21
Privacy Preserving Power Charging Coordination Scheme in the Smart Grid
Ahmed Sherif1, Muhammad Ismail2, Marbin Pazos-Revilla1, Mohamed Mahmoud1, Kemal Akkaya3, Erchin Serpedin4, and Khalid Qaraqe2
1 Tennessee Technological University, Cookeville, TN, USA
2 Texas A&M University at Qatar, Doha, Qatar
3 Florida International University, Miami, FL, USA
4 Texas A&M University, College Station, USA
21.1 Introduction
Smart grid is a progressive upgrade to the existing power grid. It consists of sophisticated systems of smart electronic devices, dispersed generators, and loads (Brusco et al., 2014) and can give two‐way power exchange among various components. Several functionalities of the smart grid require major dependence on an intelligent communication infrastructure. However, such a dependence makes the smart grid vulnerable to tremendous risks as well as hard challenges in protecting the smart grid from cyber‐security threats (Khurana et al., 2010). Compared with the existing communication networks such as the Internet, the smart grid communication systems have different objectives, architecture, and concerns about what need to be protected (Yan et al., 2012). For example, in the smart grid, we need to guarantee the real‐time performance and the features of the continuous operations. The smart grid is more concerned with the message delay than the data throughput due to the timing constraint of messages transmitted over the power networks. As a result, the existing security solutions for different communication networks cannot fit directly to the smart grid communication networks without filling the gaps where traditional communication network solutions do not work or apply. In the following, general security requirements for the smart grid are discussed. Then, we focus our attention on a specific functionality of the smart grid, discussing its security requirements, and presenting potential cyber‐security solutions.
21.1.1 Smart Grid Security Requirements
The smart grid should meet rigorous security requirements such as availability, integrity, authentication, authorization, and non‐repudiability. Such requirements can be briefly summarized as follows:
- Availability: denial of service (DoS) attacks are considered as the potential attacks against the availability of the smart grid networks. DoS attacks are aiming to exhausting all the grid resources to prevent the legitimate users from accessing these resources. These attacks can be done in the physical layer by performing false data injection or jamming attacks. In the literature, multiple frequency channels are proposed as a defense mechanism against jamming attacks (Aravinthan et al., 2011). In addition, an intrusion detection system (IDS) can be used to defend against the DoS attacks in higher layers. There are three different categories of IDSs (Faisal et al., 2012): signature‐based, specification‐based, and anomaly‐based. A signature‐based IDS uses a black list of all known attacks to detect the intrusions, whereas specification‐based IDS uses a set of rules to define the correct behavior of a program or a protocol. Finally, an anomaly‐based IDS uses a model for normal behavior, and any deviation from this model is considered an anomaly.
- Integrity: it aims to prevent unauthorized persons or systems from modifying the information via message injection, device impersonation, or message replay. Different techniques have been adopted in the literature to ensure data integrity such as cryptographic hashing (Benoit, 2011), time‐stamps and sequence numbers (Aravinthan et al., 2011), and nonces (numbers used once to make each message unique) (Xiao et al., 2013). Other techniques to detect data integrity attacks in the smart grid rely on secure phasor measurement units (PMUs) (Giani et al., 2011) and load profiling schemes (Aravinthan et al., 2011).
- Authentication: it is concerned with the determination of the true identity or valid account of each entity involved in the communication. Usually the mechanisms used for the authentication can provide also the integrity. Various tools exist for providing authentication and integrity, including hashes and keyed hashes such as SHA‐1 or HMAC‐SHA‐1 and digital signatures such as RSA or ECC signatures (Stallings, 2010). In addition, other techniques rely on a physically unclonable function (PUF) for strong hardware‐based authentication (Nabeel et al., 2012).
- Authorization: it is concerned with preventing access to the system by persons or systems without permission to do so. In the literature, public key certificates and zero‐knowledge systems can be used for authentication, and the attribute certificates are used for authorization (Vaidya et al., 2011).
- Non‐repudiability: it refers to being able to provide irrefutable proof to a third party of who initiated a certain action in the system, even if this actor is not cooperating. In the literature, such an objective can be achieved after user authentication by storing a log of transactions for a predefined number of days to resolve any repudiation by tracing back the events (Aravinthan et al., 2011).
Overall, specific smart grid functionalities require custom‐made cyber‐security mechanisms depending on the communication requirement of such a functionality. In what follows, we focus our attention on one functionality of the smart grid, namely charging coordination, and discuss one of its cyber‐security requirements.
21.1.2 Charging Coordination Security Requirement
As per NIST (National Institute of Standards and Technology, 2010), one of the principal goals of the smart grid is the diminishment of greenhouse gas emissions by integrating more renewable energy resources (Lukic et al., 2008) and electric vehicles (EVs). Recently energy storage units (ESUs) including home batteries and EVs have received broad consideration. TESLA company recently produced a home battery product (M57) that can charge when the electricity is cheap and power the home when electricity is expensive. Numerous automotive companies have already started producing EVs from their production lines (Nissan LEAF Electric Car).
These developments imply that the smart grid will have a large number of ESUs. However, the large‐scale, simultaneous charging of energy storage units (ESUs), including home batteries and EVs, will have a significant impact on the power grid, especially when the charging loads are not coordinated. This can raise technical issues including imbalance of charging demands and energy supply, more power losses, and larger voltage deviation (Sortomme et al., 2011; Hadley and Tsvetkova, 2009). These issues cannot be avoided by charging at off‐peak periods, e.g., late night, since this can make another peak that cannot be handled by the power distribution network. The most ideal approach to avoid this issue and fully utilize the accessible power is via charging coordination (Deilami et al., 2011; Clement et al., 2009). However, this needs reporting a few data, for example, whether an ESU needs to charge or not, time to complete charging (TCC), the battery state of charge (SoC), and so on. Unfortunately, this data can reveal private information about the owners of ESUs, such as the location of an EV and the activities of a house's residents (P. Akula, M. Mahmoud, K. Akkaya, and M. Song, 2015; NIST, 2010). For example, the charging demands sent from an EV can reveal whether the EV's owner is at home, to what extent he/she will stay, and to what extent he/she drives. Also, if a home battery is not charging for an extended period, this can reveal that the residents do not spend time in home because they are traveling, and charging more than the normal amount can reveal that residents host guests. While one can plan solutions for particularly securing the information exchange and concealing data from the included parties, this may unfavorably influence the performance of charging coordination plans. This is on the grounds that privacy preservation often targets to hide information; however, charging coordination needs sufficient information.
Due to technical limitations, not all ESUs can charge at the same time, so each ESU ought to send a charging request to an aggregator. The aggregator should not know whether an ESU needs to charge or not, its battery state of charge, and the needed time to finish charging to preserve privacy. The aggregator forwards the requests to a charging controller (CC) that needs sufficient data to run a charging coordination scheme without linking the requests to specific ESUs to preserve privacy. In this chapter, we present a privacy‐preserving power‐charging coordination scheme that operates in two phases (Mahmoud et al., 2016a). The first phase aims to submit anonymous and unlinkable data to the CC, and the CC computes the charging schedules in the second phase by running a modified algorithm for the knapsack problem. The proposed charging coordination algorithm is efficient and scalable as it exhibits polynomial time complexity. In the charging coordination scheme, we define a priority function to prioritize the ESUs' requests by calculating a priority index for each request. The target of the coordination scheme is to charge in every time slot a subgroup of ESUs that maximize the total priority indices and subsequently the number of charged ESUs without surpassing the power limit. In the first phase and in order to boost the level of privacy preservation, each ESU can add a random noise to its data, i.e., TCC and SoC, to prevent the CC from linking the requests coming from a specific ESU. As adding noise to the data may influence the performance of the charging coordination scheme, we will explore the impact of noise addition on performance and the gains in privacy by utilizing information‐theoretic metric referred to as entropy (Díaz et al., San Francisco, CA, USA, 2003).
The remainder of the chapter is organized as follows. Existing charging coordination and privacy preservation schemes are introduced in Section 21.2. The network and threat models and the privacy‐preserving charging coordination scheme are explained in Section 21.3. Privacy analysis and simulation results are are discussed in Section 21.4. Finally, a summary is presented in Section 21.5.
21.2 Charging Coordination and Privacy Preservation
In (Ismail et al., 2015b), Ismail et al. explain that the negative impacts of vast simultaneous charging of EVs can be addressed by using optimal design of charging facilities and charging coordination of EVs. In terms of optimal design of charging facilities, Ismail et al. present a novel optimal planning algorithm for EV‐charging facilities in (Ismail et al., 2015a). The planning model developed in (Ismail et al., 2015a) accounts for the stochastic nature of the EV‐ charging requests and determines the optimal number of chargers to be deployed within a charging station along with the queuing size within the charging facility. The proposed scheme is tested in various real‐world scenarios, and the results show positive profit values when optimal planning parameters are adopted.
