HOUR 4
Computer Concepts
What You’ll Learn in This Hour:
• How computers work
• The varieties of computer hardware
• Functions and operations of software
• Operating systems
Networks are made of computers in the same way a band is made of musicians. Each computer—and each band member—is unique, and in the right circumstances, they all work together to produce a fine performance. If they don’t, the result is chaos for the computers and cacophony for the band.
Similar to bands, networks require certain conventions be observed when computers are networked to interplay with each other. Although each computer is unique, it operates the same way as other computers on the network. If you understand how a computer works, you’ll be better prepared to understand how networks work. The analogy ends here, as I have never found a musician who operates the same way as another musician.
Anyway, keep in mind you’re not being asked to become a computer guru, but given that networks hook computers together, a basic understanding of a computer’s architecture helps to achieve a better understanding of networking.
Numbers, Magnitudes, and Fractions
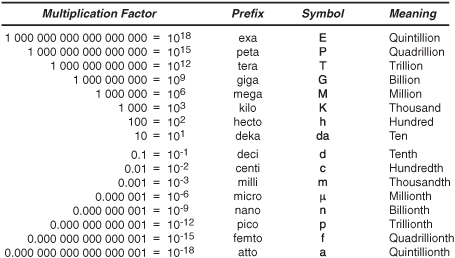
Of necessity, this book uses terms such as “giga,” “tera,” “nano,” and “pico” to describe the magnitude and precision of numbers. They can’t be avoided because computer networks are often described by their capacity, or the number of bytes (characters) or number of bits (0s and 1s) sent per second. For example, vendor literature about a high-capacity network cites a transmission “speed” of 10 gigabits per second, or 10Gbps and storage vendors refer to terabytes when discussing large file systems. Also, computers are often compared to how long it takes to perform a task. For example, access time for a disk might be 10 milliseconds, or 10ms. To help with these translations, Figure 4.1 lists common terms associated with the base 10 numbering system.
FIGURE 4.1 Common terms
Computer Hardware
Computers consist of two components: hardware and software. Hardware is the physical part of a computer. Software executes on the hardware. The hardware is usually stable and is infrequently altered. In contrast, software changes often. For example, as Internet users, we frequently receive alerts on our screens about a vendor wanting to download changes to a software product.
The two terms are self-descriptive: Hardware implies somewhat rigid components—not easily changed. Software implies flexible components—easily changed. Hmm, make that easily changed in comparison to hardware. Some software programs contain thousands of lines of code (which are instructions, such as “print,” “copy,” and “delete”) with many interdependent instructions. They may be easy to change, but they may not be easy to change correctly.
Firmware is a special type of software that rarely changes. It’s stored in hardware called read-only memory, or ROM. As its name suggests, ROM can only be “read” and not “written.” It can be changed, but only with special operations and procedures. Therefore, it’s neither “hard” nor “soft”; it’s “firm.”
Hardware, as you’ve probably guessed, makes up the physical components of a computer. It includes but is not limited to the following:
• CPU (central processing unit)
• Screen and keyboard
• Memory
• Disks
• Add-in components, such as network interface cards (NICs)
• Sockets, slots, and ports
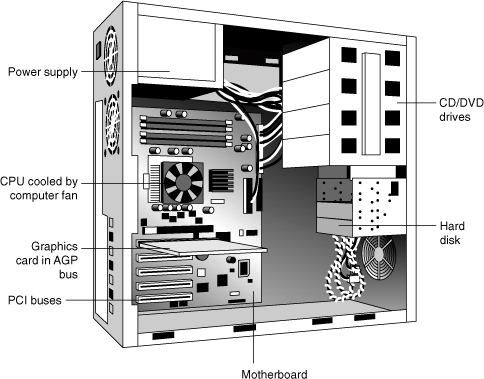
In the next few pages, we take a high-level tour of a PC. Although the descriptions will focus on an IBM-compatible PC (the most common kind of personal computer), the concepts presented here also hold for Macintoshes or any other computer designed with a modular, expandable architecture. Don’t be concerned about your specific PC, such as a Dell or an HP. Our descriptions are appropriate for any computer. Figure 4.2 will be helpful as we survey the innards of the computer.1
1 Source: Wikipedia, The Free Encyclopedia, subject: “Computer Hardware.”
FIGURE 4.2 Major hardware components in a PC
The CPU
When you remove the cover from a personal computer, the first thing you might see is a section of metal and ceramic, mounted on a circuit board. This component is the CPU, also often called the processor. The basic purpose of a CPU is to execute software programs, which are instructions the CPU uses to manipulate data stored in computer memory. The data may be an email, an Excel spreadsheet, a PowerPoint graphic, and so on. Whatever it is, the CPU, a powerful microprocessor, is the focal point for processing the data—as dictated by the software.
