HOUR 13
Network Applications
What You’ll Learn in This Hour:
• Location of network applications in OSI model
• Groupware concepts
• Client and server aspects of groupware
• Email and file transfer
In this hour, we move up to Layer 7 of the Internet/OSI (Open Systems Interconnection) model and examine common applications that run on computer networks. The focus is on groupware, email, and file transfer services. Be aware that later hours return to Layer 7. The number of protocols and services offered in the OSI application layer could fill thousands of books, such as the one you’re now reading. We concentrate on those software systems that will likely be part of your network. The goal of this hour is to acquaint you with a wide array of fine productivity tools. I suspect you already know about many of them and might be using them. Perhaps I can offer a few more for your consideration.
A network application is usually directly visible to the user, because the user interacts with the application software. For example, email and text messaging require direct input into the application from a user. Indeed, we can view the layered model as consisting of eight layers, with the user or user application setting on top of Layer 7.
Applications that a user runs from a computer network can be installed and run on the user’s computer or on a server. Whether run from a server or from individual desktops, the user will notice little difference in performance and services. In terms of administration, running the applications from the server allows for easier updates and more efficient administration.
Introduction to Groupware
Groupware consists of a suite of software modules that allow users to communicate and collaborate with each other. Some people use the terms collaborative software or workgroup support systems to describe this concept. At the desktop, the client side of these applications is collectively referred to as a Personal Information Manager (PIM).
Groupware applications embrace the client/server model of communication. A client runs on each user computer and allows the client computer to communicate with the communication server, which accumulates and holds the application data. Groupware products run on top of a particular network operating system and the lower layers of the OSI model.
For example, Exchange Server from Microsoft is a groupware environment that runs on a Microsoft 2000, 2003, or 2007 server. Three commonly used groupware product suites are Microsoft Exchange Server, Lotus Notes, and Novell GroupWise. Each of these groupware products offers several communication and collaboration features.
Some of the common features of groupware products are these:
• Electronic mail system—The groupware communication server serves as the mail server for internal email systems or Internet email.
• Group scheduling—A centralized scheduling system is maintained on the communication server.
• Discussion groups—Users can read and post messages to a discussion database. They can create discussion groups for the discussion and development of projects. This category of groupware includes electronic conferencing, which consists of message boards, video conferencing, instant messaging, online chats, and shared whiteboards.
• Information databases—The communication server can host databases such as an employee handbook and a centralized employee address book (including email and phone extension information).
• Task automation—Forms can be developed that allow users to order office supplies online and invite users to a meeting.
Other sets of software for your consideration are known by the name of collaborative management tools. These systems include the following:
• Project management—Provides a means to set up, schedule, and track the phases and steps of a project, such as the network you and your team will create.
• Electronic calendars—Allows its users to schedule events and keep all members informed about events and associated deadlines. (Electronic calendars are also called time management systems.)
• Workflow systems—Provides a means to track the flow of documents and their associated users. In a large bureaucracy, a workflow system can lead to remarkable insights (not to mention surprises) into the overhead of “doing business.”
• Shared slide shows and spreadsheets—Often used in conjunction with the groupware applications cited previously.
One of the important—perhaps the most important—features provided by groupware is email. The sending and receiving of email, although transparent to the end user, works the same as postal or “snail” mail. You create your correspondence or email, place an “address” on it, and then send it on its way. Your network email system takes care of the return address and routes your email across your local network and the Internet. If it gets there, great; if not, it will provide you a notification that the message was undeliverable.
Email started out as a simple function of the early UNIX operating systems. It was composed of an automated file copying operation in which a text file containing a message was copied from a local UNIX system’s hard drive onto a remote UNIX system’s hard drive.
To get around the nonstandard and often incompatible email systems that permeated the early UNIX environment, a programmer named Eric Allman wrote a program called sendmail. Sendmail offered a large range of options for sending and receiving mail.
Over the past couple of decades, software developers have improved the software and protocols used to send and receive email. Today, a wide variety of email clients and servers are available. Most of them now center around two Internet standards: POP3 (Post Office Protocol version 3) and IMAP4 (Internet Message Access Protocol version 4). Most email servers support both protocols, but POP3 is more common.
