Chapter 3
Configuring Active Directory
IN THIS CHAPTER
![]() Discovering directories
Discovering directories
![]() Examining how Active Directory is structured
Examining how Active Directory is structured
![]() Setting up a domain controller
Setting up a domain controller
![]() Creating organizational units
Creating organizational units
Active Directory is among the most important features of Windows Server, and much of your time as a network administrator will be spent keeping Active Directory neat and tidy. This chapter lays some foundation by explaining what Active Directory is and how it works.
What Directories Do
Everyone uses directory services of one type or another every day. When you look up someone’s name in a phone book, you’re using a directory service. But you’re also using a directory service when you make a call: When you enter someone’s phone number into your touch-tone phone, the phone system looks up that number in its directory to locate that person’s phone.
Almost from the very beginning, computers have had directory services. When I got started in the computer business back in the 1970s, I used IBM mainframe computers and a transaction-processing system called CICS that’s still in widespread use today. CICS relied on many different directories to track such things as files available to the system, users that were authorized to access the system, and application programs that could be run.
But the problem with this directory system, and with most other directory systems that were popular in those days, is that it was made up of many small directory systems that didn’t know how to talk to one another. I have the very same problem at home. I have my own little personal address book that has phone numbers and addresses for my friends and family members. I have a Day-Timer book with a bunch of other phone numbers and addresses. Then I have a church directory that lists everyone who goes to my church. Oh, and there’s the list of players on the softball team I coach, and of course, my cellphone has a directory.
All counted, I probably have a dozen sources for phone numbers that I routinely call. So when I need to look up someone’s phone number, I first have to decide which directory to look in. Some of my friends are listed in two or three of these sources, which raises the possibility that their listings are out of sync.
That’s exactly the type of problem that Active Directory is designed to address. Before I get into the specifics of Active Directory, however, I show you the directory system that Microsoft used on Windows networks before Active Directory became available.
Remembering the Good Ol’ Days of NT Domains
Active Directory was introduced with Windows 2000 Server. Before then, the directory management system in a Windows network was managed by Windows NT domains, which stored directory information in a database called the Security Account Manager (SAM) database.
PDCs and BDCs
The most important thing to know about NT domains is that they are servercentric — that is, every Windows NT domain is under the control of a Windows NT server computer that hosts the primary copy of the SAM database. This server is called the Primary Domain Controller (PDC).
Large networks couldn’t work efficiently if all directory access had to be channeled through a single computer, of course. To solve that bottleneck problem, Windows NT domains can also be serviced by one or more Backup Domain Controllers (BDCs). Each BDC stores a read-only copy of the SAM database, and any changes made to the SAM database on the PDC must be propagated down to the BDC copies of the database.
Note that although any of the BDC servers can service access requests such as user logons, all changes to the SAM database must be made via the PDC. Then those changes are copied to the BDC servers. Naturally, this arrangement raises the possibility that the PDC and BDC database are out of sync.
If the PDC should fail for some reason, one of the BDCs can be promoted so that it becomes the PDC for the domain. This promotion allows the domain to continue to function while the original PDC is repaired. Because the BDC is an important backup for the PDC, it’s important that all NT networks have at least one BDC.
Trusts
Many organizations have directory needs that are too complicated to store on just one NT domain PDC. In that case, the organization can create two or more separate domains for its network, each with its own PDC and BDCs. Then the organization can set up trusts among its domains.
Simply put, a trust is a relationship in which one domain trusts the directory information stored in another domain. The domain that does the trusting is called — you guessed it — the trusting domain, and the domain that contains the information being trusted is called the trusted domain.
Trust relationships work in one direction. Suppose that you have two domains, named DomainA and DomainB, and a trust relationship is set up so that DomainA trusts DomainB. That means that users whose accounts are defined in DomainB can log on to DomainA and access resources. The trust relationship doesn’t work in the other direction, however: Users in DomainA can’t log on and access resources defined in DomainB.
Also, trust relationships aren’t transitive. (There’s a word that takes you back to high-school algebra.) That means that even if DomainA trusts DomainB and DomainB trusts DomainC, DomainA doesn’t automatically trust DomainC. For DomainA to trust DomainC, you’d have to create a separate trust relationship between DomainA and DomainC.
