Chapter 10
Communications Systems and the Importance of Communication in an Emergency
Abstract
This chapter presents information about the importance of effective communication and the variety of communication devices that are available, including two-way radios, telephones, cell phones, and intercoms. The appropriate techniques for radio etiquette (identify yourself, right channel, etc.) are addressed. The security officer should maintain a professional tone at all times when communicating on a given device. The importance of having contact information for all personnel who need to be notified during an emergency is emphasized.
Keywords
Intercoms; P.A. systems; Phonetic alphabet; Two-way radiosAn essential part of any security officer’s job is the ability to communicate quickly, efficiently, and in a manner that is completely understood by all parties. To achieve these objectives, security officers will rely upon a variety of communication devices, including two-way radios, telephones, and intercoms.
Two-way radio communication
Two-way radio communication is regulated by the Federal Communications Commission. Security officers should use proper radio etiquette when transmitting messages. Two-way radios are used for fast communication. Therefore, long conversations should be avoided. If a security officer needs to speak at length to the base operator or to another security officer, the radio should be used to notify the second person of the need to communicate (Figure 10.1). The second person should be instructed to call the other officer using a telephone. It is important to remember that when two people are using a radio frequency to communicate with one another, no one else who is in the vicinity can use the frequency. It is critical that communications be held to a minimum and used only for essential communication.
Proper techniques for two-way radios
When using two-way radios, security officers must follow proper techniques:
1. Be certain how the radio works.
2. Know the identification number of your radio unit and that of the base station.
3. Know how to identify yourself when calling.
4. Know what channel the radio should be on.
5. Check your radio at the beginning of each shift.
6. If at a fixed post, know if the radio should remain in the battery charger when not in use.
7. Be sure there is an adequate supply of backup batteries.
8. Know if you should use earphones and shoulder microphones.
9. Know how the radio should be carried:
a. Clip or belt
b. Holder
c. Held in hand
10. Be certain who else has radios and may be listening to your conversation.
When using a two-way radio, a security officer should hold the radio near his or her mouth and speak calmly, deliberately, and in a normal tone of voice. The security officer should identify himself or herself prior to making a statement or asking a question; for example, say “Unit 20 to base, do you copy?” or “Unit 20 to base, please respond.”

The security officer should wait for 5 seconds to allow proper time for the base station operator or other officer with a radio to respond. Usually, the response will be something such as “Unit 20, this is Base…”
The security officer should then clearly and distinctly speak to the base: “Base, this is Unit 20. I have a person requesting to see Mr Jones. He states he has an appointment. Please advise.”
Often, because of past experience, two security officers can communicate with two-way radios and not waste a great deal of time, nor do they need to say everything for the other person to understand their message.
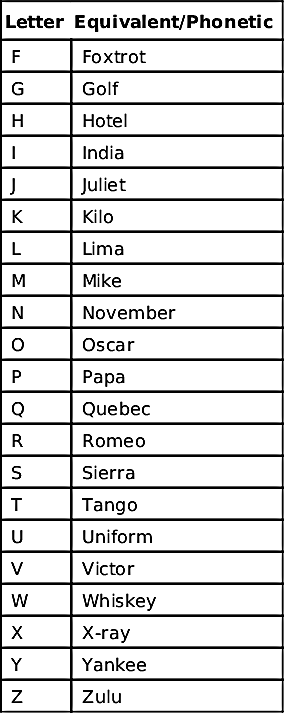
Abbreviations are often used in order to expedite conversations when using two-way radios. Additionally, certain words may be misunderstood because of similarity in sound to other words. Therefore, the phonetic alphabet was designed by the military:
| Letter | Equivalent/Phonetic |
| A | Alpha |
| B | Bravo |
| C | Charlie |
| D | Delta |
| E | Echo |
| Table Continued | |

| Letter | Equivalent/Phonetic |
| F | Foxtrot |
| G | Golf |
| H | Hotel |
| I | India |
| J | Juliet |
| K | Kilo |
| L | Lima |
| M | Mike |
| N | November |
| O | Oscar |
| P | Papa |
| Q | Quebec |
| R | Romeo |
| S | Sierra |
| T | Tango |
| U | Uniform |
| V | Victor |
| W | Whiskey |
| X | X-ray |
| Y | Yankee |
| Z | Zulu |
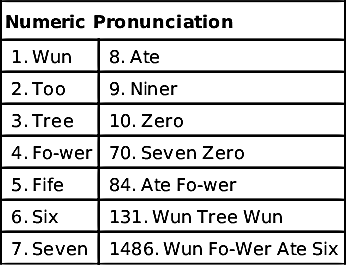
Numbers are also important in communications and should be clearly spoken in telephone and radio conversations. The pronunciation of numerals should be exaggerated to avoid misunderstanding by the receiving party. Each digit of large numbers is pronounced separately, even in the case of hundreds and thousands:
| Numeric Pronunciation | |
| 1. Wun | 8. Ate |
| 2. Too | 9. Niner |
| 3. Tree | 10. Zero |
| 4. Fo-wer | 70. Seven Zero |
| 5. Fife | 84. Ate Fo-wer |
| 6. Six | 131. Wun Tree Wun |
| 7. Seven | 1486. Wun Fo-Wer Ate Six |
When using a two-way radio, security officers should transmit only necessary and approved messages. Merely talking to pass the time or communicating at great length, when telephones are available and more appropriate, is prohibited.