POP3 and IMAP4
POP3 allows users to log on to a network and retrieve email messages. The messages can be stored and viewed later, even if the user is no longer connected to the network. POP3 is used by a client computer to collect its email from the mail server. IMAP4 is another email transport protocol that allows users to check their messages but doesn’t remove them from the email server. This feature supports a user who wants to view received email from any device or any location. IMAP4 also allows multiple users to have access to the same mailbox.
SMTP
The Simple Mail Transport Protocol (SMTP) is used to send emails, whereas POP3 and IMAP4 are used to retrieve emails. SMTP can deliver messages to one or many recipients. After a user has entered the email, it’s sent to a relaying server. This server uses a special record (called the Mail eXchange or MX record, explained in Hour 15, “Connecting to the Internet: Key Supporting Operations”) to determine which STMP server to send the email.
As suggested, SMTP is not designed to retrieve messages (called “pulling” messages). It’s a “push” protocol, in that it sends messages. POP3 or IMAP4 are pull protocols. Nonetheless, some implementations have a feature allowing reception of mail, especially for a computer that is continuously connected to the Internet. But for most users, why bother? POP and IMAP do the job just fine.
Proprietary Mail Systems
With the advent of PC-based networking in the early-to-mid 1980s, a raft of vendors began building proprietary mail systems to operate in various PC environments. These obsolete systems, which included Lotus cc:Mail, Microsoft Mail, and various packages built around Novell’s MHS (Message Handling System), often attempted to rectify what their designers saw as shortcomings in sendmail.
Proprietary email packages for computer networks are usually easy to install and configure. Three of the more popular email and groupware platforms are Microsoft Exchange, Lotus Notes, and Novell GroupWise. These platforms not only provide for the use of POP3 and SMTP to send company email using Internet standards, but they provide a centralized server for the administration of the mail and communication services.
A downside of proprietary mail systems is that they do not work with each other without the intercession of a mail gateway, a computer that converts mail from one proprietary format to another. Additionally, proprietary mail systems can’t route mail directly to the Internet. To do so, they require yet another mail gateway to convert mail to SMTP format, the section of the TCP/IP (Transmission Control Protocol/Internet Protocol) protocol suite that handles mail routing.
Open-Standards Email
An alternative to proprietary mail systems is the use of open standards. As with most things networked, the Internet Engineering Task Force (IETF) has published an extensive set of standards for running email applications over the TCP/IP protocol suite. Internet mail standards are surprisingly simple. As long as your network uses TCP/IP, it’s possible to use Internet mail; all you need is a server to run the server-side mail application software and the software to run at the client to retrieve mail from the server.
There are many manufacturers of server and client Internet mail software. The beauty of the standards set forth by the IETF is that any client can work with any server as long as both pieces conform to the standards: SMTP for “push” side operations and POP3 or IMAP for the “pull” side.
Common standards-compliant email includes the following:
• Open-source sendmail, usually running on UNIX or Linux
• Commercial sendmail from sendmail.com, usually running on UNIX or Linux
• Procmail, usually running on UNIX or Linux
• Fetchmail, usually running on UNIX or Linux
• Microsoft Exchange Server running the Internet Mail Connector
Sendmail, procmail, and fetchmail are (mostly) open source. This means that you can download the code from the appropriate web location (www.sendmail.org for open-source sendmail), configure and compile it on your UNIX or Linux system, and run it. Commercial sendmail and Microsoft Exchange are commercial solutions that offer vendor support.
Configuring Email
Getting an email client up and running requires you to install and configure the client to send and receive email. To configure the client, you must first configure an email account on the server for the client. For example, on a server running Microsoft Exchange Server, a new Exchange Mailbox is created in the Windows Active Directory, as shown in Figure 13.1.
FIGURE 13.1 Users require an email account on the mail server.

After you’ve created the account (whether a proprietary platform account or an Internet email account), you can configure the client application. For example, Microsoft Outlook walks the user through the steps of creating a new account, as depicted in Figure 13.2. It allows different account types to be created—such as Microsoft Exchange, POP3, IMAP, and HTTP (Hypertext Transfer Protocol)—and can serve as the client for a number of proprietary mail systems.
FIGURE 13.2 You must then configure the email client to communicate with the mail server.
