CHAPTER 6
Malicious Code and Activity
In this chapter, you will learn about
• Different types of malicious code
• Common ways malware infects systems
• How attackers use remote access tools
• Stages of complex malware infections
• Differences between signature-based and behavior-based detection
• The importance of keeping antivirus signature definitions up to date
• The use of spam filters and content-filtering appliances
• How the principle of least privilege helps minimize infections
• Software security practices such as input validation and code signing
• Educating users about safe computing practices to reduce infections
• The Common Vulnerabilities and Exposures list
Identifying Malicious Code
Malicious code, or malicious software (malware), is any code or software that can be harmful or destructive to computers, networks, or the computing environment as a whole. Some of the common malicious code types include viruses, worms, logic bombs, Trojan horses, and ransomware.
Malware versions that are actively spreading and infecting computers are “in the wild.” In contrast, some researchers have discovered vulnerabilities in systems that attackers could exploit with malware. Researchers sometimes develop proof-of-concept code to demonstrate the potential exploits, but this code remains isolated within lab environments.
Virus
A virus is an application or a piece of code that causes unexpected and usually negative events on computers. Viruses have the ability to infect computers by copying themselves onto the computer using a wide variety of methods. Once the virus is on a computer, it replicates itself and at some point executes its payload, which is the unexpected or malicious event.
One of the key characteristics of a virus is that the infected file must be executed for the virus to run. Typically, this means that a user must run a program to execute the virus. For example, imagine that Bob has an infected game file on his computer. If Bob starts the game, it executes the virus, but if Bob never starts the game, the virus never runs.
Users can execute a virus indirectly too. For example, many systems support an auto-play function, though it is typically disabled on most systems today. If a user inserts a CD, DVD, or USB drive into a system, the system automatically looks for an application and runs it. If this application is infected, the virus runs and can infect the system.
Viruses typically have two primary components:
• Replication component
• Activation component
A virus replicates itself by copying its code onto other applications. When a user runs the infected application, the virus runs and looks for other applications to infect. For example, a virus may wait for a user to insert a USB drive into a system. When the virus detects the USB drive, it copies itself onto a file on the USB drive. Similarly, when a user inserts the USB drive into another system, the virus tries to copy itself onto files on the new system.
At some point, the virus activates and delivers its payload, which is the malicious part of the program. The virus could delete or corrupt data or operating system files. If the virus is part of a botnet, it could check in with a botnet server for instructions. These instructions may be to download and install an additional virus, to send out spam, or even to launch an attack on another system. Chapter 5 discusses botnets in more depth.
Viruses come in many different forms based on what they attack or how they work. The following list isn’t all-inclusive, but it does describe many of the methods and forms of viruses used over the years. It’s worthwhile mentioning that many viruses combine different techniques to make them more difficult to detect.
• Stealth Many viruses try to hide themselves from antivirus (AV) software by providing false or misleading information about the virus to the AV software. For example, a file stealth virus can misreport its actual size so the AV scan thinks the infected file is the same size as the original. Additional methods used by stealth viruses include using armor, polymorphism, or metamorphism. You can compare these techniques to how a stealth aircraft hides itself from traditional radar and infrared detection devices, and remains hidden from enemies.
• Armored An armored virus uses code to make it difficult for AV researchers to reverse-engineer the code. When AV experts detect a virus, they attempt to decompile the code to determine what it does and how it operates. An armored virus uses different techniques to thwart the researchers’ attempts. For example, an armored virus can use a compiler in combination with encryption to make it difficult to reverse-engineer the code. Criminal virus developers often use complex and confusing code designed to hide what the virus is doing, along with encryption as a method of armor. Additionally, virus authors are constantly improving and inventing new armor techniques. An armored virus can also use stealth techniques to make it difficult for AV software to detect it.
• Polymorphic Some viruses can morph or mutate each time they replicate to another machine or even each time they run. Even though the file changes, the code used to replicate and deliver the payload remains the same. For example, by encrypting the file in a slightly different way each time the virus infects another file, it effectively changes the file. However, the virus replication and activation components will still behave in the same way. When the virus mutates, it’s more difficult for AV software to detect it without additional virus signatures that recognize the mutated version. Virus authors use mutation engines to modify the viruses, and some viruses can mutate into thousands of different viruses.
• Metamorphic This is similar to a polymorphic virus, but with a subtle difference. A metamorphic virus actually mutates the code used to replicate and deliver a payload. Although the function is the same, the steps used to do so are different, making the virus more difficult to detect. In contrast, a polymorphic virus will always perform the same steps to achieve the same function, while only the file changes.
• Boot sector The virus is stored on the hard drive’s boot sector and executes when the system is booted. This includes both cold starts and reboots.
• Multipartite A multipartite virus has multiple components. For example, it could combine a boot sector virus with a virus that infects one or more files.
• Macro A macro virus resides in a document such as Microsoft Word, Microsoft Excel, or Adobe Reader. When a user opens the document, it runs the macro launching the virus. Most current versions of applications that support macros restrict their use to prevent the execution of malicious macros.
Worm
A worm travels over the network, looking for systems to infect. Worms are similar to viruses, but they do not require any type of interaction to execute. Instead, they slither and worm through the network on their own. If a worm infects a network, it has the potential to add a significant amount of traffic on the network and can effectively slow legitimate traffic to a crawl.
For example, a graduate student at Cornell University launched the Morris worm (the first known computer worm) in 1988 with the goal of gauging the size of the Internet. It searched for computers and installed itself on each computer it found and then looked for other computers. It often installed itself multiple times on the same computer, consuming resources, and eventually making the computer unusable. It resulted in estimated damages between $10 million and $100 million and prompted the creation of the first Computer Emergency Response Team (CERT) at Carnegie Mellon University.
Worms use protocols to travel over a network. For example, a worm can use TCP/IP to discover computers on the network, access network shares, and then use file transfer protocols such as FTP and TFTP to copy files and infect the target computers. The ability of worms to travel over a network provides additional justification for a defense in depth strategy that includes the following components:
• Host-based firewalls on all systems
• Up-to-date AV software on all computers
• Reduced attack surface by removing unneeded protocols
Trojan Horse
A Trojan horse is an application that looks like it’s one thing but is actually something different. It presents itself as a useful or legitimate program, but includes a malicious component.
Its name comes from the Greek story of the nine-year Trojan War. Greek soldiers burned their camp and sailed away after leaving a large wooden horse in front of the gates of Troy. The residents of Troy thought the war was over and thought the horse (a sacred animal to them) was a gift. They ultimately rolled the wooden horse into their otherwise secure city and celebrated their good fortune. However, soldiers hid inside the wooden horse and the rest of the Greek army was poised to return. The soldiers emerged in the middle of the night, killed the guards, and opened the gates to the city, letting the rest of their army in. The Greeks sacked the city, ending the Trojan War. It’s a simple message I learned from a mentor who taught me how to play chess many years ago: “beware of gifts.”
As an example of a Trojan horse, one attack sent tens of thousands of e-mails to users that looked like it came from CNN and listed several titles of recent news stories. Users who clicked any of the titles opened a website page that popped up a small window. The window indicated that the user’s system didn’t have the current version of Adobe’s Flash Player, so the page couldn’t display the news story. It then prompted the user to install the current version. However, if the user clicked Yes to install the new version of Flash, it actually installed malware instead.
Variants of this attack continue. Users receive an e-mail with one or more links. If the user clicks a link, they are taken to a website and prompted to install an updated version of software, or an application under a false pretense. If the user agrees, the site downloads the malware to the user’s system and encourages the user to install it.
RATs
A remote access Trojan or remote access tool (RAT) provides an attacker with control over a target computer via the Internet. Many Trojans install RATs, and then attackers can use the RAT to do anything on the target computer. This includes using the RAT to install malware, install keyloggers, and join the compromised computer to a botnet.
Many advanced persistent threats (APTs) use RATs to gain a foothold into a network. After infecting one system, they use various techniques to gather data about other systems on the network. Chapter 5 discusses APTs in more depth.
