CHAPTER 13
Legal Issues
In this chapter, you will learn about
• Computer forensics
• The incident lifecycle
• The three phases of a computer forensic investigation
• The importance of preserving and protecting evidence
• How to protect volatile RAM and data on disk drives
• The difference between computer abuse and computer crime
• How mandatory vacations and job rotation help prevent fraud
• Some of the laws and regulations designed to protect PII
Exploring Computer Forensics
Computer forensics is the science of examining and inspecting computer systems for evidence about an event or crime. The examination includes recovering data stored on or transmitted by any electronic device. A primary goal when identifying and recovering digital evidence is to preserve its integrity. This ensures that forensic experts can analyze it and that the evidence can be used in legal proceedings if necessary.
You’ve probably watched one of the CSI television shows where detectives use crime scene investigation (CSI) techniques to piece together the elements of a crime. Investigators are careful to ensure they don’t modify the evidence as they collect it, and they protect the evidence after collecting it. Computer forensic experts have the same goals as they try to piece together evidence to investigate computer abuse or computer crime. The only difference is that computer forensic experts typically use different tools and techniques when they are investigating an incident. The following sections describe some of the important concepts to consider related to incident handling and computer forensics.
Supporting the Incident Lifecycle
As an IT or security professional, you are sure to observe security incidents, so you should be prepared to participate if asked. With that in mind, it’s important to understand the overall incident lifecycle process. Chapter 7 included a section on responding to incidents and covered methods documented in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-61, Computer Security Incident Handling Guide. This section covers the topics from a slightly different perspective using the terminology in the SSCP objectives.
As a reminder from Chapter 7, a security incident is any violation of policies or security practices that has the potential to result in an adverse event. Negative consequences include system crashes, unauthorized access to data, and the execution of malicious code on a computing system. Chapter 1 introduced the CIA triad (confidentiality, integrity, and availability). An adverse effect includes any event that results in the loss of confidentiality, integrity, or availability and is also considered a security incident.
Once an incident occurs, the primary goal of incident handling is to contain any potential damage and then repair the damage. The following sections discuss the individual phases in an incident lifecycle.
Preparation
The first step an organization takes in incident handling is preparation. Preparation includes implementing security controls (or countermeasures) to prevent, detect, and correct security incidents, as discussed in Chapter 9. Organizations typically create an incident response policy that outlines its plans to prepare for and respond to an incident.
Detection, Analysis, and Escalation
IT and security personnel often don’t know an event is an incident until they respond and begin investigating and analyzing the event. For example, a user may report erratic behavior on a computer. After investigating and analyzing the user’s computer, IT administrators could discover malware infecting the user’s system. Deeper analysis would identify the extent of the malware infection.
In this scenario, the user’s report is the event. Once administrators detect and analyze the malware, they can promote the event to an identified incident. The administrators may find that they can resolve the incident by running antivirus software and either quarantining the malware or removing it completely.
Personnel escalate an incident if they realize they cannot resolve it. This is similar to a help desk technician escalating a help desk ticket when the technician cannot solve the customer’s problem. A more experienced technician takes over and attempts to resolve the problem. Similarly, if technicians or administrators discover a security incident but realize they cannot resolve it, they take steps to escalate it. Often, this simply means they report the incident to their supervisor or a higher-level administrator to get some help.
Personnel do not escalate all incidents. For example, if a technician discovers malware and uses antivirus software to remove it, there is no need to involve other personnel. However, the technician would still document it using the organization’s procedures.
Containment
After discovering an incident, personnel respond in accordance with the organization’s incident response plan, which might include actions to take after discovering specific incidents. For example, it’s important to contain an incident to limit potential damage. If an administrator discovers a computer is infected with malware, the incident response plan might specifically state that the IT administrator should disconnect the network interface card (NIC) to isolate the computer from the network. If the malware hasn’t spread yet, this action contains the malware to the infected computer.
If multiple computers within a network are suspected of being infected, containment may require administrators to isolate the network by manipulating routers or switches. As an example, a network can be connected together with a switch and connected to other networks via a router. By disconnecting the cable from the switch to the router, the network is isolated.
The incident response plan obviously cannot include specific actions for every possible incident. However, it will include generic guidance such as protecting evidence while investigating the incident, containing the incident, escalating the incident, and reporting the incident.
Eradication
Eradication is the complete removal of all elements of an incident. In the scenario of a simple malware infection, eradication means that the malware has been detected and quarantined or removed. However, it can include much more.
As an example, advanced persistent threats (APTs) typically start with a remote access Trojan (RAT) installed on a single computer when a user clicks a malicious link within a phishing e-mail. Attackers quickly exploit this RAT and look for other computers in the network that they can exploit. It’s common for attackers to create multiple backdoor accounts that they can use to attack other systems. Eradication starts by disabling the RAT, but also includes identifying all the backdoor accounts and removing them.
For APT attacks, complete eradication can be extremely difficult, especially if the RAT was first installed weeks or months before the incident was discovered. Organizations often seek outside help from dedicated cybersecurity organizations or government agencies to fully eradicate an attacker’s presence.
Recovery
Recovery includes completing the steps required to return all systems to normal operation and confirming that the systems are operating normally. Depending on the extent of the incident, this can be very simple or very complex. For a simple malware infection, recovery may just be quarantining or removing the malware and running another antivirus scan to verify it remains clean.
For serious incidents, recovery can include multiple actions, such as completely rebuilding systems from images and installing all appropriate patches, restoring data from backups, changing passwords, and tightening network security. After attackers have successfully infiltrated a network, it’s common for them to try again. Because of this, recovery may include increasing system logging or network monitoring to detect subsequent attacks.
Reporting
Reporting an incident refers to informing personnel within the organization and entities outside the organization about the incident. Internally, an organization’s incident response plan might require personnel to report any security incident to a member of the incident response team. As an example, technicians who identify and remove malware from systems might still be required to report the incident to security personnel, even though they resolved the incident.
Many laws and regulations require organizations to report certain types of incidents. This is especially true for any data breaches that expose personally identifiable information (PII) or protected health information (PHI). These laws typically require the organization to report the data breach to affected individuals. This helps ensure that people are informed when a data breach has exposed their personal information. They can take appropriate countermeasures such as subscribing to a credit monitoring service.
Lessons Learned
Taking the time to identify lessons learned helps ensure that an organization examines incidents in an attempt to learn from them. This is often done by holding a lessons learned meeting after an incident. It’s extremely important to avoid any “blame storming” during these meetings because it puts people on the defensive and makes them reluctant to participate. Instead, the goal should be to discover things like what happened, when it happened, how the staff responded, if the existing procedures were adequate, and what could have been done differently.
