16
Implementing Network Security
Cybersecurity professionals are continuously working to stay at least one step ahead of hackers and protect their organizations from new and emerging cyberattacks and threats. Different types of hackers compromise organizations and user accounts with different motives, such as for fun or just to prove a point to others within the community, while more organized groups of hackers typically work together for financial gain. The age of ransomware shook the world as no one was ready for such a type of threat that affected many organizations and continues to be a major one. The idea of encrypting data and asking for a ransom was a good approach to easily gain money and cryptocurrencies from victims.
While many cybersecurity professionals warn victims to not pay the ransom as there’s no guarantee of retrieving their data, many organizations have given in and paid the ransom with the hope that good faith will prevail and their most valuable asset – data – will be available once more. While no single system is perfectly secured against cyberattacks and threats, network security professionals use best practices and technologies on their network to reduce the risk of cyberattacks and protect their assets from hackers. Without network security solutions, organizations are simply left open to potential attacks from hackers around the world.
In this chapter, you will learn about common techniques used by network security professionals to improve the security posture of their network infrastructure and reduce the risk of a cyberattack. You will learn about network hardening techniques and their benefits, wireless security solutions and how they are used to mitigate wireless attacks, how to securely access your network using popular remote access methods, and various physical security practices within organizations.
In this chapter, we will cover the following topics:
- Network hardening techniques
- Wireless security techniques
- Remote connectivity methods
- Importance of physical security
Let’s dive in!
Network hardening techniques
Cyberattacks occur all the time; each day, there are many reports of unknown cyberattacks that have been discovered by various security organizations and security researchers around the world. However, many organizations do not realize their systems and networks have been compromised by a threat actor until months after the attack has occurred. The longer an organization takes to discover its systems and networks have been breached, the more time the hacker has to dig deeper into the network and install multiple backdoors while going undetected. Hence, implementing network hardening techniques reduces the risk of being compromised while improving the security of the network.
Implementing network security best practices helps network professionals ensure their network infrastructure, such as its network devices and security appliances, are properly secured against hackers, cyberattacks, and threats. While networking devices are designed to forward frames and packets to their destinations, network devices such as switches and routers have an operating system. If a hacker gains access to an organization’s network and discovers an outdated version of an operating system on a router or switch, the hacker can use an exploit to compromise the vulnerable operating system and take control of the device. This allows the hacker to redirect traffic or mirror users’ traffic.
Additionally, if the hacker can find a vulnerability within a security appliance such as an organization’s firewall, the hacker can attempt to exploit it and gain control of the device. If the firewall is compromised, the hacker can insert, modify, and delete rules on the firewall to permit malicious or suspicious traffic to enter and leave the organization’s network undetected.
The following are best practices for improving the security posture of your network infrastructure:
- Secure Simple Network Management Protocol (SNMP): SNMP is a common network protocol used by network professionals to manage their network devices and security appliances over a network. SNMP allows an SNMP Manager to gather information from the SNMP Agent that’s running on the network and security devices within a company. Additionally, SNMP helps network professionals monitor the performance and health status of their network and apply configuration changes to devices. SNMPv1 and SNMPv2 have bad security features such as no data encryption or authentication mechanisms, so these versions are not recommended to be used. However, SNMPv3 supports data encryption and user authentication between the SNMP Manager and SNMP Agent.
- Router Advertisement (RA) Guard: Within an IPv6 network, RA messages are used to create a stateless configuration. The IPv6 clients on the network send Router Solicitation (RS) messages to search for any IPv6-enabled routers on the network. When an IPv6-enabled router receives an RS message, it responds with RA messages back to the client. The RA Guard security feature is used to prevent a hacker from sending unsolicited or spoofed RA messages to clients on a network. The RA Guard security feature inspects and validates the authenticity of the RA messages from the sender.
- Port security: Port security is used to mitigate a Content Addressable Memory (CAM) Table Overflow attack from occurring on a network. In a CAM Table Overflow attack, the hacker injects thousands of frames with spoofed Media Access Control (MAC) addresses into a switch’s port. The CAM table on a Cisco switch is used to store learned MAC addresses; if the CAM table is full and continues to receive new source MAC addresses, the switch will flood any incoming frames out of all other ports. Therefore, the switches become a hub, allowing a hacker to capture any frames sent into the switch from other devices on the network. Additionally, port security is used to prevent unauthorized devices from connecting to the network and accessing resources. It inspects the source MAC address for any incoming frames into the switch’s port and prevents frames with unauthorized source MAC addresses.
- Enable DHCP snooping: DHCP snooping is used to prevent both DHCP spoofing and rogue DHCP servers on a network. DHCP spoofing occurs when a rogue DHCP server is connected to a network and provides false IP configurations to clients on the network. DHCP spoofing is dangerous within any organization because clients can lease incorrect IP addresses to Domain Name System (DNS) servers and the default gateway that’s owned and managed by a hacker on the network. When DHCP snooping is enabled on a switch, it builds a DHCP snooping binding database, which records the clients’ MAC addresses, IP addresses, DHCP lease times, binding types, Virtual Local Area Network (VLAN) numbers, and interface information on each untrusted switch port. DHCP snooping prevents any DHCP Offer and DHCP Acknowledgment messages from entering untrusted ports on a switch.
- Enable Dynamic ARP Inspection (DAI): DAI prevents Man-in-the-Middle (MiTM) and on-path attacks on a network. Additionally, DAI mitigates Address Resolution Protocol (ARP) poisoning and spoofing from occurring within an organization’s network. It leverages the entries within the DHCP snooping binding table and inspects the source MAC addresses that are learned on an untrusted port and match a client’s IP address. Once DAI is enabled on a switch, all ports are untrusted by default.
- Enable Control Plane Policing (CoPP): The control plane on a networking device is responsible for controlling how the entire network device operates and functions. The control plane is like the brain of the device – it manages both Layer 2 and Layer 3 forwarding mechanisms, routing and switching protocols, IPv4 and IPv6 routing tables, Spanning-Tree Protocol (STP), and more within the device. CoPP is used to protect the control plane within the network device by filtering any unsolicited inbound messages from threat actors that are seeking to gain unauthorized access to the device.
- Implement private VLANs: A private VLAN creates an isolated port/interface on a network switch. Therefore, any device that’s connected to a switch port that is assigned to a private VLAN will be isolated from other VLANs on the switch and network.
- Disable unneeded switch ports: Sometimes, network professionals do not disable unused or unneeded ports on their network switches. This leaves the network physically open, allowing anyone to connect an unauthorized device to the network. Disabling unused or unneeded switch ports simply allows the network professionals to administratively shut down the interface via the switch’s operating system, thus preventing unauthorized access to the network via those unused or unneeded switch ports.
- Disable unneeded network services: On a network, you will commonly find servers and network devices that have been configured to provide common network services and resources to clients. However, IT professionals sometimes forget to disable any network services that are no longer needed by clients on the network. For instance, if a network switch or router has Telnet enabled, a threat actor who’s on the network can attempt an on-path attack to intercept any login credentials between the IT professionals’ devices and the Telnet-enabled devices since Telnet sends messages in plaintext.
- Change default passwords: Devices are usually shipped to customers with a default password that’s configured by the vendor of the product. Many times, IT professionals do not always change the default username and password on these devices, which often leads to their network being compromised by a hacker. Hackers seek the easiest method to compromise their targets. Imagine if you were a hacker and you were able to log into someone else’s router using the default credentials of the device; this means that anyone can do the same.
