HOUR 7
Mobile Wireless Networking
What You’ll Learn in This Hour:
• Basic concepts of mobile wireless networks
• The prominent mobile wireless standards
• Cellular systems
• Wi-Fi (Wireless Fidelity)
• Bluetooth
• Basics of security issues
• Implementation considerations
During the past six hours, we have made frequent yet general comments about wireless networks. Because they are a major component in modern networks and because you will likely deploy them in your own internet, it’s appropriate we provide more details about them.
The emphasis in this hour is on mobile wireless networking. Fixed networks, such as a nation’s microwave systems, are important, but they are not covered here because of their transparency to your networks. For example, you might have leased a DS3 line across the United States, but you will not know if AT&T is placing your DS3 payload over microwave or cable. On the other hand, wireless networks such as Wi-Fi, Bluetooth, and cellular most likely will be quite evident in your operations.
Understanding Wireless Networking
The options for wireless networking have greatly increased over the past few years. As one example, thousands of public wireless networks are now installed in hotels, coffee shops, and airports—“hot spots” available for our use. As another example, longer-distance wireless communications can take place through cellular telephone technology and satellite systems. That’s good news for users, especially with the recent explosion of local area network (LAN) wireless standards and products, because most are centered on Wi-Fi and Bluetooth, which are readily available to all of us.
The major difference between a wired network and a wireless network is how computers or other devices, such as personal digital assistants (PDAs), connect to the network at Layer 1 of the Internet/OSI model. Wireless installations use radio or infrared signals to send and receive data. Use of the radio spectrum is more common, so let’s center our discussion on radio networks.
A computer must be outfitted with a network interface card (NIC) that can send (and receive) data as a radio wave (rather than as an electrical signal over a wire). To connect to a network, a device must be installed to connect the computers and other machines. In a wired network, the device is a hub, bridge, router, or switch. In a wireless network, the central connecting device is called a wireless access point (WAP). The WAP can also be a hub, bridge, router, or switch with both wireless and wire-based ports. Thus, most access points provide for wireless connectivity as well as port connections to a wired network, such as the Internet.
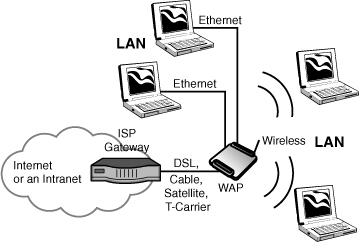
A network combining wired and wireless connectivity is often referred to as a hybrid network. Figure 7.1 shows the layout for a hybrid network.
Typically, wireless routers include a WAP, an Ethernet switch, firmware for IP forwarding, Network Address Translation (NAT), and the Domain Name System (DNS) to interwork with a WAN gateway. The wireless router allows wired and wireless Ethernet devices to connect to a WAN device such as a DSL modem. This modem is often a network card inside the router.
A wireless router can be configured through a central utility. If you are installing a WLAN to attach to the Internet, your ISP will provide this service for you, most likely from an ISP web server.
FIGURE 7.1 A typical hybrid network
When you will not be communicating with a WAN, you might opt for a wireless network bridge. This device operates at L_1 and L_2 of the layered model. This configuration can be useful for connecting two Ethernets, say, in two separate homes or offices. A wireless network bridge is simple to use.
Let’s make one more general point about the subject. Wireless repeaters can extend the reach of an existing wireless network. Repeaters allow the signal to propagate around barriers and corridors. Be aware that each repeater will add latency for each hop, and the end-to-end throughput will be limited by the lowest-capacity link in the chain.
A Brief History of Mobile Wireless Networks
Mobile wireless networks in America appeared 80 years ago. On April 7, 1928, the first mobile radio system went into operation in Detroit, Michigan. These early systems required enormous bandwidth. A 120-kilohertz (KHz) spectrum was required to transmit a voice signal of only 3KHz. By the 1960s, technology supported a “modest” 30KHz voice channel.
The mobile phone you likely have nearby as you read this sentence is a relatively new technology. In the United States, it was first implemented as a national service in 1983. This first generation (1G) mobile phone (the Advanced Mobile Phone System, or AMPS) used 30KHz of bandwidth. What’s more, AMPS was built around analog technologies. The voice signals were sent over analog waveforms—no discrete 0s or 1s in those days. Nor did AMPS have significant capabilities for sending data between computers. A few specialized devices allowed some data applications, but they were limited in their capabilities.
