HOUR 1
An Overview of Networking
What You’ll Learn in This Hour:
• Definition of a computer network
• Why we need computer networks
• Components of a network
• Different types of networks
• Importance of the Internet
Computer networks have become part of our everyday lives. We use them to take cash from the local ATM. Whenever we send email or browse the Web, we rely on the world’s largest computer network, the Internet, to be our electronic mailman. Telemarketers, usually during dinner hour, use computer networks to sell us their wares. Our cable television stations rely on computer networks to transport programs onto our TV screens. What is a compelling example of their presence in our lives? Without computer networks, our cellular phone is little more than a battery powering-up a meaningless screen.
To provide these extraordinary services, computer networks transfer data to and from our TV sets, personal computers, cell phones, and other modern machines. This data is then translated by applications into video TV images, icons on PC screens, and text messages on cell phones. These network tasks take only a second or so (often less) to be completed—even if the network must fetch data from around the world. Why watch a science fiction movie? A computer network is equally impressive.
Although data networks, like computers, have become an integral part of our lives, most people consider computer networks too complex a subject to even consider setting one up. Usually, we resort to a nearby geek squad to help us, or we bring in specialists from our company’s networking department.
But let’s leak a secret—one these technical “whizzes” would like not to be known: Networking is not all that complicated. It doesn’t require a membership in a secret society. Unless you choose to become a software programmer or a hardware designer, unless you choose to build a network from scratch, you have no need to devote years of study to be able to set up and manage your own network.
In the past, managing networks did indeed require in-depth experience and training. And make no mistake: This book will not give you sufficient information to manage the Internet! But now, with the proliferation of millions of networks and network users, the industry provides tools to allow you to not only understand computer networks but to set them up and manage them effectively.
Gaining the ability to create a computer network requires an understanding of a few fundamental concepts, the nuts and bolts of data communications. Coupled with the pliers of common sense—and reading this book—you can assemble your own network.
What Is a Network? What Is Networking?
In simplest terms, a computer network consists of two or more connected computers. This connection is twofold: (a) physical, through wires, cables, and wireless media (the atmosphere with, say, cell phones), and (b) logical, through the transport of data across the physical media. We discuss the components required to make the physical connection in several parts of this book; notably, Hours 4, 10, and 23. The logical connections are discussed throughout the book.
In the context of this book, what is networking? If I say to someone, “I’m networking!,” what does this declaration mean? For starters, it doesn’t mean I’m socializing with co-workers or mingling with parents at the local PTA. It means I’m sitting at a computer, communicating with someone or something via a computer network. Fine, but you don’t need to do 24 hours of reading to teach you how to sit at a terminal and play online Scrabble.
Thus, Sams Teach Yourself Networking in 24 Hours is a shorthand title for teaching you how to build a network so that you can later do networking.
As suggested, there’s more to networking computers than physical connectors, such as electrical plugs in the wall and ports on a PC. Several basic rules must be followed if the computers are to exchange data with each other.
• The machines in the network must use the same procedures for sending and receiving data. These procedures are called communications protocols. If these devices do not (or cannot) use the same protocols, conversions must take place, usually with services called protocol converters. The idea is akin to someone who translates between a person speaking Spanish and a person speaking English. For computer networks, I can send my son an email from my wire-based computer to his Internet cell phone.1 For my son (Tommy) to read this message, conversions are performed at the physical level (wire-based images to wireless-based images) and at the logical level (email format to text format). Fortunately, you will not have to deal with protocol converters. They are provided for you automatically.
1 As of this writing, not all cell phones support Internet sessions, but the trend is in this direction.
• The data must be delivered without corruption. That is, if I key-in “Hello, Tommy” in my email, it must (and will) be received at his cell phone as, “Hello, Tommy,” and not, say, “Hello, Mommy.”
