CHAPTER 4
Advanced Networking and Communications
In this chapter, you will learn about
• The difference between switches and routers
• Physical and logical segmentation of hosts and networks
• Securing the Voice over Internet Protocol (VoIP) with the Secure Real-time Transport Protocol (SRTP)
• Proxy servers and filtering methods
• Packet-filtering, stateful inspection, and application firewalls
• Defense diversity with firewalls
• The differences between network-based and host-based firewalls
• Risks and vulnerabilities related to remote access solutions
• Different tunneling protocols used with remote access
• Authentication methods used with remote access
• Network access control
• Virtualization environments
• Separating the control and data planes
• Cloud service models, shared responsibility, and operation models
Managing LAN-based Security
A local area network (LAN) connects computing devices together, allowing users to share resources such as data and devices. While LANs have helped improve productivity for many people, they have also added many risks. Because of this, it’s important for IT professionals to understand networks and some basic LAN-based security methods.
Comparing Switches and Routers
Switches connect devices together in a network and routers connect networks together. Figure 4-1 shows devices connected together via a switch in Network 1, devices connected together via a switch in Network 2, and both networks connected together via a router. Notice that Port 1 of the router is the gateway for computers in Network 1 to other networks. Similarly, Port 2 is the gateway for computers in Network 2 to other networks. Most networks have only one gateway labeled as the default gateway.
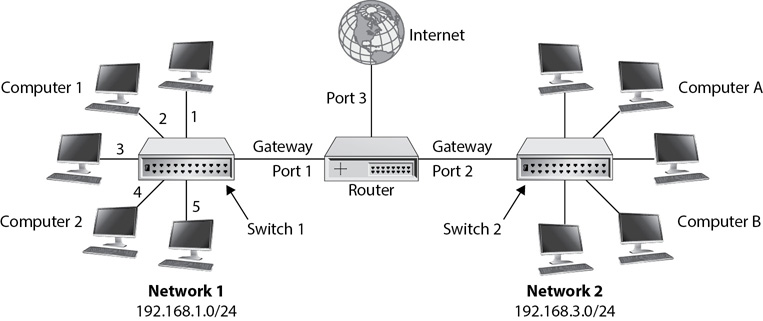
Figure 4-1 Comparing switches and routers
Chapter 3 covers the Open Systems Interconnection (OSI) Model and mentions how switches operate on layer 2 (the Data Link layer) and routers operate on layer 3 (the Network layer). Layer 2 uses media access control (MAC) addresses, and switches control traffic within a network using the MAC addresses. Layer 3 uses Internet Protocol (IP) addresses, and routers control traffic between networks using IP addresses.
Switches typically build tables mapping physical ports to the MAC address of the device connected to the port. For example, when Computer 1 sends traffic through the switch, the switch captures its MAC address and records it in the table. While administrators can statically configure the MAC address table, most switches create the table dynamically. Table 4-1 shows a table for the switch in Network 1. Note that Computer 1 is connected to physical Port 2 and Computer 2 is connected to physical Port 4. Other computers are connected to Ports 1, 3, and 5 but are just listed as other devices to simplify the discussion.
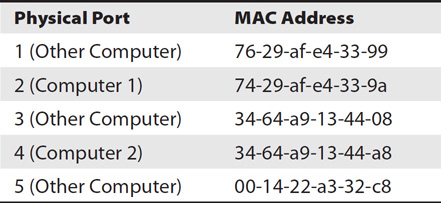
Table 4-1 MAC Address Table in a Switch
When Computer 1 sends unicast traffic to Computer 2, it includes the destination MAC address (34-64-a9-13-44-a8). The switch uses the MAC address table and sees that the destination MAC address is connected to Port 4, so it forwards the traffic to Port 4. This traffic doesn’t reach any of the other ports.
In contrast, older networks used hubs in place of switches. A hub forwards traffic going into one port to all other ports. This represents a risk because an attacker could configure a protocol analyzer (or sniffer) to capture traffic going through the hub. Chapter 5 covers sniffing attacks in more depth.
Switches can also restrict traffic with MAC address filtering, as discussed in Chapter 3.
Routers use tables too, but they use IP addresses and network addresses instead of MAC addresses. As an example, the routing table for the router in Figure 4-1 would include the following information:
• Physical Port 1 is connected to Network 1 (all IP addresses in the 192.168.1.0/24 network).
• Physical Port 2 is connected to Network 2 (all IP addresses in the 192.168.3.0/24 network).
• The path to all unknown networks (such as those on the Internet) is through Port 3.
Administrators can create routing tables manually or configure routers with routing protocols. Routing protocols such as Open Shortest Path First (OSPF) and Border Gateway Protocol (BGP) allow routers to share information with other routers and learn the best path to a different network.
Physical and Logical Segmentation
Network segmentation refers to breaking up a larger network into smaller interconnected networks. Figure 4-1 shows how a router segments traffic between two networks. The router divides a large network into two smaller networks using physical segmentation. Another method of segmenting a network is with virtual local area networks (VLANs) using logical segmentation. A VLAN allows an organization to segment traffic with a lot more flexibility when compared to segmenting traffic with a router.
Consider the single-network configuration shown in Figure 4-2. Imagine that Switch 1 connects the computers on a building’s first floor, and Switch 2 connects the computers on a building’s second floor. Switch 3 is connecting the two switches to the router. Configured like this, it creates a single broadcast domain. In other words, if any computer transmits broadcast traffic, it will reach all of the computers on the first and second floors. Routers do not pass broadcast traffic, so the broadcast domain does not extend beyond the router.

Figure 4-2 Building network on two floors
While this configuration works, it also presents a potential risk. Imagine that employees using computers 1 and 4 are working on a sensitive project. Data broadcasts between these two computers will go to all computers in the broadcast domain, meaning someone within the broadcast domain can capture this traffic with a sniffer.
One way to segment these two computers is to add another switch on the other side of the router. You can then connect the two computers to the switch as shown in Figure 4-3. However, this is highly inefficient. You have to add a switch and run additional cables from the switch to the computers on two separate floors.
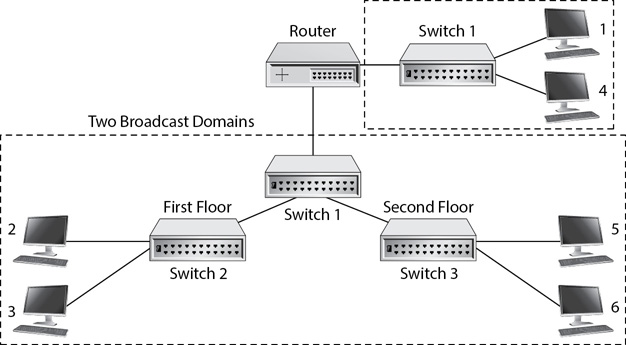
Figure 4-3 Inefficient network segmentation
VLANs provide a much more efficient solution, as shown in Figure 4-4. Computers 1 and 4 are within the VLAN named VLAN 10. This creates a logical broadcast domain for these two computers just as if they were configured with another switch connected to a different router port as shown in Figure 4-3. The switch doesn’t pass broadcast traffic within VLAN 10 to other devices on the network. Similarly, the switch won’t pass broadcast traffic from outside of VLAN 10 to computers 1 and 4. Less broadcast traffic also improves the performance of the LAN.
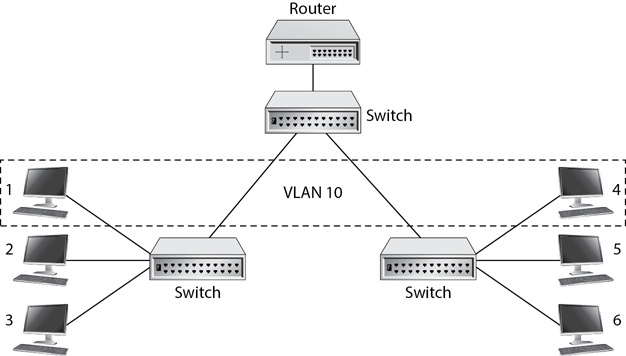
Figure 4-4 VLAN configuration
While Figure 4-4 shows a single VLAN, it’s also possible to create multiple VLANs. For example, you could create a VLAN for computers 2 and 5, and another VLAN for computers 3 and 6. VLANs provide several benefits:
• Security VLANs separate traffic from one broadcast domain to another. This is especially useful if sensitive data is transmitted over a network.
• Improved performance VLANs reduce the size of broadcast domains and improve their performance because there is less traffic within each broadcast domain.
• Reduced costs A VLAN doesn’t require any additional hardware if the switches support VLANs.
Secure Device Management
It’s important to protect routers and switches with strong physical security. A data center or server room already has strong physical security, so it is a good location for routers and switches. Another option that many organizations use is to store them in wiring closets. However, it’s important to ensure that the wiring closet is kept locked to prevent unauthorized access.
If attackers can access the devices, they can hook up a sniffer and capture traffic going through them. As an example, an attacker can connect a rogue access point to a switch. The access point will then transmit captured data wirelessly. The attacker can collect the data using a laptop while sitting in the parking lot outside the organization.
By default, a switch only forwards broadcast traffic to other ports, so the attacker cannot see all traffic going through the switch. However, most switches (and some routers) support port mirroring. Port mirroring sends a copy of all packets going through a switch to a separate port used for monitoring. Cisco switches support port mirroring with a feature called Switched Port Analyzer (SPAN), or the newer Remote SPAN (RSPAN) and Encapsulated RSPAN (ERSPAN). If the attacker can configure port mirroring using one of these features, it’s possible to capture all traffic going through the switch.
