CHAPTER 9. Virtual LANs
SOME OF THE MAIN TOPICS IN THIS CHAPTER ARE
Virtual LANs and Network Topologies 138
Switching Based on Network Frames 139
Implicit and Explicit Tagging 141
IEEE Standards for Virtual LANs 144
What Kind of Switch Should You Buy? 146
Chapter 8, “Network Switches,” discussed switches that can be used to reduce the broadcast domain limit imposed by earlier networking technologies, such as hubs and bridges. LAN switches can be used to solve more problems than just reducing network traffic, however. This chapter discusses how switches can be used to create virtual LANs, or VLANs. Besides reducing the broadcast domain, switches configured for use in a VLAN can be used to solve many other problems:
![]() The changing physical topology of the LAN
The changing physical topology of the LAN
![]() Security on the LAN
Security on the LAN
![]() Performance issues
Performance issues
![]() Centralized management of multiple LANs
Centralized management of multiple LANs
![]() Limiting multicast traffic
Limiting multicast traffic
Although a router can also be used to reduce a broadcast domain and create separate subnets in a network, switching technology works at a much faster pace. Thus, using VLANs in your network probably can enable you to get rid of a few slow routers that currently are being used to segment a LAN.
Virtual LANs and Network Topologies
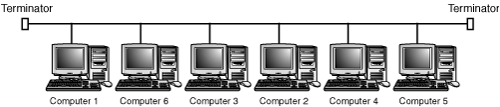
When discussing local area networks, most network administrators think of the physical topology of the LAN—that is, the switches, servers, and workstations, and how they connect to form the LAN. The physical topology, as you learned in Chapter 2, “Overview of Network Topologies,” doesn’t have to match the logical topology of the LAN. As an early example, the Token-Bus network topology (IEEE 802.4 standard) uses a single coaxial cable to connect computers into a LAN. However, the order in which individual computers gain access to this shared cable is not the order in which they exist on the cable. In Figure 9.1, you can see that six computers are connected to a single cable. In this example, you can assume that the computers are numbered in a manner that represents their actual network address (Token-Bus addresses actually can range in size from 2 to 5 bytes). For this figure, the numbers 1–6 are used instead of the network address. In a token-passing network, a token frame is passed from one computer to another, and it is this token frame that gives a computer the right to transmit data on the network.
Figure 9.1. An early Token-Bus network uses a token frame to determine which computer can transmit data on the cable.
Although in this figure it might seem logical that the token frame would be passed from Computer 1 to Computer 6, and then to Computer 3, that is not how Token-Bus networks function. The physical topology is a linear bus, in which a message broadcast on the cable by Computer 1 travels down the wire until it reaches the terminator that is placed after Computer 5 at the end of the segment.
The logical topology of a Token-Bus network, however, is that of a ring. Although all computers on the same cable segment can “hear” the broadcast that every other computer makes, communications take place in an orderly manner. The token frame is “passed” in numerical address order from Computer 1 to Computer 2, then to Computer 3, and so on. This example is intended to show you the difference between a logical and a physical topology. The physical layout of the network is a linear bus. The logical topology of this network is a ring.
So what does this have to do with virtual LANs? A lot. Early LAN technologies, such as Ethernet, were limited in their size and distance by the physical topology of the LAN. You can read about this in Chapter 13, “Ethernet: The Universal Standard.” Even Token-Ring networks are limited in size based on the physical topology of the network. Switches, as you learned in the preceding chapter, enable you to greatly expand the number of computers you can place on a LAN, and you can use high-speed communication links between switches to greatly expand the distance of a LAN.
However, using switches to create a huge LAN solves only the problem of the broadcast domain and the number of devices that can be attached to the network. In a modern networking environment, there are other factors to consider, such as security, configuration, and management. Perhaps you don’t want all your computers connected to the same LAN, though they may be in close proximity to the same LAN switch. The more computers you have on a single LAN, the greater the odds are that a security breach will occur—giving an intruder access to other computers on the LAN.
Virtual LANs, which can be created using switches, enable you to separate the physical topology from the logical topology. That is, although you might have all your computers interconnected using a switch or several switches, appropriately configured switches make it possible to configure individual virtual LANs that are independent of the physical topology. Legacy hubs allow all computers on the LAN to see every network frame that is transmitted by every other computer in the same broadcast domain. Switches make connections only between the transmitting computer and the switch port that will get the network frame to its eventual destination. By limiting the network frame to just the sending and receiving stations, and the switches that stand between them, you take a big step toward preventing eavesdropping on the LAN.
