CHAPTER 5
Attacks
In this chapter, you will learn about
• Comparisons of various types of attackers
• Differences between white hats, black hats, and gray hats
• Emerging issues related to advanced persistent threats
• Comparing various losses from insider threats
• Basic countermeasures used to thwart attacks
• Common denial of service (DoS) and distributed DoS (DDoS) attacks
• Botnets and zombies
• Reconnaissance and fingerprinting attacks
• Software security countermeasures
• Buffer overflow attacks, cross-site scripting, and cross-site request forgery
• Various password attacks and common protections
• Phishing, spear phishing, and whaling
• Wireless attacks and countermeasures
• Social engineering tactics and countermeasures
• The importance of training as a countermeasure
Comparing Attackers
Attackers break into computers and networks with malicious intent and often for personal gain. Sometimes, they try to take down a system or put it out of service. Other times, they try to get into the system to gain information. For example, an attacker may break into a system to steal credit card data from a business’s customers. The attacker can then use the credit cards fraudulently. Alternatively, they may attempt to bring a system down as an act of revenge against an organization.
Make no mistake, though. These attackers are criminals. Just as someone who breaks into your home is a criminal, attackers who break into networks and individual systems are also criminals. They are breaking laws. Many attack individuals and networks for monetary gain without any apparent care to how the loss affects their victims.
In general, criminals must have motive, means, and opportunity to complete a crime. The motive for an attacker is often money, but can also be revenge, espionage, or other reasons. The means is often with some type of malicious code (discussed in Chapter 6), and the opportunity is available for anyone with Internet or internal access. Indeed, for a greedy criminal willing to risk jail time, there are often enough programs available on the Internet that they don’t even have to write the malicious code, but only need to locate and download it. The following sections identify the different types of attackers and some names used to identify them.
Hackers and Crackers
Two terms you’ll come across when studying IT security are hackers and crackers. The following two bullets provide traditional definitions (even though many people do not use these traditional definitions):
• Hacker Someone who is proficient with computers (often with programming skills) and uses these skills to gain and share knowledge with others. By this definition, a hacker does not break into systems with malicious intent or for personal gain.
• Cracker Someone who is proficient with computers and uses these skills to attack systems. A cracker does attack systems with malicious intent or for personal gain.
The English language has a long history of changing the use of words and their meanings, often with some people kicking and screaming along the way. For example, you probably don’t use thee and thou in your daily speech. However, there was a time when everyone used these words regularly.
Similarly, the word hacker is evolving. Currently, the media widely uses the term hacker to identify anyone launching attacks on computers or networks. Even though some IT people are clinging to the traditional definition, it has lost the traditional meaning outside of these circles.
White Hats, Black Hats, and Gray Hats
Using the traditional definitions, hackers are good and crackers are evil. However, since the media began confusing these terms, the concept of white hats, black hats, and gray hats has emerged. These designations are reminiscent of the older cowboy movies where the good guys wore white hats and the bad guys wore black hats.
White hats fall into the traditional definition of hackers and are sometimes called ethical hackers. Organizations often hire them as security consultants to perform vulnerability assessments or provide other security services.
In contrast, black hats fall into the traditional definition of a cracker. Black hats are criminals who attack systems with malicious intent or for personal gain.
Of course, good and evil don’t always have definitive lines with good on one side and evil on the other. There are gray areas. Similarly, gray hats are individuals who have exceptional computer and networking skills, but they don’t use them for personal gain or with malicious intentions. However, their activities may cross ethical boundaries.
As a comparison between the three, imagine that someone discovers a weakness or vulnerability in a system. A white hat would inform the owners of the system but not take any further action. A black hat would try to exploit the vulnerability without telling the owner. A gray hat may first try to let the owners know of the vulnerability, but then decide to publish the vulnerability if the gray hat doesn’t think the owner is acting responsibly. By publishing the vulnerability, the gray hat makes the vulnerability known to the black hats, who can then use the information to exploit it.
Advanced Persistent Threats
An advanced persistent threat (APT) refers to a highly sophisticated group of people who target their attacks. They have both the capability and the intent to carry out successful attacks and are typically sponsored by a government. Once they identify a target or goal, they persistently attack until they succeed. Many countries reportedly have teams of IT personnel regularly probing the IT systems of organizations and other government networks.
In 2013 security firm Mandiant, now a division of FireEye, released a report titled APT1: Exposing One of China’s Cyber Espionage Units (available for download by searching the Internet with the title). The report documents the activities of a Chinese group that Mandiant named “APT1” and is one of the first comprehensive reports on APTs. Mandiant is very clear in its conclusions and the report includes this statement: “The details we have analyzed during hundreds of investigations convince us that the groups conducting these activities are based primarily in China and that the Chinese Government is aware of them.” The report documents the following activities by APT1:
• Compromised at least 141 companies in 20 different industries in many different countries, including the United States, Canada, and the United Kingdom
• Maintained access in compromised systems for an average of 365 days and as long as 58 months
• Stole a large quantity of intellectual property, including 6.5 terabytes of data from a single organization
• Developed over 40 different families of malicious software (malware)
Mandiant reported that the most commonly observed method APT1 used to gain access to a network was a spear phishing attack (described later in this chapter). This type of attack establishes a foothold by infecting a single system, and then the attackers quickly infect other systems in the network. For example, they often install backdoors on internal systems, providing the attackers with remote access to the systems.
An important point to remember here is that APT1 is only one APT operating out of only one country, China. There are more. As another example, the U.S. Department of Homeland Security (DHS) and the Federal Bureau of Investigation (FBI) documented Russian hacking of networks and endpoints related to U.S. elections, as well as networks of government, political, and private sector organizations. The DHS and FBI published their findings in late December 2016 in the Joint Analysis Report JAR-16-20296A, “GRIZZLY STEPPE – Russian Malicious Cyber Activity” (available for download by searching the Internet with the JAR number or the nickname GRIZZLY STEPPE).
The report identified two APTs operating out of Russia as APT 28 (nicknamed Fancy Bear) and APT 29 (nicknamed Cozy Bear) and documented how APT 29 infiltrated at least one political organization in the summer of 2015, and how APT 28 infiltrated a political organization in spring 2016. While the details of these infiltrations are quite complex, the initial infiltration apparently started with highly targeted spear phishing campaigns, similar to how APT1 gained a foothold in many organizations.
Similarly, other countries very likely have their own APTs. APTs don’t attempt to get all the information immediately. Instead, they are patient and willing to get a little bit of information at a time. However, they are also persistent. When one attack fails, they don’t give up. Instead, they look for other ways to attack and keep pursuing the target until they achieve some success.
After many successful attacks against computers and networks in the United States, the U.S. government created the United States Cyber Command (USCYBERCOM), which became operational in 2010. Its mission statement is as follows:
USCYBERCOM plans, coordinates, integrates, synchronizes, and conducts activities to: direct the operations and defense of specified Department of Defense information networks and; prepare to, and when directed, conduct full-spectrum military cyberspace operations in order to enable actions in all domains, ensure US/Allied freedom of action in cyberspace and deny the same to our adversaries.
Many other countries have created similar organizations to combat the threats of cyberwarfare.
Insider Threats
An insider is someone who works within an organization, such as an employee, consultant, or vendor, who has authorized access to the organization’s assets. Insiders have the means and opportunity to cause a significant amount of damage and can cause the loss of confidentiality, integrity, and availability of an organization’s resources.
Insiders can make mistakes or ignore security practices resulting losses. They can engage in malicious activity as revenge. And they can engage in data theft such as stealing trade secrets, customer information, or other sensitive information from the organization, which they then can attempt to sell for personal gain.
Accidental Losses from Insider Threats
Not all insider threats are deliberate theft or destruction of data. Instead, they are typically users not following security protocols or practices, resulting in losses. As an example, imagine an organization regularly tells employees not to click on links included in e-mail from unknown sources. A user that clicks on one of these links is an insider threat.
Consider the threats posed by APT 28 and APT 29. These APTs launched sophisticated spear phishing attacks. At least one user in each instance (yes, it only takes one user) responded inappropriately to these attacks. The APT 29 spear phishing attack included a link that activated malicious software (malware) if the user clicked it. The APT 28 spear phishing attack tricked users into changing their passwords through a fake website hosted by the APT 28 group. This allowed the APT 28 group to use these credentials to log on to the users’ accounts.
As another example, a U.S. military data-mining program scoured the Internet looking at social media websites and other sites. The data was openly collected as part of the government’s Outpost program and analyzed for different purposes. This data was apparently backed up in Amazon Web Services (AWS) Simple Storage Service (S3), which is a cloud-based storage platform. However, it wasn’t protected with either encryption or permissions. A security analyst did a routine scan of Amazon-hosted data silos in late 2017, and found dozens of terabytes of data hosted there. While this data has since been protected, it was openly available for anyone to locate and download for some time.
Some other examples include the following:
• Responding to phishing attempts Phishing is explained in more depth later in this chapter, but in short, it’s an e-mail that encourages the user to respond with personal information or to click a link. The user can give up valuable company information or inadvertently install malicious software on their system. This provides a method for an outside attacker to attack the organization.
• Forwarding malicious software (malware) or bringing malware from home An uneducated user can forward viruses or other forms of malware via e-mail or bring it on a USB drive from a home computer. The malware could cause damage to internal systems or use other methods to gather information for attacks against the organization.
• Unauthorized data access If adequate access controls aren’t in place, a user may be able to access data. The user may then accidentally modify or delete it, or even disclose the contents of the data to someone else without realizing its true value. Something as simple as an unauthorized employee gaining access to personal records of other employees can cause a great deal of havoc to an organization.
• Losing hardware Many organizations issue hardware such as laptops or USB drives to users. When users don’t recognize the value of the hardware and the data it holds, they may not provide adequate protection, resulting in its loss or theft. As an example, many users have left laptops in conference rooms during a lunch break, only to discover them missing after lunch.
Revenge Attacks from Insider Threats
Some insiders are out for revenge. For example, Rajendrasinh Makwana was terminated from a contractor job at Fannie Mae in 2008. However, he retained access to the systems for at least a short period afterward. He later embedded a time bomb script in the Fannie Mae system. It was set to run on January 31, 2009, and would have deleted passwords on about 4,000 servers, erased all the data and backup data for the servers, and then powered them down. He also programmed the script to disable the ability to turn the servers back on remotely. Had the script run, the result would have been catastrophic.
Luckily, another engineer discovered the damaging script before it ran. Interestingly, Makwana’s employer terminated him for allegedly making unauthorized changes to other systems. However, the employer didn’t revoke his access right away, which gave him enough time to install the malicious script. A jury convicted Makwana and he was ultimately sentenced to over three years in prison.
Some organizations are using sophisticated monitoring systems to detect and prevent insider threats before they can successfully attack and cause damage. For example, in 2009 the Transportation Security Administration’s (TSA) Colorado Springs Operations Center internal surveillance system identified the actions of Douglas Duchak as he was planting malware in a critical system about a week after he was terminated with a two-week notice. He received a two-year prison sentence.
Data Theft from Insider Threats
Data theft by insiders is also a concern. Insiders sometimes steal data with the hope of selling it, or using it in a new job with a rival company. In some cases, employees are just snooping, looking at files and folders to see what they can see. While these events are still occurring, they aren’t reported as often, but instead handled within the organization. Effective access controls (including strong authentication and authorization mechanisms) combined with strong auditing techniques help to prevent successful attacks from insiders.
Script Kiddies
A script kiddie is a relatively inexperienced attacker who can run a script or application to launch an attack. The script kiddie rarely has the knowledge to program the script or application and often doesn’t understand the details of what the attack is doing. You can think of a script kiddie as a bored teenager who downloaded some hacking tools and used them to launch attacks.
It’s worth stressing that although script kiddies exist, many attackers today are highly proficient at programming techniques. They have detailed knowledge of different attack methods and are constantly modifying existing attacks to prevent detection.
Exploring Attack Types and Countermeasures
There are numerous attack types and countless variations. As attackers have launched new types of attacks, IT security professionals have identified new methods of protection. When one attack method no longer works, attackers develop others. It’s a constant battle between the attackers and security professionals. As long as attackers are able to achieve their objectives through attacks, expect them to continue.
This section outlines many of the common types of attacks and some countermeasures. This is by no means a complete list, but it does provide an overview.
Basic Countermeasures
Countermeasures are security controls that reduce risks. They typically reduce vulnerabilities or reduce the impact of a threat. Chapter 9 covers countermeasures and controls in more depth. The following sections introduce some basic countermeasures that help prevent many attacks.
Patching Systems
Many attacks are possible because of vulnerabilities discovered in an operating system. However, once vendors learn about these vulnerabilities, they develop, test, and release patches and updates to plug the security holes. As long as administrators keep systems up to date with current patches and updates, the systems are no longer vulnerable to that specific attack. However, unpatched systems remain vulnerable to the attacks.