VoIP
Voice over Internet Protocol (VoIP) includes the different technologies used to transmit multimedia and voice communications over IP networks, including the Internet. It is possible to transmit VoIP over the Internet in a plain, unencrypted format, but such transmissions are easily intercepted. Instead, many VoIP implementations provide some type of protection for the transmissions.
RFC 3711 defines Secure Real-time Transport Protocol (SRTP), which provides confidentiality, message authentication, and replay protection for audio and video traffic, including VoIP. Chapter 14 covers cryptography topics in greater depth, but it’s worth mentioning that SRTP supports strong cryptographic methods such as Advanced Encryption Standard (AES) for encryption, and salting to protect against offline attacks. Salting adds bits to passwords or encryption keys to thwart brute-force attacks.
Using Proxy Servers
A proxy server is used as an intermediary, or proxy, for clients. Instead of clients’ retrieving web pages directly from the Internet, they send the request to the proxy server. The proxy server retrieves the web page on the client’s behalf and returns it to the client.
Chapter 3 briefly introduced proxy servers in the context of Network Address Translation (NAT). Remember that NAT translates private IP addresses to public addresses and public IP addresses back to private. Proxy servers commonly include NAT as an additional service. Additionally, proxy servers provide two more primary services: caching and filtering. Figure 4-5 shows how caching and filtering work.
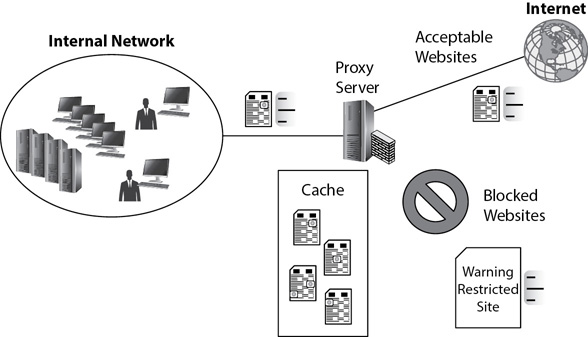
Figure 4-5 Proxy used for caching and filtering
When a user first retrieves a web page, the proxy server retrieves it from the Internet, stores a copy in cache, and sends a copy to the user. If another user requests the same page, the proxy server retrieves it from cache and sends the page to the other user instead of retrieving it from the Internet again. This improves performance for the clients and also reduces Internet bandwidth usage.
Most proxy servers can filter traffic based on the Uniform Resource Locator (URL). For example, if an organization wants to block employees from accessing websites with certain types of content, such as gambling sites, they can use a filter to block the URLs for these websites. Many organizations purchase lists of websites in certain categories from third-party companies. For example, if an organization wants to block users from accessing web-based e-mail, it can purchase a list of websites in the web-based e-mail category.
Administrators install the list of websites on the proxy server, and when users attempt to access a site on the list, the proxy server blocks the request. Instead, the proxy server displays a page indicating that the proxy server blocked their query. Many organizations personalize this web page to remind users about the organization’s security policy.
Some organizations have switched to whitelisting websites. For example, instead of blocking specific websites and allowing all others, an organization can list only the sites that are allowed and block all others. Although this does limit a user’s ability to surf the Internet, that is sometimes the goal.
Whitelists typically need to include more than just the website’s URL. As an example, many websites pull JavaScript and cascading stylesheet (CSS) libraries from other locations on the Internet.
Website developers often use JavaScript libraries to simplify the development process. These libraries include prewritten JavaScript snippets that developers use to create rich web applications. These libraries are typically stored elsewhere on the Internet, and called by web applications when they’re needed. When using a whitelist, the whitelist also needs to include the location of the JavaScript library.
Proxy servers are placed logically between the user and the Internet. It’s common to place the proxy server in the demilitarized zone (DMZ) and configure web browsers to send all web page requests to the Internet via the proxy server.
Understanding Firewalls
Chapter 3 introduced firewalls when describing differences between the Internet, an intranet, an extranet, and a DMZ. Network-based firewalls are placed inline with the traffic and they filter all traffic going into or out of a network. Host-based firewalls are software applications that run on individual systems such as a server or desktop computer. Firewalls have gone through several generations, as described in the following sections.
Packet-Filtering Firewall
The first generation of firewalls is packet-filtering firewalls that filter traffic based on the contents of a packet. More specifically, a packet-filtering firewall can filter traffic based on IP addresses, subnet addresses, ports, some protocols, or any combination of these:
• IP addresses Each packet contains the source and destination IP addresses. A packet filter can examine this data and either block or allow traffic to or from specific IP addresses. For example, if an attacker is launching an attack from a specific IP address, it’s possible to create a rule to block traffic from that IP address.
• Subnet addresses In addition to filtering specific IP addresses, you can filter entire subnets. For example, the network ID of 192.168.1.0/24 could be used to block or allow IP addresses from 192.168.1.1 through 192.168.1.254. Similarly, rules can block entire blocks of IP addresses, such as those from another country.
• Ports Well-known ports (ports from 0 to 1023) identify many protocols. For example, the well-known port for the Simple Mail Transport Protocol (SMTP) is port 25. By allowing traffic through port 25 (or opening port 25), you are effectively allowing SMTP traffic.
• Some protocols Many protocols are identified by a protocol number (or protocol ID) embedded in the IP header. For example, the protocol number for Internet Control Message Protocol (ICMP) is 1. A rule that blocks traffic with a protocol number of 1 blocks all ICMP traffic.
• A combination of IP addresses, ports, or protocols Any combination of IP addresses, ports, or protocols can be used. For example, consider Figure 4-6, which shows an e-mail server (named mail1) within a DMZ and another e-mail server (named mail2) in the intranet. Administrators would configure Firewall 1 to allow SMTP traffic (using port 25) to the mail1 server (using IP address 192.168.1.25). Similarly, administrators would configure Firewall 2 to allow e-mail traffic between mail1 and mail2. However, unless administrators add more rules to these firewalls, they will block SMTP traffic coming from the Internet and going directly to mail2.
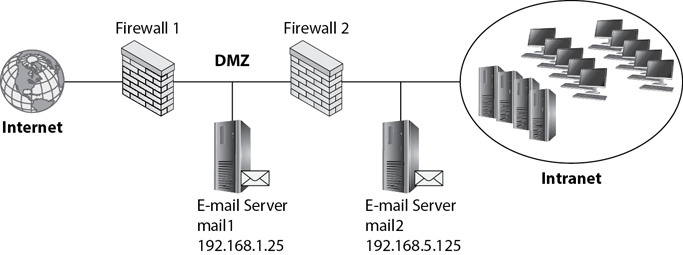
Figure 4-6 E-mail server within a DMZ
A packet-filtering firewall uses an implicit deny philosophy. All traffic is blocked (implicitly denied) unless there is a rule in the ACL that explicitly allows the traffic. Most firewalls automatically apply this rule, while some firewalls require administrators to add it. The implicit deny rule is placed at the end of the ACL and might look like one of the following statements:
• deny any
• deny any any
The actual syntax is dependent on the router brand and model, but the most important point is that it is the last rule in the ACL. If a previous rule doesn’t explicitly allow the traffic, this rule blocks the traffic. If you place this rule first in the ACL, the ACL will ignore any other rules in the ACL and deny all traffic.
Although a packet-filtering firewall is effective at blocking individual packets, it can be difficult to maintain when the ACL includes a large number of rules. Additionally, a large number of rules can negatively affect performance because the firewall must compare each packet against each rule.
Many organizations use a simple packet-filtering firewall at their boundary to the Internet. They do so by adding rules to the ACL of an external screening router. Although such a firewall doesn’t provide all the capabilities of a more advanced firewall appliance, it can be effective for smaller organizations.
Stateful Inspection Firewall
The second generation of firewalls is stateful inspection firewalls. They include the same capabilities of a packet-filtering firewall but can also filter traffic by examining much more than individual packets. Instead, they monitor the complete session. A stateful inspection firewall identifies active connections and monitors the status of these connections in a state table within the firewall.
As an example, a TCP session begins with the three-way handshake. The stateful inspection firewall uses this three-way handshake to identify that a session has started between two systems. The firewall can then monitor the traffic between the systems. Even though UDP connections don’t start with a three-way handshake, a stateful inspection firewall can still identify active UDP connections and track the state of the UDP connection.
A stateful inspection firewall is aware of packets exchanged in many communication sessions. When a session starts, the firewall dynamically opens ports based on the needs of the connections, and when the session completes, it dynamically closes ports.
In comparison, the packet-filtering firewall is a stateless firewall. It cannot determine whether a packet is part of an ongoing session between two systems or is from an attacker trying to probe or attack a system.
Application Firewall
An application firewall (also called an application proxy firewall, an application gateway firewall, and a third-generation firewall) includes different elements for different applications. For example, it would have a Hypertext Transfer Protocol (HTTP) proxy to examine web traffic, an SMTP proxy to examine e-mail traffic, a File Transfer Protocol (FTP) proxy to examine FTP traffic, and so on. Each proxy can analyze specific traffic for the protocol that it is monitoring and understands the individual protocol commands. For example, an HTTP proxy can interpret Get and Put commands used to retrieve and write web page elements, and administrators can configure the proxy to allow or block specific commands.
Although the application firewall does provide effective filtering for individual applications or protocols (such as HTTP, SMTP, and FTP), it requires a separate component for each individual protocol. If the firewall must filter many different protocols, this process can be extensive and negatively affect performance. However, if the firewall is being used only to filter a few protocols, it is manageable and can be highly efficient.
Application firewalls are often used with packet filtering. For example, the packet-filtering firewall can drop packets for protocols that aren’t desired based on the port, while the application proxy firewall can perform deep inspection of traffic for protocols that are allowed.
