CHAPTER 1
Security Fundamentals
In this chapter, you will learn about
• Requirements to earn the (ISC)2 Systems Security Certified Practitioner (SSCP) certification
• Primary goals of security related to confidentiality, integrity, and availability (CIA)
• Fundamental security terminology
Reviewing the Requirements for SSCP
The Systems Security Certified Practitioner (SSCP) certification is one of the certifications sponsored by the International Information Systems Security Certification Consortium, Inc., more commonly known as (ISC)2.
You must complete the following requirements to earn the certification:
• Have at least one year of cumulative work experience in one or more of the (ISC)2 SSCP domains
• Register for the exam
• Pass the exam
• Subscribe to the Code of Ethics and get endorsed
If you’ve earned certifications from other vendors (such as CompTIA), you’ll find that the (ISC)2 process is different. It is often confusing to people the first time they earn an (ISC)2 certification. The following sections explain the process of registering for the exam, some key information about the exam, the requirement to submit paperwork to validate your experience, and requirements to maintain the SSCP certification.
Have One Year of Experience
To earn the SSCP certification, you need to have a minimum of at least one year of cumulative paid full-time work experience in one or more of the seven (ISC)2 SSCP domains. The domains are as follows:
• Access Controls
• Security Operations and Administration
• Risk Identification, Monitoring, and Analysis
• Incident Response and Recovery
• Cryptography
• Network and Communications Security
• Systems and Application Security
(ISC)2 has added an alternative to the one year of experience requirement. If you don’t have the experience but do have a bachelors or masters degree in a cybersecurity program, you can use that instead. The degree must be from an accredited college or university and either focused on cybersecurity or in one of the preapproved degree programs listed by (ISC)2.
When you register for the exam, you identify the number of years’ experience that you have in any of the domains. After you take and pass the exam, you’re required to submit a résumé that documents this experience. Additionally, you must find an (ISC)2 certified professional (in good standing) to validate your experience and submit an endorsement form on your behalf. See the section “Getting Endorsed” later in the chapter for more details.
If you don’t have one year of experience, you can still earn the Associate of (ISC)2 designation. You still need to complete the other requirements, including passing the exam and subscribing to the Code of Ethics. You’ll then have up to two years to obtain the required experience and submit the endorsement form to convert your status from Associate of (ISC)2 to become a fully certified SSCP.
Registering for the Exam
The exams are computer based and administered at Pearson VUE test centers. You can register for exams through the Pearson VUE website (www.pearsonvue.com/isc2/). If you register online, you’ll need to have or create a Pearson VUE account. The Pearson VUE website also includes a search feature so that you can locate a test center near you.
Registering for the exam includes three steps:
1. Complete the examination agreement.
2. Answer questions related to criminal history and background.
3. Submit the exam fee.
Complete the Examination Agreement
The examination agreement requires that you confirm your assertions regarding your minimum one year of professional experience and requires that you legally commit to the adherence of the (ISC)² Code of Ethics. Refer to the section “Subscribing to the (ISC)2 Code of Ethics and Getting Endorsed” later in this chapter for an overview of the Code of Ethics.
Answer Questions Related to Criminal History and Background
The registration process requires you to answer several questions related to your history and background. These questions ask about the following topics:
• Felony convictions
• Involvement with hackers or hacking
• Revocation of any professional licenses, certifications, etc. or disciplinary actions
• Any use of aliases or pseudonyms
Answering yes to any of these questions doesn’t necessarily disqualify you. However, it’s best to resolve a potential problem before taking the exam. You can e-mail (ISC)2 at [email protected] to discuss your situation. If appropriate, (ISC)2 will declare you eligible to take the exam and pursue the certification.
Submit the Exam Fee
You submit the exam fee through Pearson Vue, the testing provider. The page www.vue.com/isc2/includes links you can use to create a Pearson Vue account, find a testing center close to you, and register for the exam. Some organizations purchase vouchers in bulk and give them to their employees. If you have a voucher, you can use it instead of submitting a fee.
Passing the Exam
The exam traditionally includes 125 multiple-choice questions and you have three hours to complete it. Most questions are stand-alone multiple-choice questions. However, you may encounter some scenario-type questions that start with a paragraph or two describing the scenario, followed by two or more multiple-choice questions about the scenario. For example, you may be given a scenario that explains an organization’s security goals, followed by questions that ask how best to implement those goals.
(ISC)2 maintains a large pool of questions and regularly adds new questions to the pool. However, (ISC)2 typically tests the new questions on actual exams before using them in the exam score. Up to 25 questions on any exam might be ungraded test questions that (ISC)2 has included for research purposes. You can think of these as beta questions that (ISC)2 analyzes for the questions’ effectiveness. For example, if everyone answers the beta question correctly, (ISC)2 may conclude that the question is too easy and needs to be revised. If everyone answers the question incorrectly, (ISC)2 will likely conclude that something is wrong with the question itself. Through this type of test question analysis, (ISC)2 attempts to identify problematic questions and revise them before including them in the questions that are graded. You won’t know which questions are graded questions and which questions are beta-type questions. In other words, you must treat each question as though it’s a valid question.
