Multilayered Access Control Implementations
Implementing multiple layers in security is providing a defense-in-depth mechanism and, therefore, stronger protection for the network and users. Multiple layers provide multiple road blocks for a user and attacker. Having multiple controls in place before something can be accessed may be tiresome for a user; however, the goal is to have the same effect on an attacker. If an attacker is able to find a hole and access a company’s network, additional layers of security might stop the attacker from reaching other systems, applications, or sensitive data.
Creating layers within the network can be done physically by segmenting users and servers onto separate networks. This can also be done logically through virtual local area networks (VLANs). Implementing security measures at each logical level of access such as application access or file access puts up additional road blocks for attackers. Making security a hierarchical structure with layers versus implementing just a few controls provides the strong defense needed to protect the overall infrastructure.
User Access Control Profiles
User access control profiles identify authorizations allowable for each user, such as what access is allowed and what is denied. You can implement user access control profiles with role-based access controls. Implementing a role-based access control allows you to manage the infrastructure with greater control. Role-based access is implemented for a large group of people who perform similar tasks and helps prevent a single user within a role from having more rights than others. Role-based security saves you time by ensuring all controls are applied to a particular role. For example, suppose you’ve already defined the access controls for the Sales Representative role. When a new sales rep is hired, you simply assign that person to the Sales Rep role instead of assigning access controls separately.
This technique benefits a multilayered access control implementation because the role may have additional access controls added or removed, depending on the risk associated with a user’s job functions. If the risk associated with a role increases, the access controls placed on the roles can change with it. For example, sales reps may be given less access to their territories’ sales figures at the end of the quarter because the finance department is compiling the financials for all regions. Allowing the sales representatives to change data while the finance department is using the data would create a problem for the entire organization.
System Access Control Lists
System access control lists (SACLs) identify which users have access to systems and what rights they have once each system is accessed. Is the system a read-only database or can users write to the database? Providing accessibility metrics and monitoring user actions help ensure the system is secure. They can also indicate that access changes need to occur.