Motherboard
The CPU is usually placed on a circuit board mounted into a socket on the motherboard. A motherboard also provides connections through which internal components of the computer communicate. For example, it’s configured with ports to which memory is attached. It may also connect external peripherals, such as a printer.
The motherboard is aptly named because it’s the focal point for the “family” of hardware components inside the computer and those attached to the computer.
The CPU is the sine qua non for computing—without it, a computer is absent its oar and tiller. The CPU administers all the 1s and 0s coming from the keyboard, the mouse, the disk, the network, and whatever else we have on our computer. It then processes this data so we can accomplish whatever it is we want to accomplish—to see a display on a video screen, type a letter, create a spreadsheet. Whatever we do on a computer, the CPU is involved.
As stated, CPUs are microprocessors. The earliest microprocessors had only a few hundred transistors per chip. Modern microprocessors, such as Silicon Graphics, Inc.’s POWER4, contain more than 170 million transistors on a square the size of your thumbnail. The next generation of processor chips are projected to have more than 1 billion transistors—an enormous capability that will likely lead to architectures different from those discussed in this hour.
Microprocessors quickly execute instructions. For example, as I key in this sentence on my PC keyboard and perhaps execute a Save command for the text, my computer’s CPU is executing lines of software code designed to support my input—my commands to the computer. The CPU will take several-to-many cycles (iterations) to fulfill this task. It must fetch software instructions from computer memory, decode them, execute them, and store the results.
The CPU performs these rather prosaic operations at astounding speeds. The PC I’m using to explain this feature has a clock rate of 1.73GHz. This figure means the CPU is operating (cycling) at 1,730,000,000 times a second. Granted, multiple cycles may be needed to, say, save this sentence in memory. Nonetheless, a 1.73GHz CPU can perform thousands of operations—such as fetching a Web page, displaying a photo on a screen, and so on—in one second. Even more, modern computers are capable of executing multiple instructions per clock cycle, which translates into an even faster CPU than described previously. Consequently, “clock speed” alone is not used much nowadays to describe the actual processing power of a computer.
Let’s make a few more points about computer processors and their capacity. Other terms are used to describe the processing power of a CPU, such as instructions per second (IPS) and floating point operations per second (FLOPS). Experts who analyze computer capacity exercise caution in using these statistics alone for evaluating and comparing performances. Nonetheless, for our analysis, it’s instructive to note that in June 2008, a CPU achieved a 1 teraflop rate. That’s 1012 FLOPS!
A typical human spends several seconds (minutes?) performing numeric addition with pencil and paper, depending on the magnitude of the number. In computer terms, the human executes this addition at roughly 0.0119 IPS. One of Intel’s 3.2GHz processors performs 59,455,000,000 IPS for a comparable numeric addition. Needless to say, this CPU can do a lot of work in a short time.
What is more, a computer does not demand health benefits or ask for a pay raise. It doesn’t leave work early to pick up the kids. While we humans continue to raise the overhead incurred by businesses, computers continue to lower these costs. You think we will see fewer automated voice services and Web sites and more human interactions for our airline reservations and other purchases? Think again. We humans have flopped! Just consider:
• 1961—About $1,100,000,000,000 ($1.1 trillion) per GigaFLOPS
• 1997—About $30,000 per GigaFLOPS
• 2008: May—About $0.13 per GigaFLOPS
Memory
A microprocessor integrates most or all of the CPU on an integrated circuit (a silicon chip). However, not all chips are microprocessors. Some chips, called memory chips, are built as arrays holding the 1s and 0s the CPU is processing. Their purpose is to provide a place in the computer for the storage of data. The data can be accessed in any order (nonsequentially)—thus, the name random access memory, or RAM.
RAM is usually associated with volatile types of memory (often called dynamic, or DRAM), where data is lost after the power is switched off. However, some types of memory can keep a charge (and maintain the data) after the computer is turned off.
In spite of the differences in terms, all computer memory works in a similar fashion: Put a charge across memory, and it holds 1s and 0s for the CPU to access. The key point with respect to memory is to make certain the memory you purchase is the type your computer requires. Your user manual should provide this information. If you can’t find it, personnel in computer stores can help you. Of course, the manufacturer’s website can also provide this information. Should you call the vendor’s telephone for help? Good luck! Remember our recent discussion on the cost/performance differences between human and computer activity. Chances are, you’ll talk to a computer about computer memory.
Anyway, memory is also used to provide CPU access to data. If the computer had to read data from tapes or disks each time it needed the next batch of data or instructions, computers would be far too slow to be useful. But the use of memory, specifically RAM, has led to extraordinarily fast computers.