A score of 700 out of a possible 1,000 points is required to pass the exam. However, that doesn’t necessarily mean that you’ll pass the exam if you answer 70 out of 100 graded questions correctly, because questions aren’t weighted the same. Out of the 100 valid questions, some questions may be worth 10 points, more difficult questions may be worth more than 10 points, and easier questions may be worth less. Just as (ISC)2 doesn’t tell you which questions are graded, it doesn’t advertise the actual value of any question.
(ISC)2 derives the examination questions from the SSCP CBK. The SSCP Exam Outline is an excellent source to see which topics are tested. The last page includes a short section on Supplementary References, along with a link to list of references. The goal of this book is to compile the relevant knowledge from these references into a single source. However, I strongly encourage you to download and review a copy of the current Exam Outline to ensure the document hasn’t changed. The Exam Outline includes a listing of objectives and subobjectives for each of the domains. You’ll find an Exam Objective Map in the Introduction of this book. It lists the objectives that went live on April 15, 2018, and maps them to the chapter that covers the objectives.
Predicting Future Question Types
It’s worth noting that (ISC)2 added what it calls “innovative Drag & Drop and Hotspot” questions to the CISSP exam. (ISC)2 started using these new types of questions in January 2014, which was two years after the release of the CISSP Common Body of Knowledge (CBK) for that version of the exam. (ISC)2 didn’t change the objectives, but instead changed the way some of the questions are presented. (ISC)2 announced the changes a couple of months before implementing them.
(ISC)2 has not given any indication that it will implement these types of questions in the SSCP exam. However, it’s entirely possible that (ISC)2 will start adding them at some point, just as it did with the CISSP exam. If it does so prior to your exam, don’t let the questions scare you. If you understand the content, you should be able to answer the questions without too much trouble. The following sections give you an idea of how to handle these types of questions.
Drag & Drop Questions In a Drag & Drop question, you simply drag an object from one area of the screen to another. As an example, the following question asks you to identify symmetric encryption algorithms from a list:
Question: Which of the following algorithms are examples of symmetric encryption? Drag and drop the correct answers from the list on the left to the box on the right.
Figure 1-1 shows the initial display you might see, along with how the display looks after you have correctly answered the question.

Figure 1-1 Example Drag & Drop question
This is really just another way of presenting a multiple-choice question that asks you to select all the correct answers. Here’s an example of a multiple-choice question that tests the same knowledge:
Question: Which of the following algorithms are examples of symmetric encryption? (Select all that apply.)
A. AES
B. Blowfish
C. 3DES
D. RSA
While you won’t see the correct answer and an explanation when you take the exam, you might like this knowledge. For clarity, here is the correct answer and an explanation.
Answer: The correct answers are A, B, and C. Advanced Encryption Standard (AES), Blowfish, and Triple Data Encryption Standard (3DES) are all symmetric encryption algorithms.
D is incorrect. RSA (named after its authors Rivest, Shamir, and Adleman) is an asymmetric encryption algorithm.
Hotspot Questions In a Hotspot question, you simply click on an area of the screen to select the correct answer. As an example, the following question asks you to identify the best location for a public-facing web server:
Question: Your organization is planning to deploy a web server. It needs to be accessible via the Internet and will access a database on the internal network. Where should they locate the new web server? (Click on the area of the diagram to indicate your choice.)
Figure 1-2 shows the graphics for this question. The numbers (1 through 4) are for the explanation only and probably would not be on an actual Hotspot question.

Figure 1-2 Example Hotspot question
The Hotspot format is also just another way of asking a question to test your knowledge. Here’s an example of a similar question worded as a multiple-choice question:
Question: Your organization is planning to deploy a web server. It needs to be accessible via the Internet and will access a database on the internal network. Where should they locate the new web server?
A. On the Internet side of the firewalls (the area marked with a 1)
B. Between the firewalls (the area marked with a 2)
C. On the private side of both firewalls (the area marked with a 3)
D. With the database server (the area marked with a 4)
Answer: The correct answer is B. This area is a perimeter network or demilitarized zone (DMZ). It provides a layer of protection against external attacks, and helps prevent a compromised server from accessing internal resources. A is incorrect. Placing the web server directly on the Internet leaves it vulnerable to more attacks. C and D are incorrect. Placing a public-facing server on an internal network increases the risk of attacks for other resources on the internal network.
Predicting the Future Exam Type
(ISC)2 has implemented adaptive testing for the Certified Information Systems Security Professional (CISSP) exam. An adaptive exam uses algorithms to determine the candidate’s knowledge level and gives different questions based on how the candidate answered previous questions. Instead of answering 250 questions within six hours, a CISSP exam candidate will see between 100 and 150 questions in up to three hours.
If (ISC)2 follows the same path with the SSCP exam, you might see fewer questions and have less time to take it. However, implementing adaptive testing is more expensive so it’s entirely possible (ISC)2 won’t implement adaptive testing for the SSCP exam.
Subscribing to the (ISC)2 Code of Ethics and Getting Endorsed
After passing the exam, you need to subscribe to the (ISC)2 Code of Ethics and go through an endorsement process. Both are described in the following sections.