- Password complexity/length: Setting a unique password on each user account or system reduces the likelihood of account takeover by a hacker. However, not everyone likes setting complex passwords on each user account. Configuring weak passwords increases the likelihood of a hacker being able to successfully use a dictionary or brute-force password attack and retrieve the password. There are many wordlist files on the internet that contain common and popular passwords used by people. A hacker can simply use a common wordlist and retrieve your passwords. Hence, IT professionals need to configure and enforce password complexity criteria for all users within their organization.
- Change the default VLAN: Managed network switches are shipped from their vendors with all physical ports assigned to a default VLAN. The default VLAN is simply the primary VLAN that is loaded onto a managed switch after the switch is powered on. Many new out-of-the-box switches have all their ports assigned to VLAN 1 by default, so if you connect end devices to any of the ports on a new switch, communication is allowed between all ports. Using the default VLAN is not recommended because a seasoned hacker who understands networking will know how easy it is to compromise all devices on the same VLAN. It’s recommended to implement multiple VLANs within an organization, such as assigning a unique VLAN to each organizational department. Overall, do not use the default VLAN.
- Patch and firmware management: Patch and firmware management are a set of procedures and processes that involve acquiring, testing, distributing, and applying system and firmware updates to devices within a network. For instance, IT professionals should download firmware and patches from the vendor’s website and not third-party websites on the internet. IT professionals should install the patches on company systems that are connected to a test environment, allowing the IT professionals to use these systems regularly for 2 weeks or more to identify any issues with the newly patched systems. If no issues are found during the testing phase, they can roll out the patches systematically to one organizational department at a time and monitor whether users are reporting any issues of system instability or application crashes.
- Implement an Access Control List (ACL): Routers allow network professionals to implement ACLs to filter traffic between networks. ACLs can filter traffic based on the five tuples: source IP address, destination IP address, source MAC address, destination MAC address, and protocol. Essentially, routers can function as a packet filtering firewall within an organization. While packet filtering firewalls are unable to filter application-layer traffic compared to next-generation firewalls, they can still provide a basic layer of security between IP networks.
- Role-based access: Role-based access is a type of access control model that is designed to only permit a user with the privileges needed to perform their job duties, nothing more. This type of access control model can be assigned to users via Group Policy Objects (GPOs) within a Windows-based environment with Microsoft Windows Server. For instance, a GPO can be created by the systems administrator or security professional who defines the user privileges for all employees who work within the customer service department of an organization. Implementing role-based access control (RBAC) ensures a person with a specific job role has all the necessary privileges to perform their job efficiently while ensuring the user doesn’t abuse any additional privileges while being logged into any system on the network.
- Firewall rules: By default, all firewalls have an implicit deny rule that simply denies any traffic from any source to any destination. This rule is typically found as the last rule within the access control list on the firewall. Simply put, the implicit deny rule will automatically block any traffic that’s not explicitly allowed through the firewall by the security professional. The implicit deny rule is needed to ensure all unwanted traffic is blocked, thus allowing the security professional to create rules to permit specific traffic types only while blocking everything else. Explicit deny rules are created by a security professional to deny (block) specific traffic between a source and a destination. The primary difference between the implicit deny and explicit deny is that the implicit deny rule is automatically created by the firewall, while the explicit deny rules are created by the security professional.
Additionally, firewall rules are used to filter traffic between networks that are directly connected to the firewall appliance. These firewall rules are created by security professionals using various criteria such as source IP address, destination IP address, source port number, destination port number, network protocol type, transport layer protocol type, application layer type, and so on. It’s recommended that these rules are organized so that more specific firewall rules are placed at the top of the list while less specific and general firewalls are placed beneath. An example of a specific firewall rule is a security professional who wants to restrict HTTP traffic from a PC on the internal network to a destination web server on the internet. Here, a general firewall rule would restrict all traffic from one network to another.
- Security Information and Event Management (SIEM): A SIEM is a security system that collects all the logs of devices on a network, performs data de-duplication, and helps security professionals quickly identify potential threats on their network. Simply put, security professionals configure their network devices, security appliances, and servers to send their log messages to the SIEM. The SIEM will both correlate and analyze all the logs collected in real time and trigger alerts for any potential security event on the network. Typically, within medium to large organizations, security professionals implement a SIEM system centrally in their network to assist with monitoring security events in real time.
Having completed this section, you have learned about some common techniques and best practices that are used to improve the security posture and harden a network infrastructure within an organization. Next, you will discover best practices for securing a wireless network.
Wireless security techniques
Wireless networking allows users to connect their wireless, mobile devices to an access point to access the resources on a wired network and vice versa. There are many advantages to implementing a wireless network infrastructure within homes and organizations, with the most obvious benefit being that wireless networking reduces the number of physical cables needed to allow clients to access the network. It’s as simple as installing one or more access points so that they’re physically connected to a network switch and configuring the wireless settings with each access point to broadcast a Service Set Identifier (SSID) and network details.
While wireless networking supports mobility, allowing users to roam around the vicinity of a wireless network, many threats and wireless-based attacks are commonly used by hackers to compromise the security of an access point, which compromises the wireless network and its users. For instance, since an access point uses radio frequencies emitted from antennas to transmit Wireless Local Area Network (WLAN) frames, a threat actor does not need physical access to the access point – they simply need to be within range of the wireless signal generated from the access point to launch an attack against it. Furthermore, if a threat actor were to gain unauthorized access to the wireless network, non-tech-savvy people would not think about frequently checking their network for any unauthorized users and devices.
Many organizations and home users are not always aware that their networks and systems have been compromised by a hacker until it’s too late. At this point, the hacker can gain control over critical systems and Internet of Things (IoT) devices and create multiple backdoors into the network. For instance, imagine that a hacker has compromised a home wireless network and can identify and compromise a home security monitoring system that’s connected to the same network. The hacker can either choose to monitor the victims’ activities or disable their security monitoring solution. Hence, it’s important to secure wireless networks using best practices to reduce the risk of a potential cyberattack and various threats.
SSID considerations
Typically, when setting up a wireless network for a home, office, or organization, it’s important to consider the SSID or the network name. Many organizations commonly configure their SSIDs using the name of their company, thus providing the convenience for employees to easily discover and connect to their wireless network. However, this convenience also helps a hacker who’s within the vicinity to easily find the company and its wireless network. Hence, setting the SSID as the name of your organization makes your wireless network a target.
Furthermore, many businesses commonly use the default SSID that’s configured on the access point by the vendor. For instance, vendors commonly pre-configure their access points with an SSID that contains the name of the vendor and device model. A hacker can use this information to research any known security vulnerabilities of a specific device and attempt to exploit its security weaknesses.
