (SOHO) Networks.”
Although you’ll certainly have to configure the ports that connect the local LAN and the WAN interface, you might have to reconfigure addressing information on clients. For example, if you’re already using a valid TCP/IP network address, possibly a subnet of the corporate network address space, you’ll need to configure only routers.
If your business has just been acquired by a larger concern, however, you might find that your LAN has been assigned a new subnet by the larger corporation. In such a case, you’ll probably have to plan on downtime for end users in order to make changes to important servers, such as Domain Name System (DNS) servers. DHCP servers (which workstations can find themselves) are used to translate between user-friendly names and IP addresses. Although DHCP can dynamically assign configuration information to workstations, important servers, such as DNS servers or gateways to other networks (usually routers), must have a static (unchanging) address. This is because part of the configuration information that DHCP supplies to clients is those addresses! If the address of a DNS server changed with every reboot of the server, you would have to reconfigure the information on each workstation client—a tedious effort even in a small network!
By using DHCP, you can overcome client configuration headaches such as this. Just reconfigure the DHCP server with the address range for the new subnet, add in the DNS servers and default gateway, and reboot your client computers. This is a simple explanation of the information supplied by DHCP servers. Indeed, you can use DHCP to provide configuration information for many other network parameters.
![]() For more information about using DHCP and how it works, refer to Chapter 28, “BOOTP and Dynamic Host Configuration Protocol (DHCP).”
For more information about using DHCP and how it works, refer to Chapter 28, “BOOTP and Dynamic Host Configuration Protocol (DHCP).”
From Bridges to Switches
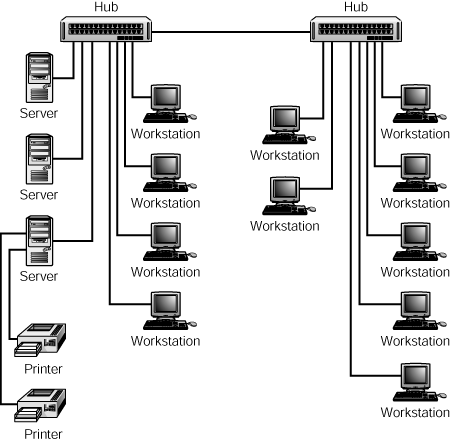
Switches can be useful for solving network problems related to traffic congestion and network segmentation. For example, they can be used as replacements for hubs at the LAN level. In Figure 52.1, you can see a small LAN that uses two hubs. The three servers for this network share a common broadcast domain with all the other users on the network.
Figure 52.1. Hubs do nothing to limit network traffic on the LAN.
When this older LAN was first installed, there was more than adequate bandwidth available and users were satisfied with the response time. Over time, however, each server was replaced with a more powerful model, and some of the end users’ workstations were replaced with high-performance machines and new database software that relies on information stored on the servers.
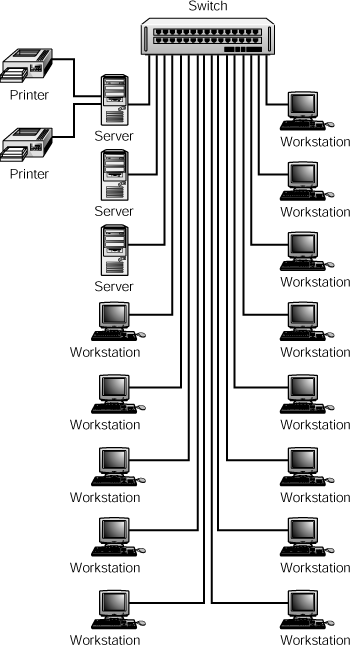
Network traffic has increased considerably, users are dissatisfied, and the network administrator must take action. Because the main problem is the traffic exchanged between the servers and the high-performance end-user workstations, a switch can be a simple solution. There are two simple solutions you could devise using switches. In Figure 52.2, you can see that both of the 8-port hubs have been replaced with a single 16-port switch.
Figure 52.2. A switch can be used to isolate high bandwidth network nodes.
Tip
Throughout this book, I keep emphasizing that hubs are now legacy devices. For large networks, this is true. If you’re using a small inexpensive hub for a SOHO network and you don’t experience a slow network response time, there is no reason to “switch.” However, when contemplating any new network installations or an upgrade, there’s absolutely no reason today to consider purchasing a hub because switches are around the same price as hubs (even at the high-end level).
Indeed, you’ll find it difficult to find larger hubs on the market anymore, except by vendors who want to support older networks.
An exception to this rule is that in a larger LAN, you might still use a hub (connected upstream to a switch) for a few users whose bandwidth is minimal. In that case, replacing a perfectly good hub would cost more in labor costs—much the cost of a replacement switch. Therefore, in larger LANs, hubs can still be used in very small departments that don’t have highband-width needs.
This layout gives each node that is connected to the switch a full 10Mbps network connection or more likely 100Mbps, depending on your hardware. If you can’t afford to replace older 10Mbps network cards (which is a possibility in a large network with a few hundred or thousands of computers), you might not need to worry. Most modern switches support autosensing, so they can detect both 10Mbps as well as 100Mbps traffic, and you can thus connect both types of network adapter cards to the switch. Even switches that support autosensing don’t always work with older network adapters, so you can use the management software that accompanies the switch to manually set ports that don’t behave as you would expect. Check your network traffic using a switch’s built-in monitoring software to ensure that you’re obtaining the maximum bandwidth that the switch port and network card enable you to use. Otherwise, you should disable the autosensing function and set both the switch port and the network card to the desired speed.
Each connection on a switch is a broadcast domain with only two end nodes: the connected workstation or server and the switch. In this solution, the server nodes were equipped with full-duplex network adapters, effectively doubling their available network bandwidth. Provided that the switch is capable of handling the traffic load, individual users on the workstations that make only moderate use of the network should notice a better response time through the switch, as compared to a hub connection.
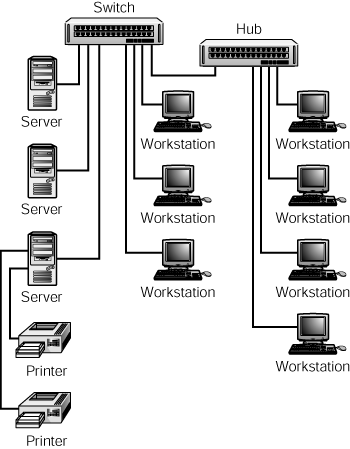
The servers and high-performance workstations should also notice better performance, but their network traffic is no longer broadcast on the segments of the other moderate users, effectively isolating this traffic. For example, in Figure 52.3, you can see another solution discussed a paragraph or so earlier. Here, a hub is used for the workstations that use the network only moderately.
Figure 52.3. Traffic on the hub is not hampered by the traffic generated by the other high-performance servers and workstations.
Here each of the three servers that are responsible for much of the bandwidth use has been placed on a separate port on the switch. Again, full-duplex network adapters were installed to further increase the available bandwidth to each server. The three high-performance workstations also were placed on separate switch ports so that their network use does not directly interfere with other nodes. A hub was retained for connecting moderate network users. Because these nodes do not generate a lot of network communications, placing them on a hub connected to the switch should allow them fast communications among themselves while still allowing access to the other servers and workstations.