Note
If you have not yet read the preceding chapter, “Network Switches,” you should do so before attempting to understand the concepts covered in this chapter. For those readers who have been working in the networking industry for a long time, be aware that switches have replaced hubs in every LAN except for the oldest because switches provide a dramatic increase in performance versus cost. If you don’t understand how a switch works, you will probably not get a lot of useful information out of this chapter.
Switching Based on Network Frames
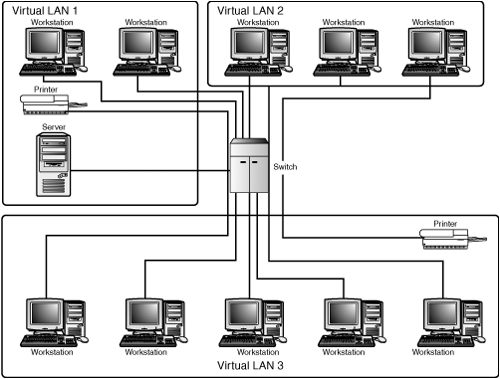
It should be obvious that, using various techniques, it is possible to physically connect a large number of computers using switches, and then use software to program the switches to limit which computers can transmit frames to other computers. In other words, you can define LANs using software inside the switch, instead of creating LANs based on the actual physical cabling (see Figure 9.2). This single switch connects several computers, printers, and a server. However, the switch separates these devices into three separate virtual LANs.
Figure 9.2. Virtual LANs can be created so that separate LANs exist on the same switch.
Of course, this is a very simplistic example. If you have such a small number of computers, one of the only reasons you would want to create virtual LANs would be for security purposes. This example is meant to show that you can connect multiple network devices (computers, printers, print servers, file servers, routers, and so on) to the same switch, or a set of switches, and then use software that comes with the switch(es) to assign each computer to a separate virtual LAN. Computers on the same virtual LAN can communicate with each other just as if they were joined by a single switch. However, just because all these networked devices are connected to the same switch doesn’t mean that they can send or receive data with devices that are configured on a different virtual LAN. In essence, it appears that you are partitioning the ports on the switch as though they were separate switches. That doesn’t have to be the case, but it was the first step in creating VLAN switches.
In this chapter it is easy to state that you can create several VLANs using a single switch. From a practical standpoint, however, a single switch is not a limiting factor. Indeed, it is usually the case that multiple switches are installed in a computer rack, and the management software that controls the switches enables you to assign ports from different switches to a VLAN. It is also possible for a switch port to be a member of more than one VLAN.
Implicit and Explicit Tagging
In more modern VLAN switches, the individual network devices or ports are not used to define the VLAN; the network frames—each handled on a case-by-case basis that the switch receives—are used. A modern VLAN, then, is based on frames, not on the computers that generate them or those to which they are addressed, or the ports to which either is attached.
In VLAN terminology, the term tagging is used to indicate what data is used to associate a frame with a particular VLAN. There are two kinds of tagging: implicit and explicit.
Implicit Tagging
Implicit tagging means that the decision is based on data that is already present in the existing frame format, such as an Ethernet frame. The data is already there, and nothing has been added; so the switch simply must examine data in the frame header and implicitly decide to which VLAN it belongs. When this type of tagging is used, no additional data needs to be added to the frame by the sending computer, so the devices on the network are considered to be VLAN-unaware. That is, they operate just as they normally would and have no idea that they are on one or another VLAN. You might as well just call this “nontagging,” but the writers of the specifications have chosen to call this implicit tagging.
When implicit tagging is used, the frame data that typically is used to create VLAN association rules is generally one of the following:
![]() Protocol—The network protocol, such as IP or AppleTalk.
Protocol—The network protocol, such as IP or AppleTalk.
![]() Data Link Source Address—The hardware address of the source of the frame. Remember that hardware addresses, also known as MAC addresses, are unique addresses burned into the card at the factory when the card is manufactured. They provide a flat address space, but they should be unique from any other such address through the world.
Data Link Source Address—The hardware address of the source of the frame. Remember that hardware addresses, also known as MAC addresses, are unique addresses burned into the card at the factory when the card is manufactured. They provide a flat address space, but they should be unique from any other such address through the world.
![]() Upper-level protocol identifiers—In addition to a protocol type, such as IP, a subnet address identifier may be used to identify which VLAN a frame is associated with.
Upper-level protocol identifiers—In addition to a protocol type, such as IP, a subnet address identifier may be used to identify which VLAN a frame is associated with.