As a simple example, after discovering and resolving a malware infection, security personnel will often try to determine the steps leading up to the malware infection. They may find that the malware infection occurred for one of the following reasons:
• Antivirus software was not installed or was disabled, or signatures were not up to date.
• Up-to-date antivirus software did not block the malware.
• A user brought the malware in from home with a USB drive.
• A user opened an attachment in a phishing e-mail, which installed the malware.
• A user clicked a link in a phishing e-mail, taking the user to a malicious website.
• A user visited a malicious website, which downloaded malware in a drive-by download.
• A system didn’t have up-to-date patches.
By understanding what allowed the malware infection, security personnel are better prepared to recommend countermeasures to prevent a recurrence. For example, the following list identifies possible countermeasures security personnel can recommend for the malware infection:
• Use technical security controls to install and update antivirus software
• Evaluate the effectiveness of the antivirus software and consider replacing it
• Implement antivirus software at other locations, such as on e-mail servers and at the network boundary (between the Internet and the internal network)
• Use technical security controls to block access to USB drives except for those purchased by the organization
• Purchase antivirus software for users to install on their home computers
• Provide training to users on the dangers of transferring data between home and work computers via USB drives
• Provide training to users on phishing e-mail tactics
• Provide training to users on drive-by downloads
• Terminate employment of users that ignore the training
• Implement or improve a patch management program
Implementing Countermeasures
Management has the responsibility of selecting which countermeasures to implement based on the organization’s acceptable level of risk. Once management approves the countermeasures, other personnel begin implementing them. Of course, it’s possible that the organization will experience a similar incident even after implementing new countermeasures. This repeats the process. The result might be that the organization implements new countermeasures or replaces existing countermeasures.
Handling Evidence
During any incident, personnel are likely to encounter evidence. Ensuring that the evidence is handled properly is important. This includes preserving the evidence by preserving the scene, protecting the evidence, and creating a chain of custody to document how the evidence has been protected.
In the medical field, the first responder is the first medically trained person to arrive on the scene of an incident that requires medical knowledge. It can include emergency medical services (EMS) personnel, emergency medical technicians (EMTs), police, firefighters, or other personnel. In the IT field, the first responder is the first forensics-trained person on the scene. This may be someone with advanced forensics training. It can also be an IT administrator who understands the basics of preserving forensic evidence and can manage the scene until a forensic expert arrives.
Medical first responders aren’t expected to have the same level of knowledge as a doctor. Instead, they’re expected to have enough knowledge to stabilize an injured person’s health until a more qualified professional arrives or they transport the injured person. In situations with multiple injuries, medical first responders perform triage to prioritize patient treatment based on the severity of their medical conditions. Similarly, IT first responders aren’t expected to have the same level of knowledge as full-time forensic experts. However, they should know the basics of incident response and perform triage during an incident. They prioritize the impact on different systems during an incident and prioritize their response based on the severity of the incident for different systems.
Preserving the evidence is extremely important in a computer forensic investigation. If the evidence is not preserved, other personnel cannot verify the analysis. Additionally, evidence that isn’t preserved is considered tainted. Tainted evidence can be misleading, indicating that innocent people are guilty and that guilty people are innocent. Tainted evidence loses its value, and a court of law won’t allow its use in legal proceedings.
Along these lines, many organizations recommend disconnecting computers from a network as an initial step in a computer investigation. This isolates the system and prevents remote access. This ensures someone cannot clear logs or delete data on the system via a remote connection. It’s also an important step to take if personnel suspect the system is infected with malware, such as a worm, that may infect other systems on the network.
As soon as evidence is collected, investigators create a chain of custody. A chain of custody form documents who obtained the evidence, where it was obtained, when it was obtained, and how it was controlled since it was first collected. Maintaining control of evidence ensures that the evidence is never out of someone’s control and subject to tampering.
Three Phases of a Computer Forensics Investigation
A computer forensics investigation is typically described as occurring in three phases of acquiring, authenticating, and analyzing the evidence, as shown in Figure 13-1. IT professionals need to be aware of the three phases and understand their role if an incident occurs. For example, if IT professionals sound the alarm to report an incident, they need to know what their responsibilities are related to protecting the evidence prior to security professionals arriving to secure the evidence.

Figure 13-1 Three phases of a computer forensic investigation
Acquire the Evidence
In the acquisition phase, the investigators collect the evidence. It’s very easy to modify the evidence during this phase if personnel don’t take steps to preserve the evidence. As a simple example, opening a file modifies it because the file now shows a new access time.
Forensic experts use bit-copy or drive-imaging tools to capture the contents of a drive without modifying the data. This copy is a forensic duplicate image. In addition to copying data, this process includes copying free and slack space on the drive or partition. The copy must be an exact bit-by-bit copy of the original in order for legal entities to consider it forensically sound. For example, Figure 13-2 shows the overall process of copying a drive. Experts analyze the copy instead of the original drive. If they want to validate their analysis, they make another copy of the original drive and repeat their analysis. Additionally, the original drive remains available as evidence in a court of law if required.

Figure 13-2 Using bit copy-tools to capture drive contents
In addition to capturing the contents of a drive, it’s often useful to capture the contents of a computer’s memory. This often has information on recently run processes and applications and the information can be useful during the investigation. However, the computer’s memory is volatile and will be lost when the computer is turned off, so it’s important to keep the system on until forensic experts have an opportunity to capture the memory contents. Forensic experts have other tools available that can read and copy data from volatile memory.
Forensic experts typically use one or more of the available forensic toolkits when collecting, authenticating, and analyzing evidence. These toolkits allow investigators to capture data more efficiently, with less loss and less effort. Table 13-1 shows some of the tools that are available. Note that this isn’t intended to be a comprehensive list of all available forensic toolkits, but instead provides a list of some examples.
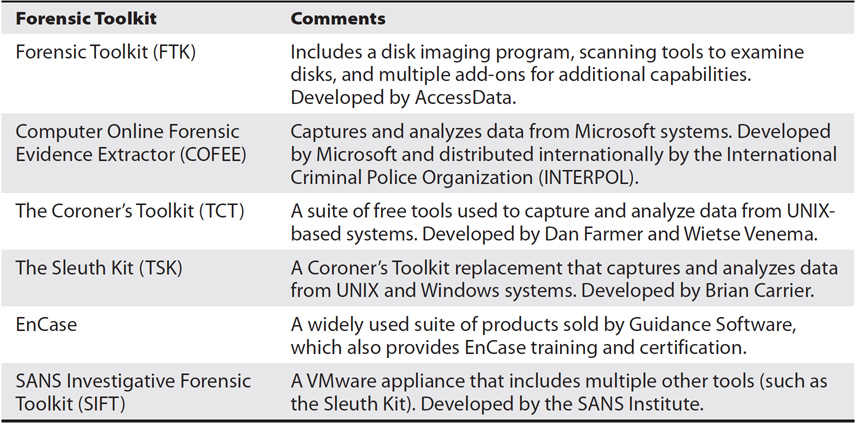
Table 13-1 Common Forensic Toolkits
Comparing Volatile Data and Persistent Data
Volatile data is data that will be lost if a system is powered down. Data stored in random access memory (RAM) is an example of volatile data. RAM often holds valuable data related to recent activity on a system that can be used in an investiga-tion. However, if the system is powered down before this data is collected, the data is lost. Several computer forensic tools are available that can capture volatile data before the system is shut down. However, there is very little possibility of retrieving information from volatile RAM after power has been removed.