This seems obvious to most security professionals. However, many attacks succeed because organizations don’t follow basic security practices such as keeping systems up to date with current patches. As an example, the 2017 Equifax data breach exposed sensitive data for as many as 143 million people. Attackers exploited a vulnerability in an Apache web application. However, Apache Software Foundation had released a patch to remove the vulnerability over two months prior to the data breach. If Equifax had applied the patch, it would have prevented the data breach.
System Hardening
Administrators harden systems by increasing the security provided with the default configuration. Hardening includes removing or disabling unneeded protocols and services, ensuring the system is deployed with all current patches and updates, and enabling software firewalls.
System Isolation
Another basic countermeasure is system isolation or segmentation. Chapter 4 covers the use of routers to provide physical segmentation for network hosts and using virtual local area networks (VLANs) to provide logical segmentation of network hosts. It’s also possible to use virtualization technologies to isolate systems.
An extreme example of system isolation is to place systems in isolated networks without any Internet access. This is most commonly done with industrial control systems (ICSs) or classified networks.
Increasing User Awareness
User awareness programs help users understand risks, recognize risky behaviors, and understand their responsibilities related to security. A goal is to reaffirm safe computing practices and encourage users to change their behavior if they are engaging in unsafe computing practices.
Security professionals use a variety of methods to increase user awareness. This includes routine training, annual updates, periodic e-mails, and more. The value of increasing user awareness by any methods possible cannot be overstated.
One method some administrators use is sending out e-mails with catchy subject lines and telling about recent compromises caused by users. As an example, imagine a user in a different organization clicked a link that took the user to a malicious site, downloaded malware onto the user’s system, and then infected other computers in the network. Sending out an e-mail to personnel with the subject line “Are you the weakest link?” can grab their attention. The e-mail can give short details about the incident, with a link to an article giving more details.
Intrusion Detection and Protection Systems
Network-based intrusion detection systems (NIDSs) can often detect attacks in progress and send alerts to administrators. Some NIDSs can take action to change the environment and block the attack, but only after it has started. A network-based intrusion prevention system (NIPS) is similar to a NIDS with one distinct difference—a NIPS is placed inline with the traffic, allowing the NIPS to inspect all traffic and identify and block potential attacks. The lines between an IDS and an IPS are sometimes blurred, so you may see them referred to as an IDPS, including in this chapter.
IDPSs are relatively common in networks today. In some networks, an IDPS may be a dedicated device. In other networks, an IDPS may be part of an appliance such as a unified threat management (UTM) device that combines multiple technologies together into a single appliance. Many next-generation firewalls also include IDPS capabilities. Chapter 8 covers IDSs and IPSs in more depth.
Spoofing
Spoofing refers to impersonating or masquerading as someone or something else, and many attacks use spoofing techniques. Chapter 3 presented the concept of spoofing in the context of IP addresses and media access control (MAC) addresses. Attackers can change the source IP address or source MAC address so that traffic appears to be coming from a different computer. Similarly, attackers can change the From field in an e-mail to make it appear as though the e-mail is coming from someone else.
Data Theft
Data theft refers to any attack that allows the attacker to exfiltrate data from an internal network. Attackers have stolen a wide assortment of data from just about every business and private sector. This includes data from banking and financial institutions, credit reporting agencies, small and large businesses, educational institutions, government and military organizations, and healthcare organizations.
Many of these attacks expose user personally identifiable information (PII). The Identity Theft Resource Center (ITRC), a U.S. nonprofit organization, publishes annual reports on data breaches in the United States. In 2017, the ITRC reported a record high of 1,579 data breaches exposing more than 178 million records. Over 50 percent of these breaches exposed user’s Social Security numbers (SSNs) and 19 percent of the breaches exposed users’ credit card or debit card data.
Almost 60 percent of these reported data breaches were the direct result of attacks, such as phishing, ransomware, and other malware attacks. Note that many of these successful attacks were caused by insiders not following security-related best practices, such as not opening attachments in e-mails received from unknown entities, or clicking links in e-mails. Other breaches occurred from unauthorized access, insider theft, accidental exposure, and physical theft.
APTs are responsible for a significant amount of data theft worldwide, including PII data, but they have stolen much more. As an example, APT1 reportedly stole 6.5 terabytes of compressed data containing intellectual property from a single organization. FireEye, in its report titled “APT28: A Window into Russia’s Cyber Espionage Operations?” concluded that APT28 is engaged in espionage against political and military targets in Eastern European governments and militaries, and European security organizations.
FireEye has also tracked an APT they refer to as APT33. They identified malware used by APT33 tied to an Iranian persona and reported “We assess APT33 works at the behest of the Iranian government.” APT33 targets many organizations in the aviation sector, aerospace sector, and energy sector. While it’s unclear what data APT33 may have obtained, FireEye suspects they may be targeting these sectors for two primary reasons:
• Military capabilities FireEye indicates APT33 is collecting data to assess military aviation capabilities of Iran’s regional rivals, such as Saudi Arabia. Additionally, they can use collected data to enhance Iran’s domestic aviation capabilities.
• Petrochemical production Iran has expressed a desire to grow its petrochemical industry. By collecting up-to-date data on competitors in the region, APT33 can help Iran expand its production and improve its competitiveness in the region.
DoS
A denial of service (DoS) attack attempts to prevent a system from answering legitimate requests from users. The attack often attempts to overwhelm the system by consuming system resources. While the attacked system responds to the attack, it doesn’t have enough resources to respond to regular requests. The goal is to deprive the organization or its customers from the use of a service.
As an example, a common DoS attack is a SYN flood attack that initiates the TCP handshake process but doesn’t complete it. Chapter 3 describes the three-way handshake used by TCP. Recall that a normal three-way handshake includes the following three packets:
1. A TCP client sends a packet with the SYN flag set to a system such as a server.
2. The server responds with a packet with the SYN and ACK flags set.
3. The client then completes the handshake process by sending back a packet with the ACK flag set.
In a SYN flood attack, the attacker withholds the third packet, leaving the half-open session on the server. For example, consider Figure 5-1, which shows the process of a SYN flood attack. The first two packets are sent just like a regular three-way handshake, but the third packet is not sent. Instead, the attacker then sends out another SYN packet.

Figure 5-1 SYN flood attack
This is similar to a practical joker extending his hand to shake yours, you extending your hand in response, and the joker pulling away his hand at the last second. He sticks his hand out again, you extend your hand again, and he pulls his hand away again. You probably won’t fall for this repeatedly. However, TCP will keep responding to SYN packets with SYN/ACK packets and continue waiting for the third packet.
If this happens once or twice, it’s no big deal. However, an attacker can initiate hundreds of half-open sessions in a short period. If the attack isn’t detected, the server can keep each of these sessions open as it waits for hundreds of ACK packets. Each one of these sessions consumes resources, such as memory, processing power, and network bandwidth. The attack can slow down the server, and in extreme cases, it can result in resource exhaustion and actually crash the server.
The following are some other well-known DoS attacks:
• Ping of death An Internet Control Message Protocol (ICMP) ping packet is normally 32 bytes of data, although different operating systems may vary the size. A ping of death attack changes the size of the ping packet to more than 64KB. These large ping packets have crashed some systems, although most systems recognize the attack today and can avoid it.
• LAND A local area network denial (LAND) attack tricks a system into sending out packets to itself in an endless loop. In other words, the source and destination addresses are set to the attacked system. A LAND attack can shut down a system.
DDoS
A distributed denial of service (DDoS) attack is similar to a DoS attack except that it comes from multiple attackers at the same time. For example, an attacker may launch a TCP flood attack against a single system from hundreds or even thousands of systems. A key to the success of DDoS attacks is for the attacker to take control of multiple systems and then use these systems to launch the attacks. Attackers often use botnets (described in the next section) to launch DDoS attacks.
Botnets and Zombies
A botnet is a group of computers (often called zombies) controlled by an attacker. The term botnet is a combination of robot and network. The attacker (sometimes called a bot herder) manages a command and control center and directs the computers in the botnet to do the bidding of the attacker.
Computer users are usually unaware that their computer has become a zombie. Instead, malware infects computers without the user’s knowledge. This allows attackers to control the computer from remote locations.
One way that a system is infected and joined to a botnet is through a drive-by download, as shown in Figure 5-2. When a user visits an infected or malicious website, the website downloads the malware and attempts to install it on the user’s system. Users sometimes unknowingly visit these sites during Internet surfing sessions. Other times, users click links included within malicious e-mails. As an example, the GameOver Zeus malware used drive-by downloads to join computers to botnets. Additionally, the attackers used malicious e-mails to encourage users to visit the malicious websites.
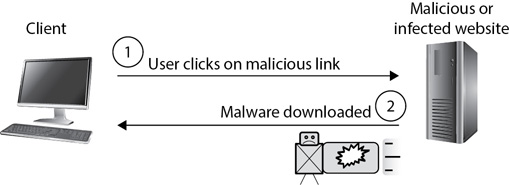
Figure 5-2 Single system infected in drive-by download
While a drive-by download is one way that computer systems are joined to botnets, it isn’t the only way. Multiple types of malware can include code to join computers to botnets. Chapter 6 covers malware in more depth.
Figure 5-3 shows a botnet with multiple zombies in it. These zombies regularly check in with the attacker’s command and control center, which is hosted on one or more servers controlled by the bot herder. Smaller botnets may have a single server hosting the command and control software. Larger botnets may have dozens of servers located around the world.
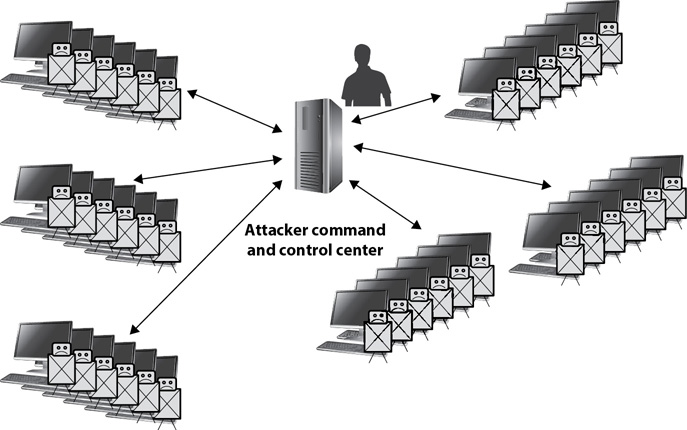
Figure 5-3 Zombies regularly check in with the command and control center.
The commands issued to the zombies in the botnet vary. Bot herders can direct zombies to bombard a server with a DDoS attack, as shown in Figure 5-4. Attackers can also direct zombies to take other malicious actions, such as send spam and phishing e-mails, spread malware, or launch other types of attacks.
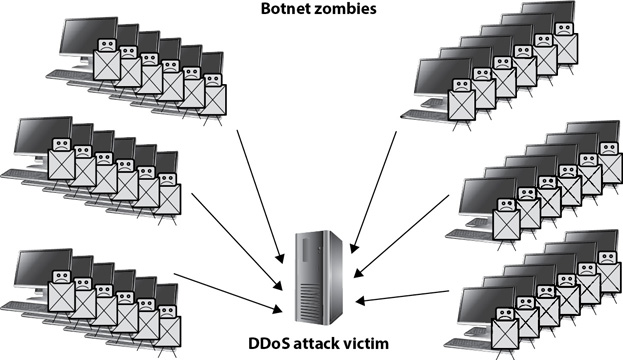
Figure 5-4 Zombies can launch DDoS attacks.
Criminals often rent out their botnets to other criminals, and if the botnet is large, the owners can generate a significant amount of money from these rentals. Many botnets control tens of thousands of computers, and some control more than a million. At its height, the Rustok botnet had more than a million zombies and sent out billions (yes, billions with a b) of spam e-mails daily. The Rustok botnet was taken down in March 2011, and IT watchers reported that spam levels immediately plummeted.
Many current botnets are smaller, in part to evade detection. However, some large botnets still appear every now and then. In 2016, attackers gained control of about 100,000 Internet of Things (IoT) devices such as digital cameras, webcams, and digital video recorders. Attackers used Mirai malware to take control of the devices, and the botnet was commonly referred to as the Mirai botnet. This botnet then attacked Domain Name System (DNS) servers on the Internet, effectively crippling many popular websites such as Reddit, Tumblr, Amazon, Twitter, and more.
Sniffing Attack
A protocol analyzer (also called a sniffer or packet sniffer) captures packets transmitted over a network. After capturing packets, you can save them in a file (commonly called a capture) and browse them at your leisure. Automated tools can also scan captures to look for trends, possible attacks, and other items of interest. IT professionals use sniffers to troubleshoot and learn details about a network. Attackers use sniffers to capture data and exploit it for personal gain.