Another method that can be used for implicit tagging involves upper-level applications. However, because this can create literally hundreds of rules, it often is not used except in large WANs. This technology is called “explicit tagging.”
Explicit Tagging
Explicit tagging refers to actually attaching an extra few bits of data to a network frame to specify its VLAN association. For this method to work, however, the sending station must be aware that VLANs exist. The switch itself also must understand explicit tagging and know where in the frame to look for the tagging data. For example, in a VLAN-aware network adapter, it is common to place a few bytes after the source address in the Ethernet frame. These additional bytes provide the explicit VLAN tag that the switch can examine to determine which VLAN the frame belongs to. Instead of having to apply a set of rules, the VLAN-aware switch can simply examine this value and quickly switch the frame to the correct output port. Because the tag is placed inside the Ethernet frame after the source and destination address, however, a switch that is not VLAN-aware (that is, does not use explicit tagging) cannot make decisions based on protocol type or other fields. This is because additional fields will be offset a number of bytes, depending on the length of the explicit tag. This can lead to nonaware switches or computers misinterpreting the tagging data and producing unpredictable behavior.
The solution to this problem is to use “edge switches” that receive explicitly tagged frames from VLAN-aware devices and remove the tags when they forward the frame to a port connected to another switch or device that is not equipped to handle explicitly tagged frames.
Explicit tagging does have some advantages over implicit tagging, however. Because the switch only has to look at the tag, and it’s always in the same place (for a given protocol), it’s easy to implement in hardware a quick switching fabric that can handle a large number of frames in a short period. Implicit tagging must check the rule set to determine what VLAN a frame belongs to, and this can involve more processing time. Although the amount of time might be just a few milliseconds, which seems like a short time to you or me, that’s a lot of time when you’re switching hundreds of thousands of packets in a short period. As you’ll find out in the next chapter, a similar situation occurs with routers. A switch forwards a network frame quicker than many routers because the router must spend time digging into the frame to find the protocol address, and then perform a lookup in a routing table to determine how to deal with the frame and recalculate the frame check sequence (FCS).
On the downside, when a switch that uses explicit tagging has to forward a frame to a switch or device that does not, it must remove the tag. When this happens, it’s necessary to recalculate the FCS value because some of the frame bits have been removed. Another drawback is that attaching an explicit tag to a large frame can cause the frame to exceed the maximum size allowed by the transport protocol, and the frame will be dropped.
MAC Address VLANs
If you have a lot of mobile users, creating a VLAN that bases its membership on a list of MAC addresses can be a good idea. Because these addresses are unique, when you plug into any switch port, a quick lookup is all that’s necessary for the switch to determine which VLAN your computer’s MAC address belongs to. And because MAC addresses are typically the way traditional switches work, there’s not much more circuitry or software that has to be tweaked to create this kind of VLAN-capable switch. The downside is that the administrator must manually assign each hardware address to the correct VLAN in the first place. However, that’s not a difficult chore when you are simply adding a few new computers to a VLAN. When implementing a set of VLANs that involve hundreds or thousands of computers, you can get tired fingers!
If you decide to use this type of switch, there is one thing you should check before purchasing the switch. What happens when a computer is connected to a port and the computer’s address is not a member of any of your configured VLANs? Some switch manufacturers will implement a mechanism that looks into the frame further and then forwards the frame based on a higher-level protocol address. This allows anyone to connect to your switch, provided that you’ve not taken the necessary physical security precautions and locked your switching equipment away in a secure computer room. Check to be sure that frames which have no VLAN mapping for a MAC address are dropped before using this type of switch.
Protocol Rule-Based VLANs
In a virtual LAN, a switch’s decision as to whether to output a frame on a particular port can be based on a set of association rules that are based on the network protocols used on the network. Each frame received on a switch port is examined and, based on a set of rules, is output on one or more other ports. The set of rules can be based on many things, such as the IP subnet addresses. However, it’s quite possible to create VLANs that subdivide even a subnet.
![]() For more information about IP subnets and how they can be used to segment the IP address space into smaller units, see Chapter 24, “Overview of the TCP/IP Protocol Suite.”
For more information about IP subnets and how they can be used to segment the IP address space into smaller units, see Chapter 24, “Overview of the TCP/IP Protocol Suite.”
Other protocol-based VLANs can be created so that AppleTalk- or NetWare-based (IPX/SPX) networks all can exist on the same set of switches—each on its own virtual LAN. In this kind of protocol-based VLAN switch, you usually can further subdivide each major protocol into smaller VLANs based on identifiers used in the protocol headers.