In contrast, some data on a system is persistent data, which is data stored on a hard drive or other type of media such as an optical disc or USB flash drive. Persis-tent data remains even when a system is powered down.
NIST SP 800-86, Guide to Integrating Forensic Techniques into Incident Response, provides a wealth of details on how to collect data from different sources. This includes collecting data from data files, operating systems, network traffic, and applications.
Authenticate the Evidence
The chain-of-custody form (described in the “Handling Evidence” section) provides proof that the evidence has been controlled since it was collected and records every interaction with the evidence since it was collected. In the absence of a chain-of-custody form, courts may question the validity of the evidence and refuse to allow its use in legal proceedings.
If an investigator confiscates a laptop as evidence but leaves it on his desk, anyone with access to the desk may be able to add, modify, or corrupt the data on the laptop. Even if no one tampered with the laptop while it was on the desk, the laptop may not be admissible as evidence in a court of law without a chain of custody. Even if the investigator locked the laptop in a safe, if he neglected to document his actions with a chain of custody, legal authorities are less likely to believe it was controlled at all times. Controlling the evidence and documenting the control with a chain-of-custody form provides proof that the evidence has been controlled and was not subject to tampering.
You can also authenticate files and drives by comparing a hash value of the original to a hash value of the copy. Chapter 14 covers hashing in more depth, but as an introduction, a hashing algorithm creates a hash, which is simply a number. A hashing algorithm will always create the same hash when executed against the same data, including a forensically sound copy of the same data.
Imagine the hash of the original disk is 123. It should always be 123 no matter how many times you execute the hashing algorithm against the disk. If it is ever anything other than 123, it indicates the original disk has been modified. Similarly, the hash of a forensically sound copy of the disk should be 123. If it’s different, it indicates that the copy is not a true bit-by-bit copy of the original disk, and courts may not accept the results from analyzing the copy as admissible evidence.
In reality, a hash is much longer than just three digits. For example, Message Digest 5 (MD5) creates a 128-bit hash expressed as a 32-digit hexadecimal number. However, for the explanation, it’s much easier to conceptualize numbers such as 123 rather than numbers like this: dc647eb65e6711e155375218212b3964.
Analyze the Evidence
In the last phase of a computer investigation, the forensic experts analyze the evidence. One of the key requirements in this phase is to use repeatable processes by analyzing copies of the data whenever possible. This ensures the original data is not modified and can be copied again if necessary.
In some cases, it is necessary to analyze the original. For example, magnetic media hard drives often hold data remnants as data remanence. This data remanence is not copied in a bit-by-bit copy but might hold valuable information. The only way to analyze data remanence is by analyzing the original hard drive. This type of analysis should only be done by trained personnel, and only when necessary.
The science of computer forensics has advanced significantly in the last few years. There are many more college and university courses and degrees focused on this science, and there are also several specialized certifications available. Additionally, forensic tools continue to improve, giving forensic experts more and more capabilities.
Legal and Ethical Principles
When responding to incidents, it’s important to apply legal and ethical principles. Applying legal principles simply means identifying relevant laws and abiding by them. These laws vary in different jurisdictions, such as in states and different countries, but organizations have an obligation to identify and follow them.
When an organization decides to add forensic capabilities, it’s important to document some basic legal and ethical principles along with guidelines within a forensics security policy. These principles and guidelines can be anything the organization chooses to add, and many professional organizations have provided suggestions of items to include.
The Association of Chief Police Officers (ACPO), a British organization recently replaced by the National Police Chiefs’ Council (NPCC), published the ACPO Good Practice Guide for Digital Evidence. Version 5.0 includes the following four legal and ethical principles:
• Principle 1 No action taken by law enforcement agencies, persons employed within those agencies or their agents should change data which may subsequently be relied upon in court.
• Principle 2 In circumstances where a person finds it necessary to access original data, that person must be competent to do so and be able to give evidence explaining the relevance and the implications of their actions.
• Principle 3 An audit trail or other record of all processes applied to digital evidence should be created and preserved. An independent third party should be able to examine those processes and achieve the same result.
• Principle 4 The person in charge of the investigation has overall responsibility for ensuring that the law and these principles are adhered to.
NIST SP 800-86, Guide to Integrating Forensic Techniques into Incident Response, stresses the importance of clearly defining the roles and responsibilities of personnel performing forensic activities. It mentions that forensic processes should be consistent with the organization’s policies and all applicable laws. It also stresses the importance of maintaining a chain of custody to support the admissibility of evidence into legal proceedings.
NIST SP 800-72, Guidelines on PDA Forensics, suggests using the Daubert method, which is a set of standards that help ensure the reliability of evidence. When applied to digital evidence, it’s important to consider the following reliability factors derived from the Daubert method and set forth in SP 800-72. Following these reliability factors will help ensure the evidence can be used in a court of law.
• Testability Has the scientific theory or technique been empirically tested? (Some tools, such as the EnCase Toolkit, have been used successfully in court cases, but some have not.)
• Acceptance Has the scientific theory or technique been subjected to peer review and publication? This ensures that flaws in the methodology would have been detected and that the technique is finding its way into use via the literature.
• Error Rate What is the known or potential error rate? Scientific measures generally have associated error rates, which can be estimated with a fair amount of precision.
• Credibility What is the expert’s qualifications and stature in the scientific community? Does the technique rely upon the special skills and equipment of one expert, or can it be replicated by other experts elsewhere?
• Clarity Can the technique and its results be explained with sufficient clarity and simplicity so that the court and the jury can understand its plain meaning?
Forensics and Fraud
While most scientists and forensic experts seek the truth, some have strayed from the law. This includes falsifying evidence, falsifying lab results, and misrepresenting evidence in trials.
As an example, Fred Zain was a forensic laboratory technician who falsified DNA results. Before this was discovered, he was regularly sought out as an expert witness, though his credentials were sketchy at best. He reportedly failed organic chemistry, flunked an FBI course on forensic science, and fabricated his resume.