A popular sniffer is Wireshark. It’s available as a free download and runs on most platforms, such as Windows, UNIX, and Linux.
If data is sent over the network in cleartext, an attacker can easily read it in a sniffer. However, if the data is encrypted, it can’t be read. For example, Chapter 3 mentioned the risks of unencrypted protocols such as File Transfer Protocol (FTP) and Trivial File Transfer Protocol (TFTP). Both FTP and TFTP send data over the network in cleartext by default. An attacker can capture these transmissions and read credential information, such as usernames and passwords, and the actual data. In contrast, FTP Secure (FTPS) uses Secure Shell (SSH) to encrypt the transmissions, preventing attackers from reading data.
Figure 5-5 shows a screenshot of Wireshark with a capture. During this capture, I connected to a network drive and opened a file named passwords.txt. After stopping the capture, I browsed through it to locate packets that held data. In the figure, you can see arrow 1 pointing to packet 1470, which is an SMB Read AndX Response command. The center pane holds the details on this packet. Arrow 2 shows where the packet includes the name of the file (passwords.txt). The bottom pane shows the data in both a hexadecimal and text format, and arrow 3 shows the username and password in cleartext (Darril Gibson, IPa$$edSSCP).
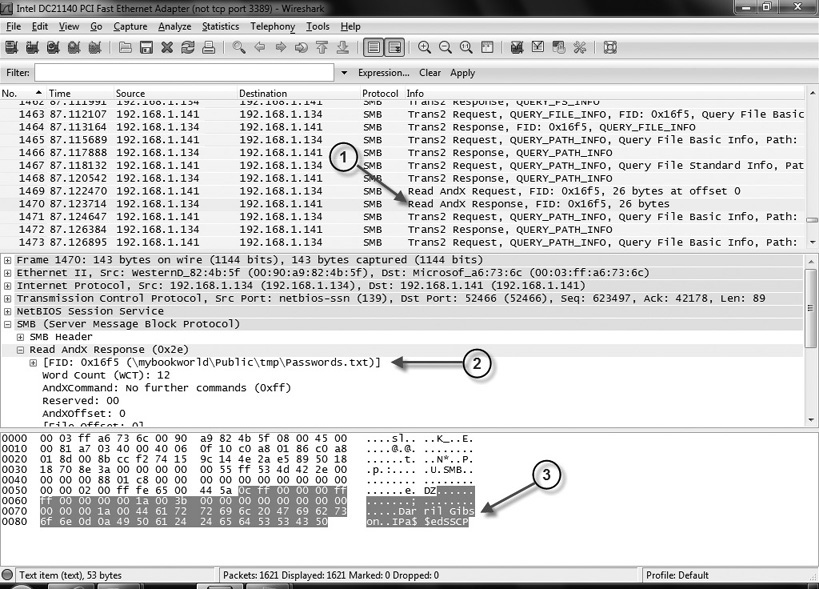
Figure 5-5 Viewing text data in Wireshark
Sniffers can work in either promiscuous mode or nonpromiscuous mode. In nonpromiscuous mode, the sniffer will capture only data sent directly to or from the computer’s IP address. It will not capture any packets that do not have the computer’s IP address as the source or destination address. In contrast, when the sniffer works in promiscuous mode, it will capture all data that reaches the computer regardless of the IP address. Technically, the sniffer configures the network interface card (NIC) to work in promiscuous mode for the application.
One of the ways an organization reduces vulnerabilities from sniffer attacks is to use switches instead of hubs. For example, consider Figure 5-6, which shows both a hub and a switch in action. In the figure, PC1 and PC3 are sending data to, and receiving data from, each other. The hub sends the data to all ports, so an attacker with a sniffer running on PC2 is able to capture the transmission with a sniffer (as long as the sniffer is running in promiscuous mode).
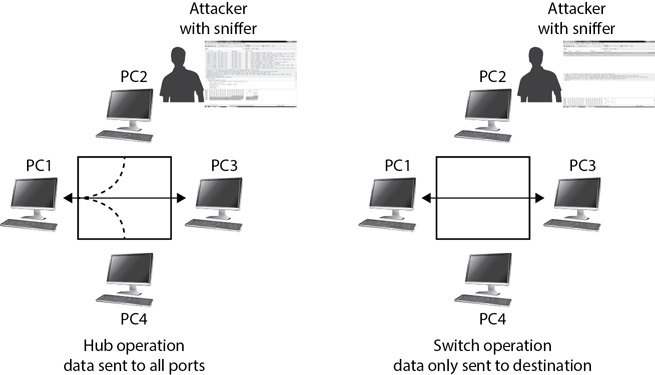
Figure 5-6 Comparing data sent via a hub and via a switch
However, when using a switch, the same data transmissions reach only PC1 and PC3. The attacker running a sniffer from PC2 is not able to capture the data because the traffic doesn’t ever reach the switch port for PC2.
It’s worthwhile noting that administrators can configure a mirrored port on most routers and switches. The device sends a copy of all data sent through the device to the mirrored port. If attackers can connect directly to the mirrored port, they will be able to capture all the traffic going through the device. This underscores the importance of physical security. Locating network devices in secure server rooms or locked wiring closets provides a necessary layer of security.
Reconnaissance and Fingerprinting Attacks
Many attackers gain a foothold into a network by first infecting a single system, often after a user responds inappropriately to a phishing e-mail. The attacker then uses various reconnaissance methods to identify other computers on the network by identifying active IP addresses. Next, the attacker attempts to learn details about each active IP address using fingerprinting methods such as port and service scans, and/or OS detection techniques.
Ping Sweep and Other IP Identification Methods
Attackers often use a ping sweep (sometimes called a ping scan) as part of an reconnaissance attack to identify active IP addresses. A ping sweep uses ICMP to identify what systems are operational within a range of IP addresses. This is similar to sending a ping to a system and waiting for a response. However, instead of sending a single ping to a single system, the ping sweep sends pings to all the IP addresses within a range, such as between 192.168.1.1 and 192.168.1.254. Tools can typically be configured with delays between each ping sent out in an effort to evade detection. However, many IDPSs can still detect this activity.
A ping sweep can be used as part of an overall attack strategy. The ping sweep performs reconnaissance to identify the system. Other tools (such as port scanners or vulnerability scanners) identify details on individual systems in a fingerprinting attack.
An Address Resolution Protocol (ARP) scan uses ARP instead of ICMP to identify active systems in a network. It sends out an ARP request with an IP address, and if a system on the network has the IP address, it responds with its MAC address. ARP uses broadcast and routers do not pass broadcasts, so an ARP scan is only effective at locating computers within a single network, or subnet.
It’s also possible to use a SYN stealth scan to identify active IP addresses. If you look back at Figure 5-1 you can see the three packets sent in a typical TCP handshake. In a SYN stealth scan, the attacker sends the first packet (SYN) to an IP address. If a computer is actively using the IP address, it responds with a SYN/ACK packet. Instead of sending an ACK packet to establish the TCP session, the attacker then sends an RST packet to reset the connection. However, the attacker now knows a system is actively using the IP address.
Port and Service Scans
The port scan attempts to detect what ports are open on a system. Attackers often use it as part of an overall fingerprinting attack to gather information on a system, such as what ports are open. Chapter 3 covered well-known ports. As a reminder, well-known ports are in the range of 0 to 1023 and are commonly used by specific protocols. For example, SSH uses port 22, Simple Mail Transfer Protocol (SMTP) uses port 25, and Hypertext Transfer Protocol (HTTP) uses port 80.
If a port scan determines that port 80 is open, it indicates that HTTP is enabled on a system. Web servers use HTTP, so this also indicates the system is probably a web server. It could be an Apache web server running on a Linux system, an Internet Information Services (IIS) web server running on a Microsoft system, or something else. Attackers often use additional steps to identify the server’s operating system and the web server software.
Port scanning tools can run sequentially through ports. You can detect them by checking firewall logs or by using automated IDPSs. For example, if the same source IP address checks for responses on ports 20, then 21, then 22, and so on, it’s a clear indication of a port scan. More sophisticated port scanners can randomize the order of the port numbers that they check, such as 22, then 80, then 25, and so on. However, most IDPSs are aware of both tactics and can detect both sequential and randomized port scans.
Service scans go a step further to validate that a service is running. For example, if port 80 is open, it indicates that HTTP is running. The service scan then uses HTTP commands such as Get to retrieve an HTML document including header information.
Operating System Detection
Operating system (OS) detection techniques attempt to discover details about a system beyond open ports and active services. They typically analyze packets sent by the system to identify the OS and its version.
TCP/IP stack fingerprinting collects packets sent across a network and analyzes them to determine details about systems. RFCs don’t require any specific values for many TCP and IP fields. Because of this, different OSs use different values. Two TCP/IP fields that can identify many systems are the initial Time To Live (TTL) field and the TCP window size field.
Some tools perform active fingerprinting by querying systems with probes. They then analyze the response to gain additional information. Many IDPSs can detect active fingerprinting techniques, and a variety of methods can thwart these attempts.
Salami Attack
In a salami attack, an attacker performs a large number of minor actions that likely won’t be noticed or reported but collectively can add up to big gains. Its name comes from a metaphor of slicing small slivers of salami sausage to create enough pieces to create a sandwich.
In one of the classic examples of a salami attack, an attacker shaves a penny off each of many financial transactions. Any individual who loses a penny is unlikely to notice or even complain about the loss. However, when attackers use the same tactic thousands or millions of times, they can pilfer a substantial amount of money. For example, programmers in the classic movie Office Space realized that they could write a program to shave fractions of pennies from transactions where they work. Unfortunately, they misplaced a decimal and ended up taking too much money, resulting in some comical results.
Salami attacks can also be used to gain information from databases. Instead of getting the entire database at a time, attackers can get small pieces of data and then combine them to reproduce the full picture. Espionage works this way when spies try to learn as much as they can using multiple sources. Similarly, social engineers (described later in this chapter) often try to gather small pieces of data from multiple sources. Both spies and social engineers can later compile all the information to gain actionable knowledge about their targets.
Man-in-the-Middle
Man-in-the-middle (MITM) attacks perform electronic eavesdropping by placing a system between two other parties. This third system captures the data sent between the two computers. For example, if one computer is exchanging data with a server, an MITM attack can capture all the data between the two systems. The attack is transparent to the two systems.
An active MITM attack can be quite sophisticated, and Figure 5-7 shows an example. A user is connecting to a web server over the Internet and the user’s web browser indicates that a Transport Layer Security (TLS) session is established with Hypertext Transfer Protocol Secure (HTTPS). However, instead of having a secure TLS session with the web browser, the user has a secure TLS session with the MITM system.

Figure 5-7 MITM attack using TLS
The MITM system establishes two TLS sessions. One session is secure between the user and the MITM system and the other session is secure between the MITM system and the web server. The MITM system is able to decrypt all of the data, allowing attackers to read it.
It’s difficult to set up such an attack without control of either the user’s internal network or the web server’s internal network. Some organizations have set up an MITM system internally to track activity of users within the organization. For example, if the MITM system is established internally, it allows personnel to track all of the internal users’ online activity. Before doing this, an organization would typically let employees know via an acceptable use policy that their online activity is tracked and that certain activity is prohibited.
If the web server is hosted at a disreputable hosting company, the hosting company may be able to implement an MITM system there. It can then capture user data such as credit card data and then run up charges on these credit cards.
Replay
A replay attack starts as an eavesdropping attack where the attacker uses a sniffer to capture the data. However, the replay attack goes a step further and uses the information to impersonate one of the systems in the session.
For example, two computers may establish a session and exchange authentication information. An attacker will capture this information and use it later to impersonate one of the systems.
Several methods help prevent the success of this type of attack. For example, Kerberos (a network authentication protocol) uses time stamps and requires systems to be within five minutes of each other. These time stamps restrict the time that an attacker can replay captured data. Additionally, many systems use unique session tokens within secure sessions to thwart replay attacks. For example, Challenge-Handshake Authentication Protocol (CHAP) uses a nonce (a number used once) to create session tokens. Because CHAP doesn’t reuse these session tokens, attackers cannot use them in a replay attack.
Session Hijacking
Session hijacking is another sophisticated attack where an attacker captures information from an ongoing TCP/IP session and attempts to take over the session by impersonating one of the parties. Such an attack is possible with HTTP sessions where cookies are used. If successful, the attacker may gain access to either of the systems in the original session or launch a DoS attack on one of the systems to take it out of service.
The session hijacking attack often starts with a sniffing attack where the attacker gathers information about an ongoing session. The gathered information includes cookies passed back and forth between the web client and the web server.
As an example, Firesheep is a Firefox extension that allows attackers to listen for and exploit session cookies transmitted over a wireless network. An attacker can sit in a public wireless hotspot, capture session cookies, and use them to take over sessions such as Facebook and Twitter sessions. Faceniff is a similar application that runs on Android systems.
