CHAPTER 22. Bluetooth Wireless Technology
SOME OF THE MAIN TOPICS IN THIS CHAPTER ARE
The Bluetooth Special Interest Group (SIG) 333
General Overview of Bluetooth 333
What Are Bluetooth Profiles? 340
Bluetooth Is More Than a Wireless Communication Protocol 345
The preceding few chapters have covered the various versions of Wi-Fi (802.11a, IEEE 802.11b, and 802.11g), which are the three major contenders for the wireless networking market. Both of these technologies have trade organizations whose purpose is to advance their technology for the markets they target. The 802.11 wireless protocols aim for a market ranging from the home to the workplace to public spaces such as airports, malls, and just about anywhere you can use a cell phone today. The goal of the 802.11 protocols is to provide a worldwide standard that enables you to use a single wireless network adapter card in many different environments.
Bluetooth is another matter altogether. Bluetooth technology was originally designed to replace wires, and for only short distances. The original expectations for Bluetooth were that it would be used to connect such things as a keyboard, mouse, computer, and possibly mobile phone. It was not designed, from the start, to be a wireless networking solution that would span any great distance. Other technologies, such as Wi-Fi and 802.11a, were expected to cover that territory, giving mobile clients easy access to a network. In the home arena, this means that a single Internet connection can be shared by numerous wireless clients (computers, printers, gaming devices). In the work environment, Access Points can allow a mobile user to quickly connect to the corporate cabled network anywhere that a wireless Access Point has been placed. For the business and residential user, it’s possible that one or the other of these standards will allow you to open your laptop in a coffee shop, an airport, or some other public space and instantly connect to an Internet provider.
Note
The name Bluetooth comes from the legacy of an ancient king named Harald Blátand (940–985 A.D.). The legend has it that he was able to unite the countries of Norway and Denmark. Yet, the word Blátand can be translated to “Blue tooth.” Some say that this name was given to him because he didn’t have much time to visit a dentist, and he had blue teeth due to his fondness for blueberries. The adoption of this name is probably, however, based on the fact that he was able to unite the two countries. The Bluetooth technology does the same thing—it enables different devices to work together, bringing together a wide range of manufacturers.
Bluetooth has been in development for several years and despite numerous delays and, for a while, slow uptake into consumer markets, it does now have a decent head of steam going in terms of adoption. When the second edition of this book was written, it was expected to be the hottest new technology of the year. That didn’t quite happen. Over the next few years the specifications were further defined, and short-distance networking became part of Bluetooth. Other profiles (which are discussed later in this chapter) were added so that Bluetooth became a practical solution for short-distance networking for many types of consumer and computer devices today. One might say that Bluetooth has finally arrived.
There are two good reasons to consider using Bluetooth to create a small wireless network although 802.11b and 802.11a are now readily available. First, as was the original intent, Bluetooth enables devices, ranging from keyboards and mice to headsets for cellular telephones to make short-distance wireless connections to base PCs and other devices. You can also use this technology for networking computers (such as laptops) over short distances. This is the same capability that 802.11b (Wi-Fi) gives you.
Second, Bluetooth radio chips are inexpensive to manufacture, so you can expect to see them in many other devices in the next few years. And this includes not just computers and communications between computers and computer peripherals, but also many other consumer devices. At this time wireless networking based on the 802.11 specifications are pretty much limited to computers. You can’t plug a PCI or CardBus network adapter into your cell phone yet. But you can do this with Bluetooth.
The Bluetooth wireless technology is
![]() A short-range, lower-power wireless technology
A short-range, lower-power wireless technology
![]() A means to replace cables, such as those that connect your keyboard, mouse, printer, and other standard computer peripherals
A means to replace cables, such as those that connect your keyboard, mouse, printer, and other standard computer peripherals
![]() A protocol that uses a very inexpensive radio transmitter compared to other wireless protocols
A protocol that uses a very inexpensive radio transmitter compared to other wireless protocols
![]() A method to allow data communications between diverse devices such as computers, mobile phones, network appliances, handheld devices, digital cameras, and other consumer devices
A method to allow data communications between diverse devices such as computers, mobile phones, network appliances, handheld devices, digital cameras, and other consumer devices
This chapter takes a quick look at Bluetooth because even though it might have failed to reach the over-hyped expectations of a few years ago, it has filled a needed and useful role in networking devices over short distances.
The Bluetooth Special Interest Group (SIG)
Bluetooth technology was originally developed by the Swedish company Ericsson, which now licenses the Bluetooth trademark to the special interest group (SIG) of manufacturers that want to market products based on this technology. You used to be able to visit the Web site at www.bluetooth.com to find more information about the group and the vendors that are members. However, recently the SIG has incorporated, and you need to sign up as a member to view the contents of the site, such as the standards documents.
The IEEE has also licensed Bluetooth technology from the Bluetooth SIG and given it the name of IEEE 802.15.1 to establish a standard. You can view an abstract (in PDF format) of the version of the IEEE standards document using the URL http://standards.ieee.org/getieee802/new.html. You can also purchase the proposed standards documents for just under $200!
Bluetooth-enabled devices, which are based on a set of standards called profiles, should make it easy to interconnect and exchange voice and data between almost any kind of electronic devices you can think of.
General Overview of Bluetooth
The original Bluetooth version 1 specifications have been updated several times. The current version of the Bluetooth specification is version 2.0, which adds support for enhanced data rate (EDR) transmissions at up to 3Mbps, compared to 721Kbps maximum with Bluetooth version 1.2. Version 2.0’s EDR achieves higher speed by using phase shift keying (PSK) modulation instead of the Gaussian frequency shift keying (GFSK) method previously used.