Investigations later indicated that he falsified evidence resulting in as many as 180 wrongful convictions. Senior Circuit Court Judge James Holiday reported that Zain engaged in misconduct and outright fraud so often, that any testimony by him should be considered invalid, unreliable, and inadmissible. Another investigation indicated that Zain often filed reports on tests that weren’t completed, reported negative results as positive, and described inconclusive results as conclusive.
Even though there were many hints that Zain was engaged in fraud during his career, supervisors, and other experts chose to ignore them. For example, two workers reported seeing him record test results from blank test results, but their complaints weren’t taken seriously. Additionally, an FBI laboratory director told state police that Zain failed basic forensic science courses, but no action was taken.
There aren’t any infamous examples of cybersecurity forensic experts engaging in the same level of fraud. However, it is certainly conceivable that some are tempted to falsify evidence in a misguided sense of justice. Hopefully, when others see these actions, they will report them and the actions will be investigated.
Chapter 1 includes the four Code of Ethics Canons that SSCP candidates should follow. As a reminder, they are
• Protect society, the common good, necessary public trust and confidence, and the infrastructure.
• Act honorably, honestly, justly, responsibly, and legally.
• Provide diligent and competent service to principals.
• Advance and protect the profession.
Comparing Computer Abuse and Computer Crime
Computer abuse and computer crime mean two separate things. In computer abuse, an individual is dishonest or unethical and using a computer in an unauthorized manner. In contrast, a criminal commits illegal acts with a computer. Both of these concepts are highlighted in Figure 13-3.
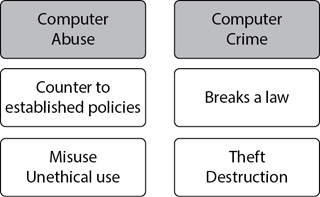
Figure 13-3 Computer abuse and computer crime
For example, in computer abuse, an individual may misuse a computer system in violation of an organization’s security policies. The user may be using the computer to shop for personal items during company time despite knowing that this is against the established acceptable use policy.
Cybercrime (or computer crime) is any crime that involves a computer. The criminal may use a computer as a tool to commit the crime, or the computer may be the target of the crime. The purpose of cybercrime is often monetary gain for the criminal, but some criminal acts are simply destructive, with the purpose of negatively affecting a computer or organization.
The three commonly quoted elements needed to commit a crime are means, motive, and opportunity (sometimes referred to as means, opportunity, and motive, or MOM). By understanding these, you have a greater chance at reducing crime. More specifically, if you can remove the means, motive, or opportunity to commit a crime, you have a better chance of preventing the crime. The means is the ability of the criminal to commit the crime, the motive is the reason (such as for money or revenge), and the opportunity is simply the chance to commit the crime.
The following are some of the common terms related to computer abuse and computer crimes:
• Cyberbullying Cyberbullying has become common among some young people. The bully uses the Internet to attack a victim through harassment, coercion, or intimidation. For example, a cyberbully may spread lies about a person via social media such as Facebook or Twitter, or send harassing text messages to the victim or to others about the victim.
• Cyberstalking Cyberstalking includes cyberbullying actions, but it goes further. For example, the stalker may gather information on the victim, monitor the victim’s activities, and steal the victim’s identity. Adults are typically involved with cyberstalking, while children are more likely to be involved in cyberbullying. A number of laws are in place addressing cyberstalking making it a criminal act.
• Cyberwarfare Cyberwarfare is a politically motivated attack on entities in another country. The goal is typically sabotage to disrupt the capabilities of an entity in the target country or espionage to gather intelligence on the target. For example, the U.S. government concluded that North Korea attacked Sony in late 2014 and labeled this cyberwarfare. Similarly, the Washington Post reported that attackers accessed computer networks in the White House and that the Post’s sources indicated the attackers were Russian state-backed groups. Attack groups sponsored by a state (or government) are typically referred to as advanced persistent threats (APTs).
Understanding Fraud and Embezzlement Crime
Fraud is the use of deception for unlawful gain or unjust advantage. It includes engaging in wrongful or illegal activities with the intention of gaining undue or illegitimate advantage over another person, group, or entity. Embezzlement is a specific type of financial fraud where an individual steals money or property from an employer, company, clients, customers, or even partners. It also includes misappropriating money or assets held in trust.
MCI WorldCom gained notoriety for a massive accounting scandal that resulted from fraudulent accounting methods. CEO Bernard Ebbers helped grow the business that ultimately became MCI WorldCom. Later, courts held him responsible for the company’s fraudulent financial reporting that resulted in the loss of over $100 billion to investors (including 401K investors), and he was ultimately convicted of fraud and conspiracy. He is serving a 25-year prison sentence.
Bernie Madoff has become a household name related to fraud. He managed a Ponzi scheme for years under the guise of an investment company. Many people regarded him as an outstanding investment banker who ran a successful wealth management company. In reality, he routinely skimmed new investments and used these investments to pay what looked like great dividends to current investors. Investigators calculated the amount of missing funds at about $65 billion. He is currently serving a 150-year prison term. Interestingly, investigations such as one by the U.S. Securities and Exchange Commission failed to uncover the fraud, which went undetected until Madoff admitted the Ponzi scheme to his sons in 2008.
Chapter 5 mentions salami attacks where an attacker takes multiple minor actions to get large gains. For example, prosecutors indicted Michael Largent for collecting more than $50,000 from some online brokerage firms by collecting between a penny and $2 at a time. He used scripts to open over 58,000 accounts under phony names with the brokerage firms. These firms verified his bank account by depositing small amounts of money into his account. However, when his bank questioned the thousands of small payments, he didn’t have any good answers and the FBI later arrested him. Largent was later sentenced to 15 months in prison and ordered to pay over $200,000 in restitution.
Many companies use job rotation and mandatory vacations to reduce the risks of internal fraud and embezzlement. These policies also reduce illegal data modifications and general misuse of information.
Mandatory Vacations
Many banking institutions implement mandatory vacation policies. These require employees to take a vacation outside of the workplace for a specified period, such as at least five or ten consecutive workdays. The goal is to require someone else to perform their job functions, which increases the possibility of exposing any suspicious activities.
For example, imagine that an employee identifies a loophole in the flow of money within an organization and discovers that he can divert a small percentage of money in each transaction. However, if he ever stopped diverting the money, the loss would appear as an anomaly. If the organization forces him to take time off work, the diversion would stop for a short time, and someone would discover the fraud. Knowing this is a possibility will often deter an employee from exploiting the loophole in the first place.