Scareware
Scareware (sometimes called rogueware) is malware that describes itself as antivirus software. A user may visit a website and then see a pop-up similar to that shown in Figure 6-1, which indicates that a virus has infected the user’s system. However, every user who visits the website will see the exact same message. The website hasn’t truly detected a virus. Instead, the pop-up attempts to trick the user into installing malicious software on their system.
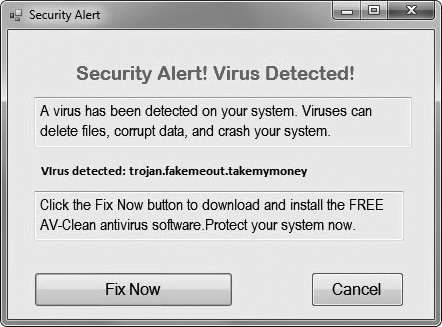
Figure 6-1 Scareware pop-up trying to trick a user into installing malware
If the user clicks the Fix Now button, it prompts the user to download and install the bogus antivirus application. After installing and running it, the bogus software indicates it is checking the user’s system, but it’s all a show. Unlike actual antivirus software that truly scans a system to look for malware, scareware does not look for malware. However, it always reports that it has discovered multiple instances of malware on the user’s system. It then informs the user that the free trial edition only scans their system. The user must pay to purchase the full version to remove the malware.
Although the extortionary nature of scareware is malicious enough by itself, most scareware applications do more. For example, the downloaded application could join the system to a botnet controlled by a criminal. It could download and install a remote access tool that allows a criminal to take control of the user’s computer, or install a keylogger to capture all of the user’s keystrokes and send the data off to an attacker to use later. The possibilities are limited only by the imagination and technical abilities of the scareware authors. History shows us that they have a lot of imagination when it comes to stealing money from victims, and their technical abilities continue to increase.
What should a user do after seeing a pop-up window like this? Close the pop-up window and leave the site. Users who don’t have antivirus software installed should go directly to a reputable site to get it, and not try to install it from one of these warnings. Many brands of antivirus software are available, and some reputable companies offer free versions.
Ransomware
Ransomware is a type of Trojan that takes control of the user’s computer or data and then demands a ransom from the user to get control back. There are many variants, but there are two primary themes. One type locks you out of your computer, preventing you from logging on. Another type encrypts your data files, allowing you to log on but preventing you from accessing any of your data.
The “Mandiant U.S.A. Cyber Security Ransomware” is an example of ransomware that locks you out of your computer. When users turn on an infected system, it displays a bogus but official-looking screen that indicates it’s a joint effort between Mandiant Cyber Security, the U.S. FBI, the U.S. Department of Defense, and the U.S. Cyber Crime Center. Variants (known as the Police Virus, Trojan Reveton, and MoneyPak Virus) replace the names of U.S. agencies with those of agencies in other countries, such as the International Criminal Police Organization (Interpol). This type of malware isn’t a joint effort with any official agencies. Instead, it’s an attempt by criminals to extort money from users.
The ransomware message accuses the user of participating in illegal activity such as distribution of pornography, copyrighted files, or malware. It then demands that the user pay a fine of $300 (or some other amount) within 48 hours or they will face legal prosecution. The software directs users to purchase a MoneyPak or MoneyGram voucher at a store such as Kmart or Walgreens. They enter the voucher code into the ransomware screen to pay the attackers, which unlocks their computer.
CryptoLocker is an example of ransomware that encrypts user files. When it infects the user’s system, it locates and encrypts data files on the user’s system, attached USB drives, external hard drives, shared network drives, and sometimes cloud storage drives. It then demands payment of $300 (or more) to get the decryption key. The message indicates that if the user doesn’t pay within 72 hours, the attackers will delete the decryption key, causing the user to lose the files forever. Attackers sometimes offer to retrieve the decryption key after the time limit has expired, but at a much steeper price as high as $2,300. Victims paid approximately $30 million between September and December 2013.
Police forces disrupted the network running the original CryptoLocker ransomware in June 2014. However, CryptoLocker and many variants began appearing soon afterward. TorrentLocker is similar and often uses the CryptoLocker name, but the underlying code is different. The FBI is offering a $3 million reward for information leading to the arrest or capture of a Russian man (Evgeniy Mikhailovich Bogachev) who they believe is the ringleader of the gang that ran the original CryptoLocker network.
Law enforcement agencies discourage victims from paying ransom. First, there’s no guarantee that the criminals will release the user’s computer or data, and there are many examples where they didn’t, or asked for more money. Second, as long as criminals receive money from these attacks, there’s no reason for them to stop.
Attackers released the WannaCry ransomware attack in 2017, infecting more than 200,000 computers in 150 countries in just four days, and more than 300,000 systems in total. It demanded a payment of $300 within three days or $600 within seven days. Government agencies in the United States, United Kingdom, and Australia concluded that North Korea was behind the attack. If true, it was likely an APT working in and for North Korea.
Notice that each of these ransomware attacks includes a sense of urgency. The Mandiant virus states that users will be prosecuted if they don’t pay the fine within 48 hours. CryptoLocker states that attackers will delete the decryption key if users don’t pay the ransom within 72 hours. WannaCry doubled the ransom if the user didn’t pay within three days. Ransomware typically includes a timer that counts down as a constant reminder to the user to take action.
Keylogger
A keylogger (also known as a keystroke logger) is a tool that can capture all the keystrokes that users enter on a computer. Keyloggers can be hardware based or software based. A hardware-based keylogger plugs into the computer between the keyboard and the computer and captures the data. For example, if the keyboard plugs into a USB slot, you would plug a USB-keylogger into the USB slot, and then plug the keyboard into the USB-keylogger. It could transmit the information wirelessly or store the data on the hardware.
Software-based keyloggers are more common. They simply run as an additional piece of software when the computer starts. For example, some parents use keyloggers to monitor children’s computer activity. Keyloggers can monitor online chats, instant message content, e-mails, and data entered into Internet website forms. Many keyloggers also include the ability to capture screenshots. These same tools are available for employers to monitor employee activities.
Of course, criminals use the same type of keylogger software to capture information entered by users. Users don’t knowingly install the keylogger. Instead, another infection such as a Trojan horse installs the keylogger.
Logic Bomb
A logic bomb is malicious code that executes in response to an event such as a point in time or in response to specific actions. For example, Chapter 5 mentioned the attempted attack on Fannie Mae by a terminated administrator. After his employer terminated him from the job, he added a script that was set to run on January 31 that would have deleted passwords, data, and backups for about 4,000 servers. This is a logic bomb because it was set to run on a specific date.
Some keyloggers have a logic bomb component. They send data to an attacker after a user accesses specific websites, such as banking sites. For example, when the keylogger detects that the user accessed mybank.com and entered a username and password, the keylogger e-mails the URL and credentials to an attacker.
Rootkits
A rootkit is a set of programs that can run on a system largely undetected. It has root-level access to the system, similar to how a root-level administrator has full and complete control over a system. Attackers can often control the computer remotely after installing a rootkit, and the user typically doesn’t notice any symptoms.
Rootkits have low-level control on systems, which allows them to identify when antivirus software is running. The rootkit can detect a system scan and hide itself from the scan or restrict the data returned to the scan. This has made rootkit detection difficult for traditional AV software. However, it’s worth noting that attackers typically install rootkits via a virus or a Trojan. In other words, if you can detect and prevent attackers from installing viruses and Trojans on your system, you have a good chance at preventing them from installing rootkits.
Several companies have released rootkit detectors. For example, Sophos has released and updated a free dedicated tool designed to detect and remove rootkits from systems. If interested, you can read about it here: www.sophos.com/en-us/products/free-tools/sophos-anti-rootkit.aspx. Additionally, most popular AV programs advertise their ability to detect and remove rootkits. This typically requires rebooting the system from a CD or bootable USB with antivirus software to detect the rootkit and clean the system.