However, RAM is no match for the pace of the CPU because of the relatively slow speeds by which memory is accessed for data and instructions. CPUs can process code in 3 nanoseconds (ns). Memory access is roughly 100ns, a huge difference in speeds. Therefore, small memories, called caches, are located close to the CPU to provide data and instructions faster than conventional memory.
Memory is great for helping computers to operate efficiently. However, there’s one thing memory can’t do, which the next section explains.
Disks
Memory abets computer speed. However, RAM is volatile, which means that it only functions when the computer is turned on. Because RAM is made of chips depending on an electrical power source to store data, when the power is cut, it can no longer store anything. I doubt you want to retype everything every time you turn on the computer. There ought to be a way to store data so that it can be retrieved the next time you turn on your machine.
External storage devices were invented to store data, regardless of the state of the computer. One such device is called the disk (or hard disk). Disks fulfill two of the most common needs of the computer: They store data in a nonvolatile state (that is, the data stored on disks doesn’t disappear when the power is cut), and they act as additional (albeit slower) memory when the computer needs more memory (RAM) than is physically installed.
Disk storage is so named because data is recorded on round, rotating surfaces called disks. Prior to the invention of disks, almost all data was stored on cardboard (punch) cards or magnetic tape. For cards and tape, access to the data was sequential. Record 1 had to be accessed before record 2 could be obtained, and so on. The disk technology permits random access, which greatly facilitates the searching for a specific record. You can imagine the delay if a directory assistance operator in Los Angeles had to sequentially search a computer file to find the phone number of XYZ Corporation.
For many years, disk storage had a limited capacity. At the risk of dating myself, I cut my programming teeth on an ancient IBM 2311 disk. It stored 7.25 million bytes on one disk pack (six platters rotated as a single unit). The data transfer rate from the disk into computer memory was only 156 kilobytes per second (Kbps). The newer units in operation today store roughly 250 gigabytes (GB) of data. Their data transfer rate is 61.4 megabytes per second (Mbps).
Varieties of Disks
Modern disks for personal computers generally come in one of two varieties: IDE and SCSI. These variations entail different methods by which hard drives connect to computers. Because devices of one type are incompatible with devices of the other type, it’s important to know a bit about both of them.
Integrated Drive Electronics (IDE) (also known as Advanced Technology Attachment, or ATA) is a connection standard for hard drives that places the electronics that control the drive directly on the drive itself. IDE/ATA supports up to two drives connected to a single cable and disk sizes up to 528 megabytes (MB). A more recent version of the IDE standard, called Extended IDE (EIDE), can support larger disks; it is now common to see EIDE disks with capacities of up to 120 gigabytes (GB). EIDE is often called “Ultra DMA.” You’ll usually find these drives sold as ATA these days, but they’re just IDE with a different name, because the interface is the same as IDE. You might also come across the term SATA, for Serial Advanced Technology Attachment, which is an enhancement to ATA in offering faster transfer rates.
Solid State Drives (SSDs)
You should also investigate the possibility of using solid state drives (SSDs). They use solid state memory for the storage of data. As of this writing, they are more expensive than conventional disk units, but for some applications the extra cost may be justified. They are much faster than rotating disks and emit no sound. For applications needing very fast response times, SSDs might be worth their expense.
Small Computer System Interface (SCSI)
The small computer system interface (SCSI, pronounced “skuzzy”), shown in Figure 4.3, is a standard for connecting peripheral devices to a computer. SCSI enables 8 to 16 devices to be connected to the computer in a chain (that is, on a single bus).
FIGURE 4.3 The SCSI connector
![]()
Each device on a SCSI chain has a number called (not surprisingly) a SCSI ID, which enables the computer to locate that device when needed. Each end of the SCSI chain must be terminated, which means that a special device called a terminating resistor must be plugged in to the end of the cable. The terminating resistor ensures the electrical characteristics of the cable remain consistent along its length. SCSI comes in a variety of speeds ranging from 5Mbps to 300Mbps. With some exceptions, SCSI is backward compatible, which is a fancy way of saying that old devices can connect to newer SCSI controllers and still work (although the entire SCSI bus slows down to the speed of the slowest device to which it’s connected).
Of course, peripheral devices, such as disks, don’t operate on their own; they must connect to something in the computer, which is the subject of the next section. Also, in Hour 11, “Selecting Network Hardware and Software,” this subject is revisited with some recommendations on which disk technology might fit your network.
Expansion Cards
At the beginning of this hour, we learned the CPU fits into the motherboard through a socket. In addition to the socket for the CPU, the motherboard provides interfaces for after-market devices. These devices, which fit into expansion slots on the motherboard, are called expansion cards (as well as expansion boards, adapter cards, or accessory cards).