Bluetooth technology uses lower-power transmissions and therefore is limited in the distance it can cover—up to about 10 meters. A more powerful version of Bluetooth allows for higher-power transmissions that can range up to 100 meters. Instead of creating a new technology from scratch, some parts of the Bluetooth specification were borrowed from existing technologies. Some of the more important ones include the following:
![]() Frequency-hopping spread spectrum (FHSS)—Bluetooth hops at 1,600 hops per second, using 79 frequencies each separated by 1MHz, over the total spectrum allowed in the 2.4GHz range. Both asynchronous communication (at 721Kbps) and synchronous communication (at 432.6Kbps) are supported to provide for both voice and data transmissions.
Frequency-hopping spread spectrum (FHSS)—Bluetooth hops at 1,600 hops per second, using 79 frequencies each separated by 1MHz, over the total spectrum allowed in the 2.4GHz range. Both asynchronous communication (at 721Kbps) and synchronous communication (at 432.6Kbps) are supported to provide for both voice and data transmissions.
![]() Motorola’s Piano—This technology allows the formation of small ad hoc networks, sometimes referred to as personal area networks (PANs). Although ad hoc networks are also used by other wireless technologies, Bluetooth forms ad hoc networks within just a small area, usually up to 10 meters.
Motorola’s Piano—This technology allows the formation of small ad hoc networks, sometimes referred to as personal area networks (PANs). Although ad hoc networks are also used by other wireless technologies, Bluetooth forms ad hoc networks within just a small area, usually up to 10 meters.
![]() Digital Enhanced Cordless Telecommunications (DECT)—This specification was adopted for the voice and telephony applications that Bluetooth can provide.
Digital Enhanced Cordless Telecommunications (DECT)—This specification was adopted for the voice and telephony applications that Bluetooth can provide.
![]() Object Exchange Protocol (OBEX)—This technology was borrowed from the IrDA (Infrared Data Association). It allows for data exchanges such as synchronizing address books between a Bluetooth-enabled PDA and a PC, for example, or for exchanging electronic business cards.
Object Exchange Protocol (OBEX)—This technology was borrowed from the IrDA (Infrared Data Association). It allows for data exchanges such as synchronizing address books between a Bluetooth-enabled PDA and a PC, for example, or for exchanging electronic business cards.
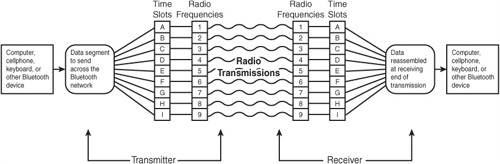
Bluetooth uses a frequency-hopping technique in which each transmission lasts for only 625μ. This means that data is sent over one radio frequency for just this short time. After that, the radio frequency changes and another small amount of data is transmitted. Because of this small allocation of time for each transmission, a transmission of just a simple message is sent over the air by dividing it into many smaller bits of information, and sending these small discrete units over a preset pattern of ever-changing radio frequencies (see Figure 22.1).
Figure 22.1. Data is sent in smaller units, each of which uses a different radio frequency.
In Figure 22.1 you can see that a Bluetooth device delivers data that needs to be sent to the radio transmitter. The radio transmitter breaks the message into many smaller units of information. Each of these units (A, B, C, and so on) is sent using a small window of time, each using a different radio frequency (1, 2, 3, and so on). At the receiving end of the transmission, each unit of data sent on different frequencies is combined back into the original data and passed on to the receiving device.
This is, however, a simplistic illustration. In a typical situation, more than one device is transmitting or receiving at the same time. Thus, the time slots (A, B, C) may not be contiguous, but are shared by all devices. So in reality a transmitter might send data using one time slot, and then wait for a few time slots before sending the next unit of data. Each unit of data, however, is sent using a different radio frequency, hence the term frequency hopping.
At the receiving end of the transmission, each small unit of data is received on a separate radio frequency, and each unit of data for each time slot is reassembled into the full message of data that was transmitted before it is passed to the receiving device. Because both the transmitting end and the receiving end of the communications know in advance what time slots will be allocated, and what frequencies will be used, it is a simple matter to keep track of multiple devices transmitting/receiving at the same time. This is because each device will be allocated different time slots, and thus different frequencies, for each data transmission.
A simple Bluetooth network consists of a single master and up to seven slaves. Transmissions take place based on a frequency-hopping scheme decided on by the master, and all members of a piconet (discussed in further detail in the next section) use the same frequency-hopping pattern. Thus, it’s possible to have multiple piconets within close proximity of each other because each piconet uses a different hopping pattern among the 79 available frequencies. When a device joins a piconet, the address of the master device is sent to the slave in a special packet called a frequency-hop synchronization packet (FHS packet). The hopping pattern is calculated based on the address of the master node. The master device’s clock is used to determine which particular point in the hopping sequence is the current one, and all slaves keep track of the difference between their own clocks and the master’s so that they can all hop along together.
Communications can take place in both directions, between master and slave, with each time slot numbered. The range of time slot numbers is from 0 to 227–1. The master device can start transmissions in even-numbered time slots, whereas slaves can start transmissions in odd-numbered slots. To provide for larger data transfers, up to five consecutive slots can be used. However, for these five slot transmissions, the data is transmitted on the same frequency, determined by the frequency to which the hopping pattern is set when the first packet is transmitted.