On the other hand, coordinated charging can prevent stressing the distribution system and avoid power outages in extreme cases (Verzijlbergh et al., 2012). The main parts of the smart‐charging coordination systems include data collection and optimization (Sundstrom and Binding, 2012). The first part is responsible for collecting the data relevant to the ESUs' charging requests such as TCC and battery SoC. Typically, this part is carried out via an aggregator, which collects the data from the ESUs and sends it to the operator, and then the aggregator sends the charging decisions coming from the operator back to the ESUs. The optimization unit can make optimal coordinated charging decisions that maintain service reliability, maximize the operator's profit, satisfy system constraints, and meet the customer demands. In general, the following approaches can be distinguished for EV charging:
- Grid‐to‐vehicle (G2V): in this scheme, EVs are connected to the smart power grid to charge. In (Bayram et al., 2014), a pricing‐based load‐shifting framework is presented for G2V fast‐charging stations with fixed capacity. Two different types of users are considered. The first type represents a customer who uses the charging station once. For this type, the charging coordination scheme offers incentives to the users to delay their service by one time period at a high peak load condition. So the users can take the offer and guarantee the service in the next time period or face the risk of being blocked in case of resource unavailability. On the other hand, the second type of users represents a customer who uses the same charging station in a frequent manner. This type of customers is referred to as EV subscribers, who can have a contract with the charging station that offers better service agreement. For EV subscribers, the objective of the station operator is to serve all peak‐hour requests within a specific time window.
- Vehicle‐to‐grid (V2G): in this scheme, an EV can discharge to the grid (as it is equipped with bidirectional chargers) to balance supply and demand (Han and Xiao, 2016; Wan et al., 2016). In (Shaaban et al., 2014b), Shaaban et al. propose a real‐time system for managing the coordinated charging decisions for EVs in a smart grid. The proposed two‐stage optimization unit guarantees the feasibility of the charging/discharging decisions by maximizing the satisfaction of the EV owner and minimizing the system operating costs. A smart coordination mechanism to coordinate the charging/discharging of EVs in parking lots is proposed in (Shaaban et al., 2014a). The proposed scheme maximizes the utility profit and minimizes the charging costs by taking into consideration the impacts of the future charging decisions and the normal load profile. Moreover, a sliding time window is used to deal with the dynamics associated with vehicles' arrivals and departures in a parking lot.
- Vehicle‐to‐vehicle (V2V): in this scheme, energy is transferred from one EV to another EV to overcome the overloading problem at the power grid. A semi‐distributed V2V‐charging coordination strategy for EVs is proposed in (Wang et al., 2014). Real‐time information delivery for the V2V strategy is provided through a heterogeneous wireless network by utilizing both vehicular ad hoc networks (VANETs) and cellular networks. In (Wang et al., 2015), the authors incorporated the mobility of EVs into the online charging coordination and an online coordinated EV‐charging strategy is proposed. The real‐time vehicle information is collected via a heterogeneous network of VANETs assisted by cellular networks. By using the real‐time vehicle information, the mobility‐aware coordinated EV‐charging strategy can be achieved jointly in a spatiotemporal framework to enhance the resource utilization while avoiding the power overload and generation‐demand mismatch. In addition, a price control mechanism is proposed in (Wang et al., 2016) to enable a V2V energy‐swapping strategy that maximizes the discharging revenues for supplying EVs and minimizes the charging cost for demanding EVs while avoiding power system overload.
Numerous privacy‐preservation schemes are proposed in the literature for different smart grid applications such as advanced metering infrastructure (AMI) (Tonyali et al., 2016; Beussink et al., 2014; H. Mohammed and Akkaya, 2016) and power injection (Akula et al., 2015; Mahmoud et al., 2016b). AMI is a communications network that enables two‐way communication between utilities and customers. Smart meters send fine‐grained power consumption data in real time, e.g., every few seconds. In (Tonyali et al., 2016; Beussink et al., 2014), the authors used a data obfuscation mechanism and proposed secure and efficient algorithms to distribute obfuscation values within an AMI network. They presented a protocol that utilizes LTE‐direct for exchanging of data among various gateways. An efficient privacy‐preserving data collection scheme for smart grid AMI networks is proposed in (H. Mohammed and Akkaya, 2016). By using a lightweight symmetric‐key‐cryptography and hashing operations, the proposed scheme can collect the consumption data while preserving the customer privacy. The authors use the asymmetric‐key‐cryptography operations for key management that is executed every long time. In (Akula et al., 2015), the authors proposed a privacy‐preserving scheme for power injection in the smart grid that is based on the idea of aggregation of sensitive information of the storage units' owners to prevent the utility from knowing individual's sensitive information. The proposed scheme can be used for the authentication of the storage units and the integrity of their data. Mahmoud et al. proposed a novel secure and privacy‐preserving power injection querying scheme over AMI and LTE cellular networks in (Mahmoud et al., 2016b). The proposed scheme is based on two aggregation techniques to hide the storage units' sensitive information. They also developed a bilinear pairing‐based technique to enable the utility company to ensure the integrity and authenticity of the aggregated bid without accessing the individual bids coming from the storage units. Additionally, numerous privacy‐preservation schemes are proposed in the literature for different applications such as VANETs (Rabieh et al., 2016, 2015a; Mahmoud et al., 2014; Rabieh et al., 2015c, b, d), LTE networks (Haddad et al., 2016, 2015), autonomous vehicles (AVs) (Sherif et al., 2016), and mobile social network (MSN) (Oriero et al., 2016). However, these schemes cannot be applied effectively and efficiently in the smart grid due to its unique problems and requirements.
As the renewable energy will play a vital role in the smart grid, the energy storage units can be used to store the excess power at the period of strong sun or wind and inject power to the grid during peak hours. The same thing can be applied to the EVs' batteries, which can be treated as storage units. The utility companies should communicate with the storage units' owners to coordinate such a charging action. However, this type of communication may reveal some sensitive information about the owners such as their location or amount of power injected. This information can be used by the utility or by other owners to misbehave and gain more benefits. Without preserving the privacy and hiding such information, the storage unit owners or the utility company may face financial losses. However, the existing research in charging coordination in the smart grid, e.g., (Ismail et al., 2015b; Wang et al., 2014, 2015, 2016; Bayram et al., 2014; Shaaban et al., 2014a,b; Ismail et al., 2015a) do not consider the privacy preservation concerns. In addition, the works on privacy preservation in the smart grid, e.g., (Tonyali et al., 2016; Beussink et al., 2014; H. Mohammed and Akkaya, 2016; Akula et al., 2015; Mahmoud et al., 2016b) do not investigate the impact of the proposed schemes on the charging coordination efficiency. This motivates our work to study the impact of privacy preservation on charging coordination efficiency.
21.3 Privacy‐Preserving Charging Coordination Scheme
21.3.1 Network and Threat Models
As outlined in Figure 21.1, the considered network model has various numbers of communities and CCs. Every community is composed of several ESUs and one aggregator. The aggregator and the CC can communicate by means of LTE or 4G (Saputro et al., 2012). The connection between the ESUs and the aggregator is based on either Wi‐Fi or LTE. The CC cannot communicate directly with ESUs; however, this must be done via the aggregators. The ESUs send charging requests to the CC via the aggregators. The CC determines the appropriate charging schedules and sends them back to the ESUs. A community is associated with an electric bus with loading limit of ![]() KWh. The normal load (residential, commercial, and industrial) signified by
KWh. The normal load (residential, commercial, and industrial) signified by ![]() is known to the CC. Henceforth, the accessible charging limit for ESU charging at a given time slot is given by
is known to the CC. Henceforth, the accessible charging limit for ESU charging at a given time slot is given by ![]() . In the event that the aggregated power requests of the ESUs are less than
. In the event that the aggregated power requests of the ESUs are less than ![]() , all ESUs can charge at the same time. Generally, the proposed privacy‐preserving charging coordination scheme is utilized to satisfy the charging requests while keeping the aggregate charging power at
, all ESUs can charge at the same time. Generally, the proposed privacy‐preserving charging coordination scheme is utilized to satisfy the charging requests while keeping the aggregate charging power at ![]() .
.
