Chapter 23
Current and Future Trends in IT
This chapter is penned to provide a foundation to harness the power of information technology in areas such as e-commerce, wireless applications and communication. The chapter begins with a discussion on e-commerce. Next, electronic data interchange and wireless application protocol (WAP) are studied. The later part of the chapter explains new technologies such as smart card, IPTV, RFID and BCI. The chapter concludes by providing a discussion on the technologies that will in future bring economies of scale to humankind.
After reading this chapter, you will be able to understand:
E-commerce, which is a way of carrying business communications and transactions using computers over Internet, or any other form of network
EDI—a way of exchanging business data between two machines
Wireless application protocol (WAP), which is the worldwide standard protocol stack specified for wireless communication networks by the WAP Forum
Smart card—a small, portable pocket-size card having data storage ability
IPTV, which is a system that provides the television services to the end users via packet switched network
Blogging, a process of creating, maintaining, writing, or adding content to a blog
RFID—an auto-identification technology, which is used to capture and transmit identification details (including location) of an object wirelessly
Brain computer interface (BCI), which is a communication pathway between brain (of either human or animal) and some external device such as a computer system
Imminent technologies including the concept of Pen PC, Napkin PC, Roll top computer, B-membrane PC, and USB memory stick
23.1 INTRODUCTION
In the early years, computer use was primarily confined to business and research. However, the 1980s and 1990s saw the development of cheaper and more versatile computers, which has led to an ever-growing number of users in the offices and in homes. Today, IT has interwoven itself into our socioeconomic fabric in such a manner that it is often said that we live in an information age. As we usher in the future, consumers are expected to sign up in record numbers for information, education, and entertainment services provided over networked computers, or perhaps in altogether different computing environment. Technological revolutions have always had different effects on different segments of the economy. The trading activities have become much easier with the use of e-commerce and EDI. The development of services like WAP has enabled people to access global information anywhere and at anytime. Some new trends like Internet protocol television (IPTV) and radio frequency identification (RFID) are directed to make the people's lives more convenient. However, these technologies are not in full use yet. Besides, future has some more interesting PC concepts that if ever developed will not only add to the ease of computer usage but will also enhance its portability.
23.2 ELECTRONIC COMMERCE (E-COMMERCE)
Traditionally, commerce is seen as the exchange or buying and selling of goods and services, which involves exchange of money, and sometimes transportation of goods from one place to another. We see commercial activities all around us in many forms. For instance, at a grocery store, we can see two main activities that form the essence of commerce, the buying (people purchasing goods or service) and selling (people offering goods and services to buyers). With the passage of time and advancement in technology, commerce has added a new dimension in the form of electronic trade, a more effective and convenient manner than the traditional commerce which is revolutionizing the way business activities are carried out across the world. In today's business world, where time and money are considered as the most important factor for success, E-commerce plays an important role in bridging the gap between buyers and sellers (Figure 23.1).
Figure 23.1 E-Commerce and Business Processes
Most people think E-commerce as buying and selling of products and services on the Internet. However, in reality, it is more than just selling and purchasing goods online. E-commerce is referred to as a way of carrying business communications and transactions using computers over Internet, or any other form of network. Here, transaction is referred to as exchanges taking place between two entities where one sells products or services to the other.
23.2.1 Types of E-Commerce
There exist four categories of e-commerce applications: business-to-onsumer (B2C), business-to-consumer (B2C), business to business (B2B), business-to-administration (B2A), and customer-to-customer (C2C).
Business-to-Consumer (B2C): B2C is a concept of online marketing and distribution of products and services over the Internet. It is a natural sequence of steps for many retailers who sell goods directly to the consumer. The general idea for achieving success in B2C e-commerce lies in reaching more customers, providing better services and increasing sales while spending less. For the consumer, it is relatively easier to appreciate the importance of e-commerce as it saves their precious time, which they spend moving around in crowded supermarkets, by enabling them to do the same from their home, by shopping online at any time in virtual Internet shopping malls, and having the goods delivered at their doorstep.
The supplier may be an existing retail outlet such as a grocery store; these businesses may have been slow in gearing-up for e-commerce compared to the innovative Internet companies, but they usally have a sound commercial structure as well as in-depth experience of running a business. This system can also be used to receive information such as share prices, insurance quotes, online newspapers, or weather forecasts.
Business-to-Business (B2B): B2B system is used for e-commerce in a pure business environment. It covers many ways where e-commerce can be used to support one business trading with the other. Much of the attention given to B2B system relates to developments such as e-marketplaces and e-exchanges, but most of the actual use of e-commerce is at a lower level in the e-commerce implementation cycle.
Typically, in the B2B environment, e-commerce can be used in procurement, order fulfilment, and managing trading–partner relationships. In recent times, e-commerce technologies have allowed the smallest of businesses to improve the processes of interacting with customers. They are now developing services for individual clients rather than providing a standard service and evaluating all aspects of their business process from where the greatest return can be obtained. B2B e-commerce can also be used to:
- Develop, retain, and cultivate relationships with customers.
- Streamline the supply chain, manufacturing, procurement processes, and automate corporate processes to deliver the right products and services to customers quickly and cost-effectively.
- Capture, analyse, and share information about customers and company operations in order to make better decisions.
Business-to-Administration (B2A): In the B2A system, business community interacts electronically with public sector organizations. B2A application includes submission of planning applications, tax returns, or patent registration.
Customer-to-Customer (C2C): C2C system refers to e-commerce activities, which uses an auction style model. This model consists of person-to-person transaction that completely excludes businesses from the equation. C2C system enables customers to directly deal with each other. Examples of this type of system are www.ebay.com and www.amazon.com.
23.2.2 Processes in E-Commerce
All information in e-commerce is expressed in the form of binary values (bits), which makes the product more versatile. For example, a tourism catalogue data stored in a web server database can be presented electronically using the web, printed in a customized catalogue at specific market, or might be included in CD-ROM as a multimedia presentation. If any information is required to be published on the Internet, the hardware and software component required are web server, database, and multimedia authoring tools. Generally, there exist five important processes in an e-commerce lifecycle: information sharing, ordering, online payment, fulfilment, and support and services.
Information Sharing: Sharing of information on the Internet is the foremost process in e-commerce activities. It makes the customer aware of all the product and services offered by the online vendor. This particular activity is carried out by means of advertising, marketing on the Internet, and customer information gathering process (see Figure 23.2). Apart from this, there are various networked communities (chat room, multi-party conference, and newsgroup) available on the Internet for the distribution of information.