The following screenshot shows the common user interface of a Cisco Linksys E1000 access point:
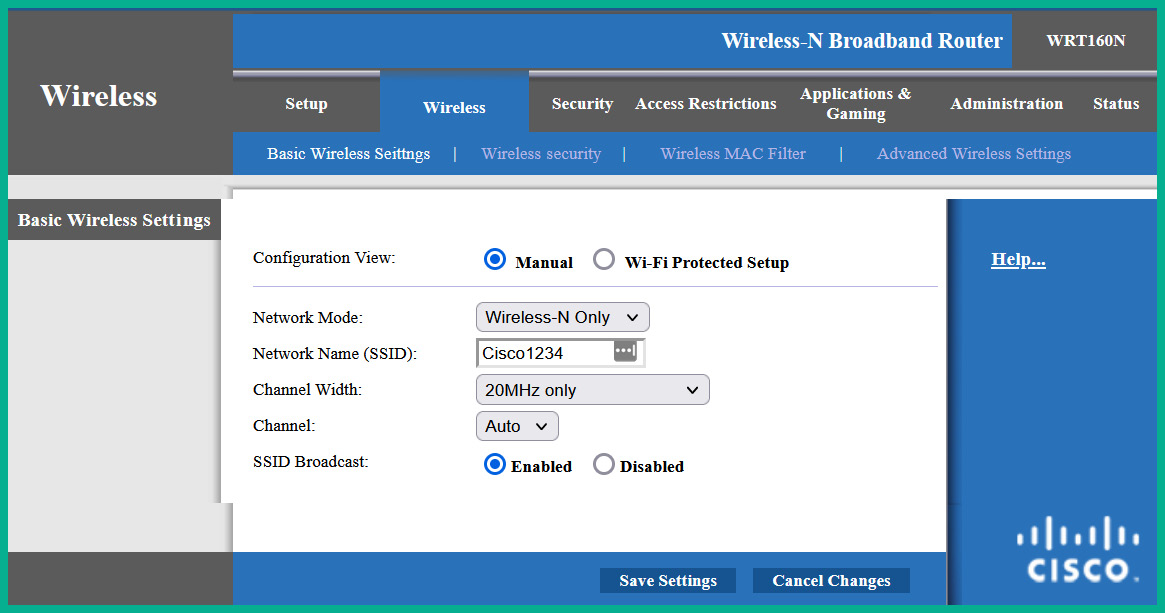
Figure 16.1 – Access point wireless settings
As shown in the preceding screenshot, when logged into an access point, selecting Wireless | Basic Wireless Settings will allow you to configure the network mode, SSID, and channel on the device. The access point is using the default SSID that’s pre-configured by the vendor before it’s shipped. It’s recommended to change the default SSID and set a network name that does not identify your specific network or organization. This technique does not prevent but deters a threat actor.
Important note
Do not use Wi-Fi Protected Setup (WPS) as there are many unresolved security vulnerabilities.
Additionally, the SSID Broadcast feature allows you to configure the access point to advertise the SSID to all wireless clients within the vicinity. By default, the SSID Broadcast feature is enabled, which makes it easier to discover the wireless network. However, disabling this feature will allow the access point to still advertise its presence without including the SSID within the WLAN frames, which means wireless clients will not detect the SSID within their list of nearby available wireless networks. From a cybersecurity perspective, a seasoned hacker can discover a hidden wireless network within a few minutes or less. Therefore, disabling the SSID Broadcast feature will not prevent a hacker from discovering the hidden wireless network and launching wireless-based attacks.
Password considerations
Whether you’re implementing a wireless network within a home or an organization, you should always set strong, complex passwords to reduce the likelihood of a hacker being able to retrieve those passwords and gain access to your network. I’ve seen many organizations configure weak and guessable passwords during my career and while it might be surprising to aspiring network professionals, it’s quite a common and bad practice within many industries. While some companies think their wireless networks are safe because a password or passphrase prevents a hacker from accessing the network, they need to consider the complexity of the password or passphrase.
The following are some guidelines to help improve the complexity of a password or passphrase:
- It should contain a mixture of alpha-numerical characters
- It should contain a mixture of uppercase and lowercase letters
- It should contain special characters and symbols
- It should be more than eight characters in length
- It should not contain easily identifiable data such as names, dates, or places
- It should not contain repeatable characters
If you’re having difficulties creating unique complex passwords, consider using an online password generator. The following are a few examples:
- LastPass Password Generator: https://www.lastpass.com/features/password-generator
- Bitwarden Password Generator: https://bitwarden.com/password-generator/
- 1Password Password Generator: https://1password.com/password-generator/
The following screenshot shows an example of a password that meets the criteria that were chosen within the password generator:
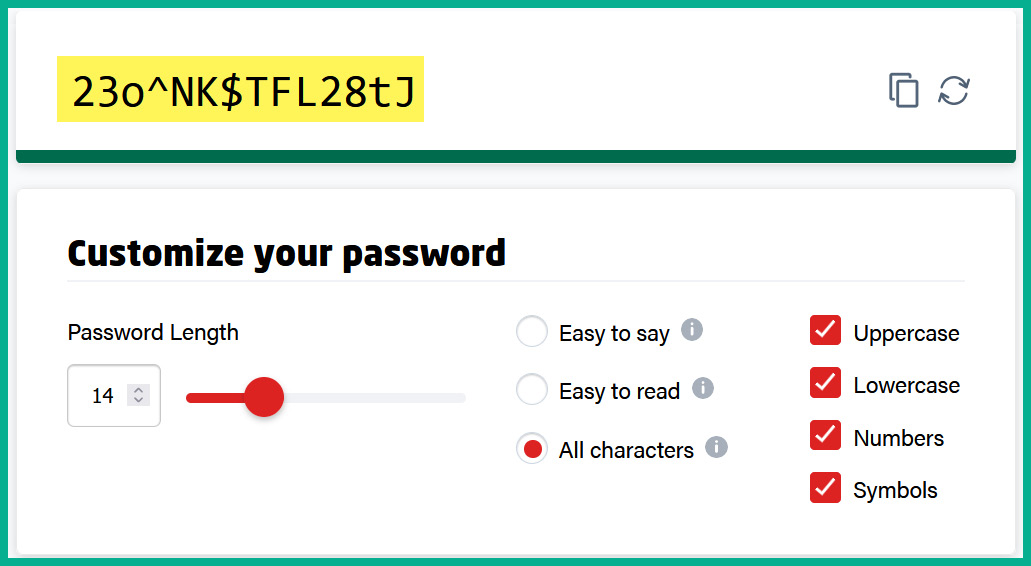
Figure 16.2 – Complex password
The Pre-Shared Key (PSK) field within the wireless security settings on an access point allows network professionals to configure a password or passphrase as the PSK value. This PSK is used with the data encryption algorithm to encrypt the data as it is sent over the wireless network.