NetBIOS names
One other important characteristic of Windows NT domains is that they use NetBIOS names. Thus, NT names such as computer names and domain names are limited to 15 characters.
Active Directory to the Rescue
Active Directory solves many of the inherent limitations of Windows NT domains by creating a distributed directory database that keeps track of every conceivable type of network object.
Active Directory is a comprehensive directory management system that tracks just about everything worth tracking in a Windows network, including users, computers, files, folders, applications, and much more. Much of your job as a network administrator involves working with Active Directory, so it’s vital that you have a basic understanding of how it works.
One of the most important differences between Active Directory and NT domains is that Active Directory isn’t servercentric. In other words, Active Directory isn’t tied to a specific server computer, the way a Windows NT domain is. Although Active Directory still uses domains and domain controllers, these concepts are much more flexible in Active Directory than they are in Windows NT.
Another important difference between Active Directory and NT domains is that Active Directory uses the same naming scheme that’s used on the Internet: Domain Name System (DNS). Thus, an Active Directory domain might have a name like sales.mycompany.com.
Understanding How Active Directory Is Structured
Like all directories, Active Directory is essentially a database management system. The Active Directory database is where the individual objects tracked by the directory are stored. Active Directory uses a hierarchical database model, which groups items in a treelike structure.
The terms object, organizational unit, domain, tree, and forest are used to describe the way Active Directory organizes its data. The following sections explain the meaning of these important Active Directory terms.
Objects
The basic unit of data in Active Directory is called an object. Active Directory can store information about many kinds of objects. The objects you work with most are users, groups, computers, and printers.
Figure 3-1 shows the Active Directory Manager displaying a list of built-in objects that come preconfigured with Windows Server 2019. To get to this management tool, choose Start⇒ Administrative Tools⇒ Active Directory Users and Computers. Then click the Builtin node to show the built-in objects.
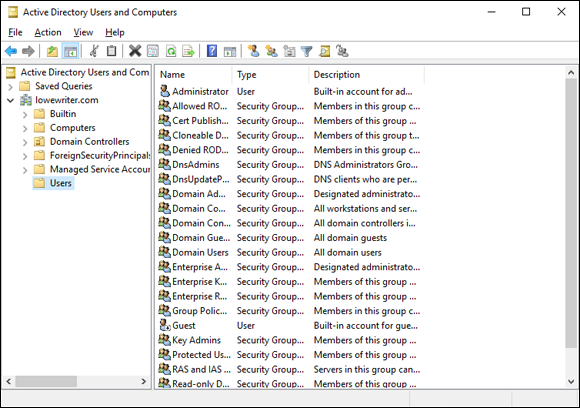
FIGURE 3-1: Objects displayed by the Active Directory Manager console.
Objects have descriptive characteristics called properties or attributes. You can call up the properties of an object by double-clicking the object in the management console.
Domains
A domain is the basic unit for grouping related objects in Active Directory. Typically, domains correspond to departments in a company. A company with separate Accounting, Manufacturing, and Sales departments might have domains named (you guessed it) Accounting, Manufacturing, and Sales. Or the domains may correspond to geographical locations. A company with offices in Detroit, Dallas, and Denver might have domains named det, dal, and den.
Note that because Active Directory domains use DNS naming conventions, you can create subdomains that are considered to be child domains. You should always create the top-level domain for your entire network before you create any other domain. If your company is named Nimbus Brooms, and you've registered NimbusBroom.com as your domain name, you should create a top-level domain named NimbusBroom.com before you create any other domains. Then you can create subdomains such as Accounting.NimbusBroom.com, Manufacturing.NimbusBroom.com, and Sales.NimbusBroom.com.