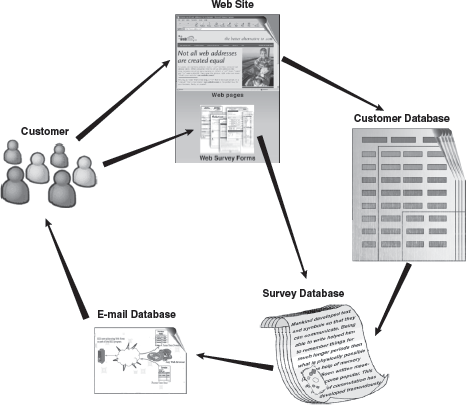
Figure 23.2 Information Gathering from Customer
World Wide Web provides one of the effective mediums for communication with the customers. Websites are designed to include product catalogues. One can obtain the data for products that are requested. At the same time, it also allows web visitors to provide information about them. Apart from this, timely notification, product upgradation, and new features are sent through e-mail.
On Internet, numerous support services are provided to the customers. For example, organization maintaining a web server can include questionnaire, which are available to the customer while using company's website. Repeated questions are often compiled into one set and distributed to the customer's e-mail. Large number of websites aim at providing information and data to the general public; however, there exist some significant sites on the Internet that cater to the business communities. These sites are called intermediaries, and their sole purpose lies in making buyers to interact, trade, and make purchases from the sellers.
Ordering: This process involves customers to electronically place order for the company's goods and services. Placing of order requires the use of client/server application where order of goods or services is placed on the electronic form placed on the company's website.
Online Payment: Online payment is a crucial process in e-commerce. The payment activity requires the use of high security to protect online money transactions from any unauthorized use. In most cases, data are transferred in encrypted form on a secured medium. Different mechanisms for payment are available on the Internet and the customers can use any of them.
Fulfilment: Modern businesses are highly dependent on the massive amount of information and precious data, which is continuously being transferred over the computer network across the world. Many online trading companies make use of Internet for transferring funds, generating money, and providing information product (newsletter, articles, stock prices, and reports). However, when product takes the shape of physical entity, support of EDI is required to clear the sale of product to the buyer with up-to-date delivery notification issued to the buyer's e-mail.
Support and Services: Support and services are regarded as one of the most important processes in e-commerce activity. The continuing relationship of an organization with the customer depends on the kind of support and services provided to the customers. Relationship of an organization with the customer starts with the sale of the product. It might happen that customer will require assistance with product and services in future. Therefore, items such as technical notes, FAQs, and support documentation should be available on the company's website.
23.2.3 Types of Electronic Payment
The method of making payment on the Internet is essentially the electronic version of the traditional payment system, used in everyday life. The fundamental difference between the electronic payment system and the traditional one is that every transaction is carried in the form of digital string. Generally, there exist three major types of payment mode: e-cash, e-cheque, and credit card.
E-cash: E-cash is one of the systems that fit small-scale commercial transactions in realtime environment on the Internet. In e-cash, the currency is transformed into an electronic form. A bank issues electronic money and debits the customer's account by withdrawing the specified amount from customer account, which equals the value of currency (token) issued to the customer. The bank then authenticates each token with the digital stamp before transmitting it to the customer computer. Now whenever the customer wants to spend e-cash, a token of roper amount to the merchant is transmitted who then relays them to the bank for verification and redemption. To ensure that no fraudulent activity occurs, bank records the serial number of each token that the customer spends. If the serial number of the token was already recorded in the bank's database, the bank would inform the merchant for its invalidity.
E-cheque: The payment mode for e-cheque is not much different from the paper cheque. A paper cheque is a kind of message given to the consumer's bank to transfer adequate fund from one customer's account to someone else's account. The message is sent to the intended receiver of the fund who presents the cheque to the bank in order to collect the money. In all aspects, an e-cheque also has the same features as the paper cheque. It sends a message to the receiver who endorses the cheque and presents it in his bank to obtain money. One advantage that e-cheque has over paper cheque is that it provides protection to the customer's account by encoding the account number with the bank's public key. This prevents the merchant from knowing the customer's account, thereby eliminating the chances of fraudulent transactions.
Credit Card: In credit card payment, customer gives a preliminary proof of the ability to pay by giving the credit card number to the vendor. The vendor then verifies it from the bank and issues a purchase slip for the consumer to endorse. The vendor then uses a copy of the purchase slip to collect money from the bank and in the next billing cycle, the consumer receives a statement of recorded transaction at the address specified by the customer. Using credit card to make purchases over the Internet requires additional steps to make transaction secure for both the buyer and seller. Credit card information is sent as encrypted credit card number over the Internet.
23.2.4 Advantages of E-Commerce
Some of the advantages of e-commerce are as follows:
- 24/7 Access: Online businesses never sleep as opposed to conventional businesses. Consumers can access goods and services anytime they want.
- Reduced Prices: The cost of product is reduced since stages along the value chain are decreased. For example, intermediaries can be eliminated by the company directly selling to the consumer instead of distributing through a retail store.
- Global Marketplace: Consumers can shop anywhere in the world. This also provides a wide selection of products and services to consumers.
- Increased Potential Market Share: Internet enables businesses to have access to international markets, thereby increasing their market share. Companies can also achieve greater scale of economies.
- Lower Cost of Advertising: Advertising on the Internet costs relatively less than advertising on print or television media. A company can spend a lot on advertising on the Internet if the company hires an external party to create their advertisement.
- Low Start-Up Cost: Anyone can start a company on the Internet. Start-up costs are lower for companies since there is less need for money for capital assets.
- Secure Payment Systems: Recent advancements in payment technologies allow encrypted, secure payment online.
- Lower Cost of Practising Business: Less number of employees, purchasing costs, order-processing costs associated with fax, telephone calls, data entry, and eliminating physical stores result in reduced transaction costs.
23.2.5 Disadvantages of E-Commerce
Every innovation in technology brings certain limitations and drawbacks along with it. The same is the case with e-commerce. The following are its disadvantages:
- Lack of Personal Examination of Products: Buying products through the Internet do not allow physical examination of products. Images of the products may be available for viewing; however, there is a risk involved in the uncertainty of the quality of the product that the consumer is purchasing.
- Hardware and Software: There are specific hardware and software that are essential to start an e-commerce company, which are bulky and costly.
- Distribution Problems: Distribution must be very efficient especially when catering to a global market.
- Maintenance of Website: E-commerce websites must be maintained and updated regularly which leads to extra labour costs.
- Extra Costs: Even though the company may initially save money by cutting middlemen and not having to invest much on capital assets, other costs may be incurred that include start-up costs of the company in terms of hardware, software, training of employees, costs to maintain the website, and distribution costs.
- Training and Maintenance: It is important to have well-skilled and trained workers to create and maintain e-commerce facilities of a company.