In the early 1990s, the industry began migrating to second-generation systems (2G). The major features introduced then are those we have in our third-generation (3G) cell phones today, as described in the following list. (By the way, 1G is now obsolete, and 2G is rapidly decreasing in use.)
• All images are digitized into binary bit streams of 1s and 0s.
• It uses less bandwidth than 1G networks.
• It supports video and data applications.
• It enables use of small phone sets.
• It provides higher-quality signals.
• It provides better security.
• It might provide interfaces to the Internet (and the Web) using the Internet protocols.
• It might support email.
• It provides text messaging.
In comparison to wire-based broadband, the 2G and 3G bandwidth are more limited. The bit rate varies, depending on network conditions and specific implementations, but a mobile phone user will not obtain the throughput and response time of conventional DSL and cable modem links.
As mentioned, the mobile wireless industry (usually called the mobile phone industry) is entering into 3G technology. One goal of 3G is to provide for a higher transfer rate for each user. The 3G standards stipulate different data rates, depending on the Layer 1 technology. For example, the international standard CDMA2000 defines a maximum data rate of 307 kilobits per second (Kbps).
Is this bad news? Yes, if we are to depend on the conventional mobile phone channel for high-capacity support. Fortunately, other wireless technologies are readily available that offer more bandwidth and are examined later in this hour.
The Cell Concept
Many wireless systems, including those just described, are implemented with the cell concept. A cell is a geographical area using low-power radio frequency transmitters. Low-power devices cannot send signals over long distances, which permit frequencies to be reused in nonadjacent cells. Given the finite frequency spectrum and the continuous jousting for radio bandwidth among the wireless service providers, frequency reuse is an important capability. Without frequency reuse, cell phone markets would be of such a small capacity that the limited customer base could not pay for the cost of building and maintaining the network.
The mobile phone communicates with the cell’s base station (a control facility with sending and receiving antenna) on control channels. These channels are predefined frequency bands reserved for call management traffic. Using the control channels, the base station (with guidance from a remote control center) assigns the mobile phone a specific frequency to be used for a call. For 2G and 3G systems, the phone is also assigned a specific slot of time it can use on that frequency. Thus, 2G and 3G permit multiple users to be multiplexed onto one physical radio channel.
Using the control channels, the phone user can dial up a party and then employ the user channel for ongoing communications. During the time the mobile phone is within a cell, the base station is monitoring the phone’s signals. If the base station detects that the signal is growing weaker, it requests the control station to determine whether the phone unit is moving out of the base station’s cell coverage. If it is, the network sets up procedures for an adjacent cell to take over the call—an operation that is usually transparent to the mobile phone users.
The worldwide mobile phone system is an elegantly simple set of networks. The mobile phone users’ locations are maintained (continuously, if the phones are turned on) by the mobile network providers working together to exchange information about the locations of all the mobile phones. In addition to phone numbers, other identifiers and locator information are exchanged between the providers to keep track of the mobile customers.
Therefore, not only can a mobile phone network hand off calls between cells within a network, it can hand off calls between cells across networks. When you first turn on your mobile phone, a service provider in the local cell picks up your phone’s signal on a control channel, which carries its phone number, its ID, and the ID of your service provider. In a matter of seconds, this local provider has sent a packet to your provider about your new location. Your location is then continually updated.
When you turn off and then turn on your phone, its location is reupdated. Don’t like Big Brother watching? Then don’t use a cell phone.
The mobile cellular phone network is an extraordinary technology. As the industry migrates to 3G, cell phones will be increasingly used for higher-quality video, data, and graphics applications. As well, more and more cell phones are being outfitted with native-mode Internet capabilities.
Now let’s examine several prominent wireless network standards and products and see how we can use them to enhance your network.
Wi-Fi
The Wi-Fi technology (published in the IEEE 802.11 standards) is used as a low-cost, limited-distance connection. But nothing precludes Wi-Fi use over greater distances with higher power and more expensive components. For this discussion, the emphasis is on the former technology.