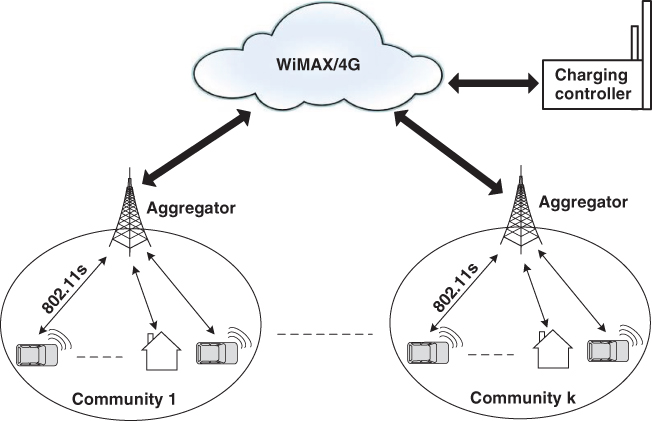
Figure 21.1 Network model under consideration.
For the threat model, an honest‐but‐curious model is employed, which assumes that the attackers do not aim to disturb the proper operation of the scheme, yet they are just interested in gathering private information. The attackers can be the aggregator, the CC, ESUs, and eavesdroppers. They may passively snoop on the communications to learn sensitive information. The attackers should not learn whether an EV needs to charge or not or the charging request data such as TCC and SoC. The CC needs TCC and SoC to run the charging coordination scheme, yet the information should be anonymized to preserve privacy. The CC should not have the ability to link an ESU's requests for high privacy assurance.
21.3.2 The Proposed Scheme
As outlined in Figure 21.2, the proposed scheme has two stages. In the anonymous data submission phase, ESUs send charging requests without revealing private data. In the charging coordination phase, the submitted information is utilized to generate charging schedules. First, a priority index for each ESU is calculated, and then a modified knapsack problem (Kellerer et al. 2004) algorithm is run to choose the subset of ESUs that can maximize the summation of the priority indices of scheduled ESUs without surpassing the total power limit.
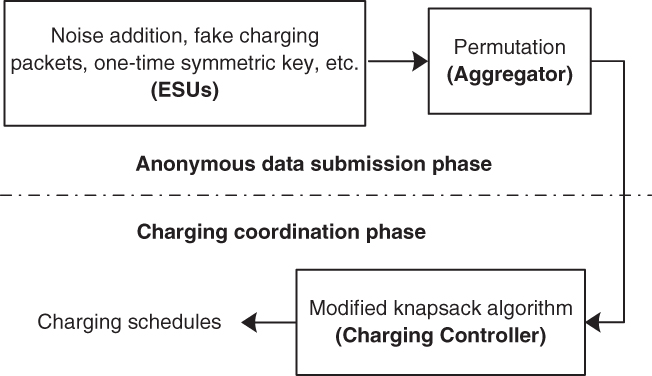
Figure 21.2 Illustration of the privacy‐preserving charging coordination scheme.

Figure 21.3 Anonymous data submission.
21.3.2.1 Anonymous Data Submission
Charging Requests Submission
The packets exchanged in the anonymous data submission phase are shown in Figure 21.3. Our goal is to empower the CC to run a charging coordination scheme without revealing private information. Time is divided into a group of slots ![]() of equivalent duration
of equivalent duration ![]() that covers the 24 hours of the day, with
that covers the 24 hours of the day, with ![]() . At the start of every time slot, each ESU in a group should send a charging request packet (
. At the start of every time slot, each ESU in a group should send a charging request packet (![]() ) to the aggregator. At a given time slot, the set of ESUs with charging requests is given by
) to the aggregator. At a given time slot, the set of ESUs with charging requests is given by ![]() . Each ESU shares a symmetric key with the aggregator using any existing key agreement and exchange scheme such as the Diffie‐Hellman (Diffie and Hellman, 1976). The charging request has the ESU's unique identity (
. Each ESU shares a symmetric key with the aggregator using any existing key agreement and exchange scheme such as the Diffie‐Hellman (Diffie and Hellman, 1976). The charging request has the ESU's unique identity (![]() ), an encryption with a symmetric key shared with the aggregator
), an encryption with a symmetric key shared with the aggregator ![]() , and its signature on the packet (
, and its signature on the packet (![]() ), where
), where ![]() (
(![]() ) is the TCC,
) is the TCC, ![]() (
(![]() ) is the battery SoC,
) is the battery SoC, ![]() is the amount of power the ESU needs to charge,
is the amount of power the ESU needs to charge, ![]() is an encryption with the public key of the CC,
is an encryption with the public key of the CC, ![]() is a one‐time symmetric key, and
is a one‐time symmetric key, and ![]() is an encryption with the symmetric key shared among
is an encryption with the symmetric key shared among ![]() and the aggregator. Only the CC can acquire
and the aggregator. Only the CC can acquire ![]() and utilize it to encrypt the ESU's charging schedule. After receiving a charging request, the aggregator first verifies the signature to guarantee that the packet is sent from
and utilize it to encrypt the ESU's charging schedule. After receiving a charging request, the aggregator first verifies the signature to guarantee that the packet is sent from ![]() . Then, it decrypts the packet to acquire
. Then, it decrypts the packet to acquire ![]() . Finally, the aggregator sends the charging requests (
. Finally, the aggregator sends the charging requests (![]() ) alongside its signature
) alongside its signature ![]() to the CC.
to the CC.
The CC should not have the ability to link a charging request to an ESU from the identity sent in the packet. One way to do that is by utilizing pseudonyms rather than the real identities. Another approach is that the aggregator can utilize a secret and random permutation to shuffle the ESUs' identities and their charging requests such that the charging information of one ESU is mapped to the identity of another random ESU in the community, as demonstrated in Figure 21.4. The figure shows that the data of ESU ![]() is sent under the name of ESU
is sent under the name of ESU ![]() , the data of ESU
, the data of ESU ![]() is sent under the name of ESU
is sent under the name of ESU ![]() , etc. The proposed permutation is not static, yet for each time slot, it maps charging information to various ESUs' identities and stores a mapping table. This table will be utilized to map charging schedules to their ESUs' identities. The CC should not have the ability to link an ESU's requests in various time slots by linking the charging data, i.e., TCC and SoC.
, etc. The proposed permutation is not static, yet for each time slot, it maps charging information to various ESUs' identities and stores a mapping table. This table will be utilized to map charging schedules to their ESUs' identities. The CC should not have the ability to link an ESU's requests in various time slots by linking the charging data, i.e., TCC and SoC.
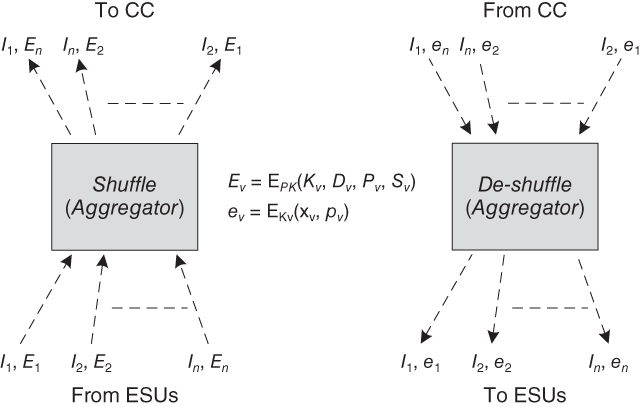
Figure 21.4 Permutation of requests.
Charging Schedules Distribution
The CC uses its private key to decrypt the charging requests coming from the aggregator and runs the charging coordination scheme. The CC determines the charging schedules ![]()
![]()
![]()
![]()
![]() , and signs and returns them back to the aggregator. As shown in Figure 21.3, a charging schedule
, and signs and returns them back to the aggregator. As shown in Figure 21.3, a charging schedule ![]() has the permutated identity
has the permutated identity ![]() and the encryption of the schedule utilizing the one‐time key sent by the ESU (
and the encryption of the schedule utilizing the one‐time key sent by the ESU (![]() ). The schedule either permits ESU
). The schedule either permits ESU ![]() to charge in the present time slot (when
to charge in the present time slot (when ![]() ) and indicates its charging rate
) and indicates its charging rate ![]() , or it postpones its charging request to a future time slot (
, or it postpones its charging request to a future time slot (![]() ). It should be noted that
). It should be noted that ![]() ,
, ![]() , and
, and ![]() indicate a symmetric‐key encryption with the one‐time key sent in the charging request, a symmetric‐key encryption with the key shared between an ESU and the aggregator, and an encryption with the public key of the CC, respectively. Upon receiving
indicate a symmetric‐key encryption with the one‐time key sent in the charging request, a symmetric‐key encryption with the key shared between an ESU and the aggregator, and an encryption with the public key of the CC, respectively. Upon receiving ![]()
![]() , the aggregator utilizes its permutation mapping table to undo the permutation, as shown in Figure 21.4, and transmits the charging schedules
, the aggregator utilizes its permutation mapping table to undo the permutation, as shown in Figure 21.4, and transmits the charging schedules ![]() to the ESUs, as represented in Figure 21.3.
to the ESUs, as represented in Figure 21.3.
