CHAPTER 23. Security and Other Wireless Technologies
SOME OF THE MAIN TOPICS IN THIS CHAPTER ARE
Instant Messaging and Consumer Devices 348
Personal Area Networks (PANs) 356
Although previous chapters on wireless technology were devoted to examining wireless devices that are currently available, this chapter examines additional types of wireless uses and wireless security. Essentially, this chapter wraps up the topic of wireless networking and communications.
Instant Messaging and Consumer Devices
If you ask a typical consumer about wireless communications, you might hear about Wi-Fi or wireless Ethernet, but it’s just as likely that cell phones, smartphones, or PDAs with onboard wireless networking would also be part of the conversation. These devices offer web browsing, email, video and still image capture, and text messaging, and they can share information with PCs.
These are some of the more popular PDA and smartphone vendors:
![]() BlackBerry (
BlackBerry (www.blackberry.net)—The BlackBerry series of devices use Java applications and are produced by a company called Research In Motion (RIM). Some BlackBerry devices include features such as digital walkie-talkie and GPS.
![]() For more information about BlackBerry, see “BlackBerry PDAs,” p. 349.
For more information about BlackBerry, see “BlackBerry PDAs,” p. 349.
![]() Palm (
Palm (www.palm.com)—Palm uses an operating system developed in-house for the PDAs and smartphones it manufactures. The OS has also been adopted by many other manufacturers, such as Garmin, Kyocera, Lenovo, LG, PiTech, and Symbol. A unique port for the Palm operating system is a wristwatch-size device available from Fossil Tech (www.fossil.com).
![]() Windows Mobile (
Windows Mobile (www.microsoft.com)—Developed by Microsoft, Windows Mobile is the family name for various mobile devices that run Windows, including Pocket PCs, Pocket PC Phone Edition, smartphones, and Portable Media Center. You can purchase Windows Mobile-based devices from many vendors, including HP, Toshiba, Dell, Audiovox, Motorola, Orange, Samsung, Siemens, Asus, and others. Windows Mobile operating systems command the largest number of manufacturers at this time.
Comparing Mobile Information Devices
Given the wide variety of wireless mobile devices on the market and the different operating systems available for them, it can be confusing to determine the exact boundaries between types of wireless mobile devices.
Generally, PDAs have the following features:
![]() Email
Email
![]() Calendar
Calendar
![]() Contact list
Contact list
![]() Photo display
Photo display
![]() Web browsing
Web browsing
![]() Instant messaging
Instant messaging
![]() Digital music storage and playback
Digital music storage and playback
![]() Support for various productivity and entertainment software
Support for various productivity and entertainment software
![]() Data synchronization via a wired cradle, Bluetooth, or Wi-Fi (varies with model)
Data synchronization via a wired cradle, Bluetooth, or Wi-Fi (varies with model)
PDAs with integrated telephones typically add these features:
![]() Voice communications
Voice communications
![]() Digital camera (note that some PDAs without an integrated telephone might also include digital photography capabilities)
Digital camera (note that some PDAs without an integrated telephone might also include digital photography capabilities)
Note
Some PDAs and PDAs with integrated telephones include a built-in mini-keyboard or a portable external keyboard.
A smartphone differs from a PDA with integrated phone in that it lacks the capability to use productivity applications other than email and web browsing and doesn’t have a keyboard, but it can usually play games. A smartphone includes the capability to synchronize via a cradle, but usually does not support Wi-Fi wireless connections. Many smartphones support Bluetooth, enabling you to use a wireless headset for hands-free and wire-free communications.
A portable media center is optimized for digital music, digital video, and still picture playback. It usually includes the capability to act as a personal video recorder (PVR). However, it lacks the capability to work with other types of information, and is not designed to connect wirelessly with other devices.
With the feature sets available on PDAs with integrated phones and smartphones, the market for classic PDAs which lack telephone and integrated wireless data support is bleak. Sony discontinued its CLIE series of PDAs in the summer of 2004, and PalmOS has lost significant ground to Windows Mobile-based and BlackBerry devices. The future of PDAs is a wireless one.