Whatever they are called, they are electronic assemblies connecting to a computer through a standard interface called a card slot. Adapter cards provide a variety of services to the computer, including video, network, and modem operations.
It is safe to make the claim that without IBM’s decision to adopt a modular design for its initial personal computer, and the computer industry’s following suit, modern personal computers would not have become the powerful and adaptable machines that they are today. The modularity and adaptability of the IBM PC drove the personal computer’s explosion of popularity in the early 1980s. In fact, the computer industry’s rapid growth can be attributed to the adapter-card standards promulgated by IBM for the early PC.
Adapter cards handle an array of functions, including the following:
• Network adapters connect computers to the network.
• Video adapters provide a way for the computer to display images on a video monitor.
• Drive controllers connect hard drives to the system.
• SCSI controllers connect any devices that use the SCSI interface to the computer.
• Sound and video cards enable a variety of media types—from CD to MP3—to be played on a computer.
This list is not comprehensive; it doesn’t include all the different types of adapter cards. Nonetheless, it does cover the devices you’re likely to encounter in a common computer. Although most motherboards have expansion slots, the expansion slots on all motherboards are not the same. Various computer manufacturers have devised different interfaces for cards used in their systems. For Intel-based computers, the most common slot designs are, in order of age from oldest to youngest, ISA, EISA, and PCI. ISA stands for Industry Standard Architecture, which was what IBM called this interface when it created it in the early 1980s. As of this writing, ISA, EISA, VESA-Local Bus, and several other slot interfaces are considered to be obsolete technologies.
Peripheral Component Interconnect (PCI)
PCI is the current interface standard, supplanting several older interfaces. PCI came about from an initiative by Intel to allow add-in adapters to run almost as fast as the system in which they’re installed. The interface into the motherboard can be an integrated circuit fitted onto the motherboard, or it can be an expansion card that fits into a socket.
Typical PCI cards used in PCs include network cards, sound cards, modems, USB or serial ports, TV tuner cards, and disk controllers. In the past, video cards were PCI devices, but growing capacity requirements for video have outgrown the capabilities of PCI. However, PCI cards are widely deployed in devices such as modems. The chances are good that the modem in your PC is PCI based.
Network Cards
To connect a computer to a network, a network card is installed into the computer. Other terms used for this hardware are network adapter card or network interface card (NIC); the terms are synonymous. Network cards are available from a variety of manufacturers and in a variety of interfaces including Ethernet and Asynchronous Transfer Mode (ATM), which you might recall from Hour 3, “Getting Data from Here to There: How Networking Works.” Thus, an NIC operates at Layers 1 and 2 of the OSI model. What is more, every LAN NIC contains a MAC (Ethernet) address.
Because of the near-universality of Ethernet, most companies now offer a network interface as part of the motherboard, either with a dedicated Ethernet chip (connected through a PCI) or with the Ethernet protocol integrated into the motherboard hardware. A separate network card is not required unless multiple interfaces are needed or some other type of network, such as ATM, is used. Newer motherboards sometimes have dual network (Ethernet) interfaces built in.
You will find network cards easy to install. Typically, just turn off the power to the computer, open the case, find a slot that matches the card’s interface (usually ISA, EISA, or PCI), center the card above the slot, and press the card firmly into the slot to seat it. Mission accomplished; turn the computer back on. When the computer is fully running, you can install device drivers. These software components (described in the second part of this hour) enable the computer to communicate with the device. After the device driver software is installed, you usually have to restart your computer one more time to connect to the network. When in doubt, read the accompanying manual!
Video Adapter Cards and Monitors
If you ask people to identify “the computer,” some will point to the monitor on their desks rather than the casing containing the CPU. Although they would be incorrect in defining a monitor as the computer, they would be making a point that we do well to heed. Human beings are visually oriented creatures. In general, visually striking images garner more attention than drab impressions. The computer box beside your desk just doesn’t create visual interest, which explains why manufacturers such as Apple offer the CPU in bright colors. It adds visual relevance to a machine. It also sells computers.
By contrast, the monitor is visually interesting because it’s colorful and full of motion. Computer monitors get attention out of proportion to the amount of actual work they do. The keyboard and mouse are where the user’s part of the work is done; the system box does the computing, but the monitor is what we see and therefore what we respond to.
Because what we see on a video monitor screen is such an important part of how we interact with computers, the video adapter card, or video card, is an important part of the system. Video cards convert the digital information the computer uses internally to a format for display on a computer monitor. The image on the screen is made up of pixels (picture elements). Think of a pixel as a small image on a grid, represented by bits (1s and 0s).