Subscribing to the Code of Ethics
The Code of Ethics includes a preamble and four canons describing (ISC)2’s ethical expectations of its certified practitioners. Candidates must commit to and abide by the Code of Ethics to earn and keep the SSCP certification. Members who violate any provision of the Code of Ethics may have their certification revoked based on recommendations from a peer review panel.
The following sections quote the preamble and canons exactly as they appear on the (ISC)2 page (https://www.isc2.org/ethics).
Code of Ethics Preamble The preamble consists of two points:
• The safety and welfare of society and the common good, duty to our principals, and to each other, requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior.
• Therefore, strict adherence to this Code is a condition of certification.
Code of Ethics Canons The four canons are as follows:
• Protect society, the common good, necessary public trust and confidence, and the infrastructure.
• Act honorably, honestly, justly, responsibly, and legally.
• Provide diligent and competent service to principals.
• Advance and protect the profession.
If a situation arises resulting in a conflict between the canons, the conflict should be resolved in the order in which the canons are listed. In other words, the first canon is more important than the second one, and so forth.
Getting Endorsed
As previously mentioned, when you register for the exam, you identify the number of years’ experience that you have in any of the domains. After you take and pass the exam, you’re required to submit a résumé that documents this experience. Additionally, you must find an (ISC)2 certified professional (in good standing) to validate your experience and submit an endorsement form on your behalf. You need to complete this endorsement process within nine months of learning that you’ve passed the exam. (ISC)2 completes periodic random audits to ensure the integrity of these documents.
Don’t worry if you currently don’t know an (ISC)² certified professional. During the course of your studies, you are very likely to meet one or more people who can endorse you. For example, if you join a local security group, you’re sure to run into someone with an (ISC)2 certification. (ISC)2 chapters exist around the world, and you don’t have to be certified to join. This page describes the chapters in more detail: https://www.isc2.org/chapters/default.aspx. Even if you don’t meet an (ISC)² certified professional, you can still get an endorsement through (ISC)2. You have to submit a special form to request (ISC)2 endorsement (see https://isc2.org/endorsement.aspx), and the process takes much longer to get an endorsement than it would take using the normal process.
Maintaining Your SSCP Certification
After you’ve earned the SSCP certification, you’re required to recertify every three years. The primary method of doing this is by acquiring 60 continuing professional education (CPE) credits every three years, with a minimum of 10 CPEs earned each year. Security constantly changes, and earning CPEs is one of the ways security professionals keep abreast of current security trends.
The CPE requirement is a surprise to some people, but many professions use the same concept. As an example, medical doctors are required to complete a minimum number of continuing medical education (CME) credits to maintain their medical licenses.
(ISC)2 categorizes CPE credits as Group A credits and Group B credits. Group A credits are for activities directly related to one of the domains in the CBK. Group B credits are optional and are earned for activities that are outside of the domain, but can still enhance a member’s general professional skills and competencies.
You typically earn one CPE credit for each hour you spend in a related activity. Group A credits can be earned by attending educational/training courses and seminars, attending conferences, attending vendor presentations, completing some academic courses, and preparing for a presentation, lecture, or training event. Some examples of Group B credits include attending a management course and participating in project planning activities. This is not an exhaustive list, but instead just a few examples.
To maintain your SSCP certification, you must earn the following CPE credits:
• At least 10 Group A CPEs annually
• At least 60 CPE credits during a three-year certification period
• At least 40 Group A CPE credits during a three-year certification period
• As many as 20 Group B CPE credits during a three-year certification period
Understanding Basic Security Concepts
Three primary goals of information security are to prevent the loss of confidentiality, the loss of integrity, and the loss of availability for information technology (IT) systems and data. You’ll find that most security practices and security controls are designed to help prevent losses in one or more of these areas. The SSCP objectives identify these as the CIA triad, using the initials for confidentiality, integrity, and availability. Figure 1-3 depicts the CIA security triad.
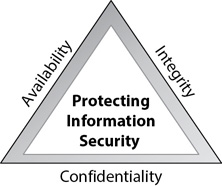
Figure 1-3 CIA security triad protecting information security
System and information owners are responsible for ensuring that security controls are in place to protect their systems and data. For example, managers that own proprietary data need to ensure that security controls are in place to prevent the unauthorized disclosure of that data. IT security personnel implement and maintain these security controls.
Confidentiality
You protect against the loss of confidentiality by ensuring that unauthorized users cannot access data. This starts by identifying and authenticating users, and then implementing access controls to restrict access. For example, you can use permissions to ensure that only authorized users can access the data.
Encryption provides another layer of protection for confidentiality. Figure 1-4 shows the overall process of encryption, where data starts as plaintext, is ciphered using an encryption algorithm, and then becomes ciphered text. For example, if you’ve ever ordered anything over the Internet using a credit card, you’ve probably used a Hypertext Transfer Protocol Secure (HTTPS) connection. HTTPS encrypted your credit card information to prevent unauthorized individuals from intercepting it and using it without your permission. If criminals had managed to capture this transmission, they wouldn’t have been able to read and use your credit card information.

Figure 1-4 Encryption used to provide confidentiality
Confidentiality only works when organizations implement secure encryption algorithms and practice sound security practices. With this in mind, it’s important to know which algorithms are secure and which algorithms have been compromised and shouldn’t be used anymore.
