Anita Roddick
Speed and the number of people who can be quickly reached is email’s greatest advantage. But what if you email information to the wrong person or type something in haste you regret? This might mean a breach of confidentiality, sensitive data being leaked, the wrong decision or a lost client. It is very important to recognise when the strength of email may also be its biggest weakness. Appreciating all the attributes of email makes it much easier to choose how to use email to maximum advantage and be more productive. This chapter covers:
- email’s strengths and how these can also be its downfall
- recognising the pitfalls of email and their potential cost
- capitalising on the strengths of email, limiting its weaknesses and therefore the cost of misuse
- measures to preserve security and confidentiality when emailing
- deploying a wider range of communications channels to save time communicating.
Strengths and weaknesses of email unravelled
Table 8.1 summarises the key benefits and drawbacks of using email instead of talking – the richest of media and, for many, the best method of communication.
It’s not always a black and white decision. It’s like trying to decide whether it would be ‘greener’ and more effective to go by car or by train. Although the train is greener, it could well take longer and be more expensive.
Table 8.1 Strengths and weaknesses of email

The following is a review of some of these criteria that will show you how to build on the positives, limit the risks from the negative aspects and when you just have to live with the inherent disadvantages of using email.
Quick and fast
Speed and ease of use is probably email’s number one advantage and disadvantage. Once you’ve hit ‘Send’ there’s no going back, and before you know it an email disaster may have broken out. If your incorrect, misdirected or gossip-laden email leaks beyond your initial recipient, then you and your company could be the stars of the next email media disaster. (Examples of email disasters to avoid can be found at www.brilliant-email.com.)
Another major weakness of email is that we can easily add as many people to the ‘Cc’ and/or ‘To’ box as we think might be interested in what we have to say. This massively drives up the volume of email traffic.

Limiting the volume of emails sent will reduce the volume of emails you receive.
Other ways to reduce the risks of hitting ‘Send’ too quickly include:
- Read and re-read your message before sending to check that what you’ve written is what you really meant to say.
- Be ruthless about the number of people you send your message to. Be daring and reduce the total number (both in the ‘To’ and ‘Cc’ box) by at least 20 per cent. Invoke the principle of sending only to those who really must know.
- When in doubt, save the email in the draft box, have a coffee/sleep on it and re-read it before sending. One executive who uses the draft box principle reckons that about 20 per cent of his emails never actually get sent.
- Delay sending any email for at least two minutes.
![]()
‘The two-minute quarantine rule has saved me, many times, from the consequences of emails that would otherwise have been regretted or recalled. Some would have been sent in error, perhaps through hitting the Send button too early or instead of Save. Others would have been sent in haste, perhaps in the heat of the moment. The two-minute rule buys me a second-chance, and I only wish that functionality extended to emails sent on the BlackBerry.’
Richard Stagg, Editorial Director at Pearson Education
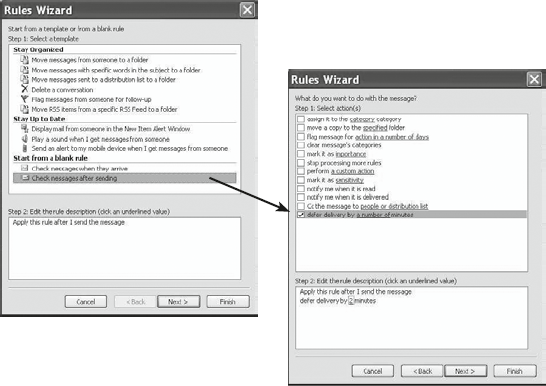
To write such a ‘Rule’ in Outlook go to ‘Tools’/‘Rules and Alerts’ and from the ‘Rules Wizard’, pick ‘Check messages after sending’ (Figure 8.1). Click ‘Next’ twice (click on ‘Yes’ to the box asking if the Rule is to be applied to every message) and on the next screen tick the box marked ‘defer delivery by a number of minutes’. Then click on the link ‘a number of’ in Step 2. Select the delay time and click ‘Next’ to add any exceptions, then ‘Finish’.
Bridges the difference in time zones and geographic locations
This is another great advantage of email, especially if you work in a global business, but it is often abused by people who send emails to colleagues in the same building, even those only two desks away. This can have serious financial consequences, as witnessed by the example opposite.
![]()
A forklift truck driver diligently loaded his lorry one morning only to return to his desk to find an email from his colleague at the next desk about an urgent extra pallet. This had to go on the truck that day but the pallet was in another part of the warehouse. The truck had to be re-loaded from scratch to accommodate the extra palate and the delivery was late. The result was a cross customer who deducted money for the late delivery.

Announce an amnesty on sending emails within a ten-desk radius, and always talk if it’s time-critical.
You could also extend the no-email zone to a two-floor radius and thereby improve your fitness and health.
Carries no body language and sense of context
Are you laughing or crying as you send your email? It could be argued that you can insert an emoticon (or smiley) to convey some sense of context and emotions. But beware as it could convey totally the wrong impression.