The following screenshot shows the wireless security window of a Cisco Linksys E1000:
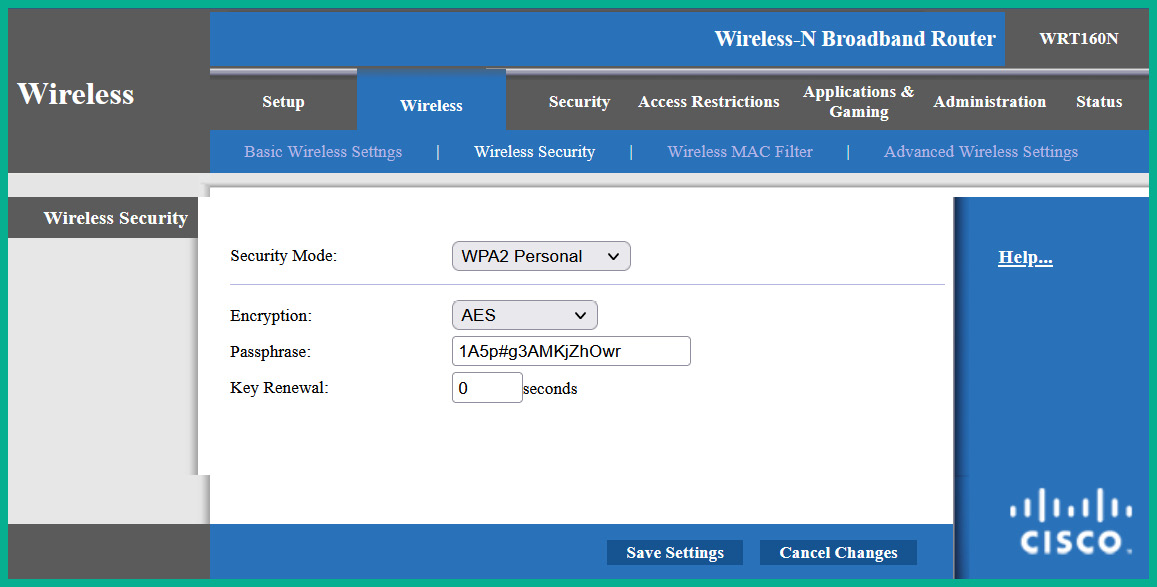
Figure 16.3 – Wireless security window
As shown in the preceding screenshot, the WPA2 Personal wireless security standard was selected, and a complex password was configured as the PSK value. Keep in mind that the wireless security feature is disabled by default on access points; network professionals shouldn’t use default configurations as it can lead to a potential cyberattack.
Older access points support the WPA2 wireless security standard, while newer access points support WPA3, the latest version. If you’re configuring your access point to use the WPA3 wireless security standard, ensure your wireless clients also support WPA3. If you’re connecting wireless clients that use WPA2 to an access point that’s configured with WPA3, the access point will scale down from WPA3 to WPA2, which allows the wireless clients to establish a connection. Hence, the wireless network will not benefit from the improvements of WPA3 in this situation.
MAC filtering
MAC filtering is a common security feature of access points that allows a network professional to configure either a whitelist or blacklist of MAC addresses. For instance, the whitelist contains a set of MAC addresses from wireless clients that are permitted to connect to the wireless network; all other devices will be denied automatically. On the other hand, the blacklist contains the MAC addresses that are not allowed to access the wireless network. Creating the whitelist (permit) or blacklist (prevent) helps network professionals add an extra layer of security to their wireless network.
If a hacker can retrieve the password or passphrase of the wireless network, the hacker will not be able to connect to the wireless network if their device’s MAC address is restricted when MAC filtering is active.
The following screenshot shows the user interface of the MAC filtering feature on a Cisco Linksys E1000:
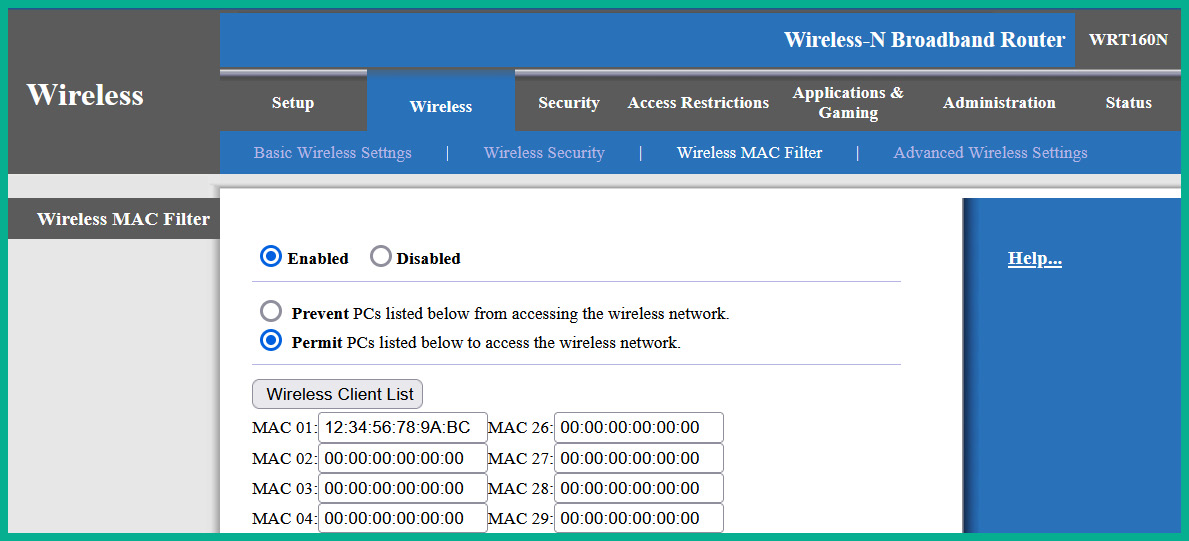
Figure 16.4 – MAC filtering user interface
As shown in the preceding screenshot, the MAC filtering feature is enabled, and it’s configured to permit the set of MAC addresses within the list. Therefore, network professionals need to ensure the MAC addresses of authorized devices are included within the list of permitted addresses.
While MAC filtering is an additional layer of security on wireless networks, a seasoned hacker can determine the MAC address of any wireless clients that are associated with an access point. While MAC filtering can be bypassed, it is still considered to be a layer of security on a wireless network.
Antennas and power levels
Without antennas on an access point, it simply won’t be able to transmit radio frequency signals to nearby wireless clients. The type, placement, and power levels on these wireless antennas affect the coverage of the wireless signals that are generated from the access point. For instance, some access points contain internal antennas while others support external detachable antennas. The main difference between antenna implementation is quite obvious – that is, the internal antennas can’t be removed or changed by the user, while the external antennas usually can be removed. Additionally, access points with external antennas are known to provide better coverage compared to those with internal antennas.
The following figure shows the detachable antennas of an access point:

Figure 16.5 – Detachable antennas
As shown in the preceding figure, these are omnidirectional antennas, which are designed to transmit radio frequencies in all directions at the same time. The omnidirectional antennas are common on access points as they provide excellent coverage for office spaces within buildings and homes.
Sometimes, network professionals implement a wireless network to bridge two buildings over a large distance, ranging from a few meters to kilometers in distance. Using parabolic antennas, network professionals can implement one antenna on the rooftop of each building while ensuring there’s a line of sight between them to create a point-to-point connection.
The following diagram shows a visual representation of using parabolic antennas between buildings:

Figure 16.6 – Parabolic antennas
As shown in the preceding diagram, parabolic antennas have a dish-like shape, which allows the antennas to radiate the radio frequencies in a specific direction compared to omnidirectional antennas. Network professionals can achieve distances over a few kilometers using parabolic antennas, provided there are good weather conditions and a line of sight between the source and destinations. If one parabolic antenna is misaligned, the throughput, latency, and connection quality will be greatly affected. Fortunately, vendors who sell commercial parabolic antennas usually provide an application that allows network professionals to test the signal quality between parabolic antennas and measure the throughput between sites.
The yagi antennas are another type of directional antenna that is used in wireless networking. This type of antenna is one of the more popular directional antennas due to its size and portability compared to large parabolic antennas.