One factor to consider about protocol-based VLANs is that if the computer is running multiple protocol stacks (such as TCP/IP and IPX/SPX), the switch can be configured to allow the device to participate in separate VLANs based on these protocols. Because this kind of switch enables you to join diverse kinds of networks, it still is quite popular, and you’ll find that it is possible to buy this type of switch inexpensively. Decision trees that are used to map different protocols into separate VLANs have been implemented in hardware, which is faster than having to use software and a processor to examine frames, extract the protocol information, and then make the forwarding decisions.
For the standard IP-based network, using a switch that bases VLANs on IP subnets has another advantage. If you don’t choose to divide the subnet itself into further VLANs, the switch can, after you’ve associated an IP address with the LAN adapter card, extract the MAC address from the frame, and from then on use the hardware MAC address to make decisions. Thus, when you move a computer from one location to another on the switch (or a series of interconnected cooperating switches), you won’t have to change the IP address of the computer. The new port simply looks at the IP subnet address and creates an entry in its table for the MAC address, and it’s basically plug-and-play (or I guess that should be “plug-and-work”!).
Using Explicit Tagging on the Network Backbone
It should be obvious by now that most of the network adapter cards that exist in the world today were not created with explicit tagging in mind. Switches that use explicit tagging are used for the most part in large WANs, such as the Internet. However, LAN switches have evolved to the point that for most small LANs, a VLAN-unaware switch will serve just fine in a small network of a few hundred computers.
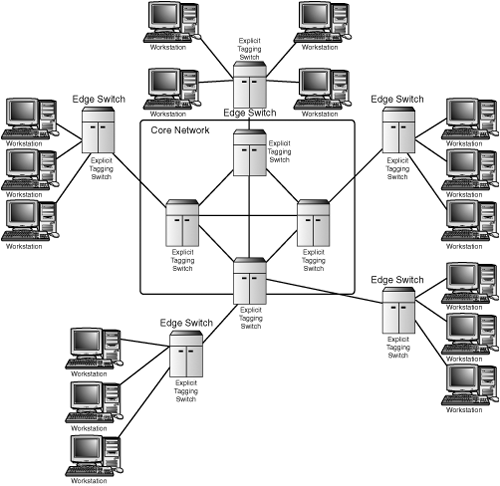
However, when you connect a large number of these VLAN-unaware LANs to the network backbone in a larger network, as in a college campus or a large business, the core switches that connect these LANs must handle a much larger amount of network traffic. Thus, it’s typical to use explicit tagging for large, high-capacity network switches than it is in smaller LAN environments (see Figure 9.3).
Figure 9.3. Explicit tagging can be employed in the network backbone to connect LANs that are not capable of using explicit tagging.
Here, the core switches that use explicit tagging are able to forward packets they receive within their switched network that understands the tags applied by the edge switches. The edge switches, however, add tags to frames they receive from the VLAN-unaware workstations, based on implicit tagging rules the administrator has set up. They remove the tags when they output frames to the individual workstations that are VLAN-unaware. Of course, these edge switches could just as easily have other switches attached to them, cascaded until you reach the end workstation or other network device. In this illustration, separate workstations are used to simplify the example. The edge switches could be connected to other switches that further subdivide the network and could use implicit tagging to forward the frames they receive from the edge switches.
![]() A technique known as Multi-Protocol Label Switching (MPLS) uses a similar tagging technique and is commonly used in the core routers (or I guess you can now call them switches) that form the heart of the Internet. You can read more about MPLS in Chapter 33, “Routing Protocols.”
A technique known as Multi-Protocol Label Switching (MPLS) uses a similar tagging technique and is commonly used in the core routers (or I guess you can now call them switches) that form the heart of the Internet. You can read more about MPLS in Chapter 33, “Routing Protocols.”
Within the core of switches that do understand tagging, switching is done at a fast pace. Although some people still debate the use of MPLS, it is now used as a major protocol in the Internet core switches, due to the lack of any other standard protocol that might be used to replace it.
IEEE Standards for Virtual LANs
There currently are two standards on which many VLANs are based. The first is called IEEE 802.1D, and the second is called IEEE 802.1Q. For the most part, the newer standard builds on and extends the IEEE 802.1D standard. The basic difference is that the IEEE802.1D standard defines switches that are VLAN-unaware, whereas the newer IEEE 802.1Q standard provides for VLAN-aware switches.