Linking ESU's Charging Requests
In light of the above discussion, the CC needs to know the charging request's data (TCC and battery SoC) to run the charging coordination scheme; however, it is hard to link the request to a particular ESU. Nonetheless, the CC can attempt to utilize the charging request data to connect an ESU's requests over various time slots since it is normal that the TCC is diminishing after some time, and if an ESU does not charge in the present time slot, its TCC and SoC in a future time slot should be near the reported values in the present time slot. Linking an ESU's requests is problematic due to the fact that it can be utilized to distinguish the ESU; furthermore, an excessive amount of data will be uncovered if the CC could recognize the ESU.
In order to prevent leaking information, ESUs should add noise to the real data in its charging requests. By adding noise to both the TCC and the battery SoC, the ESU reports its TCC as: ![]() and battery SoC as:
and battery SoC as: ![]() , where
, where ![]() and
and ![]() are random noise. It should be noted that an ESU pays only for the charging power that is recorded by the smart meter. Moreover, not all the ESUs in a community need to add noise to their charging requests such as ESUs of public places, e.g., shopping malls and governmental and educational buildings. In these cases, users can hide their data in a big amount of requests coming from the same location, and the linkability of requests will be hard.
are random noise. It should be noted that an ESU pays only for the charging power that is recorded by the smart meter. Moreover, not all the ESUs in a community need to add noise to their charging requests such as ESUs of public places, e.g., shopping malls and governmental and educational buildings. In these cases, users can hide their data in a big amount of requests coming from the same location, and the linkability of requests will be hard.
Anonymity Measurement
Noise should be added to the charging requests' data (![]() and
and ![]() ) to make it hard for the charging controller to link the requests of an ESU sent at various time slots. We utilize an information‐theoretic metric called entropy (Díaz et al., San Francisco, CA, USA, 2003) to quantitatively measure the privacy preservation level that can be gained by adding noise. The idea of entropy in information theory gives an estimation of the information contained in a distribution of probabilities (Cover and Thomas, 1991. ISBN 0‐471‐06259‐6.). In (Díaz et al., San Francisco, CA, USA, 2003), the authors propose an information‐theoretic model utilizing entropy to evaluate the level of anonymity given by anonymous communication schemes. The model can measure the level of information acquired by attackers about the probability that a message is sent by a specific user. The entropy (
) to make it hard for the charging controller to link the requests of an ESU sent at various time slots. We utilize an information‐theoretic metric called entropy (Díaz et al., San Francisco, CA, USA, 2003) to quantitatively measure the privacy preservation level that can be gained by adding noise. The idea of entropy in information theory gives an estimation of the information contained in a distribution of probabilities (Cover and Thomas, 1991. ISBN 0‐471‐06259‐6.). In (Díaz et al., San Francisco, CA, USA, 2003), the authors propose an information‐theoretic model utilizing entropy to evaluate the level of anonymity given by anonymous communication schemes. The model can measure the level of information acquired by attackers about the probability that a message is sent by a specific user. The entropy (![]() ) of linking a charging request sent at time slot
) of linking a charging request sent at time slot ![]() to one of
to one of ![]() requests sent at time slot
requests sent at time slot ![]() is given in Equation 21.1, where
is given in Equation 21.1, where ![]() is a discrete random variable with probability mass function of
is a discrete random variable with probability mass function of ![]() , where
, where ![]() is the probability that request
is the probability that request ![]() sent at time
sent at time ![]() and request
and request ![]() sent at time
sent at time ![]() are sent from same ESU.
are sent from same ESU.
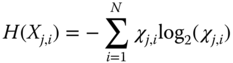
The CC utilizes ![]() and
and ![]() of the packets sent in two distinct time slots to specify
of the packets sent in two distinct time slots to specify ![]() for every request
for every request ![]() , where
, where ![]()
![]()
![]() and
and ![]() is the number of requests received at time
is the number of requests received at time ![]() . The probability
. The probability ![]() is higher as
is higher as ![]() and
and ![]() of the two requests
of the two requests ![]() and
and ![]() are close.
are close. ![]() is given in Equation 21.2, where
is given in Equation 21.2, where ![]() and
and ![]() are the SoC of the request of interest
are the SoC of the request of interest ![]() sent at time
sent at time ![]() and the SoC of the request
and the SoC of the request ![]() sent at time
sent at time ![]() , and
, and ![]() and
and ![]() are the TCC of the request
are the TCC of the request ![]() sent at time
sent at time ![]() and the TCC of the request
and the TCC of the request ![]() sent at time
sent at time ![]() , and
, and ![]() .
.
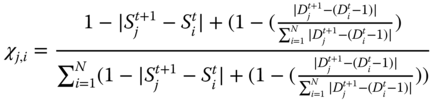
It is obvious that the term ![]() increases as
increases as ![]() and
and ![]() are close. Likewise, the term
are close. Likewise, the term ![]() increases as the TCC of the two requests are close. For two requests sent from the same ESU at times
increases as the TCC of the two requests are close. For two requests sent from the same ESU at times ![]() and
and ![]() , TCC at time
, TCC at time ![]() should be one less than the TCC at time
should be one less than the TCC at time ![]() . To guarantee that this part always gives a value in the range [0,1],
. To guarantee that this part always gives a value in the range [0,1], ![]() is normalized by
is normalized by ![]() .
.
The entropy can describe the uncertainly of the charging controller about linking various requests sent from the same ESUs. The maximum entropy (i.e., the highest anonymity level) can be achieved when the probabilities ![]() for
for ![]() follow a uniform distribution, i.e., all the
follow a uniform distribution, i.e., all the ![]() requests have a similar probability to be linked to request
requests have a similar probability to be linked to request ![]() . In this case, data privacy is completely ensured, and the charging controller cannot link a request to a certain ESU or even to a subset of ESUs. The maximum entropy (
. In this case, data privacy is completely ensured, and the charging controller cannot link a request to a certain ESU or even to a subset of ESUs. The maximum entropy (![]() ) is given in Equation 21.3.
) is given in Equation 21.3.
21.3.2.2 Charging Coordination
Once the sensitive information is concealed by using the aforementioned approaches, we next investigate how to utilize the information of the charging requests to calculate the charging schedules at every time slot. Each community is associated with an electric bus with loading limit of ![]() . At a given time slot, the regular load capacity is given by
. At a given time slot, the regular load capacity is given by ![]() . Thus, the accessible charging limit with respect to the ESUs at a given time slot is given by
. Thus, the accessible charging limit with respect to the ESUs at a given time slot is given by ![]() . Due to the limited capacity (
. Due to the limited capacity (![]() ), it is possible that not all ESUs with charging requests can charge at the present time slot. Rather, our scheme calculates a priority index for each ESU, and the ESUs with high priority will be charged at the present time slot to guarantee that
), it is possible that not all ESUs with charging requests can charge at the present time slot. Rather, our scheme calculates a priority index for each ESU, and the ESUs with high priority will be charged at the present time slot to guarantee that ![]() , while other ESUs' charging requests can be postponed to future time slots. Two components play a vital role in determining the ESU's priority for charging at the present time slot, to be specific, the TCC
, while other ESUs' charging requests can be postponed to future time slots. Two components play a vital role in determining the ESU's priority for charging at the present time slot, to be specific, the TCC ![]() and the battery SoC
and the battery SoC ![]() . In particular, an ESU with low
. In particular, an ESU with low ![]() and short
and short ![]() should have higher charging priority than an ESU with high
should have higher charging priority than an ESU with high ![]() and/or potentially long
and/or potentially long ![]() . Subsequently, for each ESU
. Subsequently, for each ESU ![]() , we specify a priority function
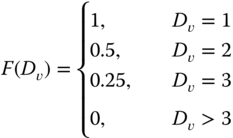
, we specify a priority function ![]() that is given by Equation 21.4, where
that is given by Equation 21.4, where ![]() is a decreasing function of
is a decreasing function of ![]() with a range of
with a range of ![]() and
and ![]() for long TCC and equals 1 for short TCC, and SoC value (
for long TCC and equals 1 for short TCC, and SoC value (![]() with
with ![]() for a completely charged ESU.
for a completely charged ESU.