Mobile Code
Mobile code is any code that can transfer itself between systems without the user taking explicit action to install it. Attackers use malicious mobile code to install malware from remote servers via the Internet. Malicious mobile code is typically transmitted via interactive web applications. Some examples of mobile code include the following:
• Scripts such as JavaScript or VBScript Attackers embed the script into a web page, or within any file, that supports the script. When users click a link to retrieve a web page, the web server sends the page along with the embedded script. As the web browser displays the web page, it also runs the script. Some Hypertext Markup Language (HTML)-based e-mail applications support the use of scripts, so opening an e-mail can launch the script. Similarly, files such as Portable Document Format (PDF) documents and Microsoft Office documents support scripts. Attackers embed the code into these documents, which executes when the user opens the document. While keeping systems and applications patched with security updates protects against most of these threats, many users don’t keep their systems patched.
• Java applets or ActiveX controls Java applets and ActiveX controls are mini programs that developers embed into web pages. Similar to scripts, they run when the web browser displays the web page. A primary method of protection is to block unsigned applets and controls. Using code signing (as discussed in Chapter 5) is one method that developers use to show their code is valid and provides assurances to users that the code is valid.
• Documents that include macros Many document types (such as Microsoft Office documents) support macros. While macros can be very helpful, an attacker can write malicious mobile code into a macro. When a user opens the file, it runs the macro. To reduce this risk, it’s common to disable macros in applications that support them.
Backdoors and Trapdoors
A trapdoor or backdoor is code that is embedded in an application and provides access to the application, the application’s code, or data via a covert method. Some backdoors provide access to the operating system.
Application developers often add backdoor code to an application for debugging purposes. For example, by entering specific keystrokes, they can display the value of variables within a running application. Although this is useful during the debugging process, a backdoor can be dangerous if developers leave it in the released version of the application. Instead, as a best practice, most developers remove all backdoor code prior to releasing the application.
Attackers often attempt to install a backdoor after infecting a system with a virus or Trojan. When successful, attackers can use backdoors to read data, install additional malware, or even take control of the user’s computer from a remote location. Within the context of malicious code, both backdoors and trapdoors mean the same thing, although the term backdoor is more common.
Some attackers have successfully added backdoor code to released applications. For example, the Mydoom worm installed a backdoor that affected versions of Microsoft Windows and allowed attackers to control the infected computers remotely over the Internet. As with most other malware, after security experts discovered the vulnerability, the vendor (Microsoft in this example) wrote and released security updates to protect systems from the threat.
Another example is the Win32/Zbot (also called GameOver Zeus or simply Zeus) family of password-stealing Trojan horses. This is also a good example of a multipartite virus with backdoor functionality. Win32/Zbot tricked users into installing the Trojan onto their systems, and then joined their computers to a botnet. Interestingly, infected systems don’t join a single huge botnet, but instead join one of many independently operated botnets. The attacker controlling the command and control center for each of these botnets then controls these infected systems through the botnet’s backdoor.
Win32/Zbot successfully used a variety of techniques to steal financial-related information such as usernames and passwords. For example, it interfaced directly with web browsers to monitor traffic and information. The Trojan deleted cookies for websites, forcing users to reenter their credentials. It injected additional HTML code into banking website pages, requesting additional information from users such as Social Security numbers or birthdays. Win32/Zbot then encrypted this information and sent it to attackers controlling the botnet. Criminals logged on to the victim accounts with the stolen credentials and transferred funds to other bank accounts controlled by the criminals.
Spyware
Spyware is software that can install itself on a user’s system without the user’s knowledge or consent. Although there was a time when spyware was relatively benign, it is much more dangerous today. For example, there was a time when spyware attempted simply to understand a user’s surfing or buying habits so that it could send targeted advertisements to the user. However, spyware today is much more malicious and attempts to learn details to steal financial data, logon information, or a person’s identity.
Most security experts consider spyware a form of malware because it can cause so much damage to an individual. Many spyware applications can identify websites that a user visits, usernames and passwords that a user enters, user’s keystrokes even when not visiting a website, and even search a user’s computer for information such as files including usernames and passwords. Spyware can also change settings on a user’s system, such as settings to enable or disable a firewall, settings to enable or disable automatic updates for the operating system, or even settings for individual applications.
Due to the malicious nature of spyware today, most AV software includes the ability to search for and detect it. Years ago, many users used one application for spyware and another application for viruses and other malware. However, if a user gets an AV application that includes a spyware component, it isn’t necessary to install a separate spyware application.
Malware Hoaxes
In its simplest terms, a malware hoax is a false message about a malware risk that doesn’t exist. Attackers and uneducated users typically spread hoaxes through e-mail while urging other users to forward it to everyone they know. Many times these e-mails encourage users to take action that can harm their system.
Hoaxes commonly include a sense of urgency and often overuse capital letters and exclamation marks, with subject lines featuring something like “URGENT!!!,” “WARNING!!!,” or “VIRUS ALERT!!!” In contrast, legitimate warnings (such as those from a cyber security alert service or from an organization’s administrator) simply provide the detailed information without stimulating emotion or fear.
In general, hoaxes just waste people’s time. When users forward it to everyone they know, they perpetuate the hoax, along with consuming more bandwidth and wasting other people’s time. Many organizations provide training to users so that they don’t forward e-mail warnings to everyone. Instead, users are encouraged to forward these types of e-mails to system administrators if they think it represents a real threat. Although this adds to the administrator’s workload, it’s better than spamming the rest of the organization.
Analyzing the Stages of an Attack
While the previous descriptions of malicious code describe individual components of malware, they really don’t paint the full picture of malware threats. Symantec released a white paper titled “Regin: Top-Tier Espionage Tool Enables Stealthy Surveillance” that describes the complexity behind some attacks that start with a serious malware threat. While the white paper (and the summary provided in this section) describes Regin, other attacks use similar complex methods to capture data after infecting a system. The ultimate goal of Regin is to collect data, and it does so through several different methods, including using Trojan RAT features, capturing screenshots of user computers, taking control of the mouse, stealing passwords, monitoring network traffic, retrieving deleted files, and collecting e-mail.
Regin 1.0 has been around since at least 2008, and Regin 2.0 has been used since at least 2013. This speaks to the technical sophistication of the attackers. Developers aren’t teenage script kiddies doing random attacks. Rather, the developers appear to be a cohesive team with specific goals of monitoring targets and stealing data. There are six distinct stages to Regin, as shown in Figure 6-2 and described in the following list:
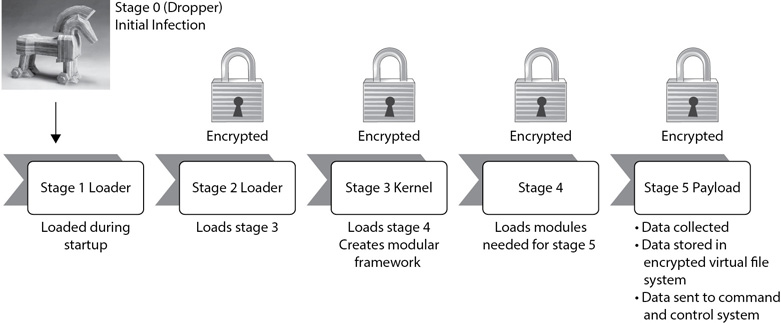
Figure 6-2 Regin stages
• Stage 0 A dropper is a type of Trojan horse that attempts to drop malware onto a computer. Within Regin, stage 0 is the dropper stage and represents the initial infection. It could be from the user opening an infected file in an e-mail, clicking a malicious link in an e-mail, or any other way users inadvertently install Trojans. Stage 0 installs and executes stage 1 files. In many cases, stage 0 code is only stored in memory and disappears after stage 1 starts.
• Stage 1 This stage loads operating system kernel drivers when the computer starts. These drivers decrypt, load, and execute stage 2. Two known names for these files are subclass.sys and adpu160.sys for version 1 and version 2, respectively. Stage 1 is the only stage that includes plainly visible code on the attacked computer. Regin encrypts stages 2, 3, 4, and 5 and stores them in files, or within nontraditional areas such as the registry, or within raw sectors of the disk drive. As mentioned previously, encryption is a method of armoring the virus to prevent AV researchers from decompiling and analyzing the code.