As an example, the Data Encryption Standard (DES) is an older encryption algorithm that was used to encrypt data. It is now considered compromised and it shouldn’t be used. The common replacement used today is the Advanced Encryption Standard (AES).
Integrity
Integrity controls prevent any unauthorized or unwanted modification of data or systems. Several different methods are used to protect integrity, including hashing and audit logging. Hashing methods will detect the alteration of data and alert personnel that it has lost its integrity.
A hash is simply a number created by performing a mathematical operation against data, such as a file or message. As long as the data stays the same, the hash (the number) will always be the same.
As an example, imagine that Sally needs to inform Joe of the price of a particular company’s stock. She creates an e-mail message stating “The price is $99” and creates a hash of the message. To keep the example simple, the hash for this message is 1234, though an actual hash would be much longer. Sally could re-create the hash on this message 100 times and each time it would be 1234. Here’s how she can use the hash to validate the integrity of the message after she sends it:
1. Sally sends her message to Joe along with the calculated hash, as shown in Figure 1-5.

Figure 1-5 Hashing used to check integrity
2. When Joe’s system receives the message, it calculates the hash again.
3. The received hash is the same as the calculated hash, providing assurances that the received message is the same as the sent message.
In contrast, imagine that someone intercepted the message and modified it before resending it to Joe, as shown in Figure 1-6. Joe’s system calculates the hash on the received message, “The price is .99,” and determines it is 9876. It compares the calculated hash (9876) against the received hash (1234) and discovers that the message is different. In other words, the message has lost integrity.
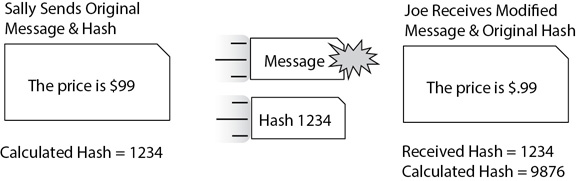
Figure 1-6 Hashing identifies altered data.
Using hashing alone, you can’t determine what altered the message. You only know that it was changed. However, this is valuable information. If the message is different, it shouldn’t be trusted.
While it’s important to be able to verify the integrity of data, integrity also applies to system configuration. As an example, organizations often use change and configuration management processes to prevent unexpected system outages resulting from changes to the system. If a technician makes an unauthorized change, it results in a loss of integrity for the system. Worse, many unauthorized changes have caused unexpected system outages.
You can also use audit logging for system integrity. An audit log tracks changes to a resource, including what was changed, who changed it, and when. A set of one or more audit logs creates an audit trail that you can use to verify whether the configuration of a system is the same or has been modified. If someone did make a change that caused an outage, investigators can use audit logs to identify what was changed and who made the change.
Availability
Preventing the loss of availability ensures that IT systems and data are available when needed. Note that there isn’t a timeframe here. Some organizations operate only during the daytime from Monday to Friday, so this is the only time when the systems are needed. Other organizations are operational 24/7, so the systems and data must also be available 24/7.
If users need to access data on a server and they can access it, then the data is available. However, if the data becomes corrupt or the server fails, the result is a loss of availability.
Organizations protect against loss of availability using a variety of different technologies. These include the following:
• Backups Regular backups capture a copy of the data. If something happens to the original data, administrators can restore the data from backups. It’s important to keep a copy of backup data in an offsite location, so that if a fire or other catastrophe destroys the entire building, the data is still available.
• Redundant disks Many Redundant Array of Independent Disks (RAID) systems will continue to operate even if a disk fails. A mirror (RAID 1) is one example of redundant disks. The RAID system stores identical data on two disks, and if one disk drive fails, a copy of the data is still available.
• Redundant servers If a service provided by a server is critically important to an organization, the organization can add redundant servers. For example, failover clustering uses multiple servers and ensures that a service will remain available, even if a server fails.
• Redundant connections Organizations often need to stay connected to the Internet or stay connected between buildings in separate locations via an intranet. When this connectivity is critical to the operation of the organization, two or more connections are used so that even if one fails, the organization still has connectivity.
• Redundant sites Many organizations must stay operational even if a catastrophic event destroys their building or makes it uninhabitable. For example, many locations are susceptible to earthquakes, tornadoes, floods, and hurricanes. An organization can plan for these catastrophes by establishing a separate location. Redundant sites are known as hot sites (ready at a moment’s notice), cold sites (an empty building with electricity and running water), and warm sites (a cross between a hot site and a cold site).
In addition to using fault-tolerant and redundant technologies, organizations create business continuity plans and disaster recovery plans. These help the organizations maintain the availability of critical systems even after a disaster.
Exploring Fundamentals of Security
In addition to knowing the main goals of security (the CIA security triad), you need to understand some basic terms and concepts for the SSCP exam. The following sections introduce these concepts and some of the common terminology.
Least Privilege
An important security principle is the principle of least privilege. In short, this means that you grant users access to what they need to perform their jobs, and no more. This includes granting permissions to access resources such as files and granting rights to perform actions such as modifying system configurations.
For example, consider a group of project managers and project team members who all need access to a folder named Project Data. The team members need to be able to read the data but not modify it, while the managers need full control over the folder. Table 1-1 shows a simple matrix identifying appropriate permissions. Notice that regular users are not granted any permissions because they don’t need access to any of this data to perform their jobs.