The relative significance of ![]() and
and ![]() are given by using weights
are given by using weights ![]() and
and ![]() , with
, with ![]()
![]()
![]()
![]() . An ESU
. An ESU ![]() with low
with low ![]() value and short
value and short ![]() will have a high priority value
will have a high priority value ![]() . Henceforth, the CC's goal is to schedule the ESUs with highest priority for charging in the present time slot and postpone the charging of ESUs with lower priorities to future time slots because of the limit capacity in the present time slot. The charging schedules indicate whether a given ESU
. Henceforth, the CC's goal is to schedule the ESUs with highest priority for charging in the present time slot and postpone the charging of ESUs with lower priorities to future time slots because of the limit capacity in the present time slot. The charging schedules indicate whether a given ESU ![]() will be charged in the present time slot (
will be charged in the present time slot (![]() ) and the charging amount (
) and the charging amount (![]() ), where
), where

The charging coordination problem formulated in 21.5 is a mixed integer program (MIP) as it includes a real variable ![]() and a binary variable
and a binary variable ![]() , which makes it NP‐complete. For a large‐scale problem (i.e., a large community with numerous ESUs), it is difficult to solve 21.5 in real time. Rather than solving the MIP in 21.5, we reformulate the charging coordination problem using an integer program (IP) that is less complex than 21.5, and is given by
, which makes it NP‐complete. For a large‐scale problem (i.e., a large community with numerous ESUs), it is difficult to solve 21.5 in real time. Rather than solving the MIP in 21.5, we reformulate the charging coordination problem using an integer program (IP) that is less complex than 21.5, and is given by
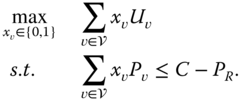
As indicated in 21.6, a scheduled ESU gets its charging demand (![]() ) in the present time slot. However, if the difference
) in the present time slot. However, if the difference ![]() is greater than 0 yet less than
is greater than 0 yet less than ![]() of all unscheduled ESUs, inefficient resource utilization is expected, as compared to 21.5 which ensures full resource utilization. To overcome such a disadvantage, the rest of the capacity after ESUs' scheduling as indicated by 21.6,
of all unscheduled ESUs, inefficient resource utilization is expected, as compared to 21.5 which ensures full resource utilization. To overcome such a disadvantage, the rest of the capacity after ESUs' scheduling as indicated by 21.6, ![]() , is assigned to the ESU with highest priority among all unscheduled ESUs. Such an ESU, which has not fully charged at the present time slot, will hold up to the next slot and get whatever is left of its charging request
, is assigned to the ESU with highest priority among all unscheduled ESUs. Such an ESU, which has not fully charged at the present time slot, will hold up to the next slot and get whatever is left of its charging request ![]() . A major advantage of the formulation in 21.6 is that it can be mapped to a well‐known optimization known as the knapsack problem (Kellerer et al. 2004).
. A major advantage of the formulation in 21.6 is that it can be mapped to a well‐known optimization known as the knapsack problem (Kellerer et al. 2004).
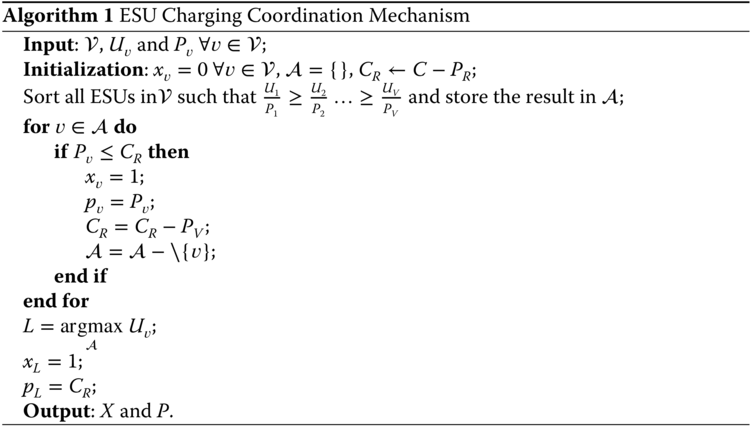
In the knapsack problem, there is a knapsack with limited capacity and a set of items each with a given value (priority) and weight. The goal is to select a subset of items to be packed in the knapsack, such that the overall value of the packed items is maximized while respecting the knapsack capacity limit. The charging coordination problem at every time slot can be described as a knapsack problem as follows. The ESUs are mapped to the items, the ESU priority ![]() resembles the item value, the ESU charging request
resembles the item value, the ESU charging request ![]() is equivalent to the item weight, and th charging limit constraint
is equivalent to the item weight, and th charging limit constraint ![]() represents the knapsack limit. We modified a greedy algorithm designed for solving the knapsack problem in polynomial time given in (Kellerer et al. 2004) to schedule ESU charging at each time slot. Hence, the charging coordination mechanism can be described using Algorithm 1, which is implemented at the CC.
represents the knapsack limit. We modified a greedy algorithm designed for solving the knapsack problem in polynomial time given in (Kellerer et al. 2004) to schedule ESU charging at each time slot. Hence, the charging coordination mechanism can be described using Algorithm 1, which is implemented at the CC.
21.4 Performance Evaluation
21.4.1 Privacy/Security Analysis
Neither the aggregator nor eavesdroppers can learn whether an ESU needs to charge or not or the amount of energy it needs. This is because the charging requests and schedules are encrypted by the CC's public key and one‐time keys. Also, an ESU should send a charging request with zero charging demand when it does not need to charge.
In a case that an eavesdropper colludes with the CC, they cannot link the charging requests to the ESUs in light of the fact that they cannot link the public‐key encryption (![]() ) received by the CC to the symmetric‐key encryption (
) received by the CC to the symmetric‐key encryption (![]() ) sent by an ESU. They cannot likewise link a schedule to its ESU as the schedules are encrypted with the keys shared with aggregator. Without this encryption, an eavesdropper can get the schedule packet (
) sent by an ESU. They cannot likewise link a schedule to its ESU as the schedules are encrypted with the keys shared with aggregator. Without this encryption, an eavesdropper can get the schedule packet (![]() ) and the CC can decrypt the schedule and link it to
) and the CC can decrypt the schedule and link it to ![]() .
.
In a case that an ESU sends the same charging request information in consecutive time slots, the ciphertexts ![]() do not look the same because
do not look the same because ![]() is utilized for only one time. For a similar reason, the ciphertexts of same schedules (
is utilized for only one time. For a similar reason, the ciphertexts of same schedules (![]() ) look different.
) look different.
The ESUs can guarantee that the schedules are sent from the CC as no entity can recover ![]() aside from the CC. The ESUs can likewise guarantee that the schedule packets are sent from the aggregator since it appends its signature. The aggregator can ensure that the charging requests are sent from the ESUs since they are signed.
aside from the CC. The ESUs can likewise guarantee that the schedule packets are sent from the aggregator since it appends its signature. The aggregator can ensure that the charging requests are sent from the ESUs since they are signed.
The CC gets enough information to run the charging coordination scheme, and privacy can be safeguarded due to the fact that the CC cannot link the charging requests to the ESUs. The CC cannot utilize the charging requests' identities or symmetric keys to link the requests of an ESU over consecutive time slots. This is on account of the random and secret identity permutation that is utilized by the aggregator and the one‐time random key that is utilized as a part of each charging request. Furthermore, noise addition to the charging requests can make linking the requests of an ESU over consecutive time slots hard.
In addition to privacy preservation, the proposed scheme is robust against repudiation attacks. An aggregator can ensure that a particular ESU performs a specific transaction or requests a service using the ESU's signature ![]() sent in the charging request packet (
sent in the charging request packet (![]() ). This signature is sent in the packet that contains the real identity of the ESU, and the aggregator has to verify the signature before forwarding the request to the CC to guarantee that the packet is sent from a legitimate ESU. No one other than the ESU can compute a valid signature because the private key needed to compute the signature is known only to the ESU. Furthermore, we can classify the compromised ESUs to two types, internal and external attackers. Our proposed scheme is protected against external attackers that aim to disrupt the proper operation of the charging coordination mechanism due to requesting each ESU to send a signature to the aggregator. For the internal attackers, if an attacker tries to send charging requests outside its community, the aggregator can detect the attack because it knows the identities of all ESUs in its community.