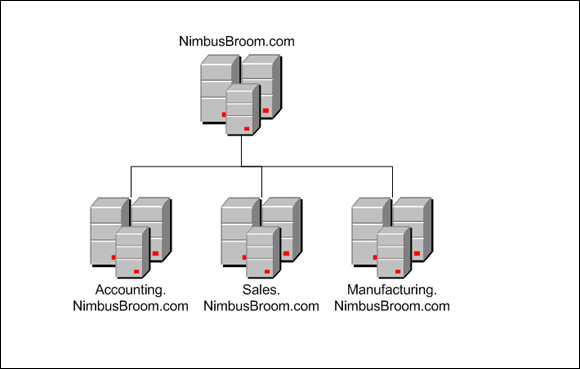
FIGURE 3-2: Domains for a company with three departments.
Note that these domains have little to do with the physical structure of your network. In Windows NT, domains usually are related to the network's physical structure.
Every domain must have at least one domain controller, which is a server that's responsible for the domain. Unlike a Windows NT PDC, however, an Active Directory domain controller doesn’t have unique authority over its domain. In fact, a domain can have two or more domain controllers that share administrative duties. A feature called replication works hard at keeping all the domain controllers in sync.
Organizational units
Many domains have too many objects to manage together in a single group. Fortunately, Active Directory lets you create one or more organizational units (OUs). OUs let you organize objects within a domain, without the extra work and inefficiency of creating additional domains.
One reason to create OUs within a domain is to assign administrative rights to each OU of different users. Then these users can perform routine administrative tasks such as creating new user accounts or resetting passwords.
Suppose that the domain for the Denver office, named den, houses the Accounting and Legal departments. Rather than create separate domains for these departments, you could create organizational units for the departments.
Trees
A tree is a set of Active Directory names that share a namespace. The domains NimbusBroom.com, Accounting.NimbusBroom.com, Manufacturing.NimbusBroom.com, and Sales.NimbusBroom.com make up a tree that's derived from a common root domain, NimbusBroom.com.
The domains that make up a tree are related to one another through transitive trusts. In a transitive trust, if DomainA trusts DomainB and DomainB trusts DomainC, DomainA automatically trusts DomainC.
Forests
As its name suggests, a forest is a collection of trees. In other words, a forest is a collection of one or more domain trees that do not share a common parent domain.
Suppose that Nimbus Brooms acquires Tracorum Technical Enterprises, which already has its own root domain named TracorumTech.com, with several subdomains of its own. You can create a forest from these two domain trees so that the domains can trust each other. Figure 3-3 shows this forest.
The key to Active Directory forests is a database called the global catalog. The global catalog is sort of a superdirectory that contains information about all the objects in a forest, regardless of the domain. If a user account can't be found in the current domain, the global catalog is searched for the account. The global catalog provides a reference to the domain in which the account is defined.
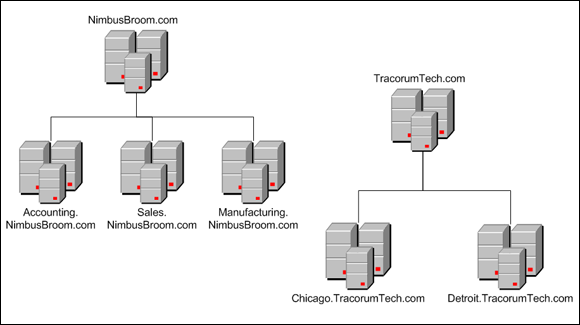
FIGURE 3-3: A forest with two trees.
Creating a New Domain
To create a domain, you start by designating a Windows Server 2019 system to be the new domain's controller. You can do that by using the Server Manager to install the Active Directory Domain Services role. (Refer to Chapter 1 of this minibook for instructions on installing server roles.) After you’ve installed Active Directory services, click the Notifications icon near the top-right corner of the Server Manager, and choose Promote This Server to a Domain Controller. This command launches the wizard shown in Figure 3-4.
This wizard lets you designate the server as a domain controller. As you can see, the wizard gives you three options:
- Add a Domain Controller to an Existing Domain: Choose this option if you’ve already created the domain and want to add this server as a domain controller.
- Add a New Domain to an Existing Forest: If you’ve already created a forest but want to create a new domain within the existing forest, choose this option.
- Add a New Forest: This option is the one to choose if you’re setting up a new domain in a brand-new forest.
