Lemma 14.2.3. Let a be a word ordering on (X>, and let a be the restriction of a to (X>. Then also a is a word ordering.
Now we are ready to state and prove the main theorem of this section.
Theorem 14.2.4 (Computation of Elimination Ideals). LetL c X, let a be an elimination ordering for L, and let a be the restriction of a to (X>. Given a two-sided ideal I c K (X> and a a-Gröbner basis G of I, the set G = G n K(X> isaa-Gröbner basis of the elimination ideal 7 = I n K(X>.
Proof. It is clear that G is contained in 7 We have to show that the leading words of the polynomials in G generate the leading word ideal Lw5(/). For f ϵ 7 {0|,we have Lwa (f) = Lwa (f) ϵ (X). Since G is a a -Gröbner basis of I, we find words w1, w2 ϵ (X> and g ϵ G such that Lwa (f) = w1 Lwa (g)w2. As this word is contained in (X>, it follows that w1, w2, Lwa (g) ϵ (X>. From the hypothesis that a is an elimination ordering, we get that g ϵ K (X>, and therefore g ϵ G. This was to be shown.
A first application of this theorem is the following method for computing the intersection of two-sided ideals in K(X>.
Proposition 14.2.5. Letf1,…,fs,g1,…,gt ϵ K(X>,letI = (f1,…,fs> andJ = (g1,…, gt > be the two-sided ideals generated by these non-commutative polynomials, and lety be a further letter. Then we have
I J = (yf1,…,yfs,(1 − y)g1,…,(1 − y)gt,yx1 .x1y,…,yxn .xny.K(x)
In particular, a system of generators of the intersection ideal I n J can be enumerated using the Buchberger Procedure.
Proof. Given h ϵ I n J,we can write h = p1f1p’1 + … + psfsp’s and h = q1g1q’1 + … + qtgtq’t with p;,p., q;-, q| ϵ K(X>. Then we have
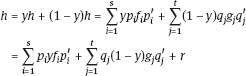
with a polynomial r ϵ (yx1 − x1y,…, yxn − xny>. Hence h is contained in the right-hand side of the claimed formula.
Conversely, let h be contained in this right-hand side. Then we have p;, p-, q;-, q’j ϵ K(X,y> such that h = £s=1 pyfp- + j qs(1-y)g;q| + rwith r ϵ Ox-x;y | i = 1,…, n>. Substituting y 1 in this representation shows h ϵ I, and substituting y 0 shows h ϵ J. □
It is clear that this proposition can be extended to intersections of finitely many twosided ideals in K (X> in a straightforward way. The main application of elimination is the possibility to compute kernels and images of K-algebra homomorphisms. For this purpose we use the following setting.
Let Y = {y1,…,ym| be a further set of letters, and let I c K(X> and J c K(Y > be two-sided ideals. We consider a homomorphism of K-algebras
0 : K(X>/I K(Y>/J
given by 0 (x;) = f with f ϵ K (Y> for i = 1,…, n.
Proposition 14.2.6 (Kernels of Algebra Homomorphisms). The kernel of0 satisfies
Ker(0) = (((X1 -f1, …,xn − fn> + J • K(X, Y>) n K(X>) + I.
In particular, it can be enumerated by applying the Buchberger Procedure to compute this elimination ideal.
Proof. Given g ϵ K(X> such that g ϵ Ker(0), we have g(f1,… ,fn) ϵ J. By replacing f by (fi − X;) + Xi in this equality and multiplying out, we obtain g = h + g(f1,… ,fn) ϵ (X1 − f1,…, xn − fn> + J where h ϵ (x1 − f1,…, xn − fn>. Hence g is contained in the right-hand side.
Conversely, let g ϵ K(X> be such that g is contained in the right-hand side. Then there exist p;, p • ϵ K(X, Y> such that g = pi X − fi)p[ + h with h ϵ J • K(X, Y>. Substituting Xj fj in this equality shows g(f1,… ,fn) ϵ J, and therefore g ϵ Ker(4>).
One application of this procedure is that we have a semi-decision procedure for checking whether an element f of a finitely generated algebra K(X>/I is algebraic or transcendental over K. Namely, we can apply the preceding proposition to the K-algebra homomorphism
0 : K[z] —> K(X>/I given by z f.
If the procedure finds a non-trivial element in Ker(0), we can also compute the minimal polynomial off, i.e., the monic polynomial which generates Ker(0).
Another application of the preceding proposition is a semi-decision procedure for checking if an element of a monoid or group has a finite order. This can be done as follows.
Remark 14.2.7. Let G = (x1,…,xn;r1 = … = rm = 1> be a finitely presented monoid having the cancellation property or a monoid presentation of a finitely presented group. Then the monoid ring over Z2 satisfies Z2[G] = Z2(X)/I where I = (r1 − 1,…, rm − 1) .Let w ϵ (X) be a word representing an element W of G.
To check whether the order of m is finite, we choose an additional letter y and form the ideal J = (y − w, r1 -1,…, rm -1) in Z2 (X, y). Then we let a be an elimination ordering for X and start the computation of a a -Gröbner basis G of J.
(1) If we have G nZ2|y] =0 at some point during the computation, the element W is algebraic over Z2. Since the ideal J is generated by binomials, its Gröbner basis consists of binomials. Thus the minimal polynomial of W is of the form Zk + ze with 1 < k <1. Since G has the cancellation property, it follows that Wl-k = 1. Notice that in this case we can compute the order of W.
(2) If the computation finishes with a Gröbner basis G with G nZ2 [y] = 0 then we have Ker(ty) = {0} and the element W has infinite order.
The next proposition provides a semi-decision procedure for checking if an element is in the image of an algebra homomorphism, and yields a preimage if the answer is positive.
Proposition 14.2.8 (Images of Algebra Homomorphisms). Letty : K(X)/I —> K(Y)/J be a K-algebra homomorphism With ty (x¡) = f¡ as above. LetD c K(X, Y) be the diagonal ideal
D = (X1 − f1,…,xn − fn) + J • K(X, Y),
let a be an elimination ordering for Y, and let Gbea a-Gröbner basis ofD.
(1) Forg ϵ K(Y), the element g is contained in the image ofty if and only if NRa G(g) ϵ K(X), i.e., if and only if this normal remainder does not involve any letter from Y.
(2) Given g ϵ K (Y) such thatg’ = NRa G(g) is contained in K (X), We have g = ty (g’).