Designing a system that meets the needs of the users but does not provide more access than is needed should be at the core of system security. Restricting access at the system level limits what changes can occur on the system. One example is restricting the installation of software, which makes the system more secure and limits the chances of Trojan horses and malware being installed. FIGURE 7-1 identifies categories of software restriction policies in the Microsoft Windows operating system.
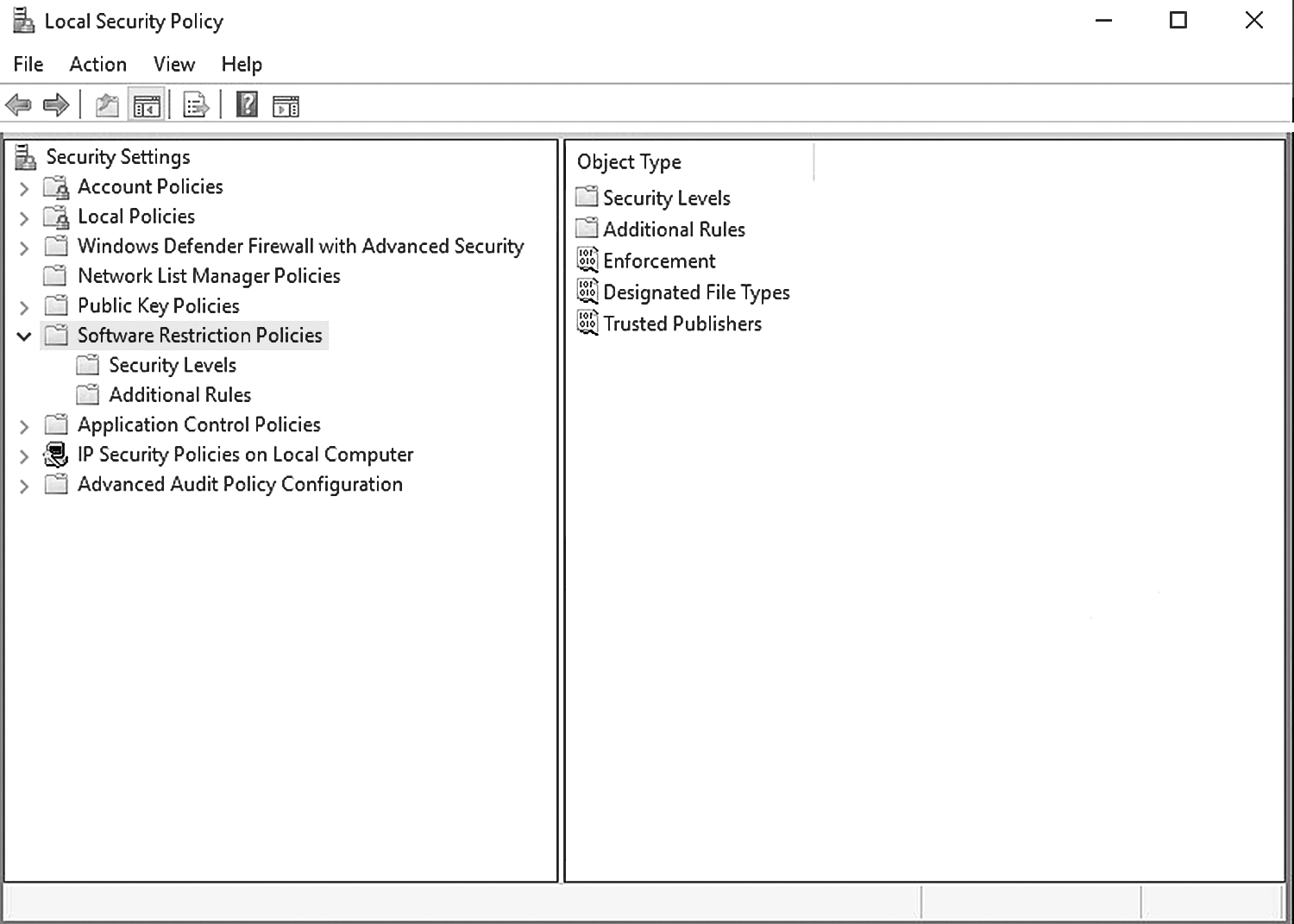
FIGURE 7-1 Categories of software restriction policies.
Used with permission from Microsoft.
The three policies that can be implemented for software download restrictions are:
- Enforcement—Enforces additional policies automatically (see FIGURE 7-2)
- Designated File Types—Determines what types of files can be downloaded to the system, such as EXE files, scripts, or ActiveX controls (see FIGURE 7-3)
- Trusted Publishers—Provides the ability to allow or not allow code that was provided from a trusted source (see FIGURE 7-4)
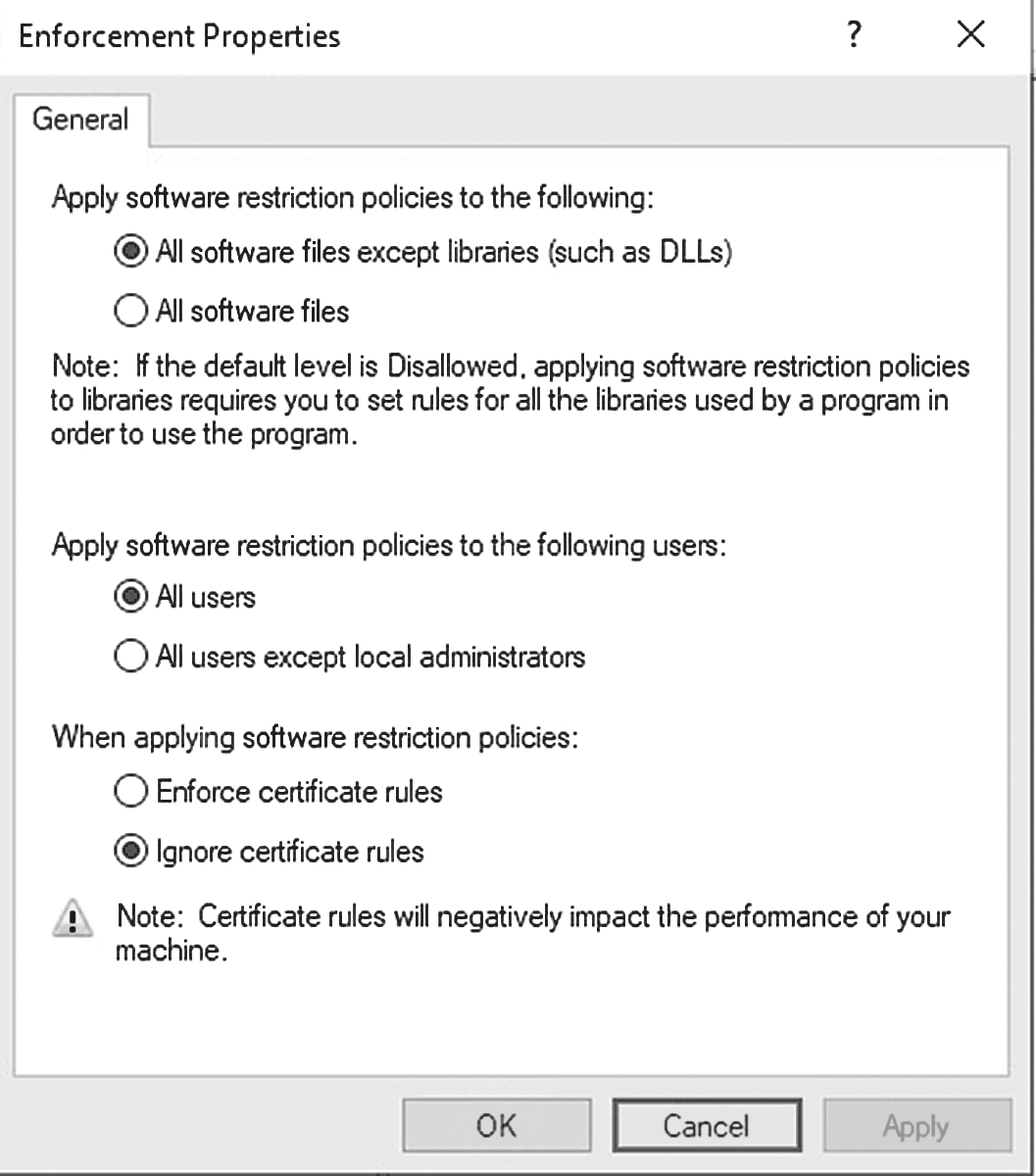
FIGURE 7-2 Enforcement properties.
Used with permission from Microsoft.
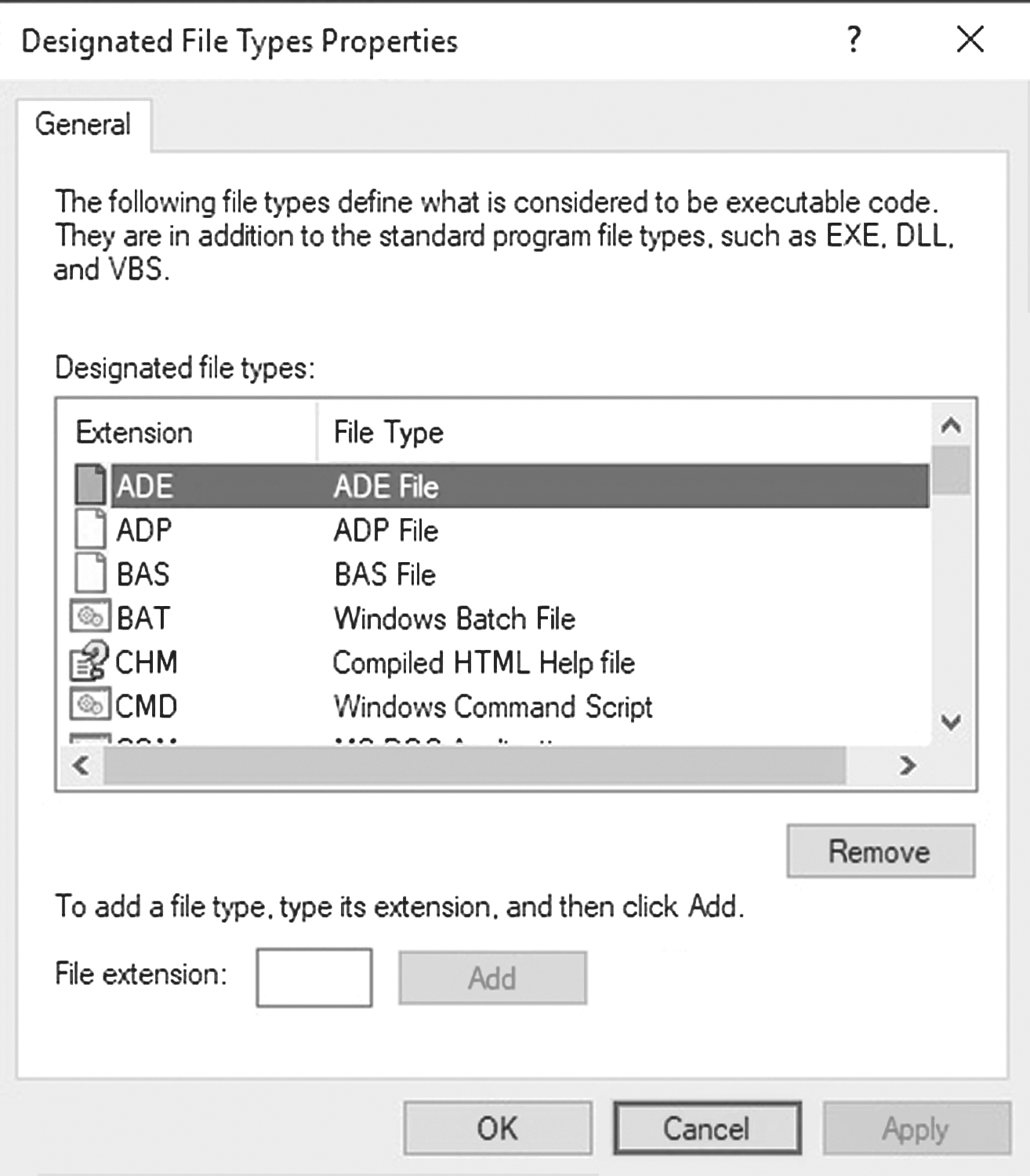
FIGURE 7-3 Designated File Types properties.
Used with permission from Microsoft.
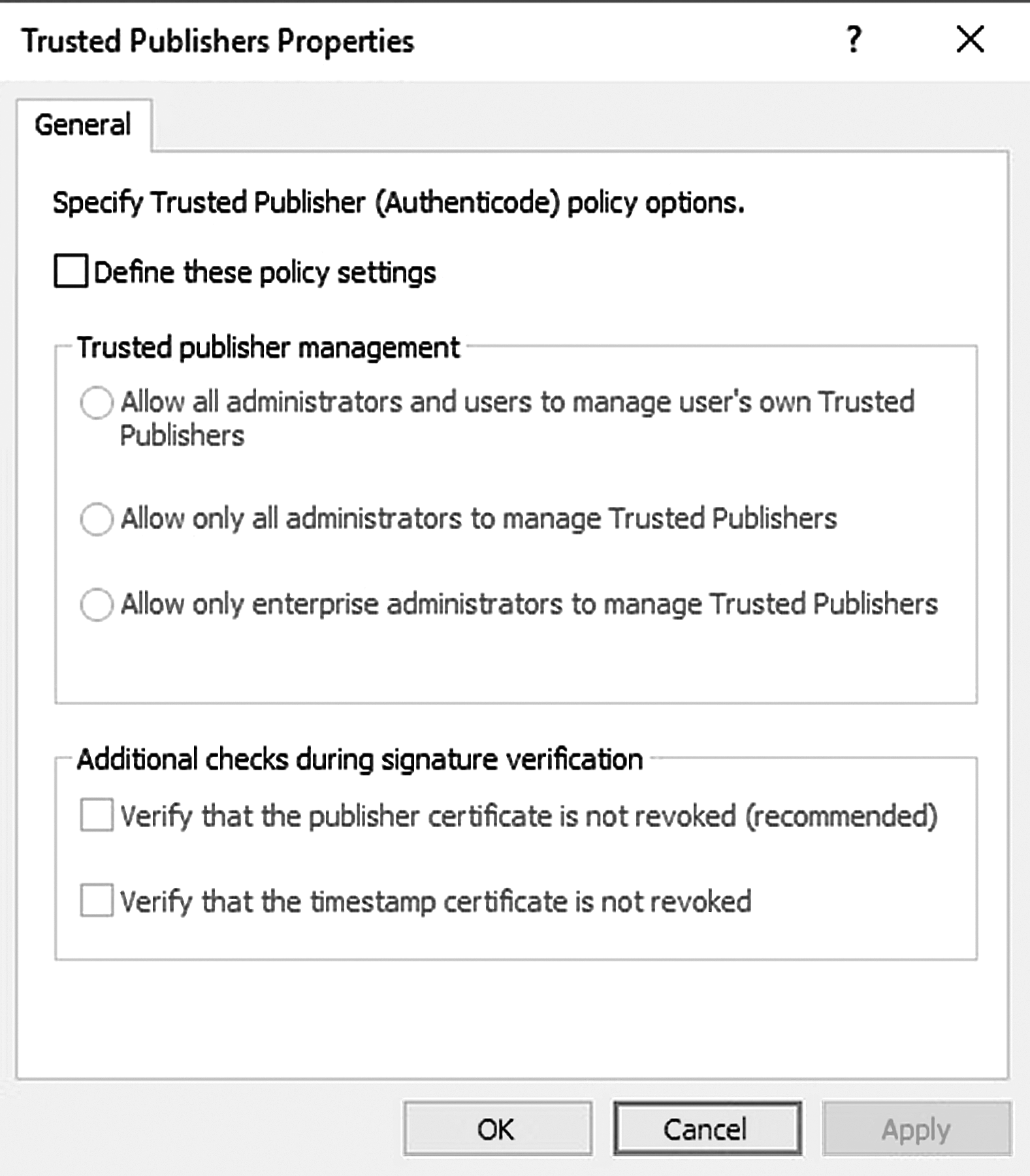
FIGURE 7-4 Trusted Publishers properties.
Used with permission from Microsoft.