DNS Cache Poisoning
Chapter 3 discusses the operation of Domain Name System (DNS) to resolve host names to IP addresses. DNS cache poisoning (sometimes called simply DNS poisoning) is an attack that attempts to redirect traffic away from legitimate servers.
As an example, when you type in google.com as the URL in your browser, your system queries a DNS server for the IP address. When it receives the reply, it stores the result (216.58.193.206) in the DNS cache. You can use the command ipconfig/displaydns to see the contents of the DNS cache on Windows systems. The Time To Live field indicates how long (in seconds) a result remains in cache. A successful DNS cache poisoning attack changes the correct cached IP address associated with a host to the IP address of another system. For example, it can change the IP address to 204.79.197.200, which is an IP address for bing.com. Now, when a user types in google.com, they will be taken to bing.com instead. Redirecting a user to bing.com instead of google.com might be fun as a practical joke, but it isn’t really an attack.
DNS servers also have a cache. When one DNS server queries another DNS server to resolve a host name to an IP address, the DNS server receiving the response stores it in its cache. If the cache on the DNS server has been poisoned, the DNS server will send the incorrect IP address to any system that queries it.
Attackers sometimes try to redirect traffic to malicious sites. For example, they might redirect a user to a site that attempts a drive-by download or tricks a user into downloading and installing malware.
China uses traffic redirection as one of many techniques that block access to certain websites outside of China. For example, DNS servers within China redirect traffic of some popular U.S. websites to Chinese versions of the same sites. Some examples are: twitter.com is redirected to weibo.com and facebook.com is redirected to wechat.com. In 2010, an Internet service provider (ISP) outside of China incorrectly configured DNS servers to receive information from Chinese DNS servers. This essentially caused a massive DNS cache poisoning attack redirecting traffic to Chinese servers.
One of the best protections against DNS cache poisoning attacks (beyond configuring them correctly) is the use of Domain Name System Security Extensions (DNSSEC). DNSSEC is a suite of extensions that validates DNS responses with a Resource Record Signature (RRSIG). When fully implemented, each DNS response includes the RRSIG, which is similar to a digital signature. The RRSIG provides assurances that the DNS record is valid and has not been poisoned.
Smurf and Fraggle Attacks
A smurf attack broadcasts ICMP ping packets to multiple computers on a network but spoofs the source address using the IP address of the attacked system. An ICMP packet normally includes the IP address of the sender in the source IP address field. However, by replacing the IP address with the victim’s IP address, the ICMP packet appears to come from the victim’s computer. By broadcasting the ping, all systems on the subnet receive the echo and respond by flooding the attacked system with echo replies.
Attackers often use an amplifying network in a smurf attack by sending a directed broadcast ping to the amplifying network. A directed broadcast ping goes through a router to the target network and then broadcasts the ping to all the computers on the target network. Each computer on this network then sends pings to the victim’s computer. However, most routers block directed broadcasts, protecting a network from being used as an amplifying network.
A fraggle attack is similar to the smurf attack, but instead of using ICMP packets, it uses User Datagram Protocol (UDP) packets for the attack. It sends packets to UDP port 7 or UDP port 19. Port 7 is the echo port, which works similarly to a ping. Port 19 is the Character Generator Protocol (chargen) port. When chargen is enabled on a system, it will respond with a random character each time it receives any traffic on the port. However, chargen is rarely enabled on current systems.
Software Security as a Countermeasure
Many organizations host their own websites, and developers can take steps to protect these websites from various attacks. Successful attacks can infect the websites and infect user systems that visit the websites. Software security includes steps that developers within an organization can take to ensure that their software applications (including web applications) are secure.
Years ago, it wasn’t common for an organization to develop its own software applications. However, now it is common for an organization to create simple web applications on its own instead of hiring an outsider. Many organizations let internal employees create them, and this practice is often successful. However, if the website developer isn’t aware of basic security measures, including input validation, application reviews, code signing, and sandboxing, security problems can arise.
Using Input Validation as a Countermeasure
Input validation checks data before using it within the application. The goal is to verify that the data is valid and ensure that an application does not use invalid data. This prevents potential problems within the application and helps prevent attacks.
As an example of input validation, imagine an application needs a user to enter a number between 1 and 100 that the application will use in a mathematical equation. Input validation does a check to verify that the user actually entered a number in this range. If the user enters 0, a number over 100, or any non-numerical characters, it fails the input validation check, and the application won’t use the entered data.
Applications should use input validation for any type of data. If users need to enter their first name, the application can check to ensure that the entered name is less than 35 characters and includes only valid characters for a name. Similarly, if users need to enter a five-digit ZIP code, input validation verifies that the input includes five digits.
Input validation doesn’t verify the accuracy of the data. Instead, it only determines if it is valid. As an example, if you can enter 23456 as your ZIP code, a web application using input validation will accept it because it is a valid ZIP code. However, the application doesn’t know if this is an accurate ZIP code for you. More advanced accuracy checks can verify that the ZIP code you entered matches the city and state you entered, but these are accuracy checks instead of validity checks.
If you’ve ever filled out a form on a web page, you’ve probably seen input validation in use. After you enter the data and submit it to the website, the web page checks your input. If something is wrong, the site redisplays the web page, often using something like a red asterisk (*) to show what items need to be addressed.
Input validation is valuable in preventing different types of attacks, such as buffer overflow, SQL injection, and cross-site scripting attacks. These attacks are discussed later in this chapter.
Client Side vs. Server Side Input Validation
Input validation can be done on the client side and/or on the server side. With client-side input validation, the web page includes embedded code that validates the user input. If the user enters incorrect data, the code within the web page validates it and modifies the display to let the user know the data isn’t valid.
Client-side validation saves a round trip to the server over the Internet. In other words, the web page doesn’t send the input over the Internet to the web server, requiring the web server to send a page back to the user to correct the input. However, a malicious attacker can modify the web page on the client side and bypass the client-side validation. Because of this, client-side validation by itself doesn’t provide reliable protection.
Server-side input validation validates the data when the server receives it. If the input is invalid, the server rebuilds the web page and sends it back to the client, typically with a message indicating what the user needs to correct. Web pages often use both client-side input validation and server-side input validation. The client-side input validation saves bandwidth and processing power on the server. The server-side input validation provides a final security check before using the inputted data.
Application Review as a Countermeasure
An application review attempts to discover vulnerabilities with an application before an organization releases it. One of the basic elements of a review is testing. A tester verifies that the application works as it should, and tests for any bugs or vulnerabilities.
Application reviews also include a review of the source code. This is a line-by-line examination of the source code of an application. The primary goal is to discover potential issues that developers can correct before the organization releases the application. Some organizations also use application reviews as a peer review to help developers improve their skills.
Code Signing as a Countermeasure
Code signing, or digitally signing software, provides security for the organization hosting a website by associating a certificate with the software. It also provides users with assurances of who wrote the software and that the software has not lost integrity. If malware infects digitally signed software, it will fail a check and alert the user. In some cases, the software is within a web page and the browser will raise an alert. In other cases, the operating systems will detect the failed check during the installation and raise the alert. Note that code signing verifies both the identity of the author and file integrity.
Vendors that release software purchase a certificate from a public certificate authority (CA). This certificate is associated with the software file and the vendor that released it. It includes the name of the vendor and a hash of the file.
When users download the software file, they also download the certificate. When they install the software, the system verifies the certificate matches the file and that the certificate is valid. Chapter 14 discusses how a system validates a certificate, but in short, it queries the CA to ensure the CA issued the certificate, and that the CA has not revoked it. The system then displays a dialog box that displays information about the certificate. If the code doesn’t have a certificate, the dialog box indicates the vendor is unknown. If malware infects the file, it changes the hash, and the certificate will no longer recognize the file. Instead, the system reports an error.
Although many legitimate software vendors are willing to purchase certificates to provide assurances to their customers, malware authors are not. If criminals purchased certificates for malware they wrote, law enforcement would be able to identify the criminals relatively easily. However, criminals don’t want to lead law enforcement personnel to their door, so they don’t purchase certificates and historically haven’t digitally signed their malware.
However, in the past few years, criminals have been signing malware with code signing certificates that they stole from others. Symantec introduced Extended Validation (EV) Code Signing certificates, and the CA/Browser Forum released standards for these in 2012. EV Code Signing certificates provide a more thorough background check with the intent of providing users with a higher level of confidence for code signing certificates.
With this in mind, it’s a safe bet that digitally signed software using EV Code Signing certificates is relatively safe. However, other code may not be safe. This doesn’t mean that all unsigned software is malicious, but unsigned software should be viewed with some suspicion. Additionally, software using standard (not EV) code signing methods should be viewed with some suspicion.
Both Java applets and ActiveX controls (commonly used in websites) support code signing. Most browsers have settings that can restrict the use of unsigned software, or at least provide users with a warning if a website tries to run unsigned software.
Malicious ActiveX controls can gain a significant amount of control over a Windows operating system. ActiveX controls are largely limited to Microsoft Windows systems, but some ActiveX controls can run in Internet Explorer running on other operating systems. Java applets are theoretically portable to any operating system. However, due to differences in operating systems, the portability isn’t 100 percent.
Sandboxing as a Countermeasure
Sandboxing runs computer programs in isolated areas of memory as a security control. Antivirus programs use sandboxing to check new or untrusted applications. If antivirus software determines that a program is malicious, it blocks the application from running normally. This prevents a malicious program from infecting a computer.
Security professionals often use virtualization to test applications. For example, they create a virtual machine, and then isolate it from the physical computer and other virtual machines. They can then run the application within this isolated virtual machine. If the application causes problems, the problems are limited to the virtual machine.
Buffer Overflow Attacks
A buffer overflow occurs when an application receives more data than it expects and is unable to handle it gracefully. Applications have areas of memory called buffers that they use for temporary data storage. These buffers are specifically defined areas of memory, and applications are normally unable to access memory spaces beyond the buffers. However, there are times when an application gets overwhelmed by the amount of data sent to it, allowing it to access memory beyond the defined buffer.
A buffer overflow error exposes normally protected memory areas. If attackers can exploit a buffer overflow error, they are able to write additional data into the overflow area. Attackers often include a large volume of no operation (NOOP) commands in an attack to position the memory pointer. Attackers can then add malicious code after the NOOPs, allowing them to insert the malicious code into memory.
As an example, an application may expect a user to enter some specific data, such as a number between 1 and 10. An attacker may try to send different data, such as an escape sequence and multiple NOOP commands, to see what happens. If the different data is not expected, it can cause an error. If the application doesn’t handle the error gracefully, the attacker can try to repeat the error but add more data. This additional data can include a malicious script that installs itself on the server.
Proper error handling within an application ensures that it can handle errors gracefully. Error handling routines provide user-friendly errors to users and log details giving administrators insight into what happened. They also ensure the application doesn’t crash.
Input validation helps prevent buffer overflow attacks. Additionally, keeping systems updated protects against buffer overflow attacks. When a buffer overflow vulnerability occurs, vendors release patches that fix the problem. Patched systems are protected against known buffer overflow attacks. Of course, if patches are not applied, the system remains vulnerable.
Injection Attacks
Injection attacks include SQL injection and command injection attacks. In either type of attack, the attacker attempts to inject code into an application. If successful, the code runs a command outside of the application. Input validation is a primary prevention against these types of attacks.
SQL Injection
SQL (Structured Query Language) is the language used to communicate with databases. SQL statements provide the ability to read, write, modify, and delete data within a database. In many cases, programmers create richer websites by interacting with a database, and they use SQL statements to do so.
Normally, this works fine. However, many malicious attackers know about SQL and they can sometimes use these same SQL statements to interact with a database through an application or an online website. As an example, when entering data into a website form, an attacker can enter a specially crafted string of code that includes a valid SQL statement. This allows attackers to access the backend database. To get a better idea of how a SQL injection attack can access data in a database, it’s useful to understand how dynamic SQL works.
Dynamic SQL Imagine a website that expects a user to enter a username and password into two text boxes on a website. If the credentials match, the website can retrieve the user’s name from a table named Authentication. The two text boxes on the web page are named txtName and txtPassword, and the following dynamic SQL statement will retrieve the user’s first name:
![]()
The statement will take the data entered in both text boxes and dynamically add it to the SQL statement. For example, if Darril enters Darril as the username and P@ssw0rd as the password, the SQL statement is interpreted like this:
![]()
SQL Injection Attack An attacker with a little knowledge of SQL can enter specific strings of characters to access the database, and possibly cause damage. Two pieces of knowledge about SQL syntax are important here:
• A semicolon (;) indicates the end of a SQL statement.
• Two hyphens (--) indicate a comment that is ignored.