Wi-Fi uses a spread spectrum radio technology. Spread spectrum was developed by the military to guard against enemy radio frequency jamming and eavesdropping. Spread spectrum spreads the signal across a range of frequencies in the public bandwidths.
• Frequency hopping spread spectrum (FHSS)—As this name implies, using a set pattern, the partnering mobile devices simultaneously hop from frequency to frequency. The receiver can receive frequency hopping spread spectrum data only if the sender and the receiver use the same hopping pattern (which is controlled by a hopping-sequence algorithm that is established during an initial session handshake). According to FCC rules, no transmitter can stay on a single band for more than 0.4 seconds within a period of 30 seconds for the 2.4GHz band. Each transmitter must also cycle through 50–75 radio bands before restarting the hopping-sequence algorithm.
• Direct sequence spread spectrum (DSSS)—In DSSS, the transmitter modifies the data with “chips,” or extra data bits inserted into the data stream. Only a receiver that knows the algorithm for the insertion of chips can decipher the code. Because of the effect of the chips, the effective throughput of DSSS is currently limited to 11 megabits per second (Mbps) in the 2.4GHz band.
The Wi-Fi implementations 802.11b and 802.11g use DSSS. Bluetooth (which is discussed in the next section) uses FHSS.
Although the 802.11 standard provides for a number of different specifications for wireless networking, these L_1 specifications are the more prominent:
• 802.11a—This standard provides up to 54Mbps of throughput and operates in the 5GHz band of the radio spectrum. (Because of overhead, a user can reasonably expect a throughput of around 25Mbps.) The 2.4GHz band is more popular; thus, 802.11a might experience less interference. Keep in mind these higher frequencies are more prone to error and cannot as easily penetrate walls and other solid objects. Also, as of this writing, public networks (public “hot spots”) use the 2.4GHz band.
• 802.11b—This specification provides a maximum data rate of 11Mbps and operates in the 2.4GHz band, utilizing DSSS. However, 802.11b devices have been known to suffer from other machines operating in this band. For example, your baby monitor might get in the way of this Wi-Fi component. Nonetheless—and this interference is rare—802.11b is extensively deployed throughout the world.
• 802.11g—This specification provides 54Mbps (with about 20–25Mbps of net throughput) in the 2.4GHz band. It’s currently the fastest growing implementation of 802.11 wireless specifications for home networks and small LANs.
The 802.11 wireless specifications are collectively referred to as Wi-Fi (Wireless Fidelity). To promote 802.11 as the standard for wireless (there’s another possibility that is discussed in a moment), the Wi-Fi Alliance, a nonprofit organization, was formed by a number of the companies that provide 802.11 wireless technology and services.
One more point about 802.11a. This technology does not use FHSS or DSSS. It uses a multiplexing scheme called Orthogonal Frequency Division Multiplexing (OFDM). OFDM splits the radio signal into numerous subsignals that are transmitted simultaneously at different frequencies. This enables a large amount of digital data to be broken into chunks and then transmitted.
Don’t Overlook 802.11n
During your evaluation of WLAN options, make certain you examine the latest offerings for 802.11n. As of this writing, 802.11n products are beginning to appear in the marketplace. Make sure you and your team factor in this technology because it offers up to 600Mbps transmission rates—a significant improvement over the other Wi-Fi technologies.
But be careful. For testing and research purposes for this book, I purchased an IEEE 802.11n-compliant router (as advertised in the router vendor’s literature). I discovered the machine didn’t yet support this Wi-Fi specification. The technical “help desk” informed me the company had experienced some problems with 802.11n. I suggested that it might consider having the technical teams occasionally meet with the marketing department.
Bluetooth
Although not currently a competitor for WLAN implementations, another wireless specification shares the same 2.4GHz bandwidth range as 802.11: Bluetooth. Bluetooth was created in 1998 as a standard for connecting mobile devices (such as PDAs) by a number of companies (such as IBM, Nokia, and Toshiba) interested in mobile computing strategies. Bluetooth was initially designed as a strategy for implementing a personal area network, or PAN—meaning the Bluetooth specification is intended to be used on devices we use on a daily basis, such as phones and printers; and personal convenience devices, such as PDAs.