Implementing security at the system level is important when implementing a multilayer access control system. It limits access to the greater system. This ensures that employees who should not be installing software or making changes to the system are not given access. As you learned earlier in this chapter, best practices for computer systems have been established by standard bodies. If an organization bases its computer system configuration on these best practices, an administrator should ensure that there are no computer system configuration changes that will result in an unsecure system.
Applications Access
Employees may be given full or limited amounts of access to the systems and applications that access data. Applications may have direct controls placed on them, such as limiting execution. Once launched, an application may have access controls that allow only specific users to view certain fields or that allow certain features to be used within the application.
In addition, applications may be read-only for some users but not others. Changes or additions may be restricted to only the owner or administrator of an application. Policies are established for each application, ensuring the accessible information is not compromised by a user or an attacker. These controls can also identify the types of data each user can view in the application and how the data should be displayed.
For example, an administrator can place specific controls on Microsoft SQL Server to ensure users cannot access data, create new databases, or change the application without appropriate permission. A SQL server has various roles that provide specific access. Several of these roles and the access granted are:
- dbcreator—Can create databases and alter and restore its own databases
- serveradmin—Can change server-wide configuration options and shut down servers
- sysadmin—Can perform any activity in the server
These access controls provide yet another layer of security on top of controls at the system level. If a failure occurs at the system level, the application access controls provide security. These layers ensure that the system and data are not completely vulnerable to attacks.
File and Folder Access
If users are not given access to certain applications, access to the location of the data may be limited as well. Assigning controls to files and folders adds yet another layer to a multilayer structure. Limiting read and write access to files and folders ensures the data cannot be compromised. Privileges need to be limited by whom and what can access specific files and folders. Administrators should assign privileges based on need.
Scott, for example, has documents that are customer-specific, such as organizational charts and contact information, on his corporate computer system. Scott’s customer wants assurance that this information is not available to its competitors. Scott needs to block access to his coworkers who support his customer’s competitors. FIGURE 7-5 shows how these controls could be put in place against a file or folder.