BlackBerry PDAs
RIM’s BlackBerry product line is the most popular PDA product family in the world. Their unique combination of smartphone, wireless PDA with keyboard, wireless web surfing, and wireless text messaging makes them extremely popular with corporate and government users. BlackBerry devices are so powerful that users have a hard time putting them away, inspiring the nickname CrackBerry. BlackBerry Connect technology for wireless email is also available in the Nokia 6820, 6822, and 9300 smartphones.
Part of the power of BlackBerry comes from its level of email integration. Not only do BlackBerry devices work with existing personal and business email accounts, but BlackBerry also provides management and control for BlackBerry devices through its Enterprise Server product line for Microsoft Exchange, IBM Lotus Domino, and Novell Group Wise.
The BlackBerry Alliance Program provides access to a wide variety of third-party business applications for BlackBerry, including many vertical market solutions. The Handago Store for BlackBerry (www.handango.com/blackberry) provides access to individual productivity, communications, entertainment, and education applications.
To learn more about BlackBerry, including comparisons of the BlackBerry devices, see the BlackBerry website at www.blackberry.com. BlackBerry devices are available from most major wireless communications vendors, including Sprint and Nextel (www.sprint.com), Verizon Wireless (www.verizonwireless.com), and Cingular Wireless (www.cingular.com), among others.
Wireless Security
When 802.11b wireless networks were first introduced, proponents maintained that their products were secure because the Wired Equivalent Privacy (WEP) security mechanism included in the IEEE 802.11b specification would keep intruders from intercepting and decoding wireless communications. In addition to preventing eavesdropping on your wireless network, WEP was supposed to keep intruders from joining your wireless network. Unfortunately, the original version of WEP used a shared 40-bit encryption key, making it very easy for knowledgeable hackers to break. It is important to point out that the Wireless Ethernet Compatibility Alliance (WECA), now called the Wi-Fi Alliance, has stated that WEP was never meant to be a single solution for securing a wireless network. Instead, other technologies, such as VPNs (see Chapter 46, “Virtual Private Networks [VPNs] and Tunneling”), as well as other mechanisms (such as secure authentication) typically found on a wired network, were meant to fill this gap.
WEP
Because the first version of WEP used a simple 40-bit encryption key using the RC4 encryption algorithm, and the same key is used on both the Access Point (AP) and the wireless client, it is a simple matter to break this security. Although most current wireless network hardware supports longer 64-bit and 128-bit WEP encryption codes (and some hardware offers 256-bit encryption if all of your hardware is from the same vendor and supports this level of encryption), WEP is still very easy to crack. You can use several utilities on the Internet to determine whether WEP is protecting your network adequately.
Caution
One of the most important reasons you need to take extra steps to secure a wireless network as compared to a wired one is that in a wired network you can physically secure the computers, the network cabling, and even a connection to a WAN (such as the Internet) by using a firewall. Wireless networks, on the other hand, do not offer a physical barrier. Instead, the distance that your wireless network can cover usually includes a range that is accessible outside your building(s). And because the signal cannot easily be controlled using the same physical methods you use for a wired network, interception of transmissions, much less intrusions into your network, becomes a simple matter when relying solely on WEP. WEP was part of the original 802.11 specification, developed in 1997. Much time has passed since then—enough time to break the encryption using simple techniques available today.
You can visit the following websites to gain access to software that can be used by both you and hackers to determine whether your network is secure:
![]() WEPCrack—This open-source tool is available to everyone, so you might as well use it yourself to determine whether your network is secure. For more information, see
WEPCrack—This open-source tool is available to everyone, so you might as well use it yourself to determine whether your network is secure. For more information, see http://wepcrack.sourceforge.net.
![]() AirSnort—This tool simply listens, and saves, 5 to 10 million packets from a wireless network (and that is really not a large number of packets if you have more than just a few clients). When the program determines that enough packets have been intercepted, it can take a second or two to decrypt the shared encryption key. Originally, AirSnort ran only on Linux platforms, but the vendor has now provided instructions for creating a Windows 2000/XP-compatible version. For more information, see
AirSnort—This tool simply listens, and saves, 5 to 10 million packets from a wireless network (and that is really not a large number of packets if you have more than just a few clients). When the program determines that enough packets have been intercepted, it can take a second or two to decrypt the shared encryption key. Originally, AirSnort ran only on Linux platforms, but the vendor has now provided instructions for creating a Windows 2000/XP-compatible version. For more information, see http://airsnort.shmoo.com.