The Bluetooth visionaries conceived a wireless environment that would surround us while we went about our daily chores, allowing us (and our tools) to be freed from the constricted wired world. Wireless phones, wireless disks, wireless coffeemakers, skillets, and toasters—all controlled by a wireless “server” that contained loads of breakfast-making software in the OSI application layer. This futuristic automated kitchen is not yet a reality, but in our hurry-up, fast-food world, it’s probably in the building contractors’ floor plans.
Anyway, Bluetooth is an open standard (as is 802.11) and can provide a transfer rate of 1Mbps. The net data rate depends on which other protocols you use with Bluetooth. Later versions support higher data rates. If this issue is important to you, check for the following: Version 1.2: 1Mbps; Version 2.0: 3Mbps. You might also check out an emerging proposal referred to as the WiMedia Alliance, which is in the process of defining a much higher data rate. As of this writing, the specific bit rate has not been defined.
Bluetooth provides a lot of possibilities for providing communication links between handheld computing devices, mobile phones, and other devices, such as wireless headsets, keyboards, printers, bar code scanners, PlayStations, and graphic pens. There’s also talk of developing Bluetooth into a full-blown LAN infrastructure medium (which would make it a competitor to 802.11).
Bluetooth is designed for low-power consumption, which, of course, results in a short-range signal area. Thus, its range is power-class-dependent: Class 3: approximately 1 meter, Class 2: approximately 10 meters, and Class 1: approximately 100 meters.
As long as the received signal is powerful enough for translation, Bluetooth devices can be located in different rooms. During start-up, the nodes execute the Link Manager Protocol (LMP) to set up the wireless link (an L_2 protocol). During this phase, the devices authenticate each other and negotiate the size of the packet to be exchanged. The Service Discovery Protocol (SDP) is also employed to perform handshakes to determine the type of device and the types of services each device supports.
You won’t have to be concerned with the details of the Bluetooth protocols. They’re mentioned to give you a better appreciation of the power and flexibility of Bluetooth, and to once again show how useful the OSI/Internet layered model is in explaining computer networking technology.
Are Wi-Fi and Bluetooth in Competition?
Wi-Fi and Bluetooth are not competitors. Their “place” in the networking picture—based on their characteristics—has been well thought-out by their developers. Wi-Fi is more expensive, yet it provides for a greater signal area and higher data throughputs. They both use the same frequency spectrum, but, as noted earlier, they use different techniques at L_1 for sending and receiving signals.
Wi-Fi is an attractive alternative to wire-based LANs. Many homes and companies use it to obviate pulling Ethernet cable between rooms. Bluetooth can be used to replace USB-type connections, such as keyboards, flash RAM, printers, and cameras.
Frequency Interference Between Wi-Fi and Bluetooth?
As stated earlier, 802.11 and Bluetooth use the 2.4GHz band as defined under Part 15 of the U.S. Federal Communications Commission Rules and Regulations. Bluetooth devices should not interfere with Wi-Fi devices because Bluetooth uses FHSS and 802.11 uses DSSS.
However, this equipment can be affected by interference from microwave ovens and cordless telephones. The chances are slight, but keep that possibility in mind when you’re nuking your coffee in the morning while talking on the Bluetooth phone set.
Security Considerations with Wireless Networks
The common procedure to protect traffic over a wireless channel is to encrypt the user data. Hour 20 provides information on encryption in general. For this discussion, the focus is on wireless channels specifically.
Wireless networking makes many folks squeamish because of security issues. After all, we’re sending our data into the air, making it a possible target for eavesdroppers. Data sensitivity has become increasingly important to those in the medical field because of HIPAA (Health Insurance Portability and Accountability Act) regulations related to the protection of patient information. Even a dentist with a small practice might think twice about implementing a wireless network in the dental office because patient data might be at risk.
Because of the vulnerability of “air data,” wireless networks have a security strategy. WEP (or Wired Equivalent Privacy) is a protocol executing in the MAC sublayer of the data link layer (L_2) of the Internet/OSI model. WEP encrypts the data sent from point to point on the WLAN using a shared secret key. This means that WEP is in force as data moves from a wireless client to an access point or to another wireless client. Keep in mind: If the data enters a wired LAN, the WEP protection ends.