When you create a new domain, the configuration wizard asks you for a name for the new domain. If you’re creating the first domain for your network, use your company’s domain name, such as NimbusBroom.com. If you’re creating a subdomain, use a name such as Sales.NimbusBroom.com.
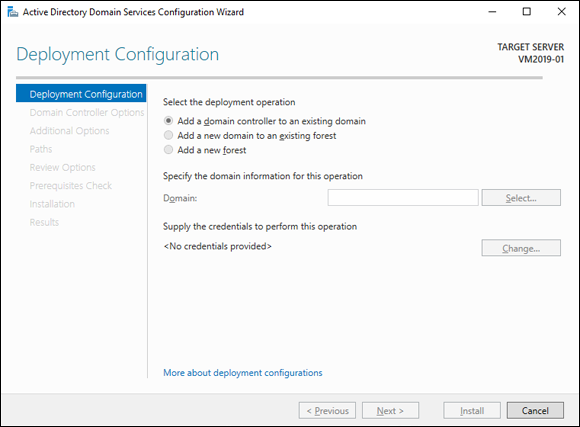
FIGURE 3-4: Creating a domain controller.
Creating an Organizational Unit
Organizational units can simplify the task of managing large domains by dividing users, groups, and other objects into manageable collections. By default, Active Directory domains include several useful OUs. The Domain Controllers OU, for example, contains all the domain controllers for the domain.
If you want to create additional organizational units to help manage a domain, follow these steps:
In Server Manager, choose Tools⇒ Active Directory Users and Computers.
The Active Directory Users and Computers console appears, as shown in Figure 3-5.
Right-click the domain you want to add the OU to, and choose New⇒ Organizational Unit.
The New Object – Organizational Unit dialog box appears, as shown in Figure 3-6.
- Type a name for the new organization unit.
Click OK.
You're done!

FIGURE 3-5: The Active Directory Users and Computers console.

FIGURE 3-6: Creating a new organizational unit.
- Builtin
- Computers
- Domain Controllers
- ForeignSecurityPrincipals
- Managed Service Accounts
- Users
Two of these OUs — Computers and Users — seem like the natural place for you to store Active Directory records for the computers and users on your domain. I recommend against doing that, though. Instead, you should create your own arrangement of OUs to manage the Active Directory objects you’ll create for your network.
I suggest you start by creating a single OU immediately beneath your domain. You can call it whatever you want — use your domain name (without the .com or other top-level domain), or use a short nickname for your organization. For example, for the lowewriter.com domain, I'll call the OU simply Lowe.
Then, within that, create OUs to contain the three most common types of Active Directory objects you’ll create: Computers, Groups, and Users. Thus, for my Active Directory, I use the following structure:
lowewriter.com
Lowe
Computers
Groups
Users
Within those OUs, you can create additional OUs as needed.
Here are just a few more thoughts about OUs to ponder as you drift off to sleep:
- You can delegate administrative authority for an OU to another user by right-clicking the OU and choosing Select Delegate Control from the contextual menu. Then you can select the user or group that will have administrative authority over the OU. You can also choose which administrative tasks will be assigned to the selected user or group.
- Remember that OUs aren’t the same as groups. Groups are security principals, which means that you can assign them rights. Thereafter, when you assign a user to a group, the user is given the rights of the group. By contrast, an OU is merely an administrative tool that lets you control how user and group accounts are managed.
- For more information about how to create user and group accounts as well as other Active Directory objects, turn to Chapter 4 of this minibook.

 Actually, NetBIOS names are 16 characters long. But NT uses the last character of the 16-character NetBIOS name for its own purposes, so that character isn’t available for use. As a result, NT names can be only 15 characters long.
Actually, NetBIOS names are 16 characters long. But NT uses the last character of the 16-character NetBIOS name for its own purposes, so that character isn’t available for use. As a result, NT names can be only 15 characters long. If you have Microsoft Visio, you can use it to draw diagrams for your Active Directory domain structure. Visio includes several templates that provide cool icons for various types of Active Directory objects.
If you have Microsoft Visio, you can use it to draw diagrams for your Active Directory domain structure. Visio includes several templates that provide cool icons for various types of Active Directory objects.