With this knowledge, the attacker can enter different data in the txtName and txtPassword text boxes discussed in the previous section. Suppose the attacker enters whoever’ OR 5=5; -- in the txtName text box and password in the txtPassword text box as part of a SQL injection attack. Dynamic SQL uses these entries to create the following statement:
![]()
The WHERE clause checks for a login name of whoever in the Authentication table, but also includes an OR statement checking to see whether 5 equals 5. Because 5 always equals 5, the WHERE clause is always true. The statement retrieves the first name of all the users in the Authentication table. The semicolon ends the statement, and the two hyphens mark the rest of the text as a comment, which SQL ignores.
Although retrieving first names from the database isn’t necessarily a problem, a SQL injection attack allows an attacker to inject any SQL statements. Attackers can retrieve all the data from the database, modify data, and even delete data.
Input validation helps prevent this type of attack. For example, a username should not include double hyphens or semicolons, and an input validation check can reject input using these characters.
Database developers also use stored procedures instead of dynamic SQL statements. A stored procedure is a group of SQL statements that executes as a small program. Instead of plugging the user input directly into the SQL statement, the data is sent to the stored procedure. The stored procedure handles the data differently and prevents a SQL injection attack.
Some SQL injection attacks have infected systems with malware. For example, the LizaMoon SQL injection attack infected websites with scareware. When users visited the infected websites, they saw a pop-up window that indicated their systems were infected with malware. It encouraged users to install rogue antivirus software named Windows Stability Center (which is not a Microsoft product). Users who installed the bogus antivirus software were then encouraged to purchase the full version to remove reported malware.
Command Injection
In a command injection attack, an attacker attempts to insert operating system commands into an application or web page form. If successful, the command executes on the system hosting the application or web page.
A simple operating system command is dir, which lists the files in an operating system directory or folder. An attacker may be able to insert a specially crafted string of characters into a web page form, followed by the dir command. The string of characters provides access to the operating system command shell and then executes the dir command.
Of course, the attack can be much more malicious than just retrieving a list of files. If successful, the attacker is able to execute any command supported by the operating system. As with other injection attacks, input validation is the primary prevention.
Cross-Site Scripting
Cross-site scripting (XSS) is a relatively common attack that attempts to inject HTML or JavaScript code into a web page. The attacker modifies the code on the website, and when the user goes to the website, the code executes on the user’s system.
In most cases, the website is a legitimate one, but after the attack, it can become a malicious website for visiting users. The attack doesn’t cause direct problems for the website, but it can cause problems for the users and indirect problems for the website.
XSS attacks attempt to steal sensitive information from users’ systems, such as cookies or other information. In some cases, the cookies can include session information, and an attacker can use this to launch a session hijacking attempt. If the website developer used the cookie to store user information such as passwords or credit card data, the attacker now has access to this information.
As with other types of injection attacks, a primary protection is server-side input validation. In this case, the website application can filter out any attempts to include HTML or JavaScript tags using the < and > characters. However, developers need to be much more proactive when developing web applications to prevent XSS attacks. The Open Web Application Security Project (OWASP) has published a list of rules developers can follow to prevent XSS attacks in their XSS Prevention Cheat Sheet. You can find it by going to https://www.owasp.org and searching on XSS Prevention Cheat Sheet.
Cross-Site Request Forgery
Cross-site request forgery (CSRF, pronounced as sea surf, and sometimes identified as XSRF) includes “cross-site” in the name, but it is different from an XSS attack. An XSS attack attempts to download malicious code from the website to the user’s system. A CSRF attack attempts to send a malicious command from the user’s system to the website. Both occur without the user’s knowledge.
In a successful CSRF attack, the attacker tricks the user into clicking a malicious link that includes a command. The website treats the command as if the user sent it and executes it.
As an example, consider an HTML query. HTML queries can include additional data. For example, if you launched Google, you could enter the following text into Google to do a search: Darril “Security+”. You can also do the same search with the following query embedded in a hyperlink:
https://www.google.com/search?as_q=Darril&as_epq=%22Security%2B%22
This query includes several elements worth pointing out:
• ?as_q The question mark character indicates that the appended HTML link includes a query, and as_q indicates the query is using Google’s advanced search function.
• =Darril This equal sign identifies a search term, which is Darril in this example.
• &as_epq=%22Security%2B%22 The ampersand indicates another search term, and as_epq indicates it is using Google’s advanced search function with quotes. It includes %22, which is the hexadecimal code for a quote symbol, and %2B, which is the hexadecimal code for the plus symbol. It looks like “Security+” in the query.
Websites often use the same type of HTML queries to send data entered in one page to a second page. For example, if mcgraw-hill.com allowed users to provide information such as their name and e-mail addresses, it could also have a web page that allows users to change their e-mail address. Users could log on, enter their new e-mail address in the form, and click a button to submit the change. When users click the button, it would send a query similar to this:
http://mcgraw-hill.com/change?action=set&key=e-mail&[email protected]
In some cases, the user doesn’t even need to be logged on to take this action. Many websites use cookies. When the user revisits a website, it reads the cookie and logs the user back on. If a user clicks a link or enters the string into his or her web browser, the website can identify the user by reading the cookie and taking the requested action.
An attacker can use this information to craft a different HTTP link to change the user’s e-mail address to the address of the attacker. Assuming the previous McGraw-Hill query actually worked, the attacker’s query would look something like this:
http://mcgraw-hill.com/change?action=set&key=e-mail&[email protected]
Once attackers craft the HTTP link, they only need to encourage the user to click it. The link can be embedded in a phishing e-mail or in any type of HTML object, such as an image that includes a link. When the user clicks the link, it sends the command to the website.
Changing an e-mail address may sound trivial. However, if the site doesn’t use security to validate the user before making a change, attackers may be able to change other types of information, such as the user’s password. In some cases, CSRF attacks may enable attackers to make purchases on behalf of the user.
Websites protect against these attacks by verifying the user before making such a change. Most professional web developers know better than to take some actions without validating the user again. In other words, they use a separate step to log a user on instead of trusting the cookie actions. As an example, if you’ve ever bought anything from Amazon.com using your computer, your computer has an Amazon cookie that allows Amazon to identify you when you visit. However, if you try to make a purchase or modify any of your account details, Amazon challenges you to enter your credentials again. This prevents a successful CSRF attack.
One of the best protections users can take is to avoid clicking unknown links. This is especially true for any links received via e-mail from an unknown source.
Password Attacks
Attackers often try to learn passwords through different methods. If the attacker is able to learn the username and password of an account, the attacker can then impersonate the user by logging on with the user’s credentials. A password cracker is a program that tries to discover, or crack, passwords.
Hashed Passwords
One of the ways that passwords are protected is by hashing them. A hash is simply a string created by executing a hashing algorithm against the password, and the hash will always be the same if the password is the same. For example, imagine a password is P@ssw0rd and the hash of the password is 1A2B3C. No matter how many times you execute the hashing algorithm against this password, it will always create a hash of 1A2B3C. (The actual hash would be longer, but I’ve shortened it here for brevity.) Instead of storing the password in cleartext, the hash of the password is stored in an authentication database.
When a user logs on, the system hashes the password entered by the user and sends the hash to an authentication server holding a database of hashed passwords. Credentials are typically encrypted when sent over a network to prevent a sniffing attack from capturing the hash. The authentication server then decrypts the credentials and compares the hash of the password provided by the user with the hash stored in the authentication database. If they match, the user is authenticated.
Older hashing functions such as MD5 are not recommended for hashing passwords. Instead, a strong hashing algorithm such as Secure Hash Algorithm 3 (SHA-3) should be used. SHA-3 can create hashes up to 512 bits long.
Common Password Attacks
The following list describes some common password attack methods:
• Brute-force In a brute-force attack, the attacker tries all possibilities until getting a match. This can be quite time consuming when performed manually, but password-cracking tools automate the attempts. Brute-force efforts generally take the most time and effort when compared with other password attacks. This attack can be thwarted by using strong passwords of sufficient length and with multiple character types. The longer and more complex a password is, the harder it is to crack with a brute-force attempt.
• Dictionary A dictionary attack attempts to use all the words in a dictionary or a database of different words. Password dictionaries usually include words from multiple languages in addition to commonly used passwords such as 123456, iloveyou, qwerty (the first five letters next to the TAB key), 7777777, letmein (let me in), trustno1 (trust no one), and qazwsx (the first six letters from top to bottom on the left side of the keyboard). Strong, complex passwords thwart dictionary attacks.
• Social engineering The simplest way to get a password is to ask for it. Although most users won’t give up their password easily, social engineers often trick users. For example, phishing attacks (described later in this chapter) often ask users for their username and password, and some users respond.
Rainbow Table Attacks
A rainbow table attack is a more sophisticated attack used to learn passwords. It uses comparative analysis techniques to identify passwords. To make this attack easier to understand, it’s worthwhile examining each of the steps in a comparative analysis.
Imagine that an attacker has captured a hashed password either by infiltrating a network and exfiltrating a database containing password hashes or by capturing packets containing a hash with a sniffer. In either case, the attacker now knows that the hash of a password is 1A2B3C. The attacker can then use the following steps to discover the password from the hash:
1. The attacker guesses a password.
2. The attacker calculates the hash of the guessed password.
3. The attacker compares the calculated hash with the captured hash.
a. If the hashes are the same, the attacker knows the guessed password is the actual password.
b. If the hashes are not the same, the attacker repeats the steps.
The most time-consuming part of this process is guessing another password and then calculating the hash. However, a rainbow table shortens this time considerably. A rainbow table includes two columns. One column is a list of guessed passwords and the matching column includes the hashes of the guessed passwords. A program compares the captured hash with each of the hashes in the rainbow table. When it finds a match, it retrieves the actual password from the second column.
Attackers create rainbow tables using programs such as RainbowCrack and character set definition files that define the keyspace for the password. A typical character set definition file includes the following character set definition lines:
• numeric:
[0123456789]
• alpha:
[ABCDEFGHIJKLMNOPQRSTUVWXYZ]
• alpha-numeric:
[ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789]
• loweralpha:
[abcdefghijklmnopqrstuvwxyz]
• loweralpha-numeric:
[abcdefghijklmnopqrstuvwxyz0123456789]
• mixalpha:
[abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ]
• mixalpha-numeric:
[abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789]
• keyboardascii-32-95:
[ !”#$%&’()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[]^_`abcdefghijklmnopqrstuvwxyz{|}~]
• ascii-32-65-123-4:
[ !”#$%&’()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[]^_`{|}~]
• alpha-numeric-symbol32-space:
[ABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()-_+=~`[]{}|:;”’<>,.?/ ]
The rainbow table generation program then creates passwords using all the characters in each character set. For example, the attacker can specify a password length up to 14 characters. The program will then create all possible combinations using between 1 and 14 characters, and using only the characters in the numeric data set (0123456789). As it creates the password, it also creates the hash and stores both in the rainbow table. When finished, the program does the same with each of the remaining character sets.
It can take several hours to create a rainbow table. The actual time depends on how many character sets are used, the length of the passwords, the hashing algorithm, and the processing power of the computer creating them. Once the rainbow tables have been created, attackers can use them to crack passwords using a simple rainbow table lookup process.
Several rainbow tables are available using different hashing algorithms, different character sets, and targeted against specific operating systems. Attackers can download the rainbow tables from sites that have already created them, or create the rainbow tables on their own. Although rainbow tables can be very large (such as 864GB for nine-character passwords hashed with the SHA-1 hashing function), they significantly reduce the time required to crack a password.
A primary protection against rainbow table attacks is key stretching. Key-stretching techniques salt the password before hashing it. A salt adds a random number of bits to the hashed password. In other words, an unsalted hash of P@ssw0rd may be 1A2B3C, but when it’s salted, it could be 3602FD or just about any other hexadecimal number. Chapter 14 discusses key-stretching techniques such as Password-Based Key Derivation Function 2 (PBKDF2) and bcrypt.
Spam
Spam is unsolicited commercial e-mail (UCE) and other unwanted electronic messages sent in bulk. It is most often associated with e-mail, but attackers send spam via other means, such as instant messaging. Companies have used spam to send unwanted advertisements. However, the bigger risk is that attackers now regularly use spam to launch different types of attacks.
The cost of sending spam is low for spammers. A single e-mail can include multiple e-mail addresses, making it relatively easy to send an e-mail to thousands of recipients at a time. Additionally, cyber criminals can rent access to botnets to send spam instead of creating their own botnet.
Criminals harvest e-mail addresses using a variety of methods. For example, some programs called web spiders crawl through the Web looking for the @ character to identify e-mail addresses. If you post messages on a website with your e-mail address, these spiders will likely find it and add your e-mail address to a spam list. These criminals then sell or rent the lists to others wishing to send spam.
Phishing Attacks
A phishing attack is spam with malicious intent. It encourages a user to respond with personal information or to click a link. Attackers send massive numbers of e-mails with the goal of fishing for victims. Phishing e-mails often claim to be from a legitimate company and encourage the user to either click a link or provide a response.