The number of bits needed to describe a pixel is called bit depth. The “shallowest” bit depth is 1. One binary bit can represent one of two states (1 and 0), a technique for monochrome monitors. A bit depth of 2 can describe four colors, and so on.
The minimum standard for video displays on Intel-based computers is called VGA, or video graphics adapter, which is a baseline, antiquated standard. Of more interest are the modern standards. For example, a display operating in SuperVGA (SVGA) mode can display up to 16,777,216 colors because it supports a 24-bit-long description of a pixel.
At the high end of quality are monitors with a bit depth of 32 bits (SuperVGA + Alpha Channel), a special graphics mode used by applications needing an even better picture, such as animation and video games. This procedure uses 24 bits for describing the color of the pixel and 8 bits for describing its light diffusion (the translucency of the pixel). You’ve seen these pixels displayed on the more expensive monitors. They produce beautiful, even stunning displays.
The Universal Serial Bus (USB)
Just a few years ago—a long time in the computer industry—computer manufacturers often designed and built vendor-specific ports on computers. (The term port is used here to describe the “plug,” or the “connector” on the back or side of a computer.) For example, Apple’s mouse port was Apple specific and prohibited an IBM mouse from plugging into it.
Fortunately, several influential standards groups succeeded in promoting the use of standard ports for certain interfaces. One set of prominent data communications standards was (is) the Electronic Industries Association (EIA) specifications. The EIA spearheaded the standardization of ports for data terminal equipment (DTE), such as a PC, and its connection to data communications equipment (DCE), such as a modem.
Notwithstanding these efforts, vendor-specific ports led to compatibility problems, resulting in the inability to “plug and play” various peripherals from other manufacturers. Not only were the “plugs” different, the device drivers (discussed shortly) were manufacturer specific. For a nontechnical PC user (most of the population), finding the correct driver for a peripheral was akin to diving into a technical black hole. In addition, many of these interfaces wouldn’t allow a peripheral device (such as an external hard disk) to be connected or disconnected without restarting (rebooting) the computer.
In the mid 1990s, several influential computer companies participated in developing the Universal Serial Bus (USB) specification (thanks to Intel, Microsoft, Philips, and US Robotics). Apple’s iMac G3 (1998) was the first computer built with USB ports. Today, the USB interface (see Figure 4.4) is commonplace and has replaced not only manufacturer-specific interfaces, but other standardized plugs and receptacles as well.
FIGURE 4.4 The USB

USB is a serial (one bit at a time) bus standard for interfacing peripheral devices with a computer. It allows hot swapping: connecting or disconnecting devices without rebooting the computer. It supports up to 127 device connections per host and can operate at a data transfer rate of 1.5 to 60Mbps. It permits a host to connect to multiple downstream USB ports though USB hubs, which is similar to a branching tree structure. The limit is five levels of tiers. A host can have multiple host controllers attached to it.
To reduce the number of manufacturer-specific interfaces, USB defines 19 classes of devices. A specific class describes how a device is to “behave”—that is, how it is to communicate with its attached computer. Consequently, the same interface (connector, cable, and software device driver) can be used by any device that adheres to the protocols for that class. As one example, Class 07h sets the behavior for printers, regardless of whether they are made by Dell, Apple, or IBM.
Furthermore, a computer’s operating system (OS, discussed in the next section of this hour) is supposed to support all USB device classes. Just a few years ago, it would have been impossible to buy a digital camera without an accompanying CD, which was filled with software to allow the camera to communicate with the computer. Now, and as another example, Microsoft’s Vista operating system includes support for device class 06h (digital camera). So does a Canon camera. They interwork, transparently to a user! (I use an exclamation point in the last sentence. The readers who have been in the industry for a while will understand why.)
USB and FireWire
FireWire, published as IEEE 1394 by the Institute of Electronic and Electrical Engineers, defines a high-speed serial bus to connect peripherals to a computer. So does the USB specification. The two standards differ in their technical “behavior,” and we need not concern ourselves with these details. Your network can do just fine with USB unless your applications need a lot of capacity (in bits per second) and are time sensitive. Examples are advanced audio and video systems. You will pay more for FireWire because it outperforms the less expensive USB.
Operating System (OS) and Other Software
Computer hardware is an intriguing subject. But left to itself, it’s little more than electrically charged, but otherwise inert assemblages of metal, silicon, and other high-tech mucilage. For this hardware to be effective, for it to “compute,” it needs software.
Indeed, computer hardware is designed to operate with software, a set of instructions that informs the hardware the tasks it is to undertake to support an end-user’s application, such as email. An operating system, or OS, is the baseline software enabling users and their applications to interact with computer hardware. If hardware is the body of a computer, the operating system is its brain.