• Stage 2 This stage loads another operating system kernel that decrypts, installs, and runs stage 3. Regin stores encrypted data for this stage within an NTFS extended attribute, or in some cases within one or more registry subkeys. This stage often hides running instances of stage 1, removing any plainly visible elements of Regin.
• Stage 3 This stage decrypts, installs, and runs stage 4 files and provides a modular framework for stages 3, 4, 5, and 6, consisting of hundreds of programmatic methods. These modules provide a wide range of functions such as compression and decompression routines, encryption and decryption routines, an encrypted virtual file system, and networking routines to send data to the attacker. Stage 3 is about six times larger than stage 2.
• Stage 4 Stage 4 loads the relevant modules needed for stage 5 depending on the targeted payloads. Because Regin includes so many different modules, attackers can modify it to collect custom payloads. For example, one implementation might collect e-mail, another implementation might install a RAT, and so on. Note that this isn’t a different version of Regin, but instead, the attacker just enables different features of Regin by implementing different modules.
• Stage 5 Stage 5 collects data from a variety of sources and stores that data within the encrypted virtual file system. It can collect network data, passwords, computer files, deleted files, and screenshots. Stage 5 sends data to the attackers via one of several standard protocols, using special flags for identification.
While these six stages occur automatically after the initial infection, Regin also supports command and control operations similar to a traditional botnet. Attackers can contact the computer periodically and instruct it to send data. This often occurs using two stages. For example, the attacker might send an Internet Control Message Protocol (ICMP) datagram with instructions to send collected data to a specific server. The infected computer then responds with the payload using User Datagram Protocol (UDP) datagrams. Regin encrypts all data before sending it to the command and control computer.
Understanding Malware Delivery Methods
Attackers deliver malware through multiple methods. While most malware is delivered via the Internet, it can also be delivered from hardware devices such as USB drives. When end users understand how malware spreads, they are less likely to be tricked into installing malware on their systems.
Delivering Malware via Drive-by Downloads
In a drive-by download, web servers include malicious code that attempts to download and install itself on user computers when the users visit. These drive-by downloads can include many different types of malware, such as installing a RAT or joining a computer to a botnet.
Criminals rarely host these computers themselves because that would make it easier for law enforcement to find them. Instead, they look for vulnerable computers that they can modify to include the drive-by downloads. As an example, attackers might look for an unpatched server with a known vulnerability. If the vulnerability allows the attackers remote access to the server, they can use this access to install malicious code.
Here are the typical steps involved in a drive-by download, depicted in Figure 6-3:

Figure 6-3 Drive-by download installing malware
1. Attackers compromise a website to gain control of it.
2. Attackers install a Trojan or other malware embedded in the website’s code.
3. Attackers attempt to trick users into visiting the site. Sometimes, they simply send the link to thousands of users via e-mail, hoping that some of them click the link. Other times the link is from another website or a malicious banner ad.
4. When users visit, the website attempts to download the Trojan or malware onto the user’s system.
Users can prevent successful drive-by downloads by keeping their systems up to date with operating system and application updates and with up-to-date antivirus software. This will prevent most infections, but it won’t prevent zero day exploits, so users still need to be vigilant. A zero day exploit is an attack that takes advantage of unpublished vulnerabilities that vendors either haven’t heard about or haven’t published updates for yet.
Many drive-by downloads prompt the user to complete the installation, and they won’t complete without the user’s permission. As an example, the “Trojan Horse” section earlier in this chapter mentioned how one attack prompted users to install an update to the Adobe Flash Player. If they agreed, it installed malware. Users should be encouraged to only install updates to applications from the site publishing the application. In other words, when updating Adobe Flash Player, users should get the update from a verified Adobe site.
Delivering Malware via Malvertising
Attackers sometimes deliver malware via malicious banner ads, commonly called malvertising. These look like regular ads, but they contain malicious code. Many of them include a link taking users to a server hosting a drive-by download. Others are Flash applets with malicious code embedded in them.
Malvertising has appeared on mainstream websites such as those belonging to The New York Times and Yahoo!. As an example, ads hosted on Yahoo! in 2013 and 2014 took users to sites hosting scareware. They included fake pop-ups as described in the “Scareware” section earlier in this chapter. In mid-2014, ads on Yahoo! took users to Eastern European sites hosting CryptoWall ransomware, a clone of CryptoLocker.
It’s worth noting that legitimate sites are not knowingly hosting these malvertisements. Instead, they sell ad space to advertising companies and these advertising companies unknowingly send the malicious ads to the legitimate sites. In some cases, criminals trick legitimate advertising companies into hosting the ads. For example, social engineers tricked people at the Gawker Media network to sell fake Suzuki advertisements. In other cases, attackers compromise websites and post their own malicious ads on the websites.
Attackers often use exploit kits, such as Magnitude EK, to create malicious advertisements. In 2017, attackers began using Magnitude EK to inject scripts into advertisements on vulnerable servers. When a user clicks a malicious advertisement, the script redirects them to a malicious server hosting malware such as ransomware. In many cases, users are quickly redirected to the site a user would expect after clicking the ad. This happens while the server is downloading the malware.
Delivering Malware via E-mail
One of the most popular methods of delivering malware is via e-mail. Chapter 5 discusses spam, botnets, and various types of phishing attacks. As a reminder, criminals control hundreds of thousands of compromised systems in botnets and they rent these botnets out to other criminals who use them to send phishing e-mails.
While some phishing e-mails attempt to trick users into giving up personal information such as their credentials for a banking site, other e-mails try to install malware on the user system.
One method includes infected attachments. If users open the attachment, it can infect the user’s system. Attachments arrive as ZIP files, PDF documents, web pages (as HTML files), apparent graphics such as JPG files, and more. One way they disguise these documents is to simulate the extension of a safe file. For example, a JPG graphic file has a .jpg extension, such as picture.jpg. An attacker can rename an executable file to picture.jpg.exe. Because the operating system normally hides the extension, the file looks like picture.jpg, indicating it’s a relatively safe JPG file.
It’s worth noting that attackers often spoof or modify the From e-mail address to make it look like it’s from someone the recipient knows. For example, attackers monitor social media sites and identify your friends. They then send an e-mail to you but change the From field so that it looks like it came from your friend. This tricks some users into trusting the e-mail and makes them more willing to download an attachment or click a link.
Delivering Malware via USB Drives
As mentioned earlier in this chapter, some viruses replicate via USB drives. An infected USB drive will try to infect a computer system when a user inserts it. An infected system waits for a user to insert a USB drive and attempts to infect the drive.
When an organization allows users to transport data back and forth from home and work using USB drives, it becomes very easy for a user to transport viruses from home and work. Although an organization can implement multiple methods to protect its environment from malware, the organization usually has no control over a user’s home network. If users are authorized to use USB drives, it’s imperative that each system has AV software installed and kept up to date. Some organizations use additional methods to prevent systems from reading data from a USB drive, writing to a USB drive (to prevent data theft), or both.
Implementing Malicious Code Countermeasures
Because malware is so prevalent, it’s important to protect systems from malware. The primary method of protection is antivirus software and an aggressive defense in depth strategy. As an overview, the following methods are effective countermeasures against malware:
• Install antivirus software on all systems.
• Install antivirus and antispam software on e-mail servers.
• Install antivirus and content-filtering software on firewalls.
• Keep all antivirus and antispam software up to date.
• Perform regular antivirus and vulnerability scans.
• Keep all systems up to date.
• Educate users.
Antivirus Software
The primary method used to detect and prevent infections is the use of AV software. In addition to being able to detect and prevent infections, AV software can remove the malware, restore infected files, or quarantine infected files if the AV software can’t remove the malware. The goal is to ensure that the malware cannot run and cause any more problems on a system. Researchers can examine and analyze quarantined files. However, the computer will not run quarantined files.