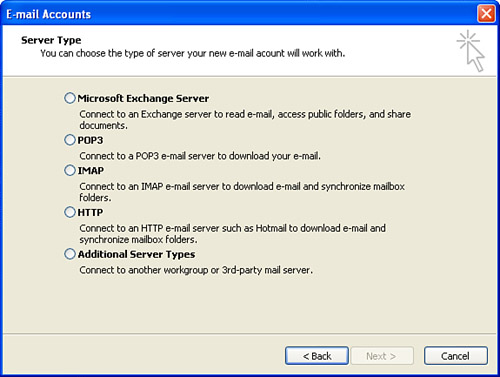
When configuring the email client, you will need to specify the user account, user password, and name of the mail server. When dealing with Internet email, you typically specify both a POP3 and SMTP server.
Multipurpose Internet Mail Extensions (MIME)
Although being able to send text messages over a network or the Internet is useful, the fact that we can attach files to email messages makes it a great way to send all sorts of personal and professional items. Examples are application files (programs you can run on your computer), picture files, video files, sound files, and so forth.
However, until the advent of MIME (Multipurpose Internet Mail Extensions), these kinds of files could not be carried over regular email channels. The problem was the design of SMTP, which supports only one format for coding text into binary images (strings of 1s and 0s). Equally serious, this format (the famous 7-bit ASCII character set) does not support diacritics (phonetic marks used in many languages).
As a result, the IETF decided to create a set of extensions for the SMTP mail standard that enabled files of many different types to be attached to email. Rather than defining all the file types and creating a new SMTP version each time a new file type came into existence, the IETF decided that it would create a system to which new file types could be added without changing the whole mail system. The IETF’s efforts resulted in the MIME standard, which is used to code files of various types across the Internet. Today, SMTP and MIME are so closely related that SMTP/MIME email is now a common term.
To gain sense of the power of MIME, we can now send and receive files containing other languages, audio and visual information, graphic representations, and computer software programs.
As the Internet matures, many new file types will become available. Fortunately, MIME is sufficiently open-ended that it will support new types of files. In this regard, it’s extensible, allowing the addition of new content types. MIME is a valuable protocol; without it, the rest of the Internet-compliant email system would lose a significant portion of its utility.
Diagnosing Email Problems
Problems encountered with sending and receiving email usually boil down to problems with the client’s mail server. This holds true no matter what mail system your network uses. Oh, and there’s always that pesky problem that can shut down any client/server-based system (such as email): connectivity issues. If there’s a network problem, even a perfectly working email client and an email server that is up and running can’t talk if the network infrastructure doesn’t provide the appropriate connectivity. Think of it this way: The lower layers of the Internet/OSI model must be operating correctly for the protocols in Layer 7 to function.
Remember that connectivity issues don’t always relate to a faulty router or a problem with cabling; other problems that control the capability of computers to communicate on the network can also be at fault. On occasion, you might notice a network provider (such as Verizon) has experienced a “down” with its email system. These outages are quite rare because an unreliable email product would be the death knell to that vendor.
Accurately diagnosing network communication problems requires a keen understanding of the TCP/IP protocol stack and network troubleshooting. We discuss TCP/IP in Hour 14, “Connecting to the Internet: Initial Operations,” and network troubleshooting in Hour 22, “Network Troubleshooting.”
Dealing with Spam
Spam = an associated curse of using the Internet.
As I’m sure you know, spam is unwanted email, and it can fill our In box. We don’t like it, but let’s be more specific. What exactly is spam?
An electronic message is spam if: (1) the recipient’s personal identity and context are irrelevant because the message is equally applicable to many other potential recipients; and (2) the recipient has not verifiably granted deliberate, explicit, and still-revocable permission for it to be sent; and (3) the transmission and reception of the message appear to the recipient to give a disproportionate benefit to the sender.1
1 Sourced from http://www.mail-abuse.com/spam_def.html
Spam not only is a nuisance, it costs companies and institutions work hours and ultimately money. It’s beginning to clog the Internet to the point at which it’s become a major problem. Some spam is innocuous, but a lot of it’s unsuitable and objectionable.
Higher-end email clients, such as Lotus Notes and Microsoft Outlook, provide filters that you can use to move spam directly to the trash bin, and some email clients can block spam based on email addresses or the domain of the sender. A number of other tools on the market also do a good job fighting spam. The following list provides some of these; consider it a list of possibilities, not necessarily recommendations:
• CloudMark is an excellent spam fighter; it’s an inexpensive subscription, and it works well.
• Bayesian filters, which are available from various sources on the Web, block spam based on local algorithms and what you select as spam. They usually require some setup efforts (“training the filter”) but can trap more than 99% of unwanted emails.