Proof. First we let g ϵ K (Y) such that y’ = NRa G(g) ϵ K(X). Then there exist elements Pi,p’ ϵ K(X, Y) and q ϵ J • K(X, Y) such that g − g’(/!,… ,/J = £”1 p¡(x¡ − f )p’ + q. Substituting x¡ f in this equality yields g-g’ (f1,…,fn) ϵ J, and therefore g = ty (g’).
Conversely, let g ϵ K(Y) be such that g is contained in the image of ty. Then there exists a polynomial h ϵ K(X) such that g + J = h(f1,… ,fn) + J. Since we have h + D = h(f1,… ,fn) + D,wegetg − h ϵ D, and hence NRa G(g) = NRa>G(h). Now the facts that h ϵ K (X) and that a is an elimination ordering for X imply NRa G (g) ϵ K (X). □
Based on this proposition, the Buchberger Procedure yields a semi-decision procedure for the Subalgebra Membership Problem: given a finitely generated K-subalgebra S = K(f1,… ,fn) of a K-algebra K(Y)/J, decide whether a given residue class g is contained in S. In the YES case, i.e., if we have g ϵ S, this will be detected in finitely many steps and the procedure returns an explicit representation of g in terms of the generators {f1,… ,fn} of the subalgebra S. Otherwise, the procedure may or may not stop.
In group theory, the proposition allows us to semi-decide subgroup membership as follows.
Remark 14.2.9. Let G = (x1,…,xn;r1 = … = rm = 1> be a finitely presented group, and let H c G be the subgroup generated by the residue classes of some words h1,…,hk ϵ (X>. The subgroup membership problem (or the generalized word problem) asks us to decide whether a given word w ϵ (X> represents an element of H. The following instructions define a semi-decision procedure for this problem.
(1) Let {y1,…, yn} be further letters. Consider the presentation
Z2[G] = Z2(x1,…,x„,x’1,…,x’n>/(r; − 1, Xjyj − 1,yjXj − 1>;=1,…,m. ;=1,…,n
(2) Using the subalgebra membership test, check whether we have W − 1 ϵZ2 (h1 − 1,…, hk -1> inside Z2 (X, Y>/I,whereI is the defining ideal for Z2[G] given above.
To prove correctness of this method, we still have to check that W ϵ H is equivalent to W − 1 ϵZ2(h1 − 1,…,hk − 1>.Let W = h,- …h. We proceed by induction on s and find that
W − 1 = h · h; _1 − 1)h!s + (h!s − 1) ϵ2h − 1,…, hk − 1>.
For a proof of the reverse implication we refer to [MR], Theorem 9.
To use Gröbner bases for other hard problems underlying non-commutative cryptography (such as the problems explained in Section 9.8), we need to generalize Gröbner basis theory from two-sided ideals in K (X> to two-sided submodules of a free module over this ring. In particular, we need the concept and calculation of syzygies. These topics are introduced in the next section.
14.3 Gröbner Bases of K(X>-Modules
Let K be a field, let X = {x1,…,xn| be a set of letters, and let K(X> be the noncommutative polynomial ring over K in the indeterminates x1,…, xn. The enveloping algebra K(X>env = K(X> <% K(X> is a two-sided module over K(X> in the obvious way: for A, f2, g1, g2 ϵ K (X>, we letf ® g2)/2 = fg ® g2.
In the category of all two-sided K(X>-modules, the enveloping algebra K(X>env plays the role of a free module of rank 1: given any two-sided K(X>-module M and an element v ϵ M, there is a unique homomorphism of two-sided K(X>-modules 0: K(X>env —> M such that 0 (1 ® 1) = v. Consequently, for every r > 1, the two-sided K(X>-module Fr = ©r=1 K(X>env is a free module of rank r in this category. For i = 1,…, r,welet e; = (0,…, 0,1 ® 1,0,…, 0) where 1 ® 1 occurs in the i-th position.
In this section we extend the Gröbner basis theory for two-sided ideals in K (X> to a Gröbner basis theory for two-sided submodules of Fr. The main motivation for this is the following notion.
Definition 14.3.1. Let M be a two-sided K(X>-module, let v1,…, vr ϵ M, and let 0: Fr —> M be the uniquely determined homomorphism of two-sided K(X>-modules satisfying 0 (e,) = v, for i = 1,…, r. Then the two-sided K(X>-submodule
![]()
is called the (two-sided) syzygy module of (v1,…, vr).
The computation of syzygy modules is a fundamental technique in computational algebra and is used frequently in non-commutative cryptography. Let us start the development of Gröbner basis theory in this setting.
Definition 14.3.2. A term in Fr is an element of the form weiw’ where W, W’ ϵ (X> and 1 < i < r. The set of all terms in Fr is denoted by T(Fr).
A module term ordering on T(Fr) is a total ordering T such that t1 <T t2 implies w1t1w’1 <T w2t2w2 for all t1, t2 ϵ T(Fr) and all W1, w1, W2, w2 ϵ (X> and such that T is a well-ordering.
Starting from a word ordering on (X>, we can define module term orderings as follows.
Example 14.3.3. Let To be a word ordering on (X>.
(1) For terms W1e;W,1, W2ejW’2 ϵ T(Fr) such that W1, w1, W2, w2 ϵ (X> and i,j ϵ {1,…,r|,welet

This defines a module term ordering ToPos on T(Fr).
(2) For terms w1eiw’1,w2e-w’2 ϵ T(Fr) such that w1,w’vw2,w2 ϵ (X> and i,j ϵ {1,…,r|,welet

Again this defines a module term ordering PosTo on T(Fr).
Given a module term ordering, the following terminology generalizes the usual definitions of leading terms etc.
Definition 14.3.4. Let T be a module term ordering on T(Fr).
(1) Givenavector v ϵ Fr{0|, there exists a unique representation v = c1f1 + … + csts with c1,…,cs ϵ K {0| and t1,…,ts ϵ T(Fr) satisfying t1 >T … >T ts .The term LtT (v) = t1 is called the leading term of v with respect to T . The element LcT (v) = c1 is called its leading coefficient.
(2) For a two-sided submodule M c Fr, the two-sided submodule LtT(M) = (LtT (v) | v ϵ M {0|> of Fr is called the leading term module of M.
(3) A subset G of a two-sided submodule M of Fr is called a T-Gröbner basis of M if the leading term module LtT (M) is generated by the leading terms LtT (f) such that f ϵ G.
Based on these definitions, many standard results of Gröbner basis theory generalize in a straightforward way. Let us mention three of them. For detailed proofs we refer the reader to [BK], Section 2.
Proposition 14.3.5 (Macaulay’s Basis Theorem). LetM be a two-sided submodule of Fr. Then the residue classes of the elements in T(Fr) LtT (M) form a K-vector space basis ofFr /M.