Piconets and Scatternets
The ad hoc nature of Bluetooth networking minimizes the need for management or administrative functions for networks made up of Bluetooth-enabled devices. In Chapter 18, “Introduction to Wireless Networking,” you learned that an ad hoc network consists of multiple wireless devices that communicate with each other, without a central controlling device. This is basically the method used by Bluetooth. Contrast this with using an Access Point with 802.11 wireless networks. 802.11 wireless networks can be used to create an ad hoc network, but usually a controlling Access Point is used to coordinate communications between members of the wireless network. To put it quite simply, an ad hoc network consists of multiple wireless devices that communicate with each other. In the case of Bluetooth, as described next, there is no dedicated Access Point to control data transmissions. Instead, the first Bluetooth device that initiates a transmission becomes a temporary “master” of the small network, and other devices are “slaves” that receive permission to transmit/receive from this master. The master is not a dedicated device like an Access Point.
In PANs, devices in close proximity can discover each other and form a small network (called a piconet) without user intervention. This enables users to transfer data between a cellular phone and a laptop computer, for example, by coming within range and instructing the cellular phone or computer what action to perform.
Piconets
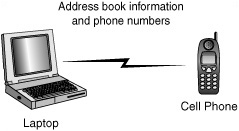
A piconet is formed when two or more devices discover each other and begin to communicate. A piconet can have up to eight devices, with one device acting as a master and the rest acting as slaves. The first device to initiate transmission becomes the master, although the specification provides for a master and slave unit to exchange roles. A specific frequency-hopping sequence is used by all devices within each piconet. Figure 22.2 shows the simplest example of a piconet: A cell phone is downloading address-book and telephone-number information to the user’s laptop.
Figure 22.2. A piconet consists of at least two Bluetooth-enabled devices.
In this example, the laptop acts as a master. The application software running on the laptop contacts the cell phone when it is within range, and requests that it synchronize its database with the one stored on the laptop.
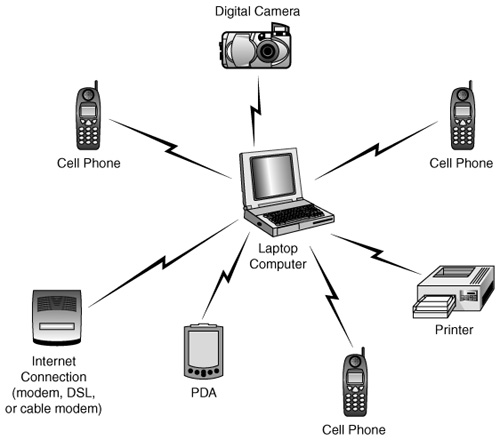
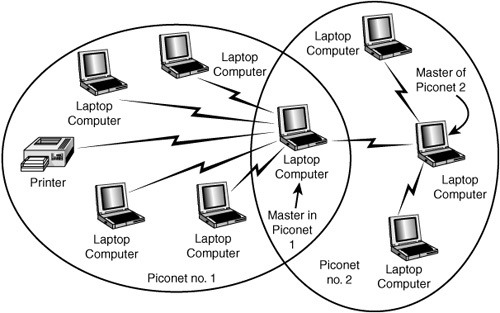
As stated earlier, a single piconet can have up to eight devices. The reason for this limit is simple: The address is only 3 bits long. This means that in binary, only the values of 0–7 can be stored in the address field. The master has no address, but 0 is reserved for broadcast messages; so the only addresses remaining for use by slaves are 1–7. However, a device can participate in two different piconets (called a scatternet), which is covered in the next section. Figure 22.3 shows an example of a larger piconet, in which one master controls multiple slaves in a piconet.
Figure 22.3. A piconet can have only one master and up to seven slave devices.
You can see that it’s possible to link various devices in a piconet. You can download digital images from your digital camera to the laptop, use more than one Bluetooth-enabled cell phone to place voice calls, and even connect a personal digital assistant (PDA) to the laptop to exchange information. Another interesting thing to note in this figure is that you also can use a single connection to the Internet without having to have a direct cable connection to the modem or broadband connection.
The master device in Figure 22.3 is the laptop computer. It controls the other devices, which are called slaves.
Scatternets
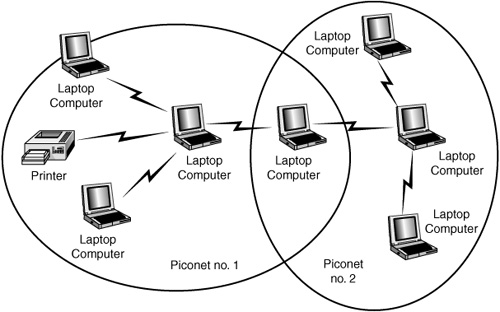
A device can be a master of only one piconet. The device can, at the same time, also be a slave in another piconet that is within range. A slave can also participate in two different piconets that are within its range. However, because the master device determines the hopping pattern used for a piconet, a device cannot be a master of more than one piconet. An example of a simple scatternet is shown in Figure 22.4.
Figure 22.4. A scatternet is formed when a device is a member of more than one piconet.
In this example, a laptop computer communicates with devices in both piconets. Note that the laptop is a slave in both piconets. It is possible, however, for the laptop to be a master in one piconet and a slave in another, as shown in Figure 22.5.
Figure 22.5. This Bluetooth-enabled laptop computer is a master in one piconet and a slave in another.