There’s no technical reason why each program couldn’t contain an OS and control the operations of the hardware. But this approach would be foolhardy because the OS frees application designers from having to delve into the intricacies of the physical architecture of the computer, which into itself is complex.
The OS also offers consistent user and programming interfaces and standard ways of doing simple tasks such as copying data between applications, writing a memo, editing a photo, or placing a song on an iPod. Applications invoke OS services with application programming interfaces (APIs), also known as system calls. An API can pass parameters, such as data, to the OS and receive parameters informing the application about the results of the operation. For nonprogrammers, a user can invoke the OS from a keyboard, a mouse, or by touching the screen. For the mouse and screen functions, the OS provides a graphical user interface (GUI, pronounced “gooey”).
Common operating systems—those you might have come across—are Microsoft’s Windows and Vista, Apple’s OS X, UNIX, and Linux.
There are several types of operating systems. The following list is a general categorization. The OS on your computer may use combinations of these categories.
• Single-tasking systems—Performs one task at a time. (A task is also called a process. It is an instance of a software program currently being executed. An example is an addition operation or a print operation.)
• Multitasking systems—Can run several tasks simultaneously and allows programs from multiple users to share in the use of the CPU and other hardware. Typically, the OS gives each user or user-support program a “slice” of time. The swapping of tasks occurs so quickly that the operations are transparent to the user.
• Single-user system—Used by one user at a time on one machine at a time.
• Multiuser systems—Supports many simultaneous user sessions on one computer.
• Multiprocessing systems—Some computers have multiple processors (CPUs). If so, different programs might run on the different processors.
Multitasking
An operating system might use one of two types of multitasking: cooperative and preemptive. The latter approach is found in more of the prominent OSs than the former.
Cooperative multitasking prevents the OS from making all decisions about which applications’ tasks are given system resources, such as the CPU. When an application is done with a task, resources are passed to another application. Preemptive multitasking has the OS making the decisions about which program gains use of the systems resources. Preemptive multitasking is the model used in Linux, UNIX, Microsoft’s Windows enterprise operating systems (Windows 2000, XP, 2003, and so on), and NetWare.
What Happens When a Computer Is Turned On
When a computer is turned on, we immediately see images and text on the screen informing us our pressing the “on” button was successful, and activities are underway to allow us to use the machine. During this time, the computer is preparing its hardware and OS to support the applications we later invoke when we click on an icon.
Generally, this startup process—dubbed by the industry as “booting the computer”—entails the execution of firmware from read-only memory (ROM), often called boot ROM. This firmware first loads program code from a disk and then executes the code, which is called a boot loader. The boot loader’s task is to load the most critical parts of the OS, called the kernel, and start the kernel running. The kernel’s name is appropriate, because it is central to the OS and remains in memory while the machine is turned on. It is responsible for the most basic tasks, such as input/output (I/O) management of attached peripherals, memory management, CPU allocation, and regulating the processes and tasks to support users’ applications.
Let’s assume you’re informed your machine is now at your disposal. Windows displays a colored (sort of) window. A MAC shows off an abstract smiley face. You want to log onto the Internet, so you click an icon on the screen identifying your Internet service provider (ISP). This simple action results in the loading of ISP software from your disk and scores, perhaps hundreds, of supporting software “routines.” Thereafter, as you interact with this software and the Internet, the OS keeps track of all these resources by
• A unique identifier for each of the software processes that is executed to support your session. It is called a process ID (PID).
• A list of memory locations the program is using or is allowed to use. Some memory is reserved for the OS and other critical “nonapplications.”
• The PID of the program, which requested the execution of this program. This identifier is called the parent process ID (PPID).
• The filename from which the program was loaded.
• A file containing values of all CPU storage locations for this program. This isn’t conventional memory. It’s implemented with special hardware called registers.
• A program counter, indicating which code in the program is currently running.
Complex? Yes, but it’s quite logical. Unlike humans, well-designed computer hardware and software can always be understood because all of it operates...yes, logically. Let’s pause for a moment and examine the items in this list and compare them to a common human activity: taking a commercial fight on an airplane. The airline keeps track of its resources (flyers) by
• A unique identifier for each of the people on the flight. It is called a reservation number.
• A list of seats on the plane that a flyer is allowed to use. Some seats are reserved for the crew and first-class passengers.
• The name of the person who set up the reservation. This identifier contains credit card information.
• The airline flight number from which the person began the journey, to check of lost luggage, for example.
• A list containing information on all passengers (especially, after 9/11). This is not conventional data, but privileged information.