Figure 6-4 shows an example of antivirus software. It includes the ability to perform on-demand scanning (shown as Scan Your PC in Figure 6-4), real-time scanning, and scheduled scanning:
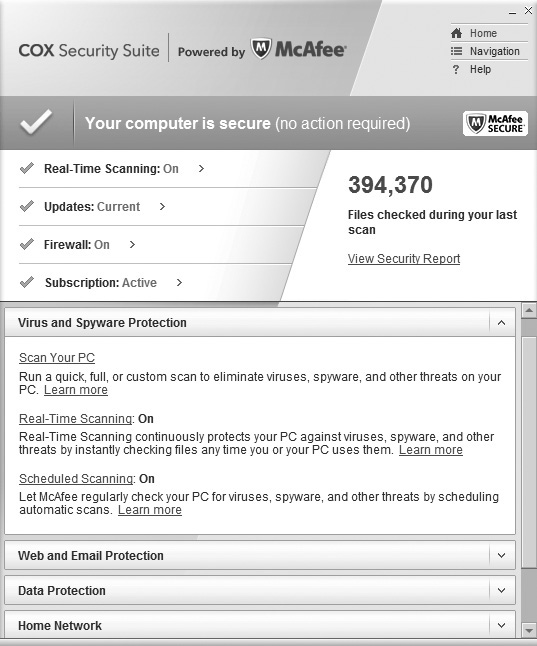
Figure 6-4 Antivirus software
• Real-time scanning This provides protection as the user opens and uses files. For example, if a user opens an e-mail attachment, the AV software checks it to ensure that it doesn’t have any malicious content. Real-time scanning checks any file that is opened or launched by either a user or the operating system.
• On-demand scanning If you suspect a computer is infected, you can perform an on-demand scan to check it. Most AV software allows you to run a scan to check memory, specific files, folders, or drives, or complete a full scan of the entire system. Figure 6-5 shows an on-demand scan in progress on a system.
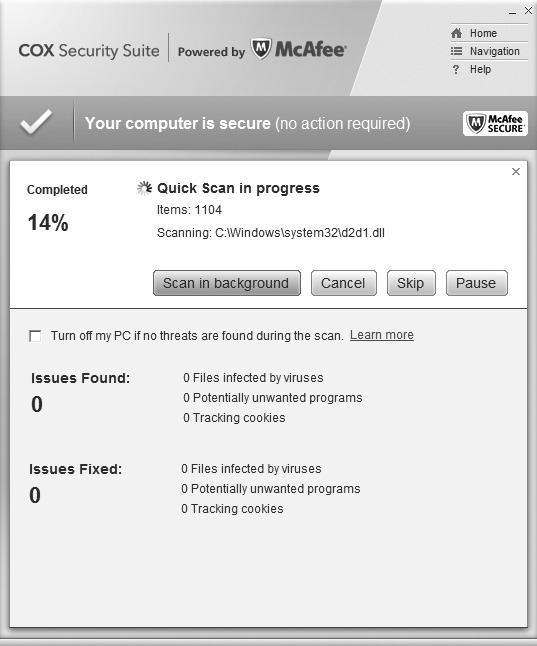
Figure 6-5 Performing an on-demand scan
• Scheduled scanning A scheduled scan occurs on a regular basis, such as once a week. Once scheduled, the AV software launches the scan based on the schedule.
Antivirus software uses a software engine to detect viruses using virus signatures. Additionally, some antivirus software uses behavior-based (sometimes called heuristic) scanning. The following sections describe both methods.
Signature-based Detection
Viruses have specific characteristics that AV software uses to identify them. The signature can be a unique characteristic such as a specific byte pattern within the virus. This is similar to how a person’s fingerprint can uniquely identify an individual. Viruses in files, memory, and a drive’s boot sector all have specific signatures that AV software uses to detect them.
When AV researchers discover malicious software, they identify its signature. AV companies add this signature definition to the AV signature database, which the AV software uses to detect the malware. When the AV software finds a file that matches a signature in the database, it alerts the user and often prompts the user to remove, repair, or quarantine the file.
You may remember from earlier in the chapter that polymorphic and metamorphic viruses change. A primary goal of attackers using these techniques is to prevent detection of the virus through signatures. Additionally, attackers have developed application tools that allow them to create new iterations of viruses rather easily. For example, the attacker can write the replication and activation component to create the core virus. The attacker can then run the virus through another application to create hundreds of different versions of the same virus. Some applications can generate as many as 500 different variants of a virus in a single month. AV software might have a signature of the original virus, but this signature is unlikely to detect all 500 variants of the virus.
Many AV developers have moved to fuzzy hashing techniques to identify malware variants. Fuzzy hashing techniques compare two different items and determine a level of similarity between the two. While fuzzy hashing might not detect all variants of a known virus, it does detect many of them.
Of course, as viruses morph to a state that prevents detection, AV researchers create signatures to detect the new variants. If users ensure their AV signature files are updated regularly, the AV software will discover these new variants. However, if users don’t update the virus signatures regularly, the new variants may run undetected.
Behavior-based Detection
Attackers release new viruses into the Internet regularly, and older viruses are regularly mutating into variants. Because of this, it’s entirely possible that at any time, a system will come across a previously unknown virus. This means that the AV software doesn’t have a signature for the new virus. However, behavior-based detection can often detect these previously unknown viruses.
Behavior-based detection (sometimes called heuristic-based detection) attempts to detect a virus based on its behavior. In other words, if a file is behaving in a way that is not typical for a file, the heuristic engine can detect this behavior, identity the file as malware, and block the malware from infecting the system. For example, legitimate applications rarely modify, copy, or delete system files. If an application does attempt to take one of these actions, the heuristic engine can detect and block it.
Many behavior-based scanners use a sandboxing technique, which relies on an isolated or confined area of memory on the system. The AV software ensures that new or modified applications run within an isolated sandbox for analysis before allowing them to run regularly. The idea is that the application can play within its own sandbox, but it can’t interfere with applications or processes in other sandboxes or other areas of memory. The scanner observes the behavior of the application as it runs within the sandbox. If it doesn’t display any suspicious activity, the AV software allows it to run.
Keeping AV Signatures Up to Date
An important element of using AV software is to keep the signature definitions up to date. Because viruses can morph so quickly, most AV software includes the ability to check automatically for new signatures, and they do so once a day and sometimes as often as once every hour. Users only need to ensure that the AV software is set to download and install the updates automatically. If the AV software is not up to date with current signature definitions, systems quickly become more vulnerable to new attacks.
Users often don’t understand the risks and the importance of updating signature definitions, so many organizations typically take control of this step. For example, some AV vendors sell server products where a central server can deploy both AV software and updates to all the clients within an organization. Administrators ensure the central server downloads the updates from the vendor site and then deploys the updates to clients within the organization. Many times these updates include more than new signature definitions. They can also upgrade and improve the antimalware application.
Spam Filters
Because attackers often deliver malware and malicious links via spam, a spam filter can provide an important layer of protection. A spam filter attempts to detect unsolicited e-mail and block it. Many e-mail servers include antispam software to filter spam. Additionally, many e-mail applications include antispam software to filter spam.
A danger of a spam filter is blocking legitimate e-mail. For example, a company that sells products and communicates to customers via e-mail doesn’t want to block legitimate queries from customers. Because of this, most spam filters have low thresholds for spam. Given the choice of accepting some spam but never blocking legitimate e-mail, or blocking more spam but occasionally blocking legitimate e-mail, most organizations choose the former. They’ll allow some spam to get through but do not want to block any legitimate e-mail.
Three technologies that have helped reduce spam are Sender Policy Framework (SPF), Domain Keys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC).
Sender Policy Framework
Sender Policy Framework (SPF) records provide a method to reduce spam by identifying spoofed e-mail. SPF records identify e-mail servers authorized to send out e-mail for a domain. For example, McGraw-Hill Education can publish an SPF record to DNS servers on the Internet that identifies the mail.mheducation.com server as the only authorized server to send out e-mail for the mheducation.com domain. Spammers sometimes spoof the source address, but the e-mail header still shows the server that sent the e-mail.
E-mail servers that receive e-mail can use SPF records to validate e-mail. When an e-mail server receives e-mail that appears to come from McGraw-Hill Education, it can check what server actually sent it and compare it to the public SPF record. If a different server sent the e-mail (not one identified in the SPF record), the receiving server marks the e-mail as spoofed. The server can then block all spoofed e-mail from this server to reduce spam levels. RFC 7208 formally defines SPF and it is currently listed as a proposed standard.