Next-Generation Firewall
Next-generation firewalls integrate multiple capabilities into a single security appliance, and these are often referred to as a unified threat management (UTM) device. Additionally, vendors update the UTM devices to adapt to new threats as they emerge.
Some of the additional capabilities that are included in UTM devices include
• Malware blocking UTM appliances typically include antivirus capabilities to detect and block malware before it enters the network. This includes malware included as attachments or downloaded from websites. Many UTM appliances can often detect and block malicious scripts embedded in web pages.
• Spam filtering Some UTMs include spam filters to block unwanted e-mail. This can be especially useful because attackers commonly use e-mail to launch various attacks. Chapter 5 discusses many common e-mail attacks such as phishing, spear phishing, and whaling.
• URL filtering UTMs commonly include URL-filtering capabilities, similar to a proxy server. URL filters can block users from accessing external websites.
Defense Diversity
Chapter 1 introduced the concept of defense in depth. A solid security program includes multiple layers of security so that even if one layer breaks down, other layers still provide protection. Similarly, defense diversity can be used when implementing a DMZ by using firewalls from two separate vendors.
For example, consider Figure 4-7. The firewall separating the Internet from the DMZ is from Cisco and the firewall separating the DMZ from the intranet is from Microsoft. Because the DMZ was created by firewalls from two different vendors, it is using defense diversity. Both firewalls are susceptible to vulnerabilities and both are regularly updated as vulnerabilities become known.

Figure 4-7 Implementing defense diversity with a DMZ
At any time, an attacker could discover a previously unknown vulnerability on either firewall. If both firewalls are the same model from the same vendor, both firewalls will be susceptible to the same vulnerability at the same time. However, if both firewalls are from different vendors, it is less likely that both will be subject to a vulnerability at the same time. Defense diversity with the DMZ firewalls provides an extra layer of protection for the internal network.
Additionally, defense diversity requires the attacker to have more skills and knowledge in order to exploit both firewalls. For example, an attacker may have extensive expertise with the Cisco router, but very little on the Microsoft router. Fewer attackers will have the same level of expertise on firewalls from different vendors.
Comparing Network-based and Host-based Firewalls
As previously mentioned, firewalls are often classified as either network-based or host-based. A network-based firewall provides protection for a network, while a host-based firewall provides protection for a single host. As an example, consider Figure 4-8. The two firewalls used to create the DMZ are network-based firewalls and are filtering all traffic coming into or out of the network.

Figure 4-8 Network with host-based and network-based firewalls
Additionally, each internal system is running a host-based firewall that filters traffic coming into or out of the computer’s network interface card (NIC). Both servers and desktop operating systems can run a host-based firewall as an additional application. As an example, many antivirus vendors now include firewalls as part of a comprehensive security suite.
Most organizations use both network-based and host-based firewalls. The network-based firewall filters and blocks malicious traffic coming from the Internet. Internal host-based firewalls block malicious traffic that reaches the internal network.
For example, imagine a user’s home computer is infected with malware. When transferring files from home to work with a USB flash drive, the user can inadvertently infect the work computer just by inserting the USB flash drive into the work computer. This virus may then have a worm component that tries to locate and infect other systems on the network. However, if other systems have host-based firewalls installed, they can block the worm.
Exploring Remote Access Solutions
Remote access solutions allow users from remote locations to access internal network resources. Remote users can connect via the Internet to a virtual private network (VPN), as shown in Figure 4-9. A VPN provides access to a private network over a public network such as the Internet.
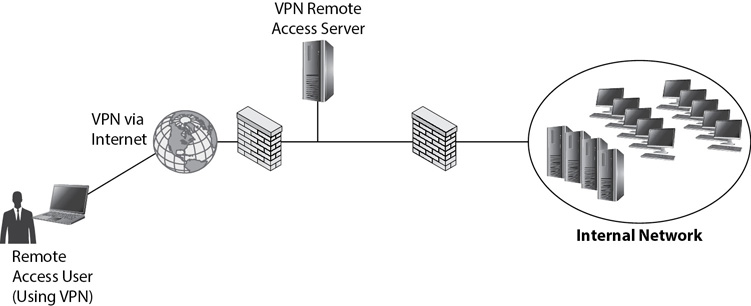
Figure 4-9 Remote access via dial-up or a VPN
It’s also possible to connect to a remote access server using a dial-up connection, though the connection is much slower. Employees of organizations hosting remote access servers typically have broadband access to the Internet, so it is much more common for organizations to host VPNs. Many organizations allow employees to work from home. VPNs support telework (sometimes called telecommute) practices, allowing employees to access resources within the corporate network from home.
Users with an Internet connection have a public IP address when they are connected to the Internet, typically assigned by their Internet service provider (ISP). The VPN remote access server also has a public IP address. The VPN client connects to the VPN server over the Internet, authenticates, and then accesses the private internal network.
Risks and Vulnerabilities
One of the primary risks of a remote access server is that anyone with access to a phone or the Internet can try to connect to the server. However, if strong authentication mechanisms are used, attackers cannot access the internal network because they lack the credentials to authenticate. Several different authentication protocols are available, and they are explored later in this chapter.
VPNs transfer data over the Internet in an encrypted format to prevent attackers from capturing the data. This includes authentication information, such as usernames and passwords, and the actual data. If the data isn’t encrypted, attackers can use a sniffer to capture the data transmissions and read the data. VPN tunneling protocols use encryption to prevent unauthorized disclosure of credentials and data.
Due to the inherent risks of using VPNs, many organizations simply don’t implement them. Instead, users perform all their work on the organization’s network while they are physically at the organization’s location.
Tunneling Protocols
A tunneling protocol encapsulates data used on an internal network and transmits it over the public network. For example, an internal network may use the Server Message Block (SMB) protocol with TCP/IP to access files and printers within an internal network. However, SMB is not used on the Internet. The tunneling protocol encapsulates SMB traffic to transmit it over the Internet.
Figure 4-10 shows the overall process. The client wants to transfer data using SMB. Before sending the data via the VPN, the client software encapsulates the SMB protocol data within a tunneling protocol. This encapsulated SMB data is then transmitted over the Internet to the VPN server. The VPN server strips off the tunneling protocol data, leaving only the SMB and TCP/IP data. The SMB data is then sent to the appropriate server within the internal network using TCP/IP. When the data is returned to the client, the VPN server again encapsulates the data in a tunneling protocol to send it back to the VPN client.

Figure 4-10 Encapsulating SMB data before sending it over the Internet
Although Figure 4-10 may give you the impression that the SMB data is sent in plaintext, that is not the case. Instead, the tunneling protocol encrypts the data before sending it over the Internet. If attackers intercept any of the data, they will not be able to read it.
Some of the tunneling protocols that you may see on the SSCP exam to encapsulate VPN traffic are Secure Shell (SSH), Layer 2 Forwarding (L2F), Point-to-Point Tunneling Protocol (PPTP), Internet Protocol security (IPsec), Layer 2 Tunneling Protocol (L2TP), with or without IPsec, and Transport Layer Security (TLS). The following subsections briefly describe these tunneling protocols.
Secure Shell
The Secure Shell (SSH) protocol can be used to create an encrypted tunnel. Although the concept is similar to that of other tunneling protocols where the underlying protocol is encapsulated, SSH isn’t commonly used for VPNs. It is used to encrypt other protocols such as Secure Copy (SCP) and Secure FTP (SFTP). Additionally, it’s often used to connect to remote servers because all data in transit between the client and the server is encrypted.
Layer 2 Forwarding
Cisco created the Layer 2 Forwarding (L2F) protocol as an early VPN tunneling protocol. L2F provides an authentication mechanism, but does not encrypt the traffic. It is rarely used today.
Point-to-Point Tunneling Protocol
Point-to-Point Tunneling Protocol (PPTP) was much more popular than L2F. RFC 2637 defines the standard generically, and Microsoft developed a Microsoft version. The RFC version doesn’t provide native encryption of the data, but the Microsoft version uses Microsoft Point-to-Point Encryption (MPPE) to encrypt the traffic in the tunnel. PPTP uses Generic Routing Encapsulation (GRE) to encapsulate the packets.
A significant weakness of PPTP is that the initial authentication connection is not encrypted. Information in the initial session can include usernames and passwords that can be intercepted by attackers. Even though the passwords are sent in a hashed form instead of in cleartext, attackers can capture them with a sniffer and use the usernames and password information in a replay attack. PPTP uses TCP port 1723.
Layer 2 Tunneling Protocol
Layer 2 Tunneling Protocol (L2TP) combines the strengths of L2F and PPTP and is documented in RFC 2661. Although L2TP doesn’t encrypt the traffic itself, it is commonly combined with IPsec for encryption and authentication and referenced as L2TP/IPsec. L2TP/IPsec provides a high level of security for VPNs and has been widely implemented.
A primary drawback with L2TP/IPsec is that IPsec packets cannot pass through a system using NAT. Recall that NAT translates private IP addresses to public addresses and public IP addresses back to private. Because of how the translation is done, it corrupts the IPsec packets. L2TP uses UDP port 1701.
Internet Protocol Security
Chapter 3 introduces Internet Protocol security (IPsec) as a secure protocol that provides mutual authentication of systems, integrity, and confidentiality. Recall that it uses the Authentication Header (AH) for authentication and integrity, and the Encapsulating Security Protocol (ESP) for encryption. It can be used with L2TP (as L2TP/IPsec) or by itself as a tunneling protocol. IPsec can work in two different modes:
• Tunnel mode In tunnel mode, the entire packet is encrypted and encapsulated into an IP packet. When tunnel mode is used for a VPN, this encapsulated packet is then sent over the Internet. When it reaches its destination, the encapsulated packet is decrypted and used on the internal network.