As mentioned earlier, to be certain that your message has been properly received, wait for a return response indicating that the message was received.
The following phrases may be used to expedite communication.
CORRECT: You are correct, or what you have transmitted is correct.
SAY AGAIN: Repeat your last transmission.
SILENCE: Cease transmission immediately.
WILCO: I have received your message, understand it, and I will comply.
CORRECTION: An error has been made.
MORE TO FOLLOW: Transmitting unit has more information to transmit.
OUT: This is the end of my transmission.
OVER: This is the end of my transmission.
RADIO CHECK: What is my signal strength and readability?
READ BACK: Repeat entire transmission.
Federal communications commission rules
The Federal Communications Commission (FCC) regulates radio and television communication in the United States. The FCC has certain regulations that must be adhered to when using two-way radios, including the following:
1. Broadcasting is prohibited, which refers to transmissions that are intended to be received by the general public.
2. Radio communication may not be used for any activity related to program production or news gathering.
3. Transmission of music is prohibited.
4. Radio communication may not be used for any type of activity that violates any federal, state, or local law.
5. The meaning of communication may not be hidden by using codes or ciphers. Universally accepted abbreviations may be used when the intention is not to hide the meaning of the transmission.
6. Transmission of obscene, indecent, or profane words, language, or meaning is prohibited.
7. You may not use someone else’s call sign without authorization or transmit a communication that is intended to deceive someone.
8. Recording previous radio communications and broadcasting the recording is prohibited.
9. You may not willfully or intentionally interfere with someone else’s radio transmission.
10. Two-way radio communication must be licensed and the original writer authorization or copy must be posted when operating.
11. You must identify your call station at the end of each contact and every 10 min during the contact, which may be done using any of the modes that are legal.
Telephone
Most security officers are required to answer the telephone for some minimum amount of time on a daily basis. This may require the security officer to simply answer telephone calls that come into the security post from another interior telephone or, as is often the case, security personnel may be required to act as the main telephone operator during evening and weekend hours. No matter the level of telephone service provided by security, it is critical that all security personnel answer the telephone in a professional manner.
Because a person who is calling on the telephone cannot see the other person who is answering the call, perceptions are made about the person on the other end of the phone. If the caller has never met the person who is receiving the phone call, a mental picture is formed. This mental picture is shaped by perceptions on the part of the caller. People have a natural tendency to guess what a person looks like. Often, these mental pictures are totally inaccurate. The soft, sweet, and even sexy female voice on the other end of the phone may belong to a woman who can bench-press 500 pounds.
People make assumptions and reach conclusions about a person based upon the tone of voice and way in which a person speaks on the telephone. A person’s mood and mental outlook are expressed in voice. A person who is tired, angry, happy, or frustrated is often very obvious by their tone of voice. Therefore, if a security officer is not very happy with having to answer the telephone, this resentment is often transferred through his or her tone of voice and their unfriendliness in demonstrating a willingness to help the caller.
As security officers, image and perceptions go a long way in the way workers and executives view the entire security operation. Security officers, who are required to answer the telephone for extended periods of time, may be accepting a telephone call from the president of chief executive officer of the corporation. For an executive of the corporation to hear an impolite, rude, uncaring security officer answer the telephone, the reputation of the entire security department is damaged. Security officers should accept the responsibility of answering the telephone and perform this task to the best of their abilities.