The actual details of these standards are beyond the scope of this book, much less this chapter. However, there are a few details that should be covered so that you’ll be more VLAN-aware when you make purchasing decisions:
![]() IEEE 802.1Q includes backward compatibility with switches that were based on the IEEE802.1D standard.
IEEE 802.1Q includes backward compatibility with switches that were based on the IEEE802.1D standard.
![]() The default behavior of a switch that is IEEE 802.1Q compliant—in the absence of any association rules—is to function as though VLANs were based on ports. This does not mean that IEEE 802.1Q provides for simply port-based VLANs. It just means that it is the default if the vendor doesn’t implement any other techniques for using a set of rules to create VLANs.
The default behavior of a switch that is IEEE 802.1Q compliant—in the absence of any association rules—is to function as though VLANs were based on ports. This does not mean that IEEE 802.1Q provides for simply port-based VLANs. It just means that it is the default if the vendor doesn’t implement any other techniques for using a set of rules to create VLANs.
![]() The IEEE 802.1Q standard talks about how association rules should be processed, but it does not require that any particular kind of rule be implemented on a switch. It’s more a guideline to be used if a vendor decides to use one or more rule-based mechanisms for creating VLANs.
The IEEE 802.1Q standard talks about how association rules should be processed, but it does not require that any particular kind of rule be implemented on a switch. It’s more a guideline to be used if a vendor decides to use one or more rule-based mechanisms for creating VLANs.
![]() The IEEE 802.1Q standard applies only to switches, not to the creation of network adapter cards that are VLAN-aware. That means if you do purchase adapter cards that support explicit tagging, you should be sure that it’s the same method used by your switch.
The IEEE 802.1Q standard applies only to switches, not to the creation of network adapter cards that are VLAN-aware. That means if you do purchase adapter cards that support explicit tagging, you should be sure that it’s the same method used by your switch.
The IEEE 802.1Q standard adds a filtering database that can be used to map devices to certain ports, and it describes algorithms that can be used with this filtering database to determine which VLAN a frame is a member of. The earlier standard provided for a filtering database, but the newer standard expands on its functionality. Perhaps more important to an administrator in a large network, the standard defines a MIB (management information database) that can be used to manage switches.
![]() For more information about SNMP, RMON, and the MIBs they use, see Chapter 49, “Network Testing and Analysis Tools.”
For more information about SNMP, RMON, and the MIBs they use, see Chapter 49, “Network Testing and Analysis Tools.”
For explicit tagging, the IEEE 802.1Q standard defines standard tag formats so that you don’t have to worry about different tagging schemes used by proprietary solutions implemented in earlier switches by different vendors.
This standard also defines a priority mechanism, which is not really necessary for VLAN operation but was added because some protocols, such as Ethernet, don’t have a mechanism for this. Although this is not specifically related to the concept of a VLAN, it was decided during the standards process to include a priority mechanism simply to avoid having to go back later and create another standard for prioritizing Ethernet frames. Strange, but true.
Another important concept is that the newer standard sets forth the methods used when a switch is used to connect dissimilar network types—such as Ethernet and Token-Ring (and FDDI, though that technology is slowly becoming a dinosaur in today’s market). This detail might not seem important, but there are many differences in the frame types used by these different network protocols (such as the big- or little-endian method of encoding bits—in other words, which bit that is transmitted for a byte is the most significant, and which is the least significant?). The newer standard defines the mechanisms for encapsulating dissimilar frames types within the frame type used on the network. For example, it tells which method to use for sending Token-Ring frames through an Ethernet network, and vice versa. Although it seems that Token-Ring has seen its better days, there are legacy systems out there that still use it. Using a switch that is IEEE 802.1Q compliant enables you to connect Token-Ring networks across a link that supports a faster technology, such as Gigabit Ethernet.
The final topic I’ll touch on is the fact that IEEE 802.1Q also sets forth a protocol (called GVRP) that can be used by switches to exchange information about VLAN membership. This is perhaps one of its more important concepts. This means that you won’t have to configure each switch in the network when VLAN membership is changed.
The IEEE standards cover a lot more territory than I can go into in this chapter. There are entire books on this subject, and if you are seriously considering implementing VLANs in a large network, you should pursue further reading, specifically purchasing the standards from the IEEE and using them to evaluate products to determine whether they meet the standards. However, for most networks today, as long as you use switches from the same manufacturer or from those who state that their products will interoperate with other vendors, you should not encounter many difficulties in setting up VLANs on your network.