The following figure is of a yagi antenna:
Figure 16.7 – Yagi antenna
The access point provides sufficient power to each antenna. Some access points allow network professionals to reduce the power levels on the antennas to reduce the coverage of the wireless signal within the vicinity. As an aspiring network professional, you’ve probably been thinking, why reduce the coverage area? Isn’t the goal to ensure there is sufficient coverage to allow all authorized users to access the network? Simply put, network professionals need to ensure their wireless networks provide sufficient coverage to all their authorized users within the vicinity, such as their office spaces within a building. However, these wireless signals can penetrate the wall of the building and spread to public spaces such as the neighboring buildings and the people who are walking along the street.
A hacker can be sitting at a coffee shop across the street and detect your organization’s wireless network because the signal is strong enough to travel outside the compound. Reducing the power levels on the antennas via the user interface of the access point will reduce the range/coverage of the wireless signal, thus reducing the likelihood of a hacker being able to detect the wireless network from a long distance. However, it’s important to understand that reducing the power levels will reduce the coverage area, and authorized users may be affected.
Geofencing and captive portals
Geofencing is a feature within some mobile operating systems, laptops, and applications that leverages the Global Positioning System (GPS) and even Radio Frequency Identification (RFID) on mobile devices to define a geographical boundary within the real world. IT professionals can configure a company-owned mobile device with geofencing to trigger a set of rules when the device either enters or leaves the building (geographic boundary). For instance, many geofencing applications use Google Maps/Earth to define the boundaries using a satellite view of the area, while other applications allow you to define the longitude and latitude positions on a web-based map.
Organizations can take advantage of geofencing on company-owned devices. For example, if a device is within an authorized geofence virtual barrier, various features and applications will be readily available for the user of the device. If the user carries the device outside the virtual barrier, an automated restriction will be applied to various features and applications on the mobile device.
Captive portals are commonly used within hotels and coffee shops to provide a web page that lists the terms and conditions for using the wireless network. Captive portals are commonly used for marketing purposes and provide login pages for users. For instance, when connecting to the free Wi-Fi at a local shop, you’ll be presented with a captive portal before you are granted access to the internet. On the captive portal, you will see the terms and conditions, along with some essential marketing advertisements. Once you’ve accepted the agreement, you’ll be able to access the network. Captive portals are also used within hotels, providing a web portal to allow authorized guests to authenticate themselves before accessing the internet.
Client isolation
Implementing client isolation allows network professionals to logically place specific wireless clients into an isolated network, preventing any communication between the isolated client and other devices that are associated with the access point. Imagine if an organization allowed guest devices and company-owned IoT devices to be connected to the same wireless network, allocate IP addresses from the same subnet, and directly communicate with each other. If a guest connects a malware-infected mobile device to the company’s wireless network, the malware can attempt to exploit the security vulnerabilities found on the IoT devices on the same wireless network.
One recommendation would be to improve the security posture of the IoT devices that are on the network. However, IoT devices do not run the same type of operating systems as traditional computers and servers – they run specialized firmware that is strictly created by the vendor of the device. Additionally, IoT devices depend on their vendor to provide regular firmware updates to resolve any bugs and security issues that may arise. However, not all vendors focus on developing updates for the firmware of their devices after the device is manufactured or even after a couple of years. For instance, Android OS is one of the most popular mobile operating systems within the mobile industry. The company, Android, has set its mark on providing operating system updates for 2 to 3 years after the launch and security updates up to 5 years after launch.
It’s recommended to set up wireless client isolation, such as creating a guest wireless network for all guest devices to join the network. The guest wireless network only provides access to the internet and restricts access to any internal networks. Many organizations that provide complimentary Wi-Fi access to their customers often create a guest wireless network to allow their visitors and customers to access the internet while restricting their access to the corporate network and resources. Additionally, network professionals can create another wireless network that’s isolated for all company-owned IoT devices. Therefore, all IoT devices are on one network, the guest devices are connected to another, and employees are connected to a third wireless network.
Wireless authentication protocols
The Extensible Authentication Protocol (EAP) is a framework that’s commonly used on IEEE 802.11 wireless networks; it defines how systems are authenticated onto the network. There are different variations of EAP that are commonly used on wireless networks that use Wi-Fi Protected Access (WPA) and Wi-Fi Protected Access 2 (WPA2).
The following are the different variations of EAP:
- EAP over LAN: This type of EAP is used on networks that support IEEE 802.1X for Network Access Control (NAC), which allows devices on a wired network to authenticate to an Access Control Server (ACS) running the Remote Authentication Dial-In User Service (RADIUS) service.
- Lightweight EAP (LEAP): This is a Cisco-proprietary version of EAP that uses passwords only and not digital certificates during the authentication process. This version of EAP was on Microsoft’s version of Challenge-Handshake Authentication Protocol (CHAP), known as MS-CHAP, so it contains the same security concerns.
- Protected EAP (PEAP): This variation of EAP was designed by various organizations such as Cisco, Microsoft, and RSA Security to provide EAP for authentication. This version encapsulates the EAP message within a security (TLS) tunnel and uses digital certificates to improve the authentication process on both wired and wireless networks.
- EAP Flexible Authentication via Secure Tunneling (EAP-FAST): This version of EAP was created by Cisco as a replacement for LEAP, which was implemented on wireless networks that used Wired Equivalent Privacy (WEP) as the wireless security standard.
- EAP over TLS (EAP-TLS): This version of EAP is transported over TLS tunnels for better security. EAP-TLS uses mutual authentication where both the client and server exchange digital certificates.
- EAP Tunnel TLS (EAP-TTLS): This version of EAP also supports TLS tunneling over the network. In EAP-TTLS, only the server needs a digital certificate.
Next, you will discover various installation considerations that can improve the performance of a wireless network.
Installation considerations
Before implementing a wireless network within an organization, it is important to perform a wireless LAN survey to determine the number of access points needed and the placement of these devices within the building or company. Typically, a network professional will use a laptop computer with a wireless monitoring application such as InSSIDer to monitor the wireless signal strength, an access point that’s preferred by the company, a floor plan of the building, an electrical extension cord, and writing materials.
The network professional will connect the access point to a power outlet and leave it on the floor, then use the wireless monitoring application while walking further away from the access point to observe the wireless signal strength and mark the areas on the floor plan where the signal is weaker. Then, it connects the access point to an area where the signal is weak or absent to continue performing the site survey. This process is repeated until the network professional has covered the entire floor plan, indicating the placement of all access points and their coverage areas. This allows the network professional to determine the number of access points needed to provide maximum coverage and their placement within the building or compound.