When a device is a member of two piconets, it keeps track of both frequency-hopping patterns and occasionally listens in on the correct frequency on each of the two piconets so that it can stay in touch with both piconets. A master device transmits a packet to its slaves occasionally to maintain the link, based on negotiations between the master and its slave devices. Thus, a device that is a member of two piconets must listen for these transmissions (or make them if it’s the master in one piconet) within the timeframe negotiated for each of the piconets of which it is a member.
Bluetooth Device Modes
Although you can incorporate Bluetooth radios in ordinary PCs, they were originally designed to be used for low-power devices. Because of this, it isn’t necessary for the Bluetooth device to be in an active state—consuming power—all the time. Before a piconet is formed, a device is in standby mode, in which a device will listen for messages every 1.28 seconds. To initiate a connection with another device, an inquiry message is sent, which is used to find other Bluetooth devices within the transmission range. If the address of the device to which a connection is desired is already known, a page message is used instead to begin the communication session.
In addition to being involved in active communications (the active mode), a device can be put into three other modes:
![]() Hold—A master unit can put a slave unit into hold mode, or the slave unit can request that it be placed into this mode. This is a power-saving mode in which the unit no longer actively exchanges data with other devices.
Hold—A master unit can put a slave unit into hold mode, or the slave unit can request that it be placed into this mode. This is a power-saving mode in which the unit no longer actively exchanges data with other devices.
![]() Sniff—In this mode, the device does not actively participate in communications with other devices. Instead, the device “wakes up” and listens for messages frequently. How often this occurs depends on the particular application for which the device is used, and the frequency is programmed into the device by the manufacturer. A master device can request that a slave device be put into sniff mode, but cannot force it to.
Sniff—In this mode, the device does not actively participate in communications with other devices. Instead, the device “wakes up” and listens for messages frequently. How often this occurs depends on the particular application for which the device is used, and the frequency is programmed into the device by the manufacturer. A master device can request that a slave device be put into sniff mode, but cannot force it to.
![]() Park—In this low-power mode, the device is still considered to be part of a piconet, but no longer has an Active Mode Address (AM_ADDR) associated with it. The device listens for broadcast messages and resynchronizes its clock with the master, but does not actively communicate. Before a device enters Park mode, the master will assign a Park Mode Address (PM_ADDR) to the device, easing the process of re-establishing active communications in the future.
Park—In this low-power mode, the device is still considered to be part of a piconet, but no longer has an Active Mode Address (AM_ADDR) associated with it. The device listens for broadcast messages and resynchronizes its clock with the master, but does not actively communicate. Before a device enters Park mode, the master will assign a Park Mode Address (PM_ADDR) to the device, easing the process of re-establishing active communications in the future.
These different modes are mainly designed to allow for different levels of low-power consumption for a Bluetooth-enabled device.
SCO and ACL Links
Two kinds of links can be established between master/slave devices in the network: the synchronous connection-oriented (SCO) link and the asynchronous connectionless (ACL) link.
SCO Links
The SCO link is established between the master and a particular slave in the network. Reserved time slots are set aside for these links, and up to three SCO links can be used for communication between the master and one or more slaves. SCO links are suitable for voice communications because the reserved slot nature of the link makes it easy to provide a steady stream of data instead of a variable rate that could cause a voice signal to degrade.
SCO links are considered switched-circuit links and must be set up before they can be used. The frequency of the dedicated time slots and other setup information is first established before an SCO link can be used.
ACL Links
ACL links are packet-switched connections between the master and one or more slaves, and can use any time slots that are not currently being used for SCO links. However, only one ACL link can exist at any one time between the master in the network and a particular slave.
Bluetooth Packets
Most Bluetooth packets use a standard format that consist of three basic fields:
![]() Access Code—This is a fixed-length field of either 68 or 72 bits.
Access Code—This is a fixed-length field of either 68 or 72 bits.
![]() Header—This is a fixed-length field of 54 bits.
Header—This is a fixed-length field of 54 bits.
![]() Payload—The payload field can range from 0 to 2,745 bits in length and contains the actual data portion of the packet.
Payload—The payload field can range from 0 to 2,745 bits in length and contains the actual data portion of the packet.
The Access Code field is used for synchronization purposes and to identify a particular channel in a piconet. If the Access Code field is followed by a header field, the Access Code is 72 bits in length; otherwise, it’s 68 bits long. Three kinds of Access Codes are used:
![]() Channel Access Code (CAC)—The CAC is used to identify a particular piconet. That is, all devices in the same piconet use the same value in the Access Code field.
Channel Access Code (CAC)—The CAC is used to identify a particular piconet. That is, all devices in the same piconet use the same value in the Access Code field.
![]() Device Access Code (DAC)—The DAC is used during certain signaling procedures, such as paging and responses to pages.
Device Access Code (DAC)—The DAC is used during certain signaling procedures, such as paging and responses to pages.
![]() Inquiry Access Code (IAC)—The IAC consists of two other kinds of access codes: the General Inquiry Access Code (GIAC) and the Dedicated Inquiry Access Code (DIAC). GIAC is used to discover other Bluetooth devices that are within range, whereas the DIAC is used by Bluetooth devices that share some common characteristic.
Inquiry Access Code (IAC)—The IAC consists of two other kinds of access codes: the General Inquiry Access Code (GIAC) and the Dedicated Inquiry Access Code (DIAC). GIAC is used to discover other Bluetooth devices that are within range, whereas the DIAC is used by Bluetooth devices that share some common characteristic.