What Kind of Switch Should You Buy?
Now that we’ve covered the basic idea of creating VLANs, let’s look at some of the ways this is done. There are standards, and then there are proprietary solutions. When upgrading a network, you should consider several questions when it comes to implementing VLANs in your network:
![]() Does the switch support VLANs? Small switches you buy at the local computer store for home or small office don’t. Medium to high-end switches used in a large network usually do.
Does the switch support VLANs? Small switches you buy at the local computer store for home or small office don’t. Medium to high-end switches used in a large network usually do.
![]() What is the port density of the switch? In a small computer room you might not have space for a large number of interconnected switches. Instead, switches with a larger number of ports can be a better choice.
What is the port density of the switch? In a small computer room you might not have space for a large number of interconnected switches. Instead, switches with a larger number of ports can be a better choice.
![]() If you are using a chassis switch, how many cards can you plug into the chassis? Can you start out with just a few cards for your current needs, and then add port cards as your network expands?
If you are using a chassis switch, how many cards can you plug into the chassis? Can you start out with just a few cards for your current needs, and then add port cards as your network expands?
![]() Do ports on the switch have LED indicator lights you can use to check for link connectivity and use, or do you have to rely on software to track down bad or misconfigured ports?
Do ports on the switch have LED indicator lights you can use to check for link connectivity and use, or do you have to rely on software to track down bad or misconfigured ports?
![]() Does the switch limit broadcast traffic to specific VLANs, or does it broadcast this traffic to all the virtual LANs on the switch? This might be desirable, or it might not, depending on your circumstances.
Does the switch limit broadcast traffic to specific VLANs, or does it broadcast this traffic to all the virtual LANs on the switch? This might be desirable, or it might not, depending on your circumstances.
![]() Does the switch support multiple network speeds (that is, 10/100Mbps or Gigabit Ethernet speeds for high-end servers)? Does the switch support high-speed connections to other switches and routers?
Does the switch support multiple network speeds (that is, 10/100Mbps or Gigabit Ethernet speeds for high-end servers)? Does the switch support high-speed connections to other switches and routers?
![]() Although TCP/IP has for all practical purposes overtaken other LAN protocols, such as AppleTalk and IPX/SPX, as the network protocol of choice, does the switch support multiple protocols? If you have a multiprotocol environment, will the switch support creation of VLANs to separate these distinct protocols into separate virtual LANs?
Although TCP/IP has for all practical purposes overtaken other LAN protocols, such as AppleTalk and IPX/SPX, as the network protocol of choice, does the switch support multiple protocols? If you have a multiprotocol environment, will the switch support creation of VLANs to separate these distinct protocols into separate virtual LANs?
![]() Is your equipment purchase going to be used for a short period (say, a year or two) or is it going to be used longer? If you’re in this for the long haul and won’t be able to replace expensive VLAN switches for a while, choose a vendor that’s known for providing an easy upgrade path (such as a firmware or software upgrade for the switch), or choose one that adheres to a known standard so that you can simply add switches as your capacity needs grow.
Is your equipment purchase going to be used for a short period (say, a year or two) or is it going to be used longer? If you’re in this for the long haul and won’t be able to replace expensive VLAN switches for a while, choose a vendor that’s known for providing an easy upgrade path (such as a firmware or software upgrade for the switch), or choose one that adheres to a known standard so that you can simply add switches as your capacity needs grow.
![]() What management software is available for the switch? If you want to move a user from one VLAN to another, do you have to physically unplug the user from one switch port and reconnect him to another port? Or, as is more often the case, can you simply use the switch management software to reconfigure that user’s port to become a member of another VLAN?
What management software is available for the switch? If you want to move a user from one VLAN to another, do you have to physically unplug the user from one switch port and reconnect him to another port? Or, as is more often the case, can you simply use the switch management software to reconfigure that user’s port to become a member of another VLAN?
Although not as important as the considerations in the preceding list, some VLAN-aware switches enable you to associate a port with more than one VLAN. For example, in Figure 9.2 we created three distinct VLANs. However, VLAN 1 has a server and a printer as well as workstations configured within its boundaries. In some situations, it might be desirable for a server to be able to participate in more than one VLAN. In that case, you want to be able to specify that the switch port to which the server is connected be part of more than one VLAN. This would not give other computers in the separate VLANs access to other VLANs, but instead it would work in reverse, allowing members of different VLANs to establish sessions with a server, or perhaps a printer or another networked device, that is a member of more than one VLAN.