- Security Risk: An e-commerce business exposes itself to security risks and may be susceptible to destruction and disclosure of confidential data, data transfer, and transaction risks (as in online payments) or virus attacks. The possibility of stealing credit card numbers is one of the major threats in e-commerce activity.
23.3 ELECTRONIC DATA INTERCHANGE (EDI)
Previously, we had discussed that E-commerce uses digital methods to exchange the variety of data needed to conduct business. Like every other business organization, online companies also exchange data related to ordering and paying for items. In fact, e-commerce covers a broad spectrum of all types of data exchange in such paperless environment. Every day, businesses generate and process a large volume of paper documents. The paper documents, ranging from purchase orders and invoices to product catalogues and sales reports, provide vital information flow which must precede, accompany, or follow the physical goods in a commercial transaction. Any interruption in the physical or information flow halts the smooth operation of the supply chain, leading to significant cost overruns.
Today, a majority of the data in commercial paper documents are generated from computer applications. These paper documents are printed and copied before the information they contain is finally communicated to the respected parties. The business partner, in turn, inputs all this information into another computer application for further processing. An increasing number of companies have found the above process extremely slow, costly, and unreliable. The need for a faster, cheaper, and more accurate solution for exchanging commercial data has become a significant priority for many companies and organizations. This gave rise to EDI. It is a subset of e-commerce and is a new way of managing information. At its most basic, EDI is the transmission of business data between two machines. More specifically, EDI is defined as a collection of public standard message formats and a data element dictionary that allows trading partners to exchange data in a simple way using any electronic messaging service. Trading partners are all the entities involved in an exchange such as a vendor and its customers. These standard message formats provide an application-neutral format (that is, a format independent of any application) for direct computer-to-computer exchange of information.
23.3.1 How EDI Works?
A two-way working process of EDI-based transactions between vendor and supplier has been depicted in Figure 23.3. After business agreements are reached between the two EDI-enabled partners, no human touch is required. The ultimate EDI implementation is a totally automated interaction between the business applications. A step-wise execution of processes involved in EDI transaction for purchase, shipment, and payment is as follows:
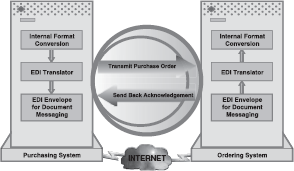
Figure 23.3 Working of EDI
- The sender's EDI translation software translates the document into a standard format and establishes the communications connection by dialling the telephone number of the network.
- The message from the sender is transferred to an electronic mailbox on the network.
- From the electronic mailbox, the trading partner's software retrieves the file, interprets the message, checks that it complies with the EDI standards, and finally, stores it. It also sends a functional acknowledgement to inform the sender if the message was received and complied with the EDI standard.
- To read and process the interpreted message, the receiver has two options. Either use the EDI translation software to produce a hard copy of the message or restructure (map) the message into a format required by the existing computer applications before further processing.
23.3.2 EDI Benefits
The goal of EDI is to provide a standard format and data element dictionary to exchange data in an electronic environment. EDI solves the problem of sharing data between dissimilar operating systems, applications, and computers using some neutral format. EDI is designed to:
- Eliminate any manual data entry into one or more software applications for analysis and reporting which dramatically reduces errors, data entry costs, and time delays.
- Improve data consistency because the format and data element dictionary provide a standard set of parameters for all contracts while accommodating unique data content.
- Eliminate proprietary software formats, interfaces, and programming effort because the standard format is application neutral.
- Provide the means for all contractors to use a standard format for all their government customers eliminating contract-specific data format and data delivery costs.
- Provide program managers with a common set of commercial tools and processes they can rely on and which are transparent to them.
23.3.3 EDI Limitations
EDI is not a technology but a new way of doing business. Though identifying the costs related to EDI is relatively easy, identifying the benefits of EDI, especially when a company is not using EDI, is hard, since most of the real benefits are strategic and intangible in nature. As such, EDI will require a different approach to cost-benefit analysis and it is essential for the success of a corporate EDI program that management has appropriate expectations on the return on investment (ROI). Still a cost-benefit analysis is not so essential as to justify the investment in EDI in order to prioritize applications and the allocation of information technology resources.
23.4 WIRELESS APPLICATION PROTOCOL (WAP)
Hardly a decade ago, when Internet just started, it was mere a thought to access the global information from our own room. In the late 1990s as the Internet grew, this thought turned into reality. From the last few years, people are more inclined to mobility, which implies a growing need of accessing global information from anywhere and at all the time. Today, the access to Internet is no more restricted to desktop computers only; people can access Internet on their mobile phones or PDAs also. One can even connect mobile phone with a computer to access Internet on the computer. The technology that has made this wireless Internet feasible is WAP.
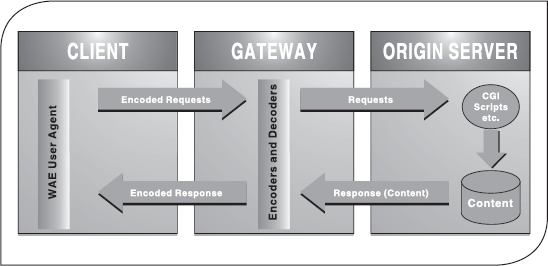
WAP is the worldwide standard protocol stack specified for wireless communication networks by the WAP Forum. It enables developing wireless applications independent of the wireless access technology being used and accessing Internet using mobile devices. WAP uses wireless markup language (WML), which is a form of eXtensible Markup Language (XML), and provides a way of adding information to the extent that tells the device receiving the content as to what action to perform.
There were certain issues in bringing wireless Internet on the mobile devices. Most cell phones and WAP-enabled PDAs have data transfer rate of 14.4 kbps or less as compared to a typical 56 kbps modem. The relatively small size of the LCD on a cell phone or PDA presented another challenge. Most web pages were designed for a resolution of 640 × 480 pixels, which is acceptable for a desktop computer. However, the pages do not fit on a mobile device's screen, which have a resolution of around 150 × 150 pixels. WAP took each of these limitations into account and provided a way to work with a typical wireless device.
Note: Like WWW, the user interface to WAP is through a mini browser in the WAP-enabled devices.
The WAP Model: WAP model is based on the existing WWW model, with the significant difference of having a gateway between the client and web server. The role of gateway is to translate the WAP-formatted messages received from WAP-enabled device into HTTP messages that can be sent to any web server on the Internet and vice versa. The following steps describe the process of retrieving information from a website using WAP-enabled device.
- The device is turned on and a mini browser is opened.
- The device then sends out a radio signal, searching for the service.
- A connection is made with the service provider.
- After that, a desired URL is provided.
