The previous sections each discussed a specific biometric property. Now, let's combine all this information to create an efficient identification system. The approach that we will implement follows the structure described in the figure below:
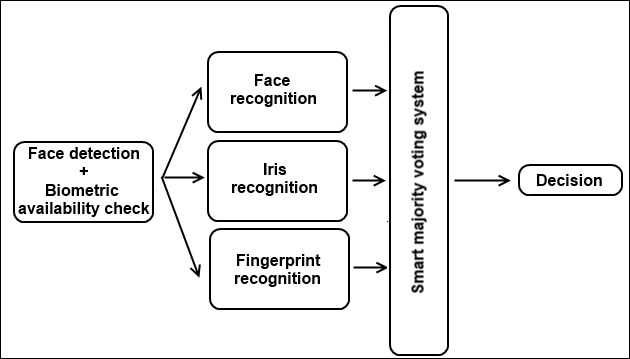
People authentication pipeline
As shown above, the first step is to use a camera interface to check if there actually is a person in front of the camera. This is done by performing face detection on the input image. We also test to see if the other biometric systems are active. This leaves us two checks that need to be performed:
- Check if the iris scanner is in use. This, of course, depends on the system used. If it depends on the eye retrieved from the face detection, this check should be ignored. If the eye is retrieved using an actual eye scanner, then there should at least be an eye detected to give a positive signal.
- Check if the fingerprint scanner is active. Do we actually have a finger available for taking a fingerprint picture? This is checked by applying background subtraction to the empty scene. If a finger is in place, then there should be a response to the background-foreground subtraction.
Of course, we are aware that some of these systems use pressure-based detection to find a hand or finger. In such cases, you do not have to perform this check yourself, but let the system decide whether to proceed or not.
Once we have all the systems, we can start the individual recognition systems described in previous sections. They will all output the identity of a known person from the common database that was constructed for this purpose. Then, all these outcomes are given to the smart majority voting. This system checks for several things:
- It checks if the biometric system checks actually succeeded, by returning their match from the database. If not, a person is not granted access and the system asks to reconfirm the failing biometrics.
- If the system has to measure biometrics more than three times in a row, the system jams and doesn't work until the owner of the system unlocks it. This is to avoid a bug in the current interface that exploits the system and tries to get in.
- If the biometric checks work, a smart majority voting is applied to the results. This means that if two biometrics identify person A but one biometric identifies person B, then the output result will still be person A. If that person is marked as the owner, then the system will allow access.
- Based on the individual software provided with the separate subtopics, it should be quite straightforward to combine them into a single interface.
- If the system still fails (this is a case study, not a 100% failproof system), there are several things that can be done to achieve the desired results.
- You should try to improve the detection and matching quality of each separate biometric. This can be done by supplying better training data, experimenting with different feature extraction methods or different feature comparison methods, as discussed in the introduction to the chapter. The variety of combinations is endless, so go ahead and give it a try.
- You should try to give each biometric a certainty score on its output. Since we have multiple systems voting for the identity of a person, we could take into account their certainty on single classifications. For example, when running a database, matching the distance to the best match can be wrapped to a scale range of [0 100] to give a certainty percentage. We can then multiply the vote of each biometric by its weight and do a smart-weighted majority voting.