Domain Keys Identified Mail (DKIM)
Domain Keys Identified Mail (DKIM) uses digital signatures to authenticate e-mails. Chapter 14 covers digital signatures in more depth, but in short, DKIM uses a certificate to provide authentication, integrity, and nonrepudiation. The sending e-mail server attaches a digital signature to outgoing e-mail. The receiving e-mail server uses the digital signature to verify the e-mail has been sent by the sending e-mail server.
Domain-based Message Authentication, Reporting, and Conformance
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is an extension of both SPF and DKIM. It allows owners of a domain to publish a policy that identifies if they are using SPF, DKIM, or both. Administrators of receiving e-mail servers can use this policy to validate incoming e-mail. DMARC is documented in RFC 7489.
Content-filtering Appliances
A content-filtering appliance is a device that filters traffic in and out of a network. It actively monitors data streams by inspecting datagrams, searching for malicious code or malicious behavior. Figure 6-6 shows the overall concept. You install the device so that all traffic going to or from the Internet goes through the device. Basic content-filtering appliances filter malware and spam. More advanced appliances can act as firewalls, proxy servers, and intrusion detection systems. Notice that both malware and spam enter the appliance, but the device can block malware and spam, preventing it from getting into the internal network.
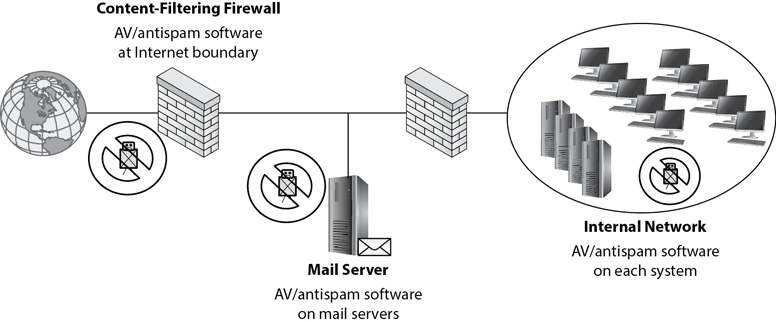
Figure 6-6 Content-filtering appliances
Similar to kitchen appliances, content-filtering appliances are rather easy to plug in and use. Think of a microwave kitchen appliance. It certainly has a lot of complexity within it, but all you have to do is plug it in, put your food in, punch some buttons, and in almost no time, you’ll be enjoying a hot meal. You don’t need to understand how the microwave works to enjoy its benefits. Similarly, an administrator doesn’t have to understand the complexity of the content-filtering appliance to use it and enjoy its benefits.
Most content-filtering appliances include additional features and capabilities that administrators can adjust. For example, if the organization uses it as a proxy server, it checks the validity of website certificates and blocks sites that fail these checks. It can also filter URLs, controlling what websites users can visit.
Figure 6-6 also shows a defense in depth strategy to protect against malware by installing AV/antispam software at the boundary, on a mail server, and on all internal clients. Installing AV software in so many places might seem like overkill. After all, if most malware reaches systems via the Internet and e-mail, the content-filtering firewall and antivirus software on the mail server should catch it. Ideally, this is true. However, users can also inadvertently install malware via USB drives just by inserting the USB drive into their system. Additionally, zero day exploits might get past the content-filtering firewall and/or the mail server. AV software on the systems might be able to detect this malware using behavior-based detection methods. Together, these methods provide a defense in depth solution to protect against malware.
Keeping Operating Systems Up to Date
It’s also important to keep operating systems up to date. Malware often exploits software bugs or vulnerabilities in a system, and as long as the bug remains, the system is vulnerable. On the other hand, updated systems are not vulnerable to these bugs.
Vendors regularly write, test, and release patches for known vulnerabilities. For example, Microsoft releases patches on the second Tuesday of every month. The goal is to allow administrators time to plan for testing and installation of these patches on a regular basis. Although Microsoft does occasionally release patches for emerging threats outside of this schedule (out-of-band releases), these releases are relatively rare.
Chapter 9 talks about hardening systems, or making them more secure from their default configuration. Keeping systems up to date is a key part of hardening a system.
Scanners
Chapter 8 covers vulnerability scanners in more depth, but in short, vulnerability scanners can check systems for vulnerabilities and report their findings. Some common vulnerability scanners used by security professionals include Nessus, Nmap, and SAINT (Security Administrator’s Integrated Network Tool).
Vulnerability scanners can check systems to verify that the operating system is up to date, has up-to-date antivirus software, and has an enabled firewall. A vulnerability scanner can also verify that the systems are not running certain services and protocols, depending on how the administrator configures the scanner.
Beware of Shortened Links
It used to be that you could easily spot malicious links in e-mails. For example, if you saw a link claiming to be from mheducation.com, you could hover over it to see the actual link was www.hackers.ru. In this case, clicking the link would not take you to mheducation.com but instead would take you to a Russian website (because the ru top-level domain is in Russia).
As an example, Figure 6-7 shows an HTML-based web mail with the user hovering over the second link. Although the link appears to be mheducation.com, if you look in the status bar at the bottom of the browser, you can see the actual link is http://www.hackers.ru. Many e-mail programs allow the user to hover over the e-mail in the same way and see the actual link as a tool tip.
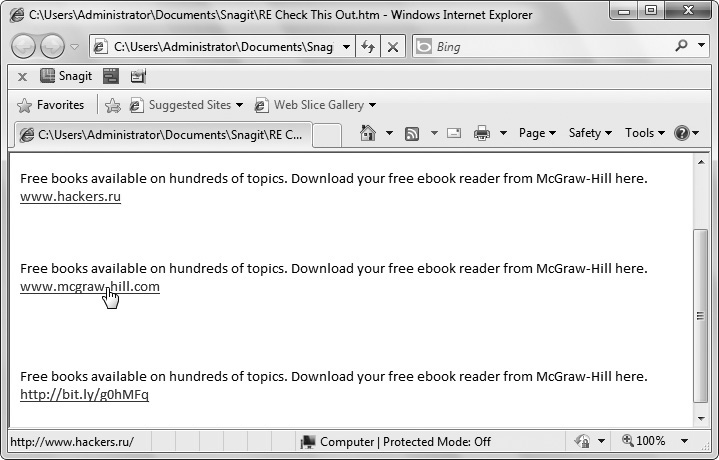
Figure 6-7 Embedding links in an e-mail
To prevent users from seeing the link, attackers sometimes use shortened URLs to mask the actual destination, as shown in the third link in Figure 6-7. Legitimate users also shorten very long URLs with tools such as Bitly (https://bitly.com) or TinyURL (https://tinyurl.com). As an example, you can go to the Bitly website, plug in a long URL, and it gives you a short one.
Now, when a user clicks the bit.ly link, it takes the user to the actual long link. Although this is useful (especially for 140- or 280-character tweets), attackers have used shortened links for attacks. End users don’t know where this link takes them until they click the link. By that point, it may be too late.
Some tools are available to expand URLs. For example, URL Expander (http://urlex.org) allows you to plug in a shortened URL and it expands it to a long URL. Users can copy the shortened URL from their e-mail or from a tweet and paste it into the text box on the http://urlex.org page.
As an example, you can use Bitly to shorten the URL of McGraw-Hill Education (https://www.mheducation.com/). The result is https://bit.ly/2Fwm4Lz (though it might be different if you do this at a different time). You can then go to http://urlex.org and plug in the shortened URL. Click Expand and it shows you that the expanded URL is https://www.mheducation.com/.
Sandboxing
As mentioned previously, behavior-based antivirus software sometimes uses a sandboxing technique. It runs new or untested code within an isolated environment. If the code is malicious, the code is unable to infect other applications or other areas of the system. Real-time scanning used by AV software uses sandboxing techniques.
Application sandboxing limits the environment where code can execute. One method that is often used is virtualization. It’s possible to create virtual machines that are completely isolated from the host or the host’s network. Additionally, AV researchers often use isolated virtual machines to analyze malware.