• Transport mode In transport mode, only the payload (the actual data) is encrypted. In other words, the IP header is not encrypted. In contrast, tunnel mode encrypts the entire packet, including the IP header. Transport mode is used within an internal network to encrypt traffic from one point to another.
The National Institute of Standards and Technology (NIST) published Special Publication (SP) 800-77, Guide to IPsec VPNs. It provides significantly more details on using IPsec for VPNs. You can view a list of SP 800 documents here: http://csrc.nist.gov/publications/PubsSPs.html.
Transport Layer Security
Many VPN solutions use TLS for the VPNs. As you might recall from Chapter 3, TLS is commonly used to encrypt HTTP (as HTTPS) over TCP port 443. A TLS VPN allows clients to connect with a web browser and it also uses TCP port 443.
A TLS VPN is a good solution when the VPN is having trouble getting through a NAT device, such as when using L2TP/IPsec without NAT-T. It’s also becoming popular because it doesn’t require any additional configuration on the client. The client only needs a web browser and knowledge of the URL to connect to the organization’s TLS VPN.
NIST published SP 800-113, Guide to SSL VPNs, in 2008. It mentions that an SSL VPN works the same as a TLS VPN, but at the time it was written, “SSL VPN” was a more popular term. Still, SP 800-113 provides a good in-depth description of TLS VPNs.
Another VPN option is to use an application instead of a web browser to connect to the VPN server. As an example, OpenVPN is an open source software application that can be used for VPNs. Users connect to the VPN server with the OpenVPN application instead of a web browser. Many desktop operating systems and mobile operating systems support the use of OpenVPN. For example, the OpenVPN Connect app is available for iPhones and iPads.
Full Tunnel and Split Tunnel Implementations
Tunneling protocols can be implemented as either full tunnels or split tunnels. This refers to how much of a user’s traffic is sent through an encrypted tunnel. As an example, imagine that Sally connects to a VPN through her employer’s organization to access internal resources. This VPN traffic is always encrypted in the VPN tunnel. Later, she goes to Google.com to do some research. Is her research traffic encrypted? It depends.
In a full tunnel, all traffic from the user is sent through the VPN tunnel and encrypted. In the example, Sally’s connection to Google.com goes from her computer, through the VPN tunnel to the organization’s VPN, and then back out to Google. The benefit is that all traffic can go through the organization’s protection technologies. For example, a next-generation firewall can scan the traffic and block malware. Similarly, a proxy server can filter traffic going to potentially malicious websites.
A split tunnel only encrypts the traffic directly related to the VPN. In the scenario, Sally’s connection to Google is not rerouted through the VPN tunnel, but instead goes directly to Google.
Authentication
One of the primary methods of controlling who can access a remote access server is authentication. Users claim an identity (such as with a username) and prove their identity (such as with a password) during an authentication process. Based on a user’s proven identity, access controls are checked to see whether the user is authorized to use the remote access server. If a user cannot be authenticated, the remote access server denies access. The following sections identify some common remote access authentication protocols.
PAP
The Password Authentication Protocol (PAP) is an older authentication protocol. Usernames and passwords are passed over the network in cleartext, which makes them highly susceptible to sniffing attacks. PAP is rarely used by itself. However, it is sometimes used with other protocols that encrypt PAP before transmission.
CHAP
The Challenge Handshake Authentication Protocol (CHAP) is more secure than PAP because the actual password is never sent over the wire. Instead, a nonce (a number used once) is combined with a shared secret known only to the client and the remote access server. The result of combining the nonce and the shared secret is then hashed with Message Digest 5 (MD5).
Hashing was briefly introduced in Chapter 1. As you’ll recall, a hashing algorithm (such as MD5) creates a number referred to as a hash. More specifically, MD5 creates a 128-bit number, or a 128-bit hash.
Putting it all together, here’s a big-picture view of how the process works. The client sends an authentication request to the remote access server. The server responds by sending back the nonce. The client then combines the shared secret with the nonce and hashes the result with MD5. This MD5 hash is then sent back to the server. Because the server knows the nonce (it created it) and it knows the shared secret, it can also calculate the hash on the server. If the MD5 hash sent by the client matches the MD5 hash calculated on the server, then the server authenticates the client.
MS-CHAPv1 and MS-CHAPv2
Microsoft improved CHAP with its versions of Microsoft CHAP (MS-CHAPv1) and MS-CHAPv2. Although MS-CHAPv1 is no longer used, MS-CHAPv2 is still used in many Microsoft implementations.
A primary improvement of MS-CHAPv2 is mutual authentication. In other words, the client authenticates to the server and the server also authenticates back to the client. This helps prevent the client from sending authentication data to an attacker impersonating the remote access server.
EAP
The Extensible Authentication Protocol (EAP) provides a more secure authentication process than many other remote authentication methods. EAP doesn’t use a specific method, but instead security developers can extend existing authentication methods using EAP. The following list identifies some of the commonly used EAP methods:
• Protected EAP (PEAP) PEAP encapsulates and encrypts the EAP transmission in a TLS tunnel. PEAP requires a certificate on the server, but clients are not required to have a certificate. A major advantage of PEAP is support by Microsoft systems and MS-CHAPv2 often uses PEAP.
• EAP-Tunneled TLS (EAP-TTLS) EAP-TTLS also uses TLS to create a tunnel to encapsulate the authentication method. It exchanges authentication information as attribute-value pairs (AVPs), allowing it to secure many older authentication methods (such as PAP, CHAP, and MS-CHAP). Note that while PAP sends the authentication information in cleartext, the TLS tunnel ensures that the authentication information is encrypted while in transit. EAP-TTLS requires a certificate on the authentication server, but clients do not need a certificate.
• EAP-TLS EAP-TLS provides the best security of these methods. It requires the server and each client to have a certificate, providing mutual authentication.
RADIUS
The Remote Authentication Dial-in User Service (RADIUS) provides centralized authentication, authorization, and accounting (AAA) for remote clients. When a remote user attempts to connect, the remote access server passes the request and user credentials to a RADIUS server. The RADIUS server verifies the user’s credentials and verifies the user is authorized to connect to the remote access server. After the user connects, the RADIUS server tracks the user activity in an accounting log.
Even though it has “dial-in” in the name, RADIUS is used for remote clients that connect through other sources, such as through a VPN.
Although a RADIUS server can be used for a single VPN server, it is more commonly used with multiple remote access servers. For example, Figure 4-11 shows several VPN servers hosted by an organization in different cities. Remote access users can connect to any of the servers over the Internet and then have access to the network physically located in that city.

Figure 4-11 Using RADIUS for authentication
In the figure, a remote access user is connecting to the Virginia Beach VPN server over the Internet. The user passes authentication credentials to the VPN server and the VPN server then passes this authentication information to the RADIUS server.
The RADIUS server might have an authentication database with the credential information (such as a database of usernames and passwords) of all authorized users. It’s also possible for the RADIUS server to check authentication with another server. For example, in a Microsoft network, the RADIUS server passes the authentication information to the domain controller. If the credentials are verified, the information is passed back to the remote access server and the client is authenticated. If a user connects to one of the other VPN servers (such as in New York), the VPN server passes the authentication information to the RADIUS server and the rest of the process is the same.
A primary benefit is that the authentication is centralized and only a single authentication database needs to be maintained. Imagine for a moment that an organization uses VPNs to allow administrators to remote in and perform administrative work. Administrators can remote into any of ten different VPN servers located in offices around the country. When a new administrator is added or removed from the administrative team, only one entry is needed on the RADIUS server. In contrast, if RADIUS were not used for central authentication, each of the ten different VPN servers would have to be modified.
Historically, RADIUS has used UDP and it only encrypts the password during the authentication session. However, RFC 6613 provides specifications for using TCP and RFC 6614 provides specifications for using TLS to encrypt the entire authentication session. As I write this, both RFCs are still in the experimental stage.
Diameter
Diameter is another AAA protocol and it was created as an alternative to RADIUS. It isn’t backward compatible with RADIUS, but it does provide several improvements. It uses TCP instead of UDP and supports both IPsec and TLS to encrypt sessions.
The name Diameter implies that it is twice as good as RADIUS. The radius of a circle is the distance from the center to an edge of the circle. The diameter of a circle is the distance from one edge of the circle to the other edge of the circle. In other words, the diameter of a circle is twice the distance of the radius.
TACACS+
Terminal Access Controller Access Control System+ (TACACS+) is another AAA protocol and is an alternative to RADIUS. Cisco originally created it as a proprietary protocol but later released it as an open standard. TACACS+ uses TCP so communication is more reliable than RADIUS transmissions. Also, TACACS+ encrypts the entire authentication process, while RADIUS only encrypts the password. TACACS+ uses TCP port 49.
Traffic Shaping and WAN Optimization
Traffic shaping refers to delaying certain types of traffic so that other traffic performs better. For example, audio and video streaming can consume a significant amount of bandwidth, so a traffic shaping policy would delay this type of traffic, giving preference to other traffic. Note that traffic shaping is not the same as packet filtering. Packet filtering drops undesirable traffic. Traffic shaping only delays it. The result is that other traffic is given priority.
Routers, firewalls, and dedicated hardware appliances are often used as traffic shaping devices. As an example of a dedicated appliance, it’s possible to place a Linux server with two network interface cards (NICs) behind a border firewall. All traffic would go through the appliance and software on the server can perform bandwidth management for different types of traffic.