- A request is then sent to a gateway server using WAP.
- The gateway server retrieves information using HTTP from the website.
- The gateway server encodes the HTTP data as WML.
- The WML-encoded data is then sent to the WAP-enabled device.
- The requested web page is displayed on the device (Figure 23.4).
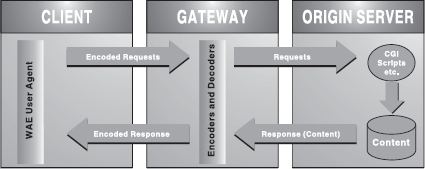
Figure 23.4 WAP Model
WAP Applications: One of the most significant advantages of mobile Internet over personal computer is the ability to instantly identify user's geographic location. Some other interesting applications of WAP are as follows:
- WAP applications are used by the children for playing games, on the cellular phones.
- Music companies offer to download the latest pop hits to customers in a daily offering.
- WAP-enabled devices are used by small-to medium-sized companies, which allows a field officer to access customer order information and stock availability details using WAP handset.
- Many cellular companies use WAP applications in customer care and provisioning, message notification and call management, e-mail, mapping and location services, weather and traffic alerts, sports, and financial services, address book and directory services, and corporate intranet applications.
Earlier, the WAP services were limited to simple information services, but with the availability of higher bandwidth and speeds, several new service types have emerged. Some of these services are:
- Infotainment includes weather forecasts, stock quotes, horoscopes, and news.
- Messaging includes e-mail, voicemail, and unified messaging.
- Personal information management includes call management and personal directories, which enable the modification of personal information.
- Financial services include mobile banking and mobile e-commerce services.
- Location-based services that are dependent on location include mapping and vehicle location information.
23.5 SMART CARD
Smart cards are small, portable pocket-size cards having data storage ability. Some people might confuse smart cards with conventional credit/debit cards that have a plastic base with magnetic stripe containing some information. But smart cards are quite different from magnetic stripe cards. Most smart cards incorporate an Integrated Circuit Chip (ICC) inside them having some computational functionality and I/O support. They come in various sizes ranging from as small as mobile phone prepaid cards to as big as credit/debit cards.
According to the applications for which smart cards are used, they are classified as microprocessor cards and memory cards. A microprocessor card is just like a complete computer in itself. It is embedded with a microprocessor and memory (RAM, ROM, and EEPROM) on the chip. The microprocessor helps in processing of information stored on the card and this processing is carried out in RAM. The data on the card are stored in the form of different files that are arranged in a file system in EEPROM. In ROM, the operating system resides that is responsible for managing the file system in EEPROM, executing the required functions in RAM, and for security and access control to data. The inclusion of operating system makes these cards multifunctional. The data on microprocessor cards can be added, deleted, or manipulated. Examples of these cards are stored-value cards (cards that hold some monetary value) and the cards that allow set-top boxes on televisions to remain secure from piracy. A memory card, on the other hand, is embedded with memory (EEPROM) only. Thus, data can only be read from such cards but cannot be added or manipulated. The memory cards are designed to undertake pre-defined operations. The prepaid mobile phone cards are the most widely used memory cards.
Note: The present-day microprocessor cards are embedded with 32-bit RISC processor.
Depending on the way the smart cards are used, they are categorized as contact and contactless cards. The contact smart cards have the same size as that of conventional credit/ debit cards. These cards have contact pads attached to the chip that needs to be in the direct contact with the smart card reader whenever these cards are to be accessed. On the other hand, the contactless smart cards need not come in direct contact with the reader. They have an embedded antenna attached to the chip that communicates with the reader to read or write data on the card. Some contactless smart cards can be accessed accurately up to 1.5 m away from the reader while some need to be only few millimetres away.
Smart Card Applications: Smart cards have greatly improved the convenience and security of transaction. They provide tamper-proof storage of user and account identity. They also provide vital components of system security for the exchange of data throughout any type of network. They protect against a full range of security threats, from careless storage of user passwords to sophisticated system hacks. Multifunction cards can also serve as network system access and store value and other data. People worldwide are using smart cards for a wide variety of daily tasks, which include:
- Personal Finance: As banks enter in competition in newly opened markets, such as investment brokerages, smart card is used for making secure transactions at an increased rate. This improves the customer satisfaction as customers can now use it for electronic transfer of fund over the Internet.
- Health Care: In health care institutions, the smart cards are used to store information about patients’ history and their verification details. The health professionals can instantly access this information whenever required as well as update the information.
- Mobile Communications: Smart cards are used to identify the GSM digital mobile phones. All the information that is required for authenticating and billing the user is stored on the card so that the user can use any of the phone terminals.
- Electronic Purse: A smart card can be used as a stored-value card that holds some monetary value. While making payments, the smart card reader can access the current amount stored on the card and subtract from it the amount for purchases made. Thus, one need not carry cash with himself/herself
- Campus Identification and Access: Businesses need simple identity cards for all its employees and similarly, universities for its employees as well as for its students. Most of these people are also granted access to certain data, equipments, and departments according to their status. Microprocessor-based smart cards incorporate identity with access privileges and store value for use in various locations, such as cafeterias and stores.
23.6 INTERNET PROOTCOL TELEVISION (IPTV)
IPTV is a system that provides the television services to the end users via packet switched network. This network uses Internet protocol suite to transmit audio, video, and control signals, thereby providing quality of service, security, and reliability.
IPTV sends data to the end user(s) in two ways, namely, unicast and multicast (or broadcast). In unicasting, data are sent to a single end user. Video on demand (VoD) is the best example of unicast in which only the subscriber who has requested for the video can view the transmitted video. On the other hand, in multicasting (or broadcasting), the same data are sent to multiple users simultaneously. For example, in Live TV, a particular video is delivered to many viewers (Figure 23.5).

Figure 23.5 IPTV
The core of any IPTV system is the operator's central distribution centre where the video stream is encoded and split into packets, which are transmitted over the IP network. The packets travelling through the network are received by the local exchanges—the IPTV middleware that routes the packets to the individual subscribers. The local exchanges are responsible for dealing with user authentication, VoD requests, billing, or channel change requests from the subscribers. In addition, here, some local content like advertisements, VoD, etc., can also be added. From the local exchanges, the packets are sent to the subscribers via local network. At the subscribers’ end, there is a device known as set-top box, which receives the incoming data, reassembles the packets into coherent video stream, and decodes it to be viewed on the television or some other form of screen.
Note: To use the bandwidth efficiently, the IPTV video is compressed using compression techniques, MPEG-2 and MPEG-4.
IPTV offers many advantages, some of which are as follows:
- Unlike the traditional television which requires wires for its working, IPTV works on various Internet services that transmit the video more efficiently and save space consumed by tangling wires.