Suggestions for answering the telephone
1. Always answer the phone within three rings and have a pen or pencil and paper ready to take notes.
2. Answer the phone by saying, “Good morning/afternoon/evening. ABC Company, Security Officer Jones speaking. May I help you?”
3. Try to help the person. If they ask for someone who is not at work, do not just say, “They are not in.” Help the caller by saying, “Is there someone else who can help you?”
4. If the person has a problem or complaint, listen to him or her and attempt to offer a suggestion or alternative.
5. If the caller asks for the home phone number of anyone, do not give it out. If the caller insists that he or she must speak to the person, ask the caller for his or her name and phone number. Advise the caller that you will call the employee at home and give him or her the caller’s name and phone number.
6. If the caller is a customer or client, be certain to obtain specific information to their questions or problems and then attempt to contact the appropriate executive at home.
7. If the caller states that he or she must speak to someone because of an emergency, take notes of the caller’s statements and be certain to notify the employee or, if required, the supervisor as soon as possible.
8. Security personnel must not convey their emotions in their voice. If the security officer is tired or angry at someone, he or she must remember that in all likelihood, the caller is not responsible for that mood. Therefore, do not make the caller the victim.
9. When answering the telephone, security personnel should always assume their boss is the person calling. Never think that you can play jokes or games on the phone because you know the caller. You might think you know the identity of the caller, but you may often be mistaken.
10. Smile on the telephone. Project a positive image. If you cannot understand the person or their message, ask them to repeat their message.
Public address systems and intercoms
Whether a security officer uses a two-way radio, telephone, public address system, intercom, or beeper, the goal is identical—to send a message and for the receiver to understand the intended message.
Public address systems
Security officers may use the public address system for the routine paging of employees for phone calls or during an emergency evacuation when all employees must evacuate the facility immediately. Many public address systems or satellite systems are stationed at security posts. Usually, there are clear and explicit instructions when a security officer is permitted to use the public address system.
1. Speak slowly and confidently. It is best to have what you intend to say written down in front of you. Practice reading it a few times before using the public address system.
2. Keep your statement brief.
3. Upon completion, repeat your statement completely. You may want to state, “This message will be repeated in 20 seconds.”
4. Have another security officer or member of management verify that the message was in fact heard.
5. If necessary, continue to repeat the message.
As with all communication equipment, security officers must assume that all of their discussions, dialogue, and background noise (music or conversation) can be overheard by others. Some very embarrassing incidents have occurred to many famous and not-so-famous persons when they thought their conversations were in private but were in fact overheard by many others (perhaps millions if on televisions). Security officers must assume that others may be in the vicinity of the person receiving the communication. For that reason, all communication should be brief and professional at all times!
Intercoms
Intercoms are either hardwired between receiving stations or they are wireless, whereby transmission is relayed through the air. For security purposes, most intercoms are used to gain access through a secured area that is normally controlled by security, usually by way of an electronic lock (Figure 10.2). Ideally, a closed-circuit television camera is used in conjunction with an intercom in order to ensure that the security officer on duty is not granting access to someone based solely on voice recognition. However, it is not uncommon for intercoms to be used without a camera or other means for providing positive identification.
When a person calls using an intercom, the security officer will normally be alerted via a beeper, buzzer, chime, or bell. The security officer should push the Talk button on the intercom and identify himself or herself: “Security Officer Jones. May I help you?” Normally, the caller will identify himself or herself and should be asked to state the reason they desire access. Once the security officer has positively identified the person, instructions should be given to the person and access granted. If the security officer cannot identify the person, the visitor should be instructed as to where he or she can enter the facility that is controlled by a posted security officer.
Importance of internal communication before and during an emergency
At every security post, a written set of post orders or instructions is available for the security officer to reference whenever a question or problem surfaces. It is essential that a security officer read these post orders frequently to be certain they know what to do during an emergency. The following information is to be included in each set of internal communication information.
List of names and phone numbers of client staff
This information should be organized by overall facility organization or by departments with the name of each person, their title, and the various ways of contacting them. This will usually include cell phone numbers, pager numbers, e-mail addresses, and possibly home phone numbers. This list should specify when the person should be contacted and in what order they should be called. Usually, the names of the various clients are contacted in some order of preference or reporting structure. It is very important for the security officer to know the proper procedure for calling the client contact list. In some cases, employees alternate who is to report to the facility or to respond to an emergency or incident. If security contacts someone out of order, the client may have to pay additional overtime. Often, the contract security provider will be required to reimburse the client for this inadvertent mistake. Therefore, know the names of and the titles of the client personnel who are to be contacted after normal business hours.