Wide area networks (WANs) often use VPNs to connect, and traffic shaping is useful to optimize the WAN traffic. As an example, imagine that a remote office connects to the main location for a business via a site-to-site VPN as shown in Figure 4-12. Instead of connecting over the Internet, the locations are connecting via a leased T-1 at a speed of 1.544 Mbps. Compared to internal speeds of 1 Gbps or more, 1.544 Mbps is quite slow. Worse, the performance of this link can become even slower if users are regularly using it for streaming audio and video.
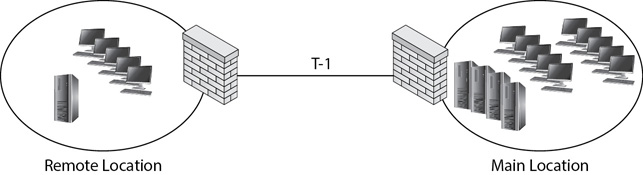
Figure 4-12 Site-to-site VPN
Traffic shaping will optimize the WAN link by delaying undesirable traffic. Note that this example focused on streaming audio and video, but an organization can choose to delay any type of traffic based on its needs.
Managing Network Access Control
Network access control (NAC) is a technology used to control which clients are granted access to a network. This is especially important when remote access solutions allow external clients into the private network. However, NAC can also control unhealthy clients within the network.
The overall goal of NAC is to inspect clients regularly to ensure they meet specific health requirements. Health is defined by criteria such as having up-to-date antivirus software installed and operational, having a host-based firewall enabled, and keeping the operating system up to date. These elements are defined in a health policy specified by administrators.
When NAC identifies an unhealthy client, it typically quarantines the client to prevent it from infecting other computers on the network. A quarantined network would also include resources that clients can use to improve their health, such as updates for the antivirus software or operating system.
When computers are completely controlled within an organization, administrators have several different tools and methods they can use to ensure that the systems are secure. They can automate the deployment of antivirus software and updates to the clients, automate the deployment of operating system updates, control what software is installed and running on the systems, and even control what the user can do on the system, such as what software the user can install.
However, remote access users may use a home computer over a VPN connection to access the private network. Because it’s a home computer, the organization’s administrators don’t have direct control over the computer. A significant risk is related to malware. If the infected system connects to the internal network, it can easily infect other computers on the network.
Figure 4-13 shows the overall process of how a NAC solution works. After a remote access user connects (via either dial-up or VPN connection), the remote access server coordinates with the NAC server to determine the health policy for the organization. The client is inspected to determine whether it meets the criteria of the health policy. If the client is healthy, it is granted access to the network. If the client is not healthy, the NAC server restricts access for the client to the quarantined network only.

Figure 4-13 Using network access control
Quarantined clients have access to some resources that can help them remediate any issues that prevent them from accessing the network. As an example, the quarantined network can include patches to bring clients up-to-date or current antivirus signatures. After a client is remediated, the NAC system will grant it admission back into the network.
Although NAC is often used for remote clients, it can also be used for internal clients. This helps prevent unhealthy systems from staying operational on the internal network. As an example, many automated methods exist to deploy operating system updates to clients. However, there are multiple reasons that a critical update may not be installed on a system, such as if the system is powered off while a user is on an extended vacation, business trip, or leave of absence. When the user turns the computer back on and tries to access the network, NAC checks its health and quarantines it if it is not healthy.
Additionally, many mobile device management (MDM) systems can interact with an existing NAC system, or provide NAC services. An MDM system can identify approved mobile devices and inspect them to ensure they meet preset requirements such as being up to date. Unapproved devices can be redirected to a guest network. Approved devices that don’t meet requirements can be redirected to the quarantined network. Healthy, approved devices can be given full access to the network.
Exploring Virtual Environments
Virtualization refers to replacing hardware with software. One of the first ways organizations did this was with servers. For example, imagine an organization has 100 servers within a data center. The organization can replace these servers with 20 powerful servers. Each of these physical servers can host five virtual machines (VMs) so the organization still hosts 100 servers.
While the cost of the 20 servers is high, an organization will quickly recoup its costs through other savings. For example, these 20 servers require less power; less heating, ventilation, and air conditioning (HVAC); and less space. Additionally, the organization reduces the hardware costs in future hardware refresh cycles. Instead of replacing 100 computers every three to five years, the organization replaces only 20 servers in the same timeframe.
In addition to creating VMs, it’s possible to create virtual networks within a host machine. These aren’t the same as VLANs created on switches. Instead, the host machine allows you to create and configure virtual switches and virtual routers running on the host machine. Administrators configure these virtual network devices to connect the host machines together and connect them to the live network.
Virtualization Terminology
Three important terms related to virtualization are host, guest, and hypervisor. The physical server is the host machine. Each VM running on the host machine is a guest and a host can run multiple guest VMs. The host runs hypervisor software such as Microsoft Hyper-V or VMware vSphere. The hypervisor is the software on the physical server that creates, runs, and manages the VMs. It also manages the resources for each of the VMs. These resources include the virtual data storage, memory, and networking components.
Because a host runs multiple guest VMs, it requires more resources than a typical server does. These physical resources include multiple processors, a significant amount of RAM, and fast drives. The host system shares the use of these resources with all the VMs.
Shared Storage
Guest VMs on host machines often share the same data storage, so it’s important to ensure it has enough space and is fast. At a minimum, it should use a fast Redundant Array of Independent Disks (RAID) subsystem. Another option is to use solid-state drives (SSDs), which are much faster than traditional hard disk drives.
A security concern with using shared storage is confidentiality. You want to ensure that users within one VM are not able to access data in another VM. Strong access controls will typically provide enough protection to prevent unauthorized access.
Chapter 11 covers data classifications in more depth. For example, the U.S. government classifies data as Top Secret, Secret, Confidential, and Unclassified. With this in mind, it’s best to put guest machines with similar data classifications on the same host system. In other words, you wouldn’t put a guest machine hosting Top Secret data on the same system hosting only Unclassified data.
Virtual Appliances
A virtual appliance is a preconfigured VM with an operating system and an application. The VM is ready to be added to a host machine as a guest. The benefit of a virtual appliance is that it is just a set of files that administrators can copy or import to a host machine. Of course, these virtual appliances are created for specific hypervisors. For example, a VM created for a Microsoft Hyper-V hypervisor will not run on a host machine using a VMware vSphere hypervisor.
As an example, Openfiler has created virtual appliances for file-based Network Attached Storage and block-based Storage Area Networking (NAS/SAN). The NAS features include support for the Common Internet File System (CIFS) and Network File System (NFS). The SAN features include support for Internet Small Computer System Interface (iSCSI) and Fibre Channel (FC). Openfiler has created virtual appliance images for a free version, and a full-featured Commercial Edition.
While Openfiler is one example, there is almost no limit to what vendors can create as a virtual appliance. This has caused many organizations to look at servers and virtualization differently. Instead of evaluating how many servers they need, they evaluate how many applications they want to host as VMs.
Virtual Desktop Infrastructure
A virtual desktop infrastructure (VDI) provides a virtual desktop for users. A user can log on to a server hosting VDI images and access a full-featured desktop including an operating system and all required applications. Some VDI-based systems support mobile clients. This allows clients to log on with a tablet or smartphone and access a specialized desktop for the mobile device.
When implementing VDIs, administrators need to decide if the desktops will be nonpersistent or persistent:
• Nonpersistent A nonpersistent desktop is the same for all users. If a user logs on and makes changes to the desktop, such as modifying the wallpaper, the changes aren’t saved. Additionally, data saved by a user in a user profile is not saved, so users should save their data elsewhere, such as in a network share. When a user logs out, the desktop is reverted to a known state. The benefit is that less disk space is required on the server. Nonpersistent VDIs are also easier to maintain because they are all the same.
• Persistent A persistent desktop retains all changes made by a user. Each time a user logs on to a VDI system and makes changes, the changes are saved and retained. A drawback is that persistent VDIs require more disk space for every user that logs on to the server.
Continuity and Resilience
Virtualization also contributes to continuity and resilience, increasing overall availability. Many cloud providers include elasticity features with virtual servers that they rent. For example, Amazon Elastic Compute Cloud (Amazon EC2) makes heavy use of virtualization. When customers rent cloud services through Amazon EC2, they rent access to virtual systems.
One of the benefits of elasticity is that capacity can easily shrink or expand based on the demand. In this way, users pay only for what they’re using. For example, if a customer’s website suddenly has a burst of activity and needs additional processing power or memory, it’s relatively easy for EC2 to expand the available resources for the site. When the additional resources are no longer needed, the virtual system can shrink back to the original size.
Many hypervisors allow administrators to manage the guest machines using a point-and-click interface. This allows them to easily create backups of an entire VM with just a few clicks. Additionally, some hypervisor management tools allow administrators to move VMs between host systems via a central server. As an example, imagine one host system is running five VMs but increased usage is overloading the host system. Administrators can use a point-and-click interface to move one or more of the VMs to another host, freeing up resources on the original host system.
It’s also much easier to restore a VM if it crashes, when compared to a physical server, assuming administrators keep up-to-date backups of the VMs. If a VM crashes, administrators can restore it by restoring the files. In contrast, if a physical server crashes, it takes much more to rebuild it from scratch.
Similarly, most hypervisors allow you to create snapshots of a system. These are very useful, especially before performing a risky operation such as an application upgrade. If the upgrade causes problems, you can revert the system to the state it was in when you created the snapshot.