• A method must be in place whereby the receiving computer (By the way, a modern cell phone contains at least one computer) can acknowledge the receipt of uncorrupted data and inform the sending computer if the data was indeed received in error. Thus, if Tommy’s machine receives “Hello, Mommy,” Tommy will never see this error appear on his screen. Unbeknownst to Tommy, a piece of software will check the data and return a message to my computer asking for a retransmission. I also will not know about this wonderful service. What is more, because all these dialogues are taking place so quickly (in a few fractions of a second), Tommy and I are unaware of the short delay in our ongoing dialogue.
• Computers on a network must be capable of determining the origin and destination of a piece of information, such as an email or a text message. After all, if Tommy wants to send a response to me, the network must be able to route it to my computer, and Tommy’s device must provide the address to the network. Once again, you usually don’t need to be concerned with these tasks. Addresses are often assigned to you automatically. As we shall see, it is yet another service provided to network users.
• Obviously, standardized addresses are required for the correct exchange of data between computers. Because millions of computers around the world can be networked, these addresses must be “scalable” to accommodate a large computer population.
• For security and management, there must be a method for identifying and verifying the devices connected to a network. Hackers must be prevented from damaging computers and files.
This list is not an exhaustive set of network requirements and, as stated, to obtain most of these services, you need not lift a finger to your keyboard or keypad. We’ve listed them to give you an idea of some of the issues faced when computer networking gurus tackle the task of exchanging and sharing data between computers. As seen earlier, for data transfer among computers to take place, rules must be followed. Otherwise, the process is akin to people attempting to speak to each other in different languages.
Networks can be as simple as a point-to-point connection between two computers transferring files to each other. Networks can also be quite complex. One example that comes to mind is the Federal Reserve’s system, which allows us to electronically transfer funds between accounts. Another is the cellular network. It tracks us as we move across a terrain and hands off our connection to the next wireless tower in a “cell” where we have recently moved.
Despite the fact the point-to-point example is much simpler than the bank and cellular examples, each has to follow the same basic rules to permit users to communicate with each other. We will explore both simple and complex networks in this book.
However, before we delve into the details of a computer network and how to set one up, we should pause and answer this question: Why would we want to build a network in the first place? I suspect you have your own answer; otherwise, you would not be reading this book. Permit me to offer some thoughts on the matter; perhaps they are the same as yours.
Why Build a Network?
If we’re happy with receiving or sending information by hand, we can resort to the postal service. But hard copy correspondence is called “snail-mail” for good reason. It’s far too slow in today’s accelerated world. By the time a letter arrives, its contents are often old news.
• In contrast, a computer network enables faster communications between parties. In so doing, it leads to more efficient use of time.
• By sharing electronic data among perhaps thousands of people, a computer network encourages (requires!) the use of standard policies and procedures. After all, our personal computer and our text-proficient cell phone have no inferential power as we humans do. We can just respond with, “Say again please,” if we don’t understand a transmission. But a computer network must be laboriously programmed to perform this one simple task. However, and once again, these standardized procedures lead to more efficient communications.
• Networks provide backup and recovery support for our data. If the postal service’s mail truck breaks down, our letter might be delayed for a day—at least. Not so for a computer network. It’s designed to provide near-instantaneous recovery from a failure—all without a loss of a single character or number in our (electronic) mail.
• “I’ve lost that file!” “I’ve lost the letter!” These lamentations are no longer true with computer networks. If networks are properly designed, it’s easy to store copies of our data. Be it mail, photographs, files, or video, we can keep copies safe and sound on another computer in another part of the country—if we take the time to instruct the network to do so.
• Shared resources lead to less expensive communications. Take the Internet, for example. It’s an expensive public network (in reality, millions of interconnected networks), but we use it for a few dollars a month, and its performance is such that we might consider it our own private network. That is, we think we have this network for ourselves, but we don’t. A term to describe this fine service is virtual private network.