). This signature is sent in the packet that contains the real identity of the ESU, and the aggregator has to verify the signature before forwarding the request to the CC to guarantee that the packet is sent from a legitimate ESU. No one other than the ESU can compute a valid signature because the private key needed to compute the signature is known only to the ESU. Furthermore, we can classify the compromised ESUs to two types, internal and external attackers. Our proposed scheme is protected against external attackers that aim to disrupt the proper operation of the charging coordination mechanism due to requesting each ESU to send a signature to the aggregator. For the internal attackers, if an attacker tries to send charging requests outside its community, the aggregator can detect the attack because it knows the identities of all ESUs in its community.
21.4.2 Experimental Study
21.4.2.1 Setup
MATLAB is utilized to evaluate the performance of the proposed privacy‐preserving charging coordination scheme. We set the ESUs' battery capacity to 200 units of power, and the accessible charging limit per time slot (![]() ) is 1000 units of power. We ran the simulation for 30 time slots, i.e., the slot span
) is 1000 units of power. We ran the simulation for 30 time slots, i.e., the slot span ![]() . At first, the framework has 7 ESUs that need to charge, and the arrival of new charging requests in every time slot follows a Poisson distribution with an average of
. At first, the framework has 7 ESUs that need to charge, and the arrival of new charging requests in every time slot follows a Poisson distribution with an average of ![]() . The SoC of each ESU battery is a random number uniformly distributed in
. The SoC of each ESU battery is a random number uniformly distributed in ![]() . Time to complete charging (
. Time to complete charging (![]() ) is a random number that follows a geometric distribution with an average of 4. The presented results are the average of 80 runs. For the priority function,
) is a random number that follows a geometric distribution with an average of 4. The presented results are the average of 80 runs. For the priority function, ![]() is set as follows
is set as follows
21.4.2.2 Metrics and Baselines
To measure the performance, we use the following metrics:
- Average satisfaction index per ESU: This metric measures to what degree ESUs' owners are fulfilled. It is calculated by dividing the amount of power an ESU charges by the amount of power required by the ESU. The satisfaction index is a value in the range [0,1], where 1 demonstrates full satisfaction, i.e., the ESU was completely charged before its charging request expires.
- Average number of expired requests without full charge: This metric measures the average number of requests that expire without full charge. Performance degradation due to the inability of the system to fully charge a large number of ESUs can be shown by the large values of this metric.
We will utilize equations explained in section 21.3.2.1 to measure the privacy level achieved by the noise addition. We will compare the privacy‐aware charging coordination scheme with two benchmarks:
- FCFS benchmark: In this approach, the ESU that requests charging first gets charged first regardless of the request TCC and SoC.
- Optimal coordination scheme: This approach utilizes the modified knapsack‐based ideal charging coordination mechanism without applying noise addition.
21.4.2.3 Simulation Results
For ![]() and
and ![]() , we attempted every conceivable values, and the optimal values were observed to be 0.9 and 0.1, respectively, as they result in the largest number of served ESUs and the highest satisfaction index at various charging demand rates.
, we attempted every conceivable values, and the optimal values were observed to be 0.9 and 0.1, respectively, as they result in the largest number of served ESUs and the highest satisfaction index at various charging demand rates.
Figure 21.5 presents the average number of expired requests without full charge at various charging request rates (![]() ), and Figure 21.6 gives the average satisfaction index at various values of
), and Figure 21.6 gives the average satisfaction index at various values of ![]() . The figures show the performance of the FCFS and our schemes without including noise and with adding random uniformly distributed noise to the SoC and TCC values up to
. The figures show the performance of the FCFS and our schemes without including noise and with adding random uniformly distributed noise to the SoC and TCC values up to ![]() 15% and
15% and ![]() 30%.
30%.
In the figures, we consider two situations where 100% and 30% of the ESUs add noise. The figures can show that our scheme has less number of expired requests before the full charge and can accomplish a higher satisfaction index unlike the FCFS. Furthermore, as ![]() increases, our scheme presents a significant performance improvement compared with the FCFS, which demonstrates that a charging coordination scheme is completely necessary when the charging demand is much larger than the charging limit (
increases, our scheme presents a significant performance improvement compared with the FCFS, which demonstrates that a charging coordination scheme is completely necessary when the charging demand is much larger than the charging limit (![]() ). In this situation, our scheme can exploit the accessible resources to serve more demands before they expire by organizing the requests and serving the high priority requests first. A degradation in the performance can be observed as the number of ESUs that add noise increases. This can be credited to the fact that as the CC gets inaccurate data, the charging coordination deviates from the ideal results.
). In this situation, our scheme can exploit the accessible resources to serve more demands before they expire by organizing the requests and serving the high priority requests first. A degradation in the performance can be observed as the number of ESUs that add noise increases. This can be credited to the fact that as the CC gets inaccurate data, the charging coordination deviates from the ideal results.

Figure 21.5
Average number of expired requests without full charge versus charging request rate (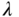 ).
).
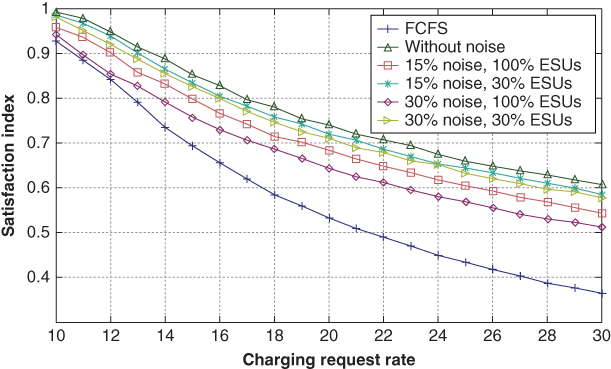
Figure 21.6 Average satisfaction index versus charging request rate.

Figure 21.7 Average entropy in case of 15% noise addition versus charging request rate.
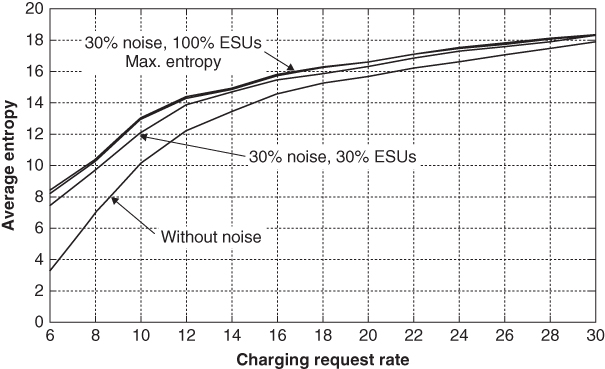
Figure 21.8 Average entropy in case of 30% noise addition versus charging request rate.
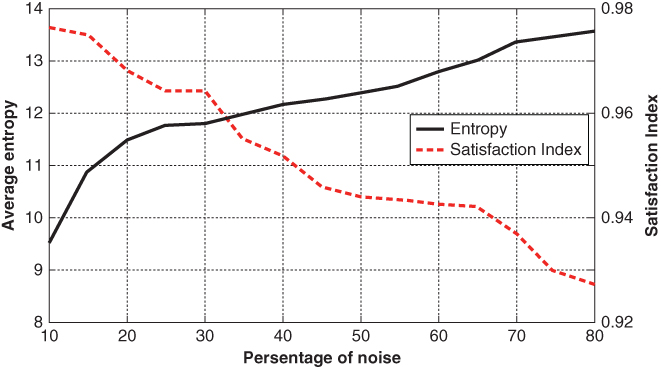
Figure 21.9
Average entropy and satisfaction versus noise with 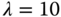 .
.

Figure 21.10
Average entropy and satisfaction versus noise with  .
.
Figures 21.7 and 21.8 present the average entropy versus the charging demand rate when adding up to ![]() 15% and
15% and ![]() 30% noise, respectively. To measure the average entropy, we utilized Equation (6) to calculate the entropy of every request at every time slot. Compared with the case that has no noise addition, it can be seen that the entropy value improves by adding noise. This shows that it is harder for the CC to link an ESU's requests since adding noise can decrease the probability of linking an ESU's request at time
30% noise, respectively. To measure the average entropy, we utilized Equation (6) to calculate the entropy of every request at every time slot. Compared with the case that has no noise addition, it can be seen that the entropy value improves by adding noise. This shows that it is harder for the CC to link an ESU's requests since adding noise can decrease the probability of linking an ESU's request at time ![]() to the same ESU's request at time
to the same ESU's request at time ![]() . The figures also demonstrate that the entropy value improves as the noise level increases.
. The figures also demonstrate that the entropy value improves as the noise level increases.