The following figure shows a typical scale from a wireless monitoring application:
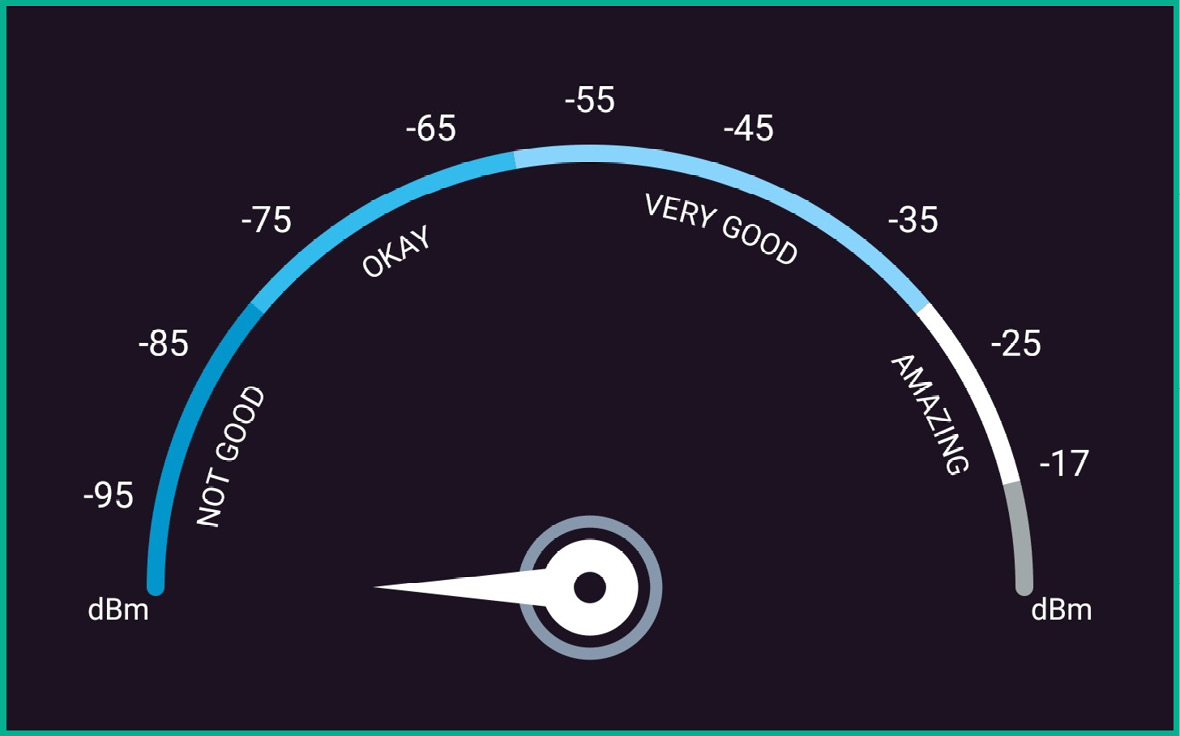
Figure 16.8 – Wireless signal scale
As shown in the preceding figure, this scale helps network professionals easily determine whether their mobile device, such as a laptop or smartphone, is too far away from the access point, or whether the wireless signal is too weak. Therefore, you want to ensure all the wireless clients on the network have amazing to very good signal. There might be a few clients who will experience okay signals on their mobile devices, but you need to remember that as devices move further away from the closest access point, the signal will become weaker.
Tip
There are many free Wi-Fi analyzer applications that all perform the same core functions: measure signal strength and operating channels and identify nearby wireless networks.
The following screenshot shows a WiFi Analyzer application detecting nearby wireless networks and their operating channels:
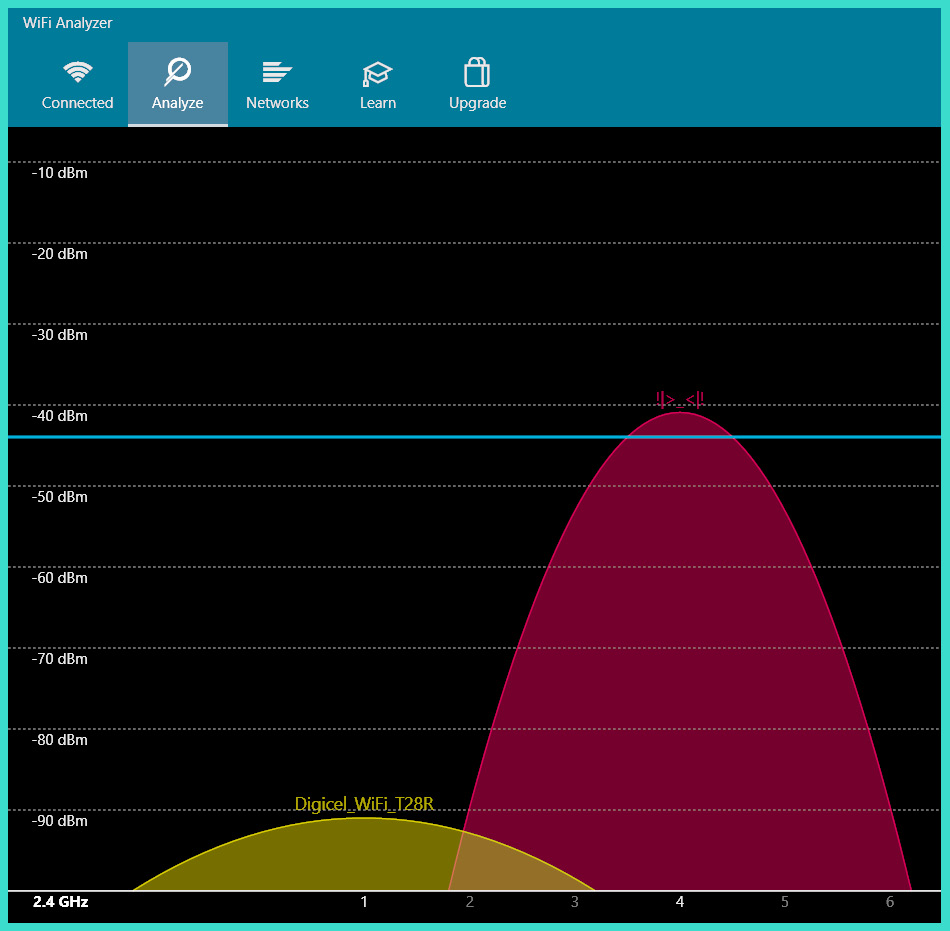
Figure 16.9 – WiFi Analyzer
As shown in the preceding screenshot, the WiFi Analyzer application can show the number of wireless networks found within the vicinity, their signal strength based on the location of the device running the wireless monitoring application, and the operating channels of each wireless network. Network professionals should ensure their wireless networks are not using any channels that overlap with other nearby access points.
Remote connectivity methods
A Virtual Private Network (VPN) provides a secure channel for communication over an unsecure network such as the internet. VPNs allow organizations to interconnect their remote offices securely without the need for a managed solution such as a Wide Area Network (WAN) from a regional Internet Service Provider (ISP). Many organizations around the world prefer a WAN because the service provider is responsible for establishing, maintaining, and troubleshooting any issues with the service to the customer. However, managed services from service providers cost money and not all organizations have the financial resources for such services. An alternative, cost-efficient solution is to implement a VPN to interconnect remote branch offices around the world. Many enterprise routers and firewall appliances support VPN technologies and allow network professionals to implement both site-to-site and client-to-site VPNs without spending a lot of money on managed services.
Important note
The client-to-site VPN was previously known as a remote access VPN.