I can’t stretch the analogy to the sixth operation, but the point to this comparison is to recognize that the seemingly complex activities of a computer’s OS is akin to many of our daily tasks: keeping an account of what’s going on.
OS: The Transparent Workhouse of the Computer
During a session on a computer, the user should not be aware of the activities of the OS. What is more, it would be unusual if you must delve into OS operations on your computer. For that matter, this statement also holds for the OS in other machines that may be part of your network, such as the router interfacing your machine to the Internet. If error messages appear on your screen informing you of a problem with your operating system, your best move is to “move” the computer to the nearest OS expert—perhaps the nearby computer shop. Some of my nontechnical friends and colleagues have attempted to fix an OS problem. Not only were they never successful, but on some occasions they made matters worse.
That stated, the integrity of modern operating systems is quite good, especially when compared to only 10 years ago. It’s no small feat for the OS to manage all the hardware and software on a modern computer. Recently, I ran virus detection software on my PC and kept a window open that informed me of the number of identifiable files the virus software examined. By “identifiable,” I mean a file with a Windows name, such as “C:Uyless BlackNetworking in 24 HoursHour 4.” After the scan was complete, I was informed 162,976 files were scanned. Bear in mind that many of the files contain programs, emails, photos, videos, slide presentations, spreadsheets, and so on. That’s a lot of things to keep in proper working order.
One more point about the operating system and other software. I suggest you allow each manufacturer to download changes to its products. If you block these updates and “fixes,” you’ll find yourself operating with an out-of-date system. This could become a problem because an outdated OS might contain problems (bugs) and might not have the latest security enhancements.
Examples of Operating Systems
To conclude the discussion on operating systems, this section highlights several of the more widely used products. First, we discuss Microsoft’s Windows and Vista.
Windows and Vista
Microsoft Windows is a family of operating systems. In November 1985, Microsoft introduced Windows as an add-on to MS-DOS in response to the growing interest in GUIs and complaints about the poor user interfaces furnished by MS-DOS—especially compared to Apple’s GUI. Windows now dominates the world’s personal computer OS market. Estimates vary, but most surveys claim Windows has roughly 90% of market share.
Microsoft takes the approach that an OS for the home (with inexperienced users) should not be the same as an OS for the office (experienced users or a competent support staff). Having worked extensively in both environments, I think this philosophy is sound. Most home users don’t need the power and complexity of an office-oriented OS. Nor do they need the price tag associated with a richer OS.
With each release of Windows, the product has improved. (With Windows 95 (1995), Microsoft OS began supporting preemptive multitasking.) Microsoft’s OSs have been criticized for many years for their “user unfriendliness” and lack of functionality. I agree with some of these complaints, but it should be noted that Mr. Gates and company began their OS work using MS-DOS and had to keep aspects of this OS as part of their future operating systems. Anyway, with the 2001 introduction of Windows XP, Microsoft gained praise for its OS.
Microsoft also entered the server market in 2003 with Windows Server 2003. Today, Windows Server 2008 is slated as its successor. Because servers play a key role in computer networks, they are discussed as separate subjects in Hours 5, 10, 14, and 15–18.
Vista is slated to replace Windows XP. It offers many new features, including a new GUI, more powerful search tools, and support for multimedia applications. It simplifies file sharing and makes it easier to install a home network. Perhaps the biggest change from XP is better security features, a subject for Hour 20, “Security.”
Mac OS
In the early days of Windows, many Macintosh users complained Microsoft had “stolen” the look and feel of the Macintosh. These users apparently didn’t know Apple’s nifty GUI contained a lot of features first developed at Xerox’s Palo Alto Research Center (PARC). As mentioned in an earlier hour, I visited PARC in 1982 to evaluate Ethernet. I was astounded when I saw PARC’s GUI, including trashcans and icons of files. I cannot say if Steven Jobs took PARC’s ideas. But I can say the two were remarkably similar...and PARC’s GUI came first.
Anyway, in 1984 Apple invented the Macintosh OS, also called the System. It had a clean and sparse interface, well suited to nontechnical users. These features, combined with the Macintosh’s reputation for freeing the user from concern about computer hardware and obscure MS-DOS commands, led users to develop a near-fanatical devotion to Apple. (I was one of those fanatics. Unlike MS-DOS applications, Apple had—for that time—an extraordinary graphics package called MacDraw. I bought my first Mac because of MacDraw. The next day, I terminated contacts with graphic artists who had been hand-drawing the illustrations for my books.)
Mac OS initially came with a proprietary network called LocalTalk, which was upgraded to become AppleTalk. It was a layered architecture, quite similar to the OSI seven-layer model explained in Hour 3. With the rise of the Internet, MacTCP arrived and replaced AppleTalk. Thereafter, Mac users could connect to the Internet using the TCP/IP protocol suite.