Under no circumstances should a security officer ever provide the personal telephone number of a client contact to anyone without the explicit consent by the person. To provide the needed customer service while maintaining the integrity of the telephone list, advise a caller who is seeking someone else’s phone number to provide you with a number where they can be reached. The security officer can provide the client contact with the phone number, then call the person and advise them that another person wants to speak with them. The officer can then provide the employee the telephone number of the caller.
In some cases when an incident occurs, it will be necessary for a security officer to simply call one person. In other situations, 5–10 people (depending on the situation) may need to be contacted. Prior to calling, it is essential that the security officer have all pertinent information to relay to the client contact:
1. Type of incident
2. Time discovered
3. Steps taken to minimize the problem
4. Other persons who have been contacted
5. Advise if anyone has responded to the site, such as maintenance, facility personnel, emergency personnel, etc.
6. Advise if there are any injuries and their extent
Upon completion of the client notifications, it is important that the contacts of your employer (contract security provider) receive notification of what has happened and what steps were initiated.
Importance of timely notification
The quicker a security officer notifies client contacts as well as their own employer, the sooner assistance can be provided, Often, when a serious incident occurs, someone has been injured, or a crime occurs witnesses to the event may leave without another opportunity of contacting them in the future. If this happens, evidence may be lost and greater harm may result if security fails to respond properly. Failure to act or a delay in action may result in:
1. Lost opportunity to provide valuable information
2. An injury, damage to property, or loss of production may be greater
3. Liability faced by the contract security provider
4. Negative publicity
Role of security officer
The role of a security officer is to minimize property loss and injury to employees or visitors when an event occurs. Security officers must always remember to obtain all the facts as quickly as possible to refrain from injecting their own opinion or commentary regarding any incident. Comments such as, “I knew that this would eventually happen,” “I have told them a hundred times about this,” or “No one cares around this place,” are all unrelated to and potentially damaging legally to the client for the company or client where the officer is employed. Always remember, when in doubt, call for help—the sooner the better!
Types of incidents when communication is essential
As mentioned earlier in this chapter, communication under ideal circumstances is often difficult. During a stressful situation where tension is extremely high, communication will be even more difficult. The following information needs to be obtained by the security officer for each of the specific incidents listed below.