Least Privilege
Most operating systems require a user to have elevated permissions to install applications. Because of this, you can reduce the ability of malware to run on your system by logging on with an account that does not have elevated permissions. This follows a best practice of giving users only the rights and privileges they need to perform their job—the principle of least privilege. If users don’t install applications as a part of their job requirements, they should not have the privileges to do so, and this reduces the ability of the user to accidentally install malware.
A best practice that many organizations follow is to require administrators to have two accounts. One account is a regular user account with little or no privileges, and the second account has elevated administrator permissions. The administrator uses the regular user account for normal, day-to-day activities and uses the elevated user account only when performing administrative work. These steps reduce the opportunities for malware to be installed.
Software Security
Chapter 5 discusses several software security methods that can also help protect against malware. This includes using input validation techniques and application reviews for web applications that an organization hosts. It also includes verifying that risky code has been signed with a digital certificate. Code signing helps reduce malware infections because criminals won’t use code signing techniques to validate malware. It also helps identify modified code because a digital certificate will identify code that has been modified and display an alert.
Application Whitelisting and Blacklisting
Another malware protection method is application whitelisting or blacklisting. Application whitelisting identifies specific applications that can run on a system and blocks all other applications. This can be effective in an organization that has a limited number of applications on systems, but it does make it more difficult to add new applications. Application blacklisting identifies specific applications that cannot run on a system. This is more difficult because it requires you to know all potential malicious applications. Chapter 9 covers application whitelisting and blacklisting as a method to secure endpoint devices.
Participating in Security Awareness and Training
Many users don’t understand the risks associated with malware or how criminals try to trick them into installing malware. Because of this, it’s important to educate users on safe computing habits. Security policies often mandate security awareness and training efforts to prevent security incidents before they occur. In other words, training is a preventive control. In contrast, detective controls attempt to detect incidents after they occur, and corrective controls attempt to reverse the effects of incidents after they occur.
The following list identifies some common items to repeat to users:
• Use spam filters and AV software.
• Don’t open any attachments from unsolicited e-mails.
• Don’t click any links in unsolicited e-mails.
• Be wary of all attachments and links in e-mails. Attackers often try to make e-mails look like they are from someone you know.
• Be wary of any warnings from a website, such as a warning that your system is infected with malware.
• Download files directly from the source website (not from a link provided through a third-party website).
Some organizations have security policies that require additional steps. For example, if a user notices a system is acting suspiciously as though it’s infected with malware, the security policy may require that the user remove the computer from the network by disconnecting the network cable.
Common Vulnerabilities and Exposures
The Common Vulnerabilities and Exposures (CVE) list is a standardized list of known security vulnerabilities, exploits, and malware. Moreover, the CVE provides a standard way of naming information security vulnerabilities. The MITRE Corporation maintains the list, and the National Cyber Security Division of the U.S. Department of Homeland Security sponsors the CVE. You can access the CVE here: https://cve.mitre.org/cve/.
The CVE has definitions for vulnerability and exposure that are worth knowing. A vulnerability is “a mistake in software that can be directly used by a hacker to gain access to a system or network.” An exposure is “a system configuration issue or a mistake in software that allows access to information or capabilities that can be used by a hacker as a stepping-stone into a system or network.”
Chapter Review
A significant security risk to computers and IT networks is in the form of malicious code, commonly called malware. Malware includes viruses, worms, Trojan horses, RATs, scareware, ransomware, keyloggers, logic bombs, rootkits, mobile code, backdoors, trapdoors, spyware, and malware hoaxes.
Viruses have a replication component to spread themselves and an activation component to deliver the payload of the virus. They use a variety of methods to thwart AV software and researchers. Stealth viruses attempt to hide themselves to escape detection. Armored viruses use techniques such as complex code and encryption to prevent a researcher from reverse engineering the code and discovering what the virus is doing. Polymorphic and metamorphic viruses change the virus file to escape detection through signature files.
Although viruses must execute, a worm can travel through a network without any human interaction. A Trojan horse appears to be one thing, such as a useful program, but is actually something different and malicious. Remote access Trojans (RATs) allow attackers to take control of a system from a remote location. Scareware is a type of Trojan. Scareware appears to be a useful antivirus program, but instead attempts to extort money from users. Ransomware locks a user’s computer or data and demands ransom to return the control back to the user.
A keylogger captures keystrokes from users and can send the captured keystrokes to an attacker. Logic bombs execute in response to an event, such as a day or time. Rootkits take control of the operating system (at the kernel or root level) and have the ability to take complete control over what the user sees and does. A backdoor (or trapdoor) is code embedded into an application or operating system that allows an attacker to access data or even gain remote control access to the infected computer. Malware often installs RATs as backdoors into systems. Spyware is any software that is installed without the user’s knowledge or consent and can be malicious. Most malware is delivered through the Internet via drive-by downloads, malvertising, and malicious e-mails.
The primary method of protecting systems from malware is the use of up-to-date AV software. AV software should be installed on every computer. It’s also highly recommended to install AV software at the boundary between the Internet and the internal network and on e-mail servers. AV software uses signature definitions and behavior-based detection methods (sometimes called heuristics) to identify malware. Signature definitions identify known viruses based on a specific pattern within the virus. Behavior-based detection methods attempt to identify malicious behavior of previously unknown viruses. Because viruses can mutate into different variations, it’s important to keep virus definitions up to date. Additionally, it’s important to keep an operating system up to date.
Spam filters and content-filtering appliances help filter out malware before it reaches the internal network. Content-filtering appliances can also filter other traffic, such as by using URL filters to control which websites users can access and performing firewall and intrusion detection services.
Other methods of protecting against malware include using vulnerability scanners to identify potential vulnerabilities in the network, using sandboxing techniques to isolate potentially malicious code, and implementing the principle of least privilege for all accounts. Many software security methods such as input validation, application reviews, and code signing help protect against malware infections. Application whitelisting identifies applications that are allowed and blocks all other applications. Application blacklisting identifies applications that are not allowed and allows all other applications.
By educating users on the basics of safe computing habits, you can help them avoid risky computing behaviors that cause malware infections. This includes not opening attachments or clicking links from unsolicited e-mails, and being wary of all attachments and links in e-mails.
The MITRE Corporation maintains the CVE list, which provides a standardized method of describing malware. The National Cyber Security Division of the U.S. Department of Homeland Security sponsors the CVE.
Questions
1. Which of the following malware types alters its own code to avoid detection by antivirus software?
A. Armored virus
B. Metamorphic virus
C. Polymorphic virus
D. Ransomware
2. What type of malware can spread without any user intervention?
A. Virus
B. Trojan horse
C. Worm
D. Spyware
3. Joe, an employee in the accounting department, received an e-mail with a subject line of “Urgent” and an attachment labeled invoices.zip. The text says “Process these invoices as soon as possible.” When Joe opens the ZIP file, his system reboots, and he can no longer locate the e-mail with the ZIP file. Which of the following provides the best explanation of this activity?
A. The ZIP file is ransomware.
B. The ZIP file is a polymorphic virus.
C. The ZIP file is a Trojan horse.
D. The ZIP file is scareware.
4. An attacker has successfully infected a user’s system. After doing so, the attacker begins scanning the network from the infected computer. Which of the following BEST describes this activity?
A. RAT
B. APT
C. Rootkit
D. Ransomware
5. After visiting a website, a user sees a pop-up indicating a virus has infected his system and offering free antivirus software. He downloads the free antivirus software, but finds that it won’t clean the virus unless he purchases the full version. What does this describe?
A. Shareware
B. Rootkit
C. Freeware
D. Scareware
6. When Sally turns her computer on, she sees a screen indicating software has encrypted all of her data files. A message indicates she must pay $300 within 48 hours to access the decryption key. What does this describe?
A. Logic bomb
B. Ransomware
C. Worm
D. Spyware
7. An employee configured malicious code to execute at midnight on February 2. What does this describe?
A. Logic bomb
B. Groundhog Day virus
C. Worm
D. Ransomware
8. What type of malware takes control of the operating system at the kernel level?
A. Trojan horse
B. Worm
C. Keylogger
D. Rootkit
9. A website developer wants to provide assurances to users that ActiveX controls used on the site are not malicious. What can provide this assurance?