Similarly, imagine if an investment banker takes millions of dollars from specific investors but never actually invests the money. Instead, he uses the money to pay healthy dividends to other investors who previously gave him money. He gives these investors fake documents indicating that they have a substantial amount of wealth. In reality, this crooked investment banker has stolen all the money. As long as the investment banker is at work, he can answer the queries from the investors and no one will discover his actions. However, if the organization forces him to take regular vacations, the Ponzi scheme will collapse while he is away.
Admittedly, a mandatory vacation policy doesn’t guarantee that fraud won’t occur. Consider this same scenario with two or more people colluding to create and manage this Ponzi scheme. If that’s the case, forced vacations won’t necessarily discover the actions. The accomplices can cover for anyone who is on vacation. However, when two or more people are involved, it increases the chances that someone will make a mistake. Additionally, law-breaking criminals committing fraud aren’t necessarily trustworthy, so any one of them might report the actions at some point and place all the blame on one of the other accomplices.
While mandatory vacations can be an effective security control, they aren’t foolproof. However, when used as part of an overall defense-in-depth plan, mandatory vacations can help reduce the chance of fraud and embezzlement.
Job Rotation
Job rotation is the practice of moving employees periodically, such as once a year or so, between different jobs. The goal is for employees to do different jobs at different times, which also prevents any single employee from doing the same job for years at a time.
Chapter 1 covered separation of duties and explained how it prevents a single person from having complete control over a process. For example, accounting departments frequently separate accounts payable tasks from accounts receivable tasks to reduce the risks. Even though a separation of duties policy separates these tasks, employees working in an accounting department typically have the skills to do both jobs. In other words, someone working in an accounts payable division also has the skills to perform accounts receivable tasks. A job rotation policy periodically moves personnel between the two jobs. Just in case an employee discovers a loophole in the process that he or she can use to defraud the company, the job rotation policy limits how long the fraud could continue. It also increases the chance of discovering the fraud, which acts as a deterrent.
Many organizations use job rotation for cross-training. For example, organizations often rotate management personnel through different jobs within an organization to gain a better overall understanding of the organization. The primary purpose of this practice is to help build the knowledge and skills of personnel rather than deter and detect fraud. Job rotation also helps in disaster recovery if key personnel are unavailable.
Understanding Privacy Issues
Although the explosion of the use of computers has certainly helped people share information, it has also resulted in people having easy access to massive amounts of personal data about individuals. If organizations don’t protect this data, it can negatively affect an individual’s privacy. Even if individuals are very careful with their personal data and reveal it only when required to do so for business transactions, they are still affected if the business suffers a data breach. If these businesses don’t protect the customer’s data, the customer loses.
Because of this, many laws require organizations to protect personal data. Despite these laws, data breaches continue. Chapter 5 discussed the Identity Theft Resource Center (ITRC). As a reminder, the ITRC reported a record high of 1,579 data breaches exposing more than 178 million records in 2017.
Legal experts agree that the key to avoiding liability for any data leakage is due diligence. In other words, if an organization is actively taking steps to protect data and prevent privacy compromises, but still suffers a loss, it is less likely to be held liable. The message seems to be that “incidents happen,” but if you’re doing your best to prevent the incidents, you’ll have less legal liability.
Chapter 11 introduced personally identifiable information (PII) and the importance of protecting it. PII is information that can be used to personally identify an individual and includes components such as those shown in Figure 13-4. Chapter 11 also introduced the Health Insurance Portability and Accountability Act (HIPAA) of 1996. HIPAA mandates the protection of protected health information (PHI), which is any PII that includes information concerning the health status, provision of health care, or payment of health care for an individual.
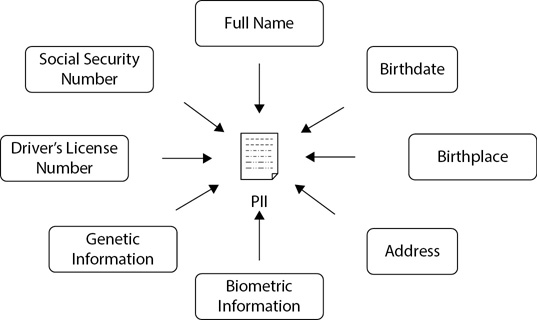
Figure 13-4 Components of PII
Defining a Data Breach
Generically, a data breach is any incident where unauthorized personnel gain access to sensitive, protected, or confidential data. It often occurs when criminals from outside an organization launch attacks allowing them to access data held inside an organization.
The Identity Theft Resource Center focuses on the exposure of personal data and defines a data breach as “an incident in which an individual name plus a Social Security number, driver’s license number, medical record or financial record (credit/debit cards included) is potentially put at risk because of exposure. This exposure can occur either electronically or in paper format.” Outside of the United States, this definition of a data breach includes a national identification number instead of a Social Security number. Note that this matches the definition of PII. Because medical records are included, it also matches the definition for PHI.
Some data breaches only expose usernames, passwords, and e-mail addresses without exposing other information that identifies an individual. The ITRC doesn’t report the number of records exposing only this data, primarily because its focus is on identity theft. However, many other definitions include this data compromise as a data breach. Attackers can do a lot of damage if they gain access to valid user-names, passwords, and e-mail addresses.
The following sections cover some of the regulations that mandate the protection of PII.
General Data Protection Regulation
Chapter 11 introduced the General Data Protection Regulation (GDPR). As a reminder, it is a European Union (EU) regulation that became enforceable in May 2018 and supersedes the Data Protection Directive (Directive 95/46/EC). The overall purpose is to protect the personal data of individuals within the EU.
Organizations that operate in the EU and/or collect data from any EU residents are required to comply with the GDPR. It requires organizations to obtain freely given, specific, informed, and unambiguous consent before collecting personal data. The European Commission defines personal data as “any information relating to an individual, whether it relates to his or her private, professional or public life. It can be anything from a name, a home address, a photo, an e-mail address, bank details, posts on social networking websites, medical information, or a computer’s IP address.”
Three relevant terms within the GDPR are data subject, data controller, and data processor.
• Data subject The GDPR defines a data subject as “an identified or identifiable natural person.” In short, a data subject is a person. However, the GDPR does not define natural person. The three likely possibilities are 1) a person who is a citizen of the EU, 2) someone who is living in the EU, or 3) someone who is a citizen of the EU and living in the EU. This is likely to play out in the courts in the coming years. The GDPR does specify that parental consent is required to collect data on any child below the age of 16 years.
• Data controller A data controller is an entity that collects data about EU residents. Data controllers must comply with certain rules related to how they collect and use personal information.
• Data processor A data processor is an entity that processes data on behalf of a data controller but doesn’t have control over the data. As an example, an external payroll company that processes data for another organization’s employees is a data processor. Cloud providers that store data are also data processors. Data processors have a responsibility to keep data secure by preventing unauthorized access, disclosure, or accidental loss.