• For people using Linux or UNIX and sendmail, SpamAssassin is another accurate server-based tool to help block spam. Recent enhancements to SpamAssassin also support Windows-based systems.
• Subscriptions are available to businesses to filter spam based on black hole lists. They keep a database of known spammers and deny messages coming from those email addresses and domains. In addition, some sites provide tutorials and product announcements on spam.
• A good spam fighter that integrates well with Microsoft Outlook (and Outlook Express) is SonicWALL. It provides a home or corporate user with the ability to filter and block spam messages. You can find more information on SonicWALL at www.sonicwall.com.
In corporate environments, it falls on the network administrator to find strategies and set rules to minimize spam on the corporate network.
You might want to devise a set of rules that users must follow on the network. For example, you might have a rule that forbids users to sign up for any Internet services or special websites using their corporate email accounts. This tactic is one way spammers build their long list of email addresses: They capture corporate email names and add them to their spam list. Spammers like to use corporate names because the name is often setup to reach many recipients.
Scheduling and Calendars
Anyone who has worked in an environment that requires the staff to meet periodically knows how difficult it is to schedule a meeting that works for all the potential attendees. I think everyone will agree that just tracking your own personal and business appointments can be problematic. We use every possible kind of system to stay organized: calendars, daily planners, and a lot of little scraps of paper.
Groupware products such as Microsoft Exchange and Lotus Notes also provide scheduling and calendar features that make it easy to schedule appointments, meetings, and other events. Let’s look at an example of how this works in the Microsoft Exchange environment.
Each user’s calendar (meaning her current schedule containing appointments and scheduled meetings) is held in folders on the Exchange server. This means that when any user attempts to schedule a meeting from Microsoft Outlook’s Calendar feature, Outlook can check to see if the invitees for the meeting are available or busy. Figure 13.3 shows the Plan a Meeting window in Outlook 2003. The AutoPick button provides a user with the ability to find open time slots for the meeting that will accommodate all the attendees.
FIGURE 13.3 A user scheduling a new meeting has the calendar resources on the Exchange Server to accommodate the attendees’ schedules.
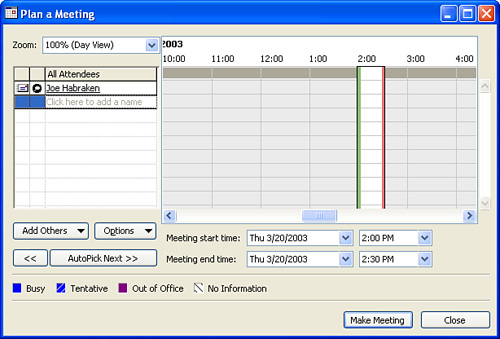
After the user schedules the meeting, the meeting is posted to the Exchange Server. This process also sends out email meeting requests to all the attendees. Figure 13.4 shows a sample of a meeting request email.
FIGURE 13.4 Meeting requests are sent out to the invitees.
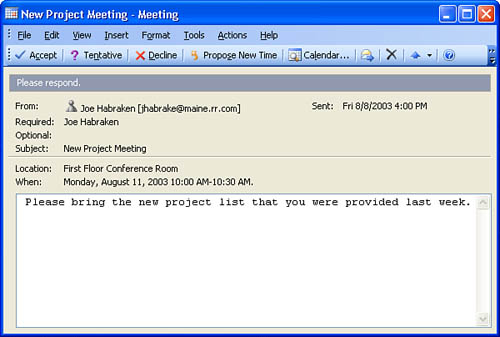
Because the Microsoft Exchange Server environment enables the Outlook client to reconcile all attendees’ schedules with the meeting date and time, the system should be foolproof in terms of “Ah! I didn’t get the message about the meeting!” However, if users haven’t kept their calendars up-to-date, this system won’t work any better than a paper calendar or the scraps of paper mentioned earlier.
Groupware products are not limited to just scheduling meetings. You can also assign tasks and appointments to users. For example, when a task is assigned to a user, the user can accept or decline the task. Because messages are sent back to the originator of the task whether the user accepts or declines, groupware, such as Microsoft Exchange, makes it easy to track job assignments and their status.
Contact Management
Another tool provided by groupware products is contact management. At its most basic, contact management allows a user to store names, addresses, email addresses, and phone numbers in a database. Not only can users create their own contacts list in a groupware client, but they can access group contact and distribution lists that make it easy to send email, phone, or otherwise communicate.