- IPTV supports VoD that allows an individual user to select and watch the desired videos at anytime. In addition, the viewer can play, pause, or stop the running video.
- By using electronic programming guides, IPTV provides better interactivity between the service provider and the end user. For instance, while watching a match, viewers can check the player's status.
- IPTV also facilitates to capture real-time broadcast television and record it on the local server, connected through a network. This helps the end user to view the recorded program of his own choice.
23.7 BLOGGING
The term blog is the shortened form of web log which was discovered by Jorn Barger in the year 1997. It is basically a type or part of website maintained by an individual with regular entries of news on some particular topic (like education, entertainment, or politics), description of events, personal thoughts, and so on. Primarily, blogs include information in textual form, but they may also include hypertext, images, videos, and links to other blogs or web pages. An important property of blog is that it allows the readers to leave their comments and share their thoughts with the blog owner or other readers. The entries posted on blog are usually arranged and displayed in reverse chronological order and can be viewed in an HTML browser.
A blog is an innovative way to organize your thoughts and present articles. Moreover, it helps to keep up with the latest information posted on various sites making it a popular personal publishing tool. The process of creating, maintaining, writing, or adding content to a blog is known as blogging and the person who posts entries onto the blogs is known as blogger.
Types of Blog: There are different types of blog depending upon the purpose for which blog has been created, the content a blog contains, or the way the content has been added to a blog. Some common types of blog are listed below:
- Personal Blogs: Personal blog is the most common and traditional form of blog. It can be considered as an online diary maintained by an individual on which he/she records daily events, commentary, or articles. These blogs help the bloggers to share their feelings and thoughts with other members or friends.
- Corporate Blogs: Corporate blog, also known as business blog, is created and maintained for business purposes. Such blogs are mainly used for marketing or advertising the company's products to the outside world. Also, they can be used within the organization to promote communication and culture among the employees as well as to keep them up-to-date with the latest information about products, services, or activities.
- Media Blogs: Media blogs constitute blogs containing media-type content. For example, blog containing videos known as vblog, containing photographs known as photoblog, or containing sketches known as sketchblog.
Apart from these types, blogs can also be categorized on the basis of device type used to add content to the blogs. For example, blogs added by using mobile devices like cell phone are known as moblog.
Creating and Using a Blog: Many websites offer to create a blog account free of cost. Some of these websites include www.blogger.com, www.weebly.com, www.blogspot.com, www.thoughts.com, and many more. Here, we will explain the steps to create a blog on www.blogger.com website.
- Type www.blogger.com in the address bar of the web browser and press Enter. The homepage of the website opens (see Figure 23.6).
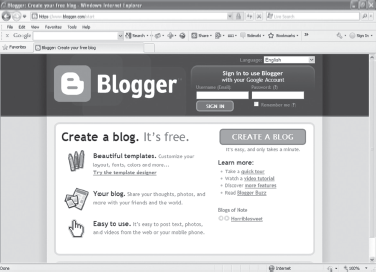
Figure 23.6 Home Page of Website
- Click on CREATE A BLOG. This displays Create a Google Account webpage (see Figure 23.7).
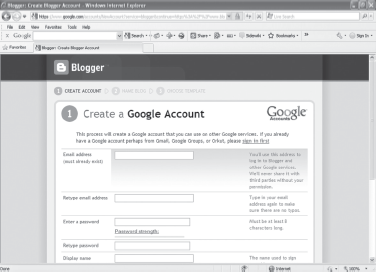
Figure 23.7 Create a Google Account Webpage
- Enter details like e-mail address, password, display name, birth date, and verification word in the webpage.
- After entering the details, click CONTINUE on the bottom right of the webpage. This displays the Name your blog webpage (see Figure 23.8).
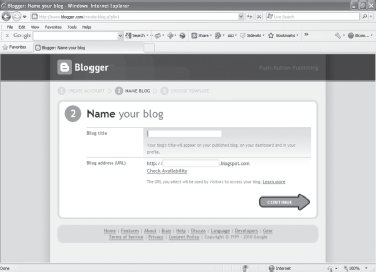
Figure 23.8 Name Your Blog Webpage
- Enter the desired Blog title and Blog address (URL).
- Click CONTINUE to display the Choose a starter template webpage (Figure 23.9).
Figure 23.9 Choose a Starter Template Webpage
- Select a design of your choice from the given templates. Whatever design you choose, your blog will look like that.
- Click CONTINUE to complete the blog creation process. A webpage appears that informs that your blog has been created (see Figure 23.10) and now, you can add posts to it or customize it to change its appearance.
Figure 23.10 Blog Created
- Click START BLOGGING to start using your blog. A webpage showing the display name (as specified by you) at the top appears. By default, the Postings tab is activated on this webpage (Figure 23.11).
- Write the text in the text area provided to add a new post. You can also format the text using the toolbar appearing above the text area.
Figure 23.11 Webpage with Posting as the Active Tab
- To add an image or video to the post, click Insert image button (
 ) or Insert a video button (
) or Insert a video button ( ) on the toolbar, respectively (Figure 23.12).
) on the toolbar, respectively (Figure 23.12).
Figure 23.12 Text and Image Added to the Blog Post
- Click the PUBLISH POST button at the bottom left corner to publish the blog post. A webpage appears that indicates your blog post has been published. Also this page provides links that enable you to view the post, edit the post, or create a new post (Figure 23.13).
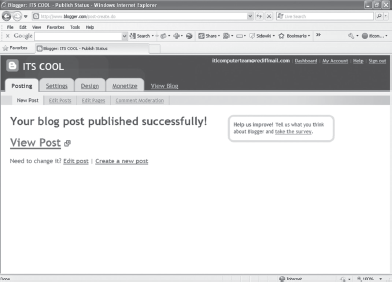
Figure 23.13 Publishing Blog Post
- Click on View Post link to view your post. A webpage similar to as shown in Figure 23.14 appears that shows your blog posts.
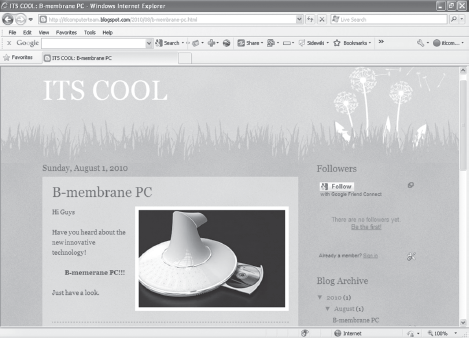
Figure 23.14 Viewing the Blog Posts
23.8 RADIO FREQUENCY IDENTIFICATION (RFID)
RFID is an auto-identification technology, which is used to capture and transmit identification details (including location) of an object wirelessly. RFID system consists of the three basic components, namely, RFID tag (or transponder), reader, and processing device (such as computer). An RFID tag contains the identification number and other data of the object on the silicon chip in encoded form. It is placed on or embedded in the object to be tracked. The stored data on RFID tag is accessed (i.e. read/write) by the reader. A reader is a device that activates the RFID tag (when it comes in the response range of the reader) by emitting radio frequency signal through antenna. Upon receiving the signal from the reader, the tag responds by transmitting the data to the reader. This data are then sent by the reader to the computer connected with it for further processing (Figure 23.15).