It is possible for an entity to be both a data controller and a data processor.
The penalties for noncompliance are fines up to 4 percent of an organization’s annual global revenue.
California Supreme Court Rules That ZIP Codes Are PII
The California Supreme Court determined in early 2011 that a person’s Zone Improvement Plan (ZIP) code is PII. In this case, Williams-Sonoma stores collected a customer’s ZIP code each time that the customer made a credit card purchase. It then combined the customer’s name and ZIP code in a search to discover the customer’s address (which the customer didn’t provide) and used this information for marketing purposes.
The court determined that a ZIP code is not required for a credit card transaction, but is readily understood to be part of an address. Because a company can combine a ZIP code with the person’s name to discover the person’s address, the California Supreme Court classified it as PII. The decision restricts businesses in California from requesting a ZIP code during a credit card transaction. The California Supreme Court’s justification in this case is that the business can use this personal information for business purposes. A similar lawsuit is playing out in Massachusetts.
While the California Supreme Court determined that a ZIP code is PII when combined with a customer name, it is one of the few jurisdictions to do so. If you buy gas with a credit card in a different jurisdiction, you are often required to enter the ZIP code.
Connecticut’s Public Act No. 08-167
In 2008, Connecticut passed a law titled “An Act Concerning the Confidentiality of Social Security Numbers.” Although the title focuses on Social Security numbers, the contents of this law go beyond just these numbers.
For example, it states, “Any person in possession of personal information of another person shall safeguard the data, computer files, and documents containing the information from misuse by third parties….” It then defines personal information as “information capable of being associated with a particular individual through one or more identifiers, including, but not limited to, a Social Security number, a driver’s license number, a state identification card number, an account number, a credit or debit card number, a passport number, an alien registration number or a health insurance identification number….”
Intentional violations of this law can result in a fine of $500 for each violation, with a maximum fine of $500,000 per event. In other words, if a database is released that includes this information on 1,000 or more people, it can result in a fine of half a million dollars.
A notable distinction with this law is that unintentional violations are not subject to the law. In this case, if an organization discloses the information, it must prove that the disclosure wasn’t intentional. The law does not consider a data breach by an attacker an intentional violation as long as the organization took steps to protect the information.
Other laws, such as the Social Security Number Protection Act of 2010 and the Social Security Number Protection Act of 2011, provide additional protection of Social Security numbers. The 2010 act prohibits federal, state, and local agencies from printing any part of a Social Security number on a check; some organizations did so to ensure only the intended recipient could cash it. The 2011 act requires the Department of Health and Human Services to eliminate the unnecessary collection, use, and display of Social Security numbers on Medicare cards and other communications.
Children’s Online Privacy Protection Act
The Children’s Online Privacy Protection Act (COPPA) is a U.S. federal law that applies to the collection of information on children under the age of 13. The goal is to protect the privacy of these children by preventing websites or online services from collecting information on them without parental consent.
For example, UMG Recordings was fined $400,000 after it was found to have knowingly collected information on children under the age of 13. The company created a website directed at children to promote a 13-year-old pop star known as Lil’ Romeo. UMG Recordings collected extensive information on the children, including their full name, e-mail address, home address, phone number, interests, and birthdate. Even when the user’s birthdate clearly indicated that the user was under the age of 13, UMG Recordings still collected and used the information. For example, it used the collected e-mail addresses to send e-mail marketing about other musicians and other websites.
Although it is possible to collect information on children under 13, the organization must gain parental consent, which is often challenging. Because of this, most organizations simply do not collect information on these children to remain in compliance of the law.
California Online Privacy Protection Act of 2003
The California Online Privacy Protection Act (OPPA) of 2003 became law in 2004. Notice the acronym is OPPA without an initial C to differentiate it from the Children’s Online Privacy Protection Act (COPPA). It requires operators of commercial websites to conspicuously post and comply with a privacy policy if they collect PII on any visitors who reside in California. In this context, a commercial website is one created by or for an organization. In other words, OPPA doesn’t apply to personal websites created by or for individuals.
Note that this law doesn’t just apply to websites created by organizations in California or hosted on servers in California. Instead, it applies to any organization that makes its website available to any California residents. In other words, it applies to any website on the Internet, because California residents with Internet access can access pages hosted anywhere in the world.
Although it’s doubtful that California law will extend to remote places like Tanzania, it will certainly affect websites operating within the United States. Because of this, most operators of commercial websites in the United States make certain that they include a privacy policy that complies with this law if they collect any information on the user, such as name, e-mail address, or other data, used to track the user.
The privacy policy must be easy to locate (for example, websites typically make it accessible from the home page) and include the following:
• What information is gathered by the website
• How the information is used and shared
• The effective date of the policy
• A description of changes since the policy was first created
Legal and Regulatory Concerns
The previous sections covered some specific laws related to privacy. Chapter 4 covers cloud computing, including various cloud server models and cloud security, and Chapter 8 covers various monitoring systems, including intrusion detection and prevention systems. It’s worthwhile to connect some of these topics within the concept of legal and regulatory concerns.
Jurisdiction refers to the legal authority that a legal body has over an organization. If an organization is operating in Maryland, for example, it must comply both with the laws in Maryland and with U.S. laws. However, the jurisdiction can easily extend to other legal entities if the organization conducts interstate or international business.
However, if an organization chooses to store data in the cloud, the jurisdiction for this data might be different. Imagine that some of an organization’s data is stored in a data center in Virginia and some of its data is backed up in a data center in Canada. The organization now must comply with laws in Virginia and Canada. Additionally, the GDPR provides another example of how jurisdiction can change. Simply by collecting data from an EU resident, an organization is obligated to comply with the GDPR regardless of the organization’s physical location.
Cloud-based surveillance solutions are becoming quite popular, but they bring other concerns. As an example, organizations can install surveillance cameras that capture video and store the video in the cloud. This can change the jurisdiction and, depending on contracts with the surveillance company, can also raise questions about data ownership.
Electronic discovery (also known as e-discovery) refers to any process that attempts to locate and secure electronic data for a civil or a criminal legal case. Legal entities often request such data with a subpoena and organizations have a legal obligation to comply. However, collecting this data and turning it over to legal authorities takes time and money.
Organizations can save time and money in potential future events by limiting the amount of data they maintain. As an example, imagine an organization has a policy to delete all e-mail older than one year, and that policy is followed. Later, a lawsuit results in a subpoena that requires the organization to turn over all its e-mail related to a specific topic. Personnel would then be required to go through all the e-mail for the past 12 months to find relevant e-mails. In contrast, imagine the organization doesn’t have a policy and the e-mail servers have e-mails from the last ten years. Personnel would then be required to comb through all ten years’ worth of e-mails.