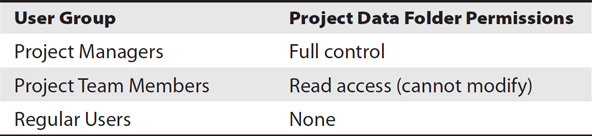
Table 1-1 Permission Matrix
If you instead gave the project team members full control permission on the folder, they would still be able to read the files, but they could also modify them or even delete them. Consider what could happen if the team members had full control and one of the team members became a disgruntled employee. That user could deliberately modify or delete data on the server. Even the most loyal employees can accidentally modify or delete files, but not if they don’t have permissions to do so. By assigning only the required permissions, you reduce the risk of anyone modifying or deleting the data.
Similarly, network administrators need elevated privileges to modify network and server configuration settings. Regular users don’t need these privileges to perform their jobs, so administrators ensure that regular users don’t have them. This reduces the possibility of a regular user accidentally making a change that affects the availability of a system.
Separation of Duties
Separation of duties is a security principle that ensures that no single person has complete control over a process. When properly implemented, separation of duties significantly reduces the risk of fraud within an organization.
Consider the process of approving and paying invoices. If Joe controlled the entire process, he could create an invoice for his own fictitious company, approve the invoice, and then make a payment to his own bank account. Of course, the loser in this scenario is the company that is employing Joe. Separating the payment process into two steps and assigning different people to handle each step reduces the risk of fraud. Figure 1-7 shows how one person approves the invoice, while another person pays the invoice. Because neither person has full control of the process, neither person can defraud the company without involving the other person.
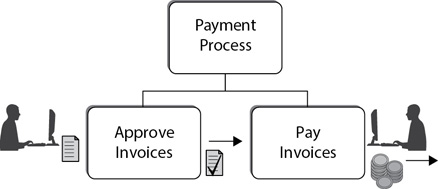
Figure 1-7 Separation of duties
Implementing separation of duties policies doesn’t eliminate the possibility of fraud, because the two employees could choose to collude to defraud the company. Therefore, many companies also use job rotation and mandatory vacations to reduce the risks of collusion. Chapter 13 covers both of these concepts in more depth.
Privacy and Data Sensitivity
Data is often an extremely valuable asset for an organization. Three types of data that are sensitive and require extra steps to protect are PII, PHI, and intellectual property.
Personally identifiable information (PII) is information that identifies an individual and includes items such as the person’s name, national identification number such as the U.S. Social Security number, and birthdate. Protected health information (PHI) is any information about an individual’s medical and health history.
National Institute of Standards and Technology (NIST) Special Publication (SP) 800-122, “Guide to Protecting the Confidentiality of Personally Identifiable Information (PII),” includes details on identifying and protecting PII. NIST SP 800-66, Revision 1, “An Introductory Resource Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule,” discusses various methods of protecting PHI.
Intellectual property refers to creations of the mind or intellect, such as literary and artistic works, and inventions. The World Intellectual Property Organization (WIPO) divides intellectual property into two categories: industrial property and copyrights. Industrial property applies to industrial designs, trademarks, and patents for inventions. Copyrights apply to literary works (such as books and screenplays), music, films, and other artistic works.
Organizations often apply confidentiality principles to protect sensitive data such as PII, PHI, and intellectual property. This includes using strong access controls to restrict access to the data. It also includes encrypting privacy data as an added layer of protection.
Defense in Depth
One of the primary tenets of security is that you’re never done. You can’t just write a security policy, install antivirus software or enable firewalls, and say, “There. We’re safe and secure now.” Instead, IT security uses the principle of defense in depth to implement several layers of security.
Consider Figure 1-8. It shows network resources protected through several layers of security. Chapter 9 covers security controls in greater depth, but in short, a security control attempts to reduce risk by either reducing vulnerabilities or minimizing the impact of a threat. One of the primary benefits of a defense in depth strategy is that even if a single control fails, other controls still provide protection.
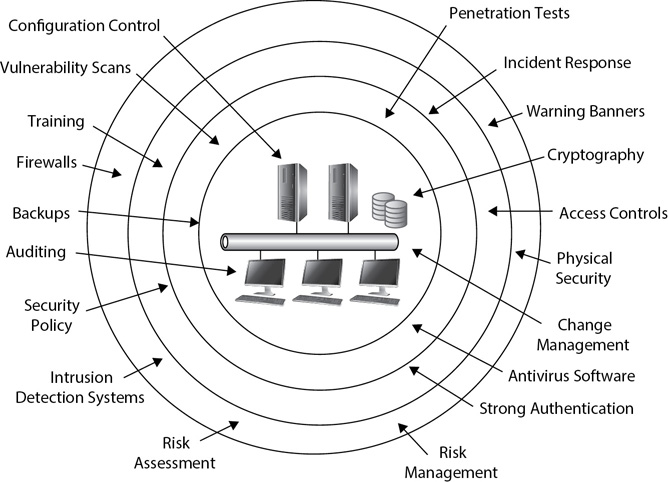
Figure 1-8 Defense in depth includes several layers of security.