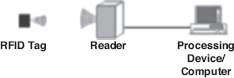
Figure 23.15 An RFID System
FACT FILE
RFID versus Bar Code
Bar code technology is also an auto-identification technology; however, RFID is an improvement over barcode in many ways.
RFID does not require any wire or line of sight between the reader and an RFID tag. This helps in identifying an object within a particular range without even seeing (or touching) it.
RFID has read/write capabilities. The information stored on RFID tag can be changed whenever required.
RFID can detect moving objects within long range (say 100 feet) and can work in harsh environment.
More than one RFID tag can be accessed simultaneously.
Various applications of RFID technology are as follows:
- One of the most common uses of RFID is in asset tracking. By placing the RFID tags in (or on) the products, companies can keep a track of their product, which minimizes the risk of misplacing, stealing, or underutilizing the product.
- Companies also use RFID technology in the supply chain management to trace their product during shipment.
- RFID is finding its way in payment systems. Using RFID, a person can pay his road toll without stopping his car.
- RFID is used in security and access control systems. Government has also started using RFID technology in making e-passport for security purpose.
23.9 BRAIN COMPUTER INTERFACE (BCI)
BCI, as the name implies, is a communication pathway between the brain (of either human or animal) and some external device like computer system. BCI devices are used to transmit or capture the brain signals, which can further be used to restore function or movement to sensory organs or to direct implanted prosthetic device as natural limbs. BCI is an important achievement in medical technology as it enables the persons suffering from some kind of physical disability to carry out their tasks like walking, picking up a glass of water, etc., just by thinking. As for now, BCI devices have succeeded in restoring damaged sight, movement, hearing, and in curing neurological problems such as depression. However, in the near future, it will be possible to intensify the human capacity and to influence someone's thinking (Figure 23.16).

Figure 23.16 A Human Interacting through BCI
The BCI works just because of the way the brain functions. Our brain is full of neurons, which fire whenever we think or perform some action. As the neurons fre, the electric signals are generated. These signals move at a very fast speed from neuron to neuron through a complex web of connections. Though the path that the electric signals follow is insulated by a white fatty substance in the brain called myelin, some electric signals get away. These signals are captured by the researchers and used for controlling some external device, activity, or for helping people to overcome their severe physical disabilities.
Types of BCI: BCI can be of the following types.
- Invasive BCI: In this type of interface, the BCI device is implanted directly into the brain of the patient. Therefore, the signals captured from the brain are of high quality. These high-quality signals can be used to control the robotic arms or legs implanted in the disabled people, thereby providing them functionality. These signals can also be used for restoring the vision by connecting external camera. But since these devices are implanted inside the brain, scar tissue can form over the device, which results in blockage of signals, reduced efficiency, and increased risk to the patient.
- Partially Invasive BCI: In this type of interface, the BCI device is planted outside the brain but inside the skull of the patient. It has lower signal strength as compared to invasive BCI, but the risk of scar formation over the device is less.
- Non-Invasive BCI: In this type of interface, the BCI device is planted onto the skull of the patient. It is the safest interface but has the least signal quality as compared to other interfaces. The non-invasive BCI device can enable the patient to move muscular implants and restore partial movement. Although it is easy to use, cheap, and portable, intensive training is required to carry out different functions.
Techniques of BCI: There are various means of reading the brain activity, some of which are as follows:
- Direct Neural Contact: It is an invasive technique in which a chip containing several pins (having width less than a human hair) is embedded into the brain such that the pins are in direct contact with the neurons. As the brain starts movement, the neurons fire and with the help of chip, scientists are able to read the firings of neurons in the brain. The language generated by the neuron firing is forwarded to a computer translator that decodes the neural language into computer language by using some special algorithms. The decoded information is transferred to another computer which in turn instructs the machine for the action to be performed. With the current technologies, this technique is highly impracticable. However, the speed with which nanotechnology is advancing, someday it might become reality.
- Electroencephalography (EEG): It is the first and most common non-invasive technique that was discovered by Hans Berger. In this technique, the electrodes, which are placed against the scalp of the patient, are used to capture the brain signals. Nowadays, this technique is widely used due to its low cost, ease of use, and high temporal resolution. But it is less accurate than direct neural contact and can capture low-frequency signals.
- Magnetoencephalography (MEG): It is a newer non-invasive technique which is much more accurate than EEG. It communicates with the brain by recording magnetic fields produced by it. The main drawback of this technique is that it requires more equipments than any other technique. For using MEG, a room filled with super-conducting magnets and giant super-cooling helium tanks surrounded by shielded walls is required.
- Functional Magnetic Resonance Imaging (fMRI): It measures the hemodynamic (the flow of blood and level of oxygen in the blood) related to the neural activity in the brain using uses MRI (Magnetic Resonance Imaging) technology. As MRI requires special equipments, this technique is costly.
23.10 IMMINENT TECHNOLOGIES
Evolution of technology in the current world shall prevail, as long as there remains gift of knowledge and wisdom in humanity. Striving for success has made humankind to make the best use of technology in making things easier and faster in everyday life. Some futuristic technologies are discussed below.
23.10.1 Pen Size Computer
Pen size computer is one of the major breakthroughs of this era. It is a revolutionary miniature computer that comes in the shape and size of a pen. The conceptual prototype of this computer was developed by a Japanese company, NEC Corp and NEC Design Ltd., way back in 2003, and was named as P-ISM (Pen-style Personal Networking Gadget Package) (Figure 23.17).

Figure 23.17 Pen Size Computer
The main idea underlying the concept of pen size computer is to break a computer into parts. Pen size computer is a set of five different components (pens) that altogether make up a computer and each component has a specific function to perform. All the pens are connected to each other wirelessly and communicate using Bluetooth technology. The description of different components of pen size computer is as follows (Figure 23.18):
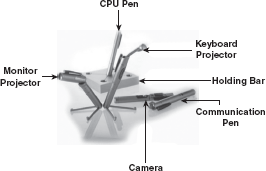
Figure 23.18 Components of Pen Size Computer
- CPU Pen: This pen serves as a CPU that administrates everything in the computer.