Monitoring systems collect data within an organization and must also comply with the same jurisdiction issues. However, they can also help an organization prove compliance with laws and regulations. Still, there are limitations on which data monitoring systems can collect. Organizations need to ensure they do not violate privacy laws within their jurisdiction when collecting data.
Chapter Review
A security incident is any violation of policies or security practices that has the potential to result in an adverse event. An incident lifecycle includes several different phases. The first phase is preparation, which includes implementing security controls to prevent, detect, and correct security incidents. When an event occurs, personnel investigate it in the detection, analysis, and escalation phase. If analysis verifies that an incident has occurred, personnel may escalate it depending on the severity of the incident. During the containment phase, personnel attempt to isolate the incident to limit potential damage. The next phase is to eradicate all elements of an incident. This phase can be combined with the recovery phase to return all systems to normal operations. After an incident has occurred, it’s important to examine the responses in a lessons learned phase. In many situations, this results in a recommendation to implement additional countermeasures.
First responders are the first forensics-trained personnel on the scene, and one of their primary responsibilities is the preservation of the scene. The three phases of a typical computer forensic investigation are acquiring the evidence, authenticating the evidence, and analyzing the evidence.
When acquiring the evidence, one of the most important concerns is to protect the data and prevent data modifications. Forensic tools allow experts to capture data in volatile RAM before a system is powered down and use bit-copying procedures to copy the contents of hard drives. Several forensic tools are available such as FTK, COFEE, the Sleuth Kit, EnCase, and more.
In the authentication stage, a chain-of-custody document is used to provide proof that the evidence was controlled after it was collected. The chain-of-custody document ensures that the evidence is admissible in a court of law. The analysis of the evidence is the last stage. Some of the same forensic tool suites used to collect evidence include tools that can be used to analyze evidence.
Computer abuse indicates that an individual is using a computer or network in an unauthorized manner, such as counter to an organization’s security policies. Computer crime indicates that the user is committing illegal acts with the computer. Computer crime is punishable by fines and/or jail time.
Computers can be used in fraud and embezzlement crimes resulting in substantial losses to an organization. Mandatory vacations and job rotation are two security policies that an organization can use to reduce the success of fraud and embezzlement crimes. These two policies are often used with other security controls as part of an overall defense-in-depth strategy.
PII includes any information that can identify an individual. Privacy issues related to the protection of PII have become more important as the amount of data that organizations collect on their customers has increased. If an organization doesn’t take precautions to protect customer data, attackers may breach the organization’s database and access its customer data. Many laws have been enacted on the international, national, and state levels requiring organizations to protect PII.
Legal and regulatory concerns apply to cloud computing and various monitoring systems. They typically identify requirements to maintain the privacy of data. Jurisdiction refers to the legal authority that a legal body has over an organization. It can change depending on the physical location of an organization, where the data is held within the cloud, and where the data was collected from, such as from an EU resident. Electronic discovery refers to any process that attempts to locate and secure electronic data for a civil or a criminal legal case.
Questions
1. What is the first phase in the incident lifecycle?
A. Event
B. Preparation
C. Detection
D. Escalation
2. Which of the following best describes a primary goal of incident handling?
A. Collecting evidence
B. Documenting evidence
C. Containing any potential damage
D. Improving security controls
3. Which one of the following is most likely to be performed during a lessons learned phase in the incident lifecycle?
A. Chain of custody
B. Hashing
C. Escalation
D. Countermeasure recommendations
4. Which of the following identifies a primary responsibility of a first responder after a computer security incident?
A. Capturing images of disks
B. Capturing data in RAM
C. Interviewing witnesses
D. Preserving the scene
5. What forensic evidence can be lost if a system is powered down before the evidence is collected?
A. Data on the disk drive
B. Data on a USB drive
C. Data in memory
D. Data in files
6. Managers suspect that an employee in your organization has committed fraud. You are told to secure his computer as part of an incident response. Which of the following are appropriate steps? (Select three.)
A. Disconnect the computer from the LAN
B. Power the system down
C. Prevent anyone from accessing the system
D. Take pictures of the system
7. Which of the following is a benefit of a chain-of-custody form?
A. It helps ensure that evidence is protected.
B. It helps ensure that evidence is controlled.
C. It helps ensure that evidence is not modified.
D. It helps ensure that evidence is admissible in court.
8. Of the following choices, what are valid phases in a computer forensic investigation? (Select three.)
A. Prosecution based on evidence
B. Authenticating evidence
C. Analyzing evidence
D. Acquiring evidence
9. Which of the following choices is the most important consideration when gathering evidence as part of a computer forensic investigation?
A. Ensuring that systems are turned off as soon as possible
B. Ensuring that a record of files on a system is recorded by accessing the system
C. Ensuring that users can log on to the system
D. Ensuring that evidence is not modified
10. A forensic expert wants to examine data on a hard drive of a confiscated computer. Which of the following actions should the expert complete first?
A. Ensure that the computer has UPS protection
B. Create a bit copy of the disk
C. Disable the antivirus software on the computer
D. Move the hard drive to another system and examine it on the other system
11. Which of the following helps to prove that collected evidence has been controlled since it was collected?
A. COFEE application
B. Chain of custody
C. SIFT
D. Audit logs
12. In general, what elements need to come together for a crime?
A. Means, motive, and opportunity
B. Criminal, software, and hardware
C. Discovery, theft, and benefit
D. Attacker, attackee, and method
13. Countries sometimes engage in espionage against other countries. What is this called?
A. Cyberbullying
B. Cyberstalking
C. Cyberwarfare
D. Cyberterrorism
14. What is the purpose of mandatory vacations in relation to security?
A. To ensure that employees do not burn out
B. To ensure that employees take time to relax
C. To reduce the payroll of an organization
D. To reduce the chance of fraud
15. What security practice moves employees into different positions periodically to reduce the risk of fraud?
A. Separation of duties
B. Job rotation
C. Mandatory vacations
D. Risk mitigation
16. A business in Florida gathers customers’ names and ZIP codes and uses them to identify the customers’ addresses. What is occurring?
A. Violation of the GDPR
B. Data breach
C. Data inference
D. Violation of COPPA
17. An organization collects customer data such as their name, e-mail address, physical address, and phone number. What term best describes this information?
A. PHI
B. PII
C. COFEE
D. FTK
18. An organization regularly collects information on customers for marketing purposes. It uses this information to personally identify the customers. Who is responsible for protecting this data?