In networked environments, groupware contact software provides a way for a sales force to not only track its clients, but also track the most recent meeting it has had with clients; it can also, in some cases, automatically schedule a time for a next call after a preset amount of time has elapsed.
Like group calendaring, contact management software does not yet have an IETF standard, so for the most part, contact management software interoperates only with itself. Your will find, however, that most contact management software packages—particularly those provided by groupware products such as Lotus Notes, Microsoft Exchange, and Novell GroupWise—do provide the ability to import and export data to and from other contact management software.
Creating a new contact in the different groupware products will vary; however, all the products provide a window that allows you to enter the information related to a particular contact such as name, address, phone number, and so on. Figure 13.5 shows the Outlook Contact window, which is used to enter information related to a new contact.
FIGURE 13.5 Contact information is entered in a simple-to-use window.
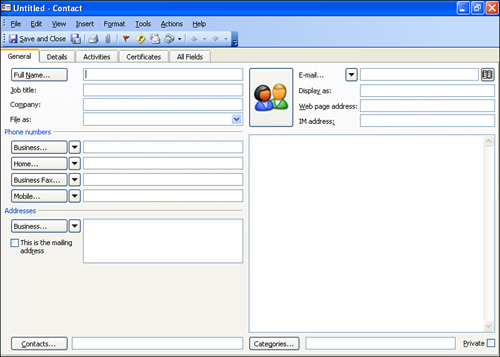
After you enter the contact, the information is then available to all the users on the network. This not only creates an environment in which client or customer data is readily available to all employees, but it sets up a system in which contact data will more likely be updated because the contact records don’t reside on individual computers; they’re held on the server.
In the late 1990s, Microsoft integrated contact management features into its Outlook and PIM products. Microsoft also offers Business Contact Manager for Outlook. Even on the Macintosh platform, in 2002, Apple began including PIM and calendar applications with its operating system. The efforts by these companies have led to a decline in native-mode contact management products in the marketplace.
A Sampler of Network-Based Applications
As mentioned, various groupware products are available. Each provides the standard groupware features such as email, scheduling, and contacts.
In the sections that follow, I will briefly discuss Novell GroupWise, Lotus Notes, and Microsoft Exchange/Outlook. You’ll find that each is similar at the user level. So, in terms of deciding to use a particular platform, you should look at the server side of each groupware product and see how they’ll fit into your current network implementation.
Novell GroupWise
GroupWise is Novell’s entry into the groupware software market. It consists of a GroupWise client and server. You can deploy the GroupWise server product on a Novell NetWare server, or you can run it on a Microsoft Windows server such as Microsoft Windows 2000 or Microsoft Server 2003. Alternatively, you can run the GroupWise client on several client platforms such as Windows, Linux, and the Mac operating system. Figure 13.6 shows the GroupWise client window on a Windows XP computer.
FIGURE 13.6 The GroupWise client window
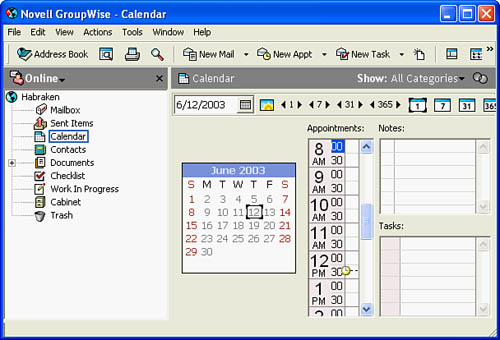
The GroupWise server product (version 8 as of the writing of this book) is fully integrated with NetWare’s eDirectory hierarchical object database, so client accounts are actually created within the eDirectory.
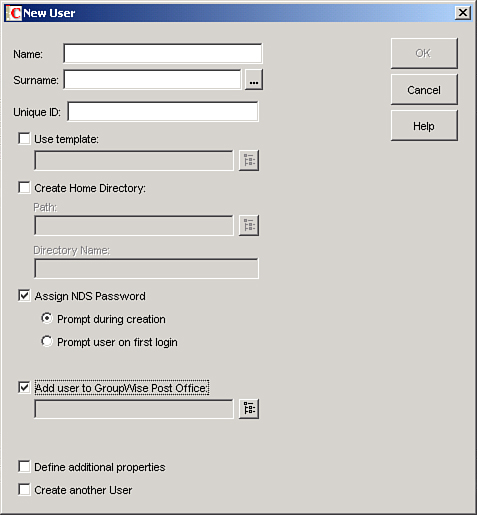
Users are provided access to the GroupWise post office when their NetWare eDirectory user accounts are created. Figure 13.7 shows the eDirectory New User dialog box. To include a user in the GroupWise post office, you must select the Add User to GroupWise Post Office check box.