Proposition 14.3.6 (The Division Algorithm). Let s > 1, and let m,f1,…, fs ϵ Fr {0|. Consider the following sequence of instructions.
(1) For i = 1,…, sletkj = 1, g;1 = g = 0,p = 0 and v = m.
(2) Find the smallest i ϵ {1,…,s| suchthat LtT (v) = w LtT (fj)w’ for some w, w’ ϵ (X>.
If such an i exists, increase s by 1, set gjk. = Lcifl w, g’ik = w’ and replace v by
v − wfjW1 . If now v = 0, continue with step 2. Otherwise, continue with step 4.
LCT (fi)
(3) Replace p by p + LcT (v) • LtT (v) and v by v − LcT (v) • LtT (v). If now v = 0, continue with step 2.
(4) Return the tuple ((gn,g11),…, (g,g),…, (gs1,g),…, (gsks,g’Sks)) and thevec- torp ϵ Fr.
This is an algorithm which returns elements ((g11,g11),…, (gsk , gsk )) and p such that the following conditions are satisfied.
(1) We have m = £s=1 £* = 1 gfgj + p.
(2) No element of Supp(p) is contained in (LtT (f1),…, LtT (fs)>.
(3) Ifgy = 0 = gj for some i ϵ {1,s| and j ϵ {1,k,-| then we have LtT (gf-gj) <T LtT (m).
(4) For all i ϵ {1,…, s| andj ϵ {1,…, k;| we have
gj-Ltr (fi)g’ijt (LtT (fi),…, LtT(fi-1)>-
(5) The elements ((g11, g11),…, (gsk , gsk )) andp are uniquely determined by the preceding conditions (1)-(4).
Definition 14.3.7. Let G = (g1, …,gs) be a tuple of elements gt ϵ Fr.
(1) A pair (i, j) with i, j ϵ {1,…, s| and i < j is called a critical pair of G if there exist words Wj, w-, Wj, w- ϵ (X> such that Wj LtT(gi)w’i = Wj LtT (g;)w|, such that Wj and Wj have no common prefix, and such that w- and wj have no common suffix.
(2) For every critical pair (i, j) of G, the element
![]()
is called the S-vector of gj andgj.
Proposition 14.3.8 (Buchberger’s Criterion). Let G = {g | i ϵ I| be a (countable) set of elements in Fr which generate a two-sided submodule M = (G> ofFr, and let B be the set of critical pairs between elements of G. Then the set G is a t-Gröbner basis ofM if and only if NRt G(S,j) = 0 for all (i, j) ϵ B.
Finally, we are ready to formulate the module analogue of Buchberger’s Procedure.
Theorem 14.3.9 (Buchberger’s Procedure for Modules). Let G = {g1,… ,gs| be a finite set of elements in Fr {0| which generates a two-sided K (X>-submodule M = (G> ofFr. Consider the following sequence of instructions.
(1) Let H = G, let B be the set of critical pairs ofH, and let s’ = s.
(2) If B = 0, return G and stop. Otherwise choose a pair (i, j) ϵ B using a fair strategy and delete it from B.
(3) Compute the S-vector Sj and its normal remainder NRt h(S,j). If the result is zero, continue with step 2.
(4) Increase s’ by one. Appendgs, = NRt h(S,j) to H, and append the elements of {(i, s ‘) | 1 < i < s ‘ and (i, s ‘) is a critical pair| to B. Continue with step 2.
This is a procedure which enumerates a tuple H ofvectors whichform a T − Gröbner basis ofM. IfM has a finite T- Gröbner basis, the procedure stops after finitely many steps and the vectors of the resulting tuple H form a finite T-Gröbner basis ofM.
A proof using the current notation and terminology is contained in [BK], Section 2. Moreover, it is shown there that Gröbner bases for two-sided submodules of Fr generalize Gröbner bases for two-sided ideals in K(X> in the following way: under the epimorphism n : F1 —> K(X> given by e1 1, two-sided submodules of F1 containing (x1e1 − e1x1,.. .,xne1 − e1xn> correspond uniquely to two-sided ideals in K(X>, and their Pos-o Gröbner bases correspond to o-Gröbner bases of their images in the obvious way.
It is clear that the Buchberger Procedure for Modules results in a semi-decision procedure for submodule membership. Since this in completely analogous to the ideal case, we leave it to the interested reader. Besides the analogues of the applications of Gröbner bases introduced in Section 4.2, we have one new application which is particular to modules and which is explained next.
In the following we let L be a subset of {1,…, r|, and we let Fr denote the free two-sided K(X>-module generated by {e; | i ϵ {1,…, r| L|.
Definition 14.3.10. A module term ordering t on T(Fr) is called a component elimination ordering for L if every element m ϵ Fr {0| such that LtT (m) ϵ Fr is contained in Fr.
Let M c Fr be a two-sided submodule. The two-sided submodule M n Fr of Fr is called the component elimination module of M with respect to L.
The following example shows that component elimination orderings exist.
Example 14.3.11. Let i ϵ {1,…, r|, and let L = {1,…, i|. If o isa term ordering on (X> then the module ordering T = Pos-o is a component elimination ordering for L. Namely, let m ϵ Fr {0| be such that LtT (M) = w1ejw,1 ϵ Fr. Then every term t = w2ekw’2 ϵ Supp(m) satisfies t <T LtT(m). This implies k > j, and we conclude that t ϵ Fr and m ϵ Fr.
The following proposition shows how one can compute component elimination modules. In fact, it yields a Gröbner basis with respect to the restriction to Fr of the given component elimination ordering.
Proposition 14.3.12 (Computing Component Elimination Modules). Let M be a twosided submodule ofFr, letLc {1,…, r|, and let T be a component elimination ordering for L. Furthermore, let G be a T-Gröbner basis o M, and let F be the restriction of T to T(Fr). Then the setG = G n Fr is a T-Gröbner basis ofM n Fr.
Proof. Let m ϵ (M n Fr) {0|. Then we have Ltf (m) = LtT(m) ϵ LtT(M) because F is the restriction of T . Since G is a T-Gröbner basis of M, there exists an element g ϵ G such that Ltf (m) = w LtT (g)w’ for some w, w’ ϵ (X>. But then we have LtT (g) ϵ Fr, and the assumption that T is a component elimination ordering for L yields g ϵ Fr, i.e., g ϵ G = G n Fr. Now the fact that LtT (g) = Ltf (g) concludes the proof. □
Module component elimination is the key ingredient for the computation of syzygies in a non-commutative setting. Recall that the two-sided syzygy module Syz(G) of a tuple G = (g1,…, gs)of elements of Fr was defined as the kernel of the homomorphism A : Fs —> Fr of two-sided K(X>-modules which is given by £, gj for i = 1,…, s. The computation of two-sided syzygy modules is based on the following proposition.