As many reasons exist for using computer networks as there are people sharing them and organizations building them. One person might have a bunch of computers at home—one for her, one for him, several for the kids. She may want to hook all the computers together so the family can have a common calendar and email, which, as we know, the kids will more readily read than the note on the fridge. Another person may want to connect his small office or home network to the Internet to use the Web. Yet another person in Texas may to play Texas Holdem with his friends living in New Jersey.
Computer networks have transformed the way we work and play. For better or worse, they’ve changed our lives. I trust that you think the change is for the better. I do. But we’ve said enough about why we use computer networks. Let’s now see how they’re used, and more to the point, how we can use them to improve our personal and professional lives.
How Networks Are Put Together
To repeat an important point, if we were to break down a network into its simplest components, these components would be identified as one of two categories. One is the physical network. It consists of the wiring or wireless medium; the network cards inside the computer that interface with the “plugs” on the computer; and, of course, the computers themselves (which might take the form of mail servers, file servers, and other machines discussed later). The other category is the logical part of the network. Usually implemented in software, it provides the means to build those parts of the network with which we “interface.” Examples are email, text messaging, web pages, videos, and the images on our computer screen. We introduce these components during this hour, and they are covered in more detail in coming hours.
The Network Architecture: Combining the Physical and Logical Components
When computers are connected, we must choose a network architecture, which is the combination of all the physical and logical components. The components are arranged (we hope) in such a way that they provide us with an efficient transport and storage system for our data. The network architecture we choose dictates the physical topology and the logical arrangements of the system. For example, if I say, “I’m building a Switched Ethernet network,” this statement implies the overall architecture of my future network. Let’s now examine these physical and logical components.
The Physical Network
The physical network is easy to understand because it’s usually visible. Mainly, it consists of hardware: the wiring, plugs such as computer ports, printers, mail servers, and other devices that process and store our data. The physical network also includes the important (read: vital) signals that represent the user data. Examples are voltage levels and light pulses to represent binary images of 1s and 0s—strung together in many combinations to describe our data.
I say “usually visible” because we can’t see wireless connections. Although more ethereal than copper wire connections, wireless connections are nonetheless physical, taking the form of electromagnetic radio waves.
Quite rare only a few years ago, wireless networks such as Wi-Fi are now common. If you have a broadband connection in your home, chances are good your computer is connected to your broadband hardware device with a wireless arrangement. How we explain the layout (also called a topology) of a wireless network is no different from that of a wire-based network.
Physical Layout—Network Topologies
As mentioned, the physical aspect of the network consists of the components that support the physical connection between computers. In today’s networks, four topologies are employed: (a) star, (b) ring, (c) bus, and (d) cell. They are depicted in Figure 1.1.
FIGURE 1.1 Network topologies: (a) Star topology, (b) Ring topology, (c) Bus topology, (d) Cellular topology
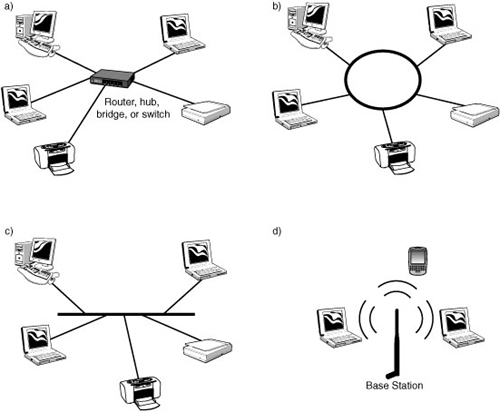
• Star—The star topology employs a central connection point, called a router, hub, bridge, or switch. The computers on the network radiate out from this point, as seen in Figure 1.1(a). The job of the central point is to switch (relay) the users’ data between user machines and perhaps other central connection points. The terms router, hub, bridge, or switch are used interchangeably by some people. Generally, the terms hub and bridge are associated with devices of a somewhat limited capacity. The term switch has historically been associated with telephone networks (with the exception of the 1970’s computer network message switches and 1980’s packet switches). The term router found its way into the industry in the 1980s and is now used more frequently than the other terms. Whatever we call these machines, they manage traffic on the network and relay this traffic back and forth between our computers.