The maximum entropy can be obtained when ![]() is the same for all requests. In this case, it is difficult to link requests. The figures demonstrate that the entropy achieved by adding noise is near the maximum entropy. Also, it can be seen that as
is the same for all requests. In this case, it is difficult to link requests. The figures demonstrate that the entropy achieved by adding noise is near the maximum entropy. Also, it can be seen that as ![]() increases, the difference in privacy level between the instances with and without noise addition reduces. This is because as the number of requests increases, several requests can present SoC and TCC values that are close to the request of interest, and thus it is harder to link requests. This demonstrates that including noise is more helpful at low charging request rates and as the request rate increases, as it gets harder to link the requests because of the vast space of various requests. The fewer the number of ESUs that add noise, the less the entropy, and hence more noise should be added to maintain high entropy. In all cases, the optimal and privacy‐aware sub‐optimal charging coordination schemes display better performance compared with the FCFS particularly for high charging request rates.
increases, the difference in privacy level between the instances with and without noise addition reduces. This is because as the number of requests increases, several requests can present SoC and TCC values that are close to the request of interest, and thus it is harder to link requests. This demonstrates that including noise is more helpful at low charging request rates and as the request rate increases, as it gets harder to link the requests because of the vast space of various requests. The fewer the number of ESUs that add noise, the less the entropy, and hence more noise should be added to maintain high entropy. In all cases, the optimal and privacy‐aware sub‐optimal charging coordination schemes display better performance compared with the FCFS particularly for high charging request rates.
The outcomes additionally uncover an interesting result with respect to the trade‐offs between privacy preservation and the charging coordination performance. Adding noise to SoC and ![]() enhances privacy since it can make linking an ESU's requests by the CC hard as affirmed by the entropy measurements given in Figures 21.7 and 21.8. However, it somewhat degrades the charging coordination performance compared with the given results of no noise addition cases as demonstrated in Figures 21.5 and 21.6. The four figures demonstrate that the performance of the charging coordination degrades with more gains in the privacy as the noise level increases. It can be seen that the performance of our scheme is still much superior to the FCFS, and a large amount of noise may not be required in the event of extensive number of charging requests.
enhances privacy since it can make linking an ESU's requests by the CC hard as affirmed by the entropy measurements given in Figures 21.7 and 21.8. However, it somewhat degrades the charging coordination performance compared with the given results of no noise addition cases as demonstrated in Figures 21.5 and 21.6. The four figures demonstrate that the performance of the charging coordination degrades with more gains in the privacy as the noise level increases. It can be seen that the performance of our scheme is still much superior to the FCFS, and a large amount of noise may not be required in the event of extensive number of charging requests.
To investigate the impact of noise addition on the charging coordination performance, Figures 21.9 and 21.10 demonstrate the trade‐off between the satisfaction index and the average entropy versus the noise level at ![]() and 20, respectively. As shown in the figures, increasing the noise level can increase the entropy; however, it reduces the satisfaction index. Furthermore, for the same noise level, the entropy increases as
and 20, respectively. As shown in the figures, increasing the noise level can increase the entropy; however, it reduces the satisfaction index. Furthermore, for the same noise level, the entropy increases as ![]() increases. The figures outline the trade‐off between privacy preservation and charging coordination performance. Noisy data can enhance the entropy yet decreases charging coordination performance. This trade‐off is not noteworthy at large
increases. The figures outline the trade‐off between privacy preservation and charging coordination performance. Noisy data can enhance the entropy yet decreases charging coordination performance. This trade‐off is not noteworthy at large ![]() , i.e., our scheme can accomplish high privacy preservation with superior charging coordination performance at large
, i.e., our scheme can accomplish high privacy preservation with superior charging coordination performance at large ![]() .
.
21.5 Summary
In this chapter, we have presented a privacy‐preserving charging coordination approach that can hide sensitive information while achieving high charging coordination performance. Our goal is to maximize the number of served charging requests before they expire without revealing private information or exceeding the maximum charging capacity. Simulation results revealed that both the optimal charging coordination scheme and the privacy‐aware charging coordination scheme exhibit an enhanced performance compared with FCFS approach particularly at a large charging demand situation. Also, the privacy‐aware scheme offers an interesting trade‐off between the charging coordination performance and privacy preservation. Our analysis has demonstrated that our approach can preserve privacy, and noise addition is an effective method to prevent linking requests. This has been qualitatively measured using entropy.
Our proposed scheme is secure against the external attackers that aim to disrupt the proper operation of the charging coordination scheme. In addition, the proposed scheme can also detect the internal attackers who send fake charging requests outside their community. In future work, we will extend the proposed charging coordination mechanism to secure it against internal attacks launched by compromised ESUs inside the same community.
Acknowledgment
This publication was made possible by NPRP grant # NPRP 9‐055‐2‐022 from the Qatar National Research Fund (a member of Qatar Foundation). The statements made herein are solely the responsibility of the authors.
References
- Tesla Home Batteries. http://money.cnn.com/2015/04/22/technology/tesla‐home‐battery/. Accessed: 05‐06‐2015.
- P. Akula, M. Mahmoud, K. Akkaya, and M. Songi. Privacy‐preserving and secure communication scheme for power injection in smart grid. In 2015 IEEE International Conference on Smart Grid Communications (SmartGridComm), pages 37–42, 2015.
- V. Aravinthan, V. Namboodiri, S. Sunku, and W. Jewell. Wireless ami application and security for controlled home area networks. In 2011 IEEE Power and Energy Society General Meeting, pages 1–8, July 2011. doi:10.1109/PES.2011.6038996.
- I. Bayram, M. Ismail, M. Abdallah, K. Qaraqe, and E. Serpedin. A pricing‐based load shifting framework for ev fast charging stations. In 2014 IEEE International Conference on Smart Grid Communications (SmartGridComm), pages 680–685, 2014.
- J. Benoit. An introduction to cryptography as applied to the smart grid. 2011.
- A. Beussink, K. Akkaya, I. Senturk, and M. Mahmoud. Preserving consumer privacy on ieee 802.11s‐based smart grid ami networks using data obfuscation. In 2014 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), pages 658–663, 2014.
- G. Brusco, A. Burgio, D. Menniti, A. Pinnarelli, and N. Sorrentino. Energy management system for an energy district with demand response availability. IEEE Transactions on Smart Grid, 5(5):2385–2393, Sept 2014.
- K. Clement, E. Haesen, and J. Driesen. Coordinated charging of multiple plug‐in hybrid electric vehicles in residential distribution grids. In Proc. of IEEE/PES Power Systems Conference and Exposition, PSCE'09, pages 1–7, 2009.
- T. Cover and J. Thomas. Elements of information theory. John Wiley & Sons, Inc., 1991. ISBN 0‐471‐06259‐6.
- S. Deilami, A. Masoum, P. Moses, and M. Masoum. Real‐time coordination of plug‐in electric vehicle charging in smart grids to minimize power losses and improve voltage profile. IEEE Transactions on Smart Grid, 2(3):456–467, 2011.
- C. Díaz, S. Seys, J. Claessens, and B. Preneel. Towards measuring anonymity. Proceedings of the 2Nd International Conference on Privacy Enhancing Technologies, San Francisco, CA, USA, 2003.
- W. Diffie and M. Hellman. New directions in cryptography. IEEE Transactions on Information Theory, 22(6):644–654, Nov 1976. ISSN 0018‐9448. doi:10.1109/TIT.1976.1055638.
- M. Faisal, Z. Aung, J. Williams, and A. Sanchez. Securing Advanced Metering Infrastructure Using Intrusion Detection System with Data Stream Mining, pages 96–111. Springer Berlin Heidelberg, Berlin, Heidelberg, 2012. ISBN 978‐3‐642‐30428‐6. doi:10.1007/978-3-642-30428-6_8. URL http://dx.doi.org/10.1007/978‐3‐642‐30428‐6_8.
- A. Giani, E. Bitar, M. Garcia, M. McQueen, P. Khargonekar, and K. Poolla. Smart grid data integrity attacks: characterizations and countermeasures;. In 2011 IEEE International Conference on Smart Grid Communications (SmartGridComm), pages 232–237, Oct 2011. 10.1109/SmartGridComm.2011.6102324.
- K. R. M. M. H. Mohammed, S. Tonyali and K. Akkaya. Efficient privacy‐preserving data collection scheme for smart grid ami networks. In Proc. of IEEE Globecom 2016, Washington DC, USA, 2016.
- Z. Haddad, M. Mahmoud, S. Taha, and I. Saroit. Secure and privacy‐preserving ami‐utility communications via lte‐a networks. In 2015 IEEE 11th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), pages 748–755, 2015.
- Z. Haddad, M. Mahmoud, I. Saroit, and S. Taha. Secure and efficient uniform handover scheme for lte‐a networks. In 2016 IEEE Wireless Communications and Networking Conference, pages 1–6, 2016.