The Packet Header field consists of several components:
![]() AM_ADDR—This is the active member address, and it is only 3 bits in length. This is why only 7 slaves can be in a single piconet, because 3 bits can be used to express an address range from 0 to 7 in binary notation. The address of 0 is used to broadcast packets to all slaves in a piconet. The slave’s 3-bit address is used in packets that travel to and from the master/slave. The master doesn’t need an address, because Bluetooth uses a point-to-point messaging service and there is only one master in the piconet.
AM_ADDR—This is the active member address, and it is only 3 bits in length. This is why only 7 slaves can be in a single piconet, because 3 bits can be used to express an address range from 0 to 7 in binary notation. The address of 0 is used to broadcast packets to all slaves in a piconet. The slave’s 3-bit address is used in packets that travel to and from the master/slave. The master doesn’t need an address, because Bluetooth uses a point-to-point messaging service and there is only one master in the piconet.
![]() PM_ADDR—This is used to put a device into park mode, making it easier to re-establish active communications in the future when the device needs to transmit or receive data.
PM_ADDR—This is used to put a device into park mode, making it easier to re-establish active communications in the future when the device needs to transmit or receive data.
![]() Type—This is a 4-bit field, so up to 16 packet types can be specified for either an ACL or an SCO link.
Type—This is a 4-bit field, so up to 16 packet types can be specified for either an ACL or an SCO link.
![]() Flow—This is a single-bit field used for flow control purposes on an ACL link. A value of 0 indicates that data transmissions should be stopped. When the receiving end of the communication has sufficient buffer space to begin receiving ACL packets, it sets this bit to a value of 1.
Flow—This is a single-bit field used for flow control purposes on an ACL link. A value of 0 indicates that data transmissions should be stopped. When the receiving end of the communication has sufficient buffer space to begin receiving ACL packets, it sets this bit to a value of 1.
![]() ARQN—This acknowledgment indication is a 1-bit field used to acknowledge (value = 0) that a packet was received successfully (that it passed the CRC check), or that it was not (value = 1).
ARQN—This acknowledgment indication is a 1-bit field used to acknowledge (value = 0) that a packet was received successfully (that it passed the CRC check), or that it was not (value = 1).
![]() SEQN—This 1-bit field is used to determine that packets are received in the correct order (sequence number), and alternates between 0 and 1.
SEQN—This 1-bit field is used to determine that packets are received in the correct order (sequence number), and alternates between 0 and 1.
![]() HEC—The Header Error Check field consists of an 8-bit word calculated based on a polynomial. This error checking covers only the header information.
HEC—The Header Error Check field consists of an 8-bit word calculated based on a polynomial. This error checking covers only the header information.
The address field is important because it limits the number of devices that can participate actively in a piconet at any given time. The master can reuse any address when a slave goes into park mode so that a large number of devices can be used in a piconet. However, only seven can be assigned active addresses and are allowed to communicate at any point in time.
The Type field has different values depending on whether the packet is an SCO or an ACL packet. It is beyond the scope of this chapter to define all the packet types, and indeed some are still undefined in the specification and reserved for future use. However, five packet types are commonly used:
![]() ID packet—This type of packet is used for paging, inquiry, and responses to paging and inquiries, and the packet contains the DAC or IAC value.
ID packet—This type of packet is used for paging, inquiry, and responses to paging and inquiries, and the packet contains the DAC or IAC value.
![]() Null packet—This packet type is made up of only the HAC and the CAC, and no payload. It is generally used to return the status of a previous transmission (the ARQN field), and the Null packet does not have to be acknowledged.
Null packet—This packet type is made up of only the HAC and the CAC, and no payload. It is generally used to return the status of a previous transmission (the ARQN field), and the Null packet does not have to be acknowledged.
![]() Poll packet—The master can use this packet to poll slaves in the network. This packet is similar to the Null packet in that it has no payload, but slaves are required to respond to this packet even if they have no data to send at the time.
Poll packet—The master can use this packet to poll slaves in the network. This packet is similar to the Null packet in that it has no payload, but slaves are required to respond to this packet even if they have no data to send at the time.
![]() FHS packet—This is the packet type discussed earlier that a slave device uses to obtain the frequency-hopping sequence of the piconet, along with other information about the piconet. This packet also contains the address the slave will use if it is joining the piconet.
FHS packet—This is the packet type discussed earlier that a slave device uses to obtain the frequency-hopping sequence of the piconet, along with other information about the piconet. This packet also contains the address the slave will use if it is joining the piconet.
![]() DM1 packet—This type of packet is used for control messages for both the SCO and the ACL link types.
DM1 packet—This type of packet is used for control messages for both the SCO and the ACL link types.
Various packet types are defined in the Bluetooth 1.1 specification for ACL and SCO links. Refer to the documentation available at the SIG Web site for further information. The details of these packets and the ways they are used depend on the kind of Bluetooth device being considered. One of the ways Bluetooth differs from other wireless technologies—such as Wi-Fi (IEEE 802.11b)—is that in addition to defining the mechanisms to grant access to the media (air waves) and provide transport (packet types), Bluetooth also defines profiles, which describe basic functionality for many devices that are expected to adopt this technology.
What Are Bluetooth Profiles?
Profiles are an important concept in Bluetooth technology. A profile is a set of specifications for how end-user functionality should be implemented. The International Organization for Standardization (OSI) developed the idea of profiles many years ago, which makes sense because OSI is, after all, in the business of standardizing technology worldwide. Many profiles exist for Bluetooth because it has a large number of possible uses. A profile defines minimal parameters for particular Bluetooth product types, but also allows vendors to enhance their products so that they can differentiate it in the marketplace. Also, if a Bluetooth device implements a feature that is described by a profile, it must do so in the way the profile dictates. Because of this, the capability of Bluetooth devices that implement the same function(s) can be achieved across different vendor platforms. This doesn’t mean that all features described by a profile need to be implemented by all vendors—just that they must be implemented in the same way if a particular feature is used.