FIGURE 13.7 GroupWise post office access is provided via the user’s eDirectory account.
GroupWise provides all the tools that users expect from a GroupWare product: email, calendar, contacts, and tasks. GroupWise also provides a handy web interface tool that allows users on the road to access their GroupWise account via the Internet.
Lotus Notes
Lotus Notes from IBM provides a client/server groupware platform that can be run on a number of different network operating systems such as Microsoft Windows, Sun Solaris, and Novell NetWare servers. The server side of the Lotus Notes platform is called Lotus Domino Server, and it can provide users with email, contacts, tasks, and different discussion and communication databases.
One of the strengths of Lotus Notes is its capability to create discussion databases. These databases are much like Internet newsgroups in that users can post a particular message and then other users can post comments related to that message (or post a new message). This allows users to have an online dialogue without having to clutter their email In boxes. For example, several workers involved in the same project could design a discussion database and then post status information, tips, or even frustrations on the database.
The latest version of Lotus Notes is 8, with three releases:
• Version 8.0—Server versions for Windows, Linux, Solarix, AIX, and client versions available for Linux, Windows, and Vista.
• Version 8.0.1—Support added for Widgets and Google Gadgets.
• Version 8.02—Support for Office 2007 files.
Some industry watchers (Forbes Magazine, for example) state that Lotus Notes is losing its customer base. IBM claims otherwise and says its customer base has more than tripled during the past 10 years. Lotus Notes is a fine product that I don’t believe is going away.
Microsoft Exchange/Outlook
Microsoft Exchange Server runs on a server class computer that already has the Windows network operating system installed on it. Exchange Server is tightly wrapped with Microsoft’s Active Directory (the hierarchical database used to store objects on a Windows network). Users in the Active Directory gain access to the Exchange Server resources by clicking the Create an Exchange Mailbox check box on their User Properties dialog box.
Exchange Server is managed using the Exchange System Manager, which allows the network administrator to manage mailboxes and public folders (such as those holding distribution lists and other public contacts). Figure 13.8 shows the Exchange System Manager window.
FIGURE 13.8 The Exchange System Manager

The latest release of Exchange Server is 2007. Here are some of its features:
• Supports both IPv4 and IPv6
• Enhancements for operating with POP3 and IMAP4, including port settings (see Hour 14) and authentication operations
• Additional features for MIME support
• Quality of service (QoS) features
• Support for Secure Realtime Transport Protocol (SRTP)
Outlook is closely linked with Microsoft’s Office desktop productivity suite (products such as Microsoft Word, Excel, and so on). In a special folder called the Journal, Outlook can log all documents generated in Office for future reference. This allows a user to track her activity in relation to her use of other Office applications. Not only does the Journal track Office application use, but it can be set up to track activities within Outlook itself, providing a user with an even higher degree of organization.
The most current versions of Outlook (2003 and 2007) support the mail protocols (POP3, IMAP4, HTTP) as well as Microsoft’s proprietary Exchange-based mail systems. The products also offer groupware applications that you can download from the Microsoft website.
Since its introduction, Outlook has become a powerful mail client, and its groupware features have steadily become stronger. Here are a few examples for the features of Outlook 2007:
• Create and subscribe to Internet calendars. Users can add a static Internet calendar, subscribe to a dynamic Internet calendar, or create their own Internet calendars to share with others.
• Send calendar information to anyone with calendar snapshots. With calendar snapshots, Office Outlook 2007 creates an HTML representation of a user’s calendar so it can be shared with others.
• Publish Internet calendar to Microsoft Office Online. Users can create a new Internet calendar and publish it to share with others. Using Microsoft Passport credentials, you or your team can invite a group of coworkers, customers, and so on to view and work with your calendar.
• Customize and share electronic business cards.
• Prevent junk email and reduce exposure to malicious sites. New antiphishing features can disable threatening links and warn users about possibly malicious or phishing content within an email message.