Proposition 14.3.13. LetFr+s be the free two-sided K(X>-module of rank r + s, and let {e1,…, er+s| be its canonical basis. Let G = (g1, …,gs) be a tuple of elements ofFr {0|, letFr+s = (er+1,…, er+s>, and for every m ϵ Fr let m denote the corresponding element in Fr+s under the canonical injection e, e,. Let U be the two-sided submodule ofFr+s generated by {g1 − er+1, …,gs − er+s|. Then we have
U n Fr+s = Syz(G).
In particular, we can enumerate the syzygy module Syz(G) using module component elimination.
Proof. Let us consider the homomorphism 0 : Fr+s —> Fs given by er+j £, for i = 1,…,s. By restricting 0 to U n Fr+s, we obtain an injective homomorphism p. Therefore it suffices to prove that the image of p is Syz(G). Let m = Zs=1 ZjeN wWy be an element of Syz(G) with c¡j ϵ K and w,j, wj ϵ (X> for i = 1,…, s. Notice that for every j ϵ N, all but finitely many of the elements c,j are zero. Then the element m = ZSi=1 ZjN cijwijer+iw’ij = ZSi=1 ZjN cywygiwy-Zs=1 ZjN cijwij(g-er+i)w’ijis contained in U n Fr+s, and it satisfies p (m) = m.
Now suppose that U n Fr+s contains m = Zs=1 ZjeN c,jW,jer+jwj. Then we have A (P(m)) = Zs=1 Z’gN cijwijgMj = Zs=1 Zj6N - er+i)wij + Zs=1 Zj6N cijwijer+Mj ϵ U. Moreover, none of the generators er+1,…,er+s appears in the representation of A (p(m)). Since U is generated by the elements {g1 − er+1,…,gs − er+s|, this implies A (p(m)) = 0. Hence we get p (m) ϵ Syz(G).
Using this result, it is easy to formulate a procedure for the computation of a two-sided syzygy module.
Corollary 14.3.14 (Computing Two-Sided Syzygy Modules). Letg1,…,gs c Fr {0|, and let G = (g1,… ,gs). Let p : Fr+s —> Fs be the homomorphism defined by er+j £, for i = 1,…, s, and for every m ϵ Fr let m denote the corresponding element in Fr+s. Consider the following sequence of instructions.
(1) Choose a component elimination ordering T for L = {1,…, r| on T(Fr+s).
(2) Compute a T-Gröbner basis H of the two-sided submodule U = (g1 − er+1, …,gs -
er+s> ofFr+s.
(3) Compute H = H n Fr+s. Return p (H) and stop.
This is a procedure which enumerates a T -Gröbner basis of the two-sided syzygy module Syz(G), where T is the restriction ofT to T(Fr+s).
Proof. By the above proposition, the two-sided module UnFr+s is isomorphic to Syz(G). Since U n Fr+s is also the component elimination module of U with respect to L, Proposition 14.3.12 implies the claim.
Using the computation of two-sided syzygies, we arrive at the following Gröbner basis algorithm for solving the Conjugator Search Problem (CSP) in certain finitely presented groups. This problem has been used as a basis for group-based cryptosystems in previous chapters.
Problem CSP: Given a group G and two elements g, h ϵ G which are known to be conjugated to each other (i.e., such that there exists an element a ϵ G for which ag = ha), find a conjugator (i.e., find such an element a).
In the sequel we make the following assumptions.
(1) The group G is finitely presented: G = (x1,…, xn; r1 = … = rm = 1>
(2) There exists a word ordering o on (X> such that R = {r1 − 1,…, rm − 1| is a o- Gröbner basis of the defining ideal in Z2 (X> of the group ring Z2 [G].
Thus we can use R to represent the residue class of a word w ϵ (X> in G uniquely by its normal remainder NRo r(W). In particular, we can use R to solve the word problem in G effectively. In this setting, the following algorithm solves CSP in G. We outline its proof which is based on the results of this section. For the full details, we refer to [BK], Section 5.
Proposition 14.3.15 (The Conjugator Search Algorithm). In the setting described above, let w, W ϵ (X) be two words representing conjugated elements of the group G. Consider the following sequence of instructions.
(1) Let F6 be the free two-sided module ofrank 6 over K(X). In F6 form the two-sided submodule
U = (ew − e3, exw’ − e4, e2 − e3 − e5, e2 + e4 + e6,
el(wl − w[),…, ex(wt − w’t), e2(wl − w),…, e2(wt − w’t),
x-e-i − e1x1,…,x„e1 − e1xn,x − e2x1,…,x„e2 − e2xn).
(2) Choose the following module term orderingr on T(F6):for t1, t1, t2, t2 ϵ (X), let
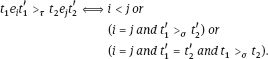
Compute an interreduced two-sided T-Gröbner basis H ofU.
(3) In H there exist elements whose leading term is of the form t¡e5 where t¡ ϵ (X) is the normal remainder with respect to R. Return the words t{ and stop.
This is an algorithm which solves the Conjugator Search Problem in G.
Proof. It is clear that the module term ordering T defined in step 2 is an elimination ordering for both L = {1,2} and L’ = {1,2,3,4}. Hence the elements of H n (e5, e6) form a Gröbner basis of the intersection of Syz(w, w’) and Syz(1, -1).
By assumption, there exists a word a ϵ (X) representing a conjugator such that aw = w’ a. Therefore ae5 − e6a represents a syzygy in Syz(w, w’) and is contained in U. In particular, there exists an element h ϵ H whose leading term is of the form LtT (h) = te5 with t ϵ (X). Since the elements (W¡ − w- )e5 are all contained in U, we may assume that the word t is a normal remainder with respect to R.
Observe that we can consider the computation of Syz(w, w’) n Syz(1, -1) as the composition of the computation of the two individual syzygy moduls combined with the computation of the intersection of two submodules. For all three Gröbner basis computations, we start with a system of generators consisting of binomials. Hence also the computed Gröbner bases consist of binomials. Consequently, the element h ϵ H found above is of the form h = te5 + be5c or h = te5 + b’ e6c’. In the first case, the definition of T yields c =1 and t >a b. This contradicts the fact that we assumed t to be a normal remainder with respect to R. Therefore only h = te5 + b’ e6c’ is possible. Here u ϵ SyzK[G](1, -1) yields t = b’ c’. Hence the element a = (b’)-1t satisfies ae5 − e6a = (b’)-1u ϵ SyzK[G](w, w’). Thus the word a ϵ (X) represents the desired conjugator.