Profiles aren’t entirely separate entities. Instead, a layered approach is taken. The Generic Access Profile gives a basic starting point for designing Bluetooth devices. It is composed of the Service Discovery Application Profile and three other basic profiles used by other profiles:
![]() The Serial Port Profile Group—This group of profiles uses the RFCOMM for serial port emulation.
The Serial Port Profile Group—This group of profiles uses the RFCOMM for serial port emulation.
![]() The Generic Object Exchange Profile Group—The OBEX protocol is used by all profiles in this group.
The Generic Object Exchange Profile Group—The OBEX protocol is used by all profiles in this group.
![]() The Telephony Control Protocol Specification Group—The name of this profile should make its use obvious—for profiles for telephone (and intercom) devices.
The Telephony Control Protocol Specification Group—The name of this profile should make its use obvious—for profiles for telephone (and intercom) devices.
The Generic Access Profile is examined first, and then the other profiles defined in the current standard are discussed briefly.
The Generic Access Profile
All Bluetooth devices must implement the Generic Access Profile. This profile can be considered a base on which the other profiles are built because it specifies functionality common to all Bluetooth devices. To summarize, this profile provides for the methods that devices use to discover other Bluetooth devices, specifies link-management techniques for establishing connections, and also provides some common formats for the user interface. This profile also defines the methods used to initially establish security mechanisms for the device, if desired and selected by the user.
The protocols used to establish and maintain links between Bluetooth devices—the Link Controller (LC) and the Link Manager Protocol (LMP)—are at the lower levels of the protocol stack. Also included are higher-level protocol elements, relating to services and security. The Logical Link Control and Adaptation Protocol (L2CAP) is above the LC portion of the protocol.
Finally, sitting above these protocols are several other protocols used by various profiles:
![]() Telephony Control Protocol (TCS)
Telephony Control Protocol (TCS)
![]() RFCOMM
RFCOMM
![]() Service Discovery Protocol (SDP)
Service Discovery Protocol (SDP)
Discovery, Security, and Bonding
The LC and LMP components of the protocol stack describe how Bluetooth-enabled devices are to behave when in standby mode (anything other than the active mode), and how they operate when trying to discover other Bluetooth devices and establish connections.
Bluetooth devices can operate in various modes, described in the Generic Access Profile. Bonding occurs when devices that allow connections establish a link. However, a device does not have to automatically respond to requests from another device. A Bluetooth device can be in a discoverable or nondiscoverable mode. If the device is set to nondiscoverable mode, it won’t respond to inquiries from other devices. The profile describes several types of discoverable and nondiscoverable modes, such as limited discoverable mode and general discovery mode. Basically, these terms define the length of time a device will respond or will not respond to inquiry messages from other devices.
During the discovery process, the initiator of the discovery obtains the address, clock, and class of the discovered device, as well as the name of the device.
The important thing to remember is that just because a Bluetooth device comes within range of another similarly enabled device, a connection does not automatically happen. This can be controlled by the user or the application. In addition to discoverability modes, this profile also defines bonding and pairing modes, which establish whether a connection can be made after a device is in a discoverable mode.
During the bonding procedure, the Bluetooth devices establish a link between each other and exchange a key that is stored in the device to identify the link for future data exchanges.
If a device is discoverable, and if it allows a link to be established, security mechanisms come into play. This profile defines several levels of security:
![]() Security Mode 1 (nonsecure)—This mode means that the device will not initiate any security mechanisms, such as authentication.
Security Mode 1 (nonsecure)—This mode means that the device will not initiate any security mechanisms, such as authentication.
![]() Security Mode 2 (service level enforced security)—In this security mode, the device will not initiate any security mechanisms until after a channel-establishment procedure or request has been initiated. The service for which the device is used determines whether security mechanisms (authentication, authorization, or encryption) are used.
Security Mode 2 (service level enforced security)—In this security mode, the device will not initiate any security mechanisms until after a channel-establishment procedure or request has been initiated. The service for which the device is used determines whether security mechanisms (authentication, authorization, or encryption) are used.
![]() Security Mode 3 (link level enforced security)—This mode requires the device to initiate security mechanisms before the LMP link setup procedure has completed.
Security Mode 3 (link level enforced security)—This mode requires the device to initiate security mechanisms before the LMP link setup procedure has completed.
Creating Connections
After devices have discovered each other and established a link, they create a channel through which applications can create a connection. Additionally, multiple applications can establish more than one connection using the same channel, or a separate channel that is created between the two. A channel is a specific radio frequency hopping sequence. As you learned earlier in this chapter, a device can be a member of one or two piconets, and thus can establish a channel on each. Applications can establish connections using the channels created between devices to exchange data.
The Service Discovery Application Profile
This profile describes the methods used by an application to discover the services of another Bluetooth device, and to obtain information about those services. This profile uses the SDP to find out what services another device offers. SDP can search for services based on the service class or service attributes. SDP also supports browsing for services to determine what is available.
The SDP process generally consists of the exchange of a series of messages defined by SDP in a connectionless mode. That is, SDP is a connectionless datagram service. Instead, SDP makes use of the Logical Link Control and Adaptation Protocol portion of the protocol stack for any link establishment, as well as for tearing down the connections that might be used during an exchange of SDP Protocol Data Units (PDUs).