- Keyboard Projector: This pen projects a virtual keyboard on the desk or any other flat surface. It emits the laser beam on the surface, which generates a full-size, perfectly operating virtual keyboard. You can work on this virtual keyboard in the same manner as you do on the normal keyboard. Also, when you press the keys of virtual keyboard, you can listen the same tapping sound that is produced in case of normal keyboard.
- Monitor Projector: This pen projects an A4 size screen on a flat surfaceand displays the output produced by the computer on it. The resolution of the projector is 1024 × 768 approximately.
- Camera: This pen helps in video conferencing, video recording, etc, just like a webcam. It provides a three-dimensional visual communication.
- Communication Pen: This pen serves as a cellular phone and is used to connect the pen size computer to Internet through Tri-wireless modes (Bluetooth, 802.11B/G and cellular). It can serve as a pointing device (to enter the input) as well as contains earpiece.
All the pens of pen size computer rest on a holding block which keeps the mass storage together as well as recharges the batteries.
23.10.2 Napkin PC
Have you ever thought that your PC can resemble the design of a napkin holder? This revolutionary idea of PC prototype named as Napkin PC is given by Avery Holleman. He has also won Microsoft's Next-Gen PC Design Competition's first prize for this innovative idea.
The Napkin PC consists of a napkin holder having a base station PC, number of e-paper napkins, and a set of coloured pens. The e-paper napkin looks like a paper and works as a storage and display medium. It is reusable—can be rewritten thousands of times. The user can write or draw on the napkin (i.e. can give commands) using one of the pens. Anything that the user writes on the napkin is transmitted by the pen to the napkin interface using short-range RF technology. Not only this, the pen also keeps track of who is drawing what. Note that both the pen and the napkin interface interact with the base station using long-range RF (Figure 23.19).
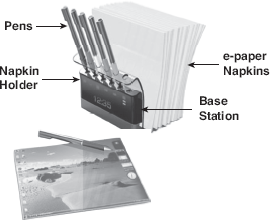
Figure 23.19 Napkin PC
The best part of Napkin PC is that it is very easy to work with because of the use of pen and paper. Besides this, it offers many other advantages, some of which are as follows:
- Multitasking will become easy. Unlike other computers where you have to shuffle through windows on a single interface, you can work on multiple napkin interfaces in parallel with much ease.
- E-paper can retain the images intact for indefinite period of time. Thus, the need for print is eliminated. Moreover, if the data on the e-paper napkin are no longer required, it can be simply returned to the base station as a fresh napkin.
- Napkin PC requires very little power, even battery is not required. It uses a single-layer circuit board for inductive power.
- In business meeting, entrepreneurs can work together to share their personal ideas by passing the napkins to each other and thus can work in collaboration.
- Artists can pin-up the e-paper napkins containing the pictures in an art gallery for exhibition while the engineers and architects can place them (where each napkin contains a small sketch) together to make a giant digital sketch for large-scale blue prints.
23.10.3 Roll Top Computer
Roll top computer is a portable and stylized computer concept unveiled by Orkin Design of Germany. The basic idea behind this concept is to enhance the portability of conventional book-form laptops by turning them into unfurling and convolving portable computers. Due to enhanced portability of roll top computer, you can roll it like a newspaper (when not in use) and carry it around wherever you want.
The conceptual prototype of roll top computer comprises two parts: an energy-efficient and flexible OLED (organic light-emitting diode) display with multi-touch screen capabilities and a tower on which the display can be wrapped around (see Figure 23.20 (a)). The tower incorporates a power adapter, USB ports, webcam, and speaker within itself. A multimedia integrated pen is also incorporated in the device.
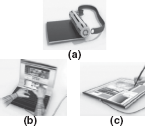
Figure 23.20 Roll Top Computer
The roll top computer can be used as a laptop, tablet PC, or a Television. As you unroll it (but not fully), it can be used as a 13-inch laptop/notebook (see Figure 23.20 (b)) with a portion of display being used as a keyboard. If you flatten it out, it can be used as a graphics tablet with an enclosed stylus pen (see Figure 23.20 (c)). When you fully unroll it, you get a 17-inch flat screen display to view the videos. This conceptual device also contains a hanging belt using which it can be easily carried over the shoulders. In short, the roll top computer is an all-in-one gadget that removes the burden of carrying heavy laptop bags.
23.10.4 B-membrane PC
B-membrane is an innovative and revolutionary PC prototype designed by a Korean designer Won-Seok-Lee. On the first look, it does not seem like a conventional computer at all; rather it resembles a space ship. It contains all the computer components within itself. The features that make the B-membrane computer concept interesting include:
- A built-in projector that is capable of projecting the computer screen on almost any surface at which the projector is pointed to. The interesting thing is that the projector is omnidirectional, which means you can point it in any direction on the surface. The use of projector eliminates the need of bulky monitors completely.
- A membrane like touch screen keyboard that appears only when you need to use it.
- An optical drive incorporated into the design using which you can play CDs or DVDs on the computer (Figure 23.21).

Figure 23.21 B-membrance PC
Apart from being used as a PC, B-membrane computer can also be used as a source of ambient light. When you turn off this computer, its projector transforms it to an ambient light effect system that can display lighting on any surface. One aspect that seems unfavourable to B-membrane computer is its shape and size, which makes it difficult to carry it around.
23.10.5 USB Memory Stick
A Japanese designer Mac Funamizu devised the idea of USB memory stick that combines the concept of disco lights with flash drive. The USB memory stick looks similar to pen/flash drive and has a transparent (glass) body that illuminates to present its storage capacity as well as the data stored in it. The glass shows different colours of light to indicate different type of data stored in the flash drive. For example, it shows pink light for images, blue for documents, and green for movies. However, if the glass shows no light, then it indicates no data are stored in it. On the other hand, if the glass is filled with lights then it means no storage space is available in the flash drive (Figure 23.22).

Figure 23.22 USb Memory Stick
Let Us Summarize
- E-commerce is a way of carrying business communications and transactions using computers over Internet. However, most people think E-commerce to be just buying and selling of products and services online on the Internet.
- There exist four distinct categories of e-commerce applications: B2C, B2B, B2A, and C2C.
- There exist five important processes in an e-commerce lifecycle; these are information sharing, ordering, payment, fulfilment, and support and services.
- The method of making payment on the Internet is essentially the electronic version of the traditional payment system, used in everyday life. Generally, there exist three major types of payment mode: e-cash, e-cheque, and credit card.