Fire
1. Time reported to you
2. How you were notified and by whom
3. Specific location of the fire
4. Materials involved (solvents, flammables, etc.)
5. Extent of injuries and number of persons injured
6. Any fire protection suppression systems that were activated
7. Time that 9-1-1 was notified and by whom
8. Time emergency personnel arrived on scene
9. Whether the facility was evacuated
10. Time you notified client contacts and your supervisor
Chemical spill or leak
1. Time reported to you
2. How you were notified and by whom
3. Specific location of the spill
4. Materials involved (solvents, flammables, etc.)
5. Extent of injuries and number of persons injured
6. Whether any of the materials entered a drain
7. If the spill was contained with absorbing clay or other cleanup material
8. Time that 9-1-1 was notified and by whom
9. Time emergency personnel arrived on scene
10. Whether the facility was evacuated
11. Time you notified client contacts and your supervisor
Environmental emission
1. Time reported to you
2. How were you notified and by whom
3. Specific location of the emission
4. Source of the emission (material or chemical)
5. Extent of injuries and number of persons injured
6. Time you notified client contacts and your supervisor
7. Time that 9-1-1 was notified and by whom
Weather-related event
1. Damage to the property
2. Time you notified client contacts and your supervisor
3. Time that outside services were notified to remove tree limbs, restore power, etc.
4. Number of injuries and their extent
5. Time 9-1-1 was notified
6. Number of persons in the building
7. Whether extra security personnel are able to report for duty
Assault/domestic dispute at work
1. Time reported to you
2. How were you notified and by whom
3. Specific location of the incident
4. Names of the persons involved
5. Extent of injuries and number of persons injured
6. Identify (if known) whether any weapons were involved
7. Identify (if known) any hostages
8. Time that 9-1-1 was notified and by whom
9. Time emergency personnel arrived on scene
10. Whether the facility was evacuated
11. Time you notified client contacts and your supervisor
Occupational Safety and Health Administration (OSHA) inspection
1. Time the OSHA officer arrived on the scene
2. How you were notified of their arrival
3. Specific location of the inspection
4. Whether the OSHA officer was asked to provide proper photo identification
5. Time you notified client contacts and your supervisor
Theft
1. Time reported to you
2. How you were notified and by whom
3. Specific location of the theft
4. Property involved (personal or company)
5. Identification of the property (color, size, model and serial number, weight; if a vehicle, make, model, year, color and license number)
6. Names of any witnesses
7. Names of any possible suspects
8. Time that the police were notified (if so)
9. Time police arrived on the scene
10. Time you notified client contacts and your supervisor
Summary
• An essential part of any security officer’s job is the ability to communicate quickly, efficiently, and in a manner that is completely understood by all parties. To achieve these objectives, security officers will rely upon a variety of communication devices, including two-way radios, telephones, and intercoms.
• Security officers should use proper radio etiquette when transmitting messages. Two-way radios are used for fast communication. Therefore, long conversations should be avoided.
• When using two-way radios, security officers must follow proper techniques:
1. Be certain how the radio works.
2. Know the identification number of your radio unit and that of the base station.
3. Know how to identify yourself when calling.
4. Know what channel the radio should be on.
5. Check your radio at the beginning of each shift.
6. If at a fixed post, know if the radio should remain in the battery charger when not in use.
7. Be sure there is an adequate supply of backup batteries.
8. Know if earphones and shoulder microphones should be used.
9. Know how the radio should be carried:
a. Clip or belt
b. Holder
c. Held in hand
10. Be certain who else has radios and may be listening to your conversation.
• When using a two-way radio, a security officer should hold the radio near his or her mouth and speak calmly, deliberately, and in a normal tone of voice. The security officer should identify himself or herself prior to making a statement or asking a question.
• Often, because of past experiences, two security officers can communicate with two-way radios and not waste a great deal of time, nor do they have to say everything for the other person to understand their message.
• Abbreviations are often used in order to expedite conversations when using two-way radios. Additionally, certain words may be misunderstood because of similarity in sound to other words.
• When using a two-way radio, security officers should transmit only necessary and approved messages. Merely talking to pass the time or communicating at great length when telephones are available and more appropriate is prohibited.
• The Federal Communications Commission (FCC) regulates radio and television communication in the United States. The FCC has certain regulations which must be adhered to when using two-way radios.
• Most security officers are required to answer the telephone for some minimum amount of time on a daily basis. This may require the security officer to simply answer telephone calls that come into the security post from another interior telephone or, as is often the case, security personnel may be required to act as the main telephone operator during evening and weekend hours.
• People make assumptions and reach conclusions about a person based upon the tone of voice and way in which a person speaks on the telephone. A person’s mood and mental outlook are expressed in the voice. A person who is tired, angry, happy, or frustrated is often very obvious by his or her tone of voice.
• Whether a security officer uses a two-way radio, telephone, public address system, intercom, or beeper, the goal is identical: to send a message and for the receiver to understand the intended message.
• Security officers may use the public address system for the routine paging of employees for phone calls or during an emergency evacuation when all employees must evacuate the facility immediately. Many public address systems or satellite systems are stationed at security posts. Usually, there are clear and explicit instructions about when a security officer is permitted to use the public address system.
• As with all communication equipment, security officers must assume that all of their discussions, dialogue, and background noise (music or conversation) can be overheard by others.
• Intercoms are either hardwired between receiving stations or they are wireless, whereby transmission is relayed through the air. For security purposes, most intercoms are used to gain access through a secured area that is normally controlled by security, usually by way of an electronic lock. Ideally, a closed-circuit television camera is used in conjunction with an intercom to ensure that the security officer on duty is not granting access to someone based solely on voice recognition.
• It is essential for you as a security officer to thoroughly know and understand all of your responsibilities during an emergency because you will not be afforded the time or understanding to learn during a crisis.
• It is vital that you as a security officer know who is to be notified during an emergency and that you know how to contact them.
• All client or company information is considered confidential and should be protected at all times.
Exercises
1. What government agency regulates two-way radio communications?
2. What is meant by the term “base” in radio communications?
3. What is the purpose of the phonetic alphabet?
4. How frequently must the call station of the radio system be broadcast per government regulations?
5. How can a security officer project a positive image over the telephone?
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.