Let us recall that the computation of the Gröbner basis necessary in step (2) is an enumerating procedure. After a new Gröbner basis element has been found and fully interreduced, we can check whether it has the shape required by step (3). Since we assume that w and w’ are conjugates, a suitable element u will be discovered eventually, i.e., our instructions can be performed in such a manner that they define an algorithm.
Up to now, we have used non-commutative Gröbner bases mainly to deal with the computational problems mentioned in Section 9.8 effectively. In the final section of this chapter, we use them to construct cryptosystems whose security relies on the difficulty of computing certain Gröbner bases.
14.4 Non-Commutative Gröbner Basis Cryptosystems
As mentioned previously, the worst-case bounds for the complexity of computing a Gröbner basis are very high. This has led many researchers to suggest cryptosystems whose security is based on the difficulty of computing a certain Gröbner basis. Initial attempts at doing this via commutative polynomials met with a lot of skepticism and mixed success. However, generalizing the approach to submodules of two-sided free modules over the non-commutative polynomial ring provides sufficient freedom to define cryptosystems which are resistant to all known attacks. In fact, in this section we show that moving from polynomial rings to modules over polynomial rings has the added advantage that we can include the operation of a group (or a ring) on a finite (or countably infinite) set in the encryption algorithm. In this way, we can show that all public key cryptosystems discussed in the earlier chapters of this book are special cases of Gröbner basis cryptosystems.
To define the most general kind of Gröbner basis cryptosystem, we use a setting which is slightly more general than that of the preceding sections. Instead of working over the non-commutative polynomial ring K(X>, we work over a monoid ring K[M] where M is a finitely presented monoid defined by a convergent rewriting system, i.e., such that the defining ideal of K[M] has a finite Gröbner basis. Of course, the noncommutative polynomial ring is then nothing but the special case of a free monoid M. More precisely, we consider the following setting.
Let X = {x1,…, xn| be a finite alphabet, and let M = (x1,…, xn;l1 = r1,…,lm = rm> be a finitely presented monoid. Then the monoid ring K[M] satisfies K[M] = K(X>/Im, where IM is the two-sided ideal generated by R = {l1 − r1,…,lm − rm|. We assume that there exists a word ordering o on (X> such that R is a o-Gröbner basis of IM and I, >o r, for i = 1,…, m. Consequently, we can represent every element of M by a word w ϵ (X>, and there is a unique representation by a word NRor(w) which is in normal form, i.e., the normal remainder w.r.t. R of some other word representing the same monoid element.
Furthermore, we let r > 1 and Fr = (K[M] ®K[M])r the free two-sided K[M]-module of rank r. The standard basis of Fr is denoted by {e1,…, er|. Let T be a module term ordering on T(Fr), and for a two-sided submodule U of Fr we let OT (U) = T(Fr) LtT (U).
Definition 14.4.1. A (general, two-sided) Gröbner basis cryptosystem consists of the following data.
(1) Public Information: the monoid presentation of M,the free two-sidedmodule Fr, a subset S of the set OT (U), and finitely many elements u1,…,us ϵ U.
(2) Secret Information: a T -Gröbner basis G of a two-sided submodule U of Fr.
(3) Encryption Procedure: A plaintext unit is an element m ϵ {S>K. The corresponding ciphertext unit is c = m + f1u1g1 + … + fsusgs with suitably (e.g. randomly) chosen elements f,,gj ϵ K[M].
(4) Decryption Procedure: Compute m = NRt G(c).
The correctness of this cryptosystem follows from the fact that every element of Fr has a unique normal remainder with respect to G and this normal remainder is contained in (OT (U)>K. Notice that the correct choice of the elements f,, gj ϵ K[M] in the encryption procedure is crucial for the security of the cryptosystem. It depends on the concrete setting in which this cryptographic primitive is used. For some settings this issue will be discussed later in this section. A similar definition of Gröbner basis cryptosystems is used in [AKr], but it relies on one-sided rather than two-sided modules. However, most remarks and constructions carry over from this case to the two-sided case without problems.
Next we collect some easy remarks about properties and variations of Gröbner basis cryptosystems.
Remark 14.4.2. Let a Gröbner basis cryptosystem be given as above.
(1) If an attacker can compute G, he can break the cryptosystem. In general, the computation of Gröbner bases is EXPSPACE-hard.
(2) The attacker knows u1,…,us and S, but not a system of generators of U. We can make his task difficult by choosing u1,…,us such that a Gröbner basis of (u1,…, us> is hard to compute.
(3) The advantage of using modules (rather than two-sided ideals in K (X>) is that one can encode hard combinatorial or number theoretic problems in the action of the terms on the canonical basis vectors (see the examples below).
(4) The free module Fr is not required to be finitely generated. Any concrete calculation will involve only finitely many components.
(5) We shall also consider the following variant: for the ciphertext unit we construct a pair c = (f0, mf0 + f1u1g1 + … + fsusgs) wheref0 ϵ K[M] is a further randomly chosen element. Then the decoding procedure consists of computing NRt g (mf0 + f1u1g1 + … + fsusgs) = NRt >G(mf0) and “dividing” by f0 to obtain m. In this way we achieve some additional data hiding: the summand mf0 on the right hand-side resembles the other summands. However, there is no general method for performing the “division” NRt G(mf0) ^ m. We have to provide an explicit procedure in every individual example.
In the following we give some examples of Gröbner basis cryptosystems. In particular, we show that many classical cryptosystems can be realized as special cases.
Example 14.4.3. Let K = Fq be a finite field, where q = pe with a prime number p and e > 0. Let M be the monoid M = N” = (x1,…,xn; x,xj = XjX, = 1forall i, j>.Weusethe module F1 and submodules containing (x,e1 - e1xi>, i.e., ideals in the commutative polynomial ring K[M] = K[x1,.. .,xn]. Choose a point (a1,…, an) ϵ K”. Let U = (x1 - a1,…,xn - an> and choose elements u1,…,us ϵ U such that u,(a1,…,an) = 0 for i = 1,…, s. Consider the following Gröbner basis cryptosystem.
(1) Public information: The polynomial ring K[x1,.. .,xn], a term ordering T on T”, the set OT(U) = {1|, and the polynomials u1,…, us.
(2) Secret key: The point (a1,…,an) ϵ K” corresponding to the Gröbner basis G = {x1 - a1,…, xn - an| of the ideal U.