Here’s an example of a phishing e-mail that attempts to get users to respond with their logon credentials for a bank account.
Warning! This is a security alert from YourBank. We have noticed suspicious activity on your account. To protect you, we are putting a hold on your account until we can verify certain activities. Please click the following link and validate your account. If you do not validate your account, funds in your account will be frozen and remain inaccessible.
If you click the link, it takes you to a bogus website that looks similar to YourBank’s website, but is actually a malicious website. It includes logon text boxes where you can enter your username and password. Of course, if you enter your credentials, the attacker will use them to remove your money.
Attackers quickly funnel money drained from accounts this way to offshore accounts. If the activity isn’t discovered within 24 hours, the chances of recovering the money are extremely low. Thankfully, banks typically provide fraud insurance for personal bank accounts, so the account holders receive their money back if it is stolen. However, business accounts don’t have the same protection. If an employee accidentally gives up credentials for the organization’s bank accounts, attackers can drain the accounts. This can cause a financial catastrophe if the organization doesn’t have fraud insurance.
You’ve probably received some phishing e-mails that look like they are from a bank or a company where you don’t have an account. Attackers send out mass quantities of these e-mails knowing that not every recipient has an account with the bank, but also knowing that many of them do. Imagine that an attacker sends out an e-mail to 10,000 recipients but only 1,000 of the recipients (10 percent) actually have an account with that bank. If an attack reaches 1,000 potential targets, it has some great possibilities of success.
Even though phishing has been going on for a long time, it still fools many people. Google released the “Handcrafted Fraud and Extortion: Manual Account Hijacking in the Wild” study in late 2014. The study found that phishing attacks succeed between 3 percent and 45 percent of the time, with sophisticated attacks enjoying the most success. Additionally, the study found that attackers used the stolen credentials within 30 minutes after users provided them.
A phishing e-mail usually has several basic components:
• Impersonation A phishing e-mail impersonates a legitimate company. It may include actual graphics from the company and use similar fonts. For example, an e-mail that claims it is from PayPal may include PayPal graphics.
• Identification of a problem The e-mail usually indicates some type of problem that is of a concern to the reader. The phrase “suspicious activity” or something similar is often included in these e-mails.
• A sense of urgency Recipients are encouraged to take immediate action. Although the phishing e-mail doesn’t state it this way, the goal is to get the user to click without any more thought.
• Dire consequences The phishing e-mail warns of some dire consequences, such as closing an account, locking out an account, or freezing funds, if the recipient doesn’t respond. For individuals doing business through a company such as eBay or PayPal, the threat of their account being closed, or locked, sounds dire. This often propels them into taking immediate action.
Phishing and Drive-by Downloads
Some phishing e-mails just want users to click a link. If they click, the link takes them to a malicious website that attempts to start a drive-by download. Notice that in this case, it doesn’t matter whether a user enters any personal information or not because the attacker only wants the user to click the link. Drive-by downloads attempt to install malware and, when successful, often join the computer to a botnet.
Some phishing e-mails mention a failed delivery attempt from a service such as FedEx, and encourage the user to click the link for more information. Other e-mails have impersonated funeral homes. They mention a pending funeral and encourage the user to click for more details. These are just two examples, but attackers have used many more methods.
Spear Phishing and Whaling
Spear phishing and whaling are variants on the phishing theme. Phishing attacks send out massive amounts of spam e-mail without knowing the targets. In contrast, spear phishing and whaling attacks attempt to identify the targets.
A spear phishing attack targets a specific organization or group. For example, a spear phishing attack could target a military organization by sending e-mails to recipients with the appearance that Sergeant Jones sent it from within the organization. Because it looks like it’s from someone within the organization, recipients are more likely to open it. The contents could state something about a missed deadline and ask the user to provide some information in an attached document. However, the attachment includes malware and attempts to install itself on the user’s computer if the user opens it.
The From address provides a level of trust because it looks like it’s coming from a fellow employee. Because of this, some users are more willing to open the e-mail and the attachment. In contrast, these users might not respond to a typical phishing attempt.
In a whaling attack, the attacker attempts to identify an executive such as a chief executive officer (CEO), president, vice president, or manager. The attacker may be able to get the name and e-mail address information from public sources or through a social engineering attack with another employee. The subject line of a whaling attack may include words such as “Past Due” or “Lawsuit” that may get immediate attention from the executive.
If an attacker can get a response from a high-profile figure (a whale, if you will), the potential payoff is huge. For example, if an attacker is able to convince an executive to install keyloggers on the organization’s systems, the attacker can steal highly valuable information and perhaps even account information to empty an organization’s bank accounts.
Vishing
Vishing is a slight variation of a phishing attack. Instead of using e-mail, the attacker uses the telephone system or possibly a Voice over Internet Protocol (VoIP) system. The goal is similar to phishing. It attempts to trick the user into providing information that the attacker can use for personal gain.
A vishing attack starts by making a call. Some use a recording to alert people of some type of fraudulent activity with their bank or credit card, and encourage them to call a phone number immediately. If individuals return the call, an automated system often prompts them to enter information in the phone’s keypad, such as a credit card number, expiration date, and more.
I once received a voicemail message mentioning suspicious activity on a credit card. I called back, and the woman who answered started asking personal questions that raised alarms for me. When I expressed distrust, the woman said, “You called us,” as if that was supposed to tell me everything was OK. It wasn’t and I ended the call. There weren’t any problems with my credit card then, but if I kept answering questions, there would have been.
In contrast, after a business trip, one of my credit cards had some actual suspicious activity. My bank called and left a message asking me to call back. When I called back, the person provided information that made it clear she was an employee of my bank before asking me to provide information about my account. In other words, we provided mutual authentication.
Because vishing uses VoIP, it often takes advantage of additional features. For example, attackers can trick caller ID so that phone calls appear to be coming from a bank or someone else other than the attacker’s phone number.
Smishing
Smishing is another variation of a phishing attack, but it uses text messages such as Short Message Service (SMS) messages commonly used with many smartphones. Attackers send a text message to users, indicating that there has been suspicious activity on an account. It then prompts the user to call a phone number to resolve the problem.
When the user calls the number, he or she often hears a voice recording that prompts the user to enter information such as an account number and personal identification number. It may prompt the user to give additional information, such as their birthdate, Social Security information, and more.
Zero Day Exploits
Zero day exploits are attacks that take advantage of vulnerabilities that are unknown to and/or unpublished by the vendor. However, even though the vendor might not know about the vulnerabilities, some attackers know about them. The two common scenarios for zero day vulnerabilities are
• Unpublished and unknown by the vendor, but known by attackers For example, an attacker may discover a buffer overflow vulnerability and launch an attack using this vulnerability. The attacker may share the knowledge with other criminals, and each of these attackers can launch zero day exploit attacks.
• Known by the vendor, but not published At some point, the vendor learns about the vulnerability. However, it takes time to develop and release a patch to fix it. For example, an antivirus company could discover an issue with a Microsoft operating system and inform Microsoft. Microsoft will investigate and write a patch to fix it, but its personnel also need to test the patch before releasing it. Attacks that attempt to exploit the vulnerability before Microsoft publishes the patch are zero day exploits.
The danger from zero day exploits also helps to emphasize the importance of a defense in depth strategy. If the vulnerability is unknown to the public and the vendor hasn’t released a patch, IT personnel won’t know about it. However, other security practices can help prevent a successful attack.
For example, one of the basic elements of hardening a system, or making it more secure from the default configuration, is to disable unneeded protocols and services. Imagine that an attacker discovers a zero day vulnerability with FTP and launches an attack on a server. If the server has FTP enabled by default, even though it does not need FTP, it is vulnerable to this attack. On the other hand, if the server was hardened and FTP is disabled, it is not vulnerable to the attack.
Covert Channel
A covert action is a secret one that is not open or acknowledged, such as a clandestine spy operation, and a channel is a communications path between two computers. Combined, a covert channel is a mechanism used to transmit and receive information surreptitiously between two computers. Covert channels often use nontraditional communication paths, which helps them bypass traditional controls such as firewalls and IDPSs.
For example, TCP uses a TCP handshake process to establish a TCP session. The primary pieces of information used in these packets, besides the source and destination data, are the SYN and ACK flags. However, there is room elsewhere in the TCP packet, such as in the protocol ID field, to add more data. For example, one person could add ASCII codes for individual characters in the protocol ID field before sending the TCP packet to another person. If both people know the packets include this data, they can use it as a covert channel to share information.
The ability to transfer small pieces of data in the protocol ID field is a well-known tactic. Many firewalls and IDPSs can check packets for this additional data and identify the covert channel. However, attackers can use other covert channels that aren’t known to others.
Wireless Attacks and Countermeasures
Wireless networks have become very popular due to their convenience. However, convenience often has a cost, and with wireless networks, the cost is increased risk. Attackers have multiple methods they can use to attack a wireless network, but countermeasures are effective at blocking these attacks or thwarting their success.
WPA2 as a Countermeasure
Wi-Fi Protected Access 2 (WPA2) provides strong protection against attacks. WPA2-Enterprise uses an 802.1x authentication server and is more secure than WPA2-Personal. WPA2-Enterprise requires each user to log in with an account before they can access the wireless network. WPA2-Personal only requires users to know the SSID and a password or preshared key.
Wired Equivalent Privacy (WEP) has several significant weaknesses and should not be used. Wi-Fi Protected Access (WPA) is stronger than WEP, but WPA2 is stronger. WPA2 uses Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP). CCMP is based on the Advanced Encryption Standard (AES) and provides significantly stronger security than protocols used with WEP or WPA. WPA3 will be the strongest when it is fully implemented.
The Wi-Fi Alliance announced three security enhancements to WPA2 in January 2018. Vendors that create wireless devices are required to implement these enhancements in their devices to maintain the Wi-Fi CERTIFIED classification. Most users are unlikely to notice these changes as they are technical changes that aren’t readily apparent. The Wi-Fi Alliance’s announcement didn’t include a timeframe of when these changes will be required by vendors. However, it will take time for vendors to fully implement these changes. The security enhancements are as follows:
• Protected Management Frames (PMF) PMF helps ensure the integrity of wireless network management traffic. Many devices are already using PMF.
• Best practice checks Device vendors are required to conduct several checks on their devices to ensure they are using best practices. The goal is to reduce common vulnerabilities caused by misconfigurations.
• 128-bit level cryptography Devices are required to implement 128-bit level cryptographic suite configurations. This will help standardize network security.
WPA3 as a Countermeasure
The Wi-Fi Alliance announced WPA3 at the January 2018 Consumer Electronics Show (CES). While they didn’t provide a lot of details, they did mention that it is the designated replacement for WPA2 and it will provide a significant upgrade to wireless security. They outlined four new security capabilities that WPA3 will provide:
• Protection against brute-force dictionary attacks Devices will send an alert to the network when it detects someone guessing a password. This is intended to prevent attackers from guessing a password offline and to protect users who create weak passwords.
• Simplify the configuration process Many wireless devices, such as IoT devices, have limited display interfaces, making it difficult to implement them securely. Users will be able to configure WPA3 devices on a network. They will initiate the process by scanning a QR code or possibly tapping a smartphone against the device.
• Improved privacy on open networks Users commonly connect to open networks, such as in a coffee shop, without the need for a password. However, by default, this traffic is sent over the wireless network in an unencrypted format. WPA3 devices will connect to open networks with individualized data encryption.
• 192-bit level cryptography Devices are required to support 192-bit-level cryptographic suite configurations. These are formally defined as the Commercial National Security Algorithms (CNSA) suite.
WIDS and WIPS as Countermeasures
Wireless intrusion detection systems (WIDSs) and wireless intrusion prevention systems (WIPSs) monitor wireless frequency channels and can discover many problems. They monitor the 2.4-GHz and 5-GHz wireless frequency spectrums and can detect unauthorized access points and suspicious activity. This includes rogue access points, evil twins, MAC spoofing, and traffic patterns from known attacks. When they detect an unauthorized or suspicious activity, they can send alerts to notify administrators.
Rogue Access Points
A rogue access point (AP) is an unauthorized wireless AP set up within an organization’s premises. Attackers connect the rouge AP to a wired network and then use it as a sniffer to capture traffic. After installing the rogue AP, attackers can collect traffic from a distance, such as in the organization’s parking lot. The attacker simply uses a laptop to connect to the rogue AP and collects the traffic.
Physical security is a primary countermeasure against rogue APs connecting to a network. Protecting network devices (such as routers or switches) in secure server rooms or locked wiring closets prevents an attacker from connecting the rogue AP to the wired network.
Attackers sometimes set up rogue APs in public places such as coffee shops. They leave them open so that any user can connect and access the Internet via the AP. Often they’ll name the AP something similar to the location (such as CoffeeAndFreeWiFi). However, the attackers can capture all data sent to and from the user.