At this time it is not illegal to use devices to listen to wireless network transmissions, and it’s certainly debatable as to whether it should be. Yet, because these tools are available to everyone, you should probably use them to see whether your network is as secure as you think it is. This is not meant to encourage hackers to use these tools; the tools previously listed are meant for you to use them so at least both sides can have access to the same intrusion applications.
This goes along with the benefits touted by the open-source community. Although the source code and applications are available to everyone (a glass house, so to speak), they enable hackers to search for vulnerabilities, and they also enable users to create solutions to prevent these attacks. This is an argument that is often used to compare proprietary operating systems and applications and open-source ones. I guess it all depends on your perspective. If you want to use proprietary applications, you have to depend on your vendor to fix security problems. If you use open-source applications, there are many programmers worldwide who can develop a solution.
Whom do you trust? This is a difficult decision to make. But, at the very least, you should have access to the same programs that hackers use to determine whether your network is vulnerable, whether or not you use other open-source applications. And if you search the Internet, you will find many other programs used by hackers in addition to those listed previously. A good search, on a regular basis, is recommended by this author.
Eventually WEP was implemented with a stronger 128-bit key, but even that could be easily detected and broken. Although the strongest WEP encryption available is now 256-bit, it can still be compromised by hacking tools such as those mentioned earlier in this section, and is supported only by some wireless Ethernet vendors, including Cisco, Proxim, D-Link and US Robotics. However, other consumer-grade vendors such as Linksys, NETGEAR, Belkin, and other familiar faces at electronics superstores are limited to 128-bit WEP encryption. If you cannot upgrade to wireless devices that support WPA or WPA2 encryption, there are several steps you should take to protect a WEP-based wireless network.
You should separate a wireless network from the wired network using a firewall (see Chapter 45, “Firewalls”). At least this assists in keeping intruders from accessing the entire corporate network, though the wireless portion is still vulnerable. And you should incorporate techniques such as VPNs, as suggested by the Wi-Fi Alliance, to further enhance security on the wireless portions of the network.
Many consumers who purchase inexpensive devices for home networks might think that the SSID (service set identifier) that you enter when installing the network card and Access Point provide security for the wireless network, but this is not the case. Instead, the SSID is simply used to separate wireless networks. The SSID is easily discovered, especially if you do not choose to use additional security mechanisms. The SSID is not a security mechanism! It is simply a method used to associate wireless devices with an AP. If you don’t broadcast the SSID, it’s harder for a casual snooper to borrow your bandwidth, but it doesn’t stop a determined hacker from finding your network. Without using some form of encryption, the SSID is easily discovered by broadcast messages from the AP. When discovered by an eavesdropper, all that is necessary for the intruder is to reset his wireless adapter to use the same SSID, and then join your network. It is useful to change the SSID from the manufacturer’s default to make it more difficult for hackers to determine what brand of wireless Access Point you use, but this step alone is not adequate security.
A good website to visit if you are interested in the latest developments in wireless security is www.netstumbler.com. Here you’ll find various articles about wireless security, as well as downloads that can help you enhance your current wireless device and check out security lapses.
Tip
If your network includes 802.11b or very early pre-802.11g–compatible hardware that cannot be upgraded to the final 802.11g standard, the strongest encryption possible for your network might be 128-bit WEP encryption. If your SOHO network contains very sensitive information, consider other techniques as mentioned in the main text of this chapter. If you use a broadband connection only to access the Internet, all you really need to worry about is having neighbors intrude on your wireless network and use your broadband connection. This type of invasion has received much attention in the press lately. Yet, because it is typical that a home user does not store sensitive information on a computer (unless using a credit card online), and because most users do not continuously use the entire bandwidth provided by broadband services, you probably won’t notice much difference in performance. However, if you work from home or access your home computer remotely, you should use the most secure settings possible to protect your SOHO network. Keep in mind that Windows XP, unlike Windows 9x, does not permit you to use different passwords on different shared folders. To protect yourself, use only the default Shared folder if you need to have a shared folder at all, and keep sensitive information out of it.