For example, you may combine access controls with the principle of least privilege to restrict access to data within your organization. You may also have some research and development data that you want to ensure remains confidential. In addition to access controls and least privilege, you can use cryptography methods to add an extra layer of security for this research and development data. Even if someone is able to bypass the access controls, he or she will not be able to decrypt the data easily.
Nonrepudiation
Nonrepudiation ensures that a party cannot believably deny (or repudiate) taking an action. Audit logging and digital signatures are two common methods used to enforce nonrepudiation.
Consider a system that has audit logging enabled for a specific folder. If any user reads, modifies, or deletes data in the folder, the system logs the event in an audit log. The log includes who performed the activity, when they did it, and what they did. If Joe logs on to a computer using his credentials and he deletes a file, the audit log holds a record of his actions. Because the log recorded information from Joe’s credentials, you know that Joe did it.
Digital signatures also provide nonrepudiation. For example, if Sally sends an e-mail to Bob and signs it with a digital signature, Sally can’t later deny that she sent the e-mail. Digital signatures use certificates and public/private key encryption. They also provide authentication, giving assurances of who sent the e-mail.
Another example of nonrepudiation is related to commerce and e-commerce transactions. If you use a credit card to purchase a product and you sign the credit card bill, the company can use your signature to prove you are the person who made the purchase. You couldn’t later deny it, because your signature verifies that you purchased it. Similarly, e-commerce transactions require you to enter additional information such as the expiration date and the security code on the card. The idea is that only someone with the card in his or her possession knows this additional information.
AAAs of Security
The AAAs of security are authentication, authorization, and accounting. Combined, they help to ensure that only authorized entities have access to resources and that their access is recorded. Figure 1-9 shows the AAAs of security, and the following list explains them. While reading the explanations, imagine that Dawn is a project manager and she needs to modify project files stored on a server.
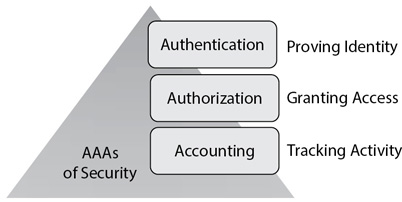
Figure 1-9 AAAs of security
• Authentication A user provides credentials (such as a username and password) that are checked against a database to prove the user’s identity. The authentication system verifies the credentials. In the scenario, Dawn’s username is her identity, and she provides the correct password to prove her identity. If she enters the correct username and password, the system authenticates her.
• Authorization Administrators assign rights and permissions to resources, which authorize users to access the resources. In the scenario, when Dawn attempts to access files on the server, the system checks to see if Dawn’s user account has been granted appropriate permissions and is authorized to access the files. If her account has appropriate permissions, the system grants her access. If her account doesn’t have appropriate permissions, the system blocks her access.
• Accounting Logging tracks activity of a user through monitoring. A basic accounting mechanism is an audit log, such as the Security log in Windows systems, and audit logs create an audit trail. Imagine that administrators have configured the server storing the project files to log events anytime someone accesses the files. When Dawn opens a file, the system logs an event in the Security log. Similarly, if she saves changes that modify a file, or deletes a file, the system records these events with log entries.
Note that you cannot restrict authorization without proper identification and authentication. If all users have the same account, you can either authorize access to everyone or block access to everyone. Similarly, without authentication, you can’t have accounting. If everyone used the same account, event logs could record when users accessed a resource, but they wouldn’t be able to record who accessed the resource.
Accountability
One of the underlying goals of the AAAs of security is accountability. If a system can identify individual users, track their actions, and monitor their behavior, it provides accountability. Authentication provides identification for users, and accounting tracks their activities in audit logs. If users are not required to authenticate or if audit trails are not created, then a system does not provide accountability.
It’s worthwhile noting that you don’t have to track every single action of a user to provide accountability. For example, your network may have proprietary data stored in a folder named Research and publicly available information stored in a folder named Public. You may want to track each time any single user accesses any single file within the Research folder. This includes any time someone views, modifies, or deletes a file. However, it’s not important to know who viewed any of the data in the Public folder; instead, you only want to know who modified it. In this situation, you would track all activity in the Research folder, but only some of the activity in the Public folder.
Due Diligence
Due diligence refers to the investigative steps that an organization takes prior to taking on something new, such as signing a contract or making a major purchase. In the IT world, an organization has an obligation to exercise due diligence to discover risks associated with a large purchase.
For example, if an organization is planning to purchase a software development company, that organization is obligated to exercise due diligence to determine as much as it can about the company and whether the purchase is a sound decision. Suppose the software company claims it earns about $100 million in revenue a year, but in actuality only earns $10,000. If the organization ignores due diligence and simply believes the company’s statements without verifying them, they may purchase the company based on the $100 million claim and pay way too much for it. By exercising due diligence and investigating the claims, the organization will likely discover the discrepancies and avoid the losses.
From an IT security perspective, an organization has a responsibility to exercise due diligence to discover risks. The goal is to identify risks that can result in the loss of availability, integrity, or confidentiality of any data or IT systems. Risks can’t be eliminated, but an organization can take steps to mitigate or reduce the risks by exercising due care.