A. The organization.
B. It depends on whether the customers gave permission to collect the data.
C. It depends on whether a data breach occurred.
D. Customers.
19. What law requires an organization to get a parent’s consent prior to collecting information on children under 13?
A. COPPA
B. OPPA
C. GDPR
D. E-Privacy Directive
20. What law requires organizations to post a privacy policy on their website?
A. SOX
B. PHI
C. OPPA
D. COPPA
Answers
1. B. The first phase in the incident lifecycle is preparation, which includes implementing security controls to prevent, detect, and correct security incidents. An event isn’t necessarily an incident. Events are investigated to determine if they are incidents during the detection, analysis, and escalation phase.
2. C. Primary goals of incident handling include containing any potential damage and repairing the damage that has occurred. While incident handling often includes evidence collection and using chain-of-custody forms to document collected evidence, these are not primary goals. The lessons learned phase often improves security controls, but this is not a primary goal.
3. D. The lessons learned phase examines the incident and the response, and often results in countermeasure recommendations. The goal is to prevent a recurrence of the incident. A chain of custody validates that evidence has been controlled since it was collected. Hashing provides assurances that data (such as a bit-by-bit copy of a disk) is identical. Escalation refers to getting more people involved in an incident.
4. D. A primary responsibility of first responders is the preservation of the scene. Forensic experts acquire and analyze the evidence, which includes capturing images of disks and data in RAM. Investigators interview witnesses.
5. C. Data in memory (volatile RAM) is lost if a system is powered down. Power isn’t required to retain data on disk drives or USB drives, so it is not lost when powered down. Data in files is retained on disk drives.
6. A, C, D. Organizations often have policies to disconnect a computer from the local area network (LAN) to isolate it and protect evidence on the system. No one should be allowed to access the system as a precaution to ensure that data (and potential evidence) is not modified. In some situations, taking pictures of the system can help preserve evidence. You should not power the system down, as doing so will delete any data in volatile RAM.
7. D. A chain-of-custody form provides proof that evidence has been protected and helps ensure that the evidence is admissible in court. Note that it only documents how the evidence has been protected and controlled, but it doesn’t actually protect or control the evidence. It also doesn’t ensure that the evidence is not modified.
8. B, C, D. A computer forensic investigation typically includes the three phases of acquiring, authenticating, and analyzing evidence. Prosecution is not a part of a computer forensic investigation but may occur based on the results of an investigation.
9. D. It’s important that evidence is not modified when collecting evidence. If a system is turned off, data in volatile RAM is lost. If files on a system are accessed, it modifies the files by showing new access times. If a user logs on to a system, it can modify information about the last user that logged on.
10. B. Disk drives should be copied with an approved bit-copy tool prior to examining any of the data because the process of examining the data can result in the loss of data. An uninterruptible power supply (UPS) protects a system from a power loss, and antivirus (AV) software protects a system from malware, but neither has anything to do with protecting evidence. Moving the drive to another system and examining it on the other system will modify the original evidence.
11. B. A chain-of-custody document provides proof that collected evidence has been controlled since it was collected by identifying exactly who has control of it and where it was located since it was collected. Microsoft developed the Computer Online Forensic Evidence Extractor (COFEE) to help law enforcement forensic experts. SANS Investigative Forensic Toolkit (SIFT) is another set of applications that computer forensic experts use. Audit logs can be used in a forensic investigation but they don’t validate evidence.
12. A. The three commonly quoted elements for a crime are means (the ability to commit the crime), motive (such as money or revenge), and opportunity (the chance to commit the crime). Crimes can be committed without software or hardware. Criminals can commit crimes (such as vandalism or destruction) without theft. Similarly, criminals can commit crimes (such as theft) without an attack.
13. C. Cyberwarfare is a politically motivated attack on entities in another country and is done for sabotage and/or espionage. Cyberbullying occurs when one person harasses, coerces, or intimidates another person using the Internet. Cyberstalking is more serious than cyberbullying and is a criminal act. Cyberterrorism is the use of the Internet to launch terrorist attacks.
14. D. A mandatory vacation policy can reduce the chance of fraud by requiring other employees to take over the tasks and responsibilities of a vacationing employee. While vacations are good to help employees relax and reduce the chance of burnout, these matters aren’t as relevant to security issues as reducing the chance of fraud. While some companies do implement mandatory vacations to reduce payroll expenses during periods of low activity, this is not a security policy.
15. B. Job rotation is a security practice of rotating employees into different positions periodically to reduce the risk of fraud. It is often combined with a separation of duties policy, but separation of duties by itself does not require employees to rotate between jobs; only that a single employee doesn’t control all elements of a process. A mandatory vacation security policy requires employees to take time away from work to increase the chances of suspicious activity being discovered. Risk mitigation is any practice that reduces risks, but it is not limited to only rotating employees to different positions or only reducing the risk of fraud.
16. C. This is an example of data inference, because the company is collecting small pieces of information to get other information that isn’t provided directly. The General Data Protection Regulation (GDPR) doesn’t restrict the collection of data, but instead mandates the protection of data that a company collects. The question doesn’t indicate the company is not protecting the data adequately. A data breach occurs when unauthorized individuals access stored data, but there’s no indication of unauthorized access in this scenario. The Children’s Online Privacy Protection Act (COPPA) protects the privacy of children under 13.
17. B. This information is personally identifiable information (PII) because it can be used to identify the customers personally. Protected health information (PHI) is information concerning the health status, provision of health care, or payment of health care for an individual. COFEE is a forensic tool used by law enforcement agencies. The Forensic Toolkit (FTK) is another forensic tool used by cybersecurity professionals.
18. A. Organizations are responsible for protecting personally identifiable information (PII), which is information that can identify individuals. This is true even if the customers give permission to the organization to collect the data, and even if a data breach has not occurred. Customers are not required to protect the information that they give to an organization.
19. A. The Children’s Online Privacy Protection Act (COPPA) requires organizations to get a parent’s consent prior to collecting information on children under 13. The California Online Privacy Protection Act of 2003 (OPPA) requires operators of commercial websites to post a privacy policy on the website if the website collects personally identifiable information (PII). The General Data Protection Regulation (GDPR) requires the protection of European Union (EU) residents and requires parental consent if a child is under the age of 16. The GDPR supersedes the E-Privacy Directive.
20. C. The California Online Privacy Protection Act of 2003 (OPPA) requires operators of commercial websites to post a privacy policy on the website and comply with it if the website collects personally identifiable information (PII). Sarbanes-Oxley (SOX) Act is a U.S. law that requires executives of publicly held companies to validate the integrity of their financial data. HIPAA is a law focused on the protection of protected health information (PHI) and requires organizations to post a privacy policy. However, PHI is not a law. The Children’s Online Privacy Protection Act (COPPA) is a U.S. federal law that applies to the collection of information on children under the age of 13.