Apple has rewritten its operating system software to create OS X, an OS constructed around the UNIX-based microkernel. It’s a preemptive operating system that acts a lot like a high-end UNIX technical workstation with a user-friendly interface. It’s proven quite reliable and has made further inroads into the artistic/technical community.
UNIX and Linux
The final operating systems we examine for computers and computer networks are UNIX and Linux. UNIX began as an experiment in a Bell Labs computer lab in 1969 and is now a popular server and workstation operating system. AT&T made UNIX available to anyone under liberal license arrangements. The licenses included all the source code, which was an unheard-of practice at that time. Early on, the Internet TCP/IP protocol stack was included in the package, which further spawned its use (and helped foster the relatively new Internet standards).
UNIX runs on almost every type of computer ranging from Intel compatibles to high-end multiprocessor transaction servers used by banks, public safety agencies, and other institutions. It bears mentioning that the owner of the trademark is The Open Group. Only systems fully compliant with and certified to the Single UNIX Specification are qualified to use the trademark.
UNIX, like its younger sibling Windows NT, is a preemptive operating system. As mentioned, unlike every other operating system we’ve discussed, it’s often shipped with the source code (the set of instructions written in a computer language such as C). Most commercial operating system vendors don’t provide source code because they believe it’s proprietary. With UNIX, you often get the source code, which means that if you can program a computer, you can customize the operating system.
Since the mid 1990s, a new variant of UNIX called Linux has sprung up and received a lot of attention. Linux is a UNIX-like operating system written in such a fashion as to evade the copyright restrictions on UNIX while retaining its look and feel. From a cost/benefit perspective, Linux is an attractive operating system.
Renowned for its use in servers, Linux is supported by many companies. It operates in a variety of machines, including computers, E-book readers, DVRs, video game devices, mobile phones, and routers.
As network clients, UNIX and Linux perform quite well. Their default network protocol stack is the TCP/IP model, which is the set of protocols used on the Internet. UNIX (or Linux) servers are the foundation of most of the Internet’s web servers. We’ll take a closer look at UNIX and Linux in Hour 17, “UNIX and Linux Networking.”
Device Drivers
A device driver is a software module operating on behalf of a device, such as a scanner, a printer, a disk unit, and so on. It permits other software programs to interact with the device and usually communicates with the device through the computer bus. When a program requests a service, say to access data on an external hard disk, the driver issues commands to the disk. Once the disk sends data back to the driver, the driver may inform the program of the activity, as well as cause the application to take other actions. Drivers are very hardware dependent and operating system specific. It’s at the device driver level where products become the most specific to a manufacturer.
Device drivers are quite important to the overall architecture of a computer because they isolate the application programs and the operating system from the many details of a specific piece of hardware. For example, an application program might have a line of code instructing the computer to print a document. The code might be “WRITE,” “PRINT,” or “PRINTLN” with a parameter in the code identifying what’s to be printed. A Hewlett-Packard printer requires a different command than a generic PRINTLN, as does an Apple Computer, and so forth. The driver accepts generic software commands and converts them into the specific commands the device uses.
Summary
At the beginning of this hour, we noted it’s helpful to know a bit (or byte) about the computer to understand certain aspects about computer networks. This hour was written to assist you in doing just that.
If you don’t have a general understanding of how a computer works, what the parts of a computer are, or what an operating system is, you can still build your own network. After all, for small networks, vendor products are often “plug and play.” Nonetheless, if you’ve grasped the concepts presented in this hour, you’ll make networking your systems a much easier task. Okay? Let’s see how you did.
Q&A
Q. Which of these components consist principally of software: CPU, OS, device drivers, Windows, RAM, ROM, disk, UNIX, memory, applications, Vista?
A. OS, device drivers, Windows, UNIX, applications, and Vista consist primarily of software.
Q. What is the purpose of cache?
A. Cache provides for a higher-speed memory to reduce the speed differences between the CPU and main memory. Remember, cache is placed closer to the CPU than the memory modules, which reduces the time of the data to “travel” back and forth between these components.
Q. Which computer component connects internal components, such as memory, as well as external components, such as printers?
A. It’s the mother of all boards: the motherboard!
Q. Which of these computer components likely has an Ethernet address associated with it: CPU, cache, network interface card (NIC), device driver, OS?
A. The network interface card (NIC) likely has this. The very name of this component should have given you a hint. After all, we’ve learned that Ethernet is a networking standard.
Q. Fill in the blank: If hardware is the body of a computer, __________ is the brain.
A. If hardware is the body of a computer, the operating system is the brain.