Wireless spectrum analyzers can detect rogue APs. For example, Fluke’s AirMagnet WiFi Analyzer Pro allows administrators to monitor all the channels in the 2.4-GHz and 5-GHz ranges to detect activity. It will identify rogue APs and monitor the overall health of the wireless network. Two other tools used to detect rogue APs are WIPSs and WIDSs, as described in the preceding section. Fluke’s analyzer is an example of a WIDS.
Evil Twins
An evil twin is a type of rogue access point that appears to be legitimate. Attackers use the evil twin to trick users into connecting, and when users connect, attackers collect the data. Attackers use evil twins in one of two ways:
• Within an organization When evil twins are used within an organization, attackers name the APs with the same or similar service set identifier (SSID) names. Users are more likely to connect to APs with similar SSIDs. Organizations use WIDSs and WIPSs to detect these APs.
• In a public place Attackers set up APs in public places such as airports, hotels, coffee shops, parks, and restaurants. Users connect to get free or cheap wireless access, but the attacker uses the AP to collect their data.
The best protection against evil twins is to avoid connecting to public wireless networks. However, some basic countermeasures provide protection. They include
• Confirm that the wireless network is legitimate before connecting to it.
• Do not enter any login credentials that an attacker can capture and use.
• Do not install software from the public wireless network.
A more advanced countermeasure is to use a commercial virtual private network (VPN) service. For example, CyberGhost offers both free and paid versions of its CyberGhost VPN service. Users create secure connections to the VPN service through the free public wireless network. This prevents attackers running evil twins from collecting user data.
Wardriving
Wardriving is the practice of looking for wireless networks, typically from a car. Attackers can drive around with a laptop and a wireless connection. When they find a wireless network, they attempt to access it.
The best countermeasure against war driving attacks is to use secure wireless protocols. This includes WPA2. WPA2-Enterprise uses an 802.1x authentication server and is more secure than WPA2-Personal, which only requires a preshared key or password.
WPA Cracking Attacks
Attackers use WPA cracking attacks to learn the password for a wireless network. They use a wireless sniffer to capture wireless packets and look for a WPA four-way handshake (indicating a user has logged on). The handshake includes an encrypted version of the AP’s password. Once attackers capture the encrypted password, they use an offline brute-force attack to discover the password.
It might take some time before a user authenticates and initiates the WPA handshake. To speed up the attack, attackers send data onto the network, causing the user’s system to lose its association with the AP. This requires users to log on again, initiating the four-way handshake.
The best countermeasure against WPA cracking attacks is to use WPA2. If WPA2 is used, a strong wireless network password helps thwart WPA cracking attacks. Passwords can be up to 63 characters long.
WPS Attacks
Wireless access points typically include Wi-Fi Protected Setup (WPS). WPS allows users to configure wireless devices by clicking a button on the access point and clicking a button on the wireless device. These are typically physical buttons, but in some cases they are logical buttons accessed via an interface, such as a web page. Other times, users configure the devices by entering a personal identification number (PIN). While using the buttons is an easier method for users, WPS always supports the use of a PIN.
A WPS attack uses brute force to discover the PIN. Because WPS doesn’t include a lockout feature, attackers can keep guessing until they discover the correct PIN. When they guess the correct PIN, the access point responds with the SSID and password used for the access point. Reaver is an open source tool that automates the process. It can discover an eight-digit PIN in 10 hours or less.
The best countermeasure is to disable WPS when it is not in use. You can usually disable WPS within the AP interface. Unfortunately, this isn’t always reliable. Some access points still respond to Reaver queries even with WPS disabled. If your AP is still responding to Reaver WPS queries with WPS disabled, check with the AP’s vendor to see if it has released an update for the device.
Understanding Social Engineering
Social engineering is the practice of convincing people to give up sensitive data or to perform actions they wouldn’t normally perform. A social engineer uses deception and fraud to trick or manipulate unsuspecting users.
Sometimes a phone call to an employee can elicit a good deal of information. Attackers can learn the names of executives through public sources such as web pages, newsletters, and company brochures. Attackers can say something like, “I’m gathering some information for so-and-so,” using the name of a high-level executive. This might be enough to get the employee to give out information.
With some basic information from a first phone call, attackers can build on that with other phone calls to other departments. Repeated a few times, attackers can build their knowledge, such as identifying how the organization formats e-mail addresses (perhaps as firstname.lastname@company.com) and learning the format of user accounts. Attackers may make a phone call to the IT department and ask something like, “I can’t remember my password. Can you help me log in?” Such an inquiry may convince an uneducated help desk technician to change the password and give it to attackers. It’s also possible for an unsuspecting employee to give up his or her own username and password, allowing attackers to log on with that employee’s account.
Social engineers appeal to someone’s inherent desire to be helpful and liked. They exploit values such as courtesy and appeal to other people’s vanity. Often they take the time to build familiarity and build trust. In some cases, they can invoke the name of an authority figure, such as an executive, to encourage a person to respond. If necessary, they can use intimidation tactics and threaten undesirable action to get what they want. They often create a sense of urgency to prevent people from analyzing the activity.
One of the primary methods to counteract social engineering is to educate users in the tactics of social engineers. Once employees recognize the value of information and common tactics used by social engineers, they are better able to identify and thwart a social engineer in action. The following sections identify some common social engineering tactics.
Tailgating
Tailgating (or piggybacking) occurs when someone passes through a controlled entry without providing credentials by following closely behind someone who has provided credentials. As an example, some organizations issue proximity badges to users. Employees swipe their badge in front of a proximity badge reader and it unlocks a door. All employees should use their own badge to open the door and gain entry. However, it’s possible for one employee to open the door with a badge and other people to follow that person in without using their own badges. These other people are tailgating.
Imagine the beginning of the workday as the majority of the employees are coming into the building. It’s unlikely that each employee will shut the door in the face of fellow employees. If the organization is large, employees may not know who is a fellow employee and who isn’t. A social engineer could easily slip into the crowd and walk into the normally secure building without raising any suspicion.
Most people are courteous and consider slamming the door on someone else to be rude. When people have the choice of being either courteous or secure, they often choose the courteous path. Attackers know this. Often just a friendly smile is all that’s needed if someone gives the social engineer a questioning look. Similarly, an attacker can load her arms with books or boxes and approach the door. A friendly employee may actually hold the door open for her to enter.
Educating users is a great start against tailgating, but it isn’t always enough. Another way to stop tailgating is with a mantrap. The formal definition of a mantrap is a large enclosure that allows entry through one side and exit through the other, and can actually lock the person inside. Some are large steel bars formed as a revolving door that looks very similar to a cage.
However, instead of using cages to control entries, many organizations simplify this to turnstiles similar to what you see in a subway or bus station. Employees swipe their badge and the turnstile releases to allow one person through. When using a mantrap, even if it’s a simple one like a turnstile, employees cannot keep the entrance open for a potential attacker, and it thwarts tailgating.
Impersonation
Another social engineering tactic is impersonation, where the social engineer impersonates someone. Impersonation can be over the phone, such as by invoking the name of someone in authority. It can also be in person, such as impersonating a technician.
For example, it’s relatively easy to get a uniform that looks like it’s from another company, such as the phone company. The social engineer can don the uniform, enter the building, and let a receptionist know he or she is there to fix some fictional problem. An uneducated employee might lead the attacker directly to a wiring closet, where the attacker can install a rogue access point.
Skimming
Skimming is the process of capturing information from credit cards at point-of-sale (POS) readers, gas pumps, and automated teller machines (ATMs). The attacker typically places a thin filament-based plastic, called a skimming film, into a card reader. When the victim inserts their credit card or debit card into the reader, the skimmer captures the data on the credit card or sometimes withdraws money from the debit account.
Attackers have gotten more sophisticated in these attacks, making it more difficult to detect the skimming film. Many gas pumps now have tamper-proof stickers that will be broken if an unauthorized individual opens the card reader and installs a skimming film. Experts recommend using ATMs and POS readers that are in the open and enjoy a lot of traffic. Attackers are less likely to insert skimming films in a reader that has a lot of regular traffic.
Dumpster Diving
Many attackers gain information by sifting through someone else’s trash, a practice commonly known as dumpster diving. Dumpster diving can provide significant returns depending on how much information an organization or an individual throws away.
For example, if an organization regularly throws away papers that include information such as customer names, addresses, and credit card data, an attacker can retrieve this from the trash and use it. Similarly, if an individual throws away credit card offers, blank checks from a credit card company, or other personal data, an attacker can retrieve it and use it.
As a best practice, any information that contains any type of personal information should not be thrown away. Instead, these papers should be shredded using a crosscut shredder or burned to ensure they cannot be read.
Shoulder Surfing
Shoulder surfing is the practice of looking over someone’s shoulder to gain information. For example, an attacker may try to watch someone enter a username and password to learn the user’s credentials, or watch someone enter the numbers for a cipher lock on a door, a PIN for a badge, or even a PIN for a debit card.
Social Networking Attacks
Attackers are taking advantage of the popularity of social networks such as Facebook, Twitter, and YouTube to launch social engineering attacks. Attackers craft e-mails that look exactly like they came from the social network site and send them out to users.
For example, Facebook often sends notifications to users indicating that they have messages or pending invites and includes a link to the Facebook site. The attacker uses the same template letting the user know a message is waiting, but includes a link to a malicious website. If the user clicks the link, the website may attempt a drive-by download or encourage the user to install a Trojan horse. In other cases, the site is a fake one claiming to sell cheap drugs or casino gambling access or some other site intended to get the user to enter credit card data.
User Awareness as a Countermeasure
A primary method of combating social engineering attacks is by raising user awareness through training and other methods. When users recognize the tricks that social engineers use, they are less likely to fall for them.
User awareness training can’t just be a one-time event, either. Instead, users need occasional retraining. Attackers are constantly modifying their attacks and attack methods. Likewise, users need updates on these different tactics, in addition to reminders of risks.
The following are some of the common methods used to educate and reeducate users:
• Acceptable use policy Most organizations include an acceptable use policy that informs users of the organization’s expectations regarding the employee’s use of computing resources. It lets users know what their responsibilities are and can include basic information on the risks of social engineering attacks. Employees normally review and acknowledge an acceptable use policy when they are hired and then periodically afterward, such as annually.
• Initial training when hired Many organizations include initial security training as part of a new employee’s indoctrination. This could be a short presentation, a short video, an online presentation, or even a written document for the new employee to read and acknowledge. As risks and threats change, the organization modifies the initial training.
• Annual refresher training Refresher training reminds personnel about basic risks and trains them about new and current attack methods. Organizations often require employees to read and acknowledge an acceptable use policy at the same time.
• Newsletters If an organization sends out regular newsletters, it’s relatively easy to add a short article or a sidebar about security. It reminds users about security while providing information on current threats.
• Periodic e-mails Just a simple e-mail reminding users of certain risks, with an example of a recent way that a victim was tricked into giving up information, can be useful.
Chapter Review
Traditional definitions indicate that hackers aren’t malicious, but crackers are. However, the media generally uses the term hacker to identify anyone who launches attacks on computers or computer systems with malicious intent. Some security professionals separate the good guys from the bad guys with terms such as white hats and black hats and refer to anyone who attacks with malicious intent as an attacker. An advanced persistent threat (APT) is a state-sponsored group that has both the capability and intent to carry out successful attacks. Insider threats often cause accidental losses by not following security policies, and allowing outside attackers into an organization.
Attackers are constantly modifying their attack strategies just as IT security professionals are constantly modifying their countermeasure strategies. Even though attacks have changed over the years, many attacks share common characteristics. By understanding past attack methods, it is easier to respond to new threats and understand the need for certain countermeasures. Basic countermeasures include patching systems, hardening systems, increasing user awareness, and implementing intrusion detection and protection systems (IDPSs).
Attackers often use spoofing techniques, such as modifying the source IP address, the source MAC address, or the From field in an e-mail. Data theft refers to any attack that allows an attacker to exfiltrate data. A denial of service (DoS) attack launches an attack on a single system from a single system. A distributed DoS (DDoS) attack launches an attack on a single system from multiple systems. A botnet is a group of computers (called zombies) controlled by an attacker through a command and control center. A botnet can control tens of thousands of computers, and some have controlled over a million computers. Criminals rent out the botnets to others for money, and these botnets are used to launch attacks and send out spam.
Some attacks attempt to gain information about a network and/or traffic sent over a network. Sniffing attacks use protocol analyzers to capture data sent over a network. If the data is sent in cleartext, the attacker can read the data with the protocol analyzer. Reconnaissance attacks (such as ping sweeps) attempt to discover active IP addresses on a network. Fingerprinting attacks (such as port and service scans and TCP/IP analysis) attempt to identify details of individual systems.