The Cordless Telephony Profile and the Intercom Profile
This profile is used for Bluetooth devices that implement cordless telephony services to communicate with a base station, which is connected to a telephone network, as well as for voice connections between two Bluetooth telephone devices. Two roles are defined in this profile: gateway and terminal. A gateway role implies that the device acts as a base station to connect to an external telephone network. In most cases, this is a unit connected to the public switched telephone network (PSTN). However, support also is provided for other telephony connections, such as ISDN (Integrated Services Digital Network) and satellite connections that offer telephone services.
A terminal role describes the unit that communicates with a gateway device, or perhaps another terminal (acting more like an intercom). Because Bluetooth devices can communicate directly with each other in this role, you can eliminate cellular phone charges if you are using a Bluetooth-enabled cordless phone that is within range of another. This intercom capability is also described by the Intercom Profile, which must be supported by the Bluetooth device for this functionality to be implemented.
The L2CAP layer of the protocol stack is used to establish a connection between a terminal and a gateway when they come within range of each other. When a terminal unit is within range of a gateway device, the terminal unit is normally put into park mode, discussed earlier in this chapter. When a call needs to be sent or received, the terminal is put into active mode. The L2CAP connection does not need to be re-established each time a call is made.
This profile also describes how services such as call setup, termination, and caller ID are performed.
The Serial Port Profile
This profile defines the use of Bluetooth devices that emulate serial port communications—such as RS232 cable connections. Most PCs have several kinds of ports you can use to connect external devices, ranging from serial ports to USB (universal serial bus) ports and FireWire ports. This profile deals with the decades-old serial port type of connection. This type of port was commonly used for such things as connecting to a modem or another device to establish a communications session. For example, you can use a serial cable to create a quick connection between two PCs and exchange files using products such as LapLink or other similar programs.
The Headset Profile
The Headset Profile describes how headsets are to be implemented using Bluetooth. A headset can be used for telephone audio use, for listening to music, and in various other similar cases. Headsets can even be used with voice-recognition software to provide input/output capabilities for a PC.
Similar to the Cordless Telephony Profile, the Headset Profile defines a gateway and a Headset device. The gateway can be a cordless telephone, a PC, or another similar device that is equipped with Bluetooth for audio communications. The Headset is the actual headset device that the user wears to provide the earphone and microphone hardware.
The profile provides for the initiation of a session by the gateway (as in the case of an incoming telephone call) or by the end user (by pressing a button on the device, for example). The connection can be terminated by either side of the connection. Provisions are also made for controlling the volume of the transmitted or received audio signal.
The Dial-Up Networking Profile
Bluetooth devices can act as an “Internet bridge” to allow you to use a cellular phone (or another device that can connect to an ISP) so that you can use a laptop or another device to communicate on the Internet. This profile also allows a computer to use a cellular phone to accept incoming digital calls. Like the Headset Profile and the Cordless Telephony Profile, this profile defines a gateway device, which is the cellular phone or possibly a modem with a cabled connection to the Internet. A Data Terminal (DT) is the device that makes use of the gateway to connect to the Internet. This profile provides for speeds up to 128Kbps, but higher speeds are optional.
The profile specifies a subset of the AT modem command set that is employed for this type of service; only one call can be established between the gateway device and a DT. That is, the DT cannot be used to establish more than one call with a gateway device at any point in time. Just as you’d need more than one telephone line if you had two modems in your computer, the DT is capable of placing only a single call through a gateway.
Other Bluetooth Profiles
In addition to the profiles discussed in this chapter, Bluetooth 1.x and 2.0 specifications provide for several others. More profiles are expected to be added if the technology is accepted by the marketplace as a solution for short-distance cable replacement. Many of the following profiles are still in draft format and are not yet considered to be standards that all Bluetooth vendors will adopt. When you purchase a Bluetooth device that supports the following profiles, be sure to check the description of the device to determine whether it supports an established standard, or whether it is based on a draft standard. For example, devices supporting 802.11g wireless networking (see Chapter 21, “The IEEE 802.11g Standard”) were originally released based on the draft of this protocol, assuming that there would be very few changes from the drafts to the adopted standards.
Tip
Some of the following drafts may become standards in a short time. Thus, the reader is again cautioned to check the description of any device that claims to support the profiles described in this section. And you can expect that additional profiles will be added as Bluetooth devices continue to make inroads into the consumer marketplace.
For those who want to find out what may be in store for Bluetooth devices, the draft profiles include the following:
![]() Fax Profile—This profile allows for wireless fax services.
Fax Profile—This profile allows for wireless fax services.
![]() LAN Access Profile—This profile provides for a connection to a LAN. This is similar to the functions that Wi-Fi provides using Access Points. The Point-to-Point protocol (PPP) is used. This profile also can be used to create a LAN consisting of only Bluetooth devices.
LAN Access Profile—This profile provides for a connection to a LAN. This is similar to the functions that Wi-Fi provides using Access Points. The Point-to-Point protocol (PPP) is used. This profile also can be used to create a LAN consisting of only Bluetooth devices.
![]() Generic Object Exchange Profile (GOEP)—This profile borrows from the OBEX protocol and allows for the exchange of data between devices—between a cordless telephone, a PDA, and a PC. It is used by the other profiles in this list.