Separation of Data Plane and Control Plane
Traditional hardware routers implement both the data plane and the control plane. A current trend is to replace hardware routers with software-defined networking (SDN), which separates these two planes. Before discussing SDN concepts, it’s worth defining the data plane and the control plane:
• Data plane The data plane (sometimes called the forwarding plane) uses rules within an ACL to identify whether the router will pass traffic or block traffic. These are the same type of rules described in the “Packet-Filtering Firewall” section earlier in this chapter. The data plane is responsible for deciding if traffic should be forwarded or not. The data plane is proprietary. In other words, rules used by one router often have different syntax when compared to rules created by another router manufacturer.
• Control plane The control plane is responsible for identifying paths to other networks. Routers typically do this with routing protocols such as OSPF and BGP. These routing protocols allow routers to share information with each other to create a virtual map of the network.
Software-defined Networking
Software-defined networks separate the data and control planes using virtualization technologies. This allows an organization to replace many of the hardware routers and switches with software. This helps organizations move away from proprietary hardware and also gives them much more flexibility.
As an example, Chapter 2 discusses Attribute-based Access Control (ABAC) models, which SDNs typically support. An ABAC model allows administrators to create policies that are much more versatile than rules within an ACL.
While SDN and network function virtualization (NFV) are relatively new technologies, they are growing fast. The 2015 Edition of the SDxCentral SDN and NFV Market Size Report includes several predictions of explosive growth. For example, it indicates sales of SDN products replacing traditional layer 2 and layer 3 hardware (switches and routers) will exceed $10 billion in 2015 and grow to more than $105 billion in 2020. For comparison, SDxCentral reported the SDN market size in 2013 was about $1 billion.
The section “Physical and Logical Segmentation” earlier in this chapter discussed how routers and switches provide physical segmentation of networks. Additionally, it mentioned how switches can be used to provide logical segmentation within a network. SDNs also provide logical segmentation by separating the data and control planes.
Protecting Virtualization Systems
As additional software running on the server, the hypervisor represents another potential risk. If an attacker can access the host machine from within a VM, the attacker potentially can access all the guest machines. The following list identifies some of the specific risks associated with virtualization, along with steps to protect against these risks:
• Improperly configured hypervisor The security of all the guest systems is directly related to the security of the hypervisor on the host. If administrators don’t adequately restrict access, it becomes easier for unauthorized personnel to gain access to all the systems. The key here is to ensure that administrators have appropriate training to manage and secure the hypervisors.
• Infected virtual appliances Free virtual appliances sound very appealing. However, it’s possible for attackers to infect these with Trojans or other malware, and once you add the virtual appliance, attackers have a foothold in your environment. This is similar to the many new computers built in foreign countries that have been shipped to users with malware preinstalled. Just as a single infected physical machine in your network can spread malware to other systems, a single infected VM can also spread malware. A key here is to be suspicious of any files downloaded from the Internet and to only use trusted files from a trusted source.
• Data leakage Because VMs are simply files, it’s very easy to copy an entire VM just by exporting and copying the files. If unauthorized personnel have access to these files, they might be able to import them to their own system running a hypervisor and access all the data within the VM. Additionally, attackers might be able to scan the data within the files and extract meaningful data. These VM files should be protected with the same level of security as the highest classification of data stored on the VM.
• Improperly configured virtual network Most network devices are configured by administrators with specialized knowledge about routers and switches. However, server administrators typically configure virtual network devices (such as virtual routers and virtual switches) on the host. They might not have the same level of knowledge and expertise and might configure them improperly. An improperly configured virtual network might incorrectly direct sensitive traffic to guest VMs on the host system.
• VM escape VM escape is an exploit that allows a guest to interact with the host system. As an example, contestants in the 2017 Pwn2Own hacking competition in Vancouver, Canada won $105,000 by successfully performing a VM escape attack. They escaped from a Windows 10 guest operating system running as a VM in VMware Workstation. They exploited a bug in the Microsoft Edge web browser, a bug in the Windows 10 kernel, and a buffer vulnerability in VMware Workstation. They achieved a complete VM escape gaining access to the host system. Microsoft and VMware have patched these bugs, preventing the same type of exploit again. Keeping systems patched is one of the best ways to prevent successful VM escape attacks.
Understanding Cloud Computing
Cloud computing refers to any type of computing services provided over the Internet. It has become quite popular in recent years. Cloud computing is very cheap and sometimes even free, but it includes some security concerns.
Shared Responsibility Models
Three common services provided through the cloud are Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS), and Infrastructure-as-a-Service (IaaS). The lines between these cloud services are sometimes blurred, partly due to how cloud vendors market them. However, one way to categorize them is to look at the different maintenance responsibilities, which correlate with security responsibilities. The Cloud Computing Security Requirements Guide, published by the U.S. Department of Defense (DoD), includes a figure similar to Figure 4-14. Figure 4-14 shows that the vendor has the most maintenance and security responsibility for SaaS, a little less for PaaS, and the least for IaaS.

Figure 4-14 Maintenance and security responsibility
SaaS
Software-as-a-Service (SaaS) is also known as on-demand software. It provides users with access to software or applications over the Internet. For example, Google provides several applications through the cloud, including Gmail for e-mail and Google Docs for other types of files, such as spreadsheets, presentations, and word processing documents. Users access the applications using a web browser. This allows the cloud-based applications to support different operating systems.
Domain Name System (DNS) also fits into the SaaS service model. Chapter 3 discusses DNS and how it resolves host names to IP addresses. For example, if you want to reach Google, you type google.com as the address in your web browser, and your system queries DNS to return an IP address. Organizations that maintain resources on the Internet need to ensure that they register and maintain records for these resources. They could create and maintain their own DNS server, but it’s often easier to outsource this and use a cloud provider to manage the records on the cloud provider’s DNS server. A huge benefit is that the cloud provider manages the security of the DNS server and often has more knowledge and expertise to thwart DNS attacks.
The “Exploring Remote Access Solutions” section earlier in this chapter discussed the use of VPNs for remote access. However, VPNs can also be used in a SaaS model. Users connect to the VPN service provider and surf the Internet through it. The VPN encrypts all traffic and prevents attackers from capturing the traffic. This is especially useful for wireless users accessing Internet resources through public hotspots.
Similarly, a proxy server is typically used within an organization for caching and web filtering. However, you can also subscribe to proxy services from some cloud providers. Administrators configure the proxy settings within the web browsers, which causes all Internet access to go through the cloud-based proxy server. The proxy server performs web filtering just as an in-house proxy server does.
PaaS
Platform-as-a-Service (PaaS) provides users with a computing platform. This includes hardware, an operation system, and applications. As an example, many web-hosting companies rent access to servers that are preconfigured with an operating system and web hosting applications, such as WordPress. Customers may install the applications from a list of available options, or the vendor may install the applications. The vendor performs all the hardware maintenance on the server, and typically performs most of the software maintenance. For example, the vendor would keep the server up to date with current patches. The customer is responsible for keeping applications up to date, but the vendor may help.
IaaS
Infrastructure-as-a-Service (IaaS) is sometimes called Hardware-as-a-Service, and this is a good way to think of it. Customers rent access to hardware, such as servers and networking infrastructure, and the vendor maintains the hardware. The customer is responsible for installing operating systems and applications on the hardware, and is responsible for maintenance of the operating systems and applications.
Cloud Operation Models
When considering security with cloud-based computing, it’s also worth examining the different operation models, or deployment models. NIST SP 80-144, Guidelines on Security and Privacy in Public Cloud Computing, defines the following four models:
• Public cloud Public cloud–based services are provided by third-party vendors and are available to anyone. As an example, Apple provides cloud-based storage via its iCloud service. Google hosts the Google Cloud Platform, which is a suite of cloud computing services developers use to create and serve cloud applications. Similarly, Amazon hosts Amazon Web Services (AWS), which provides a wide variety of cloud computing platforms.
• Private cloud A private cloud is available only to users within an organization. As an example, a company can set up cloud-based storage for its employees. The company would ensure the server is accessible via the Internet, but employees would be the only personnel authorized to access the server.
• Community cloud A community cloud is a private cloud that is shared by two or more organizations. For example, imagine that Globex set up a private cloud for Globex employees. Later, Globex and Acme sign a partnership deal and need an easy method to share files. Globex can configure its private cloud so that Acme employees can access it. It is now a community cloud.
• Hybrid cloud A hybrid cloud is a combination of any two or more clouds. It can be a combination of different clouds or similar clouds. For example, imagine that both Globex and Acme host their own private clouds. Later, they sign a partnership deal with each other, and Acme shares part of its private cloud with Globex, creating a community cloud. The Globex employees will be able to access a single cloud-based service and have access to both the private Globex cloud and the Acme community cloud.
A private cloud provides the best security for sensitive data. However, it’s worth remembering that a private cloud is still accessible via the Internet. If users don’t use secure passwords, or if they reuse their credentials on other sites, attackers may be able to access the data in the cloud. While a community cloud is similar to a private cloud in that it is private between the companies sharing the data, it’s important to ensure that only shared data is stored in the community cloud.
Storage
Storage in the cloud is almost limitless. An organization can easily rent the storage space it needs, and that space is often very cheap or even free. For example, Google Drive provides every user with 15GB of storage space for free. If you need more, you can rent 100GB for $1.99 a month. Microsoft OneDrive offers 5GB of storage for free and 5TB of storage for Office 365 subscribers. These are moving targets though, and the pricing might be different by the time you read this.
However, free storage isn’t necessarily safe storage. Organizations need to be careful about what they store in the cloud. A data breach with the cloud provider can result in a data breach for an organization.
When picking a cloud storage location, it’s sometimes useful to consider the legal jurisdiction of the storage location. As an extreme example, imagine the cloud provider accesses an organization’s data and sells it to a competitor. If the cloud provider is located in the same country, the organization can pursue a legal remedy. However, if the organization is in the United States and the cloud provider is in Russia, the organization may not have any legal options. Similarly, if a U.S. cloud provider outsources storage locations to other countries, sensitive data might wind up being stored in unfriendly locations.