VPNs use a set of technologies such as authentication protocols, data encryption algorithms, and integrity-checking algorithms to ensure a secure, encrypted tunnel is established to provide confidentiality, integrity, and authenticity. A site-to-site VPN allows organizations to interconnect their remote offices using a secure and free method over the internet. To set up a site-to-site VPN, the following resources are needed at each remote branch office:
- An internet connection
- A VPN router or firewall
- A static IP address
The following diagram shows a site-to-site VPN interconnecting two office locations:
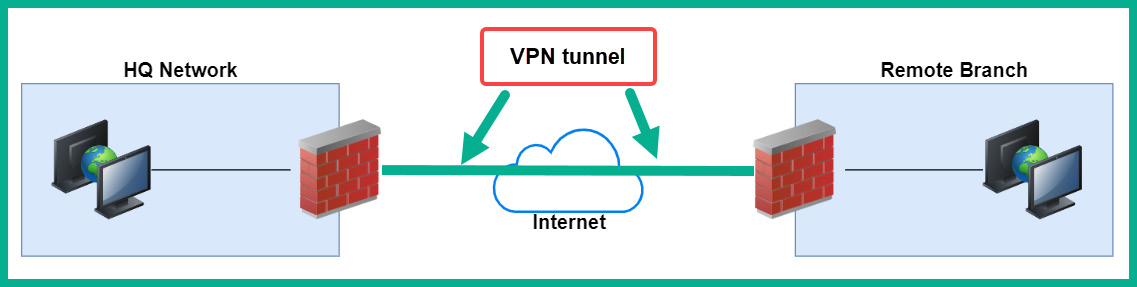
Figure 16.10 – Site-to-site VPN
As shown in the preceding diagram, two branch offices are both interconnected using a site-to-site VPN. Additionally, a firewall is placed on the internet edge at each location and is assigned a static, public IP address on both devices. If the IP address on each device changes, the VPN tunnel will be broken. Furthermore, if a user at the remote branch wants to access a service at the head office, the user’s traffic will be sent from their computer to the firewall; then, it’s sent through the VPN tunnel directly to the firewall at the head office. While the traffic is passing through the VPN tunnel, it is encrypted to prevent any unauthorized users and devices from seeing the data. Once the firewall at the head office receives the message, it’s decrypted and forwarded to the destination server on the network.
Important note
The device that is providing the VPN service, such as a firewall, is referred to as a VPN concentrator.
When using a site-to-site VPN, internal users are not aware that their messages are being encrypted and decrypted as they’re being sent between remote offices. This is because the data encryption and decryption process takes place on the branch firewalls and not on their computers. Site-to-site VPNs have many benefits, such as cost savings and security, but the disadvantage is that network professionals are responsible for configuring, maintaining, and resolving any issues with the VPN service between remote branches.
Important note
There are free, open source firewalls that allow network and security professionals to implement site-to-site and remote access VPNs such as pfSense (https://www.pfsense.org/).
Client-to-site VPNs are more common in organizations that support teleworkers and remote working. As its name suggests, a remote access VPN is a type of VPN solution that allows a remote worker to securely connect and access resources on the corporate network. Remote workers can securely connect from the comfort of their homes, hotels, coffee shops, or anywhere with an internet connection. The VPN ensures all data between the teleworker’s computer and the corporate network is encrypted to provide confidentiality and data security.
The following diagram shows a client-to-site VPN:
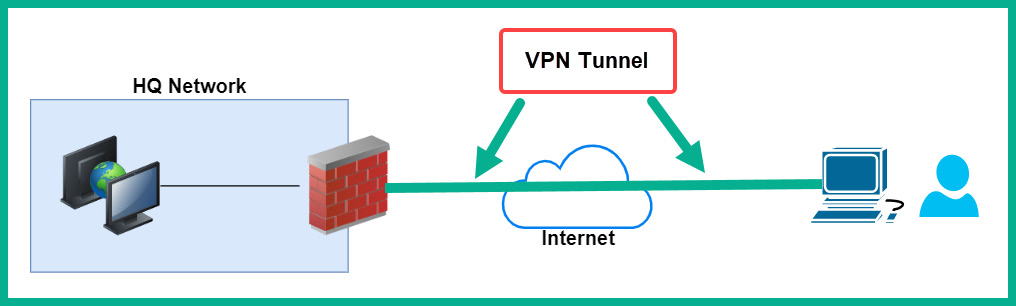
Figure 16.11 – Remote access VPN
When using a client-to-site VPN, a VPN client is installed on the teleworker’s computers, and a VPN firewall is configured on the corporate network to access inbound VPN connections and apply policies to the authorized users. When the user wants to access resources on the corporate network, the user launches the VPN client and enters their user credentials, such as a username and password, to authenticate to the VPN firewall on the company’s network. This type of VPN establishes a secure tunnel between the user’s computer and the firewall over the internet.
The following screenshot shows the simplified user interface of the Cisco AnyConnect Secure Mobility Client on a user’s computer:
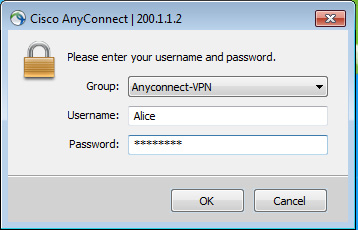
Figure 16.12 – VPN client user interface
Typically, VPN clients allow a user to select a pre-configured profile that contains the details needed to establish a connection to the firewall over the internet. The user simply needs to enter their credentials and connect.
Network professionals can configure client-to-site VPNs to operate in one of the following modes on the user’s device:
- Full tunnel: This allows outbound traffic from the teleworker’s computer to be sent through the VPN tunnel. Therefore, if the user wants to access a resource on the internet, the traffic is routed through the VPN tunnel to the corporate firewall, then out to the internet, and vice versa. This mode is not recommended for remote workers because the corporate firewall applies policies to both inbound and outbound traffic, which has the potential to restrict the teleworker from accessing various websites.
- Split tunnel: If the teleworker has to access a resource on the corporate network, the VPN client ensures the traffic is routed through the VPN tunnel, while all other traffic is routed directly through the internet.
A clientless VPN is a type of VPN solution that does not require a VPN client on the teleworker’s computer. This type of VPN allows the teleworker to log in via a web portal using a standard web browser to access the company’s resources. A clientless VPN provides data encryption using TLS over an HTTPS connection between the client’s web browser and the firewall. This type of VPN is suitable for providing users with quick and easy access to resources that can be embedded into a web portal.
Remote access methods
As an aspiring network professional, you will need to remotely connect and access systems over your network. Various in-band management methods allow an IT professional to securely access a system over a network, some of which are as follows:
- Remote desktop connection: The Microsoft Windows operating system uses the Remote Desktop Protocol (RDP), which allows IT professionals to establish a remote desktop connection between their computer and the destination system. On a remote desktop connection, the IT professionals will see a graphical user interface of the destination system as if they’re right there, allowing them to remotely control the system.
- Virtual Network Computing (VNC): VNC is a common remote access method that uses the Remote Frame Buffer (RFB) protocol. It is commonly used by IT professionals for its wide support on many operating systems and being mostly open source to users. VNC allows IT professionals to share the desktop experience and control the system remotely over a network.
- Remote desktop gateway: Within large organizations, IT professionals commonly implement a remote desktop gateway, which allows a user to secure access to RDP-enabled servers from outside the organization’s network. For instance, let’s say there’s an IT professional who is working from home and securely connects to the remote desktop gateway using an SSL or TLS tunnel. Once connected to the remote desktop gateway, the IT professional will be able to use RDP to connect to any internal RDP-enabled server.
- Secure Shell (SSH): SSH allows IT professionals to securely connect to a remote device using the Terminal. SSH is a secure protocol that provides terminal access to remote systems. This differs from Telnet, which is unsecure and does not encrypt data between the source and destination.
- Virtual Desktop Infrastructure (VDI): After setting up a virtual machine within a data center or on the cloud, the user can connect to a pre-built desktop environment, allowing the user to interact with the desktop environment from any device, such as a mobile device with a web browser. The connection between the mobile device and the VDI on the cloud uses a secure connection such as SSH or TLS with HTTPS.