(3) Encryption procedure: A plaintext unit m ϵ K is encrypted as the polynomial c = m + u1f1 + … + usfs with randomly chosen polynomials f1,…, fs ϵ K[M].
(4) Decryption procedure: Compute m = NRt G(C) = c(a1,…, a”).
Clearly, this is Neal Koblitz’ Polly Cracker Cryptosystem from Section 13.2. Unfortunately, it allows many dangerous attacks, as we have seen in Section 13.3.
A number of improvements of Koblitz’ original approach have been proposed. Many of them fit our scheme.
Example 14.4.4. In the setting of the preceding example, choose a second commutative polynomial ring Q = K[y1,…,ym] and polynomials g1,… ,gm in K[M]. In this way there is a K-algebra homomorphism 0 : Q —> K[M] given by 0 (y,) = g, for i = 1,…,m. Choose a point (<1,…,<n) ϵ K” and elementsf1,…,fs ϵ Q such that 0 (f1),…, 0 (fs) ϵ U = (x1 - <1,…,X” - <“>. Now construct the following Gröbner basis cryptosystem.
(1) Public information: The rings K[M] and Q, the homomorphism 0, the term OT(U) = {1|, and the polynomialsf1,…, fs ϵ Q.
(2) Secret key: The point (<1,…, <n) ϵ K”, or equivalently, the Gröbner basis {x1 - <1, …, X” - <“| of the ideal U in K[M].
(3) Encryption procedure: We proceed in a similar way to the variant above. A plaintext unit is an element m ϵ K. We choose random polynomials h ϵ (1,… ,fs>, a polynomial h’ ϵ Ker(0), and a random exponent K ϵ N”. Then we send c = (yK, myK + h + h’) where y = (y1,.. .,ym). In other words, an attacker knows the pair (0 (y)K, m0 (y)K + 0 (h)).
(4) Decryption procedure: Compute v = [m0(y)K + 0(h)](<1,…,<n) = m0(y)K • (<1, …,<“) and obtain m = v/[0 (y)K(<1, …,<“)].
This is Le van Ly’s Polly Two Cryptosystem (see [vLy]). Compared to Polly Cracker, it has the advantage that the usual linear algebra attacks do not work. It appears that an attacker has no choice but to compute a (possibly hard) Gröbner basis. Supposedly hard concrete instances of this cryptosystem have been suggested, but were not able to withstand side-channel attacks.
Now we show that the RSA Cryptosystem is in fact a Gröbner Basis Cryptosystem.
Example 14.4.5. Let K = Z2, let X = {x,y|, and let M = N2 = (x,y;xy = yx>. Then K[M] = K[x, y] is the commutative polynomial ring in two indeterminates. Moreover, let p, q » 0 be two distinct prime numbers, let n = pq, and let n = be the set of residue classes prime to n. We use the free module Fn = ©”=0 K[x, y] e, and the term ordering T = deglex-pos. Choose a number e ϵ Zjp_1)(q_1) and compute the inverse d 0of £ in Z(p_1)(q_1).
(1) Public information: The module Fn (and thus the number n), the set OT (U) = {e0,…, en_11, the number e, and the vectors {u1,…, us| = {e,x - ej£modn | i = 0,…, n - 1|u {e,xy - e, | i = 0,…, n - 1|.
(2) Secret key: The secret key consists of the primes p and q and the number d. Equivalently, the secret key is the T-Gröbner basis G = {u1,…, us| u {e,y - e,dmodn; i = 0,…,n - 1| of U = (G>.
(3) Encryption procedure: A plaintext unit is a vector em ϵ OT (U). To encrypt it, we form em + (xyem - em) - (xem - yemmodn) ϵ em + U to obtain the ciphertext unit
c = yenf modn.
(4) Decryption procedure: Compute NRTG^m-modn) = em^modn = em.
It is easy to see that this is the Gröbner basis version of the RSA cryptographic primitive studied in Section 7.5. If an attacker is able to factor n, he can break the system. This is equivalent to being able to find d. In the Gröbner basis version, the problem the attacker faces is that he does not know the Gröbner basis elements ye, - e,dmodn.
Also discrete logarithms can be used in Gröbner basis cryptosystems.
Example 14.4.6. Let K = Z2, let X = {x|, and let M = (X> s N. Then K[M] = K[x] is the univariate polynomial ring over K. Moreover, let p » 0bea prime number. We use the K[x]-module F2p_2 = ©f=_11 K[x]e, ® ©p_11 K[x]e;- where e,-, ej are the standard basis vectors. Let g be a generator of the multiplicative group Z*, and let T = deg-pos with e,- >T ej for all i, j = 1,…,p - 1. Choose a number a ϵ {1,…,p - 1| and compute b = gamod p. Now we introduce the following Gröbner basis cryptosystem.
(1) Public information: The module F2p_2, i.e., the primep, the set OT(U) = {e1, e2, …, ep_1|, the number b, and the vectors {u1,…, us| = {e1 - e1| u {xe, - | i = 1,…, p -1 |u {xe;- - ebj | j = 1,…, p -11 where all indices are computed modulo p.
(2) Secret key: The number a ϵ {1,…,p - 1|, or equivalently, the T-Gröbner basis G = {u1,…, us|u - eja | i = 1,…,p - 1| of U = (G>.
(3) Encryption procedure: A plaintext unit is of the form e1 + em with a number m ϵ {0,…,p - 1|. Using the variant, we randomly choose a number k ϵ {0,…,p - 1|, form (e1 + em)xk and send the ciphertext unit c = + embk ϵ xk(e1 + em) + sup>(u1,…,us>.
(4) Decryption procedure: We compute NRT G(c) = ebk + embk. Since ebk + embk reduces via G to xk(e1 + em), we have to “divide” this vector by xk .To this end, it suffices to compute m = (mbk)/(bk) in K and to form e1 + em.
Clearly, this is the Gröbner basis version of the ElGamal Cryptosystem of Section 8.1. It can be broken if the attacker is able to compute the discrete logarithm a of b = ga or k of gk. In the Gröbner basis version, an attacker can only reduce using egt via U¡ to xkex and then via u1 to xke1. This takes k » 0 reduction steps. If one knows a, one can get rid of the vector egt by using just one reduction step egt —> egka = ebk.
The next example is based on non-commutative polynomials. In order to prevent linear algebra attacks, T. Rai suggested in his doctoral thesis [Rai] to construct Gröbner basis cryptosystems utilizing two-sided ideals in K(X).
Example 14.4.7. Let K be a (finite) field, let X = {x1 ,…,xn}, and let M = (X). Then K[M] = K(X) is the non-commutative polynomial ring. We choose a two-sided ideal
I c K[M] for which we know a finite (two-sided) Gröbner basis G = {g1;… ,gt} with respect to some word ordering T .