Electronic discovery (e-discovery) refers to any process that searches data with the goal of using it as evidence. It also includes locating and securing the data so that it can be used in a civil or criminal case. Using a cloud provider from a local jurisdiction ensures that e-discovery processes can be used when necessary.
Privacy
Privacy of data posted on the Internet has always been a concern. A good guideline to adopt is that if you post data on the Internet, you have lost control of that data and might have also lost privacy of that data. This includes data that you store in the cloud.
Cloud computing attempts to provide users with privacy of their own data, but any cloud provider is vulnerable to attacks, potentially resulting in data loss or data leakage. When an organization hosts data on the Internet through a cloud provider, protection of that data is now partially dependent on the provider using adequate protection. If the provider has a failure, it can result in a data breach. Additionally, users often don’t know about the severity of a data breach right away.
For example, Dropbox, a cloud-based storage provider, suffered a data breach in mid-2012. It was unclear at the time how many user accounts were compromised. Four years later (2016), attackers posted details of over 65 million accounts from the 2012 data breach. Admittedly, users should have changed their passwords over the four-year timeframe, but all users aren’t security conscious. About a week before these details were made public, Dropbox forced all users to reset their passwords in 2016, which prevented anyone from using the hacked data after the reset.
Cloud customers also have a responsibility for security, and poor security practices by customers can lead to data breaches. In 2014, attackers accessed data on Dropbox again, but this was due to data breaches from other organizations and weak security practices of customers. Specifically, customers were using the same username and password on Dropbox that they used with other companies. When attackers gained access to user credentials, they methodically tried them on different services such as Dropbox. Similarly, after the 65 million Dropbox accounts were published in 2016, attackers could use these same credentials to access accounts on other cloud providers if customers used the same credentials on other sites.
Encryption is an excellent method of providing confidentiality. If you are using encryption to protect your data in the cloud, the data should be encrypted on the client end and not in the cloud. In other words, if you want to store sensitive data in the cloud, encrypt it before posting it to the cloud. If you use encryption tools made available by the cloud provider, it’s very possible that the provider holds the decryption keys and employees of the provider can access the data or may inadvertently decrypt it, making it available to other users.
Data Control and Third-party Outsourcing
Organizations that store data in the cloud are effectively outsourcing some of the security requirements. With this in mind, an organization should consider implementing some security controls to increase the control of the data.
A service level agreement (SLA) is an agreement between an organization and a vendor. Organizations use SLAs when contracting services from service providers, including cloud service providers. An SLA typically stipulates performance expectations, such as minimum uptime, and can include expectations for the availability and security of data. The SLA can mandate certain requirements such as the following:
• Data portability Data portability allows users to reuse data across interoperable applications. Cloud providers can implement different application programming interfaces (APIs) to support data portability.
• Data destruction When the data is no longer stored with the cloud provider, it’s important that it is destroyed. Chapter 11 discusses various methods of adequately destroying data, and it’s important to ensure that the cloud provider uses similar methods to eliminate any data remnants of sensitive data.
• Auditing An organization owns the data, and this ownership doesn’t change when the organization chooses to store the data with a cloud provider. Auditing processes can help ensure that employees of the cloud provider are not accessing the data inappropriately.
• Data resilience The cloud provider needs to implement appropriate security controls to ensure the resilience of the data. This includes appropriate backup and recovery processes to overcome any potential system failures.
Compliance
Organizations that must comply with laws and regulations need to be careful when using the cloud, especially for data storage. The security provided via the cloud may not be adequate to protect some data, but this doesn’t relieve the organization of its legal responsibilities. For example, the U.S. Health Insurance Portability and Accountability Act (HIPAA) of 1996 mandates the protection of health-related data. This includes any data that directly relates to patients of medical facilities and any data collected about an individual’s health. Many non–health-related organizations must comply with HIPAA because they collect information on users for insurance and health plans.
Organizations that process transactions from major credit cards need to comply with the Payment Card Industry Data Security Standard (PCI DSS). E-commerce transactions traverse the Internet, and data is often stored in cloud-based storage. Organizations that use cloud-based storage for credit card data need to ensure that the cloud-based provider meets the minimum standards defined by PCI DSS.
Some cloud providers are meticulous about complying with laws and standards, but other providers might not be so careful. Organizations need to be aware that they are ultimately responsible for protecting their data. If attackers gain access to sensitive data that an organization stores in cloud-based storage, the organization is still responsible for the data breach.
Chapter Review
Switches connect devices together in a network, and routers connect networks together within a local area network (LAN) and provide physical segmentation between systems and networks. Virtual local area networks (VLANs) increase security by logically segmenting traffic with a switch, similar to how a router physically segments traffic between networks. Physical security methods protect routers and switches. Voice over Internet Protocol (VoIP) is used to transfer multimedia and voice communications over IP networks, including the Internet. Secure Real-time Transport Protocol (SRTP) provides confidentiality, authentication, and replay protection for VoIP signals.
Proxy servers improve the speed of Internet access for users and can also filter traffic. Retrieved web pages are cached on the proxy server, and the proxy server serves these cached web pages instead of using Internet bandwidth to retrieve the web page from the Internet again. Website filtering allows a proxy to block a user’s access to specific website locations. Most proxy servers also have NAT installed to translate private and public IP addresses.
Firewalls are an important security element in a network and for individual computers. Packet-filtering firewalls can filter traffic based on IP addresses, ports, and some protocols by using the protocol ID. Stateful inspection firewalls identify active TCP and UDP sessions and can open and close firewall ports dynamically based on the needs of active connections. An application firewall includes different elements to examine specific commands used by different protocols, such as Hypertext Transfer Protocol (HTTP), File Transfer Protocol (FTP), and Simple Mail Transport Protocol (SMTP). Next-generation firewalls and unified threat management (UTM) devices add more filtering capabilities such as blocking malware, filtering spam, and URL filtering.
A DMZ is commonly created with two firewalls from separate vendors to achieve defense diversity. This is in line with an overall defense in depth strategy. Even if a vulnerability appears in one firewall, it’s unlikely a vulnerability will appear in both firewalls at the same time. Additionally, to succeed in penetrating an internal network that employs defense diversity, an attacker must have in-depth knowledge about firewalls from two vendors.
Firewalls can be network-based or host-based. A network-based firewall protects traffic going into or out of an overall network, while a host-based firewall protects traffic for an individual system. Network-based firewalls are typically hardware-based, while host-based firewalls typically run as an additional software component on a server or desktop system. Using both network-based and host-based systems is part of an overall defense in depth strategy.
Many organizations provide access to their internal network through a VPN remote access solution. A VPN provides access to the private network over a public network such as the Internet. VPNs use a tunneling protocol to encapsulate the protocols needed on the internal network. Tunneling protocols include Secure Shell (SSH), Layer 2 Forwarding (L2F), Point-to-Point Tunneling Protocol (PPTP), Layer 2 Tunneling Protocol (L2TP), Internet Protocol security (IPsec), and Transport Layer Security (TLS). When using TLS, users often only need a web browser to connect to the VPN server.
Authentication protocols used for remote access include Password Authentication Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), Microsoft CHAP (MS-CHAPv1), MS-CHAPv2, Extensible Authentication Protocol (EAP), Remote Authentication Dial-in User Service (RADIUS), Diameter, and Terminal Access Controller Access Control System+ (TACACS+). RADIUS, Diameter, and TACACS+ also provide authentication, authorization, and accounting.
Traffic shaping devices can delay certain types of traffic, such as audio and video streaming traffic, so that it doesn’t consume as much bandwidth. This gives other traffic a higher priority. WAN optimization can use traffic shaping to improve VPN connections.
Network access control (NAC) helps protect internal networks by differentiating between healthy and unhealthy systems and restricting access of unhealthy systems to quarantined networks. NAC is very useful with remote access because remote clients aren’t directly controlled by the organization and can have varying levels of security applied. NAC can also be used within the organization to ensure that unhealthy clients are isolated from healthy clients.
Virtualization refers to replacing hardware with software. Host systems include a hypervisor that creates, runs, and manages virtual machines (VMs), also known as guest systems. Virtual desktop infrastructures (VDIs) provide users with a virtual desktop that can be persistent or nonpersistent. Software-defined networking (SDN) separates the data plane and control plane, providing logical segmentation within a network. An important security step with virtualization is to keep all hosts and guests up to date with current patches.
Cloud computing includes Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS), and Infrastructure-as-a-Service (IaaS). A public cloud can be accessed by anyone. A private cloud is used by only a single organization. A hybrid cloud is a combination of any two or more clouds. Although cloud computing provides reduced costs for many users, it also includes increased risk. Data hosted in the cloud can be compromised due to errors or problems with the cloud provider. Encrypting data on the client before storing it in the cloud can help provide confidentiality of data, but encrypting data using a cloud provider’s encryption services often does not provide adequate protection.
Questions
1. Which of the following best describes the mapping of data held within a switch’s table?
A. IP address to port
B. MAC address to port
C. IP address to MAC address
D. Physical port to logical port
2. Which of the following provides physical segmentation for hosts and networks?
A. SDNs
B. VLANs
C. Routers and switches
D. Proxy servers
3. Which of the following is the best choice to logically segment traffic on a network?
A. VLAN
B. EAP
C. SSL
D. TLS
4. Which of the following can provide security for VoIP?
A. RADIUS
B. TACACS+
C. Diameter
D. SRTP
5. Administrators recently installed a proxy server and configured all clients to use it when accessing websites. How does the proxy server filter traffic?