But what if the internet service is down or portions of the internal network within an organization are unavailable? How will network professionals connect to their network devices and security appliances for troubleshooting? Implementing out-of-band management allows network professionals to access devices when a network connection is unavailable. On many networking devices, there are USB, serial, or console interfaces, which allow network professionals to physically access the management interface of the device. Additionally, some network devices allow network professionals to connect an internet modem directly to a management port on the device, allowing remote access to the device.
Having completed this section, you have discovered the importance and concepts of VPN and remote connectivity methods. In the next section, you will explore physical security.
Importance of physical security
As an aspiring network professional, it’s important to understand the role physical security plays within organizations and the various techniques that are used to protect assets from malicious activities. Without physical security, anyone can simply walk into restricted areas within a company and access systems, or steal and even tamper with assets. Organizations must implement various detection and prevention controls within their compound to reduce the risk of a physical threat.
Important note
Detection methods are simply deterrents and do not prevent a physical threat from occurring, while prevention methods allow security professionals to implement a type of preventative control to stop the threat from occurring.
The following are common detection methods:
- Camera: Implementing a Closed Circuit Television (CCTV) system provides security personnel with visibility into various areas within a compound or remote location. Some camera systems can identify various objects and support motion detection. Often, these camera systems are all connected and record footage over time.
- Asset tracking tags: Asset tracking tags allow IT professionals to create a record of every asset owned by the company. Additionally, these tags can be placed on anything such as laptops, network devices, security appliances, and other equipment. The information from asset tags can be integrated with financial records and audits within the company. These tags help IT professionals track when the device was acquired, its warranty, and other relevant information.
- Tamper detection: Since IT professionals cannot physically watch all the equipment within the company all the time, implementing tamper detection on devices allows the system to monitor itself for any form of tampering done by the user. For instance, manufacturers implement a physical seal that is broken if the device is opened; this can only be replaced by a service agent or vendor. Additionally, IT professionals can implement hardware tampering sensors within the chassis (case) that identify if the case was opened or removed.
The following are common prevention methods:
- Employee training: Training all employees regularly on the dos and don’ts helps improve the physical security within the organization. Implementing proper signage that’s visible to everyone helps ensure everyone understands what’s allowed and what’s not.
- Access control hardware: Organizations commonly implement physical security such as gates and locks to prevent unauthorized access to the building or various zones within the compound. These access control hardware systems are usually connected to a network, which allows security professionals to perform real-time monitoring and control over these systems.
- Badge readers: Many organizations implement an electronic system that uses a pin or card system, which allows the employee to use the pin or card to access the building. This system is closely managed and controlled, allowing security professionals to monitor who accesses the area and when.
- Biometrics: This is a common type of authentication system that allows a user to use themselves to authenticate and verify their identity to the system. Biometrics involves fingerprint, retina, facial, and voice metrics to verify someone’s identity. A user needs to be enrolled in the system before it can be effective. For instance, once a user’s fingerprint has been scanned, it’s converted into a mathematical representation and stored on the system.
- Access control vestibule: This was previously known as a mantrap, which prevents unauthorized people from tailgating an employee into a secure area within a building. It’s usually a very small room that contains two doors: one door allows access into the vestibule and another allows them to exit. However, only one door can be opened at a time; the other door is locked. Therefore, a person has to open one door to enter the vestibule and close it upon entering; then, they will be allowed to open the other door to exit the vestibule.
- Locking cabinets: Server racks should be locked at all times when an IT professional is not performing any physical work on the servers. However, the responsibility of locking the ranks is managed by the owner.
- Smart lockers: These are safe and automated lockers that allow a retailer to deliver items to customers at a specific location. When the customer arrives, they enter a code or pin to access the smart locker and collect their purchased items. Smart lockers reduce the risk of theft.
The following are some common asset disposal methods:
- Asset disposal: Asset disposal focuses on how to securely destroy assets or media that contain sensitive data. Without properly destroying the data, anyone can attempt to retrieve the data and use it for malicious purposes.
- Factory reset/wipe configuration: Clearing the device’s configurations ensures no one will be able to determine how the device was used within an organization or determine either the VLAN or IP configurations. A factory reset will restore the original default configurations on the device and remove any customized settings.
- Sanitize devices for disposal: Before disposing of storage media, it’s important to sanitize or wipe the media devices thoroughly to ensure data is not recoverable.
Having completed this section, you have learned about various techniques and methods that can be used to improve physical security within an organization. Now, let’s summarize this chapter.
Summary
In this chapter, you learned about popular and common network security solutions and strategies that are used within organizations to prevent and mitigate various types of cyberattacks and threats. Most importantly, they are used to improve the security posture of the network infrastructure. You also learned about network hardening techniques, wireless security solutions, remote access methods and technologies, and how physical security plays an important role within many organizations.
I hope this chapter has been informative for you and is helpful in your journey toward learning networking and becoming a network professional. In the next chapter, Chapter 17, Network Troubleshooting, you will focus on performing network troubleshooting to resolve issues that are common on modern networks.
Questions
The following is a short list of review questions to help reinforce your learning and help you identify areas that may require some improvement:
- Which of the following can be used to prevent an unauthorized device from accessing the resources on a wired network?
A. Router guard
B. DHCP snooping
C. Port security
D. Root guard
- Which of the following can be used to prevent MAC spoofing on an internal network?
A. Dynamic ARP inspection
B. Router guard
C. MAC snooping
D. Root guard
- Which of the following can be used to ensure only authorized clients are associated with an access point?
A. Disable the SSID broadcast
B. Implement AES encryption
C. Implement MAC filtering
D. All of the above
- What can a network professional do to reduce the coverage of a wireless network?
A. Turn off the access point when it’s not in use
B. Reduce the power levels on the antennas
C. Decrease the bandwidth on the wireless network
D. Increase the power levels on the antennas
- How can an organization ensure applications on their company-owned mobile devices are accessible only when the user is within the office?
A. Remove the application from the mobile device when it’s not in use
B. Turn on the GPS on the device
C. Implement WPA3 on the wireless network
D. Implement geofencing
- Which of the following allows organizations to interconnect remote offices using a secure method over the internet?
A. Client-to-site VPN
B. Remote desktop connection
C. Clientless VPN
D. Site-to-site VPN
- Which of the following is an unsecure remote access method?
A. Telnet
B. SSH
C. HTTPS
D. RDP
- Which of the following is a deterrent security control?
A. Biometrics
B. Cameras
C. Locks
D. All of the above
- Which of the following prevents tailgating?
A. Smart locker
B. CCTV
C. Access control vestibule
D. None of the above
- Which of the following wireless security standards is not recommended on wireless networks?
A. WPA2
B. WPA3
C. WPS
D. All of the above
Further reading
To learn more about the topics that were covered in this chapter, check out the following links:
- Small Business Network Security Checklist: https://www.cisco.com/c/en/us/solutions/small-business/resource-center/security/network-security-checklist.html
- What Is Wi-Fi Security?: https://www.cisco.com/c/en/us/products/wireless/what-is-wi-fi-security.html
- Differences among WEP, WPA, WPA2 and WPA3 wireless security protocols: https://www.techtarget.com/searchnetworking/feature/Wireless-encryption-basics-Understanding-WEP-WPA-and-WPA2
- VPN (virtual private network): https://www.techtarget.com/searchnetworking/definition/virtual-private-network