• Ring—The ring topology, shown in Figure 1.1(b), connects the computers through a wire or cable. As the data (usually called a packet) travels around the ring, each computer examines a destination address in the packet header (similar in concept to a postal envelope’s “to” address) and copies the data if the computer’s address matches its address. Otherwise, the computer simply passes the packet back onto the ring to the next computer (often called the next node). When the packet arrives at the originating node, it removes the packet from the ring by not passing it on.
The ring topology is the first example of a broadcast network: Nodes in the network receive all traffic in the network. Whether a node chooses to accept the packet depends on the destination address in the packet header.
• Bus—The bus topology is shown in Figure 1.1(c). It consists of a wire with taps along its length to which computers connect. It is also a broadcast network because all nodes receive the traffic. The sending node transmits the packet in both directions on the bus. The receiving nodes copy an image of the packet if the destination address matches the address of the node. The packet rapidly propagates through the bus, where it is then “terminated” at the two ends of the bus. As you may have surmised, packets traveling along this bus may interfere with each other if the nodes relay the packets onto the bus at about the same time. The bus topology handles this situation with a collision detection procedure. A node keeps sending until it detects its transmission has occurred without interference (by checking its own transmission).
• Cellular—The cellular topology is employed in wireless networks, an arrangement shown in Figure 1.1(d). Cellular networks use broadcast protocols; all nodes (cellular phones) are capable of receiving transmissions on a control channel from a central site. A wireless control node (called the base station) uses this common channel to direct a node to lock onto a specific (user) channel for its connection. During the ongoing connection, the cell phone is simultaneously communicating with the base station with the control link and the user link.
The Logical Network
The previous section explained the physical layout of networks, such as the star topology. In explaining how packets of user traffic are moved across these topologies, we have also explained the logical aspects of a network. Again, the logical parts of computer networks entail the invocation of software to “propel” the packets across the physical media and to receive them at the other end.
Unlike the physical network, the logical network is not visible. It uses the physical network for transport of data. We defer describing the details of the logical network here, as it is described extensively in almost every subsequent hour.
Two Varieties of Networks: Local and Wide Area
The topology of a computer network is an important feature of its composition. Another is the geographical composition: the network’s coverage. That is to say, how far does it extend? The span of a network—its physical girth—often dictates how it goes about sending, receiving, and otherwise managing data.
LANs
A local area network (LAN) is so-named because the nodes are in close proximity to each other, usually within a building or inside a home. In the past, the procedures (protocols) employed to manage a LAN depended on the nodes being close to each other—within a kilometer or so. The older Ethernet bus topology is an example of this distance-limited idea. Another way to describe a LAN is that it is usually a private network. It is owned, operated, and used by a company or an individual, to the exclusion of other companies and individuals.
Also, in the old days (a couple decades ago), a LAN was noted for its “high-speed” capacity. The original Ethernet LAN sent and received data at 10 million bits per second (bps)—a phenomenal transfer rate in those days. Today, this capacity and beyond is enjoyed by both LANs and wide area networks (WANs), discussed next.
The term “speed” to describe (1) a high-capacity system (2) offering fast response times is just fine. Speed in this context describes the rate at which data is transmitted or the measurement of how long it takes for a function to be performed.
WANs
As their name implies, wide area networks (WANs) are geographically scattered. They are usually connected to local networks with a router. This machine relays the packets between computers, which often reside on LANs, as seen in Figure 1.2. Access to a WAN is obtained with a dial-up telephone line or with a broadband link, such as a Digital Subscriber Line (DSL), a cable TV link, or a satellite link. The dial-up option, although widely used, is quite limited in its capacity, perhaps operating at only 56,000bps. In contrast, broadband links transport data in the megabit per second (Mbps) range. Once you’ve used broadband, you likely won’t be happy with dial-up. Downloading a web page on a dial-up line might take several minutes, in contrast to a broadband link, which takes a few seconds.