A. URLs
B. ACLs
C. MACs
D. VLANs
6. A packet-filtering firewall can block ICMP traffic, such as ping requests. How does a packet-filtering firewall identify ICMP traffic?
A. Based on the protocol number having a value of 1
B. Based on the port having a value of 1
C. Based on the state of the ICMP packet
D. Based on the protocol number of 1701
7. Which of the following choices provides the best protection against potentially malicious FTP commands?
A. Defense diversity
B. Packet-filtering firewall
C. Stateful inspection firewall
D. Application firewall
8. How can you provide defense diversity with a DMZ?
A. Use a single firewall.
B. Use two firewalls from the same vendor.
C. Use two firewalls from different vendors.
D. Ensure that only trusted partners are allowed access.
9. It’s common to enable or install a firewall on a server to protect the server. What type of firewall is this?
A. Network-based
B. Hardware-based
C. Packet-filtering
D. Host-based
10. Your organization is planning to implement a VPN. Which of the following will provide the best security for the VPN?
A. SSL
B. PPTP
C. L2TP
D. L2F
11. Of the following choices, what is used for VPNs? (Select all that apply.)
A. L2TP
B. PPTP
C. SSLTP
D. TLS
12. What port does a TLS VPN typically use?
A. 1701
B. 1723
C. 143
D. 443
13. How can users access a TLS VPN? (Select all that apply.)
A. With a web browser
B. With a dedicated application
C. With broadband access but never DSL access
D. With an IMAP application
14. Of the following choices, what indicates the primary improvement that MS-CHAPv2 included over previous protocols?
A. Support for biometrics
B. Use of certificates
C. Mutual authentication
D. Use of a nonce
15. Which of the following identifies the correct representation of RADIUS?
A. Remote Access Dial-in User System
B. Remote Authentication Dial-in User Service
C. Roaming Access Dial-in User Service
D. Remote Authentication Dialing User System
16. What port does TACACS+ typically use?
A. 25
B. 49
C. 53
D. 443
17. What can be used to examine the health of a client prior to allowing network access and restricting access of unhealthy clients to a quarantined network?
A. RADIUS
B. TACACS+
C. NAC
D. SRTP
18. Which of the following represents the greatest risk to virtual systems?
A. Confidentiality
B. VM escape
C. Increased costs for power and cooling
D. Loss of control of data in the cloud
19. Your organization is evaluating various cloud service models. Management wants to pick a model that places most of the security and maintenance responsibility on the cloud vendor. Which of the following is the BEST choice?
A. IaaS
B. PaaS
C. SaaS
D. RADIUS
20. An organization is sharing resources with another organization using cloud-based computing. Which of the following cloud operation models does this describe?
A. Community
B. Hybrid
C. Private
D. Public
Answers
1. B. A table in a switch maps the media access control (MAC) address to the physical port. Routers map network IP addresses to the physical port with the corresponding gateway IP addresses. The Address Resolution Protocol (ARP) resolves IP addresses to MAC addresses, but this data is not held in a switch. Physical ports and logical ports are not mapped together.
2. C. Routers and switches provide physical segmentation for hosts and networks. Software-defined networks (SDNs) and virtual local area networks (VLANs) provide logical segmentation for hosts and networks. Proxy servers do not segment networks.
3. A. A virtual local area network (VLAN) segments traffic on a network using a switch. Extensible Authentication Protocol (EAP) is used for authentication, not segmentation. Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are transport encryption protocols and do not segment traffic. Note that this is an example of how the SSCP exam may just be testing your knowledge of relevant acronyms. If you know what the acronyms represent, the answer to the question becomes obvious because EAP, TLS, and SSL have nothing to do with segmenting traffic.
4. D. The Secure Real-time Transport Protocol (SRTP) provides confidentiality, authentication, and replay protection for Voice over IP (VoIP) transmissions. Remote Authentication Dial-in User Service (RADIUS), Terminal Access Controller Access Control System+ (TACACS+), and Diameter are used to provide authentication, authorization, and accounting (AAA) for remote access.
5. A. A proxy server filters traffic using URLs and can block users from accessing websites. While the question didn’t ask, a proxy server also caches web pages to improve overall performance of web traffic. None of the other answers are directly related to proxy servers. Routers and firewalls filter traffic using access control lists (ACLs). Switches can filter traffic using media access control (MAC) address filtering. A virtual local area network (VLAN) logically segments traffic and it is unrelated to a proxy server.
6. A. Packet-filtering firewalls can filter traffic based on IP addresses, ports, and protocol numbers, and a protocol number of 1 identifies Internet Control Message Protocol (ICMP) traffic. ICMP does not use port 1. A packet-filtering firewall is a stateless firewall, so it doesn’t evaluate the state of the ICMP packet. Protocol number 1701 is not used, but Layer 2 Tunneling Protocol (L2TP) uses port number 1701.
7. D. An application firewall (also called an application proxy or an application gateway firewall) can inspect commands used by individual protocols such as File Transfer Protocol (FTP) and block potentially malicious commands. Defense diversity refers to using firewalls from two different vendors in a demilitarized zone (DMZ). A packet-filtering firewall can only inspect individual packets for IP addresses, ports, and protocol IDs. A stateful inspection firewall can track the activity within TCP and UDP sessions, but can’t interpret commands.
8. C. You can provide defense diversity with a DMZ by using two firewalls from different vendors. If a vulnerability appears in one, it’s unlikely that a vulnerability will exist in the second firewall at the same time (unless the second is from the same vendor). A single firewall doesn’t provide any diversity. An extranet (not a DMZ) would allow access only to trusted partners. Note that this question could also be presented as a “Select all that apply” question by asking which of the following are used for VPNs.
9. D. A host-based firewall is installed or enabled on individual hosts, such as desktop computers or servers, and provides protection for the host. Network-based firewalls protect the network rather than individual systems. Packet filtering identifies the method used by the firewall, and both network-based and host-based firewalls can filter packets.
10. C. Layer 2 Tunneling Protocol (L2TP) is the best choice of those given. It can use Internet Protocol security (IPsec) for encryption. Secure Sockets Layer (SSL) has been deprecated and should not be used. Transport Layer Security (TLS) is the designated replacement for SSL and can be used for a VPN. Although the terms are often used interchangeably, TLS is not the same as SSL. Layer 2 Forwarding (L2F) is a legacy VPN tunneling protocol that is rarely used because it does not encrypt the traffic.
11. A, B, D. Layer 2 Tunneling Protocol (L2TP), Point-to-Point Tunneling Protocol (PPTP), and Transport Layer Security (TLS) are used for virtual private networks (VPNs). There is no such thing as SSLTP in the context of VPNs.
12. D. A Transport Layer Security (TLS) virtual private network (VPN) typically uses TCP port 443, the same port as Hypertext Transfer Protocol Secure (HTTPS). Layer 2 Tunneling Protocol (L2TP) uses port 1701. Point-to-Point Tunneling Protocol (PPTP) uses port 1723. Internet Message Access Protocol version 4 (IMAP4) uses port 143.
13. A, B. Users typically access a Transport Layer Security (TLS) virtual private network (VPN) using a web browser or a dedicated application (such as OpenVPN Connect). A TLS VPN is not dependent on a specific type of Internet connection (such as broadband or DSL). Internet Message Access Protocol (IMAP) is used with e-mail, not VPNs.
14. C. MS-CHAPv2 uses mutual authentication, where the client authenticates to the server and the server authenticates to the client. MS-CHAPv2 does not directly support biometrics. MS-CHAPv2 can be used with the Extensible Authentication Protocol (EAP) to support certificates, but it cannot do so on its own. CHAP uses a nonce (a number used once), so this isn’t an improvement.
15. B. RADIUS is an acronym for Remote Authentication Dial-in User Service. The other choices are not valid.
16. B. Terminal Access Controller Access Control System+ uses TCP port 49. Simple Mail Transport Protocol (SMTP) uses TCP port 25, Domain Name System (DNS) uses TCP port 53 and UDP port 53, and Hypertext Transfer Protocol Secure (HTTPS) uses TCP port 443.
17. C. A network access control (NAC) system can check a system’s health based on a predefined health policy and restrict the access of unhealthy clients to a quarantined network. Remote Authentication Dial-in User Service (RADIUS) and Terminal Access Controller Access Control System+ (TACACS+) are used to provide authentication, authorization, and accounting (AAA) for remote access. Secure Real-time Transport Protocol (SRTP) provides confidentiality, authentication, and replay protection for Voice over IP (VoIP) transmissions.
18. B. VM escape is a known attack against virtual systems. If the attack is successful, an attacker can access the host system and all virtual systems within the host. Loss of confidentiality (not confidentiality) is a risk that can be reduced with encryption. Virtualization reduces costs for power and cooling. Loss of control of data stored in the cloud is a risk associated with cloud computing, but organizations can use virtual systems internally to keep control of their data.
19. D. Cloud vendors have the most responsibility with the Software-as-a-Service (SaaS) model and customers have the least amount of responsibility. Cloud vendors have the least responsibility with the Infrastructure-as-a-Service (IaaS) model and customers have the least amount of responsibility. Customers and vendors typically share responsibility in a Platform-as-a-Service (PaaS) model, with the vendor typically managing a little more than the customer. Remote Authentication Dial-in User Service (RADIUS) is not a cloud service model.
20. A. A community cloud is a private cloud that is shared by two or more organizations. A hybrid cloud is a combination of any two or more clouds. A private cloud is only available to users within an organization. Public cloud–based services are provided by third-party vendors and are available to anyone.