Fortunately, WEP is no longer the only security option you have on a wireless network, especially if your network is based on 802.11g or its many proprietary enhancements.
Tip
There is one situation in which you might want to ensure that your wireless network is secure in a home network. Because the distances of the current technologies can range from about 100 to 300 meters, it’s quite possible for someone in the house next door to use your wireless Access Point and tap into your broadband Internet connection. If you don’t want to have neighbors sharing your bandwidth, you must use whatever security measures your particular technology provides. This should also be a factor when choosing hardware devices.
Wired Protected Access (WPA), WPA2, and 802.11i
In response to the vulnerability and criticism of WEP, the Wi-Fi Alliance created the Wi-Fi Protected Access (WPA) standard in 2003. WPA was designed to be an interim security solution until the completion of the IEEE 802.11i security standard, and its features are a blend of features originally developed for WEP and those being developed for 802.11i.
Like WEP, WPA uses RC4 encryption for its keys, but unlike WEP, WPA modifies the original key for greater security and supports an optional authentication server. WPA is the minimum recommended security standard for network hardware that supports it, such as 802.11g hardware that supports the full 802.11g standard, and most recent 802.11a hardware. Although some vendors of 802.11b hardware have provided upgrades to support WPA, most 802.11b hardware is not compatible with WPA security.
Caution
If your wireless network has a mixture of WEP-compatible and WEP/WPA-compatible hardware, you must use the weaker WEP security standard for all devices. Because WEP-only devices are primarily limited to the 11Mbps 802.11b standard, upgrading to 802.11g hardware, which supports WPA, WPA2 and WEP, improves network security as well as speed.
One of the main complaints about WEP, besides its limited-length keys, is the fact that the same key is used by both sides of the transmission, and the key does not change during a session. These factors make it easy to examine network traffic on a wireless network and eventually crack the encryption key.
WPA solves two problems associated with the earlier WEP security mechanisms. First, it uses encrypted techniques for authentication that should assist in preventing unauthorized clients from becoming part of the wireless network. Second, it uses a constantly changing key instead of the single shared key used for encryption by WEP. By changing in the encryption key at frequent intervals, WPA can be much more difficult to crack. The constant changing of encryption keys is known as the Temporal Key Integrity Protocol (TKIP). This key-changing method makes it very difficult for intruders to decipher keys used by your wireless network, especially when compared to the static keys known by both sides of the communications link used by the simple WEP standards.
WPA also includes an integrity check that is basically a check sum based on the network packet that can detect whether a packet is originating from a valid network user or an intruder who is attempting to crack the key used by your network. Thus, if an unauthorized user uses the standard techniques to attempt to determine a fixed key, you can detect these intrusion attempts and then deal with them.
Overcoming Potential Vulnerabilities in WPA
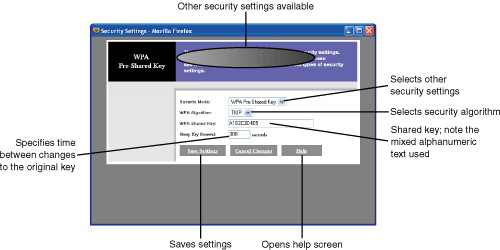
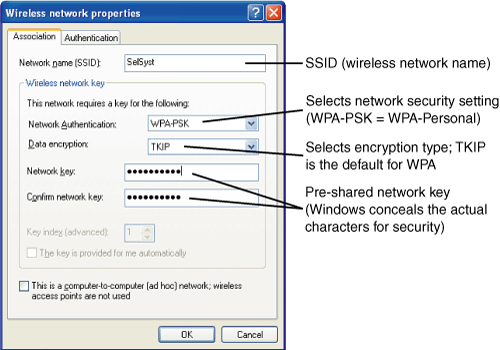
The version of WPA used in SOHO and small-business networks that lack an authentication server is known as WPA-Personal. The encryption key is known as a Pre-Shared Key (PSK); the PSK must be provided by a network client before it can log into a WPA-based wireless network. The original PSK is encrypted using the TKIP process, which changes the key repeatedly during a connection to help keep the connection secure. WPA-Personal is also known as WPA-PSK (see Figure 23.2, later in this section).