- EDI is defined as a collection of public standard message formats and a data element dictionary that allows trading partners to exchange data in a simple way using any electronic messaging service. It is a transmission between businesses of information in standard, computer-readable format which includes electronic order placement, electronic shipping notification, electronic invoicing, and many other business transactions which computers can actually perform better than people do on the computer network.
- WAP is the worldwide standard protocol stack specified for wireless communication networks by the WAP Forum. It enables developing wireless applications independent of the wireless access technology being used and accessing Internet using mobile devices.
- Smart cards are small, portable pocket-size cards having data storage ability. Most smart cards incorporate an ICC inside them having some computational functionality and I/O support. They come in various sizes ranging from as small as mobile phone prepaid cards to as big as credit/debit cards.
- IPTV is a system that provides the television services to the end users via packet switched network. This network uses Internet protocol suite to transmit audio, video, and control signals, thereby providing quality of service, security, and reliability.
- The term blog is the shortened form of web log which was discovered by Jorn Barger in the year 1997. It is basically a type or part of website maintained by an individual with regular entries of news on some particular topic (like education, entertainment, or politics), description of events, personal thoughts, and so on.
- There are different types of blog depending upon the purpose for which blog has been created, the content a blog contains, or the way the content has been added to a blog. Some common types of blog include personal blogs, corporate blogs, and media blogs.
- RFID is an auto-identification technology, which is used to capture and transmit identification details (including location) of an object wirelessly. RFID system consists of the three basic components, namely, RFID tag (or transponder), reader, and processing device (such as computer).
- BCI, as the name implies, is a communication pathway between the brain (of either human or animal) and some external device like computer system. BCI devices are used to transmit or capture the brain signals, which can further be used to restore function or movement to the sensory organs or to direct implanted prosthetic device as natural limbs.
- BCI can be of three types: invasive, partially invasive, and non-invasive. Direct neural contact technique is an example of invasive BCI while EEG and MEG are the most commonly used non-invasive BCI techniques.
- Pen size computer is one of the major breakthroughs of this era. It is a revolutionary miniature computer that comes in the shape and size of a pen. It is a set of five different components (pens) that altogether make up a computer, and each component has a specific function to perform. These components include CPU pen, keyboard projector, monitor projector, camera, and communication pen.
- The Napkin PC consists of a napkin holder having a base station PC, number of e-paper napkins, and a set of coloured pens.
- Roll top computer is a portable and stylized computer concept that comprises two parts: an energy-efficient and flexible OLED display with multi-touch screen capabilities and a tower on which the display can be wrapped around. The tower incorporates a power adapter, USB ports, webcam, and speaker within itself.
- B-membrane is an innovative and revolutionary PC prototype that resembles a space ship. It comprises a built-in projector, membrane like touch screen keyboard, and an optical drive. It can also be used as a source of ambient light when it is turned off.
- USB memory stick looks similar to pen/flash drive and has a transparent (glass) body that illuminates to present its storage capacity as well as the data stored in the flash drive.
Exercises
Fill in the Blanks
- ............ is referred to as a way of carrying business communications and transactions using computer over Internet, or any other form of network.
- ............ In B2B environment, e-commerce can be used in ............, ............, and ............relationship.
- The fundamental difference between the electronic payment system and the traditional one is that every transaction is carried in the form of ............
- The goal of EDI is to provide a ............ and ............ to exchange data in an electronic environment.
- All information in e-commerce is expressed in the form of ............, which makes the product more versatile.
- In ............, the BCI device is planted outside the brain but inside the skull of the patient.
- In Napkin PC, ............ orks as a storage and display medium.
- IPTV sends data to the end user(s) in two ways, namely,............. and ...............
- A .............. is an innovative way to organize your thoughts and present articles.
- The basic idea behind ............. concept is to enhance the portability of conventional book-form laptops by turning them into unfurling and convolving portable computers.
Multiple-choice Questions
- Which of these is a type of electronic payment?
- E-cash
- E-cheque
- Credit Card
- All of these
- Which of these is not an e-commerce activity?
- B2B
- C2B
- B2A
- C2C
- Which of the following language is used by WAP?
- HTML
- WML
- XML
- Both (a) and (b)
- Which of the following is a process in e-commerce life cycle?
- Service
- Payments
- Ordering
- All of these
- Which component of Pen PC is used to connect the computer to Internet?
- Communication pen
- Camera pen
- CPU pen
- None of these
- Which of the following is not a component of RFID system?
- Transponder
- Reader
- Set-top box
- Computer
- Which of the following is not an advantage provided by IPTV?
- Online bill payment
- No wiring
- Video on demand
- Better interactivity
- Which of the following is an invasive BCI technique?
- EEG
- Direct neural contact
- MEG
- MRI
- Which of the following designers has devised the concept of Napkin PC?
- Mac Funamizu
- Orkin Design
- Won-Seok-Lee
- Avery Hollman
- Which of the following is not included in a B-membrane PC?
- Projector
- Touch screen keyboard
- Multimedia pen
- Optical drive
State True or False
- E-commerce refers to the physical transfer of goods on the Internet.
- All processes in e-commerce are expressed in terms of numeric values.
- Most cell phones and WAP-enabled PDAs have data transfer rate of 14.4 kbps or less as compared to a typical 56 kbps modem.
- HTML can be used instead of WML in WAP.
- Most web pages are designed for a resolution of 640 × 480 pixels, which is acceptable for a desktop computer.
- In Pen PC, the pens communicate with each other via RF technology.
- The USB memory stick fashes blue light for images.
- Won-Seok-Lee has devised the concept of B-membrane PC.
- E-paper can retain the images intact for an indefinite period of time.
- In IPTV, the local exchanges receive the incoming data, reassemble the packets into coherent video stream, and decode it to be viewed on the television or some other form of screen.
Descriptive Questions
- What do you mean by e-commerce? Discuss its advantages and disadvantages.
- Explain the concept of EDI. List some benefits of EDI.
- What is brain computer interface? Explain its types and techniques.
- What is the purpose of blogs? List the steps for creating a blog.
- Discuss RFID along with its applications.
- Write short notes on:
- Smart card and its categories
- Applications of WAP
- Internet protocol television
- USB memory stick
- Explain the futuristic computers concept in brief.
ANSWERS
Fill in the Blanks
- E-commerce
- Procurement, Order fulfilment, Managing trading-partner
- Digital string
- Standard format, Data element dictionary
- Binary values
- Partially invasive BCI
- E-paper napkin
- Unicast, Multicast
- Blog
- Roll top computer
Multiple-choice Questions
- (d)
- (b)
- (b)
- (d)
- (a)
- (c)
- (a)
- (b)
- (d)
- (c)
State True or False
- True
- False
- True
- True
- True
- True
- True
- False
- True
- True