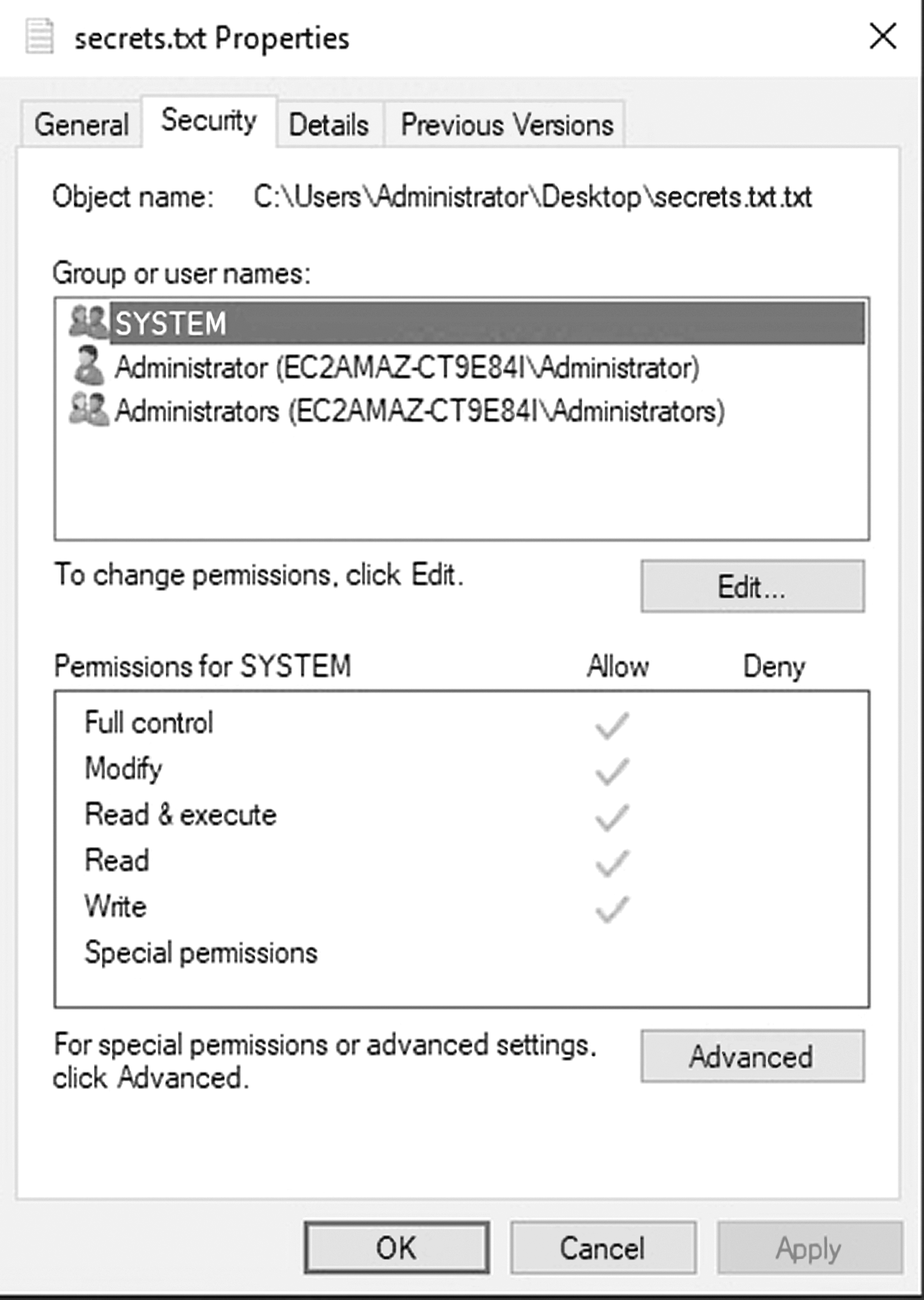
FIGURE 7-5 File system access control.
Used with permission from Microsoft.
Employing this access control provides yet another layer of protection in a multilayer access control implementation.
Data Access
After passing through most of the layers of access control, limiting access to the data itself is your last method of protecting it. A privilege such as read or write is an example of a security measure placed against data. As mentioned previously, many database applications, such as Microsoft SQL Server, provide controls to limit access to data.
Results or statistics are only as reliable as the data that they are based on. If the data are changed or augmented, the work that is being done on the data will be unreliable. Limiting access to data protects all who rely on the data, including individuals and systems. Allowing full access leaves data vulnerable to attack and human error. It may not be the intent of an individual to erase or destroy data, but accidents happen.