Although WPA is a stronger encryption standard than WEP, several potential weaknesses exist in the way users can configure WPA. These include
![]() Encryption keys that are too short—The longer the encryption key, the more secure the network is. Network experts recommend an encryption key of at least 20 characters. The Wireless Network Setup Wizard that Microsoft includes in Windows XP Service Pack 2 creates a 63-character WPA key.
Encryption keys that are too short—The longer the encryption key, the more secure the network is. Network experts recommend an encryption key of at least 20 characters. The Wireless Network Setup Wizard that Microsoft includes in Windows XP Service Pack 2 creates a 63-character WPA key.
![]() Plain-text encryption keys—A key such as
Plain-text encryption keys—A key such as The quick brown fox jumps over the is certainly longer than the 20-character minimum recommended, but because it is comprised of recognizable words, it is relatively easy to crack. Instead, use mixed, random alphanumeric keys. For example, a key such as 2F1ACB67EF90O F77A would be much harder to crack because there are no recognizable words or alphanumeric patterns in it.
To see for yourself the threat that short, plain-text encryption keys pose to your WPA-based wireless network, you can download the WPA Cracker utility from tinyPEAP (www.tinypeap.com). The network packets WPA Cracker needs for analysis can be gathered with the Ethereal open-source network protocol analyzer available from www.ethereal.com. As suggested earlier in this chapter, you should use WPA Cracker and similar tools to analyze your current WPA-based network configuration for vulnerabilities.
For larger, corporate networks, a more powerful version of WPA known as WPA-Enterprise can be used. WPA-Enterprise (also known as WPA-RADIUS) differs from WPA-Personal in these ways:
![]() A RADIUS or AAA server is used to authenticate individual users.
A RADIUS or AAA server is used to authenticate individual users.
![]() Authentication uses the IEEE 802.1X standard developed in 2001.
Authentication uses the IEEE 802.1X standard developed in 2001.
![]() WPA supports the Extensible Authentication Protocol (EAP).
WPA supports the Extensible Authentication Protocol (EAP).
Regardless of the version of WPA you might select, your APs and network clients must be configured to use the same settings to make a connection possible, just as with the older WEP security standard.
Figure 23.1 shows a typical router being configured to use WPA encryption, and Figure 23.2 shows a matching configuration for a network client running Windows XP.
Figure 23.1. This router is configured to use WPA-Personal encryption.
Figure 23.2. Configuring a Windows XP client to use WPA-Personal encryption.
Moving to WPA2 (IEEE 802.11i)
Although WPA, particularly in its WPA-Enterprise version, is much more secure than WEP, it is not as secure as it could be. As mentioned previously in this chapter, WPA was designed as an interim solution until the ratification of the IEEE 802.11i standard could take place. IEEE 802.11i was ratified in 2004, and the first products became available in the fall of 2004. IEEE 802.11i-compatible products are known as WPA2-compatible. WPA2 differs from WPA in the use of a stronger encryption algorithm. Although WEP and WPA used RC4 encryption, WPA2 uses the stronger AES encryption algorithm.
To upgrade existing WPA-compatible wireless network hardware to use WPA2/802.11i security, you might need to perform one or more of the following operations:
![]() Download and install updated client device drivers—Some client adapters might not support WPA2 security because WPA2 security requires more intensive computation than WPA.
Download and install updated client device drivers—Some client adapters might not support WPA2 security because WPA2 security requires more intensive computation than WPA.
![]() Download and install updated router and AP firmware—Some wireless routes or APs might not support WPA2 security because WPA2 security requires more intensive computation than WPA.
Download and install updated router and AP firmware—Some wireless routes or APs might not support WPA2 security because WPA2 security requires more intensive computation than WPA.