In a recent workshop, at least 75 per cent of participants cringed and said that smileys convey the exact opposite to that intended. They found them very annoying and said they look ‘cheesy’ and ‘unprofessional’ in the work place. The other 25 per cent said they liked them as they ‘add a touch of humour’ and ‘friendship’.

In business emails, don’t even contemplate a smiley. If more ‘emotional information or intelligence’ needs imparting, compose your message to say what you mean or pick up the phone and talk.
The email audit trail exposed
In today’s increasingly litigious society, an audit trail of what has been said and done is often essential. Email can be a double-edged sword. For example, businesses to which the Corporate Manslaughter Act is applicable need to have a record of who told who, what and when. Without such an audit trail it can be difficult to assign responsibility if there is a major incident.
Sadly, the audit trail phenomenon is often used to create a blame culture within organisations about fairly trivial matters. ‘I asked you to do X. You did not do it and I have the email to prove it.’ X is often neither life threatening nor will it cost the business if it is not done immediately. In many cases a conversation would have been better and more effective. It would have allowed you to see if the other person understood the request and had any intention (never mind the time and inclination) to do X.
![]()
To minimise the risk of an audit trail becoming more of a disadvantage than an advantage:
Do
- Make a note of the request for yourself and get on: you don’t need to send a follow-up email. The exception to this is the classic corridor conversation with a senior executive who you are trying to warm up. Then if asked for an email – do it and make the link to the corridor conversation.
- Speak when matters are spiralling out of hand before committing words to email.
Don’t
- Ever put anything in an email that you are not prepared to defend in court.
- Use an audit for matters which do not carry a cost to the business or require to be audited for compliance, such as ordering pens.
- Respond to a verbal request with ‘Put it in an email’.
Push or pull communications culture
One of the reasons many people feel so overloaded and stressed by email is not just the volume, but the fact that it’s dumped on them unbidden. This is commonly referred to as a ‘push’ information culture. Communications are issued regardless of the individual’s needs or interest in them. Typical of this syndrome is the blanket ‘All users’ emails. The top management team decrees what employees need to know. The major pitfall of this system is that each individual can delete these items unopened.
The alternative and healthier culture is a ‘Pull’ one. It implies that items of potential interest are posted somewhere (generally on the intranet and blogs). You can seek them out when you wish. It’s a much less stressful approach and, to a large extent, the holy grail of knowledge management.
Social media is very much a ‘pull’ culture – you choose what you read and when. For a more detailed explanation of push–pull information cultures and how to create them using social media see www.brilliant-email.com.
To move away from push and towards a pull culture:
- Limit the number of ‘All user’ ‘and ‘Cc’d’ email.
- Use intranets and blogs to distribute blanket information.
- Be selective: ask yourself, ‘Who really needs this information?’ Use the principle of must know, maybe should know, nice but doesn’t really need.
A major benefit of sending out fewer emails is that you will reduce the number of emails you personally receive and your overall email stress levels.
Induces endless chatter in the organisation
It’s easy to play endless rounds of ‘email thank you’, with no one quite knowing when to close the conversation down:
- Stop sending endless pleasantries like ‘Thanks’, ‘My pleasure’ and ‘OK’ – this will reduce the risk of endless empty email conversations.
- Prioritise your information needs and push back unwanted emails (see Chapter 3).
Eco-friendly
Email has the power to drive forward the green economy. Yet many would agree that it has had the reverse effect. For most, the paperless office remains a myth. Look around your own office. Read Sellen and Harper’s The Myth of the Paperless Office.
To assess how green your workspace is, check:
- How many piles of paper do you see around you?
- How many of these are printouts of emails (or attachments)?
- How many email-enabled devices are running and driving up the level of electricity consumed?
- Of these email-enabled devices, how many do you really need going at one time?
- By how much has your demand for storage space increased as a result of the volume of email traffic?
Common retorts to the last question are that ‘Storage is cheap’, ‘It’s in the cloud’, ‘It’s unlimited’. All true but, however energy-efficient, these servers are still driven by electricity.
To enable email to support the green economy:
- Reduce the level of email traffic and amount of emails kept and especially in archive (.pst) files.
- Be daring and talk more.
- Avoid the trap of following up conversations with an email unless the matter is contractual. If it is, the email can be shorter as it need only be a summary of the agreed points.
The managing director of one international management accountancy firm recently asked his business systems team to provide a solution to the current paper and energy burn being generated by the increase in email storage systems. It’s a work in progress, and a total ban on using .pst files are some of the options now being considered.
Lowers the quality of communications
A recent survey by the DTI suggested that email can lower the quality of communications because of the sloppy ways in which people write emails and include jokes and other casual remarks. For more on this, see Chapter 13. Email allows one to get away with sloppy communications, especially those sent from a handheld device such as a BlackBerry or iPhone.
Shipley and Schwalbe (2007) suggest that to include the strapline ‘Sent from my BlackBerry’ acts almost as an acceptable apology for sloppy communications. Indeed, some users even add to the BlackBerry line with ‘Small keyboard, big thumbs’ asking for mistakes to be excused. What’s your view? These communications will affect your image so you must decide on the best course of action for your business.