• Improvement of graphical user interfaces (GUIs). The GUI screens are easier to view. The options presented on the screens are concise and unambiguous.
File Transfer and FTP
The Internet standards include a widely used file transfer system, called the File Transfer Protocol (FTP). As its name implies, FTP defines the procedures for the transfer of files between two machines. FTP also supports data transfer between a device other than the original server (and client). The operation is known as a third-party transfer.
If you have used FTP, the chances are good that some of its operations were displayed on your computer screen, usually in status indicators called FTP reply codes. For example, a code of “1yz” indicates a file transfer command is being acted upon. Of course, most users don’t care about such details, and many products, while capturing these codes, do not make them available on the GUIs.
FTP provides a file-sharing environment that can control access to the file server by requiring a login name and password. This means that the FTP server must validate a user and his password before he can access files on the server.
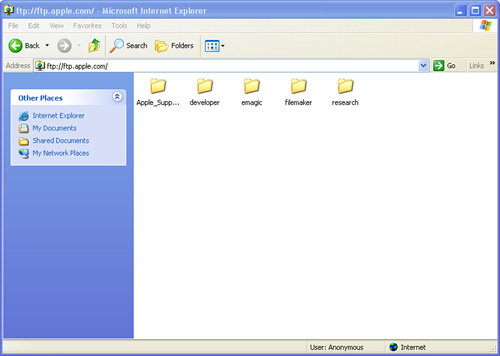
On the Internet, many public FTP sites allow an anonymous logon. Anyone can log on to the FTP site using a username of “anonymous.” The password for an anonymous logon is often your email address. A site allowing anonymous logons is referred to as an anonymous FTP site. Figure 13.9 shows Apple’s anonymous FTP site that has been accessed using the Internet Explorer web browser. Note that the command FTP replaces the HTTP in the address window because you’re accessing an FTP site rather than a website (HTTP).
Please note that on a Windows-based computer, the directories on the FTP site appear in the Internet Explorer window the same as local directories would. You are potentially accessing files that reside on a computer clear across the world, but the computer’s connection to the Internet makes the directories and files appear as if they are local.
Because we use web browsers to access anonymous FTP sites, most of us have never had to use an FTP client. Several FTP clients are available and can be used to access FTP sites without using a web browser. If you’re accessing FTP sites that require a username and password, you’ll need an FTP client. You can find a number of freeware FTP clients (and some demos for commercial software) on the web. Just key in File Transfer Protocol (FTP), and you’ll be presented a wide range of sites to visit.
FIGURE 13.9 Anonymous FTP sites are common on the Internet.
So, what are the flaws of FTP? And if there are many, why is it so popular? First, FTP is an old Internet protocol that was designed during the days when most Internet users weren’t concerned with security breaches. (How times have changed!) Thus, FTP isn’t set up to easily deny hackers access. That stated, additions have been added to FTP to ameliorate these problems. Second, FTP software logic, although well structured, consumes bandwidth during the exchange of several packets to set up the association between the two FTP users. Third, FTP employs two separate connections: one for control and the other for data transfer. In hindsight, this technique isn’t necessary and adds yet more overhead to the process.
So, why use FTP? Because it’s the accepted standard for transferring files between computers. Some other standards for file transfer made a go of it but were never successful. As long as you and your design team have addressed the security faults of FTP, you shouldn’t worry about using it.
I’ve used FTP for the submittal of manuscripts to book publishers, articles to magazines, and essays to a reader community. An FTP server is identified with a uniform resource locator (URL). The server contains a folder whose name I share with anyone who wants access to it. With an FTP server password, a party can open the folder and, at his leisure, access my material.
Summary
In this hour, we’ve explored network applications, with a special highlight on email and file transfer systems. We examined groupware concepts and some of the communication features provided by groupware products. We discussed scheduling, contact management, and file transfer. We also looked at some of the most popular groupware platforms.
Q&A
Q. What network model do groupware products embrace?
A. Most groupware products embrace a client/server model, where a desktop client is used to access information stored on a network server.
Q. Why are Internet/TCP/IP standard applications more desirable than applications that use proprietary communications protocols?
A. TCP/IP is a vendor-independent standard; applications that adhere to it can work with other TCP/IP applications. By contrast, proprietary systems require gateway protocol converters to communicate with other systems.
Q. What are some of the services that groupware products provide to users?
A. Groupware products provide email, scheduling, calendars, contacts, and other collaboration features.