Man-in-the-middle (MITM) attacks capture traffic sent between two systems, typically with a sniffer or protocol analyzer. Advanced MITM attacks can create two TLS sessions, giving the user the impression they have a secure HTTPS session, but all data is still viewable on the attacking system. A replay attack starts as an MITM attack. It then uses the captured data to impersonate one of the systems. A session hijacking attack captures information from a TCP/IP session and attempts to take over the session by impersonating one of the parties.
Domain Name System (DNS) cache poisoning attacks attempt to redirect users to alternate sites. Domain Name System Security Extensions (DNSSEC) helps prevent DNS cache poisoning.
Organizations that host their own websites need to implement software security. Countermeasures include input validation, application review, code signing, and sandboxing. Input validation is the most important countermeasure. It checks all input data before using it to ensure it is valid. It helps prevent many attacks, including buffer overflow attacks, SQL injection attacks, cross-site scripting (XSS) attacks, and cross-site request forgery (CSRF) attacks. A buffer overflow attack sends unexpected data to an application and exposes normally protected memory areas. SQL injection attacks send embedded SQL statements as input to access backend databases. An XSS attack exploits the user’s trust of a website and downloads code onto the user’s system. A CSRF attack exploits the trust that a site has in the user’s browser and attempts to send unauthorized commands from the user’s system to the website.
Password attacks attempt to discover a user’s password. Using strong, complex passwords helps thwart many password attacks. Passwords are typically stored in a hashed format. Older hashing functions such as MD5 should not be used to hash passwords. Newer hashing functions such as SHA-3 provide more security. Salting passwords with additional bits helps thwart rainbow table attacks.
Phishing is a form of social engineering that uses e-mail. The attacker sends out massive amounts of spam (unsolicited e-mail) hoping that someone responds by either clicking a link or responding to the e-mail with sensitive information such as a username and password. Simply by clicking the link, the responder can install malware on their system through a drive-by download. Variations on phishing attacks include spear phishing (targeted at an organization), whaling (targeted at a specific person, such as an executive), vishing (using telephones or VoIP), and smishing (using text or SMS messages).
Social engineering is the practice of using primarily nontechnical means to get people to give up sensitive data or perform actions they wouldn’t normally perform. A social engineer uses deception and fraud to trick or manipulate people into giving up information they wouldn’t normally give up. Tailgating occurs when one person enters a controlled space without providing credentials by following closely behind someone else who has used his or her credentials. Social engineers sometimes impersonate others, either in person or over the phone. Dumpster diving is the practice of sorting through trash to get potentially useful information that may have been thrown away.
A primary method of combating social engineering attacks is through training. The goal is to raise user awareness and change user behaviors from unsafe actions to safe actions. Training can be completed when a person is initially hired, annually, and/or periodically throughout the year. Training can consist of live presentations, online presentations, periodic e-mails, articles in newsletters, or any other means that an organization finds effective.
Questions
1. What is an APT?
A. A group, often sponsored by a government, that has the capability and intent to launch persistent attacks against an organization.
B. Software that alerts a user that their system is infected with malware, but won’t remove the malware unless the user pays a fee.
C. An attack that redirects users to a bogus website.
D. A scan to detect open ports.
2. What is the difference between a DoS attack and a DDoS attack?
A. There is no real difference.
B. A DoS attack uses technical methods, but a DDoS attack uses nontechnical methods.
C. A DDoS attack is an attack from a single system, but a DoS attack is an attack from multiple systems.
D. A DoS attack is an attack from a single system, but a DDoS attack is an attack from multiple systems.
3. Of the following choices, what is a common DoS attack?
A. TCP flood
B. Tailgating
C. Smishing
D. Whaling
4. Thousands of computers have been infected with malware and are periodically directed to send out spam to other computers. What does this describe?
A. Zombies
B. Spear phishing
C. A botnet
D. Phishing
5. Which of the following best identifies a computer controlled by a botnet?
A. DoS computer
B. DDoS computer
C. Attacker
D. Zombie
6. An attacker is using Wireshark to capture and analyze TCP sessions. What is the best term that identifies this action?
A. Dumpster diving
B. Shoulder surfing
C. Sniffing
D. Vishing
7. A system has a protocol analyzer installed. What mode must the system operate in to capture all packets that reach it, including those that are not directly addressed to or from the system?
A. Promiscuous
B. Nonpromiscuous
C. DoS
D. DDoS
8. An attacker has infected a computer within an organization and wants to identify all active hosts within the organization’s network. Which of the following methods will best meet this need? (Select three.)
A. Ping sweep
B. Port scan
C. ARP scan
D. SYN stealth scan
9. A user attempted to access http://mcgraw-hill.com/ but was redirected to a website that advertises pharmaceutical drugs for sale. What does this describe?
A. Session hijacking
B. Cross-site scripting
C. Whaling
D. DNS cache poisoning
10. Of the following choices, what provides the best protection against buffer overflow attacks?
A. SQL injection
B. Input validation
C. Cross-site scripting
D. Code signing
11. An application has received more input than it expected and the resulting error has exposed normally protected memory. What is the best explanation for what happened?
A. Phishing attack
B. Salami attack
C. Buffer overflow attack
D. Session hijacking attack
12. What type of attack can access data in a database used by a website?
A. Cross-site scripting
B. Cross-site request forgery
C. Rootkit
D. SQL injection
13. A website is preventing users from entering the < and > characters when they enter data. What is the website trying to prevent?
A. SQL injection attack
B. Cross-site scripting attack
C. Input validation attack
D. Trojan horse
14. A user receives an e-mail indicating that the bank has detected suspicious activity on the user’s bank account. The message indicates the user should log on immediately to prevent loss of funds. What is the best term to describe this attack?
A. Sniffing
B. Session hijacking
C. Phishing
D. Tailgating
15. An attacker sends an e-mail to many members of an organization and spoofs the From address so that the e-mail looks like it came from within the organization. The e-mail tries to trick recipients into following a link. What is the best definition of this action?
A. Phishing
B. Spear phishing
C. Whaling
D. Vishing
16. A system has been attacked by an exploit that isn’t published. What type of attack is this?
A. Scareware
B. APT
C. Pharming
D. Zero day
17. A user connected to a free wireless network at a coffee shop to access Facebook. Later, someone else started making posts on the user’s page. What is the most likely cause of this?
A. Zero day exploit
B. WPS cracking
C. Evil twin
D. WPA cracking
18. An attacker uses nontechnical means to learn the e-mail address of a manager within a company. Which of the following best describes this attack?
A. Social engineering
B. Shoulder surfing
C. Smishing
D. Covert cramming
19. Of the following choices, what is the best method to prevent tailgating?
A. Education
B. Mantrap
C. Antivirus software
D. Access controls on the phone system
20. What is a primary goal of security-related user awareness training?
A. Increase use of e-mail
B. Change behavior
C. Implement technical solutions
D. Show how to use applications
Answers
1. A. An advanced persistent threat (APT) is a group of people (often sponsored by a government) that has the capability and intent to launch persistent attacks against organizations. Scareware is software that alerts a user their system is infected with malware, but won’t remove the malware unless the user pays. Pharming is an attack that redirects users to a bogus website. A port scan is a scan that detects open ports.
2. D. A DoS attack is an attack from a single system, and a DDoS attack is an attack from multiple systems. Both typically use technical methods.
3. A. A TCP flood attack (also known as a SYN flood, TCP SYN, or TCP half-open attack) is a common DoS attack that withholds the third packet of the TCP three-way handshake. The other answers are not DoS attacks. Tailgating is a social engineering tactic. Smishing is a form of phishing using SMS messages. Whaling is a form of phishing against a single person, such as an executive.
4. C. A botnet is a group of computers that an attacker has taken over and now controls from a command and control center. The individual computers are referred to as zombies, but together they are a botnet. They may be directed to send out phishing or spear phishing e-mails, but that is the attack, not the network.
5. D. Computers controlled within a botnet are commonly called zombies. They are not referred to as DoS or DDoS computers, or attackers, although they can be directed to take part in a DDoS attack.
6. C. Sniffing is the practice of capturing and analyzing packets with a sniffer (a protocol analyzer). Dumpster diving refers to going through the trash looking for information. Shoulder surfing is the practice of looking over someone’s shoulder to gain information, such as the password that a user enters to log on. Vishing is a form of phishing using telephones or VoIP.
7. A. The network interface card of the system running the protocol analyzer (or sniffer) must be in promiscuous mode. If it is in nonpromiscuous mode, the sniffer will only capture packets addressed directly to or from the sniffer. DoS and DDoS are not modes for a sniffer.
8. A, C, D. Ping sweeps, ARP scans, and SYN stealth scans are three methods that can be used to discover active IP addresses within a network. Hosts on a network have IP addresses, so this method can identify all active computers. A port scan attempts to discover what ports are open on a single system. While port scans can be run on all computers, they won’t identify all hosts on the network.
9. D. A DNS cache poisoning attack attempts to redirect traffic away from legitimate servers. A session hijacking attack captures information from an ongoing TCP/IP session and uses it to take over the session, impersonating one of the parties. A cross-site scripting attack attempts to inject malicious HTML or JavaScript code into a web page. Whaling is a phishing attack that targets executives such as CEOs.
10. B. Input validation techniques validate data before using it and can help prevent a wide variety of attacks, including buffer overflow attacks. SQL injection is an attack that attempts to inject SQL code into an application. Cross-site scripting is an attack that attempts to inject HTML or JavaScript code into a web page. Code signing uses a certificate to digitally sign an application, but will not protect against buffer overflow attacks.
11. C. A buffer overflow occurs when an application receives more input than it expected and it is not able to handle the error gracefully. Attackers exploit buffer overflows to insert malware into systems. The best protection against a buffer overflow is to keep systems up to date. A phishing attack is sent through e-mail. A salami attack uses multiple small, usually unnoticeable actions, such as shaving a penny off a transaction. Session hijacking attempts to take over a session.
12. D. A successful SQL injection attack can access data in a database. Cross-site scripting injects HTML or JavaScript into a web page and runs the code on a user’s system. A cross-site request forgery attack performs actions on behalf of a user without the user’s knowledge. A rootkit is malware that takes over a user’s system.
13. B. Cross-site scripting (XSS) injects HTML or JavaScript into a web page, and input validation techniques help prevent XSS attacks. The users are prevented from entering HTML or JavaScript tags that start with < and end with >. A SQL injection attack uses SQL code, but SQL code does not use < or > characters. Input validation is a prevention technique, not an attack. A Trojan horse is an application that looks like it’s something useful but is actually something malicious.
14. C. A phishing attack sends an e-mail to multiple recipients impersonating an e-mail from a legitimate company, indicating a problem, urging the recipient to take action, and warning of dire consequences if the recipient doesn’t respond. A sniffing attack uses a protocol analyzer such as Wireshark to capture and analyze traffic. Session hijacking attempts to take over sessions and doesn’t use e-mail. Tailgating is the practice of one person following another into a secure area while only the first person provides credentials.
15. B. Spear phishing is a phishing tactic that targets a specific organization. Phishing doesn’t target individual organizations, but instead casts a wide net, hoping to catch someone. Whaling targets a specific individual, such as an executive. Vishing uses voice methods such as the telephone or VoIP.
16. D. Zero day exploits are attacks that take advantage of vulnerabilities that are unpublished and often include attacks that are unknown by the vendor. The other answers are known methods. Scareware is malware that scares users into thinking their system is infected with a virus and encourages them to install malware on their system. An advanced persistent threat (APT) is a group of people who have the capability and intent to launch extended attacks against organizations. Pharming is an attack that redirects users to bogus websites.
17. C. The most likely cause is an evil twin, which is a type of rogue access point (AP). An attacker likely created a free wireless hotspot in the coffee shop (perhaps on the attacker’s laptop). When the user connected to it, the attacker captured the user’s data, including logon credentials. This is a known attack but a zero day exploit is not widely known. Wi-Fi Protected Setup (WPS) cracking discovers the PIN of an access point and uses it to discover the access point’s password. Wi-Fi Protected Access (WPA) cracking discovers the password on the access point by intercepting the four-way handshake and performing an offline brute-force attack.
18. A. Social engineering uses nontechnical (or low-technical) means to gain information, such as the names of people, e-mail addresses, and user credentials. Shoulder surfing is just looking over someone’s shoulder, and although it may allow an attacker to see an e-mail address of a manager, it isn’t the best answer. Smishing is a variant of phishing using SMS messages. There’s no such thing as covert cramming.
19. B. A mantrap is the best method to prevent tailgating, which is the practice of one person following another into a secure area while only the first person provides credentials. Although education of employees can go a long way, ingrained courtesy sometimes overcomes security practices, and a person may actually open the door for a social engineer. Antivirus software, access controls, and the phone system aren’t related to the social engineering practice of tailgating.
20. B. A primary goal of security awareness training is to change user behavior from unsafe practices to safe practices. It isn’t related to applications such as e-mail, and end users aren’t expected to implement technical solutions.