Due Care
Due care is the practice of implementing security policies and practices to protect resources. It ensures that a certain level of protection is applied to protect against losses from known risks. The goal is to reduce the risk to the resources to a manageable level.
Because risks can’t be eliminated, an organization is likely to experience losses. If these losses are due to negligence, then the organization may face legal action against it. However, if the organization took due care to protect the resources but still suffered the loss, it’s less likely that a court will find the organization negligent.
For example, imagine that a company holds customer data—including names, addresses, birth dates, and credit card data—in cleartext in a database hosted on a web server. The company uses this information when customers make purchases through a website. A hacker checks out the website, discovers the database, and realizes that he can easily retrieve all the data. He steals the data and sells it to identity thieves, who proceed to steal millions of dollars.
Did the company take due care? Many would say no.
A web server accessible by users on the Internet will be attacked. It’s not a matter of if it will happen, but when. Further, if valuable data is on the server, attackers will find it. Even if it does have some protection, such as encryption, it’s still at risk if it’s accessible from the Internet.
Taking due care, the organization would implement security controls to protect the data. For example, administrators could store the customer information on a different server within the private network that isn’t accessible from the Internet but is accessible from the web server. Additionally, they could encrypt sensitive data on the server to protect against the loss of confidentiality. They don’t need to encrypt the entire database, but instead just encrypt columns holding sensitive data such as credit card data.
Chapter Review
There are several requirements to earn the (ISC)2 System Security Certified Practitioner (SSCP) certification. Candidates must have at least one year of experience in one of the seven domains defined by the (ISC)2 for the SSCP exam. During the registration process, candidates must agree to comply with the (ISC)2 Code of Ethics.
The SSCP exam is computer based and is administered at Pearson VUE test centers. The exam includes 125 questions, but up to 25 of these are ungraded beta questions. You need to score a minimum of 700 on a scale of 1,000 to pass the exam.
The CIA security triad includes confidentiality, integrity, and availability. System and information owners are responsible for ensuring that security and access controls are in place to prevent losses in these areas.
• Confidentiality protects against the unauthorized disclosure of information. You can ensure confidentiality with access controls and encryption.
• Integrity ensures that unauthorized users have not altered data. Hashing provides assurances that data, such as messages or files, has not been altered. Audit logs provide an audit trail identifying whether data has been modified, who modified it, and when.
• Preventing loss of availability ensures that systems and data are operational and available when needed. Organizations prevent the loss of availability with backups, fault tolerance, and redundant systems.
This chapter also presented several fundamental security terms:
• The principle of least privilege ensures that users are granted only the rights and permissions they need to perform their jobs, and no more.
• Separation of duties helps prevent fraud by ensuring that no single individual has complete control over a process. Instead, tasks are divided between multiple people.
• Organizations are responsible for protecting the confidentiality of sensitive data. Many laws mandate the protection of both PII and PHI. Organizations also have a responsibility for protecting intellectual property.
• Defense in depth provides a layered approach to security and protects an organization even if one or more security elements fail.
• Nonrepudiation prevents an individual from denying that he or she took an action. For example, if a user sends a digitally signed message, the user cannot later deny sending it, because a digital signature provides nonrepudiation.
• The AAAs of security are authentication, authorization, and accounting. Authentication identifies users, authorization defines what the users can access, and accounting tracks a user’s activities.
• If a system has accountability, it can identify and track the activity of a user. Accountability starts with strong authentication practices.
• Due diligence refers to the investigative steps that an organization takes prior to making a major purchase or taking on an obligation.
• Due care refers to the steps that an organization takes to protect resources. If an organization doesn’t take due care to protect resources, such as any individual’s private data, it can be susceptible to legal action or fines.
Questions
1. How many years of experience are required to earn the Associate of (ISC)2 designation?
A. Zero
B. One
C. Two
D. Five
2. What are the three elements of the security triad?
A. Authentication, authorization, and accounting
B. Confidentiality, integrity, and availability
C. Identification, authentication, and authorization
D. Confidentiality, integrity, and authorization
3. Who is responsible for ensuring that security controls are in place to protect against the loss of confidentiality, integrity, or availability of their systems and data?
A. IT administrators
B. System and information owners
C. CFO
D. Everyone
4. You are sending an e-mail to a business partner that includes proprietary data. You want to ensure that the partner can access the data but that no one else can. What security principle should you apply?
A. Authentication
B. Availability
C. Confidentiality
D. Integrity
5. Your organization wants to ensure that attackers are unable to modify data within a database. What security principle is the organization trying to enforce?
A. Accountability
B. Availability
C. Confidentiality
D. Integrity
6. An organization wants to ensure that authorized employees are able to access resources during normal business hours. What security principle is the organization trying to enforce?
A. Accountability
B. Availability
C. Integrity
D. Confidentiality
7. An organization has created a disaster recovery plan. What security principle is the organization trying to enforce?
A. Authentication
B. Availability
C. Integrity
D. Confidentiality
8. Your organization has implemented a least privilege policy. Which of the following choices describes the most likely result of this policy?
A. It adds multiple layers of security.
B. No single user has full control over any process.
C. Users can only access data they need to perform their jobs.
D. It prevents users from denying they took an action.
9. Your organization wants to implement policies that will deter fraud by dividing job responsibilities. Which of the following policies should they implement?