FIGURE 1.2 LANs and WANs
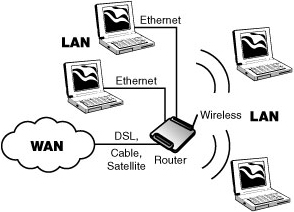
The term “broadband” can be confusing. Strictly speaking, it refers to the frequency spectrum with a broad band of frequencies, but it also describes a network or communications link that sends and receives data at a high bit rate, such as 4,000,000bps. If eight bits are used to comprise a character, such as the letter A, this broadband link can accommodate 1/2 million alphabetic characters per second (4,000,000/8 = 500,000). It’s easy to understand why broadband is so popular.
WANs are often public networks. That is, they’re available to anyone who wants to use them and pay for their use. The telephone system is a WAN public network facility. So is the Internet. Some WANs are private networks, owned and operated by companies or other enterprises. An example of a private WAN is a bank’s ATM network. Typically, the bank leases communications links from a communications carrier, such as AT&T, and then installs its own ATM machines and routers, configuring them for its own unique requirements. As a bank customer, we can use the ATM network, but we can’t connect our computers to it. In this regard, it’s a private network.
Examples of Network Topologies, LANs, and WANs
Insofar as possible, we’ve avoided using buzz words to describe network topologies. It might be helpful to associate specific names with these topologies, but you can skip this section if you prefer. Here’s a list of common computer networks and their associated topologies; all will be examined in subsequent hours:
• Star networks—Switched Ethernet (LAN); Asynchronous Transfer Mode (ATM) (LAN or WAN); Frame Relay (WAN); the Internet (WAN); Synchronous Optical Network (SONET) (WAN)
• Ring networks—Token Ring (LAN); IBM Token Ring (LAN); Fiber Distributed Data Interface (FDDI) (LAN); Synchronous Optical Network (SONET) (WAN)
• Bus networks—Ethernet Bus (LAN); Token Bus (LAN)
• Cellular networks—The cell phone networks (WAN); Bluetooth (LAN); Wi-Fi (LAN)
How the Internet Relates to Your Network
The most widely used data network in the world is the Internet, which is a public WAN. We gain access to it by paying a monthly fee to an Internet service provider (ISP) such as AOL or Verizon. Our interface with the ISP is with a dial-up link or a broadband connection. The ISPs have contractual arrangements with each other for the purpose of exchanging traffic with their respective customers.
The Internet owes its origin to the pioneering endeavors of the U.S. Department of Defense. During the 1960s, the Advanced Research Projects Agency (ARPA) was tasked with creating a government network to facilitate the exchange of information between various agencies and universities. Eventually, the ARPANET evolved to the Internet of today. This extraordinary network consists of millions of connected networks, such as the LAN in your home or office. According to www.internetworldstats.com/stats.htm, 1.5 billion people are now using the Internet (sometimes called the Net for short).
The ISPs manage their respective part of the Internet with routers, servers, and firewalls and play the vital role of informing other networks and providers about their customers. This procedure is elegantly simple. An ISP advertises its customers to the Internet by sending out information. For example, a packet, sent to practically any ISP in the world, states, “Uyless Black can be reached through me.” In so doing, the ISP advertises my name (such as UylessBlack.com) and an address to reach me (such as a network ID and an end user ID).
Connecting to the Internet
Until a few years ago, the prevalent method for connecting to the Internet was through POTS (plain old telephone services). These dial-up connections are still popular, but they are of limited capacity. Increasingly, Internet users are migrating to broadband services provided by the telephone and cable TV companies, as well as satellite and cellular companies.