- S. Hadley and A. Tsvetkova. Potential impacts of plug‐in hybrid electric vehicles on regional power generation. Electricity Journal, 22(10):56–68, 2009.
- W. Han and Y. Xiao. Ip2dm: integrated privacy‐preserving data management architecture for smart grid v2g networks. Wireless Communications and Mobile Computing, 16(17):2956–2974, 2016. ISSN 1530‐8677. doi:10.1002/wcm.2740. URL http://dx.doi.org/10.1002/wcm.2740. wcm.2740.
- M. Ismail, I. Bayram, M. Abdallah, E. Serpedin, and K. Qaraqe. Optimal planning of fast pev charging facilities. In 2015 First Workshop on Smart Grid and Renewable Energy (SGRE), pages 1–6, 2015a.
- M. Ismail, E. Serpedin, and K. Qaraqe. Pev charging in the future smart grid. In 2015 International Symposium on Signals, Circuits and Systems (ISSCS), pages 1–4, 2015b.
- H. Kellerer, U. Pferschy, and D. Pisinger. Knapsack problems. 2004. Springer, Berlin.
- H. Khurana, M. Hadley, N. Lu, and D. Frincke. Smart‐grid security issues. IEEE Security Privacy, 8(1):81–85, Jan 2010. ISSN 1540‐7993. doi:10.1109/MSP.2010.49.
- S. Lukic, J. Cao, R. Bansal, F. Rodríguez, and A. Emadi. Energy storage systems for automotive applications. IEEE Transactions on Industrial Electronics, 55(6):2258–2267, 2008.
- M. Mahmoud, S. Taha, J. Misic, and X. Shen. Lightweight privacy‐preserving and secure communication protocol for hybrid ad hoc wireless networks. IEEE Transactions on Parallel and Distributed Systems, 2014.
- M. Mahmoud, M. Ismail, P. Akula, K. Akkaya, E. Serpedin, and K. Qaraqe. Privacy‐aware power charging coordination in future smart grid. In 2016 IEEE Wireless Communications and Networking Conference, pages 1–6, April 2016a. doi:10.1109/WCNC.2016.7564967.
- M. Mahmoud, N. Saputro, P. Akula, and K. Akkaya. Privacy‐preserving power injection over a hybrid ami/lte smart grid network. IEEE Internet of Things Journal, 2016b.
- M. Nabeel, S. Kerr, X. Ding, and E. Bertino. Authentication and key management for advanced metering infrastructures utilizing physically unclonable functions. In 2012 IEEE Third International Conference on Smart Grid Communications (SmartGridComm), pages 324–329, Nov 2012. doi:10.1109/SmartGridComm.2012.6486004.
- National Institute of Standards and Technology. NIST framework and roadmap for smart grid interoperability standards, release 1.0. http://www.nist.gov/public_affairs/releases/upload/smartgrid_interoperability_final.pdf, January 2010.
- Nissan LEAF Electric Car. Available: http://www.nissanusa.com/leaf‐electric‐car.
- NIST. Guidelines for smart grid cyber security: vol. 3 supportive analyses and references. NISTIR 7628, The Smart Grid Interoperability Panel ‐ Cyber Security Working Group, August 2010.
- E. Oriero, K. Rabieh, M. Mahmoud, M. Ismail, E. Serpedin, and K. Qaraqe. Trust‐based and privacy‐preserving fine‐grained data retrieval scheme for msns. In 2016 IEEE Wireless Communications and Networking Conference, pages 1–6, 2016.
- P. Akula, M. Mahmoud, K. Akkaya, and M. Song. Privacy‐preserving and secure communication scheme for power injection in smart grid. Proc. of IEEE International Conference on Smart Grid Communications, 2015.
- K. Rabieh, M. Mahmoud, M. Azer, and M. Allam. A secure and privacy‐preserving event reporting scheme for vehicular ad hoc networks. Security and Communication Networks, 2015a.
- K. Rabieh, M. Mahmoud, T. Guo, and M. Younis. Cross‐layer scheme for detecting large‐scale colluding sybil attack in vanets. In 2015 IEEE International Conference on Communications (ICC), pages 7298–7303, 2015b.
- K. Rabieh, M. Mahmoud, A. Siraj, and J. Misic. Efficient privacy‐preserving chatting scheme with degree of interest verification for vehicular social networks. In 2015 IEEE Global Communications Conference (GLOBECOM), pages 1–6, 2015c.
- K. Rabieh, M. Mahmoud, and M. Younis. Privacy‐preserving route reporting scheme for traffic management in vanets. In 2015 IEEE International Conference on Communications (ICC), pages 7286–7291, 2015d.
- K. Rabieh, M. Mahmoud, and M. Younis. Privacy‐preserving route reporting schemes for traffic management systems. IEEE Transactions on Vehicular Technology, 2016.
- N. Saputro, K. Akkaya, and S. Uludag. A survey of routing protocols for smart grid communications. Elsevier Compututer Networks, 56(11):2742–2771, July 2012. ISSN 1389‐1286.
- M. Shaaban, M. Ismail, and E. El‐Saadany. Pevs real‐time coordination in smart grid based on moving time window. In 2014 IEEE PES General Meeting — Conference Exposition, pages 1–5, 2014a.
- M. Shaaban, M. Ismail, E. El‐Saadany, and W. Zhuang. Real‐time pev charging/discharging coordination in smart distribution systems. IEEE Transactions on Smart Grid, 2014b.
- A. Sherif, K. Rabieh, M. Mahmoud, and X. Liang. Privacy‐preserving ride sharing scheme for autonomous vehicles in big data era. IEEE Internet of Things Journal, 2016.
- E. Sortomme, M. Hindi, S. MacPherson, and S. Venkata. Coordinated charging of plug‐in hybrid electric vehicles to minimize distribution system losses. IEEE Transactions on Smart Grid, 2(1):198–205, March 2011.
- W. Stallings. Network Security Essentials: Applications and Standards. Prentice Hall Press, Upper Saddle River, NJ, USA, 4th edition, 2010. ISBN 0136108059, 9780136108054.
- O. Sundstrom and C. Binding. Flexible charging optimization for electric vehicles considering distribution grid constraints. IEEE Transactions on Smart Grid, 2012.
- S. Tonyali, O. Cakmak, K. Akkaya, M. Mahmoud, and I. Guvenc. Secure data obfuscation scheme to enable privacy‐preserving state estimation in smart grid ami networks. IEEE Internet of Things Journal, 2016.
- B. Vaidya, D. Makrakis, and H. Mouftah. Device authentication mechanism for smart energy home area networks. In 2011 IEEE International Conference on Consumer Electronics (ICCE), pages 787–788, Jan 2011. doi:10.1109/ICCE.2011.5722864.
- R. Verzijlbergh, M. Grond, Z. Lukszo, J. Slootweg, and M. Ilic. Network impacts and cost savings of controlled ev charging. IEEE Transactions on Smart Grid, 2012.
- Z. Wan, W.‐T. Zhu, and G. Wang. Prac: Efficient privacy protection for vehicle‐to‐grid communications in the smart grid. Computers & Security, 62: 246 –256, 2016. ISSN 0167‐4048. ttps://doi.org/10.1016/j.cose.2016.07.004. URL http://www.sciencedirect.com/science/article/pii/S0167404816300761.
- M. Wang, M. Ismail, R. Zhang, X. Shen, E. Serpedin, and K. Qaraqe. A semi‐distributed v2v fast charging strategy based on price control. In 2014 IEEE Global Communications Conference, pages 4550–4555, 2014.
- M. Wang, M. Ismail, X. Shen, E. Serpedin, and K. Qaraqe. Spatial and temporal online charging/discharging coordination for mobile pevs. IEEE Wireless Communications, 2015.
- M. Wang, M. Ismail, R. Zhang, X. Shen, E. Serpedin, and K. Qaraqe. Spatio‐temporal coordinated v2v fast charging strategy for mobile gevs via price control. IEEE Transactions on Smart Grid, 2016.
- Z. Xiao, Y. Xiao, and D. Du. Non‐repudiation in neighborhood area networks for smart grid. IEEE Communications Magazine, 51(1):18–26, January 2013. ISSN 0163‐6804. doi:10.1109/MCOM.2013.6400434.
- Y. Yan, Y. Qian, H. Sharif, and D. Tipper. A survey on cyber security for smart grid communications. IEEE Communications Surveys Tutorials, 14(4): 998–1010, Fourth 2012. ISSN 1553‐877X. doi:10.1109/SURV.2012.010912.00035.