(1) Public information: The ring K[M], the set OT (U), and a finite subset {u1,…, us} ϵ I such that computing a Gröbner basis of (u1,…, us) is infeasible.
(2) Secret key: The T -Gröbner basis G of I.
(3) Encryption procedure: A plaintext unit m is an element in (OT (U))K. The corresponding ciphertext is c = m + f1 u1g1 + … + fsusgs where the non-commutative polynomials fi, gi are suitably chosen so that in the computation of c many leading term cancellations occur (see [Rai], Section 4.1).
(4) Decryption procedure: Compute m = NRT G(c) using the Gröbner basis G.
In [Rai] several concrete instances of this cryptosystem are proposed. They offer good resistence to linear algebra attacks because using indeterminate coefficients for the polynomials fi and gj leads to systems of quadratic equations in these coefficients which cannot be solved using linear algebra. However, one has to take great care to make these instances secure against attackers who are able to compute partial Gröbner bases (see [Rai], Chapter 4).
Our approach also includes the group based cryptosystems studied in Chapter 11. The following Gröbner basis cryptosystem relies on the difficulty of solving the conjugator search problem in certain groups.
Example 14.4.8. Let K be a field, and let M = (x1,…,xn; r1 = … = rm = 1) beafinitely presented group. We use the free two-sided K[M]-module Fr = ©wgM K[M] ewK[M] ® ©weM K[M] ew K[M] (which is possibly of infinite rank). Moreover, let T = llex-pos be such that % >T eu for all w, u ϵ M. Choose a, g ϵ M and compute g’ = a-1ga. Now consider the following Gröbner basis cryptosystem.
(1) Public information: The module Fr, the elements g, g’ ϵ M,asetB c{b ϵ M; ba = ab}, the set OT(U) = {ew; w ϵ M}, andthevectors {uA; A ϵ A} = {eh - eh-1ih | i, h ϵ M} u {eg - eg, }u {e;k - ek-1jk | j, k ϵ M}.
(2) Secret key: The element a ϵ M, or equivalently, the T-Gröbner basis G = {uA | A ϵ A| u - ea-1ia | i ϵ M| of the two-sided submodule U = (G> of Fr.
(3) Encryption procedure: Randomly choose an element b ϵ B. A plaintext unit m ϵ M is written in the form eg + egim, where m = bmb_1. Then we use the elements uA to obtain the ciphertext unit c = eb-1gb + eb-1g,mb.
(4) Decryption procedure: Find NRt g(c) = ear1g„a + eb-gbm = eb-1gb + eb-gbm first, where g” = b-1gb. Then determine m using the equality m = (b-1g,b)_1 • (b^g’bm).
As one can readily check, this is a Gröbner basis version of an ElGamal like cryptosystem based on a group with a “hard” Diffie-Hellman conjugacy problem, i.e., the problem to find a_1b_1gba given g, a_1ga and b_1gb where a and b commute. One can solve this problem if, given g and g = a_1ga, one can find a1, a2 such that a1ga2 = g’ and a1, a2 commute with the elements from B. The advantage of knowing the Gröbner basis is that one can pass from eg to the corresponding e, without going through the reduction steps eg —> egi. The computation of that Gröbner basis is equivalent to finding a.
To perform the encryption step explicitly, one has to perform the following simple computations in the group: Conjugate g’ with b to obtain b_1g,b and multiply with the plaintext m. Conjugate g with b to obtain b-1gb.
If we want to decrypt the ciphertext eb-1gb + eb-1gtmb knowing the secret a, an explicit decryption amounts to performing the following: conjugate b_1gb with a to obtain the Gröbner basis element eb-1gb - ea-1b-1gba, reduce c via this element in one step to NRt G(c) = ea-1b-1gba + eb-1a-1gabm and obtain m by multiplying the inverse of the first index with the second index.
So, all computations performed to encrypt and decrypt are actually computations in the group M.
In Chapter 11 braid groups have been suggested for this kind of cryptosystem. However, we mentioned that there is a polynomial time algorithm to solve the Diffie- Hellman conjugacy problem in braid groups. If one chooses reasonable parameters, this algorithm is not feasible today, but it seems that the braid group based version of this cryptosystem may not be secure in the future.
In the final part of this section we collect some remarks about the security of Gröbner basis cryptosystems.
Remark 14.4.9 (Linear Algebra Attacks). Several types of linear algebra attacks have been proposed which apply to special Gröbner basis cryptosystems.
(1) The basic type is the attack proposed in the original paper [FK]. In the equation c = m + f1u1g1 + … + fsusgs, the attacker regards the coefficients off,,gj as unknowns and tries to solve the resulting system of equations. In our setup, it is possible to make this attack infeasible:
(a) In general, the system of equations will be quadratic rather than linear.
(b) Now suppose that the system of equations is linear in a particular setup. By choosing a large set OT (U), we can make the plaintext m “similar” to the cyphertext c, so that the resulting linear system of equations involves | OT (U)| coefficients. By using a module of large rank, we can make the solution of this linear system infeasible. Moreover, since we are working over a monoid or group ring, many products (e^t’ with e£ ϵ Supp(u;) and t ϵ Supp(f) are going to yield the same term, so that the corresponding coefficients cannot be recovered.
(2) The “intelligent” linear algebra attack suggested by H. W. Lenstra described in [Bar] is based on the idea that in the equation c = m + f1u1g1 + … + fsusgs one can guess the terms t occurring in the support of u1,…,us if t • Suppf) intersects Supp(u), and that the list of all such terms is not too large. As before, in our approach this attack can be repelled in several ways, for instance by choosing a large set OT (U), by working over group rings, or by using a free module of large rank. In each case sufficient cancellation happens during the computation of the cyphertext.
Remark 14.4.10 (The Attack Using Characteristic Terms). If a representation c = m + f1u1g1 + … + fsusgs is such that there are terms in c which do not belong to OT (U) and therefore not to Supp(m), then it is sometimes possible to reveal individual messages by performing suitable linear algebra on the coefficients of c and the elements ft, gj. In particular, this works if there exist “characteristic terms”, i.e., terms which occur in just one of the elements ft, gj. By recognizing multiples of these terms in the ciphertext one can then reconstruct a constant message unit. As before, this attack rests on the fact that plaintext units are small, i.e., that OT (U) is small. Furthermore, if several products t •t’ with t ϵ Supp(u,)and t’ ϵ Suppf) u Supp(gj) contribute to one coefficient of c, this attack becomes infeasible. Thus the defensive measures described above apply.