A. Input validation
B. Code signing
C. Code review
D. Enabling cross-site scripting
10. What does antivirus software use to detect previously unknown viruses?
A. Signatures
B. Polymorphism
C. Heuristics
D. Armor
11. A virus is detected on a system based on the virus’s behavior. What detected the virus?
A. Heuristics
B. A virus fingerprint
C. A virus filter
D. A signature
12. What should users do to ensure that antivirus software can detect recently released viruses?
A. Update signatures
B. Update the operating system
C. Update the AV software
D. Regularly purchase new AV software
13. Of the following choices, how is malware most often delivered today?
A. Over the Internet
B. Via an intranet
C. Via USB drives
D. Through company policies
14. A company authorizes users to transport data from work to home using USB drives. What’s the best method of protecting systems from malware without affecting the user?
A. Install AV software on the network firewall
B. Install AV software on the e-mail server
C. Install AV software on each user’s work computer
D. Prevent users from using USB drives
15. Of the following choices, what is the best technique you can implement on an e-mail server to reduce infection through e-mail?
A. Block all e-mail
B. Add a spam filter
C. Add a polymorphic filter
D. Remove all attachments
16. Of the following choices, which are valid methods to reduce malware infections? (Select all that apply.)
A. Don’t open attachments from unsolicited e-mails.
B. Don’t click links in unsolicited e-mails.
C. Don’t send encrypted personal information via e-mail.
D. Don’t follow shortened links from unknown sources.
17. Of the following choices, which one is a principle that prevents users from accidentally installing malicious software on their systems?
A. Nonrepudiation
B. Least privilege
C. Separation of duties
D. Accountability
18. Of the following choices, what network device can filter e-mail, spam, and malware?
A. Packet-filtering firewall
B. Proxy server
C. An intrusion detection system
D. Content-filtering appliance
19. Your organization mandates security training for users within its security policy to educate users about malware and methods to prevent malware infections. What is the best description of this effort?
A. A detective control
B. A corrective control
C. A preventive control
D. A technical control
20. What provides a standardized method of describing malware?
A. The Consortium of Antivirus Vendors (CAV)
B. The Consortium of Virus Authors (CVA)
C. The National Institute of Standards and Technology (NIST)
D. The Common Vulnerabilities and Exposures (CVE) list
Answers
1. B. A metamorphic virus changes or mutates its code as it replicates itself to prevent detection. An armored virus uses techniques such as encryption to make it more difficult for AV researchers to decompile the virus. A polymorphic virus changes the file, but not the code. Ransomware takes over a user’s computer and demands a monetary ransom to return control back to the user.
2. C. Worms spread through a network without any user intervention. Viruses, Trojan horses, and spyware all require some level of interaction.
3. C. The ZIP file is most likely a Trojan horse, appearing to be a ZIP file of invoices, but instead has a malicious component. While the ZIP file could have installed ransomware, the scenario doesn’t indicate any actions other than rebooting the system and hiding the original e-mail and attachment. Similarly, the virus might have polymorphic characteristics causing itself to mutate, but simply hiding the e-mail doesn’t indicate the virus mutated. Scareware uses a pop-up to indicate a system is infected with malware and attempts to trick a user into installing malware.
4. A. A remote access Trojan or remote access tool (RAT) allows an attacker to use an infected computer to scan a network. While advanced persistent threats (APTs) often use RATs, any criminal can use a RAT to scan a network from an infected computer. A rootkit has root-level access on a system, but the scenario doesn’t indicate root-level access. Ransomware takes control of a user’s system or data and demands payment from the user.
5. D. Scareware is malware that scares users into thinking a virus has infected their system and encourages them to install a free download. The free download appears as antivirus software that doesn’t remove viruses unless users pay, but it often includes malware itself. Shareware is software that users are free to try and pay for if they like it and continue to use it. A rootkit takes over the system with root-level privileges. Freeware is free software.
6. B. Ransomware takes control of a user’s computer or data and demands a ransom to return control to the user. This scenario describes CryptoLocker. A logic bomb is malware that executes in response to an event such as a specific date and time. Worms infect computers over a network, and while worms deliver malware, not all worms include ransomware. Spyware is software installed on a user’s system without the user’s knowledge with the goal of spying on the user, not extorting money from the user.
7. A. A logic bomb is malware that executes in response to an event such as a specific date and time. While February 2 is Groundhog Day, the scenario doesn’t describe a Groundhog Day virus. Worms infect computers over a network, not on a specific day. Ransomware takes control of a user’s computer or data and demands a ransom from the user.
8. D. A rootkit is a set of programs that runs on a system, largely undetected, because it runs at the kernel level or root level of the operating system. A Trojan horse is malware that looks like one thing but is something else. A worm is a type of malware that spreads through a network without any user intervention. A keylogger captures keystrokes from users.
9. B. Code signing digitally signs ActiveX controls and provides assurances to users who created the control and that it hasn’t been modified. Input validation helps prevent injection attacks, but it’s used to protect the website, not provide assurance to users. Code review is a valuable tool to detect problems with applications before an organization releases them. Cross-site scripting is an attack and would not be enabled.
10. C. Antivirus software uses heuristics to detect previously unknown viruses. Signatures detect known viruses. Polymorphism and armor are techniques used by virus authors to prevent the detection of a virus.
11. A. Heuristics can detect malware based on the behavior of the malware and are designed to detect previously unknown viruses. There’s no such thing as a virus filter or a virus fingerprint, although a virus signature does uniquely identify known malware similar to how a fingerprint can identify a person.
12. A. Antivirus software uses signature definition files to detect viruses, and these signatures must be regularly updated. It’s not necessary to update the operating system, update the AV software, or purchase new AV software to detect recently released viruses.
13. A. The common way attackers deliver malware is over the Internet. While some attacks can come from internal intranet sources, they do not compete with the volume of attacks from the Internet. Unsuspecting users transmit viruses with USB drives, but this isn’t as common as virus delivery over the Internet. Company policies would not deliver viruses.
14. C. Installing AV software on each user’s work computer provides the best protection against a user inadvertently transporting malware from home to work. Installing software on the network firewall and on an e-mail server is a good practice, but it won’t help if the virus is transported via a USB drive. Preventing the users from using USB drives will affect the users.
15. B. The majority of malware comes through spam, so a spam filter can reduce infections through e-mail. An e-mail server isn’t very useful if it blocks all e-mail or removes all attachments. E-mail servers don’t have polymorphic filters.
16. A, B, D. Common methods that help reduce malware infections are: not opening attachments from unsolicited e-mails, not clicking links in unsolicited e-mails, and not clicking shorted links from unknown sources. Sending e-mail in an encrypted format helps protect confidentiality, but it doesn’t necessarily reduce malware infections.
17. B. The principle of least privilege specifies that users are given rights and privileges to do their job but no more. If a user doesn’t need to install applications, the user is not given permission to do so, which reduces the possibility of the user accidentally installing malware. Nonrepudiation prevents a person from denying an action. Separation of duties divides tasks so that no single person or entity controls an entire process. Accountability ensures that user actions can be tracked and monitored.
18. D. Content-filtering appliances can filter e-mail to remove spam and malicious attachments. They can also act as a proxy server or an intrusion detection system (IDS). A packet-filtering firewall can only examine packets. A proxy server can filter websites but not e-mail. An IDS detects attacks, but not e-mail and spam.
19. C. Training is a preventive control because it attempts to prevent incidents from occurring. Detective controls attempt to detect incidents, and corrective controls attempt to reverse the effects of an incident. Technical controls use technology to implement the control, but training doesn’t require technology.
20. D. The CVE is maintained by the MITRE Corporation and provides a standardized method of describing security vulnerabilities, exploits, and malware. There is no such thing as the Consortium of Antivirus Vendors (CAV) or Consortium of Virus Authors (CVA). NIST is a U.S. government entity that regularly publishes standard publications related to IT security, standards, and practices, but it does not maintain the CVE.