A. Nonrepudiation
B. Least privilege
C. Defense in depth
D. Separation of duties
10. Which one of the following concepts provides the strongest security?
A. Defense in depth
B. Nonrepudiation
C. Security triad
D. AAAs of security
11. Which of the following would a financial institution use to validate an e-commerce transaction?
A. Nonrepudiation
B. Least privilege
C. Authentication
D. Signature
12. What are the AAAs of information security?
A. Authentication, availability, and authorization
B. Accounting, authentication, and availability
C. Authentication, authorization, and accounting
D. Availability, accountability, and authorization
13. You want to ensure that a system can identify individual users, track their activity, and log their actions. What does this provide?
A. Accountability
B. Availability
C. Authentication
D. Authorization
14. Which of the following is required to support accountability?
A. Encryption
B. Authentication
C. Hashing
D. Redundant systems
15. Which of the following statements accurately describes due care?
A. It is the practice of implementing security policies and procedures to protect resources.
B. Due care eliminates risk.
C. A company is not responsible for exercising due care over PII.
D. Organizations cannot be sued if they fail to exercise due care over resources such as customer data.
Answers
1. A. You don’t need to meet the experience requirement to earn the Associate of (ISC)2 designation, so zero years of experience are acceptable. The SSCP certification requires one year of direct full-time security work experience. If you earn the Associate of (ISC)2 designation, you have two years from the date (ISC)² notifies you that you have passed the SSCP exam to obtain the required experience and apply to become a fully certified SSCP (which includes submitting the required endorsement form). The CISSP certification requires five years of experience.
2. B. The CIA security triad includes three fundamental principles of security designed to prevent losses in confidentiality, integrity, and availability. Authentication, authorization, and accounting are the AAAs of security, and identification, authentication, and authorization are required for accountability, but these are not part of the CIA security triad.
3. B. System and information owners are responsible for ensuring that these security controls are in place. IT administrators or other IT security personnel might implement and maintain them. While it can be argued that the Chief Executive Officer (CEO) is ultimately responsible for all security, the Chief Financial Officer is responsible for finances, not IT security. Assigning responsibility to everyone results in no one taking responsibility.
4. C. Confidentiality helps prevent the unauthorized disclosure of data to unauthorized personnel, and you can enforce it with encryption in this scenario. Authentication allows a user to claim an identity (such as with a username) and prove the identity (such as with a password). Availability ensures that data is available when needed. Integrity ensures that the data hasn’t been modified.
5. D. Integrity ensures that data is not modified, and this includes data within a database. Accountability ensures that systems identify users, track their actions, and monitor their behavior. Availability ensures that IT systems and data are available when needed. Confidentiality protects against the unauthorized disclosure of data.
6. B. Availability ensures that IT systems and data are available when needed, such as during normal business hours. Accountability ensures that users are accurately identified and authenticated, and their actions are tracked with logs. Integrity ensures that data is not modified. Confidentiality protects the unauthorized disclosure of data to unauthorized users.
7. B. Availability ensures that IT systems and data are available when needed. Disaster recovery plans help an organization ensure availability of critical systems after a disaster. Users prove their identity with authentication. Integrity provides assurances that data and systems have not been modified. Confidentiality protects against the unauthorized disclosure of data.
8. C. The principle of least privilege ensures that users have access to the data they need to perform their jobs, but no more. Defense in depth ensures an organization has multiple layers of security. Separation of duties ensures that no single user has full control over any process. Nonrepudiation prevents users from denying they took an action.
9. D. Separation of duties helps prevent fraud by dividing job responsibilities and ensuring that no single person has complete control over an entire process. Nonrepudiation ensures that parties are not able to deny taking an action. The principle of least privilege ensures that users have only the rights and permissions they need to perform their jobs, but no more. Defense in depth provides a layered approach to security.
10. A. Defense in depth provides a layered approach to security by implementing several different security practices simultaneously and is the best choice of the available answers to provide the strongest security. The security triad (confidentiality, integrity, and availability) identifies the main goals of security. Nonrepudiation prevents an individual from denying that he or she took an action. The AAAs of security are authentication, authorization, and accounting.
11. A. Digital signatures used by some online institutions to validate transactions and provide nonrepudiation. Least privilege ensures that users have only the rights and permissions they need to perform their jobs, and no more. Authentication verifies a user’s identity. A written signature is not used in e-commerce.
12. C. The AAAs of information security are authentication, authorization, and accounting. Availability is part of the CIA security triad (confidentiality, integrity, and availability), but it is not part of the AAAs of information security.
13. A. If a system can identify individual users, track their activity, and log their actions, it provides accountability. Availability ensures the system is operational when needed. Authentication identifies the individual using credentials. Authorization identifies resources that a user can access.
14. B. Users prove their identity with authentication, and strong authentication mechanisms are required to support accountability. Encryption helps provide confidentiality. Hashing helps provide integrity. Redundant systems help provide availability.
15. A. Due care is the practice of implementing security policies and procedures to protect resources. You cannot eliminate risk. A company is responsible for exercising due care over PII and can be sued if it fails to exercise due care.