Remark 14.4.11 (Chosen Ciphertext Attacks). In the proposed cryptosystems the receiver has no method to detect invalid ciphertexts. In addition, since decryption is K-linear, the chosen ciphertext attacks described in [Ko2] are possible. However, by using suitable hash functions the system can be made secure in the following way: The sender appends a suitable random value to his message, computes the hash value of the result, and transmits the ciphertext of the message together with the ciphertext of the random value and the hash value. If the receiver detects an invalid ciphertext, he refuses to decrypt or returns a meaningless or random decryption result.
Altogether, it appears that there are sufficiently many defenses for Gröbner Basis Cryptosystems to the known attacks. In fact, breaking them in general would entail breaking essentially all cryptosystems in practical use today.
14.5 Exercises
14.1 Let X = {x1,…,xn}, and let a be a complete ordering relation on (X) which is compatible with multiplication. Prove that the following conditions are equivalent.
(a) The relation a is a well-ordering, i.e., every non-empty subset of (X) has a minimal element.
(b) Every descending chain w1 >a w2 >a … in (X) is eventually stationary.
(c) For every w ϵ (X), we have w >a 1.
14.2 Show that the length-lexicographic word ordering llex defined in Example 14.1.4 is indeed a word ordering.
14.3 Let K be a field, let I = (x2 - xy) c K (x, y), and let a be a word ordering on (x, y) such that x >a y. Prove that Lwa(I) = (xyix | i > 0) (see Example 14.1.10).
14.4 Prove the Non-Commutative Division Algorithm 14.1.13. Proceed as in the proof of the commutative case 13.1.10.
14.5 Let P = Z2(x1,…,x6), let a = llex, and let G = (g1,…,g5), where the non-commutative polynomials gi are defined as in Example 14.1.17. Using Buchberger’s Criterion 14.1.16, prove that G is a a-Gröbner basis of the twosided ideal (G).
14.6 Consider the dihedral group D3 = (x, y; x3 = y2 = (xy)2 = 1) and its group ring Z2[D3] = Z2(x,y)/I,whereI = (x3 + 1, y2 + 1, (xy)2 + 1).
(a) Show that I has the llex-Gröbner basis G = {y2 + 1, yxy + x2, yx2 + xy, xyx + y, x2y + yx, x3 + 1}.
(b) Find the shortest word representing the inverse of x2y in D3.
14.7 Let X = {x1, …,xn} and I ϵ {1,…, n}. Show that the ordering elim on (X) defined in Example 14.2.2 is a word ordering and an elimination ordering for L = {x1,…,xf}.
14.8 Work out the proof of Lemma 14.2.3.
14.9 Consider the infinite dihedral group DTO = (x, y; y2 = (xy)2 = 1).
(a) Using the method of Remark 14.2.7, prove that the element x ϵ DTO has infinite order.
(b) Similarly, compute the order of the element yxy in the group D3 = (x, y; x3 = y2 = (xy)2 = 1).
14.10 Let G = (x1,…,xn;r1 = … = rm = 1) be a finitely presented group, let Y = {y1,…, yn} be a set of further letters such that yi represents xr1, let h1,…,hk ϵ (X, Y) be words whose residue classes generate a subgroup H = (h1,…, hk) of G, andletS be the subalgebra S = Z2(h1 - 1,…,hk - 1) of Z2[G]. Prove that, for a word w ϵ (X, Y), the following conditions are equivalent.
(a) w ϵ H
(b) w - 1 ϵ S
14.11 Consider the free Q(x, y)-module F2 of rank 2 and the module term ordering T = Pos-llex on T(F2).Let M bethe Q(x, y)-submodule of F2 generated by g1 = x2x1e1x2 + e2 and g2 = exx + x1e1. Using Buchberger’s Procedure for Modules 14.3.9, enumerate a T-Gröbner basis of M. Showthat G = {g1, g2, x2x^-1e1 + (-1)ke2x2k-5 | k > 3} is a T-Gröbner basis of M.
14.12 Formulate and prove a semi-decision procedure for the submodule membership problem in finitely generated K(X)-submodules of Fr.
14.13 Let K be a field, let X = {x1,…,x„},andletM = (v1 ,…,vs) and N = (u1,…, ut ) be two K(X)-submodules of the two-sided free module Fr. Consider the inclusions »1 : Fr ^ F2r given by »1(e,-) = ei and î2 : Fr ^ F2r given by *2(ef) = er+i. Moreover, let
V = (»1(v,-) + »2(v,-) | i = 1,…, s) + (»2(u;-) | j = 1,…, t).
Prove that M n N = V n(e1,…, er) and conclude that a system of generators of M n N can be enumerated via Buchberger’s Procedure for Modules.
14.14 Let K be a field. Consider the following special case of the Gröbner basis cryptosystem described in Example 14.4.7.
Secret Key: h = z - c ϵ K(x, y, z) with c ϵ K.
Public Information: f = x - a, g = y - b, u1 = fhg + gh, and u2 = ghf + hg
in K (x, y, z) with a, b ϵ K.
Show that this instance is not secure, because the secret key can be derived from the public information.
14.15 Let K be a field. Consider the following special case of the Gröbner basis cryptosystem described in Example 14.4.7.
Secret Key: f1 = z - a, f2 = w - b in K(x, y, z, w) with a, b ϵ K.
Public Information: u1 = xf1y + xf2y + yf1 + yf2 + f1 + f2 and u2 = yf1x + yf2x + Ay + f2y + A + A.
Show that the secret key cannot be read off the public information. Then explain how this instance can be broken by computing a partial Gröbner basis of U = (u1, u2).
14.16 Let K be a field. Consider the following special case of the Gröbner basis cryptosystem described in Example 14.4.7. In K(x1, …,x6), consider the words w1 = x1x3x5x4x2x6, w2 = x1 x5x2x4x3x6, and w3 = x1x2x3x4x5x6.
Secret Key: h = w3 + c1x1 + … + c6x6 + c0, where c0,…, c6 ϵ K {0} are arbitrary constants.
Public Information: f = w1 + a1x1 + … + a6x6 + a0 g = w2 + b1x1 + … + b6x6 + b0, where a1, bj ϵ K {0} are arbitrary constants, u1 = fhg + gh, and u2 = ghf + hg.
(a) Prove that the private key can be deduced from the public information as follows: first show that Lwff (h) = w3, Lwff(f) = w1, and Lwff(g) = w2 for a suitable word ordering a. Then find the coefficients c0,…, c6 from the coefficients of u1 and u2.
(b) Modify this instance such that the attack described in (a) fails.