Generic Object Exchange Profile (GOEP)—This profile borrows from the OBEX protocol and allows for the exchange of data between devices—between a cordless telephone, a PDA, and a PC. It is used by the other profiles in this list.
![]() Object Push Profile—This profile uses GOEP for the exchange of simple objects, such as electronic business cards or appointment data. This profile can be used to “pull” objects, as well as to push them to another device.
Object Push Profile—This profile uses GOEP for the exchange of simple objects, such as electronic business cards or appointment data. This profile can be used to “pull” objects, as well as to push them to another device.
![]() File Transfer Profile—This profile uses GOEP to browse a file system on a remote device, as well as transfer files between devices, delete files, or create new folders (directories).
File Transfer Profile—This profile uses GOEP to browse a file system on a remote device, as well as transfer files between devices, delete files, or create new folders (directories).
![]() The Synchronization Profile—This profile uses GOEP to provide a service for synchronizing data in various kinds of databases, for example, calendars, address books, and Personal Information Managers (PIMs).
The Synchronization Profile—This profile uses GOEP to provide a service for synchronizing data in various kinds of databases, for example, calendars, address books, and Personal Information Managers (PIMs).
![]() The Audio/Video Remote Control Profile (AVCP)—This profile describes features used for Bluetooth devices that support audio and/or video exchanges. The command set used for this type of exchange is defined by this profile. Streaming audio or video is not defined in this profile, however.
The Audio/Video Remote Control Profile (AVCP)—This profile describes features used for Bluetooth devices that support audio and/or video exchanges. The command set used for this type of exchange is defined by this profile. Streaming audio or video is not defined in this profile, however.
![]() The Generic Audio/Video Distribution Profile (GAVDP)—Based on AVCP (and other previous profiles, such as the Generic Access Protocol), this profile describes the techniques necessary to support streaming audio and video between Bluetooth devices.
The Generic Audio/Video Distribution Profile (GAVDP)—Based on AVCP (and other previous profiles, such as the Generic Access Protocol), this profile describes the techniques necessary to support streaming audio and video between Bluetooth devices.
![]() The Advanced Audio/Video Remote Control Profile (AVRCP)—This profile is designed to enhance AVCP and GAVDP by providing for remote control functionality, for example, the features usually found on an audio or video remote control, such as volume settings, pause, play, and so on.
The Advanced Audio/Video Remote Control Profile (AVRCP)—This profile is designed to enhance AVCP and GAVDP by providing for remote control functionality, for example, the features usually found on an audio or video remote control, such as volume settings, pause, play, and so on.
![]() The Basic Imaging Profile (BIP)—Standard network protocols such as FTP can be used to transfer graphic imaging files, as well as other types of files. With FTP, however, there is no guarantee that a receiving device can correctly display the images it receives. This profile provides the mechanisms needed to provide interoperability between devices, by requiring that Bluetooth devices be able to transmit/receive imaging files in JPEG thumbnail formats, regardless of the imaging format stored on the sender. This profile also enables the device to download the characteristics of other imaging file formats, and transfer them to printers, as well as offering the capability of controlling an imaging device, such as a digital camera.
The Basic Imaging Profile (BIP)—Standard network protocols such as FTP can be used to transfer graphic imaging files, as well as other types of files. With FTP, however, there is no guarantee that a receiving device can correctly display the images it receives. This profile provides the mechanisms needed to provide interoperability between devices, by requiring that Bluetooth devices be able to transmit/receive imaging files in JPEG thumbnail formats, regardless of the imaging format stored on the sender. This profile also enables the device to download the characteristics of other imaging file formats, and transfer them to printers, as well as offering the capability of controlling an imaging device, such as a digital camera.
![]() Basic Printing Profile (BPP)—The Generic Object Exchange Profile and Generic Access Profile are combined with the specifications of this profile to provide simple printing capabilities for Bluetooth. This profile addresses printing simple files, such as emails, and some formatted documents, such as calendars.
Basic Printing Profile (BPP)—The Generic Object Exchange Profile and Generic Access Profile are combined with the specifications of this profile to provide simple printing capabilities for Bluetooth. This profile addresses printing simple files, such as emails, and some formatted documents, such as calendars.
![]() The Bluetooth Extended Service Discovery Profile (ESDP)—This profile describes how Bluetooth devices can make use of Bluetooth’s Service Discovery Protocol (SDP) to discover devices that use the Universal Plug and Play (UPnP) service.
The Bluetooth Extended Service Discovery Profile (ESDP)—This profile describes how Bluetooth devices can make use of Bluetooth’s Service Discovery Protocol (SDP) to discover devices that use the Universal Plug and Play (UPnP) service.
![]() The Hands-Free Profile (HFP)—A minimum set of functions necessary for a mobile phone that uses hands-free devices is described by this profile. The Bluetooth device will be able to provide voice communications as well as remote control for the hands-free device.
The Hands-Free Profile (HFP)—A minimum set of functions necessary for a mobile phone that uses hands-free devices is described by this profile. The Bluetooth device will be able to provide voice communications as well as remote control for the hands-free device.
Bluetooth Is More Than a Wireless Communication Protocol
As you can see, Bluetooth is not just a protocol used to exchange data between devices. The use of profiles further delineates the different kinds of applications that can be used with Bluetooth radio transmitters and thus makes it easier for manufacturers to produce portable devices that have applications built in and ready for use. You can contrast this with Wi-Fi, which simply provides the communications link just as traditional LAN or WAN protocols provide. Bluetooth provides both the radio frequency transport mechanisms and application-specific solutions that make interoperability between devices easy to implement.