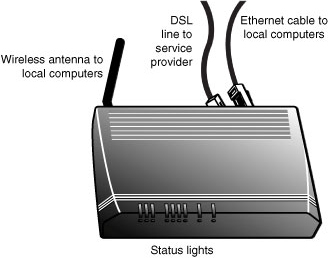
Figure 1.3 shows an example of a machine that can connect users’ computers to the Internet. It is called by various names because it provides a multitude of services. First, it is a modem. A modem (from modulator/demodulator) provides the physical transmissions for the connection, such as voltages and frequencies. Second, it acts as a firewall; that is, it attempts to block unwelcome visitors from intruding into users’ computers and files. Third, it performs the functions of a router. For example, this machine can support several computers’ Internet sessions with both remote and local computers. It “routes” traffic back and forth by examining addresses in each packet. Fourth, it is a wireless (cellular) machine. The antenna and associated components in the machine send and receive traffic within a LAN—in this situation, our home or office.
FIGURE 1.3 A router and attached links
Why the Internet Matters
At the risk of stating the obvious, the Internet has transformed the way we do business. Prior to its inception, it was quite difficult to transfer data from one computer to another—unless that computer toed the line and used the same proprietary procedures as the sending machine. For example, IBM marketed its own suite of protocols, as did other vendors. None of them could communicate with each other. The data communications industry was operating in a Tower of Babel. It was suffering from serious compatibility problems, with the resultant loss of productivity.
To their credit, many international organizations had standards used by hardware and software vendors. The modem and fax standards, published by the International Telecommunications Union (ITU), were adapted by all modem and fax manufacturers. But this is not the situation for data communications protocols. For example, the ITU’s Open Systems Interconnection (OSI) protocols never caught on. The OSI protocols suffered from unnecessary complexity and from the fact that the standards (the documents) were “owned” by the ITU. But, as discussed in Hour 3, the OSI model itself is still widely used and cited by the industry.
In contrast, the Internet’s protocols are designed for simplicity. What’s more, they’re “open.” Anyone can use the Internet specifications without paying a red cent for them. These standards are codified in the Request for Comments (RFCs). They are the Bible of the Internet and the bedrock of data communications networks.
Later we will examine several of the Internet data communications protocols. I suspect you’ve already come across many of them. Does TCP/IP ring a bell? You may not know, but these communications protocols run in your computer each time you log on to the Internet. We won’t get ahead of ourselves but will return to the Internet several times in this book.
Intranets, Extranets, and internets
The Internet (uppercase I) is the public network we use to send email and browse the Web. If we use the Internet protocols (such as TCP/IP) in a private network, we have created an internet (notice the lowercase i). Some vendors and associated literature use the term intranet to describe a private network that uses the Internet protocols. (Another term is extranet.)
Today, many businesses use the Internet to connect their internets with their customers, suppliers, and business partners. When implemented with proper security measures, Internet-internet associations provide a tremendous value to an organization. They dramatically reduce the costs of “doing” networking. The open, noncopyrighted standards of the Internet have been an extraordinary technical and financial blessing to the data communications industry and to our wired world. The virtual private network, introduced earlier, owes its existence to the Internet.
Summary
In this hour, we’ve learned about what computer networks are and how they operate. We’ve also come to know a bit about bits, bandwidth, and bits per second (bps). We’ve explored network topologies, local and wide area networks, and the Internet and internets.
Q&A
Q. What is a computer network?
A. A computer network is an organized collection of computers linked together for the purpose of exchanging data with each other.
Q. What are the different topologies used on computer networks?
A. The topologies are star, ring, bus, and cellular.
Q. Given the information gleaned from the previous question and answer, what is another variety of a computer network?
A. The composition of a computer network is further distinguished by its geographical situation: local or wide area; and its “openness”: private or public.
Q. What is the relationship of the Internet to an internet?
A. The Internet is a public network. An internet is a private network that uses the same procedures (protocols) as the Internet. By using common protocols, internets can readily communicate with each other through the Internet.