To improve the quality of email communications:
- Decide what is best for you and your business: speed of response or slower response and better quality communications.
- For those managing businesses, check your email best practice policy for guidelines on email and compliance. Chapter 17 has more about this.
An email sent can imply the recipient has taken action
The biggest problem in communications is the illusion that it has taken place.
George Bernard Shaw
A common mistake. As seen in Chapter 1, many people read emails but actually then do nothing with them. Do not rely on either the email-read receipt or delivery receipt as confirmation that any action will be taken. Moreover, read receipts can smack of playing politics and make people feel even more like ignoring you.
Confidentiality
This is a major challenge and in many respects has nothing to do with the richness of the media used. An email is no more confidential than a postcard. There are three key reasons. First, anyone with access to the email server can read the content of an email if they are minded too, as illustrated by this example.
![]()
In 2008, an IT technician at the Body Shop was fined £850,000 for accessing confidential email which contained information about the state of Body Shop sales. He used the information to short the stock and bet on their share price falling.
Second, you think you have sent the email to the right Dave Smith but what happens if you haven’t? How many times have you had a message to the effect ‘Ignore last (and confidential) email’ message? Worse still is the ‘Sender wishes to recall this email’. We are all nosy and by the time the second email comes through most of us have opened the first one and seen something we really should not have done.
Third is the compromising situation in which you send a highly sensitive and confidential email to someone only to discover their PA is managing their inbox and sees it. Now you have compromised both yourself and possibly the PA. I conducted a survey across 300 PAs and administrators that revealed that 82 per cent had accidentally read confidential information at one time or another. While most managers would say their PA is the most trusted person in their business lives, there are still occasions when either they should not or do not want to see highly sensitive information.
![]()
There are several ways to reduce the risk of breaching confidentiality through email.
Do
- Mark the email confidential and warn the recipient if talking is not possible. As a recipient, use a ‘Rule’ to move all such emails to a folder which only you access and read.
- Turn off the auto-address feature.
- Send the information as a password-protected attachment – this cannot be seen by anyone checking in the mail server room.
- Encrypt the email if that option is available to you.
Don’t
- Use email – talk. Of course there is still nothing to stop the other person gossiping, but at least you have some control of the initial delivery of the information.
Attributes of email and media richness
These key attributes of email and their relationship to the richness of the medium are summarised in Figure 8.2. Use the summary as a quick reference template for assessing the optimum communication choice. Review the criteria listed and add others as appropriate to your situation.
Benefits of using the full range of communications channels
Precision of communication is important, more important than ever, in our era of hair-trigger balances, when a false or misunderstood word may create as much disaster as a sudden thoughtless act.
James Thurber
The downside of using ‘richer’ communications channels than email is that they generally take longer. A blog takes more time to write. Videoconferencing often means pre-booking the technology – although increasingly people now have Skype. Discussions with several contributors to this book were done through Skype, and the ability to see their faces greatly enhanced the quality of the discussion and helped build relationships.
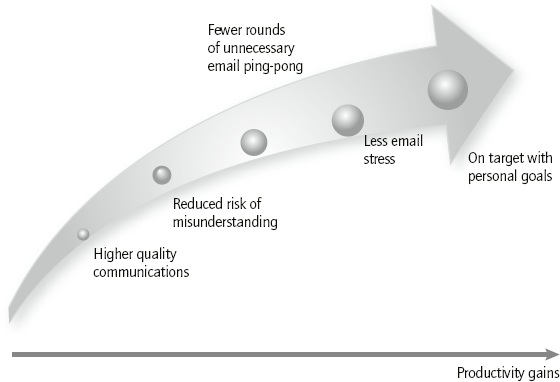
The upside is that widening your range and choice of communications media will enable you to save time and improve your own productivity, as summarised in Figure 8.3.
In addition, using a broader and richer range of communications provides opportunities to:
- widen the scope of the discussion and pick up useful information about other potential opportunities
- limit breaches of confidentiality
- develop a better understanding of related issues which might impinge on the business.
The goal of any communication should be ‘right message right first time’. This can only be attained through being selective about which channel you use and when.
- Email software is feature-rich. Nonetheless, email remains a thin medium that lacks the ability to convey any of the associated contextual and emotional information surrounding the message.
- Be more selective and daring in the channels you use.
- Here are seven ways to leverage the potential of email and mitigate the downsides of it being – at times – too easy and fast:
- Limit your use of email to simple factual messages. Choose a richer medium such as talking for complex, emotional messages, especially when there is a significant chance of a misunderstanding which could put you and your business at risk.
- Be very selective about who you include in ‘All user’ and ‘Cc’ emails.
- If things go pear-shaped, talk. Don’t default to the email audit trail, which is often only the symptom not the problem.
- Reduce the level of email stress by creating a ‘pull’ rather than a ‘push’ information culture – for example, posting general information on intranets in preference to sending ‘All user’ emails.
- Don’t assume a sent message will either be opened or actioned. Where action is needed, especially if it’s urgent, talk first and email later.
- Take adequate steps to reduce the risk of leaking confidential information.
- Write a ‘Rule’ to delay sending any email by at least two minutes.