Some vendors don’t explicitly state that their products support WPA2. Instead, they might list the security features the adapters support. Table 23.1 cross-references security features to WPA/WPA2 security standards supported.
Table 23.1. Wireless Security Features/Security Standards Cross-Reference

How Well Do You Know Your Users?
One of the main concerns of network administrators in the 1980s was that any person in the company network could easily install a modem in her computer and connect to computers outside the network. For digital telephone systems, this was not a problem. But for small businesses using an analog telephone system, this could present a major security headache.
The equivalent today is known as rogue Access Points, and these are difficult to detect with modern network analysis tools. Because APs are so inexpensive, what can you do to stop a user, or a department in your company, from installing an AP and enabling wireless access? In large corporate environments where it can be a complicated process, what is to stop a user from simply connecting an AP to her own network connection, and thus enabling a larger number of computers to connect to the network? Because APs generally use DHCP to assign addresses to clients, and use the single valid address on your network to exchange data for these clients, just how secure is your network?
This is yet another reason to use wireless detection programs on a regular basis, even if you do not authorize wireless networking, to determine whether some user has enabled this access on your wired network.
In Chapter 42, “Basic Security Measures Every Network Administrator Needs to Know,” the importance of establishing corporate security policies and procedures is discussed. If you ensure that each employee, contractor, and vendor signs off on these policies (which should include policies on wireless access), you at least have grounds to dismiss those who violate the procedures and possibly to pursue legal action. There’s not much you can do about rogue users, and this problem is more common than many administrators think. If a user is stymied by corporate procedures and paperwork, it is not a difficult thing to justify implementing a solution on his own. Again, because these types of security breaches can easily occur, especially in a large network, you should use wireless sniffing programs to determine whether users are bypassing your policies and procedures that are employed in your network.
Although you may indeed use wireless networking at certain junctions in your network, you should regularly test to see whether unauthorized wireless networks are being created by users. When you consider the low cost of an AP today, it is very feasible to install a wireless network anywhere in your large network. And many of the users who have been caught using this method say that the reason they did so is that it would take too long to get permission from the network administrator, or whatever body you use to authorize such connections.
I guess the best thing to say about this topic is “trust no one.”
Personal Area Networks (PANs)
A personal area network (PAN) is a short-range wireless network that can span from a few feet to a few hundred feet. This covers many short-range wireless standards, including Bluetooth, IEEE 802.11a/b/g hardware running in ad-hoc (direct connect; no AP) mode, and forthcoming standards. The IEEE 802.15 Working Group (www.ieee802.org/15) is the standards body overseeing development of current and future PAN (also known as Wireless PAN) standards.
Major IEEE PAN standards currently include
![]() IEEE 802.15.1-2002—This standard is based on Bluetooth version 1.1.
IEEE 802.15.1-2002—This standard is based on Bluetooth version 1.1.
![]() IEEE 802.15.3—This is a draft standard for high-rate (up to 55Mbps) wireless personal area networks running in ad-hoc (direct connect) mode.
IEEE 802.15.3—This is a draft standard for high-rate (up to 55Mbps) wireless personal area networks running in ad-hoc (direct connect) mode.
![]() IEEE 802.15.4-2003—This standard is designed to support simple, low-power, and low-data-rate (up to 250Kbps) devices such as sensors, interactive toys, smart badges, home automation (ZigBee; see
IEEE 802.15.4-2003—This standard is designed to support simple, low-power, and low-data-rate (up to 250Kbps) devices such as sensors, interactive toys, smart badges, home automation (ZigBee; see www.zigbee.org for details), and remote controls.
Whenever you connect two or more IEEE 802.11-based clients together in ad-hoc mode, or use a Bluetooth phone, keyboard, or printer, you are using a PAN. Keep in mind that a PAN is optimized for easy connections, not for security. Don’t use PAN-type wireless networking in environments in which security is a critical issue. Rather, today’s and tomorrow’s PAN implementations should be used where quick exchange of data via wireless frequencies is desirable. For more about Bluetooth, refer to Chapter 22, “Bluetooth Wireless Technology.”