In the early 2000s, WEP was used in many products, but it was found to be vulnerable to hacking. Thus, Wi-Fi Protected Access (WPA-2) is in many products today and offers better protection. Nonetheless, you should check your system to determine if the data is encrypted, because some products default to a clear mode (encryption free) of operation. If the Wi-Fi product itself doesn’t provide this level of security, you can secure your data by other means. In Hour 20, we explore these alternatives.
Implementation Considerations
Implementing a wireless network is not much different from implementing a wired network. You must plan your network layout and then acquire the necessary hardware to get the network up and running. You should plan for growth, security, and all the other issues that you would plan for if you were implementing a wired network. We won’t get ahead of ourselves about this subject, as Hours 9–19 contain a lot of information about network implementations. But a few comments specific to wireless networks are in order.
In terms of network size and growth, keep in mind that Wi-Fi implementations such as 802.11b are inexpensive and fairly easy to set up. However, they provide limited bandwidth. Also, the more users on the network, the less the throughput and the longer the response times will be (which, of course, is true with any network). So Wi-Fi shouldn’t be considered to support a large base of users. For this community, you should use wired Ethernet.
The number of access points you decide to deploy depends on the number of users. Each access point provides specifications for the number of users who can connect to the access point without suffering drops in performance and reliability.
As you plan your Wi-Fi network, keep in mind the range of the medium. Indoors, you’re looking at ranges of 150 to 300 feet (the maximum distance from a client to an access point), unless you install repeaters. Building construction can also affect the range, so consider setting up test equipment before you outfit all your users with Wi-Fi hardware.
You must determine the access point range boundaries in your building and between your buildings, which will help you determine the number of access points you will need to accommodate your users. Also, allow some overlap between the access point range boundaries so that users can roam within the building or between buildings.
Regarding hardware, many products are available for both access points and Wi-Fi network interface cards (NICs). For small networks, companies such as Linksys and D-Link provide access points and wireless NICs. Many of the access points provide firewall capabilities, and some (designed for home use) have parental control capabilities for Internet connections.
For larger networks, companies such as 3Com and Cisco provide high-end access points for enterprise networking. For example, Cisco offers products simultaneously supporting Wi-Fi standards 802.11a, 802.11b, and 802.11g.
Make sure you research and test your Wi-Fi hardware as you would hardware for a wired network. A good starting point for more information about Wi-Fi is the Wi-Fi Alliance at www.wi-fi.org. This organization provides information on Wi-Fi standards and provides information on Wi-Fi-certified products, Wi-Fi network implementation, and other Wi-Fi-related news.
Summary
In this hour, we discussed wireless networking. Starting with a brief history of cellular systems, we covered the elegant efficiency of the wireless cell concept. We examined wireless standards such as the IEEE 802.11 and the Bluetooth specifications. We looked at the different implementations of 802.11 and Bluetooth, and methods for securing a wireless network. We concluded the hour with some recommendations on implementation strategies.
Q&A
Q. What type of device can you use to interwork a wireless network with a wired network?
A. The wireless access point (WAP) is the key device for this interface. It often contains an Ethernet switch, firmware for IP forwarding, as well as address translation and domain name services.
Q. List the major differences between a wireless Ethernet and a wire-based Ethernet.
A. The differences between the two are as follows:
• Wireless Ethernets are easier to install.
• Wireless Ethernets are more subject to security breaches.
• Wireless Ethernets usually have less throughput capacity.
• Wireless Ethernets are more apt to suffer from signal degradations.
• Wireless Ethernets are vulnerable to channel interference.
Q. How does frequency hopping improve security and reduce channel interference?
A. Because of the frequent changing of transmit and receive frequencies, it will be highly unlikely that an unauthorized party will be able to monitor another’s traffic. As well, it will be unlikely that two senders are sending on the same frequency at the same time.
Q. Wi-Fi and Bluetooth use the same frequency spectrum. So why does your Wi-Fi PC not interfere with your Bluetooth toaster?
A. These devices do not interfere with each other because (a) they use different spread spectrum techniques, (b) they employ protocols that allow them to understand they are not allowed to send/receive traffic to/from each other, and (c) a smart Wi-Fi PC would never condescend to communicate with an obtuse Bluetooth toaster.
